RISK: THE NEW FRONTIER IN SECURITY
Find out why the modern SOC must be a team of de-riskers
FROM BLUEPRINT TO REALITY
Digital twins for transport safety and security

Find out why the modern SOC must be a team of de-riskers
Digital twins for transport safety and security
Convergint — Country Director KSA, Saif Al Shahrani, shares his vision for the company’s growth plans into Saudi Arabia



Altronix has the solutions you need to integrate critical infrastructure and provide power for all your surveillance and security applications.
And our powerful LINQTM network management platform lets you remotely monitor and control all your devices from a single-pane platform.
We’ve got it all covered.
EDITORIAL
Publisher
Barry Bebbington
+44 1708 229354
barry@pubint.co.uk
Editor
Cora Lydon
+44 7834 244613
cora.lydon@securitymiddleeastonline.com
ADVERTISING
Worldwide
Mike Dingle
+44 1752 267330
mike@securitymiddleeastonline.com
Ryan Bickerton +44 1752 265802
ryan@securitymiddleeastonline.com
Gareth Driscoll
+44 1752 260603 gareth@securitymiddleeastonline.com
Rahul Vara
+44 1752 604352 rahul@securitymiddleeastonline.com
Marketing Manager
Paul Riglar
+44 7496 377630 paul@securitymiddleeastonline.com
Digital Editor
Britt Jones
britt@securitymiddleeastonline.com
PUBLISHED BY
Publications International Ltd
+44 1708 229354
166 Front Lane, Upminster, Essex, RM14 1LN, UK
This publication may not be reproduced or transmitted in any form in whole or in part without the written consent of the publishers.
©Publications International Ltd. 2024
For subscriptions and advertising enquires, or for further information on the magazine visit our website at: securitymiddleeastmagazine.com

As the security landscape in the Middle East continues to evolve at a rapid pace, it’s imperative for industry professionals to stay informed and ahead of the curve. Our magazine is dedicated to providing you with the latest insights, trends and best practices shaping the region’s security landscape.
In this issue, we delve into the transformative power of technology in enhancing security solutions. From digital twins revolutionising transport security (page 42) to AI-driven video analytics transforming surveillance (page 19), the Middle East is at the forefront of innovation.
We’re also excited to highlight the upcoming Security Middle East Conference 2025, taking place on May 13th at the prestigious VOCO Hotel Riyadh (page 17). This premier event brings together industry leaders, experts and decision-makers to discuss the latest trends, challenges, and opportunities in the security sector.
Our features cover a wide range of topics, including the critical importance of securing industrial control systems in today’s interconnected world (page 27) and the need for separating security practices for physical and information security (page 30), as well as understanding the evolving nature of threats and the strategies needed to mitigate them (page 59).
We hope this issue provides you with valuable insights and resources to navigate the complex and dynamic world of security.
Cora Lydon Editor
cora.lydon@securitymiddleeastonline.com
smemag
Security Middle East Magazine

03 Up front
Foreword from the Editor
06 News Monitor
The latest regional and international security news
08 Market Monitor
A roundup of the latest security products and solutions
12 Cover story: Convergint
Saif Al Shahrani, Country Director, KSA, Convergint MEA, shares the company’s ambitions as it expands into the region
19 Industry Insight: Visual Intelligence in association with Bosch
Bosch takes us through its ‘power to predict’ ethos and how AI-driven video surveillance can become powerful visual intelligence
17 Security Middle East Conference 2025
The Security Middle East Conference is returning once again in 2025 with an improved programme of activities and exciting new initiatives
27 Bridging the IT-OT divide
Daniel Norman, Regional Director, EMEA, ISF, looks at how vital it is to secure industrial control systems as they become interconnected with IT networks
42 Transit’s new shield
Digital twins are revolutionising the transport sector. We find out how they’re being used to bolster security already in the region
51 Powering integrated security solutions in the Middle East
Sales Team Lead MEA at TRASSIR, Valery Mymrin, shares news of the company’s partnership with Suprema
52 How mobile credentials are changing the access control landscape
Faisal Mohamed, CEO of ScreenCheck at Centena Group, looks at the role mobile credentials have in supporting easier access control
54 Real-time eyes on crime
Firas Jadalla, Regional Director, META, Genetec, explores how real-time crime centres can unify data and operations across city departments
78 Beyond the swipe
Eugeniya Marina, Business Development Director, MENA, RecFaces, looks at biometrics in education
48 Who’s got your back(up)?
30 Convergence of the security bastions
Separating the security practices of physical security and information security is no longer useful, says Ian Keller, a global information technology expert
35 Lock down your finances
Shiraz Kapadia, CEO and President of Invixium, looks at strengthening the foundations of financial integrity with access control solutions
38 Milipol Qatar
Anne Frayssinet, Milipol Network Director, exclusively shares her insights into the growing homeland security market
Businesses relying solely on Microsoft 365 backups could be leaving critical information vulnerable warns Charles Smith, Consulting Solution Engineer, EMEA, Data Protection at Barracuda Networks Inc

59 Risk redefined
The modern SOC must be a team of de-riskers, according to Maher Shehab, Security Solutions Architect at Qualys
62 Cyber Warfare: A military mindset
James Gerber, CFO of SimSpace, explores why taking a military approach to cybersecurity can help organisations win the undeclared cyber war
76 Interview: Oil and gas
Meshal Aljohani, Security Operations Specialist, discusses the oil and gas industry with Ahmed Ibrahim Abd Allah, Geo-Unit Senior Security Manager at Control Risks
82 Diary
Diary dates for forthcoming security exhibitions, conferences and events
65 Shaping the Kingdom’s future
Find out more about this year’s Saudi Arabia edition of Intersec and what it offers for security professionals
68 Intersec Saudi Arabia Agenda
Explore the programme of presentations and debates planned for the show
71 Meet the exhibitors
Hear from some of this year’s exhibitors ahead of the event
CONTRIBUTORS

Saif Al Shahrani
Country Director KSA, Convergint MEA
Saif Al Shahrani has a background in engineering and a strong strategic vision for supporting Convergint MEA as it supports the Kingdom on its transformative journey.

Daniel Fernandez
VP Sales & Marketing META, Bosch
Daniel Fernandez’s role at Bosch benefits from his strong focus on strategy deployment and business development in different markets in the Middle East, Africa and Europe.

Ian Keller
Global Information Technology Expert
Ian has over three decades of experience, and has served as Executive for Information Security at multinational companies across numerous industry verticals.

Daniel Norman
Regional Director, EMEA, Information Security Forum (ISF)
Daniel Norman’s role at the ISF is to help organisations manage their current and emerging cyber risks.








Intersec Saudi Arabia officially sold out two months before the exhibition’s start date.
A record number of 300 exhibitors, representing a 25 per cent increase on last year’s number, and more than 17,000 visitors are expected to attend.
The event will welcome 138 new exhibitors, including Saudi Arabian companies Draeger Arabia, Emdad Najed Company and SETRA Saudi Electronic Trading & Contracting Ltd, as well as 162 returning companies, representing 27 countries.
Three country pavilions have also been confirmed, including China, the Czech Republic and the UK, further underscoring the event’s international standing.
Organised by 1st Arabia and licensed by Messe Frankfurt, the exhibition will be held under the patronage of the High Commission of Industrial Security and in association with the

Ministry of Interior and Saudi Civil Defence. It will return for a sixth edition from 1 - 3 October at the Riyadh International Convention and Exhibition Center (RICEC).
Bilal Al Barmawi, CEO and Founder of 1st Arabia Trade Shows & Conferences, said: “Due to the sheer demand from exhibitors, Intersec Saudi Arabia has reaffirmed its position as a leading showcase for the security, safety and fire protection industries. We look forward to welcoming these record numbers to Riyadh when the exhibition returns in October.”
intersec-ksa.ae.messefrankfurt.com
INTERNATIONAL NEWS
According to new research from the Qualys Threat Research Unit (TRU), between January to mid-July, the common vulnerabilities and exposures (CVE) count rose by 30 per cent from 17,114 in 2023 to 22,254 in the same period in 2024.
The increase in CVEs reflects rising software complexity and the broader use of technology, which is necessitating advanced and dynamic vulnerability management strategies to
mitigate evolving cybersecurity threats.
A thorough analysis of the 22,254 reported vulnerabilities during the initial 7.5 months of 2024 (up until the research cut-off date of July 21, 2024) reveals that a precise subset of 0.91 per cent has been weaponised, and a very small fraction accounts for the most severe threats.
This subset represents the highest risk, characterised by

weaponised exploits, active exploitation through ransomware, threat actors, malware, or confirmed wild exploitation instances.
The analysis also indicates an increase in the weaponisation of old CVEs since the onset of 2024. Over the last 7.5 months, there has been a notable increase, slightly over 10 per cent, in the weaponisation of older CVEs identified before 2024, which is a stark reminder that
cybersecurity is not just about staying ahead but also about not falling behind.
Some of these vulnerabilities have been trending on the dark web for months. One such example of this is CVE-202343208 NextGen Mirth Connect Java XStream (Qualys Vulnerability Score 95/100), which heavily involves systems used by healthcare organisations around the world. qualys.com
Vertiv and Gulf Data Hub (GDH) have revealed details surrounding their transformational multi-year data centre collaboration project at a facility dedicated to advancing biotechnological research and renewable energy generation in Dubai, UAE. Vertiv supported GDH in successfully deploying a new purpose-built, state-of-theart data centre in Dubai Silicon Oasis, helping to achieve high energy efficiency and operations.
This collaboration recognises their shared commitment to establishing new data centre efficiencies and sustainability benchmarks in the region, leveraging Vertiv’s
uninterruptible power supply (UPS), energy storage and cooling technologies.
For almost 10 years, Vertiv has lent its expertise and resources to help realise GDH’s project potential, providing nextgeneration technologies and solutions that have proven influential in helping meet critical milestones.
The Dubai Silicon Oasis data centre’s implementation has enabled GDH to maintain robust operational efficiency with enhanced power usage effectiveness (PUE) while at the same time supporting worldclass functionality standards. vertiv.com

Security Essen, happening 17-20 September at Messe Essen, is set to unveil a host of innovative new products for the security market, including:
• Eibenholz: protective clothing that is comfortable to wear, fashionable shirts, pullovers and vests that are cut-, stab-, and bullet-resistant.
• Security Robotics: Artificial dog robots used for patrols in security.
• Energy Robotics: AI software that is used for autonomous inspections used with robots, to detect gas leaks, people and defects in fences.
• Heylogin: password manager with hardware-based end-to-end encryption that works without a master password.
• Safe2Home: Self-developed wireless alarm systems. security-essen.de
Experts from countries across Asia, the Middle East and Africa took part in the Standoff cyberbattle, which was held in 2024 as part of the Saint Petersburg International Economic Forum for the first time. The Oman team took on over two dozen countries to test their cybersecurity defence tactics.
Dr Mohammed Hamad Al-Kuwaiti, Chairman of the UAE Cybersecurity Council, has announced that the council is currently finalising three new policies aimed at strengthening the country’s cybersecurity framework. These policies, set to be unveiled by the close of 2024, are designed to reinforce the UAE’s stature as a global leader in advanced technology and Artificial Intelligence (AI).
Discussions between the governments of Maldives and the United Arab Emirates (UAE) have been held to boost cybersecurity cooperation efforts. The Head of the UAE Cyber Security Council Dr Mohamed Al Kuwaiti led the delegation and according to the Maldives Police Service (MPS), the visit aimed to enhance relations and boost cybersecurity cooperation between both parties.
A national campaign to protect children from online exploitation was launched by the Bahrain government to raise cybersecurity awareness among children and protect them from fraudsters. The Himaya campaign is set to run until the end of the year and is being overseen by the Public Prosecution in co-operation with various ministries.
Security solutions provider Ahram Security Group is currently undergoing an integrated study to establish a new factory in Riyadh next year. The goal of the new factory will be to increase exports to GCC countries while also meeting the demands of the lucrative Saudi Arabia market.
According to Samir Aref, the group’s Chairman, who spoke to Al Arabiya
Business, construction on the factory is anticipated to start early next year, with it being operational in 2026.
According to Aref, Ahram Security Group is in discussion with the National Bank of Egypt to borrow around EGP 500m for the expansion plan, while the group is also looking to a grant from the Ministry of Environment and self-funding the remaining sum.
The Ministry of Transport, Communications and Information Technology (MTCIT) has issued comprehensive security guidelines designed to enhance information security practices across government entities in Oman. The guidelines will ensure the protection of valuable information assets and standardise cybersecurity measures.
The use of mandatory biometric fingerprinting in Kuwait has led to the apprehension of hundreds of individuals who were wanted for crimes. The initiative was implemented at Kuwait International Airport and land crossings in May 2023.
e-con Systems™ has unveiled its latest product, See3CAM_CU31, a 3MP HDR Low-Light USB Camera.
The new high-performance camera includes a unique combination of USB interface as well as the advanced SONY ISX031 automotive-grade sensor.
This USB camera leverages sub-pixel HDR technology and offers an HDR performance of up to 120 dB, along with LED Flicker Mitigation. The technology ensures clear, motion-blur-free images even in highly dynamic environments, while LFM allows for stable image capture under flickering light sources.
In addition to its HDR capabilities, the See3CAM_CU31 camera excels in capturing superior images in low-light conditions. With plug-and-play functionality, See3CAM_CU31 offers easy integration, allowing you to quickly set up and start using the camera without any complex configurations.
Suresh Madhu, Head of Industrial Business Unit at e-con Systems
SentinelOne has unveiled a series of new Purple AI, Cloud, Endpoint and Identity innovations to the company’s Singularity Platform.
Announced at Black Hat 2024, the new offerings and capabilities all leverage the industry’s most advanced generative AI technology, modern secureby-design single-agent architecture, and most performant data lake to protect organisations against attacks across any surface, from endpoint and identity to the cloud.
“Our latest innovations are designed to give security teams the ability to see everything, already prioritised and contextualised, so that they can stay ahead of attacks and strengthen their security posture across every surface from a single platform,” said Ric Smith, Chief Product and Technology Officer, SentinelOne.
A new capability delivered as part of the Singularity Platform, xSPM provides real-time insights into vulnerability and misconfiguration that security teams can use to drive enterprise-wide visibility and control across cloud, endpoint, identity and third-party risk.

