



PLUS www.smechannels.com India’s leading IT magazine for channel business VOLUME 13 | ISSUE 08 | PAGES 40 | OCTOBER 2022 | RS. 20/INTERVIEW / 28 Power Management Redefined SME CHAT / 36 A Holistic Approach to securing Hybrid Networks DATA SECURITY / 24 Nipping Insider Threats in the Bud Lenovo Celebrates 30th Anniversary of ThinkSystem Innovation /05 TOWARDS A P-18 APPARATUS ZERO TRUST As October is observed as the International Month of Cybersecurity across the world, India Security Market bets big, riding on the opportunities cre ated by massive digitalization

SECURITY / 13
The Big Shift Towards Zero Trust Security.
India’s leading IT magazine for channel business

PARTNER CORNER / 14 Maximizing the Value of Data.

GUEST ARTICLE / 33 Weak Cyber Resiliency: Blocking the Road to Progress In the Data Era
EDITORIAL
HAPPY AND PROSPEROUS DIWALI 2022 TO ALL THE PARTNERS
SANJAY MOHAPATRA sanjay@smechannels.com
Dear Friends
After two long years of subdued celebrations due to pandemic, 2022 Diwali has been very sublime for all the people in India. Everywhere there was gaudy atmosphere with multiple colours of light, flowers, and decorations. There was smile in everyone’s mouth.
From economy and growth perspective, India has grown past UK and become a superpower. Devel oped world have started noticing the country for its might. Besides being one of the largest selling and consumers’ destinations, India is becoming an alternative destination for manufacturing too. This has emerged out of two years of pandemic. This means there must be inflow of investment into the country. Either it would be invested on the existing companies or there would be new companies too. Due to its large geography, conditions of different cities and welcoming policy of various states, invest ment is going to happen in various cities and states. Therefore, the growth is going to be decentralized. All the development would need ICT at the backdrop. 5G has already been kicked off by the Prime Minister from the Indian Mobile Congress and it appears that the stage is set for India. Now the interest of the partners is that they can expand to every direction, but the biggest concern is that the partners are aging and many of their kids are not joining the organization to take it forward. There is need of better planning for the partners - either create a roadmap for the employees to take it forward or motivate the kids enough that they embrace the business. I know, for the kids the journey would not be very struggling as they would get the entire business for free, and their father is there on top to do the mentoring. This is a big challenges and issue for the kids as they need something creative, and they need to do something of their own and prove to the peers and friends that they have done something independently. This is where the partners need to think through and after basic mentoring leave the kids as independent operators.
I mentioned earlier, the market is quite open now and it is going to grow with the growth of the invest ment into the market. Without IT, no involvement would have return. Partners are the only rout to market for the IT vendors to reach out to the investors. So nice time ahead for the business growth. Again, Happy Diwali 2022.


MY EXPERIENCE
The Dell Precision 7865 Tower workstation

This new high-performance tower - The Dell Precision 7865 Tower worksta tion - offers full-spectrum performance for a variety of demanding profes sional applications, powered by the
latest AMD Ryzen Threadripper PRO processors. The Precision 7865 Tower is maximized for demanding, multiapplication workloads and empowers users to tackle intensive, complex workstreams more efficiently. Bridging clock speed (valuable in interactive workflows such as computer-aided design) and multi-core computation (needed for workflows such as render ing or simulation), the Precision 7865 Tower powers data science, graphic design, engineering, imaging, and VR and AI initiatives without compromise.
FEATURES: THE NEWLY DESIGNED CHAS SIS FEATURES A HEXAGONAL VENTING PATTERN THAT SUPPORTS DEDICATED AIR CHANNELS FOR CRITICAL COMPONENTS.
FINAL WORDING: DELL ENGINEERS
PRIORITIZED UPGRADABILITY AND SCAL ABILITY TO NOT ONLY MEET THE PERFOR MANCE NEEDS OF TODAY BUT ALSO TO GROW AND EVOLVE ALONGSIDE THE PROS WHO USE THEM
Vertiv Launches Prefabricated Modular Data Center Offerings in India Pg: 12PLUS
www.smechannels.com
SME CHANNELS OCTOBER 2022 3
Publisher: Sanjib Mohapatra

Editor: Sanjay Mohapatra
Sub Editor: Nidhi Shail
Content Editor: Manash Ranjan Debata Art Director: Shadab Khan
Technical Writer: Manas Ranjan Lead Visualizer: DPR Choudhary

MARKETING
Marketing Manager: Kunal Yadav Events Marketing: Tanu Malik Circulation and Printing: Rajkumar Hansa
SALES CONTACTS

Delhi 6/102, Kaushalya Park, Hauz Khas New Delhi-110016
Phone: 91-11-41055458 / 8587835685 sanjeev@smechannels.com Bangalore #28/1, 3rd Floor, Sri Lakshmi Krupa, Near Shamanna Park, Model House Street, Basavanagudi, Bangalore - 560004 Ph. No. +91 88618 21044
Mumbai Tahmeed Ansari 2, Ground Floor, Park Paradise, Kay-Bees CHS. Ltd.,Opp. Green Park, Oshiwara, Andheri (west), Mumbai - 400 053. Ph. +91 22 26338546, Fax +91 22 26395581 Mobile: +91 9967 232424
E-mail: Info@smechannels.com
Kolkata S Subhendu BC-286, Laxmi Apartment, Kestopur Kolkata-700101
Phone: 9674804389
EDITORIAL OFFICE
Delhi: 6/103, (GF) Kaushalya Park, New Delhi110016, Phone: 91-11-41657670 / 46151993 info@ smechannels.com

Bangalore #28/1, 3rd Floor, Sri Lakshmi Krupa, Near Shamanna Park, Model House Street, Basavanagudi, Bangalore - 560004 Ph. No. +91 88618 21044 E-Mail info@ accentinfomedia.com
Printed, Published and Owned by Sanjib Mo hapatra
Place of Publication: 6/101-102, Kaushalya Park, Hauz Khas New Delhi-110016
Phone: 91-11-46151993 / 41055458
Printed at Karan Printers, F-29/2, 1st floor, Okhla Industrial Area, Phase-2, New Delhi 110020, India.
All rights reserved. No part of this publication can be reproduced without the prior written permission from the publisher.
Subscription: Rs.200 (12 issues)
All payments favouring: Accent Info Media Pvt. Ltd.
SME CHAT TENABLE / 36 “A Holistic Approach to securing Hybrid Networks.” Trusted Advisor of Channel Business OCT contents VOLUME 13 ISSUE 08 2022 Editorial 03 Snippets ~~~~~~~~~~~~~~~~~~~~~~~~~~~ 05 Product 37 more inside DATA SECURITY EXTERRO / 24 “Nipping Insider Threats in the Bud.” INTERVIEW EATON / 28 “Power Management Redefined.” TOWARDS A ZERO TRUST APPARATUS / 18 As October is observed as the International Month of Cybersecurity across the world, India Security Market bets big, riding on the opportu nities created by massive digitalization CoverStory SME CHANNELS OCTOBER 2022 4
Celebrates
Anniversary of ThinkSystem Innovation
Lenovo announced the most com prehensive portfolio enhancement in its history, unveiling new end-to-end infrastructure solutions and services optimized to accelerate global IT modernization with advanced performance, security and sustain able computing capabilities. The new Lenovo Infrastructure Solutions V3 portfolio delivers industry-leading innovations to help companies of all sizes more easily deploy and manage hybrid multi-cloud and edge environments, as well as traditional and artificial intelligence (AI) workloads across retail, manufactur ing, financial, healthcare, telecom industries and more.
The introduction celebrates the 30th anniversary of the ThinkSystem x86 server, a pivotal breakthrough in enterprise computing technology that enabled an open ecosystem for
innovation and propelled busi nesses into the modern information era. Today, as global digitalization accelerates, Lenovo’s new Infrastruc ture Solutions V3 portfolio provides a unique open architecture with advanced management, superior reliability and extended security to help companies harness the new era of IT.
“In a rapidly changing business environment, IT solutions need to evolve as fast as businesses do. Lenovo’s new Infrastructure Solu tions V3 provide customers with the ultimate flexibility, reliability, and performance to meet the evergrowing workload requirements in India,” said Amit Luthra, Managing Director – India at Lenovo ISG. “We are committed to delivering robust IT infrastructure to help our custom ers succeed.
Dell Technologies and Fujitsu Collaborate to Accelerate Open RAN Global Adoption
Dell Technologies and Fujitsu are working together to make it easier for communications service provid ers (CSPs) to accelerate the adoption and simplify the deployment of open radio access network (Open RAN) solutions globally.
The companies will pave the path for CSPs to design open networks with the technologies of their choice by collaborating on Open RAN solutions and initiatives.
Designed for Dell PowerEdge and other x86-based servers, the Dell Open RAN Accelerator Card is an inline Layer 1 processing card that brings the performance of today’s radio access networks to the Open RAN ecosystem. The card increases the server’s performance by process ing all Layer 1 computations, allow ing the server CPU to focus only on Layer 2 computations. Offloading the Layer 1 computations from the
server CPU reduces the overall CPU requirements, power consumption and overall costs.
“With Fujitsu’s ORAN technol ogy, we’re bringing more value to communication service providers with access to a broad choice of ecosystem partners and price per formant technology for their open network deployments,” said Andrew Vaz, vice president of product man agement, Dell Technologies Telecom
Systems Business. “We’re expanding our partner ecosystem to drive faster innovation and a less costly and more efficient path to open RAN, so network operators can deploy open, 5G networks with confidence.”

Lenovo
30th
SME CHANNELS OCTOBER 2022 5 SNIPPETS SNIPPETS for more log on to smechannels.com PRODUCT | CHANNEL | CONSULTING | SERVICES
AWS Launches an AWS Local Zone in Delhi

Amazon Web Services, Inc. (AWS) today launched its new AWS Local Zone in Delhi, India. AWS Local Zones are a type of infrastructure deployment that places AWS compute, storage, database, and other services near large population, industry, and information technology (IT) centers—enabling customers to deploy applications that require single-digit millisecond latency to end users or on-premises data centers. Customers can run workloads with low latency requirements on AWS Local Zones while seamlessly connecting to the rest of their workloads running in AWS Regions. Today’s launch marks the first international expansion of AWS Local Zones outside the U.S. and includes new locations in Delhi and Taipei, Taiwan. AWS now has 19 AWS Local Zones around the world, with announced plans to launch 31 more Local Zones globally over the next two years, including additional AWS Local Zones in India, in the cities of Chennai, Bengaluru, and Kolkata.
The launch of the new AWS Local Zone in Delhi gives customers the ability to easily deploy applications located close to end users in the metro area. Having AWS Local Zones close to large population centers in metro areas enable customers to achieve the low latency required for use cases like online gaming, live streaming, and augmented and virtual reality. They can also help customers operating in regulated sectors like health care, financial services, and public sector that might have preferences or requirements to keep data within a geographic boundary.
Barracuda bolsters its Zero Trust Access solution with integrated web security functionality


Barracuda has announced that CloudGen Access, now transactable on AWS and Azure marketplaces, has been expanded with new functional ity. As part of Barracuda’s SASE platform, Barracuda CloudGen Access now includes web security to protect users from malicious web content and keep employees safe and productive no matter where they work.
Barracuda CloudGen Access takes a “Zero Trust” approach to security that trusts no one implicitly -- not employees, not partners, not systems, until the permissions and identity are verified. It requires verification of every user and device before granting access to resources, making it difficult for attackers to penetrate the network or steal data.
Customers and channel partners that want to take advantage of simpli fied and streamlined procurement and deployment processes can now transact Barracuda CloudGen Access on AWS and Azure Marketplaces. This offers additional flexibility to buy Barracuda CloudGen Access with existing AWS or Microsoft billing procedures and to deploy with a few clicks.
EXECUTIVE MOVEMENT
TENABLE APPOINTS
AS