Intelligent scoring and contextual assessment ensure teams effectively prioritise risk, with integrated guidance and native remediation to accelerate decision-making and improve security posture. sentinelone.com

said: “See3CAM_CU31 represents a substantial leap forward in HDR and low-light imaging technology with USB. We are confident it will offer significant benefits to our customers across various industries. This camera delivers exceptional performance and versatility making it an ideal choice for diverse applications like dashcams, intelligent transportation systems (ITS) and more.” e-consystems.com
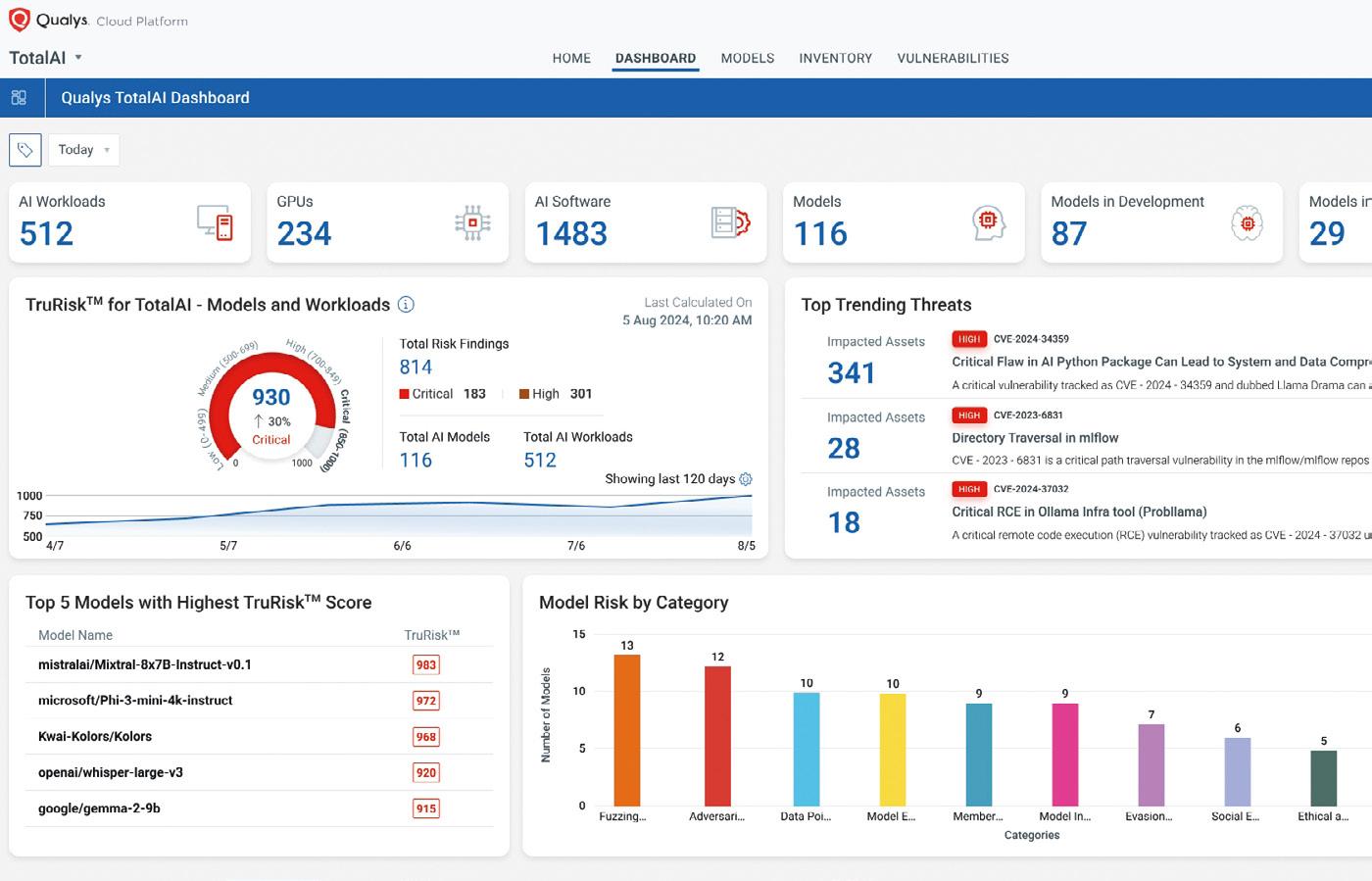
Qualys, Inc. has announced it is expanding its portfolio with Qualys TotalAI, a solution to address the challenges and risks associated with securing generative AI and large language model (LLM) applications.
As businesses increasingly integrate AI and LLMs into their products and solutions, they face an expanded attack surface and heightened cyber risks.
Traditional cybersecurity practices are now insufficient to address these new challenges which has led to a rise in threats to unknown or unapproved LLMs or AI models.
Qualys TotalAI harnesses the features the Qualys platform is known
for, to empower organisations in confidently adopting AI technologies.
“As the global adoption of AI and large language models (LLMs) accelerates, outpacing governance and safety measures, it’s crucial for organisations to implement robust protections,” said Philip Bues, Senior Research Manager at IDC Cloud Security.
“Qualys TotalAI is focused on providing businesses with the tools they need to confidently secure their AI investments, offering comprehensive visibility and defence against emerging cyber threats.”
qualys.com
Hear, be heard and be understood, every time and everywhere for any environment

Our extensive unified communication portfolio enables us to provide one-stop solutions for all your communication needs, including PAVA, IP Speakers, Intercoms, and Help Points. Zenitel’s communication solutions deliver exceptional audio intelligibility, scalability, and reliability for safety, security, and infotainment applications.
With a wide range of integrated solutions, we empower you to seamlessly incorporate audio into your access control, video management, and other security platforms.
With hundreds of communication systems deployed, Zenitel Middle East is the proven and preferred communication partner for environments requiring crystal-clear audio to protect human life, properties, and other assets.
Zenitel Middle East is driving the future of Unified Critical Communication solutions.



Core42 and AIREV have announced the launch of the OnDemand AI Operating System (AIOS) – the first significant joint effort since their partnership announcement in February this year.
OnDemand, developed by AIREV and built on Core42’s foundational infrastructure, is a decentralised AI operating system designed to facilitate seamless AI deployment. It offers developers, engineers, enterprises and startups a robust platform to build, deploy and manage their AI applications with ease.
OnDemand includes the ability to facilitate AI model deployment directly from sources like Hugging Face, supporting both
open-source and closed-source models. It also allows users to deploy their own models, offering flexibility and customisation.
Talal Alkaissi, Chief Partnerships & Government Affairs Officer, Core42, said: “This groundbreaking platform exemplifies our commitment to driving AI innovation
Barracuda Networks, Inc. is bringing its global support for MSPs to the Middle East.
The move will enable channel organisations across the region to better support their customers through a comprehensive suite of managed security services.
These services include threat prevention, detection and response across attack surfaces such as email, endpoint, network and more, which will create layers of security around customers’ data, users and reputation.
The launch underscores Barracuda’s commitment to supporting Middle East partners in creating or strengthening sustainable revenue streams.
In its recent TheEvolvingLandscape oftheMSPBusinessReport2024, the company found that globally, IT service providers expect 44 per cent of revenue to come from recurring managed services in 2024, up from 34% in 2023.
barracuda.com
Group-IB has signed a global partnership agreement with SecurityHQ, an independent Managed Security Service Provider (MSSP).
With this partnership, SecurityHQ will leverage Group-IB’s Threat Intelligence, Attack Surface Management and Digital Risk Protection to boost its global Security Operation Centres (SOCs), as well as Fraud Protection services as part of its portfolio to enhance the defences for its financial services customers.
The signing of the MSSP agreement was held at Group-IB’s headquarters in Singapore, between Vladimir Goliashev, Director of MSSP and MDR of Group-IB, and Aaron Hambleton, Director (MEA) of SecurityHQ.
“This collaboration is a significant step forward in advancing global cybersecurity efforts. By integrating our cutting-edge solutions in Attack Surface Management, Threat Intelligence and Digital Risk Protection with SecurityHQ’s extensive expertise and operational reach, we are enhancing the capabilities of Security Operation Centres (SOCs) worldwide,” said Goliashev. group-ib.com, securityhq.com
and empowering businesses across the Middle East and beyond. By leveraging Core42’s state-of-the-art infrastructure, we are enabling developers and enterprises to unlock unprecedented capabilities and accelerate their journey towards a smarter, AI-driven future.”
core42.ai
Trend Micro Incorporated has announced a strategic partnership with Intel to bring cuttingedge, AI-enabled security solutions to consumers. Through this collaboration, Trend Micro will integrate Intel’s next-generation Lunar Lake processors into its advanced consumer security offerings. This integration will empower users to experience unparalleled privacy and performance while safeguarding themselves against emerging AI-driven threats.
“As the adoption of AI-powered devices and applications continues to surge in the MMEA markets, with the total expected gains of AI in the region reaching US$320 billion by 2030, it is crucial that we provide consumers with the most robust security solutions to protect their digital journeys,”
said Dr Moataz Bin Ali, Regional Vice President and Managing Director, MMEA, Trend Micro.
“We are pleased to collaborate with Trend Micro on AI solutions leveraging our next-generation Intel Core Ultra processors (code name Lunar Lake). Specifically, Trend Micro will be the first to utilise Lunar Lake’s 48 NPU Tops on their email defence feature to run scans locally, increasing user privacy and security while lowering latency,” added Carla Rodriguez, VP and General Manager of Client Software Ecosystem Enabling at Intel. “Intel enables a broad and open ecosystem and brings unmatched scale and channels for AI ISVs like Trend Micro.”
trendmicro.com

Convergint is aiming high in Saudi Arabia with ambitions to be the leading service provider of innovative, tech-focused solutions. We find out more from Country Director KSA, Saif Al Shahrani
Convergint MEA, a leading global systems integrator specialising in delivering comprehensive technology and security solutions tailored to the unique needs of mission-critical verticals, is on a mission to make its mark in Saudi Arabia. With a strong presence in the UAE, Iraq and South Africa since 2003, Convergint MEA will be bringing its wide range of solutions and services — including design, installation and maintenance of advanced security systems — to Saudi Arabia and carving out its niche for meeting and exceeding customer expectations.
As Saudi Arabia accelerates its development under Vision 2030, Convergint MEA is emerging as a key player in providing the essential security infrastructure and solutions to support the nation’s ambitious goals. With a strong regional presence and a deep understanding of the local market, the company is uniquely positioned to deliver tailored solutions addressing the specific challenges and opportunities facing organisations in the Kingdom. Leveraging its extensive expertise in security systems integration, Convergint MEA offers a comprehensive range of services. Its commitment to localising operations and building strong partnerships ensures that clients receive the highest level of support and service. And by providing innovative solutions that combine advanced technologies
with a focus on efficiency and scalability, Convergint MEA is helping to drive Saudi Arabia’s digital transformation and secure its future.
Can you tell us about your career to date?
I have had the privilege of building a career deeply rooted in the engineering and technology sectors. My journey began with a solid foundation in engineering management, where I gained critical hands-on experience in managing complex projects. Over the years, I transitioned into leadership roles, where my focus shifted toward strategic growth, operational excellence and market expansion. This blend of hands-on experience and strategic vision has shaped my approach to leadership and has been instrumental in my journey to this point.
What qualities and experiences will you be bringing to Convergint MEA?
With 23 years of experience in the Saudi market, I bring to Convergint MEA a blend of strategic vision and operational expertise, my engineering background enables me to tackle challenges with a technical mindset, ensuring that solutions are both innovative and practical. Additionally, my experience in leading diverse teams and driving business development across various markets will be crucial in aligning Convergint’s offerings with the unique
needs of our customers in the region. My commitment to fostering strong client relationships and a deep understanding of regional market dynamics will be key assets in driving Convergint’s growth.
What will Convergint MEA be bringing to the Kingdom?
Convergint is bringing a wealth of global expertise in technology and security systems integration, combined with a strong commitment to localising our solutions to meet the specific needs of the Kingdom of Saudi Arabia. Our approach is centered on delivering world-class security solutions that enhance safety, security and operational efficiency. We are also committed to developing local talent and contributing to the country’s economic development through strategic partnerships and collaborations. Convergint’s global footprint, combined with our deep understanding of the local market, positions us uniquely to support the Kingdom’s ambitious growth plans.
What approach will the company take in KSA, particularly around the proliferation of the region’s giga projects?
Convergint’s approach to the giga projects in Saudi Arabia is to be a trusted partner that delivers tailored and scalable technology and security solutions that align with the unique demands of these
transformative initiatives. We understand that these projects are not just about building infrastructure but about creating sustainable, secure environments that drive economic growth and societal advancement. Our strategy involves leveraging our global expertise, particularly in smart technologies and integrated systems, to provide solutions that enhance security while supporting the broader objectives of these giga projects. At Convergint, we work closely with our customers and stakeholders to ensure our solutions are fully aligned with the vision and goals of each project.
How is Convergint MEA working to align with Vision 2030?
Convergint MEA is fully committed to supporting Saudi Arabia’s Vision 2030 by aligning our services with the Kingdom’s goals of diversification, sustainability and technological advancement. We are investing in the development of smart, integrated security solutions that not only protect assets but also contribute to the creation of smart cities and sustainable communities. Additionally, we are focused on building local capabilities, including the training and development of Saudi talent, which is a cornerstone of Vision 2030. By providing cutting-edge security solutions and fostering innovation, Convergint aims to play a vital role in supporting the Kingdom’s transformative journey.
We deploy a range of smart technologies that are at the forefront of the systems integration industry. These include advanced security and AI-video analytics, complex IT Infrastructure and data centres in addition to audio-visual solutions and AI software developments, like dashboards that provide real-time insights and enhance decision-making. We are also leveraging advanced cybersecurity measures to protect against digital threats, ensuring that our clients have a comprehensive security solution that covers both physical and cyber domains. These technologies are not only improving security but also driving operational efficiencies and enabling our clients to meet their strategic objectives.
The Kingdom of Saudi Arabia presents significant growth opportunities, particularly in the areas of smart city development, critical infrastructure

protection and the security of giga projects. As the Kingdom continues to invest heavily in infrastructure and technology, the demand for advanced security solutions will only increase. Additionally, the government’s emphasis on digital transformation and cybersecurity opens up new avenues for growth, particularly in providing integrated solutions that enhance both physical and digital security. Convergint is well-positioned to capitalise on these opportunities through our comprehensive suite of services and deep market expertise.
Saudi Arabia faces several unique security challenges, including the protection of critical infrastructure; safeguarding its vast and rapidly expanding urban areas; and addressing the complexities of cybersecurity in an increasingly digital world. The Kingdom’s strategic importance, coupled with its ambitious growth plans, also makes it a target for various security
threats. At Convergint, we are focused on addressing these challenges through innovative, integrated solutions that combine physical security with advanced technologies like AI and IoT. Our goal is to provide holistic security solutions that not only protect but also enhance the operational efficiency of our customers.
My ambition for Convergint MEA is to establish it as the leading systems integrator in the Kingdom and to be our customers’ best service provider, known for delivering innovative, tailored solutions that meet the unique needs of our customers. I aim to expand our operations across the Kingdom by building strong partnerships, investing in local talent and continuously innovating. By applying this I am confident that we can achieve significant growth and make a lasting impact not only in the Kingdom but across the region. convergint.com/convergint-middle-east




Multiple

server
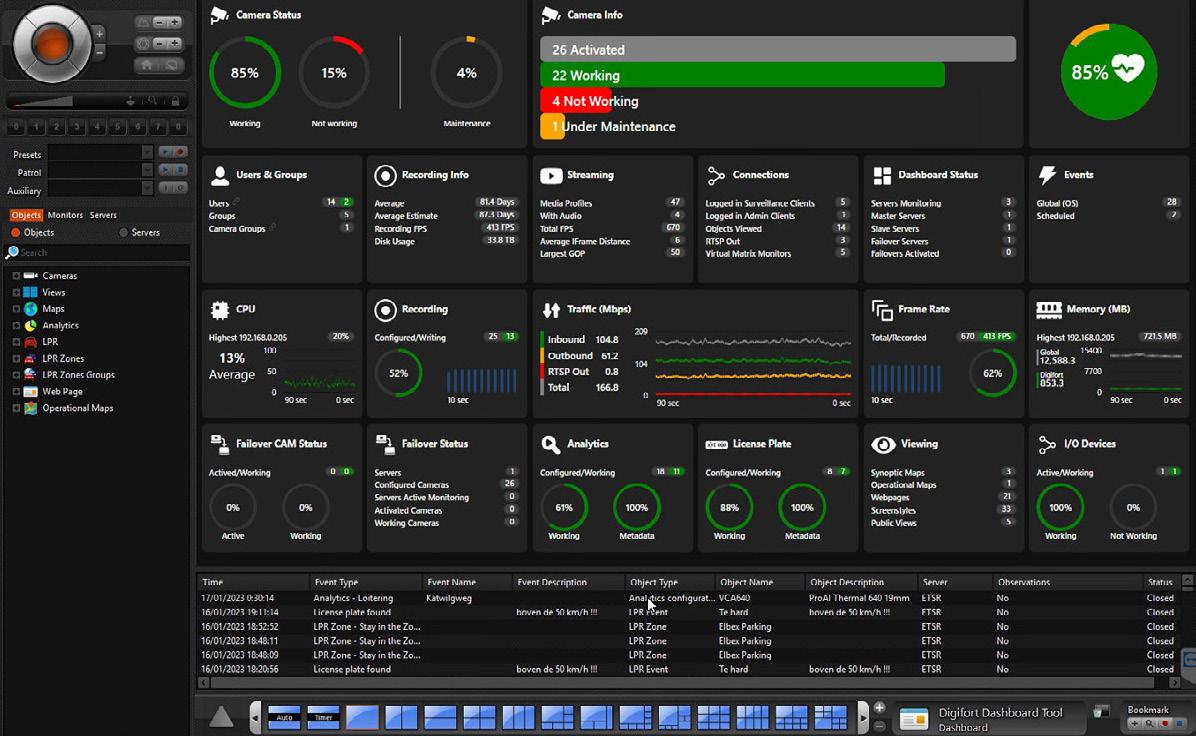
Recording,

Camera function and operational status. Users and Groups plus events.