PATRICIA GRANT
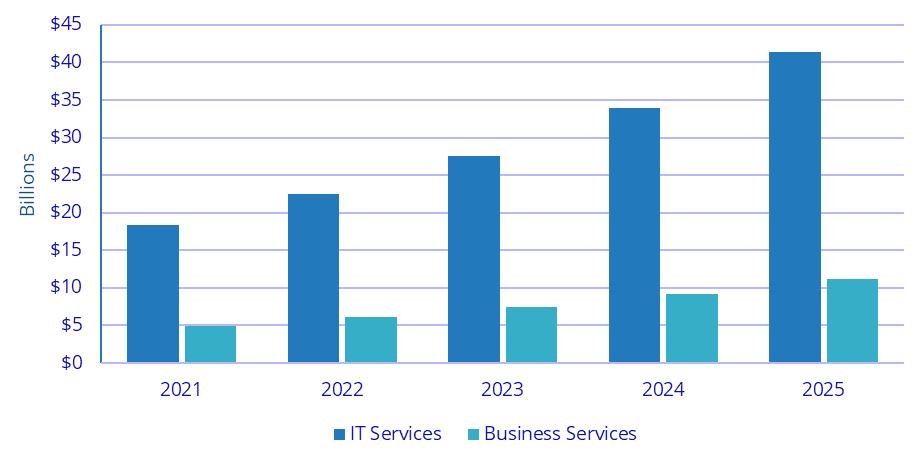
CHIEF INFORMATION OFFICER DATASWITCH NAMES SIVAKUMAR AGNEESWARAN AS GROUP CEO & CHAIRMAN COMMVAULT APPOINTS BALAJI RAO AS AREA VICE PRESIDENT FOR INDIA & SAARC LEXAR ONBOARDS KUMARAVEL VISWANATHAN AS NATIONAL BUSINESS HEAD FOR ITS INDIAN OPERATIONS Worldwide AI Services Forecast by Technology Category Detail, 2021-2025 Source: IDC 2022 SME CHANNELS OCTOBER 2022 6 SNIPPETS
Commvault appoints Balaji Rao as Area Vice President for India & SAARC
Commvault has appointed Balaji Rao as its Area Vice President for India & SAARC. Balaji joins the company with deep experience in global sales operations and team leadership and will be responsible for accelerating growth and driving sales execution excellence and expanding market share in India & SAARC.
Balaji brings over 25 years of experience in the industry and worked across prominent enterprises like Veritas, VMware, HPE, and most recently, in the cyber security sector.
Commvault has a leading product portfolio, with strong momentum in Asia Pacific, and as region-wide business requirements shift to SaaS based priorities, Balaji’s appointment is an important commitment to strengthen Commvault’s leadership and go-to-market team in India to help drive the company’s next wave of growth.
“I’m delighted to welcome Balaji to our Commvault International leadership team. With his experience, we look to gain critical industry insights to strengthen long-established relationships within our ecosystem in India,” said Marco Fanizzi Senior Vice President and General Manager, Commvault International.
Exterro hire top forensics and legal duo to spearhead EMEA drive for Legal GRC
Exterro Inc. today announced two new hires to drive momentum in Legal GRC (governance, risk and compliance). Anna Urbani takes the helm as Director of Channel EMEA, with Nick Rich leading the sales team as Director of UK&I Corporate.
The duo bring almost 3 decades of experience to Exterro to mature, nurture and recruit channel partners and drive sales across the Legal GRC portfolio. Urbani will work alongside Ian Rainsborough, Regional Vice President Channels, in her newly established role to develop a channel-first strategy, reinvigorating existing partner relationships and recruiting more Partnerships across the EMEA region.
With Exterro’s aim to expand its reach in Legal GRC, Urbani’s 17 years in forensics and e-discovery will stand her in good stead as Exterro continues its growth across Europe, enabling and identifying partners that can address multiple areas of the business.
Quantum Expands Atempo Partnership with New Validated Solution Bundles and Worldwide Reseller Agreement
Quantum Corporation today announced an expanded partnership with Atempo, a leading European software vendor known for its award-winning Tina and Miria data protection and unstructured data management software. As part of the expanded partnership, the companies are introducing validated solution bundles that combine Atempo Tina software, a Quantum® media server, and Quantum secondary storage solutions. As part of a new worldwide reseller agreement, Quantum will resell Atempo Tina software with an all-inclusive, capacity-based subscription licensing model that is only available through Quantum.
“Resellers and end users are looking for easy-to-use, easy-to-purchase solutions that provide comprehensive data protection,” says James Mundle, global channel chief, Quantum. “Providing complete solutions based on Atempo Tina software with Quantum’s secondary storage portfolio simplifies procurement, deployment, and ongoing support.”
TELUS
Tech Data today announced its distribution partnership with MailGuard – a leading player in email security space. At launch, its Integrated Cloud Email Security (ICES) solution, MailGuard 365, will be available in 6 markets across the Asia Pacific & Japan region, namely Hong Kong, India, Indonesia, Malaysia, Singapore, and Vietnam. This distribution partnership allows Tech Data to add MailGuard 365 - a solution built in Azure by MailGuard in collaboration with the Microsoft team to protect the more than 345 million Microsoft 365 subscribers - to its cyber security go-to-market portfolio in APJ. This partnership is part of Tech Data’s overall strategy of empowering ISVs (Independent Software Vendors) and partners, while further building on its cloud security solutions portfolio.
Sundaresan Kanappan, Vice President High Growth Technologies and Country General Manager Tech Data India, said “With the increasing adoption of technology use across businesses, and emails having become fundamental to business communications.
Palo Alto Networks has been selected by communica tions technology company TELUS to assist with securing one of the largest and fastest 5G networks in Canada.
“Securing 5G requires a Zero Trust approach to protect all elements of the mobile network across key network interfaces, cloud workloads and user traffic,” said Anand Oswal, senior vice president, Network Security at Palo Alto Networks. “Our 5G-Native Secu rity is the industry’s most comprehensive Zero Trust solution, with best-in-class capabilities to safeguard mobile infrastructure and the business-critical applica tions that run on it. We’re thrilled to help TELUS create a 5G network that provides enterprise-grade security to their customers.”
Palo Alto Networks will help TELUS secure its 5G network and provide real-time threat mitigation. TELUS will leverage Palo Alto Networks’ hardware and software firewalls to protect high-capacity network interfaces across its 5G stand-alone core and internet perimeter as well as to provide security to its IoT customers. Palo Alto Networks will leverage its Zero Trust approach, a security framework that is rigorously applied through to the full ecosystem of controls — network, endpoint, cloud, application, IoT, identity and more.
Selects Palo Alto Networks to Secure Cloud-Native 5G Networks in Canada Tech Data Asia Pacific & Japan Strengthens its Security portfolio in partnership with MailGuard SME CHANNELS OCTOBER 2022 7 SNIPPETS
Trellix accelerates channel Suc cess through trellix xtend new partner program
Trellix has announced its Trellix Xtend new partner program, designed to increase profitability, engagement, and growth across its global partner ecosystem. Trellix also announced new technology integrations to Trellix XDR through the Security Innovation Alliance, a program simplifying the development of inter-operable security products for complex customer environments.
“Our unified partner program, Xtend, continues to reinforce our priority as a channel-first business,” said Britt Norwood, SVP, Global Channels & Commercial, Trellix. “We co-developed the Xtend program with our partners to create the right business model for deploying Trellix XDR. Partners can count on Trellix to help drive profitability for our partners and reward partner value.”
Launching in early 2023, Trellix Xtend is designed to put the partner first. Able to be tailored to each partner’s business model and target market, the program delivers stronger customer outcomes.
Trellix expands the reach of its open platform with the addition of ten technology partners.
Wider Industry Analyst Recognition For UiPath Business Automation Platform
UiPath has said that it has received a record number of industry analyst recognitions year-to-date for its UiPath Business Automation Platform. The UiPath Business Automation Platform is an easy-to-use, scalable, and open platform that allows everyone – from RPA developers and testers to citizen developers and business end users – to collaborate and position automation squarely at the core of everyday work. With capabilities that support every phase of the automation lifecycle and deployment options that give organizations immediate management of their software robots, UiPath is bringing automation to enterprise workers by enabling them to both engage in the automation process and benefit from working alongside robots every day.
Highlights of industry analyst recognition for the UiPath Platform include being positioned in the 2022 Gartner Magic Quadrant for Robotic Process Automation.
Veira Group Invests Rs. 200Cr in 2nd Facility in Noida
Veira Group is investing Rs. 200 crore at its new manufacturing plant in Greater Noida. The company has already invested 120 crore and the rest to be phased in the next 6 months. This is the second manu facturing plant of Veira Group in India, the first being at sector 63 in Noida as well.
With the new manufacturing facility, the company increases its total production capacity of Smart TVs by more than 3 million units annually, amounting to a total of 4 million LED TVs per year, from the present 10 lakh units annual capacity. Along with increased capacity, the investment also prioritizes R&D and innovation to create intuitive TVs that meet the needs of the ‘new Indian customer.’
The plant currently has 400 000 square feet dedicated to LED TV production. In addition, the plant has the largest AHU-based (10K property) clean room in North India for manufacturing LED TV modules.
Prisma Cloud Delivers ContextAware Software Composition Analy sis to Secure Deployment of Open Source Software
Palo Alto Networks has introduced the industry’s first context-aware software composition analysis (SCA) solution to help developers safely use open source software components. The integration of SCA into Prisma Cloud further demonstrates Palo Alto’s capability as the leading cloud-native security provider.
Traditional SCA solutions are standalone products that can produce a large number of alerts but lack the runtime context to help fix vulnerabilities. With the addition of SCA to the Prisma Cloud platform, developers and security teams can proactively surface and prioritize known vulnerabilities that impact the application lifecycle (i.e., code, build, deploy and run). Prisma Cloud SCA delivers deep dependency detection and remediation of vulnerabilities in open source software before applications reach production.
Tenable Appoints Patricia Grant as Chief Information Officer
Tenable has appointed Patricia Grant as its Chief Information Officer (CIO). As the leader of the IT organisation, Grant will drive digital transformation, innovation and modernisation to support the company’s ambitious business objectives.
Grant has dedicated nearly 30 years in the high-tech industry to build ing, optimising and leading transformations across IT. Grant joins Tenable from ServiceNow, where she was the vice president of digital technology operations, leading multiple transformational initiatives for both employ ees and customers. During her tenure, Grant built the “Women in Tech” program–an internal mentorship group dedicated to empowering women in the industry, and served as a mentor and advocate. Prior to ServiceNow, she worked at Symantec for 11 years and PeopleSoft, an Oracle Company, for nearly nine years.
“Patricia joins Tenable at a pivotal moment for the company,” said Amit Yoran, chairman and chief executive officer, Tenable.
SME CHANNELS OCTOBER 2022 8 SNIPPETS
Mindtree Launches Integrated Cloud-Based Solution
Mindtree has rolled out Construction 360, a comprehensive, integrated cloud-based Salesforce solution designed to enable construction companies to streamline processes and increase productivity.
Launched at Dreamforce 2022, Construction 360 combines Mindtree’s extensive domain expertise, cloud capabilities, and NxT product suite with Salesforce’s advanced Sales Cloud, Service Cloud, and other technologies. It provides the needed digital infrastructure for construction companies to gain real-time end-to-end visibility across the construction value chain and adopt next-generation technolo gies, boosting efficiencies, streamlining costs, and accelerating time-to-market.
The solution enables construction companies to maximize performance and predictability across project lifecycle through superior management of bids, clients, suppliers, and projects, enhanced resource mobilization, and improved asset operations, thus making their operations and projects more sustainable.
Barracuda adds Zero Trust Access to its Email Protection to enhance security
Barracuda has added Zero Trust Access to its email protection suite. The new capabilities allow custom ers to control and manage access to email systems and Microsoft 365 applications on a need-to-know basis, providing an additional layer of security for their businesses.
Barracuda Email Protection Premium Plus, now with Zero Trust Access included, hardens the Microsoft 365 environment by continuously verifying and only allowing the right users to access speci fied resources. Conditional, time-based, and context-based access policies for Microsoft 365 email and applications can reduce the attack surface and compliance risks for businesses.
“Barracuda Email Protection with Zero Trust security provides complete protection for Microsoft 365, improving resiliency and security,” said Don MacLennan, SVP, Engineering & Product Manage ment, Email Protection.
DIGEST
SENTINELONE LAUNCHES S VENTURES FUND
SENTINELONE HAS LAUNCHED S VENTURES, A $100 MILLION FUND TO INVEST IN THE NEXT GENERATION OF CATEGORY-DEFINING SECURITY AND DATA COMPANIES.
“SENTINELONE PIONEERED A DATA-DRIVEN APPROACH TO DELIVERING AUTONOMOUS CYBERSECURITY. OUR EARLY DAYS WERE DE FINED BY THE SUPPORT OF OUR INVESTORS, WHO SAW THE POWER AND PROMISE OF OUR VISION. TODAY, I’M PROUD TO SEE SENTI NELONE INVEST IN FUTURE DISRUPTORS, DOING OUR PART TO CONTINUE A LEGACY OF INNOVATION,” SAID TOMER WEINGARTEN, CEO, SENTINELONE. “OUR FOCUS ON CYBERSECU RITY AND DATA INNOVATION BRINGS SENTI NELONE’S TECHNOLOGY AND ENGINEERING EXPERTISE, GO-TO-MARKET, AND CUSTOMER BASE TO S VENTURES PORTFOLIO COMPANIES.
NUTANIX UNVEILS PARTNER PROGRAM UPDATES AND INCENTIVES
NUTANIX HAS ANNOUNCED THE NEXT ERA OF ELEVATE, A GLOBAL PARTNER PROGRAM DESIGNED TO RE-DEFINE THE PARTNER EN GAGEMENT JOURNEY. NUTANIX HAS EVOLVED THE ELEVATE PROGRAM FOCUS TO PROVIDE A BETTER EXPERIENCE FOR THE ENTIRE PARTNER ECOSYSTEM AND CUSTOMERS THROUGHOUT THE CUSTOMER LIFECYCLE, WHILE STAYING TRUE TO THE PROGRAM’S UNIFIED FRAMEWORK. THIS INCLUDES AN EXPANDED BENEFITS PACKAGE TO BUILD A PARTNER PROFIT CONTINUUM.
L&T Technology Services Limited has launched the first-ever Digital Engineering Awards, in associa tion with Information Services Group (ISG), a leading global technology research and advisory firm, and business news channel CNBC TV18 in India.
The Digital Engineering Awards recognize outstanding leaders who challenge the status quo with innovative approaches that maximize performance and value across the entire lifecycle of an asset, and lead to a more sustainable future.Enterprises and their service providers are invited to submit nomina tions through October 15, with winners announced during a gala awards celebration to be held in December in the U.S. Enterprise award winners, selected by a global panel of industry experts, will be named in nine categories – five team awards and four individual awards:
Amit Chadha, Chief Executive Officer and Managing Director, L&T Technology Services Limited, said, “The need of the hour is dominated by demand for continuous evolution, driven by disruptive innovations.
Trellix Launches Advanced Research Center
Trellix, the cybersecurity company delivering the future of extended detection and response (XDR), has announced the establishment of the Trellix Advanced Research Center to advance global threat intelligence. Comprised of hundreds of the world’s most elite security analysts and researchers, the Advanced Research Center produces actionable real-time intelligence and threat indicators to help customers detect, respond, and remediate the latest cybersecurity threats.
“The threat landscape is scaling in sophistication and potential for impact,” said Aparna Rayasam, Chief Product Officer, Trellix. “We do this work to make our digital and physical worlds safer for everyone. With adversaries strategically investing in talent and technical know-how, the industry has a duty to study the most combative actors and their methods to innovate at a faster rate.”
Trellix Advanced Research Center has the cybersecurity industry’s most comprehensive charter and is at the forefront of emerging methods, trends, and actors across the threat landscape.
“THE IT INDUSTRY IS AT AN INFLECTION POINT IN HOW CUSTOMERS WANT TO PROCURE AND CONSUME TECHNOLOGY,” SAID CHRISTIAN ALVAREZ, SENIOR VICE PRESIDENT OF WORLD WIDE CHANNEL SALES AT NUTANIX.
#DLTLEDGERS RAISES $ 8.5 MILLION IN SERIES B INVESTMENT, CROSSING THE $ 100 MILLION VALUATION MARK
BLOCKCHAIN BASED MULTI ENTERPRISE SUPPLY-CHAIN BUSINESS NETWORK (MESCBN) PLATFORM, #DLTLEDGERS HAS ANNOUNCED THAT IT HAS RAISED $ 8.5 MILLION FROM ITS LEAD INVESTOR IN A SERIES B FUNDING ROUND. THIS STRATEGIC ROUND NOW BRINGS #DLTLEDGERS’ VALUATION TO WELL ABOVE $ 100 MILLION, UP FROM $ 46 MILLION AFTER ITS SERIES A ROUND JUST OVER A YEAR AGO.
#DLTLEDGERS’ SUBSCRIPTION AND TRANSACTION-BASED MESCBN PLATFORM ENABLES MULTI-PARTY TRANSACTIONS ACROSS ENTERPRISES. A CONNECTED SUPPLY CHAIN BETWEEN ENTITIES RESOLVES A HUGE PROBLEM FOR LARGE ENTERPRISES, BANKS, LOGISTICS AND FINANCING ORGANISATIONS. THE DIGITALISATION OF MULTI-PARTY TRANSACTIONS PROVIDE AUTHENTICITY AND ENABLES A LARGE PART OF SUSTAINABILITY AND FINANCING INITIATIVES WITH SUPPLIERS AND DISTRIBUTORS. IT’S INDUSTRY AGNOSTIC AND CAN BE SUBSCRIBED AND RUN BY ANY ENTERPRISE WHICH HAS A NETWORK OF SUPPLIERS, DISTRIBUTORS, BANKS AND LOGISTICS.
L&T Technology Services, ISG and CNBC TV18 Launch First-Ever Digital Engineering Awards
SME CHANNELS OCTOBER 2022 9 SNIPPETS
Oracle Releases Java 19
Oracle has announced the availability of Java 19, the latest version of the world’s number one programming language and development platform. Java 19 (Oracle JDK 19) delivers thousands of performance, stability, and security improve ments, including enhancements to the platform that will help developers improve productivity and drive business-wide innovation. Oracle will showcase the latest capabilities in Java 19 at JavaOne 2022, taking place October 17-20 in Las Vegas, and via a keynote broadcast airing on dev.java/ at 9:00 a.m. PT on Tuesday, September 20.
“Our ongoing collaboration with the developer community is the lifeblood of Java. As the steward of Java, Oracle is steadfastly committed to providing developers and enterprises with the latest tools to help them create innovative apps and services,” said Georges Saab, senior vice president of develop ment, Java Platform and Chair, OpenJDK Governing Board, Oracle. “The powerful new enhancements in Java 19 are a testament to the monumental work across the global Java community.”
The latest Java Development Kit (JDK) provides updates and improvements with seven JDK Enhancement Proposals (JEPs).
Vossle releases v1.5: Inline AR for SEO
Vossle, a No-Code WebAR development SaaS platform that enables businesses to create augmented reality in under one minute, recently included a new feature of ‘Inline AR’ to its capability. Vossle released its latest product version (v1.5) with the feature to embed Augmented Reality (AR) experiences into any website to make it more intuitive for users thereby improving SEO parameters and making the website rank higher on search engines like Google and Bing.
With this Vossle update, users can now experience augmented reality while they are scrolling through the website content. Digital content creators can embed Face Filters or 3D AR experiences on their web pages through this
“With the latest release of Vossle, we are introducing conversion-driven AR experi ences to the world. This revolutionises how we consume information on websites and gives a never seen before ammunition to website owners to rank higher on search engines” explains Prafulla Mathur, co-founder of Vossle.
Whatfix Named Leader in DAP PEAK Matrix Assessment 2022
Whatfix has been named a Leader for the third consecutive year in the Digital Adoption Platform (DAP) PEAK Matrix® Assessment 2022 released by Everest Group, a global research and analyst firm.
Despite an influx of new players entering the space, Whatfix was one of only two designated as a Leader, and saw a sharp improvement in its overall analytics offerings from the 2021 assessment. Whatfix also noted a strengthened position in the PEAK Matrix® from 2021, and a more distinct differentiation from competitors, especially on industry verticalization.
“We’re excited to be recognized again as a Leader among digital adoption platforms,” said Khadim Batti, CEO and co-founder, Whatfix. “Consistency and sustained excellence are baseline targets for Whatfix. We look forward to maintaining our leadership position by continuing to pursue technical excellence combined with relentless customer focus.”
Akamai in 2022 Gart ner Magic Quadrant for Cloud Web Application and API Protection
Akamai Technologies, Inc. has been named a Gartner Magic Quadrant Leader for Cloud WAAP for the sixth year in a row. In a companion report called Gartner Critical Capabilities for Cloud Web Application and API Protection, Akamai scored highest in 3 out of 4 use cases for cloud-based WAAP: API Security and DevOps, High Security, and Web-Scale Business Application.
The Magic Quadrant for Cloud Web Applica tion and API Protection was previously published as the Magic Quadrant for Web Application
DataSwitch Inc. has appointed Sivakumar Agneeswaran as the Group CEO and Chairman effec tive September 8, 2022. In this role, Siva will provide strategic direction, expand and strengthen partnerships, establish a professional services arm and scale the overall business. Karthikeyan Viswanathan (Karthik), will continue in his current role as the CEO of DataSwitch Products.
“Siva brings a rich services experience coupled with building automation platforms. With Siva onboard, it will help DataSwitch scale the product as well as incubate the professional services arm.”, said Karthik.

Before joining DataSwitch, Siva was the VP and Global Delivery Leader for the Data & Intelligence Practice in Cognizant for the Global Growth Markets (Europe & APAC) and the Life Sciences vertical (Global). In his nearly 23-year stint in Cognizant, he has held several leader ship roles. He built the Insurance practice for Data & Intelligence and scaled it to a few hundred million USD in ten years. Later, he led the Data Technology Horizontal and was instrumental in building an Automation Platform for Data Modernization.
Firewalls and Akamai has been named a Leader for six consecutive years. The report analyzes the market of cloud App & API Security solutions and evaluates providers on their ability to execute and completeness of vision.
The report notes, “The overall cloud WAAP market is mature, though some segments are quite dynamic, such as bot management and API threat protection. Unlike the WAAP appliance market, which is dominated by replacement purchases, the cloud WAAP market continues to experience double-digit growth, thanks to new customers, new applications to protect, and shifts from appli ances to cloud-delivered security.”
DataSwitch Names Sivakumar Agneeswaran as Group CEO & Chairman SME CHANNELS OCTOBER 2022 10 SNIPPETS
Huawei 5G Core Continues to Rank No.1
GlobalData recently released a report entitled 5G Mobile Core: Competitive Landscape Assessment. The assessment concluded that Huawei 5G Core portfolio is the strongest, rated as the “leader” among all the 5G core solutions and use cases around the world. The score gap between Huawei and No.2 is up to 2.3 times that of 2021, and this is the fourth straight time Huawei 5G Core has been rated as the global leader since 2019.
GlobalData is a leading data analytics and consulting company in the ICT industry. It provides expertise in market research and predic tions in addition to vendor analysis. According to the report, higher requirements are posed on network stability, and in turn on network reliability design as more global core networks go cloud and transition to 5G. Facing this trend, how a 5G core network solution performs on live networks is weighed more when evaluating whether it is ready for commercial use.
As 2G, 3G, 4G, 5G Non-Standalone (NSA), and 5G Stand Alone (SA) networks will coexist for a long time, equipment vendors need to provide a 5G core network solution that can facilitate smooth network evolution towards 5G SA and utilize a convergent core network architecture to address the challenges of multiple RATs coexistence, like complex O&M.
India to be a USD 300 bn electronics manufacturing industry by 2025-26
The U.S. Chamber of Commerce’s U.S.-India Business Council (USIBC)’s India Ideas Summit 2022 saw Rajeev Chandrasekhar, India’s Minister of State for Electronics and IT participate in a panel discussion on data governance and advanced manufacturing.
Speaking at a panel discussion, the Minister said “Our ambition is to build a USD 300bn electronics manufacturing industry in India by 2025-26. Electronics manufacturing, currently at USD 75 bn, will form an important component of the USD 1 trillion economy for India. India’s manufacturing capabilities have really strengthened during COVID-19 landscape making us a preferred partner in the supply chains across the world”.
He further added “Our approach is focused on expanding India’s innovation ecosystem and the internet and technology are going to be big enablers in the continued expansion of our economy. We also have a comprehensive approach and will enact a new legislative framework that addresses the digital space and acts as a catalyst for the Indian economy by enabling more innovation.
Temenos and Bahwan Cybertek Forge Exclusive Partnership to Expand Market Reach
Temenos and Bahwan CyberTek (BCT) have inked an exclusive strategic agreement to scale Temenos’ operations in India, Sri Lanka, Nepal and Bhutan. As part of the agreement, BCT will market, imple ment, and support all Temenos products and solutions in these countries. The agreement is exclusive for seven years, and signals Temenos’ commitment to long-term growth in the region.
As an exclusive Sales and Delivery partner, BCT will enable Temenos to expand its market coverage and deepen local expertise through BCT’s network of 4,000 product engineering and digital services practitioners and consultants. Financial institutions in these geographies will benefit from Temenos’ world-class banking platform and BCT’s global professional services and regional expertise.
This agreement provides Temenos with enhanced visibility on profitability and cash flow and will help Temenos accelerate business growth and sharpen customer focus in these four countries.
Over Half of Global Firms’ Supply Chains Com promised by Ransomware
Trend Micro has revealed that global organizations are increasingly at risk of ransomware compromise via their extensive supply chains. Trend Micro commissioned Sapio Research in May and June 2022 to poll 2,958 IT decision makers across 26 countries. The research revealed that 79% of global IT leaders believe their partners and customers are making their own organization a more attractive ransomware target. The challenge is particularly acute considering that potentially less well-secured SMBs make up a “significant” portion of the supply chain for over half (52%) of these organizations.
A year ago, a sophisticated attack on a provider of IT management software led to the compromise of scores of MSPs and thousands of downstream customers. Yet only 47% of organizations share knowledge about ransomware attacks with their suppliers. Additionally, 25% said they don’t share potentially useful threat information with partners.
This could be because organizations don’t have information to share in the first place. Detection rates were worryingly low for ransomware activities “We found that 52% of global organizations have had a supply chain organization hit by ransomware, potentially putting their own systems at risk of compro mise”, said Sharda Tickoo, Technical Director at Trend Micro, India and SAARC.
Matrix Participates in IISE, Delhi
Matrix has been a consistent participant at IISE and participated at the Delhi event this year as well. It unveiled its recently launched Extreme series of NVR and Professional Dome Cameras. The company also exhibited its other Video Surveillance, Time-Atten dance, and Access Control solutions at this event.
In this event, Matrix displayed its latest range of IP Video Surveillance solutions, including server-based enterprise-grade NVRs, UL-listed Cameras 8/5/3MP Cameras, and Matrix VMS solutions. The entire solu tion focused on solving the challenges that customers face bandwidth utilization, storage cost, managing multi-site offices, and reactive security.
Matrix unleashed Server-based Enterprise grade NVRs with Pre-installed Video Management Software supporting redundan cies and hot-swappable hard disks - HDD/ SSD. With a wide range of up to 128 channels reining in an enormous storage capacity of up to 144 TB, this solution covers all security needs.
SME CHANNELS OCTOBER 2022 11 SNIPPETS
IceWarp Empowers the Health Industry with its Secure, All-In-One, and Flexible Solution
IceWarp has onboarded some of the top pharma and healthcare companies by providing the brands with a clear TCO helping them save costs as well as the comfort of a Secure Email solution for thousands of their work-force. Today, IceWarp is clearly holding a big market share in the Pharma and Healthcare Industry.
Recently, IceWarp has intensified its focus on the Pharma and Healthcare sector as the cloud-based Business Email and Collaboration Suite. The software company aims to optimally deploy the secure, innovative, and integrating features of the solution to help the industry achieve its goals with a more costeffective solution.
In their efforts to overcome the challenges of the pharma industry, IceWarp has empowered many companies to avoid cyber risk by providing Enterprise Email solutions hosted on their Cloud at a local data centre. The ABM approach combined with the expertise gained over the years while enabling the healthcare sector workforce allowed the IceWarp team to onboard a majority of the leading pharma/healthcare companies as users of IceWarp’s e-mailing ecosystem.
Pramod Sharda, CEO, IceWarp India & Middle East, said “As a brand that thrives to extend affordable, seamlessly integrated, secure and an All-in-One Emailing solution to businesses of all sizes.
Protectt.ai launches AppBind enabling Zero Trust Device Binding for Mobile Banking Apps
Protectt.ai has announced the launch of AppBind that enables Zero Trust Device Binding for Mobile Banking Apps. The MTD cyber security startup also announced the inauguration of a new Office in Mumbai thereby carrying forward its expansion momentum.
AppBind, the first-of-its-kind easy-to-plug-in solution to enable the much-required safe and secure mobile banking experience with advanced mobile device binding technique, will help banking app providers to assure ‘peace of mind’ experience to its end-users.
AppBind from Protectt.ai is designed on the principle of Zero Trust that involves advance scrutiny verifying each users on multiple parameters. Banking regulator, the Reserve Bank of India has mandated introduction of security measures including device binding for mobile banking apps. With zero trust device binding mechanism in place, banking service providers will be able to curb the growing menace of mobile banking app based cyber frauds as also staying compliant with regulatory expectations.
Wesco International Acquires Rahi Systems
Wesco International has entered a definitive agreement to acquire Rahi Systems Holdings, Inc., a privately held company headquartered in Fremont, California for $217 million, and a leading provider of global hyperscale data center solutions. The purchase price represents approximately 7.5x Rahi’s projected trailing twelve months adjusted earnings before interest, taxes, depreciation, and amortization (EBITDA).
Rahi Systems serves the full lifecycle of data center solutions by helping their customers manage and simplify technology. With this acquisition, Wesco will combine Rahi with its Communication and Security Solutions (CSS) strategic business unit.
“This acquisition strengthens our leading data center solution offerings for our global custom ers,” said John Engel, Chairman, President and CEO of Wesco. “Rahi’s extensive services portfolio serving the leading global hyperscale data center providers expand the cross-sell opportunities across our company.”
Vertiv Launches Pre fabricated Modular Data Center Offerings in India
Vertivs has launched Vertiv prefabricated modular data centers, modular data center infrastructure offerings, in India. The integrated solutions are flexible platforms, optimized for deployment of IT assets, and offer a simple way to install capacity in reduced time. They also provide easy scalability, allowing the data center operator to start with a solution that meets immediate requirements and to expand capacity as needed.
Happiest Minds Technologies has announced that it has achieved Select tier partner status from Snowflake, the Data Cloud company. As a Select partner, Happiest Minds can accelerate the digital transformation of its joint customers who can fully leverage the performance, flexibility, and near-infinite scalability of the Snowflake Data Cloud.
Happiest Minds and Snowflake are able to mobilize the world’s data with Snowflake’s Data Cloud by catering to the demand for simplified data administration through robust, costeffective, and proven technology solutions. Happiest Minds is proud to strengthen its relationship with Snowflake and is excited to bring innovation and new capabilities to joint customers in their data journey.
The Snowflake Partner Network unlocks the potential of the Data Cloud with a broad array of tools and partners. Certified partnerships and integrations enable customers to leverage Snowflake’s flexibility, performance, and ease of use to deliver more meaningful data insights.
The Vertiv prefabricated modular data centers leverage Vertiv critical power and thermal manage ment capabilities, and monitoring and control technologies. They integrate features from Vertiv’s solutions portfolio, including the modular and scalable Vertiv Liebert EXM uninterruptible power supply (UPS) power protection, row-based Vertiv Liebert CRV thermal management units with intelligent Vertiv Liebert iCOMTM controls, Vertiv VR racks, and Vertiv’s rack power distribution units (rPDUs). To optimize thermal performance, the modular data centers include thermal containment to isolate hot and cold aisle airflows.
Jaideep Roy - director - business development, integrated modular solutions, Vertiv.
Happiest Minds Technologies achieves Select Tier Partner Status with Snowflake SME CHANNELS OCTOBER 2022 12 SNIPPETS
DEEPEN DESAI GLOBAL CISO, ZSCALER
THE BIG SHIFT TOWARDS ZERO TRUST SECURITY
Over the last year, cybersecurity profes sionals have increasingly witnessed an unhealthy spurt in exploits tar geting their business VPNs. This has again brought the use of VPNs into sharp focus, demonstrating the risks associated with this tech nology when deployed to support remote users. The findings of Zscaler’s recently released annual VPN Risk Report, conducted by Cybersecurity Insiders, indicates that there’s a growing number of VPN-specific security threats. The Zscaler report also calls for the need for Zero Trust secu rity architecture in enterprise-level organizations.
The 2022 report surveyed over 350 IT profes sionals in North America at organizations with global workforces. Despite high awareness of VPN risks, remote work forced many companies to rely more heavily on legacy access methods during the pandemic. At the same time, cybercriminals con tinue to take advantage of long-standing security vulnerabilities and increased attacks on VPNs. This year’s Zscaler VPN Risk Report includes anal ysis of the state of the remote access environment, the most prevalent VPN risks, and the growth in adoption of Zero Trust.
“As evident in several high-profile breaches and ransomware attacks, VPNs continue to be one of the weakest links in cybersecurity. Their architec ture deficiencies provide an entry point to threat actors and offer them an opportunity to move laterally and steal data,” said Deepen Desai, Global CISO of Zscaler. “To safeguard against the evolv ing threat landscape, organizations must use a Zero Trust architecture that, unlike VPN, does not bring the users on the same network as businesscritical information, prevents lateral movement with user-app segmentation, minimizes the attack surface, and delivers full TLS inspection to pre vent compromise and data loss.”