The countdown is on! The Security Middle East Conference 2025 is confirmed to take place on May 13 2025, at the prestigious VOCO Hotel Riyadh
Saudi Arabia stands at the precipice of a new era, defined by rapid urbanisation, technological advancement and a steadfast commitment to security.
The Kingdom’s ambitious Vision 2030 has ignited a transformation across sectors, with security and safety as paramount pillars. As a result, the demand for innovative solutions and cutting-edge technologies has surged — and the Security Middle East Conference aims to support the evolution of the sector and facilitate its growth.
The Security Middle East Conference is perfectly positioned to address these evolving needs and showcase the latest advancements in the industry. Since its launch in 2023, the conference has emerged as the pivotal platform where industry leaders,
visionaries and decision-makers converge to shape the future of the region’s safety landscape.
A premier event in a prime location
Slated for May 13, 2025, and to be held at the prestigious VOCO Hotel Riyadh, the conference offers an unparalleled opportunity to connect, collaborate and learn.
This luxurious venue sets the stage for a high-calibre event, perfectly reflecting the prestige of our distinguished guests — industry leaders, security professionals and decision-makers supporting the advancement of the sector. The setting also mirrors the high standards and excellence we uphold for the event.


The security sector in the Middle East is experiencing remarkable growth, with Saudi Arabia at the forefront of this exciting journey. Driven by ambitious initiatives like Saudi Vision 2030, the Kingdom is prioritising advancements in security technology and infrastructure.
The Security Middle East Conference 2025 is your gateway to this dynamic environment. Here’s what you can expect if you join us for this one-day event:
■ Unparalleled Networking Opportunities: Connect with key decision-makers, industry peers and potential partners from across the region. Forge valuable connections that can propel your business and career forward.
■ High-Profile Workshops and Presentations: Gain insights from leading industry experts on the latest security trends, technologies and best practices. Stay ahead of the curve and equip yourself with the knowledge to excel in this evolving market.
■ Alignment with Saudi Vision 2030: Discover solutions and strategies that directly contribute to the Kingdom’s ambitious development goals. Be part of the conversation shaping a more secure future.
■ Groundbreaking Solutions: Explore the latest technologies and trends shaping the future of security and speak to the companies who are bringing them to life.
More than just a conference, it’s a strategic investment
Whether you’re a security professional or a leading security solutions provider, the Security Middle East Conference 2025 offers unmatched value.
For organisations seeking to make a significant impact on the region’s security landscape, the Security Middle East Conference offers an unparalleled platform. By partnering with us, you gain exclusive access to a high-calibre audience of industry influencers and decision-makers.
■ Gain Direct Access to Decision-Makers: Showcase your brand and solutions to a targeted audience of industry leaders with purchasing power.
■ Forge Strategic Partnerships: Network with key players and build lasting connections that can fuel your business growth.
■ Elevate Your Brand Image: Position yourself as a leading innovator in the regional security landscape.
We are delighted to already have two sector heavyweights join us as sponsors of the Security Middle East Conference 2025. They are Eagle Eye Networks and Convergint MEA, both of whom were sponsors at last year’s events and are delighted to be returning.
And now you have the opportunity to become a part of the region’s premier security event. Secure your spot as a sponsor by emailing ryan@securitymiddleeastonline.com
For individuals working within the field then attendance at the Security Middle East Conference is a ticket to your ongoing career progression.
Joining us for the Security Middle East Conference is an investment in your professional growth and your organisation’s success. By participating, you gain exclusive access to a wealth of knowledge, networking opportunities and industry insights.
Discover the latest trends and technologies impacting the future of security. Learn from industry experts through engaging workshops and keynote presentations. Expand your professional network by connecting with like-minded professionals and potential partners. Stay ahead of the curve and position your organisation as a leader in the security industry.
The conference offers a unique platform to explore innovative solutions, address emerging challenges and contribute to the development of a safer Middle East. Don’t miss this opportunity to enhance your knowledge, expand your network and drive business growth.
Excited for the opportunity to connect, learn, and shape the future of security in the Middle East?
Join us on May 13, 2025, at the VOCO Hotel Riyadh and be part of the conversation that will shape the future of security in the Middle East.
securitymiddleeastconference.com

Find out how video surveillance can become visual intelligence to support security functions
Visit Bosch at Intersec Saudi Arabia to discover how AI-enabled video systems can enhance the security and safety of people and property.
Bosch will unveil its latest products, innovative technologies and predictive-ready video solutions.
Guided by the Power to Predict, the team will show you video security solutions that empower you to anticipate potential incidents and respond proactively or leverage business intelligence beyond security. Ultimately, to give you the ability to know what’s next.
Connect with a team of experienced security professionals to explore AI-driven video analytics solutions specifically designed for the Middle Eastern market.
Don’t miss out — visit Bosch at booth 2-C22.

Bosch is innovating at the speed of AI — leading the transition to predictive video security solutions with visual intelligence. Think AI-enabled cameras and cloud services that extract metadata from your video footage, turning them into valuable insights and supporting informed decision-making. No unwanted alarms. No guesswork. Our AI-enabled solutions can find meaningful information in video footage in real-time, recognise patterns and ultimately help predict what will happen next. So, it’s never been easier to identify and respond to potential risks and unwanted threats. Or improve the safety, security and operational efficiency of your environment.


“AI has radically changed the status quo. Shifting video surveillance from detection to proactive responses.”
Imagine a world where safety and security are a given. Where people and property have 24/7 protection and unwanted incidents are prevented before they ever happen. When you know what’s next, anything is possible.
Bosch calls it the Power to Predict. And it drives the technology behind all its solutions. They may not be able to promise you that utopia just yet, but every innovation takes us one step closer to our vision of a world uninterrupted.
Bosch is laser-focused on creating AI-enabled video security solutions that outsmart potential threats to your safety and security. AI is tipping the value proposition of video surveillance away from detection to delivering visual intelligence that enables proactive responses. With its ongoing investments in edge and cloud AI, it is continuing to enhance the capabilities of cameras, data capture and cloud services to bring users more value.

Bosch delivers predictive-ready solutions designed to support smarter, data-driven decisions that go way beyond the scope of security to enhance business efficiency and performance.

Ask yourself this: your building may be protected to some degree, but are your video cameras? With solutions from Bosch, the answer is a resounding yes.

Build quality matters. The excellence of the products, software and solutions reflects the ongoing dedication to quality.

Daniel Fernández, Vice President of Sales and Marketing for Bosch Video Systems and Solutions in the Middle East, Turkey, Africa and Iberia regions, shares his insights on the challenges and opportunities in the security industry
How does Bosch’s current strategic direction align with the ever-evolving needs of the security industry?
We want to help our customers move from reacting to security incidents to predicting and preventing them. It only makes sense to focus on predictive cyber-secure solutions designed with our customers’ needs in mind.
On the other hand, our core strategy provides more than just traditional security measures. In addition to offering complete end-to-end solutions with AI-enabled cameras, we’re all about embracing open play to build joint solutions with top cloud and VMS partners.
Research indicates that artificial intelligence (AI) is advancing rapidly, and its ability to process
and analyse data is becoming increasingly critical across various industries, such as energy and utilities, transportation, government facilities, cities and building security. AI is reshaping the role of video surveillance by creating what is now known as ‘visual intelligence’.
We have embraced this trend since 2016, making AI a standard feature in all our cameras. Cameras are evolving into versatile tools within the industry, expanding beyond their initial function as recording devices. They offer the potential for exponential value. These devices are no longer just cameras but platforms equipped with multiple sensors such as audio, chemical and temperature sensors.
With AI and analytics applied to these camera sensors, their value to end users could increase
by 10, 100, or even 1,000 times. The traditional practice of monitoring cameras by security personnel day and night is shifting to automated 24/7 monitoring with real-time alerts.
AI is set to revolutionise existing systems, enabling deep searches of recorded content. Future systems will involve real-time video content analysis rather than just storing it.
What are the future trends the security industry will face in addition to AI, and which ones are Bosch most committed to?
With the rise in connectivity and technological advancements, customers are getting more worried about digital trust and regulatory compliance. The surge in data collection also increases the risk of cybercriminals stealing sensitive data. So, it’s becoming increasingly critical for customers to find trusted solutions that offer the right performance, capabilities, data security and privacy protection.
In cybersecurity, we are ahead of our competition having achieved critical cybersecurity certifications: UL 2900-2-3 Level 2 and IEC 62443-4-1 Certificate of Conformity – Industrial Cyber Security Capability. As upcoming regulations like NIS2 and the Cyber Resilience Act are discussed more, it’s useful for security consultants, installers and system integrators to know which products and manufacturers have these certifications when selecting products for their projects. Choosing UL and IEC-certified products can give customers peace of mind. The National Defense Authorization Act in the US is another factor to consider when specifying products for a local or federal government project. That’s why we offer a complete NDAA, section 889(a)(1)(A) compliant portfolio.
Another trend is customisation. To meet tomorrow’s security requirements, we must cater to individual requirements and be as specific as possible. We have introduced a new suite of edge-based, application-specific AI licenses that support this view. Intelligent Video Analytics Pro (IVA Pro) delivers valuable insights for enhanced security, safety and efficiency. The more specific the video analytic algorithms are trained to be, the more reliable and accurate they will be. This will help to keep false alarms to a minimum.
As building security and government facilities sectors continue to grow, we invest in developing solutions for these sectors. They are experiencing a significant increase in activity due to the high volumes of people and vehicles concentrated in specific areas simultaneously. Our latest video surveillance cameras are perfect for commercial and high-security buildings. They leverage visual intelligence to enhance the security and safety of the buildings and their perimeters.
Our entire portfolio is equipped with edge-based AI which allows us to analyse highly congested scenes with improved reliability, identifying and classifying
people and objects. These cameras collect a lot of metadata from the camera at once, allowing the security team to make very early decisions—the power to predict. If you can predict what will happen next, you can prevent things from happening, creating safe and secure environments without disruption.
The hot, arid climate in the Middle East and other extreme conditions pose various challenges for video security systems to perform, let alone integrate video analytics for highly accurate detection. The MIC camera family, for example, is designed to perform in any environment, withstanding high winds, 100% humidity and temperatures from 40 to 65 degrees Celsius. Despite the most extreme conditions, video data can be interpreted directly at the source to improve the security level further and enable video data to do more than security alone.
We believe it is essential to prioritise helping our customers transition from simply reacting to security incidents to being able to predict and prevent them, ensuring their world remains uninterrupted by safety and security concerns. All of this, coupled with the quality of our products, makes them very durable over time. It ensures smooth operation with an exceptional mechanical design.
A people-first business culture. As Simon Sinek says “Our customers will never love our company until our employees love it first”. I have always believed that our people are the real differentiator in our business. Our teams’ passion and commitment are stronger than ever, as we continue to make significant investments in the Middle East.
The Middle East presents unique challenges and opportunities in the constantly changing global security landscape. Bosch Video Systems & Solutions recognises this and is making strategic investments to expand within this dynamic region, making an impact through innovation, expertise and a solid commitment to its customers and their future. Local support and expertise are also crucial. With a new office in Saudi Arabia, we are solidifying the ability to offer local support and expertise. Establishing this presence is central to tackling the challenges unique to the Middle East, including diverse climates, architectural styles and cultural intricacies that impact security requirements. Customers can expect video security solutions that can help them to anticipate potential incidents, enabling a quick and appropriate response or leveraging business intelligence beyond security. We also build robust partnerships. Together, we’re shaping the change and creating a smarter, safer future.


Saudi Arabia’s rapid urbanisation and economic growth have placed a significant emphasis on developing a robust security infrastructure. At the forefront of this development is Bosch Video Systems and Solutions, a leading provider of video security solutions. To gain deeper insights into the company’s strategies and the evolving security landscape in the Kingdom, we sat down with Alaa Ezzeldin, Country Manager in Saudi Arabia, to discuss the company’s role in supporting Saudi Arabia’s Vision 2030, the company’s strategies for addressing local market needs, and its plans for fostering strong partnerships to deliver exceptional security solutions.
Can you tell us a little about Bosch’s position in the Saudi market and your role?
The Bosch Video Systems and Solutions is revolutionising security in Saudi Arabia with our predictive-ready video security solutions. Guided by the Power to Predict, we provide solutions that support data-driven decision-making to enable proactive and timely responses, minimising risks and potential damages. Our mission is to deliver systems that are designed to perform, last, and be accessible no matter what.
We’re expanding and bringing on new team members to support our business, from technical support and training to marketing to sales. The energy and dedication of our teams in the Middle East are fantastic. It’s an exciting time for us. I am looking forward to leading the Video Systems and Solutions team in Saudi Arabia, drawing from my 15 years’ experience within the local security market.
There is a big demand for robust and trusted video surveillance in Saudi Arabia in order to maintain a secure environment for residents and visitors.
Our purpose-built video analytics solutions are designed to meet these stringent needs, revolutionising surveillance, threat detection and response. With our expert suite of analytics, Intelligent Video Analytics Pro (IVA Pro), we enhance building security and operations, traffic monitoring, long-range perimeter intrusion detection around critical infrastructures, and the uninterrupted tracking of objects, even in busy and crowded scenes.
In November this year, we will expand our IVA Pro offering to include solutions such as PPE (Personal Protection Equipment) detection, visual gun detection, appearance search analysing physical attributes, and license plate recognition. These applications are critical for key industries, including smart city projects, government facilities, energy and utilities, transportation and commercial buildings. By deploying these advanced technologies, we contribute significantly to the overall safety and development of Saudi Arabia.
How is Bosch aligning itself to Vision 2030?
Our commitment aligns seamlessly with the Saudi Arabia Vision 2030, a transformation for the economy and the well-being of its people as well as the goals that has been set by the Saudi government. By leveraging our edge-based, application-specific AI side-by-side with our technology partners, we aim to meet the ultimate goal of sustainability, secure environments for citizens and increased operational efficiency and performance for businesses.
How do you intend to work with local partners to improve the customer experience?
In line with our strategic objectives, we are actively seeking powerful channel partnerships with system integrators and distributors in Saudi Arabia. Local partners is a key factor in our success.

These partnerships are crucial for expanding our reach and delivering best-in-class security solutions to a broader audience. By collaborating with local partners, we ensure that our solutions are effectively integrated and maintained, providing unparalleled security and peace of mind.
Furthermore, we are growing our team to be closer to our customers in Saudi Arabia. By expanding our local presence, we can offer more personalised support and better understand the specific needs of our clients. This customer-centric approach allows us to tailor our solutions even more precisely, ensuring maximum effectiveness and satisfaction.
The Saudi Arabia market is a key factor in our vision. By addressing the unique requirements of the local market and aligning with Vision 2030, we are committed
to enhancing security and safety, and contributing to the Kingdom’s development. We will continue investing in critical areas such as our product roadmaps, long-term projects, marketing activities, business development, formidable partnerships and sales resources.
Our roots lie within the Bosch Group, which means innovative thinking is in our DNA. That’s why we’ve put AI at the center of our camera portfolio as a built-in standard since 2016. We will continue to position ourselves as a dependable provider for reliable AI-enabled solutions that meet the current and future needs of the Saudi market.









As industrial control systems become increasingly interconnected with IT networks, the stakes have never been higher for securing these critical infrastructures, says Daniel Norman, Regional Director, EMEA, ISF
One of the major cybersecurity challenges facing security professionals in industries such as manufacturing, oil & gas, construction etc, is the cross-over between threats posed to IT, OT and industrial control systems (ICS) The consequences of cyber attacks on ICS can be incredibly damaging, not only to organisations but human lives.
ICS are converging with information technology (IT) environments, as previously isolated ICS systems become increasingly connected to other networks. With a focus on safety, reliability and performance (SRP), ICS environments operate in a fundamentally different way to IT environments. To embed security and protect ICS environments from cyber threats requires a nuanced approach, which starts with cultural alignment. IT and ICS teams can only pursue a collaborative and
balanced ICS security programme if they understand each other’s environments and respective challenges.
Securing the industrial frontier
ICS in areas such as oil fields, manufacturing hubs, food processing plants and many other locations have historically not required persistent external connectivity. However, changing business requirements along with innovations in technology and the promise of lucrative operational advantage has changed the landscape considerably. This larger attack surface that has been created brings new opportunities for threat actors; information security teams now need to seriously consider how to effectively secure this converged environment without compromising any of its intrinsic value or desired business and safety outcomes.
The convergence of IT, OT and ICS environments has occurred organically, rather than by design, especially since the relationship between ICS and information security practitioners remains in its formative stage. Motivating factors for this convergence include the need to:
■ Retain data from ICS equipment logs and sensors (e.g. production information management systems), whether on-premise or in the cloud, for subsequent analysis (i.e. production interruption investigations).
■ Enable remote access for maintenance and engineering support by employees, manufacturers and third parties.
■ Optimise production and support predictive maintenance through machine learning and artificial intelligence — monitor the environment for potential safety issues or security incidents.
A broad variety of industries now have integrated IT with OT, which has inadvertently introduced cyber risk. For example, in the agricultural industry there is automated livestock feeding; in the shipping industry there is cataloguing and loading of cargo using IT; in retail there is stock management; in pharmaceuticals there are automated control of medications and biochemicals
‘Now is the time for information security teams to proactively seek collaboration with ICS and OT teams.’

— all which used to be isolated, but now with integrated, and in many cases, wireless control access points.
ICS devices were historically designed as a sealed unit, performing a specific function, with direct access to the underlying control hardware, with limited capabilities to make alterations to the device. This has advantages and disadvantages: very little can go wrong with the device itself, but if there is an issue or software vulnerability with the device there is little that can be done to easily resolve it. Inevitably this will involve the manufacturer of the device having to update it. Although this has historically been the case, IT assets are being incorporated within the environment to help improve productivity and create greater visibility of what is happening with the ICS environment. IT assets are therefore becoming an important tool.
Convergence offers significant opportunities that benefit both manufacturers and organisations. As a result, the merging of IT, OT and ICS environments is fast becoming inevitable. Now is the time for information security teams to proactively seek collaboration with ICS and OT teams. Such collaboration should be supported by executive management buy-in, enabling a controlled approach to managing the threats posed by convergence.
The ultimate aim is to work together to achieve a safe and secure converged environment. This requires information security, ICS and OT teams to speak the same language, to formally agree how to work together and to respect each other’s strengths and objectives. While the information security team has become well-versed at communicating
with different business functions, this has not always extended to OT engineers — in part, because there was historically no need. Building rapport begins with a conversation to learn about the motivations of OT engineers and the nuances of the OT environment (where the core focus is safety) especially as it is impractical,or in some cases counterproductive, to directly impose information security standards, policies and controls.
Due to the complexity and safety-induced need for considered change management, securing the ICS environment will not be quick or easy — however, OT and IT teams need to collaborate and coordinate controls and wider security strategies to protect this increasingly targeted environment.
securityforum.org

Key features:
• Automatic vehicle identification
• Cost-efficient reader based on UHF RFID technology
• Adjustable read range up to 10 meters (33 ft)
• Simple integration with all leading access control platforms
• Supports OSDP v2, including secure channel protocol
• Easy installation and maintenance
• Robust reader for outdoor use
Typical applications:
• Car parks
• Staff parking areas
• Gated communities
• Universities


It has been a long-standing tradition to have the security practices of physical security and information security as two distinct separate bastions. But this dual bastion approach has reached the end of its useful life, says Ian Keller, a global information technology expert
Distinct digital and physical boundaries no longer define the threat landscape of today, these have blurred into the grey areas we are so fond of referencing. The threats we face today, and in the future, are multifaceted and often employ a combination of digital and physical means to compromise an organisation. This evolving landscape necessitates this paradigm shift – a convergence of information security and physical security into a unified security strategy.
Previously, information security and physical security functioned as isolated bastions, each addressing distinct threats. Physical security focused on safeguarding buildings, assets and personnel through access control systems, security cameras and on-site security personnel. Information security, on the other hand, concentrated on protecting data and networks through firewalls, intrusion detection systems and data encryption.
The proliferation of interconnected devices, the Internet of Things (IoT), and cloud computing has blurred the lines between the physical and digital worlds. Cyber-attackers can now gain access to physical systems, while physical breaches can open doors for digital intrusions.
A stark example of this convergence can be seen in information-enabled physical attacks. We have seen hackers infiltrating a building’s access control system, disabling security cameras and doors to facilitate a physical theft. Conversely, a physical breach might involve stealing a server or laptop containing sensitive data, or even just the copying of its data. These attacks highlight the vulnerability of physical security to execute a digital exploit and vice versa.
A continued siloed approach leaves organisations exposed to these blended
threats. Communication gaps and a lack of information sharing between teams can hinder a swift and coordinated response. Furthermore, organisations might invest heavily in one area while neglecting the other, creating an uneven security posture; we all know the adage ‘a chain is only as strong as its weakest link’.
This is where a unified security strategy, or the single fortress concept, comes to the forefront. Having both physical and information security measures integrated into one offers significant advantages to the organisation. Some of the key areas where we can see these advantages are:
By sharing data between physical security and information security teams, organisations can gain a more comprehensive view of potential threats. Security information and event management (SIEM) systems can be configured to correlate events from both domains, revealing patterns and anomalies that might otherwise go unnoticed. This convergence of events allows for a faster and more comprehensive response to incidents, minimising potential damage.
The convergence of physical and information security streamlines security operations by eliminating redundant processes and fostering collaboration between teams. A centralised security management system can integrate data from access control systems, security cameras and intrusion detection systems, along with the data collected through traditional cyber technologies to provide a holistic view of the organisation’s
security posture. This has the additional benefits of allowing for cross-skilling staff and potentially reducing the manpower and resources needed to manage separate security systems.
The converged approach eliminates the security gaps that arise from isolated measures. For example, integrating video surveillance footage, physical access control logs, digital access logs and user and entity behaviour analytics can provide valuable insights into suspicious activity by creating a unified view of security events and trends. This comprehensive approach minimises vulnerabilities, making organisations less susceptible to sophisticated blended attacks. This is especially important for national key infrastructure.
It is worth spending a little more time on how this convergence can lead to informed decision-making, which is a critical benefit enabled by the merging of information and physical security. When these areas operate in silos, valuable data is compartmentalised, hindering strategic resource allocation and effective security planning. This unified view provides for a more comprehensive risk assessment. Traditionally, risk assessments might focus heavily on either the information security threats (data breaches, malware, information loss) or physical threats (theft, vandalism). Merging these perspectives creates a truly holistic picture of your risk posture. You can identify how a digital attack might impact physical security (disabling access control) or how a physical breach could expose sensitive
data (stolen information). This broader risk assessment allows you to prioritise vulnerabilities and allocate resources more effectively which in turn leads to a more robust reporting of risk.
Security investment is now data-driven. Imagine having a constant stream of data from access control systems, security cameras, intrusion detection systems and user activity logs. By merging this data, you can analyse trends and identify areas needing improvement based on fact and not assumptions.
This data-driven decision making leads to cost-effectiveness and resource optimisation. Disparate security systems often require separate teams and management processes. Convergence can streamline operations by creating a unified security management platform. This reduces duplication and allows for more efficient use of manpower and
‘Imagine one security team managing all access points (physical and digital) with a single system, eliminating the need for duplicate teams’
resources. Imagine one security team managing all access points (physical and digital) with a single system, eliminating the need for duplicate teams for physical access cards and network access credentials.
Convergence enables proactive threat mitigation. Imagine receiving an alert about a suspicious login attempt originating from an unusual location. With a converged system, you can cross-check this activity with physical security data like badge swipes or video footage. This real-time correlation allows for quicker identification of potential threats and a more proactive response, potentially preventing a successful compromise from occurring.
Most likely the most important element for the shareholders is the return on investment (ROI). Security investments often struggle to demonstrate a clear ROI. With a converged approach, you can track the impact of security measures on both physical and cyber incidents. This data can be used to justify future security investments and demonstrate the effectiveness of your converged strategy.
Convergence fosters a culture of shared responsibility for security across the organisation. When employees understand the interconnectedness of physical and information / digital threats, they become more vigilant and responsible for adhering to security protocols in both digital and physical spaces.
The implementation of this converged security strategy requires you to create a well thought out and defined plan, which like all others, have critical key steps which must be executed successfully. The first is obtaining leadership buy-in. Senior management must champion the convergence initiative and provide the resources necessary to break down silos and foster collaboration between teams. Their active and public support of the convergence will be pivotal for success. This must not be confused with stakeholder management, which is also instrumental in the success of the convergence strategy.
Next is the development of a unified security policy. This is a comprehensive security policy that encompasses both
physical and information measures into a single document. This policy should clearly define roles and responsibilities, incident response protocols and acceptable use of technology amongst others.
Technology integration is another of the key success factors that should be given serious study. Investment must be made in security solutions that can integrate with existing systems across both domains. SIEM tools can play a crucial role in unification of data and facilitating incident response.
As with all changes user training and awareness should also be done. Provide regular training programmes to educate employees about the importance of converged security, the evolving threat landscape, and their roles in maintaining a secure environment and importantly on how to notify the security centre of any potential red flags.
The convergence of information security and physical security is not merely a trend; it’s a necessity for organisations seeking to effectively address today’s multifaceted threats. By breaking down silos, fostering collaboration and leveraging technology solutions, organisations can achieve a holistic security posture.
This unified approach enhances threat detection, reduces risk, improves operational efficiency and ultimately leads to a more secure and resilient organisation. As the digital and physical worlds continue to converge, so too must security strategies to create a robust and impenetrable fortress.


Allied Telesis have been serving the needs of our customers and the telecommunications industry since 1987.
We guarantee secure, reliable technology from a company you can trust. Our hard-earned reputation for performance and product reliability has remained constant, offering highly respected value to our customers and partners around the world.



Eagle Eye Networks is number one worldwide in delivering true cloud video surveillance and artificial intelligence to make businesses more efficient and the world a safer place – all on the only video management platform robust and flexible enough to power the future of video surveillance.


Shiraz Kapadia, CEO and President of Invixium, looks at strengthening the foundations of financial integrity with access control solutions
Many financial institutions continue to use access control systems deployed decades ago. While these legacy systems were once a cornerstone of security, they have become inadequate in the face of evolving risks. Today, advanced biometric access control solutions, such as face recognition, finger vein, or fingerprint represent a significant advancement. Implementing them can enhance overall security aligning financial institutions’ physical security measures with contemporary risk management strategies. Whether it’s a retail bank with a few branches around the city or a larger financial institution at a central location, the entire banking sector faces some
common challenges. In the Middle East, compliance with stringent regulatory requirements is crucial, as each country has its own set of governing bodies and regulations. Banks in the region must adhere to regulations mandated by authorities such as the Central Bank of the UAE, Saudi Central Bank (SAMA) and others. Central to these regulations are mandated security measures to protect customer data and ensure financial stability. By implementing modern biometric solutions, financial institutions can meet these requirements, control access to IT infrastructure and data centres and significantly reduce the risk of cyberattacks and unauthorised access.
With the digitalisation of the banking sector, threats associated with online banking systems take a central focus, but it is important to understand that the risks related to physical security cannot be neglected. Physical security encompasses not only the protection of property, people and assets but also the mitigation of insider threats, fraud and workplace violence. Advanced access control solutions help mitigate unauthorised access attempts within the banking sector’s physical premises, offering capabilities that antiquated systems (i.e. keys or physical cards) simply cannot match such as maintaining a robust audit trail. These solutions leverage cutting-edge technologies and real-time monitoring systems to provide granular control over access permissions, enabling precise tracking of who is entering, when, and which specific areas are being accessed. Additionally, outdated access control solutions are standalone systems that fail to meet the evolving needs of modern banks. They neither comply with the latest data protection laws nor offer necessary real-time reporting functionalities. Without advanced access control devices integrated into every stage of the security system, banks risk compromising their customers’ data and violating local, regional and national laws due to negligence.
There is also a critical need for the convergence of digital and physical security. IT teams have become essential to deploying physical security systems, as even one poorly protected device can have catastrophic consequences. As awareness increases, IT specialists are asking the right questions, and when they are not, manufacturers must lead the conversation. Establishing security infrastructures with end-to-end encryption (dynamic encoding) is crucial to protecting data during communication. Given the volume and sensitivity of data that financial institutions collect and store, encrypting both data in transit and data at rest is essential for additional security. Banks can modernise security systems by taking advantage of new technologies and aligning teams to support the overall security framework.
Banks require sophisticated access control systems that are capable of discerning the nuances between authorisation and authentication, accurately recognising the distinction, and adhering to access requirements accordingly. Authorisation ensures that personnel at varying levels of responsibility are granted appropriate access privileges. Clerks and other frontline staff cannot access high-security areas like vaults or safe deposit box rooms, which are reserved for high-level management. There was a time when the primary concern of banks was preventing robberies and acts and regulations were passed to address
This multi-layered approach substantially mitigates the risk of security breaches.
Selecting a flexible and integrated security system that effectively balances access control requirements, workforce and visitor management is paramount for modern banking institutions. In environments where a large volume of individuals enter and exit premises regularly, maintaining a comprehensive overview of movements can be challenging. However, with a unified
‘This multi-layered approach substantially mitigates the risk of security breaches’
this issue. Today, insider threats have become a major concern. By implementing multifactor authentication and strict access control measures, banks can better protect themselves against such threats. Another notable requirement within banking institutions is the implementation of multi-user authentication. This protocol mandates the submission of multiple authentication factors from distinct sources before granting access to high-risk areas or sensitive information. For example, both the bank employee and the customer must undergo authentication procedures before accessing a safe deposit box, which may involve providing face recognition and fingerprint.
access control system security managers can attain a holistic view of all activities within the premises, enabling proactive monitoring and response to potential security incidents.
Managing diverse guest credentials and access cards manually can be time-consuming and inefficient. Advanced visitor management solutions address these security gaps by streamlining visitor experience and breaking down silos between disparate systems. This enhances efficiency and improves security by reducing the risk of human error and unauthorised access.
Integrating access control systems with other security technologies, such as video
surveillance and intrusion detection systems, creates a comprehensive security ecosystem that provides layered protection. Banks should collaborate with trusted partners who can manage every aspect of their security setup and offer in-house manufacturing to ensure that the highest standards are maintained.
As banks undergo expansion, branch openings and diversification efforts, access control solutions should accommodate these changes without causing disruptions or necessitating extensive reconfiguration. Whether integrating with existing systems or extending to new locations, access control solutions ensure continuous protection and security while avoiding the upheaval of system overhauls and bolstering productivity. While robust access control remains paramount for safeguarding financial assets, it’s equally crucial to strike a balance with user experience. Cumbersome authentication processes or overly restrictive access policies can hamper productivity and frustrate users. Therefore, financial institutions must embrace user-centric approaches, implementing adaptive authentication methods to streamline user access while upholding strict security standards.
invixium.com