Zero Trust Secures Remote Access
While more and more companies have employees returning to the office, 95 percent of surveyed workplaces still rely on VPNs to support a com bination of hybrid and distributed work environ ments that often span multiple geographies. In addition to remote employees, large organizations often extend network access to other external stakeholders, including customers, partners, and contractors. In many cases these users are connecting from untrusted devices on insecure networks, are granted far more freedom than necessary, and result in additional security risks. Unlike cumbersome, insecure VPNs, Zero Trust architecture improves organizational security posture without sacrificing the user experience. In
addition, Zero Trust allows IT teams to keep the location of their network and applications secret, reducing the attack surface and threat of internetbased attacks.
Status Quo Falls Behind as VPN Risks Con tinue To Grow
The increase in the number of remote workers across industries has resulted in a sharp spike in cyberattacks that are tailor-made to target VPN users. As VPNs grant a greater degree of trust to users when compared to Zero Trust architecture, cybercriminals are more active in seeking to gain unauthorized access to network resources through exposed attack surfaces. According to the report, 44 percent of cybersecurity professionals have wit nessed an increase in exploits targeting their business VPNs in the last year, demonstrating the risks associated with this technology when deployed to support remote users.
Legacy network security architectures are per vasive and deeply entrenched in corporate data centers, making it difficult to challenge the status quo and adopt new architectures. So it should come as no great surprise that nearly all of the organizations surveyed continue to use VPNs despite knowing they are being targeted by ran somware and malware. Meanwhile, incumbent network security vendors have a vested interest in maintaining the remote access status quo. Organizations should be wary of legacy network access approaches that rely on cloud-based VPN, and examine vendors’ architectures to understand whether they will bring significant benefits in risk reduction and user experience. VPN technology carries the same fundamental shortcomings and risks in cloud virtual machines as it does on appli ances, and should be avoided in favor of more modern approaches.
To access more info login to: https://www.smechannels.com
“AS EVIDENT IN SEVERAL HIGHPROFILE BREACHES AND RANSOMWARE ATTACKS, VPNS CONTINUE TO BE ONE OF THE WEAKEST LINKS IN CYBERSECURITY. THEIR ARCHITECTURE DEFICIENCIES PROVIDE AN ENTRY POINT TO THREAT ACTORS AND OFFER THEM AN OPPORTUNITY TO MOVE LATERALLY AND STEAL DATA.”
As VPN exploits grow, Zscaler 2022 VPN Report stresses that organizations should be mindful of Firewall/VPN solutions marketed as Zero Trust Cloud Security
SME CHANNELS OCTOBER 2022 13 SECURITY
RAJEEV SINGH VICE PRESIDENT & BUSINESS HEADMIDMARKET & EMERGING BUSINESS SAP INDIAN SUBCONTINENT
 BY SANJAY MOHAPATRA sanjay@smechannels.com
BY SANJAY MOHAPATRA sanjay@smechannels.com
work manufacturing, real-time alerts, and many more to magnify business growth.
Riding on the uptick in market demand, the global big data analytics market size is surging ahead and is expected to breach a USD 549.73 billion mark by 2028. From an overall market size of USD 206.95 billion in 2020, it has reached USD 231.43 billion in 2021. Continuing its growth streak, the market is estimated to grow at a CAGR of 13.2% during the 2021-2028 period, according to “Big Data Analytics Market Forecast, 20212028” report from Fortune Business Insights.
The Big Data Analytics market in India is cur rently valued at $2 Billion. This is expected to grow at a CAGR of 26 percent reaching approximately $16 Billion by 2025, making India’s share approxi mately 32 percent in the overall global market. The nearly eight fold leap of the Indian Big Data market is a lucrative opportunity waiting to be tapped.
As the India market remains in the eye of a major digital transformation buoyed by a techcentred Union Budget, SME Channels embarks upon recording the voices of the who’s who of the Big Data Analytics landscape. Leading Technol ogy company SAP is at the forefront of this niche segment whether leveraging this highly promising technology or preparing solutions for customers.
Solutions Galore
The pandemic-driven digital revolution across industries such as healthcare, manufacturing, wholesale and retail, etc. has resulted in enhanced big data implementation. Industrial internet of things (IIoT), and artificial intelligence (AI) too have propelled computerization in the production industry. Big data technology is increasingly being employed across portfolio management, asset administration and analytical maintenance, net
The world of Big Data is rapidly evolving with Indian enterprises accelerating their digital transformation journey. The rapid shift to cloud is fuelled by enterprises’ aim to better sense and respond to consumer demand, monetize new business models, and continue to stay relevant in a competitive market.
To maximise the value of data and deliver tan gible business outcomes, SAP offers its customers an enterprise grade, industry leading and analysts endorsed Platform-As-a- Service (PaaS) suite called the Business Technology Platform (BTP).
SAP’s Business Technology Platform brings together data, data management, analytics, plan ning, Artificial Intelligence, integration, automa tion and application development cloud native services in a unified environment.
Indian customers across industries have piv oted to SAP’s Business Technology platform for their data strategy needs and have realized quick business value. They have deployed Bigdata usecases covering real-time cash flow & liquidity forecasting, raw material & inventory forecasting, customer & business partner risk scoring, predic tive quality management etc. based on existing data stored in SAP & Non-SAP applications.
Rajeev Singh, Vice President & Business Head - Midmarket & Emerging Business, SAP Indian Subcontinent, says, “SAP’s BigData Analytics core offerings include SAP Analytics Cloud, SAP HANA Cloud and SAP Data Intelligence. With SAP Analytic cloud we bring together AIpowered analytics and planning with a unique integration to SAP applications and smooth access to heterogeneous data sources. With over 100+ prebuilt industry and line of business templates, business users are now able to act on real-time insights, make agile decisions, plan, simulate and forecast business outcomes based on historical and current trends. With SAP HANA Cloud, our customers can now modernise their data founda tion with an in-memory database technology that runs transactions and analytics on multi-model data at a petabyte scale with integrated multi-tier storage. With SAP Data Intelligence we provide a set of tools to identify, gather, analyze, and make available the most context-relevant data through out the enterprise.”
Mega Trends in Analytics Market
Today many companies are using historical data to conduct product research, track customer engagement and loyalty, and identify key market trends. As a result, data analytics has emerged as
SAP’s Business Technology Platform brings together data, data management, analytics, planning, Artificial Intelligence, integration, automation and application development cloud native services in a unified environment
MAXIMIZING THE VALUE OF DATA
“TO DRIVE CONTINUOUS LEARNING THROUGHOUT THE WHOLE SAP PORTFOLIO AND AID PARTNERS IN STAYING UPDATED, A NEW LEARNING SERVICE HAS BEEN CUSTOMIZED FOR OUR PARTNERS TO MEET THEIR UNIQUE BUSINESS NEEDS.”
SME CHANNELS OCTOBER 2022 14 PARTNER CORNER
a critical component of enterprise digital trans formation initiatives. Some of the key trends that Rajeev foresees are:
a. Enterprises will need to adopt data fabric architectures: Channels for digital marketing, sales, customer support, and services are rapidly expanding, however, a remote working style complicates matters. Enterprises are now dealing with many applications, devices, and data infra structure (think data warehouse, data lakes) and the distributed enterprise lacks a centralized data infrastructure that seamlessly weaves all available data and caters to the organization’s data and ana lytics needs from beginning to end. In the future, organizations will need to strategize ways to drive a unified enterprise-wide data and analytics man agement approach that empowers them while also improving delivery time.
b. Increase in AI-based data analytics: AI, automation, and machine learning are reshaping the business landscape around the world. AI is advancing quickly, particularly in data analytics, where it not only augments human capabilities but also contributes to increased business value.
The pandemic and remote work have increased data tracking and measurement opportunities significantly, spawning a new data-driven culture in organisations. This data culture is encouraging investments in AI-based analytics.
c. Data-analytics to drive Diversity and inclusion & Sustainability efforts: Organiza tions have begun priortising the enabling of a future with zero emissions, zero waste, and zero inequality. This has resulted in an increase in connecting environmental, social, and financial data holistically to steer businesses toward better decision making and address current and antici pated regulatory compliance reporting. Similarly, Diversity and inclusion (D&I) is a significant driver of effectiveness and profitability, as well as a force for social cohesion. It is not surprising that D&I is now the top priority for HR professionals across industries. Businesses can gain insights into the entire employee lifecycle by using quantita tive and qualitative data, including recruitment, employee behaviours, governance, processes, talent attraction, learning and development, and so on. We will see more organizations investing in cloud-based data analytics to drive their Sustain ability as well as D&I efforts.
What Drives this Growth
Increased internet consumption and the advent of smart mobility technologies have all contributed to an exponential data explosion. As per IDC, the global big data analytics market is projected to grow from $271.83 billion in 2022 to $655.53 billion by 2029, at a CAGR of 13.4% in the forecast
period. With data establishing itself as the new oil, companies across industries such as healthcare, IT& Telecom, Retail, BFSI, etc., are using data ana lytics to improve operational efficiencies, develop better products and enhance consumer experi ences. “This is just the beginning, and we will see more organizations embrace the trend, particu larly with enterprises in the government & public sector, as being seen in India,” predicts Rajeev.
“Other factors such as increase in cloud com puting traffic, the burgeoning development and acceptance of technologies like IoT and AI, the increased implementation of big data and AI have all contributed to the growth in big data analytics market.”
Where Partner Profitability is Paramount
SAP fosters a vibrant and growing partner eco system that helps it achieve its corporate strategy, as well as its services and support aspirations. SAP’s partners supply vital industry and digital insights to help its customers plan and execute their transformation. “Their success means excel lent customer experience. To this end, we have aligned our services and support portfolio to be complementary to partner offerings and pro vide combined value in customer engagements. Additionally, our biggest opportunity as of today is in the cloud. In the coming years, cloud-based activities will account for more than 60 percent of net new revenues for SAP partners. One of the major priorities for us is therefore to create more partner-ready products. Through a variety of our next-gen partner programs such as SAP Partner Edge, they also receive access to SAP expertise. This helps partners enable, build and improve their capabilities especially during the transition to cloud,” says Rajeev.
Response from Partner Community So, how has been the response of the partner community towards this new technology? Rajeev says, “SAP has been consistently recognized as the leader and #1 technology solutions provider across various industry platforms and reviews. Our innovations are led by customer require ments and we service organizations, both big and small, across 25 industries in India. We help our partners quickly deliver solutions, leverag ing pre-configured industry and line-of-business functionality which are complementary to their offerings. Together, our partners believe that we are adding true value to our customer’s business transformation and hence, they are aligned and open to taking newer technologies to the market.
Partner Upskilling
Big Data Analytics calls for intensive Partner Upskilling. How does SAP ensure that its partners are properly trained for this? Well, with the current pace of innovation, SAP has long supported learn ing and enablement across the ecosystem and has been offering an array of cost-effective, role-based learning solutions. “To drive continuous learning throughout the whole SAP portfolio and aid part ners in staying updated with SAP solutions, a new learning service has been created and customized for our partners to meet their unique business and training requirements. The SAP partner ecosystem has successfully adopted this service since launch, and thousands of learners are actively using it to enhance their skills and knowledge on SAP prod ucts and obtain certification,” informs Rajeev.
Launched on a private cloud, SAP PartnerEdge is another programme that offers benefits across various roles within the partner’s organization. For instance, the administrators can better supervise learning activities and comprehend the value obtained from the solution, while learners can upskill in a more private setting with companyspecific learning content.
Expanding Area of Application
While almost all industry verticals are currently witnessing application of Data Analytics solutions, some areas are having the lion’s share of these.
“The adoption of our solutions is not limited to any specific industry vertical anymore. While the initial push arose from B2C sectors (CPG, Retail & Fashion, Healthcare), now, even traditional B2B setups like discrete manufacturing & EPC are demanding analytics & platform solutions. The shift has been accelerated in the wake of macroeconomic headwinds where promoters & CXOs understand the role of analytics in rede fining their strategy. They realize it can help with swiftly responding to challenges like supply chain disruption, optimizing working capital manage ment & talent management to gain completive advantage. Conversations too have evolved from operational dashboard to more prescriptive based analytics where CXOs expect applications to pro vide guidance considering constraints & historical outcomes,” says Rajeev.
The company is also looking to expand appli cation of Analytics solutions to other verticals. “From an expansion perspective, we are looking at this application segment holistically. As men tioned above, SAP has an extremely rich portfolio around bigdata, platforms (BTP), data intelligence & business warehouse. With 77% of all worldwide business transactions touching an SAP system, we’re ideally placed to be the OEM of choice for everything related to data for our existing custom ers & prospects,” says Rajeev.
SME CHANNELS OCTOBER 2022 15 PARTNER CORNER
YUANQING YANG CHAIRMAN AND CEO, LENOVO