Security Middle East magazine speaks exclusively with Anne Frayssinet, Milipol Network Director
Under the high patronage of His Highness
Sheikh Tamim bin Hamad Al-Thani, Amir of the State of Qatar, the 15th edition of Milipol Qatar, the global event for homeland security and safety, will be held under the theme ‘The technology in the service of security’ from October 29 – 31, 2024, at the Doha Exhibition and Convention Centre (DECC).
In an exclusive interview, Anne Frayssinet, Director of the Milipol Network, shares her thoughts on the challenges and opportunities shaping the industry. She discusses the role of Milipol shows in presenting the latest security innovations; fostering global collaboration; and the future of homeland security.
Can you elaborate on the key factors behind Milipol’s enduring success and global recognition in the security sector?
Milipol Paris is a premier event that gathers the entire internal security ecosystem, including buyers and solution providers. It serves as a hub where companies and exhibitors engage with market realities, discuss developments and anticipate future trends. The global homeland security market is witnessing significant growth driven by increasing security challenges such as terrorism, cyber threats and natural disasters. Advanced technologies and government initiatives are propelling the market towards substantial expansion.
As technology evolves rapidly, information and communication systems become more interconnected and complex, necessitating state-of-the-art solutions to prevent system failures and malicious acts. Milipol Paris showcases the latest innovations that address current and future threats effectively.
Additionally, we have expanded Milipol events globally, including Qatar in 1996, Singapore in 2015, and New Delhi in October 2023, allowing companies to enhance their global market positions alongside leading contractors. The Milipol Network, with its numerous exhibitors, speakers, conference cycles and workshops, offers comprehensive solutions to combat various forms of crime.
The recent Milipol Asia-Pacific was a significant event. What were some of the highlights and key takeaways from this year’s edition?
This year’s major highlight was the collaboration between Milipol Asia-Pacific



and HTX’s TechX Summit, showcasing the central role of science and technology in enhancing public safety and national security in the Asia Pacific region. The trade exhibition featured the latest homeland security innovations, while the TechX Summit hosted high-level conferences with prominent government officials, industry leaders and academia. Singapore’s Minister for Home Affairs and Law, Mr Kasiviswanathan Shanmugam, and France’s Minister of the Interior, Mr Gérald Darmanin, were notable attendees. The event, themed ‘Powering Innovation: A Safe & Secure Future’ is Asia Pacific’s flagship homeland security gathering for both public and private sector security. Significant growth has been observed in homeland security technology, particularly in AI surveillance, airport infrastructure security and cybersecurity. Milipol Asia-Pacific’s presence expanded by 30% this year, featuring 305 exhibitors from 31 countries across a 14,500 sqm exhibition space.
Left and below: Previous Milipol events have been hugely successful in the security sector
Notable global companies such as AREA S.p.A; ClearTrail Technologies; ESRI; Hikvision Technology; Innovatrix; Idemia; Microsoft; NUIX; Swissdrones; Thales Solution Asia; VMI Security; and WEY Singapore Technology participated, along with country pavilions from China, Italy, France, Germany, Hungary, Singapore and the USA. The HTX Pavilion highlighted innovations from HTX and key industry partners, including ST Engineering, CISCO, DXC Technology and Samsung
Looking ahead to Milipol Qatar, what are some of the key preparations and priorities your team is focusing on?
Our current focus includes organising international pavilions, the conference programme, the opening ceremony, the gala dinner for sponsors and exhibitors and sending invitations to official delegations. We are also addressing all exhibitor enquiries to ensure their preparations for the show are seamless. Additionally, visitor registration is now open, allowing attendees to obtain their passes online.
What emerging trends and critical topics in security do you plan to highlight at Milipol Qatar?
Milipol Qatar attracts the leading global public and industrial security players who showcase the latest security, safety, detection and prevention equipment, systems and services. The event aligns
with Qatar’s National Vision 2030, addressing the country’s growing security needs. The 15th edition of the show, scheduled for October 29-31, 2024, at the Doha Exhibition and Convention Centre, will build on the success of its previous edition, which featured 222 exhibitors from 22 countries, 11,500 visitors from 84 countries and 389 official delegates, as well as secured contracts worth 592 million QAR. The event seminars attracted over 500 attendees.
As head of Milipol events and the Milipol Network, what is your vision for the future of these events? How do you see them evolving in the next five to ten years?
In an increasingly uncertain environment, protecting people and infrastructures requires constantly updated resources and solutions. Milipol events enable global security professionals, from both public and private sectors, to find the most suitable equipment and technologies for their needs by bringing together solution providers, manufacturers and distributors. These events offer several advantages, including economic support for the security industry; strengthened bilateral cooperation between ministries of interior; and a unique platform for promoting exports from the security sector. I am confident that the Milipol Network will continue to be the world’s leading network of events dedicated to safety and homeland security, fostering innovation and collaboration in the industry.
milipolqatar.com






01. - 03. October 2024 Riyadh, KSA
The Middle East, a region undergoing rapid infrastructure development and economic diversification, is also witnessing a paradigm shift in transport security, and digital twins are revolutionising the sector
Digital twins, virtual replicas of physical systems, are emerging as a powerful tool for enhancing safety and security across various transportation modes. They are created by collecting real-time data from sensors, cameras and other sources to build a computer model that mirrors the behaviour of its physical counterpart. This data can include everything from sensor readings on train tracks to passenger flow patterns within stations. By analysing this data, digital twins can predict potential problems, simulate scenarios and optimise operations, making them invaluable tools for enhancing transport security.
Digital twins are essentially digital representations of physical assets like airports, railways, ports and even individual vehicles. They are created by integrating real-time data with 3D models of the infrastructure. This creates a dynamic virtual environment that allows for real-time monitoring, simulation and optimisation of various aspects, including security.
The benefits of digital twins for transport security are numerous – and they’re already being utilised in the Middle East:
■ Enhanced threat detection and risk assessment: Digital twins provide a comprehensive view of a transportation network, allowing security personnel to identify potential vulnerabilities and security gaps. Simulations can be run within the digital environment to predict potential security breaches and assess the effectiveness of existing security measures. This proactive approach allows authorities to anticipate threats and take preventive actions before they occur.
■ Improved emergency response: Digital twins can significantly enhance emergency
response times and effectiveness. Real-time data from the physical environment can be fed into the digital twin, providing a clear picture of the situation during an emergency. This allows for faster and more coordinated response efforts by emergency personnel, minimising casualties and damage.
■ Training and preparedness: Digital twins can be used to train security personnel for various scenarios in a safe and controlled virtual environment. By simulating emergencies, cyberattacks and other security incidents, security teams can practise their response procedures and develop better coordination and decisionmaking skills.
■ Cybersecurity and critical infrastructure protection: With increased reliance on digital technologies in transportation, the risk of cyberattacks on critical infrastructure has grown. Digital twins can be used to identify vulnerabilities in a system’s digital components and simulate cyberattacks to discover potential weaknesses. This proactive approach allows for the implementation of robust cybersecurity measures to protect critical transportation infrastructure.
■ Predictive maintenance: Digital twins can monitor the health and performance of critical infrastructure in real-time. By analysing data on wear and tear, potential equipment failures can be predicted, allowing for preventative maintenance to be scheduled and so helping to avoid any disruptions to service.
As digital twin technology continues to evolve, its applications in transport security will become even more sophisticated. Potential future developments may see the technology integrate with artificial intelligence. By integrating AI with digital twins, the system can learn and adapt to changing conditions, making real-time security decisions.
Digital twins could also be used to identify vulnerabilities in the cyber infrastructure and implement proactive measures to strengthen overall cybersecurity. In the future, passenger data may be integrated into the digital twin, allowing for personalised security measures based on individual risk profiles. They also offer several advantages that cater to the unique needs of the Middle East. Digital twins can facilitate collaboration between different transport authorities within the region. Sharing data and insights through these platforms can
improve regional security by identifying and addressing cross-border threats.
In addition, the rapidly evolving nature of security threats demands adaptability. Digital twins allow for the continuous refinement of security protocols and scenarios to stay ahead of any emerging dangers.
Finally, this technology can be used to optimise traffic flow and infrastructure utilisation, resulting in reduced energy consumption and improved environmental footprint. This aligns with the sustainability goals of many Middle Eastern nations.
Although digital twins offer immense potential for revolutionising transport security, some challenges would need to be overcome before the technology can be more widely adopted.
The success of digital twins hinges on integrating vast amounts of real-time data. Ensuring the security and privacy of this data is paramount. Robust cybersecurity measures and data governance frameworks must be implemented to prevent unauthorised access and misuse of sensitive information.
In addition, integrating data from different sources and ensuring seamless communication between various systems can be challenging. Ensuring compatibility between existing infrastructure and digital twin technology can be complex.
Developing and implementing digital twins requires significant investments in technology and expertise. This can be a
barrier for some transportation authorities, especially in smaller countries located within the region.
Despite these challenges, the adoption of digital twins is expected to continue accelerating in the Middle East. Collaboration between governments, technology companies and transportation authorities is crucial to overcome implementation hurdles and develop standardised security frameworks tailored to the region’s needs.
Investing in research and development to ensure the affordability and accessibility of this technology will further encourage its widespread adoption. Fostering knowledge sharing and best practices within the region will accelerate the learning curve and optimise the use of digital twins for transport security.
Digital twins are poised to revolutionise transport security in the Middle East. By proactively identifying threats, optimising response times and facilitating training, this technology promises a safer and more secure transportation landscape for the region. As digital twins gain traction and technological advancements continue, we can expect to see even more innovative security solutions emerge, further strengthening transportation networks across the Middle East. And as the region continues to invest in its infrastructure, digital twins will undoubtedly play a crucial role in creating a secure and sustainable transportation ecosystem for the future.
The end of last year saw Naver, a Korean IT firm, sign a $100m contract with Saudi Arabia’s Ministry of Municipal and Rural Affairs and Housing, for a digital twin platform project. Ultimately it hopes to develop the transport system, transforming the country into a global logistics hub to support sustainable economic development in line with Vision 2030.
Dubai’s Roads and Transport Authority (RTA) uses a digital twin of the entire Dubai Metro network. This digital replica helps them monitor real-time traffic flow, identify potential disruptions and manage emergencies effectively.
Dubai Airports has implemented a digital twin of its entire operation, including terminals, runways and airside facilities. This allows it to simulate various security scenarios, such as drone intrusions or unauthorised access attempts, and identify the most efficient response strategies.
The Abu Dhabi Department of Transport is working on a digital twin project that will integrate cybersecurity measures. This will allow them to monitor potential cyber threats in real-time and quickly respond to security breaches, protecting critical transportation systems from cyberattacks. The project integrates
advanced technologies such as aerial photography, LiDAR scanning and game engines providing a rich and interactive 3D model.
Hamad International Airport in Doha, Qatar, boasts a state-of-the-art digital twin, as part of its smart airport programme. This platform aids in streamlining passenger flow, optimising security measures, and enhancing overall operational efficiency, thereby contributing to airport security.

Secure your checkpoint with our industry-leading X-ray inspection, optical inspection, and radiation detection technologies that help to uncover threats and identify and authenticate vehicles and occupants. With our comprehensive checkpoint security solutions, we can help you maximize threat detection and operational success. rapiscan.com VISIT US INTERSEC KSA BOOTH 1-C29









The spectre of data loss or cyberattacks looms large over businesses relying solely on Microsoft 365 backups, leaving critical information vulnerable warns Charles Smith, Consulting Solution Engineer, EMEA, Data Protection at Barracuda Networks Inc
Business in the Middle East remains highly relationship driven, and online collaboration tools help to facilitate collaboration in addition to boosting productivity, efficiency and enabling remote and hybrid working amongst other benefits. One of the most widely used productivity software suites is Microsoft 365.
Microsoft 365 (M365) is used by more than 3.7 million organisations worldwide, with around 345 million individual users, according to the company itself. From email to shared documents and spreadsheets, video conferencing and more, if your organisation uses a cloud-based business productivity suite of applications, the chances are around one in two is M365. But this deep dependency can create risk if your data is not secure.

The scenarios outlined below are all quite possible in the modern workplace and, critically, happen far more often than you may imagine:
■ Somebody hacks your M365 account, deletes everything in your mailbox, and empties the recycle bin. This type of deletion is common during account takeover attacks, so that there is less evidence of the attack left behind.
■ You accidentally delete a sub folder containing important work emails and various documents (attachments). You may not notice this straight away as often you have lots of sub folders in your mailbox and this type of thing is easy to do by mistake on your phone.
■ A cyberattack, a human error, or otherwise unexpected event has caused data loss in OneDrive for Business, SharePoint Online, or Microsoft Teams.
Who’s responsible for your data?
Microsoft has a highly resilient infrastructure and this matters because Microsoft is responsible for making sure your M365 environment is available. However, as Microsoft itself warns customers, Microsoft is only responsible for the infrastructure that supports your data. It is not responsible for the data in your M365 environment. Microsoft specifically calls this out in their Managed Services Agreement.
A recycle bin is not a backup
Microsoft provides a recycle bin for some services. However, the recycle bin is not a backup; it is just a folder that contains items that you have deleted. You cannot do a point-in-time recovery from your deleted items folder, because this folder only holds items that were deleted
and would not contain the valuable emails or files that you would most want and need to restore. Additionally, the maximum extended retention of the Recycle Bin is 93 days, and your items may be purged and unrecoverable after that time.
If Microsoft 365 data isn’t properly backed up, several risks can arise. Human error could result in accidentally deleted files or emails being lost forever. Cyber attackers could encrypt or corrupt data making it inaccessible. Misunderstandings or misconfigurations in retention policies could result in unintended data loss, while failing to meet regulatory requirements for data retention and protection can lead to legal penalties. Last but not least, any problems with third-party applications syncing with M365 could result in data inconsistencies or loss.
A robust data backup solution designed for cloud applications and the precious data they store is business critical.

Companies have a choice of options, but there are a few things to look out for when selecting the backup platform that’s best for your business.
First, the data backup service should ideally itself be based in the cloud to optimise resources – no-one really needs the additional burden of moving data to a cloud service and then back to an on-premises backup platform.
It should offer powerful security features such as least privilege access, data encryption and immutability to protect it from unauthorised access and tampering. Plus it should include an online remote management console designed specifically for backing up M365 data with unlimited retention and storage capability, and it should be easy to implement and use. Barracuda’s Cloud-to-Cloud back up is one such option. It’s a complete backup solution for M365 that operates entirely in the cloud.
The most important thing, however, is that you do something. The alternative is losing important work forever – and there are more than enough cyber attackers willing to do that for you. barracuda.com
According to Statista the global cloud backup and recovery services market is expected to reach $109.8 billion by 2028, growing at a CAGR of 16.5% from 2022 to 2028.
84% of companies use cloud backups, says UniTrends. Adoption rates are the highest for small businesses at 93%, mid-sized businesses adoption rates are at 82% and large companies are at 81%.
According to research from Arcserve 43% of IT decision-makers falsely believe that cloud providers are responsible for protecting and recovering public cloud data.
A survey from tenable found that 79% of companies experienced at least one cloud data breach, with 43% reporting 10 or more breaches in recent years.
CloudKnox Security’s State of Cloud Entitlements Report revealed that more than 90% of cloud identities are using less than 5% of the permissions they’ve been granted.
According to a study from Backbaze, 11% of users create backups weekly, 20% create backups monthly, 13% create them yearly, 26% create them less than once a year, and a significant 20% have never backed up their data.
Veeam’s 2022 Ransomware Trends Report reported that nearly all — 97% — of modern ransomware incidents attempt to infect backup repositories as well as primary systems.
In Saudi Arabia, annual spending on public cloud services is expected to reach US$3.9bn in 2027 with an expected compound annual growth rate (CAGR) of 23.4%, according to research by the International Data Corporation (IDC).









Sales Team Lead MEA at TRASSIR, Valery Mymrin shares more about the company’s new collaboration with Suprema
The strategic alliance marks a pivotal step in TRASSIR’s mission to become a leader in the region’s integrated security sector. By combining Suprema’s advanced access control solutions and world-leading biometrics with TRASSIR’s video management systems, the partnership is set to deliver robust, scalable and tailor-made security solutions designed to meet the specific demands of the Middle East market.
What drives this collaboration?
TRASSIR is a global company, with offices in the UAE, Turkey, India and Russia. Founded in 2002, since then we have been dedicated to developing cutting-edge software and hardware products, with a special focus on AI-driven video surveillance, seamless integration with security systems and IoT technology. Our advanced solutions are meticulously designed in-house, guided by the core principle that modern security systems must be future-proof and offer extensive compatibility. We see tremendous potential in the Middle East market, especially in Saudi Arabia, and we are confident that our partnership with Suprema will deliver significant benefits to end-users.
How will this partnership position TRASSIR as the go-to choice for VMS integration in the region’s security projects?
Suprema is ranked among the world’s top 50 largest security manufacturers. Leading the EMEA region with the highest market share in biometrics, Suprema’s AC platform, BioStar 2, is indispensable across diverse sectors, including government, infrastructure, research institutes, data centres, banks, hospitals, offices, construction sites and universities.
This strategic partnership positions TRASSIR as the go-to choice for VMS integration in the region’s security projects. The integration between Suprema
BioStar 2 and TRASSIR VMS will be fully supported by TRASSIR’s in-house engineering team, ensuring a seamless fit for complex security projects where access control and VMS need to work together. This integration will allow us to create customised scenarios to meet the specific needs of our customers in various industries. For example, in case of an unauthorised access attempt, the customer will be able to view the video footage, receive different types of notifications or even send the signal to different devices via alarm outputs connected to TRASSIR.
Both TRASSIR and Suprema bring extensive experience in video surveillance and access control across a wide range of sectors in the MEA region including Saudi Arabia, UAE, South Africa, Morocco and others. This depth of experience naturally led to the decision to join forces, ensuring that we can provide the best possible service to our customers.
Suprema emphasises automation in its solutions. How can TRASSIR leverage this focus to offer deeper automation possibilities for its customers in the Middle East?
TRASSIR offers a range of automation options, from simple rules — such as ‘perform specific actions based on certain conditions’— to more advanced logic through scripting. Customers can create their own Python scripts using the TRASSIR Framework or leverage universal scripts developed by our team. For example, a simple rule might trigger an email with event details, screenshots and video clips when an event is received from Suprema. For more complex needs, scripts can be used to generate reports, adjust server settings, or send POST requests to other systems, providing extensive customisation and automation capabilities.
“ This collaboration will enhance integration capabilities and boost business efficiency, allowing customers to experience unparalleled convenience and effectiveness.”
One of the key advantages of this integration is the creation of a unified operations centre. How does this streamline security management for TRASSIR’s customers?
TRASSIR customers will see the following key benefits from this integration:
■ Effortlessly link access control events with video recordings via integrated event linking.
■ Create complex, customised security scenarios with advanced automation.
■ Suprema Access Control combines advanced biometric technology with intelligent card readers, ideal for various applications. Due to open REST APIs, the BioStar 2 platform offers unmatched flexibility in system design.
How will you continue to innovate and adapt your offerings to meet evolving security needs in the region?
TRASSIR and Suprema are committed to ongoing innovation, incorporating technologies such as AI, machine learning and advanced analytics into their security solutions. These advancements will empower the development of smarter, more proactive systems that can detect and respond to threats in real time. Additionally, the partnership will prioritise the customisation of solutions to address specific regional challenges, enhance cybersecurity measures and ensure compliance with local regulations. By remaining at the forefront of technological advancements and maintaining a flexible, customer-centric approach, TRASSIR and Suprema aim to provide scalable, future-proof security solutions adaptable to the evolving landscape of the Middle East.
trassir.com

Faisal
Mohamed, CEO of
The modern world is growing increasingly interconnected owing to the digital transformation that is drastically revolutionising industries and improving our everyday lives. In this age, striking an ideal balance between user convenience and security may be challenging for organisations. This is where access control systems, particularly mobile credential access control, come into the picture. While traditional methods assist us in safeguarding research facilities and securing data centres, numerous technological breakthroughs have ushered in a new era of security. The mobile credential access control is a cutting-edge, effective and extremely safe substitute for traditional methods as it utilises smartphones and other mobile devices to provide a flexible and efficient way to control access to physical spaces. It leverages cutting-edge technologies found in today’s smartphones, such as NFC and Bluetooth Low Energy (BLE), to increase security by providing secure access credentials or digital keys stored in the phone to the access control reader. This technology offers a more convenient and safe approach to managing access by seamlessly integrating with current security systems.
Mobile credential access control is becoming more and more popular in the GCC region, where governments and corporations place a high premium on digital transformation. Businesses are increasingly using digital solutions to improve security and optimise their operations due to growing mobile internet adoption rates and a focus on innovation. In the GCC, where countries have the highest mobile internet penetration rates in the Middle East and North Africa (MENA) region, it was projected that the
number of mobile internet users will go beyond 350 million by 2025, according to Statista figures.
This cutting-edge technology has several benefits. Compared to conventional techniques, mobile credentials offer a significant security upgrade as unauthorised access is less likely when digital keys are encrypted and safeguarded with multi-factor authentication. Moreover, in any event that a device is lost, or an employee leaves the company, mobile credentials can be promptly updated or revoked. Furthermore, mobile credential access control makes it easier for staff members to enter secured locations. They can stop worrying about losing their keycards and carrying multiple of them. For administrators, managing access rights becomes more streamlined and less time-consuming, as updates can be made remotely and in real time. In addition to convenience, mobile credential access control solutions have significant long-term benefits, such as cost savings. Physical keycard production and distribution can save organisations a substantial amount of money. Systems for mobile credential access control are highly scalable. With organisations’ needs and requirements evolving, it becomes easy to issue or modify new credentials with this system. Because of its adaptability, the security system can adapt to meet changing needs without incurring additional expenses.
The capability to monitor and regulate access in real time is one of the most striking characteristics of mobile credential access control. By monitoring
who accesses what places and when, security managers can respond quickly to any suspicious activity. In addition to improving overall security, this real-time capability offers valuable data for organisational management.
Upgrading the legacy access control system to mobile credentials is not a challenging task today. Many mobile credential solutions provide add-on readers to the existing legacy system, which immediately upgrades to the state-of-the-art mobile credential system without changing the infrastructure. This option catalyses the adoption of the mobile credential access control system in the market.
Privacy is the most important concern that comes with any digital solution. Therefore, it is imperative for businesses to guarantee that the data collected through mobile credential systems is stored securely and used appropriately by adhering to relevant laws. Being open and transparent with employees about how their data will be utilised can help build trust.
Mobile credential access control represents a significant leap forward in organisational security. Artificial intelligence and biometrics are two examples of the emerging technologies that will shape the future of access control. These developments can improve mobile credentials’ ease and security even more. Using face recognition or fingerprint scanning, for instance, can add another degree of protection and security, and artificial intelligence (AI) could enable predictive security measures by recognising possible dangers. Additionally, adopting mobile credential access control is a smart and strategic choice for companies seeking to improve their security infrastructure.
Undoubtedly, this system, among other technologies, will become the cornerstone of a secure and more convenient future for organisations. It is a desirable option owing to the numerous benefits, including higher security, convenience, cost savings and scalability. Organisations that adopt these cutting-edge solutions will be better equipped and well-positioned to safeguard their employees’ safety and preserve their assets as technology advances. screencheck.com


Firas Jadalla, Regional Director, META, Genetec, explores how real-time crime centres can unify data and operations across city departments for reduced crime rates, speedy incident response and stronger inter-agency collaboration
Cities of all sizes around the world are working hard to manage crime and ensure public safety, placing significant pressure on law enforcement and public safety teams. Real-time crime centres (RTCCs) are emerging as a solution, helping cities use existing technology, real-time data and advanced analytics to enhance public safety. RTCCs unify data and operations across city departments, reducing crime rates, efficient incident response and stronger collaboration.
Public safety agencies today face many challenges that make protecting and serving communities harder. One major issue is disconnected systems and data. Police departments use various advanced technologies, but these systems often don’t communicate with each other. This makes retrieving data slow and inefficient, which delays emergency responses and investigations. The lack
of integration also hinders communication and collaboration between different agencies, leading to inefficiencies.
Cyber threats and privacy concerns are also significant problems. The rise of Internet of Things (IoT) devices and new crime-fighting technologies has created more opportunities for cyberattacks. Even with advancements in cybersecurity, cities often struggle to keep up with sophisticated cybercriminals. At the same time, the public demands more transparency in how their data is used and managed. Balancing strong cybersecurity with public trust is a difficult task.
Evidence management is another challenge. Investigators spend a lot of time collecting evidence from various sources. The process of gathering, storing and sharing physical evidence is resource-heavy and can slow down investigations. Ensuring the authenticity of evidence and maintaining a secure chain of custody are also difficult tasks that are crucial for fair judicial outcomes.
Personnel shortages add to these difficulties. This shortage puts extra stress on existing officers, leading to burnout, and potentially affecting the quality of policing.
Increased violence towards officers is also a growing concern. Rising violent crime and anti-police sentiments have led to more aggression towards law enforcement. Ensuring officer safety is a top priority, and using technology to improve information sharing and preparedness can help achieve safer outcomes.
Budget constraints further complicate these issues. Rigid budgets and lengthy approval processes limit the ability of public safety agencies to adopt new technologies that could improve efficiency and effectiveness. Despite recognising the benefits of these innovations, agencies often struggle to secure the necessary funding. Investments in technology, though initially costly, could lead to significant long-term savings and better operations.
Real-time crime centres (RTCCs) take public safety initiatives to the next level. They act as crime-fighting nerve centres, unifying data streams and operations across city departments. Within these state-of-the-art tech hubs, public safety and law enforcement teams can tap into a central source of real-time information and trending data, including calls to emergency services, dispatch data, live video and sensor data. All this information can be streamed onto video walls and monitors for all operators and investigators to see. During an emergency, they can then quickly understand what’s happening and effectively deploy resources to mitigate the situation. During investigations, detectives can dive deep and collect evidence with all relevant data at their fingertips. Ultimately, an RTCC enables a unified front of public safety technology and resources that help reduce incident response times, improve officer safety, speed up investigations and enhance data collection across the city landscape.
At its core, an RTCC is built on a foundational, front-end solution that offers operators a single interface. This is what brings all data from various systems and sensors together and provides public safety teams with real-time situational awareness and support. It does this by analysing and correlating incoming information and then pointing officers to the most pressing situations. The relevant videos and data are displayed on an interactive city map, allowing for added situational context to make faster, more informed decisions.
However, not all RTCC platforms offer true real-time capabilities. Some systems may only provide video and data with a slight delay, which can be critical in emergency response operations. True real-time information is essential for properly mitigating events and tracking suspects, ensuring that officers can respond promptly and effectively.
Real-time crime centres (RTCCs) support public safety operations by providing intelligence and automation to public safety teams, enabling them to work more efficiently and effectively. An RTCC allows for faster responses and more comprehensive investigations, sending a clear message that crime and gun violence will be swiftly addressed.
This proactive approach can deter criminal activities and reduce offences within communities. Additionally, the centralised data collection inherent in an RTCC enables cities to identify crime hotspots, recognise trending patterns and implement process improvements. This data-driven approach informs strategic decisions that can further decrease crime rates.
RTCCs can automatically change the behaviour of a security system to address specific threat levels. For example, in the event of a public safety emergency, presets can be triggered in the security management platform to automatically restrict access to a particular building or selectively grant control access to law enforcement and first responders.
The true power of an RTCC lies in its ability to transform raw data from multiple sources into actionable information, facilitating faster and more effective decision-making. When a gunshot is detected, or a call to emergency services is made, operators receive immediate alerts and access to relevant data such as nearby cameras, license plate readings and historical reports. This information is shared with patrol officers in real time, enabling them to respond swiftly and safely. RTCC operators can monitor ongoing situations, provide updates and compile evidence post-incident. This system reduces guesswork, increases automation and enhances resource efficiency, ensuring a rapid and secure response to any situation.
The need for speed
RTCCs also expedite investigations by serving as central repositories for city data, streamlining evidence collection and management. Operators can export emergency services calls, case notes and videos into digital evidence systems, while officers on the scene use mobile apps to collect and transfer witness statements and other evidence.
Investigators can leverage forensic analytics and search tools within the RTCC to locate crucial information and securely request evidence via email. They can digitally share entire case files with attorneys, simplifying the discovery process, saving agencies countless hours, and increasing clearance rates.
Improving officer safety is another critical benefit of an RTCC. Public safety operators provide virtual assistance to field officers, dispatching the nearest patrol car and transmitting relevant information directly to in-vehicle laptops. This enables officers to be better prepared for situations they encounter. RTCC operators also monitor nearby cameras to offer real-time updates and ensure incidents are handled smoothly. During large city events, RTCCs remotely monitor crowds, use analytics to identify potential risks, and alert officers as needed, keeping them out of harm’s way.
Finally, RTCCs enhance city-wide collaboration by providing a unified view of activities across the city, leading to more effective resource coordination and faster incident response. Public agencies can partner with private businesses and residents to access public-facing cameras, streamlining evidence collection. They can also integrate video cameras and IoT sensors from other city agencies into the RTCC platform, broadening their situational awareness. This extensive data collection not only improves public safety but also generates insights that can enhance disaster recovery and sustainability initiatives.
Real-time crime centres (RTCCs) are revolutionising public safety by integrating advanced technology and real-time data to create safer urban environments. By unifying disparate data sources and enhancing situational awareness, RTCCs enable quicker response times and more efficient investigations while improving officer safety. By fostering collaboration and using data-driven insights, RTCCs enable cities to proactively tackle crime and ensure public safety, paving the way for safer, more resilient communities. genetec.com

















clearly to the executive decision-makers. Context is everything.
Just as the board’s function is to think in terms of long-term business goals, security executives must learn to see their role as serving the same big-picture objectives. This is implied by the very addition of CISO to the C-suite. Each security leader and every member of their team can now be thought of as a ‘de-risker’, tasked with reducing cyber risk and ensuring the business can perform optimally in its industry.
This shift from ‘defender’ to ‘de-risker’ will arguably be challenging for some security analysts – born troubleshooters and problem-solvers who thrive on the eternal battle between their protectee and the Wild Wild Web. But this serves to establish the SOC as a value-adding entity with an indispensable role in the future of the business. The first step, then, is measurement. Teams must quantify cybersecurity risk throughout the organisation so that non-security executives can grasp the scale of the problem. This is best managed through a programme of auditing and discovery that unites information and makes it available from a single point of control.
You’ve probably heard this common phrase: ‘you cannot protect what you cannot see’. Enhancing asset management and visibility is a prerequisite for measuring security preparedness and business risk. This involves having a comprehensive, single-pane view of every endpoint and application, their vulnerabilities, and how those flaws are paths to catastrophe. It is the ‘catastrophe’ that senior business leaders will understand. However, presenting this in formal metrics in the form of X hours of downtime, Y dollars of cost, and so on, will prove most effective at getting the message across, all collated from data like threat intelligence, vulnerability status and asset values.
Now that the CISO has their board’s attention, executives can see the value of mitigation because they have seen the relationships that exist among assets, vulnerabilities and common attack vectors. Disruptions in operations or services need no further explanation and may very well be an existential threat for some businesses. The costs are not limited to lost revenue and unhappy customers. There’s the more intangible loss of brand trust, corporate reputation and even employee burnout. Not to mention, material breaches also have legal implications these days.
Once the CISO has alignment from
decision makers, they can start to talk about de-risking other areas and studying other metrics like supply-chain stability, sales performance and changes in customer behaviour. By this stage, organisations hopefully will have already taken steps to improve basic security processes such as remediating software vulnerabilities. Patching has always been one of the most efficient ways to mitigate risk, and now that automation has become a de facto necessity in digital transformation programmes, patch deployment can be sped up, and taken off the plates of security staff, so they can concentrate even more on their new de-risking goals.
By adopting a business-oriented, risk-focused stance on cybersecurity, the SOC will command new respect from those that control budgets. With this level of support, the SOC can wade into the threat landscape appropriately armed for the battle. In return, business leaders are protected by a security function that understands what matters to the business. As a result, the innovative side of the business can stretch its legs with confidence in an enterprise environment poised for success. qualys.com
The number and size of mega breaches is increasing, according to PwC’s 2024 Middle East Digital Trust Insights report. Globally, 36% of organisations have reported their worst breach as costing $1 million or more in the past three years – up from 27% in last year’s report. When looking specifically at the Middle East that figure stands at 29% currently.
According to the PwC report the top security risks in the Middle East are:
■ Cloud-related threats – 53%
■ Attacks on connected devices – 53%
■ Business email compromise/attack takeovers – 32%
■ Hack-and-leak operations – 31%
In 2023, the Middle East retained its second-place spot for two years running in terms of the total cost of data breaches. The average cost was reported by IBM’s Cost of a Data Breach Report 2023 as being $8.07m – an increase of 8.2% from the previous year, a 15% rise over the last three years and a significant 155.9% increase over the last decade.
Frost and Sullivan has predicted that the cyber threat intelligence market in the Middle East will exceed $31 billion by 2030. Notably, oil and gas industries are emerging as key targets for advanced persistent threats (APTs).
Research from Kaspersky found that 87% of UAE companies faced a cyber incident in the past year. A quarter of those cybersecurity incidents (25%) were as a result of malicious actions by staff.
A 2023 Kaspersky study revealed that 77% of companies in the APAC region don’t have the necessary tools to identify cyberattacks.
2024 research from the Qualys Threat Research Unit (TRU), found the common vulnerabilities and exposures (CVE) count rose by 30 per cent between Jan 2023 and mid July 2024.