UNLEASHING SMARTER TECH INNOVATIONS
Technology leader Lenovo unleashed a bevy of innovations at its annual global innovation event, Tech World’ 22, sharing its vision for the evolution of collaboration across users, spaces, and devices to unlock unlimited possibilities in both real-world applications and the Metaverse. Unveiling new concepts, solutions, and emerging innovations that will define the way we work, learn, and engage in the digital world, the company also announced its vision for net-zero emissions, honing in on a credible and collaborative blueprint to addressing one of humanity’s greatest challenges.
Lenovo unveiled innovations including the first public showing of rollable proof of concepts for smartphones and laptop PCs. Infusing computing into rollable screens provides productivity, enter tainment, and connectivity on a dynamic, adjust able, and larger screen, but on smaller device – addressing customer pain points and improving
hybrid working productivity.
Also unveiled was the compelling interactive and physical holographic solution for immersive telepresence communication and teamwork, called Cyber Spaces. As data proliferation con tinues, Lenovo also showcased how its innova tions, empowered by AI with edge computing, are enabling faster data processing at the source of its creation, transforming city streets, precision medicine, and shopping markets.
“Technology is transforming our future work space and living space into a combination of vir tual and physical worlds, enabled by the power of new IT infrastructure which is prevalent, expected and on demand,” said Lenovo Chairman and CEO, Yuanqing Yang. “The power of innovation is not only digitalizing and smartifying all industries but also helping solve humanity’s greatest chal lenges. For that purpose, Lenovo is doubling our investment in R&D to use smarter technology to
ROLLABLE FORM FACTOR INNOVATIONS
• Lenovo and Motorola unveiled rollable proof of concepts for smartphones and laptop PCs, ushering in a new potential era where this unique form factor enables more content and offers huge possibilities for the future to improve hybrid work and life. Designed to elevate multi-tasking, browsing, and mobile use cases, the new rollable proof of concepts are compact, yet don’t sacrifice screen size – enabling content on screen to be dynamically adjusted to the device as the expandable screen rolls inward into the base of the laptop, and smartphone.
INNOVATIONS FOR PRODUCTIVITY
• Lenovo Freestyle app enables universal control and collabora tion between a tablet and PC, allowing users to seamlessly pair and transform their tablet into a portable second screen to extend desktop space or a wireless touchscreen for their laptop.
• motorola edge smartphones include Ready For Plat form, which extends smartphone capabilities to bigger screens and allows for a mobile desktop experience, console-like gaming, content streaming and video chats
• Lenovo revealed its Remote Work Enablement solution, which delivers hardware, software, and premium services straight to employees, and allows remote workers to get set up quickly.
• Lenovo also presented a future concept called Cyber Spaces, which replicate an immersive face-to-face experience by providing an interactive, physical holographic solution for telepresence communi cation and teamwork.
• Additionally, the event saw new advancements in “virtual perso nas” or “digital humans,” to address challenges posed by traditional video conferencing, including bandwidth, quality, and privacy.
AI SOLUTIONS
• Lenovo showcased its Production Decision Engine, which uses AI and big data to address digitalization pain points. Its Supplier 360 identi fies, analyzes and mitigates supply chain risks to help plan for ‘what if’ scenarios.
• The company also presented its Smart Ser vices solution, which forecasts repair needs and optimizes the network of parts, service engineers and logistics support.
• Lenovo demonstrated how its Virtual Classroom solution offers virtual teachers to students, providing personalized tests and recommendations.
• The new remote video collaboration solution connects frontline workers with remote experts to perform repair jobs through real time marks.
At Tech World’22, Lenovo unveilled new concepts, solutions, and emerging innovations that will define the way we work, learn, and engage in the digital world
“THE POWER OF INNOVATION IS NOT ONLY DIGITALIZING AND SMARTIFYING THINGS BUT SOLVING HUMANITY’S GREATEST CHALLENGES.”
SME CHANNELS OCTOBER 2022 16 SMART TECH
empower a rapidly changing world.”
Innovation Unleashed
At Tech World ‘22, Lenovo unveiled Rollable Form Factor Innovations, Innovations for Pro ductivity, AI Solutions, its Vision for Net-Zero by 2050, and Edge and AI technologies Enabling Next-gen Data Processing.
Lenovo also unveiled the findings of its global multi-industry research study of 500 chief tech nology officers (CTOs). The study uncovered CTO’s viewpoints on how traditional IT will continue to evolve into a ‘New IT’ architecture where client devices, edge computing, cloud computing, network and AI all work together to address common pain points and provide solu tions that drive further global digitalization across all industries.
Tech World ‘22 coincides with Lenovo’s global Think30 celebration, honoring 30 years of Think Pad’s and ThinkSystem’s purposeful design and engineering innovation. Building on this legacy, the company unveiled the broadest enterprise portfolio enhancement in its history, designed to accelerate global IT modernization with the new Lenovo Infrastructure Solutions V3, and celebrated over 200 million ThinkPad devices sold. Lenovo continues to redefine device inno vations, including with the recent launch of the new ThinkPad X1 Fold, the next generation of the world’s first foldable PC.
Lenovo Chairman and CEO, Yuanqing Yang delivered the Tech World ‘22 keynote speech and shared insight into how Lenovo’s smarter technol ogy is empowering people everywhere to change
their world for the better.
In the keynote, Yang was joined by Lenovo business leaders and leading global CEOs, includ ing Cristiano Amon, President and CEO of Qual comm; Pat Gelsinger, CEO of Intel; Julie Sweet, Chair and CEO of Accenture; as well as Lisa Su, CEO of AMD, and Arvind Krishna, Chairman and CEO of IBM. Customers and partners includ ing Stefano Domenicali, President and CEO from Formula 1 and Panos Panay, Executive Vice Presi dent and Chief Product Officer from Microsoft also discussed the role of Lenovo’s smarter tech nology in empowering intelligent transformation.
Dr Yong Rui, Lenovo’s Chief Technology Offi cer, discussed how Lenovo will develop Metaverse tech solutions to empower intelligent transfor mation. He highlighted how Lenovo’s core tech nology and innovations across devices, servers, software, and solutions will connect the virtual and physical worlds.
During the main keynote session, Luca Rossi, President of Lenovo’s Intelligent Devices Group, presented new future concepts. From consumer innovations that improve life to productivity and collaboration solutions, new form factors like the rollable laptop PC and smartphone proof of concepts, and even emerging AI and Metaverse solutions like the new Lenovo ThinkReality VRX virtual reality solution will empower future gen erations as they navigate the digital transforma tion of our evolving world.
Kirk Skaugen, President of Lenovo’s Infrastruc ture Solutions Group, presented the evolution of computing everywhere. Kirk discussed the need to immediately harness data across all indus
tries to intelligently transform. Lenovo’s smarter infrastructure is enabling this transformation, via servers, storage, and services. Kirk was joined by leaders from VMware and the Barcelona Super computing Center as he showcased how Lenovo is leading AI at the edge to help customers harness the power of the global data growth (expected to double by 2025) happening across today’s chang ing IT landscape.
Ken Wong, Executive Vice President and President of Lenovo’s Solutions & Services Group, discussed how the role of a CIO has expanded as the world digitizes. Ken also highlighted the value of industrial Metaverse solutions, the importance of digital workspace solutions and how optimiz ing track management for engineers can improve infrastructure such as public transportation, in real time. Claudia Contreras, Executive Director of Lenovo’s Global Sustainability Services also highlights that Lenovo’s services can help custom ers work toward their own sustainability goals, no matter where they are in their journey.
Laura Quatela, Senior Vice President and Chief Legal Officer at Lenovo highlighted the ways Lenovo is working toward enhanced sustainabil ity across its product offerings on its journey to net-zero. In addition to sustainable product inno vations, Laura shares sustainable improvements Lenovo is making to lead the way in low-emis sions manufacturing, as well as Lenovo’s inten tions to share and report its progress for a credible, collaborative approach to emissions reduction. These sustainability efforts were bolstered by Yang’s closing announcement of Lenovo’s com mitment to a vision for net-zero by 2050.
VISION FOR NET-ZERO BY 2050
• Lenovo shared its vision for net-zero emissions, and its first step toward that vision with near-term 2030 emis sions reduction goals. Lenovo is aligning its emissions reduction goals to the Science Based Targets initiative in both the near and long-term to contribute to the goals of the Paris Agreement.
• Lenovo highlighted the innovations that will help it realize its vision for net-zero, and the actions the company is taking across products and manufacturing to lower its carbon footprint.
• Guest experts clarified the need for credible standards and collaboration between public and private entities in order to make progress toward a smarter, more sustainable future while clarifying the meaning and importance of net-zero commitments.
EDGE AND AI TECHNOLOGIES ENABLING NEXT-GEN DATA PROCESSING
• Lenovo and VMware announced an MOU for joint Edge and Cloud Innova tion Labs, with plans underway to develop co-engineered edge, AI and multi-cloud solutions that will help accelerate business transformation across manufacturing and retail environments.
• Lenovo showcased its ThinkEdge series of servers – including SE350 and SE450 –to show how the servers perform well under extreme conditions, with top-performance GPUs to support heavy AI .
• Lenovo also presented XClarity, a unified, open cloud software management platform that simplifies IT orchestration, deployment, automation, metering, and support from edge to cloud. The company also showcased its Edge Cloud Platform, which enables various applications across vertical industries as well as its Hybrid Cloud Solution, which covers the full lifecycle of building, migrating, using and managing hybrid cloud.
• Additionally, TruScale, an all-inclusive, subscription-based model, has expanded to more customers.
SME CHANNELS OCTOBER 2022 17 SMART TECH
TOWARDS A
ZERO
TRUST
APPARATUS
BY MANASH RANJAN DEBATA manash@accentinfomedia.com
As October is observed as the International Month of Cybersecurity across the world, India Security Market bets big, riding on the opportunities created by massive digitalization
The pandemic driven massive digi talization and unprecedented cloud migration brought along with them a significant rise in cyberattacks and security breaches. Attackers went on to outsmart and realigned their tactics and techniques, including social engineering and exploited misconfigurations, to target cloud environments.
This too pushed security-conscious organi zations to uptick their security preparedness through the right combination of expertise, intel ligence, and adaptive technology. As ransomware, credential theft and endpoint security issues become all-pervasive, leading cybersecurity war riors moved to empower businesses to smoothsail today’s threat landscape.