James Gerber, CFO of SimSpace, explores why taking a military approach to cybersecurity can help organisations win the undeclared cyber war
We are in an undeclared cyber war. Recent geopolitical unease has ushered in the first hybrid war, incorporating espionage, cyberattacks and online disinformation alongside the more traditional military onslaught. However, the cybersphere has no borders, and without proactive defensive tactics the failure of retrospective cybersecurity remediation in the GCC area has led to a mean time of 349 days to contain a cyberattack.
Cyberattacks are often the weapon of choice for nation-state actors, occurring in a ‘grey zone’ of conflict between peace and outright war. In this atmosphere,
protecting Middle Eastern infrastructure and networks is as critical as protecting our airspace and our shores. Ex-NATO General Ben Hodges recently suggested that cybersecurity has become just as important as missile defences.
A cyberattack on critical functions like oil and gas (O&G), energy or finance risks the way of life that we take for granted. The US-based colonial pipeline attack of 2021 resulted in fuel shortages and stockpiling, warning of the potential dangers sewn by a ransomware attack. Cybercriminals from nation-state actors and ransomware-as-a-service gangs alike are always probing for vulnerabilities
that would allow them to cause chaos and extort money from businesses and government organisations.
Developing a military mind-set
Security teams tasked with protecting government and business networks need to see beyond the illusion that the Middle East is immune to the threats often targeting eastern European infrastructure. If there are any weaknesses in their defences they will be discovered and exploited by the cybercriminals probing day and night for a chink in their armour. Security teams at businesses and critical national infrastructure organisations should be training like the military. That is, they should train as they fight and train to failure as they are on the front line of an undeclared cyber war which is now transcending geographical boundaries.
The Bin Laden raid back in 2011 was successful because the Navy SEAL

operatives rehearsed the mission exhaustively in advance, using like-for-like replicas of Bin Laden’s compound beforehand. Operational success can only be achieved when you rehearse in realistic environments and focus not only on the primary plan but also on the backup plan.
Conversely, the IT community’s focus revolved around uptime and functionality, the defence of these IT operating systems now mirrors urban warfare. Security teams are doing the equivalent of buildingto-building street fighting in a city full of people, vehicles, hospitals and other vulnerable infrastructure which they must avoid damaging. There needs to be a mind-set shift to a military-like proactivity, whereby IT security teams are transformed into combat-ready cyber defenders trained to withstand even the most sophisticated attacks.
For this reason, more and more governments and organisations are mission-rehearsing for combat with cyberattackers in cyber ranges – a high fidelity replica of a company’s network, able to be hit with three years’ worth
of attacks in just 24 hours. A cyber range is a simulated environment used for cybersecurity training, testing and research. It is designed to replicate real-world networks and systems, allowing professionals to practise and hone their skills in a safe and controlled environment.
Currently, we are performing inadequately when protecting our critical national infrastructure and our way of life. Despite years of investment, the people, processes and technologies tasked with keeping hackers at bay are unprepared to meet the necessities of modern cyber warfare. Any one of an organisation’s people, processes and technology may not be up to the task, or perhaps the three are not working well in unison. Only by stress testing security systems with combat-like cyber warfare simulations can businesses, such as oil and gas conglomerates, gain visibility into what they are doing well and where they are falling down.
Cyberattacks are forecast to cost the global economy AED38.5 trillion a year
by 2025, according to Cybersecurity Ventures, with the GCC region suffering an average loss of AED25.3 million, as opposed to the global average of AED15.4 million. Most cyberattacks go undetected and those that are identified tend to remain publicly unreported, making accurate estimates of the true cost of cybercrime very difficult.
Companies and critical national infrastructure organisations now need to take best practices from the military’s approach to training and readiness and apply a mission rehearsal approach to protecting their critical assets. We have become adept at protecting ourselves on land, at sea and in the air, now we need to take those approaches to protecting the infrastructure that underpins Middle Eastern prosperity.
Security teams should train as they fight. They should be pushed to train to failure because it is better to fail in training than to fail in a real attack and allow the next Colonial Pipeline attack occur on their watch. simspace.com

Find out what’s on the agenda over the three show days
Intersec Saudi Arabia returns to Riyadh for 2024

The Kingdom of Saudi Arabia is undergoing a period of unprecedented transformation. Vision 2030, the government’s ambitious plan for economic diversification and social development, places a strong emphasis on security and safety


The 6th edition of Intersec Saudi Arabia, held from October 1-3, 2024, at the Riyadh International Convention & Exhibition Centre (RICEC), emerges as a critical platform for security professionals to play a vital role in shaping this secure future.
The event is expected to attract over 17,000 visitors and showcase a massive lineup of over 350 exhibitors from 27 countries. This year’s edition underscores its commitment to Saudi Arabia’s ambitious Vision 2030 goals, focusing on innovative solutions that address the evolving needs of the Kingdom’s rapidly developing security and safety landscape.
In addition, Intersec Saudi Arabia 2024 boasts the highest level of industry support ever witnessed. The event is held under the patronage of the High Commission of Industrial Security and enjoys strong associations with the Ministry of Interior and Saudi Civil Defence. This prestigious backing emphasises
the event’s critical role in fostering collaboration and innovation within the Kingdom.
The event will feature a dedicated Future Security & Safety Summit, bringing together leading industry experts to discuss critical topics like future-proofing security, Generative AI, cyber resilience and the evolving threat landscape. This knowledge-sharing platform provides invaluable insights for professionals looking to stay ahead of the curve in a rapidly changing environment.
Dive into topics like ‘Moving Beyond Security — how to react to AI’s transformative potential’, ‘Safeguarding Mega Events: securing the spectacle’ and ‘Crisis Driven Innovation Vs Proactive Modernisation’. Witness interactive sessions that address the most critical issues faced by security professionals today, leaving you equipped with the knowledge and strategies to stay ahead of the curve and contribute to a more secure future.

Intersec Saudi Arabia presents a unique opportunity to discover the latest security solutions and technologies that are transforming the industry. With over 350 exhibitors from 27 countries showcasing their innovations, the exhibition space is a treasure trove of cutting-edge products and services. Visitors can explore solutions specifically designed to address the unique security challenges associated with mega-projects in the region. Stay ahead of the ever-evolving cyber threat landscape by encountering innovative advancements in data security, access control and perimeter security systems. Witness firsthand how AI, machine learning, and IoT are revolutionising security management and threat detection. Discover the latest innovations in surveillance technologies, access control systems and physical security equipment to enhance both physical and virtual security measures.

Intersec Saudi Arabia facilitates invaluable networking opportunities for security professionals. Connect with key decision-makers from government agencies, leading security consultancies and private companies.
Gain valuable insights by networking with esteemed industry leaders and renowned security specialists. Forge lasting business relationships with potential partners and collaborate on future projects. Connect with colleagues from across the security spectrum and create a network that fosters knowledge sharing and professional development.
Intersec Saudi Arabia boasts a compelling conference programme featuring insightful workshops, interactive sessions and keynote addresses from industry experts, on critical topics shaping the future of security:
■ Immerse yourself in the latest security trends and participate in discussions with global experts on topics like cyber resilience, smart security technologies and managing emerging security threats.
■ Stay informed about the latest security regulations and legal frameworks impacting the Kingdom.
■ Learn from leading security professionals about implementing robust security protocols and optimising security operations.
■ Gain valuable insights from real-world implementations of innovative security solutions.
Intersec Saudi Arabia goes beyond mere product displays. Join the Future Security & Safety Summit, a dedicated platform that showcases emerging trends and game-changing technologies. Explore advancements in:
■ Artificial Intelligence: AI-powered analytics can enhance threat detection and predictive security measures.
■ Drone Technology: Explore the potential of drones for surveillance, perimeter control and security operations in remote areas.
■ Virtual Reality (VR): Witness how VR simulations can facilitate realistic security training and incident response drills.
Intersec Saudi Arabia offers an unparalleled platform for security professionals to showcase their expertise and services. This is your chance to connect with potential clients, generate leads and promote your business solutions to a captive audience of decision-makers across the Kingdom of Saudi Arabia.
Attending Intersec Saudi Arabia 2024 is more than just visiting a trade show; it’s an investment in your professional future. Here’s what you gain:
■ Unmatched Learning: Build expertise and stay ahead of the curve with insights from industry leaders.
■ Explore Cutting-Edge Technologies: Witness the latest innovations shaping the future of security.
■ Strategic Partnerships: Build invaluable connections with key stakeholders and potential partners.
■ Career Development: Enhance your professional network and learn from the best in the industry.
■ Knowledge Sharing: Participate in interactive sessions and gain valuable insights from industry peers.
■ Competitive Edge: Stay informed about the latest regulations and trends shaping the security landscape in Saudi Arabia.
Don’t miss out on this opportunity to contribute to a secure future for the Kingdom of Saudi Arabia. Intersec Saudi Arabia is not just a trade show; it’s an investment in your professional future and a catalyst for innovation. Embrace the opportunity to be at the forefront of security solutions that will shape a safer and more secure future for the Kingdom of Saudi Arabia.

Register for Intersec Saudi Arabia 2024 and take your role in the security industry to the next level.
DAY 1
1 October 2024
13:00 Chairperson Opening Remarks
13:10 Opening Keynote Speech by Patron
13:15 HCIS’s Role in Raising the Level of Industrial Security Fields
13:30 Beyond Borders: International Collaboration Initiatives for Securing Our Nation
13:50 Developing a Security Strategy for Island and Coastal Tourism Destinations
14:10 Safeguarding Mega Events: Integrated Security Strategies for Mega Events in Saudi Arabia
14:45 Roadmap to a Successful Security Career
15:00 City Scale Resilience: Strategic Security Design at Diriyah, the Jewel of the Kingdom
15:20 Cybersecurity in the Age of Artificial IntelligenceOpportunities & Risks
15:40 Green-Sustainable Energy Era
16:00 Threat Risk Assessments: Detect, Respond & Prevent
16:20 PwC Global CCC Index: Identifying the Pioneers in Command & Control Centers
16:40 Drones: The Vanguard of Modern Security
17:00 Paving the Way Towards Smart Safe Sustainable Cities
17:45 Chairperson Closing Remarks
DAY 2 2 October 2024
11:50 Recap & Opening Remarks
12:00 Future-Proofing Security: Preparedness, Adaptability & Response
12:30 Promoting a Diverse and Inclusive Culture for the Security Workforce
13.00 Developing a Comprehensive Business Continuity Plan in the Digital Era
13:20 HCIS
13:40 Healthcare Crisis Management: Navigating Challenges Ensuring Recovery and Continuity of Care
14:00 Crisis Command Centres in Hospitals: Enhancing Emergency Response and Patient Care
14:15 Implementing Smart Security Systems as Part of Urban PlanningLimitations & Best Practices
14:40 AI on Security & Safety Industry: Impact and Concerns
14:55 Physical Security Vs. Cybersecurity
15:10 Security Soars: Revolutionising Asset Management and Master Planning for Safer Skies
15:30 Preparing for New Threats: Industry Development & Regulatory Requirements
16:10 Crime Prevention Through Environmental Design (CPTED)
16:25 The Role of Generative AI & Multi-Modal Biometrics in Managing Responsive Cities
16:45 CBRN Decontamination & Process
17:00 Crisis-Driven Innovation vs Proactive Modernisation
17:15 Chairperson Closing Remarks
DAY 3 3 October 2024
Future Readiness Program
The Future Readiness Programme is an essential platform for government officials and security leaders who are focused on today’s dynamic security landscape and pioneering future-ready solutions. This programme examines the evolution of security threats, offering insights into the trends, challenges and emerging risks. Participants will gain valuable knowledge about national transformation programmes aimed at modernising security entities, emphasising advancements in talent development, innovation, mission readiness and future force capabilities. Additionally, the programme explores future security technologies, with a focus on discussing the maturity and strategic applications of AI and machine learning. Leaders will be equipped with the crucial insights and strategies needed to effectively navigate and address evolving security challenges, ensuring resilience and adaptability
10:00 Opening Remarks by Andrea Lugini
10:05 The Evolution of Security Threats
10:35 Bridging Skills Gap in an Emerging World
11:15 Break
11:30 Future of Security Technologies (incl. AI)
12:10 Closing Remarks by Andrea Lugini
KEY Presentation Dual Presentation Panel Discussion On-Stage Conversation


www.hochiki.ae



Venue:

Venue:





Time: 11am to 8pm






















Hear from some of the companies who will be exhibiting at Intersec Saudi Arabia this year, and find out where to locate them on the show floor




PERCo equipment will be presented at the Intersec international security exhibition on October 1–3, 2024 in Riyadh, Saudi Arabia. PERCo will showcase access control solutions demanded both in the Middle East and worldwide:
■ ST-01 Speed gate with a face recognition terminal and a built-in card capture reader
■ TTD-12A Motorised box tripod turnstile with a barcode scanner
■ RTD-14 Full height rotor turnstile
■ WMD-06 Swing gate
■ IRP-01 Reader post
PERCo is a leading Russian manufacturer of security systems and equipment, ranking in the top 5 global market leaders. It has 36 years in the security market; exports to 95 countries worldwide; and offers a five-year warranty for the whole product range. PERCo has an office, showroom and warehouse, all located in Dubai, UAE perco.com
TRASSIR, a leading developer of AI video surveillance, security systems, IoT solutions and software since 2002, is excited to announce its participation in Intersec Saudi Arabia 2024!
It will be showcasing its latest innovations, including the new series of Ultra 5MP/2MP cameras and advanced neuroanalytical modules for object and human counting, queue and crowd monitoring, time

Genetec Inc. is a global technology company that has been transforming the physical security industry for over 25 years. The company’s portfolio of solutions enables enterprises, governments and communities around the world to secure people and assets, and support operational efficiency, while respecting individual privacy.
Based on an open architecture, and built with cybersecurity at their core, Genetec solutions can be implemented on-premises, in the cloud, or in hybrid deployments. The company’s flagship products, Genetec Security Center and Genetec Security Center SaaS, unify core physical security functions, such as access control, video surveillance, automatic license plate recognition (ALPR), intrusion detection, communications and analytics.
Headquartered in Montreal, Canada, Genetec has an extensive network of certified partners and consultants in over 159 countries. genetec.com

and attendance analysis, sabotage prevention, fire and smoke detection and more.
Visitors to the stand will have the opportunity to experience TRASSIR solutions firsthand and discover how they can benefit businesses of all sizes, from medium-sized retail chains to large construction sites or manufacturing plants. Its technologies address all aspects of security, from recognising the number of vehicles entering a site to reducing incidents of theft and sabotage. trassir.com
Founded in 2002, Digifort is a global leader in video surveillance software, operating in 140 countries and offering a platform in 19 languages. The company aims to advance VMS technology with its ‘Beyond Expectations’ vision, leveraging artificial intelligence and deep learning to enhance data interpretation. Its integrated solution provides a unified view for monitoring all IP-connected hardware and metadata devices. Known for its stability, solid coding and performance-driven approach, Digifort’s software is more responsive and less CPU-intensive than its competitors. This innovation is poised to revolutionise video surveillance operations and provide transformative solutions for market leaders, offering a new level of proactive response and situational awareness.
digifort.com
Intelligent Security Systems (ISS) stands at the forefront of AI-driven video analytics innovation. At the heart of its offerings is the SecurOS® platform, an end-to-end solution renowned for its seamless integration with most third-party security systems. The state-of-the-art solutions leverage the latest advancements in video intelligence technology, encompassing the SecurOS® VMS, SecurOS® Auto, SecurOS® Cargo, SecurOS® Tracking Kit and the SecurOS® UVSS, which has recently been manufactured in Saudi Arabia.