With rising ransomware cyberattacks on
IT infrastructure, businesses have realized the importance of embracing zero tolerance for gaps in their security strategy. They are increasingly investing on strengthening their cybersecurity to secure their crown jewels and their valuable data. This has thrown open a big opportunity for cyber security players.
“Every industry in recent years has undergone rapid digital transformation. While the rapid adoption of digital technologies helps in imple menting new and disruptive business models and processes, it also involves risks, increasing cyberattacks being the biggest risk factor. The rapid adoption of cloud-native architectures have expanded the attack surface for adversaries to exploit especially where security provisions haven’t kept pace with the acceleration of digital transformation,” says Nitin Varma, Managing Director, India & SAARC, CrowdStrike India.
SME CHANNELS OCTOBER 2022 18 COVER STORY
Manish Alshi, Head of Channels and Growth Technologies - India and Saarc, Check Point Soft ware Technologies, says, “We have a robust prod uct portfolio to provide any organization with the ability to conduct their business on the internet with the highest level of security. We address orga nizations’ most imminent cyber security needs based on three core principles i.e. Prevention-first approach, Gold Standard Management and Con solidated Solution.”
Ripu Bajwa, Director and General Manager, Data Protection Solutions, Dell Technologies India, says, “With businesses in India running workloads in a hybrid environment, it is critical to securely store data in multiple spaces like data bases, file servers, and network-attached storage (NAS). While considering a solution that gives businesses the flexibility to access, upload, protect and analyse data, an asset that gives the advantage of long-term retention, reporting and insight into cloud storage use, will serve organisations better.”
Bajwa adds, “Dell Technologies’ new SaaSbased Apex Backup Services offers end-to-end scalable, secure data protection with centralised monitoring and management for SaaS applica tions, endpoints and hybrid workloads.”

“It is essential that businesses have a com prehensive data backup plan in place to be fully prepared at the time of a data breach. That’s not all! Only backing up may not protect your data from ransomware - it is equally important to ensure that the backup is well protected and securely stored. Organizations need to ensure their data protection capabilities keep pace with the demands of their business, to close the gap between how much data they can afford to lose after an outage versus how frequently data is backed up,” says Sandeep Bhambure, Vice Presi dent, Veeam Software – India & SAARC.
As the India market remains in the eye of a major digital transformation buoyed by a digital upsurge, SME Channels embarks upon making an incisive analysis of the threat landscape and taking stock of the changes that has overtaken the Cybersecurity industry.
Capitalizing Market Demand
Cybersecurity players are leveraging the uptick in demand for security solutions in a big way. “We recognize that today’s organizations are operat ing on distributed, hybrid networks that stretch across many data centres in multiple geolocations, cloud-based infrastructures, applications, virtu alized platforms and services and much more.
There are more types of technologies, assets and services in every organization and each and every one of them is vulnerable to some sort of attack or threat beyond a simple, exploitable vulnerability
caused by a missing patch,” says Glen Pendley, CTO, Tenable.
“It is for this reason that we recently launched Tenable One an Exposure Management Platform to help organizations holistically look at the entire attack surface and operationalizes preventive security practices,” Pendley adds.