Connected Technical Furniture (CTF) designs, manufactures and installs furniture for control rooms, crisis rooms, meeting rooms and conference rooms. Crafted in a state-of-the-art factory in Dubai, UAE, CTF ensures top-quality engineering and manufacturing in the GCC. Offering hands-on service throughout the project lifecycle, CTF tailors its solutions to meet specific client needs. Consoles can be delivered within two weeks in the UAE and three weeks across the GCC — an impressive turnaround compared to the usual 16+ week delays many integrators and end users face. Designed to meet ISO 11064-4 2013 ergonomics standards, CTF’s consoles offer a variety of add-on features and customisation options. Accessories like PDUs, cable management, monitor brackets and wireless charging pads are included in CTF’s product offering, along with free delivery and installation. Every console also comes with a lifetime warranty on the metal body, supported by dedicated teams and facilities in the UAE and KSA for hassle-free operations. ctfconsoles.com
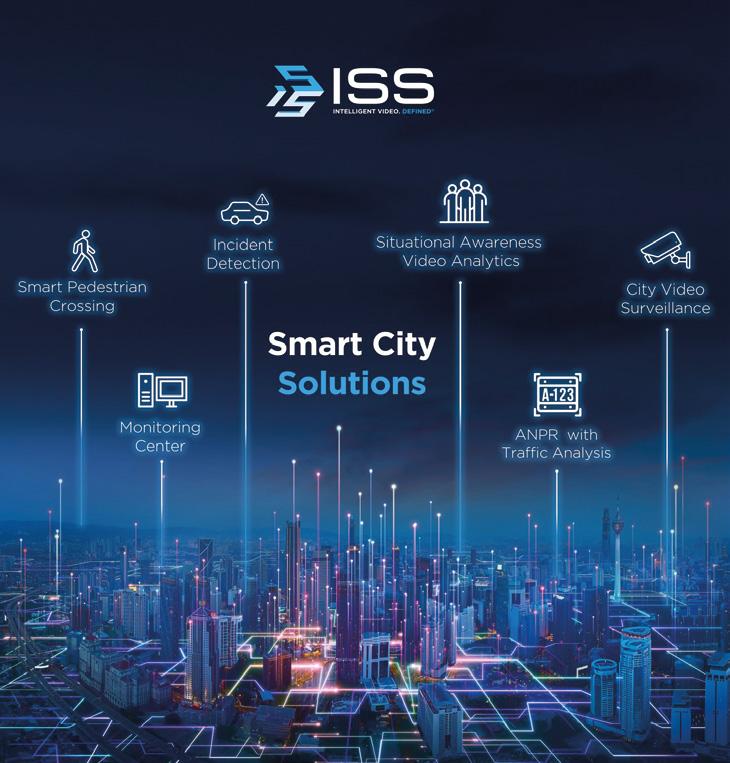

Discover Bosch’s AI-powered video solutions at Intersec Saudi Arabia 2024. Experience how its advanced technologies enhance the security and well-being of people and properties. At the Bosch booth, the company will unveil the latest in predictive-ready video solutions, designed to help you anticipate potential incidents and respond proactively.
The team of highly experienced security professionals is ready to share insights on how its video security solutions can leverage business intelligence beyond traditional security measures. Engage with Bosch to explore AI-driven video analytics, tailored for the Middle Eastern market.
Visit Bosch and learn how our innovative solutions give you the ability to know what’s next.
boschsecurity.com
At Intersec KSA, ISS will unveil two groundbreaking solutions: the SecurOS® ITS, an AI-powered platform designed to enhance traffic monitoring and streamline transportation infrastructure management by addressing accidents and moving violations; and the SecurOS® Stadium, a suite of AI-powered solutions for sports events meticulously engineered to meet the security requirements of the FIFA World Cup Saudi 2034.
issivs.me
Rapiscan is an industry leader in security screening technology, providing cargo and vehicle inspection systems to help borders, ports, military, high-threat locations and law enforcement combat terrorism, smuggling and trade fraud. Its broad array of scanning systems leverages optical inspection, X-ray inspection and radiation detection technologies to address each customer’s unique security application

requirements. Customers can further enhance inspection capabilities and operational efficiencies with its analyst assist tools and data integration platform. With this technology, information can be collected and combined from multiple
Eagle Eye Networks is the global leader in cloud video surveillance, delivering cyber-secure, cloud-based video with artificial intelligence (AI) and analytics to make businesses more efficient and the world a safer place. Eagle Eye Networks provides security and real-time business intelligence, helping organisations of all sizes and types optimise their operations.
Eagle Eye’s 100 percent cloud-managed solutions are smart, simple, and secure. The Eagle Eye Cloud VMS (video management system) is the only platform robust and flexible enough to power the future of video surveillance and intelligence. Purpose-built for the cloud and AI, it addresses customers’ security needs with infinite scalability, flexible pricing plans, a wide array of advanced analytics and an open API platform for unlimited integration.
Eagle Eye Networks believes true cloud video surveillance, with appropriate privacy and cybersecurity protections, provides proactive security and valuable actionable data. Ultimately, it will ensure businesses and communities are more informed, engaged and safe.
een.com
sources in the inspection operation to automate manual processes and control workflows, and deliver targeted, actionable intelligence. Rapiscan’s commitment to excellence in imaging performance, cutting-edge digital technology and uncompromising quality ensures its solutions help customers find threats and contraband with ease and confidence. rapiscan.com
HID powers trusted identities for people, places and things, enabling safe transactions, productive work and free travel. Headquartered in Austin, Texas, HID has over 4,500 employees worldwide, supporting more than 100 countries.
An ASSA ABLOY Group brand, HID provides solutions for governments, businesses and institutions.
Visit HID, a leader in trusted identity solutions, at Intersec KSA to see the latest in access control technologies:
■ HID Mobile Access® solutions: Use mobile devices to access secured areas and services, catering to a mobile-first world.
■ HID® Signo Readers™: Supports over 15 credential technologies, OSDP verified and reduces energy consumption by up to 43% in idle state.
■ HID® Aero™ and HID Mercury™ controllers: Flexible, open architecture for deploying a broad range of access control systems. hidglobal.com

For over 100 years Hochiki has led the way in the design and manufacturer of innovative life safety solutions. Its leading edge commercial and industrial fire detection and emergency lighting products have acquired global acceptance as the benchmark for high-integrity and long-term reliability.
Its ongoing commitment to manufacturing innovation ensures customer satisfaction and its production facilities in Japan, the USA and Europe offer international continuity in quality, service and supply. Offering a wide range of robust and reliable solutions, all approved to the highest standards including EN and UL approvals as well as UAE Civil Defence in the following Emirates — Dubai, Abu Dhabi, Ras al-Khaimah, Ajman and Sharjah.
In addition to point detectors, beam detectors, wireless devices etc., Hochiki also offers devices for specialist application. For example, the Intrinsically Safe (I.S.) and SIL approved products are ideal for use in hazardous environments. Hochiki products are easy to install and maintain, and where required come with extensive training and technical support when required. hochiki.ae

Convergint MEA is thrilled to be exhibiting at Intersec Saudi Arabia, where it will showcase its advanced technology solutions tailored for industries such as government and critical infrastructure, education, energy, aviation, retail, hospitality, entertainment and more. Visit Convergint in Hall 5, Stand D12 to explore its comprehensive offerings in advanced security, audio visual, data centres and AI software. Join Convergint MEA for a hands-on experience and live demos featuring innovative solutions in city surveillance, AI video analytics and edge computing, unified command and control, smart traffic solutions and state-of-the-art audio-visual systems. Discover how its customised solutions can elevate your operations, safeguard your assets and meet your unique needs. Don’t miss this opportunity to see cutting-edge technology in action and connect with industry experts. convergint.com/convergint-middle-east
At Intersec Saudi Arabia 2024, DNAKE will showcase:
■ IP Intercom Solution: DNAKE’s smart intercom systems offer unparalleled functionality and userfriendliness, and are designed to meet the evolving needs of modern security and communication. Visitors will discover what sets DNAKE’s IP intercom systems apart, how the DNAKE cloud platform enhances intercom management and explore the new features available through the platform.
■ 2-wire IP Intercom Solution: The DNAKE 2-wire video intercom solution combines the simplicity of traditional

For over 35 years, Allied Telesis has been delivering reliable, intelligent connectivity for everything from enterprise organisations to complex, critical infrastructure projects around the globe. It helps protect people and secure premises by providing highly available, intelligent network solutions with extended lifespans and long-term support. For physical security partners, Allied Telesis offers cost-control benefits through infrastructure designed for longevity and a single-pane-of-glass management system. Combined with network automation capabilities, these features streamline operations and reduce ongoing expenses. Intelligent, high-performance solutions continuously protect everything from airports to malls, to corporate buildings and train stations.Trust Allied Telesis. Network smarter. For more information please visit the website. alliedtelesis.com
2-wire systems with the advanced capabilities and flexibility of IP technology, making it an ideal choice for modern communication needs.
■ Smart Home Solution: New smart switches, smart curtains and other smart home devices will be released for an integrated and enhanced living experience.
■ Wireless Doorbell:
The new DNAKE wireless doorbell kit provides a sleek, wire-free alternative, addressing connectivity issues and offering a practical and modern solution for entryway communication. dnake-global.com




Ahmed Ibrahim Abd
CNSP,
Describe your experience in the security industry.
With a career spanning more than two decades in military and corporate security and bolstered by a master’s degree in security and risk management and CPP certification, I realised that the security industry serves as a force multiplier for business organisations. The seamless integration of security risk management into the organisational risk management process is the bedrock of security function success, making it an essential component of the organisation’s resilience capabilities. This entails implementing mitigation risk strategies guided by the principle of ‘as low as reasonably pragmatic’ (ALARP) while aligning these strategies with corporate crisis management and business continuity plans to ensure that the organisation can cultivate an antifragile business model to thrive in the face of uncertainties and disruptions.
What do you think are the most pressing security challenges facing the oil and gas industry in the Middle East?
The industry faces many security challenges due to its pivotal role in geopolitical dynamics. The regional powers have used the industry as a political tool to advance their agendas, leading to increased conflicts. Therefore, extremist groups who are seeking both financial gain and media attention have made the industry their primary target, while protesters have specifically targeted O&G to express their socio-economic grievances.
The precarious state of maritime security, particularly in the strategic waterways
of the Middle East, has had negative impacts on global O&G supply chains and the broader energy markets. The protection of the O&G infrastructure poses an immense challenge due to its vast scale and strategic significance. Lastly, the growing reliance on digital technologies has rendered the industry susceptible to cyberattacks, further exacerbating security concerns.
What are the most common physical security threats in the Middle East’s oil and gas industry?
The types of physical security threats
This may include state actors, like geopolitical rivals; non-state actors like terrorist groups; insider threats involving disgruntled employees; and emerging threat actors like cybercriminals. Hence, the related types can be categorised into two main groups. The first group comprises industry-indirect threats, like armed conflicts, terrorist attacks, maritime piracy and national protests. The second group encompasses industry-direct threats, such as site hostile takeovers, employee kidnappings, sabotage and theft of infrastructure, community and labour protests and emergent technology-enabled physical attacks such as drone strikes.
How does AI improve physical security in the oil & gas industry?
AI is a game-changer for O&G physical security, which faces operational challenges from evolving threats, human error and ageing infrastructure. AI algorithms’ sophisticated abilities like advanced data analysis, predictive analytics, deep learning and visualisation tools have empowered physical security processes such as threat intelligence, risk assessment, security systems and emergency response to optimise the proactive response, predict vulnerabilities and provide valuable insights for decision-making, while also having

How do you anticipate security in the Middle East’s oil and gas industry developing in the coming years?
The future of the industry’s security landscape is a complex puzzle however monitoring key trends reveals its shape. Cyber warfare is expected to escalate, with nation-state attacks, supply chain vulnerabilities and crippling ransomware. Physical threats like drone attacks and insider threats persist. Geopolitical tensions and the energy transition further muddy the waters. However, technological advancements like AI-powered security and blockchain hold promise. To thrive, industry and governments must embrace tech wisely, cooperate regionally and adapt to change. By actively navigating these evolving threats, the O&G future can remain secure and prosperous.
controlrisks.com
The Middle East accounts for approximately 31% of global oil production, with Saudi Arabia being the largest producer (39% share in 2019), followed by Iraq (17%) and the UAE (14%), according to IEA.
Five of the top 10 oil-producing countries are located in the Middle East; Saudi Arabia, Iraq, UAE, Iran and Kuwait, according to the US Energy Information Administration.
In 2023, oil production in the Middle East amounted to approximately 30.4 million barrels per day, with Saudi Arabia, producing over 12.2 million barrels per day, says Statista. Saudi Arabia also tops the region for crude oil distillation capacity with close to three million barrels a day.

According to the Oil & Gas Journal, Qatar holds 11% of the world’s proved natural gas reserves, equalling almost 30% of the Middle East’s reserves.
A 2023 report from Statista forecasted 598 oil and gas projects were due to commence operations in the Middle East between 2022 and 2026, with 51% of those being petrochemical projects.
As of 2022, approximately 2.8 million people were employed in the oil and gas supply sector in the Middle East, making it the region with the highest number of industry jobs, says Statista Research Department.
ICT offers a unified solution for access control, intrusion detection, and building automation - from small business to large-scale enterprise projects with complex requirements.
With native support for mobile credentials, and integrations with VMS, lifts, wireless locks, PSIM, and more, Protege platforms provide your customers with a flexible and secure solution that will also help grow your business.
Contact the ICT Dubai office for more information.


In light of the urgent global problems such as violent conflicts, discrimination, racism, xenophobia and hate speech, education is a lighthouse for hope that will bring about change. As we look into the world of biometrics, especially facial recognition technology, we start seeing not only the ways it can influence access and security, but also find out how it has contributed to securing one’s peace through knowledge and inclusivity. Biometrics as part of this symbiotic relationship, provides a pathway towards a secure, more accessible, and harmonised education system.
These days, biometric technology is widely used in the education sector, transforming the security and convenience of facilities for students and teachers. Modern protocols have reduced the hazards that came with employing traditional biometric techniques. The most widely used biometric technologies in educational institutions are face recognition and contactless fingerprint or palm recognition. And because of their utilisation, biometrics are gaining more and more trust.
Exam boards and educational institutions may use voice, iris, fingerprint, or facial recognition technology to confirm test taker identities. This has been demonstrated to improve academic integrity.
One of the most liked and effective uses of biometrics in education is attendance monitoring. Administrators can identify truancy issues more easily, thanks to the automatic function of biometric attendance monitoring, which also removes the hassle for needless
roll calls before courses.
Verifying each person attempting to enter a university or school with biometricenabled access control can also significantly boost safety. In addition, restricted biometric security access can be used to secure areas that are off-limits to students.
Biometrics can play a very significant role in activity tracking. In fact, it can be used to track various activities. On the other hand, employing manual reporting procedures to record activities could be time-consuming. Instructors can use biometrics to keep an activity diary and generate quick reports as needed.
The contactless and user-friendly nature of facial recognition technology makes it a superior biometric modality compared to others, such as fingerprints. The seamless and non-intrusive nature of facial recognition make it a much more convenient and hygienic alternative for usage in an educational facility. The major difference between fingerprint scanners and facial recognition is that the latter provides a touchless experience in accordance with contemporary requirements, which increases general user satisfaction.
The scalability, as well as its ease of implementation and adaptability, make facial recognition a better option in transforming safety and accessibility within educational settings providing superior security and comfort.
In the world of rapidly changing educational technology, facial recognition
systems represent a revolutionary force for accessibility, security and inclusion within these institutions. The safety of students and staff is an issue that educational facilities all over the world have in common. Biometric systems, incorporated into access points of dormitories and laboratories, add another layer of security. Using facial biometrics, the authentication of online learners also becomes very easy. This is a blessing for a large number of educational institutions providing online courses, making education more accessible to those who live in remote areas or have mobility issues. It also provides a low-cost alternative for students who are unable to move in order to complete their higher education.
Rather than a fortress, a secure campus enabled by facial recognition technology evolves to become an enriching environment in which learning thrives. Educational establishments equipped with technologically advanced security measures create an environment of safety that pervades every area, creating a space where both students and teaching staff feel safe. A great security infrastructure is not only a shield but also an accelerant of positivity. In a scenario devoid of security concerns, the positive attitude settles in, establishing an excellent atmosphere for learning and working together.
Ultimately, the combination of strong security measures made possible by facial recognition technology and increased inclusivity leads to an educated space that not only protects but also drives students toward academic success as well as personal development.
recfaces.com






menaisc.com 18 September
CYSEC UAE Rosewood, Abu Dhabi, UAE
uae.cysecglobal.com
24–25 September
International Security Expo Olympia, London internationalsecurityexpo.com 1–3
22–26 October SAHA Expo Istanbul Fair Central, Türkiye
sahaexpo.com
29–31 October
Milipol Qatar Doha Exhibition and Convention Center
milipolqatar.com

Please
23–26 October
Korea Police World Expo
Songdo ConvensiA, Incheon, Korea
eng.police-expo.com
30 Oct–1 Nov
Secutech Thailand BITEC, Bangkok
secutechthailand.tw. messefrankfurt.com