Cyberattacks have been around for quite some time now, but the recent pickups in data breaches and ransomware attacks have crippled critical infrastructures and revealed that no enterprise, large or small, is immune to cyberattacks. As restricted corporate networks become more vul nerable, tried-and-tested security methods have become outdated. With the security threat land scape growing more complex each day, customers need an adaptable protection solution. This is where players like Trellix come in.
“Trellix’s XDR delivers adaptable, scalable, and innovative security solutions to organizations around the world. We spot, stop, and adapt to incoming threats – our ‘Living Security’ frame work is constantly learning, making us smarter with each attempted attack. We utilize an open technology platform, from which businesses can benefit from automated security policy orches tration across a wide range of security products, which is intended to deliver the greatest visibility, control, and vendor choice across all attack sur faces,” says Manish Sinha, Director Sales Engi neering- India and SAARC, Trellix.
Alarming Threat Perception
According to a recent survey by Gartner, by 2025, 30% of critical infrastructure organizations will experience a security breach that will result in the halting of an operations- or mission-critical cyber-physical system.
“With accelerated adoption of the cloud-first model, there has been an exponential rise in cybercrimes. India has seen a major spike in cybersecurity-related threats, with over 6.7 lakh cases recorded so far in 2022. Cybercriminals have now realized that instead of targeting com pany networks, they are better off targeting users by leveraging the information available on public forums and social media. Phishing and social engineering attacks have increased more than ever before. CISOs need to invest in solutions that help users identify phishing emails and also be cautious about their social media footprint,” states Satya Machiraju, VP, Information Security at Whatfix.
Akshat Jain - Co-founder and CTO, Cyware, says,“Cybercriminals frequently morph their attack methods to stay under the radar of exist ing cyber defenses deployed by organizations. Every newly discovered software vulnerability or
unguarded asset on an enterprise network pres ents an opportunity for attackers to infiltrate.”
Fighting Threat Organizations now need to focus on specific train ing such as secure coding and security hackathons for developers. IT leaders should understand that the targeted attacks will continue to rise and ensure that they invest heavily in user education and enablement towards Cybersecurity.
“To address the challenges, cyber-security should be woven into the digital fabric so as to achieve a state of “security by design”. Timely detection of intrusions is a crucial element of every comprehensive cybersecurity strategy. The earlier an organization can detect an attack, the less impact it will have on the business and the easier it will be to resolve. Organizations should understand their own data assets and have absolute visibility and security capabilities for protection such as by maintaining a register of processing activities. Without centralized vis ibility, organizations risk leaving a back door open and falling victim to significant attacks or ran
19SME CHANNELS OCTOBER 2022 “AS AN EXPOSURE MANAGEMENT PLATFORM, TENABLE ONE HELPS ORGANIZATIONS HOLISTICALLY LOOK AT
THE
ENTIRE ATTACK SURFACE AND OPERATIONALIZES PREVENTIVE SECURITY PRACTICES.” GLEN PENDLEY, CTO, TENABLE
COVER STORY
somware often via illegal access to their networks through stolen credentials,” echoes Nitin.
“Security teams require a thorough knowledge of how the sophisticated threat actors operate, and accordingly evolve their detection, analysis, and response workflows. They also need to maintain complete visibility and control over their entire attack surface to ensure no loopholes exist in their defensive measures. This means smarter decisionmaking for SecOps can be enabled by strategic and tactical threat intelligence, along with threat visibility and real-time situational awareness to bring about positive security outcomes,” recom mends Akshat.
What’s Up in the Sleeves of Cyber Warriors
Creating an environment that is resilient, reliable, and that employees can trust on to simply meet their needs is one step closer to sustaining the link between technology and people. According to a report by GlobalData, more than 50% of Indian businesses have significantly boosted their Infor mation and Communications Technology (ICT) budgets for this year compared to 2021, as a result of the expanding digitisation of organisations.
“Therefore, Secure Access Service Edge (SASE) and Zero Trust framework have rather become vital elements for IT leaders to ensure complete visibility, control, and enforcement of their net work security. The Zero Trust Security should ensure that home or remote workers are subject to the same security measures as campus or branch networks. With AI-powered client visibility and integrated security ecosystems, enterprises can provide a holistic edge-to-cloud security to its customers and therefore, tackle the ever-evolving security threats,” says Prakash KrishnamoorthyDirector, India at Aruba, a Hewlett Packard Enter
prise company.
Our interaction with the leading lights of the security industry has led us to affirm the potential risks and the innovation and sophistication in Cybersecurity solutions in the arsenal of cyber warriors.
Venkat Krishnapur, Vice-President of Engi neering and Managing Director, Trellix India, says, “The majority of current security options rely on siloed intelligence. These may address immedi ate threats, but the increasing number and com plexity of cyberattacks are forcing security teams into a noticeably constant reactive posture. Ergo, we are unknowingly creating security silos.
If we throw a cursory look at the threat land scape, some prominent trends will catch our atten tion. Let’s walk through them one by one.
WFH Heralded Severe Security Challenges
The remote working culture adopted by a high proportion of the workforce poses significant new cybersecurity risks. This has emerged as one of the most talked-about new trends in cyber security. Compared to well-protected office environments, Home offices are often less protected. Central ized offices are usually well protected by secure firewalls, routers, and access management run by IT security teams, whereas traditional security vetting kept in place in home offices may not be as rigorous, with cybercriminals adapting new tactics to take advantage of this.
“With hybrid work becoming the new default, critical corporate infrastructure and networks demand increasing protection from the rising cyberattacks. Employees using unsecured remote work endpoints, bypassing VPN usage, and misconfigurations in the cloud applications are proving to be an emerging threat that traditional
methods like passwords and IP-based controls are no longer sufficient to mitigate,” says Edgar Dias, Regional Vice President of Channel and Partner ships for Asia Pacific at F5, Inc.

Challenges of a Distributed Workforce
With remote working in vogue, a critical cyber security trend for organizations is to focus on the security challenges of distributed workforces. This necessitates identification and mitigation of new security vulnerabilities, improving systems, implementing security controls, and ensuring proper monitoring and documentation.
Dr. Robert Blumofe, CTO, Akamai, says, “In Hybrid working environment, employees have the liberty to work from home as easy as it is in an office setup. It has created security complexity while exposing organizations to a potential attack. This includes employee’s consumer devices - like home WiFi routers and smart TVs. Hence, orga nizations will be forced to address this complex ity and decide how to balance corporate security without hampering employee satisfaction,”
IoT -- New Frontier of Attack
Increasing adoption of Internet of Things (IoT) has prepared favorable breeding ground for cybercrime. The Internet of Things makes a net work of physical devices other than computers, phones, and servers, which connect to the inter net and share data. Starting from wearable fitness trackers, smart refrigerators, smart household appliances to smartwatches, and voice assistants like Amazon Echo and Google Home – all comes under its purview. The IoT has been recognised as a specific threat. As per one estimate, by 2026, there will be 64 billion IoT devices in use around the world. The trend towards remote working is also fuelling its growth.
“Channel Partner expertise will be crucial in helping CISOs understand the IoT estate, assess risk, and take the appropriate steps to secure the network. Educating enterprises on Zero Trustthe key to beat the IoT threat - and what they need to do to develop this framework will be instru mental in this scenario and also be a significant part of the partner role. Network segmentation through the implementation of physical and virtual firewalls will be essential in reducing the attack surface,” says Krithiniwas Neelakantan, Channel & Alliances Leader, Palo Alto Networks.
Spurt in Ransomware
According to a survey by the UK National Cyber Security Centre says three times as many ransom ware attacks were conducted in Q’1 of 2021 as they were in the entire year of 2019. Another research by PwC suggests that 61% of technology execu
“WE ADDRESS ORGANIZATIONS’ MOST IMMINENT CYBER SECURITY NEEDS BASED ON THREE CORE PRINCIPLES I.E. PREVENTIONFIRST APPROACH, GOLD STANDARD MANAGEMENT AND CONSOLIDATED SOLUTION.”
MANISH ALSHI, HEAD OF CHANNELS AND GROWTH TECHNOLOGIES - INDIA AND SAARC, CHECK POINT SOFTWARE TECHNOLOGIES
SME CHANNELS OCTOBER 2022 20 COVER STORY
tives expect this to increase in 2022. Although it has been there for almost two decades, Ransom ware has driven new worries for IT security teams. Cybersecurity experts estimate that there could be over 120 separate families of ransomware doing the rounds.
Nitin Varma, Managing Director, India & SAARC, CrowdStrike India, says, “This past year, we saw the rise of the double extortion ransom ware model, in which threat actors will demand one ransom for the return of the data and an additional ransom on top to prevent the data from being leaked or sold. However, in 2022, we expect to see the extortion/exfiltration side of ransom ware achieve even higher levels of sophistication, possibly with a shift away from encryption to a sole focus on extortion.”
VPN Exploits Grow
Over the last year, cybersecurity professionals have increasingly witnessed an unhealthy spurt in exploits targeting their business VPNs. This has again brought the use of VPNs into sharp focus, demonstrating the risks associated with this tech nology when deployed to support remote users. The findings of Zscaler’s recently released annual VPN Risk Report, conducted by Cybersecurity Insiders, indicates that there’s a growing number of VPN-specific security threats. The Zscaler report also calls for the need for Zero Trust secu rity architecture in enterprise-level organizations.
The 2022 report surveyed over 350 IT profes sionals in North America at organizations with global workforces. Despite high awareness of VPN risks, remote work forced many companies to rely more heavily on legacy access methods during the pandemic. This year’s Zscaler VPN Risk Report includes analysis of the state of the remote access environment, the most prevalent VPN risks, and
the growth in adoption of Zero Trust.
“As evident in several high-profile breaches and ransomware attacks, VPNs continue to be one of the weakest links in cybersecurity. Their architec ture deficiencies provide an entry point to threat actors and offer them an opportunity to move laterally and steal data,” said Deepen Desai, Global CISO of Zscaler. “To safeguard against the evolv ing threat landscape, organizations must use a Zero Trust architecture that, unlike VPN, does not bring the users on the same network as businesscritical information, prevents lateral movement with user-app segmentation, minimizes the attack surface, and delivers full TLS inspection to pre vent compromise and data loss.”


Customizing Offerings
Choosing the correct solution from a crowd of solutions is like searching a needle in a hay stack. In order to win the customer attention and trust, security players are bringing in quality product differentiation on the table. As the threat land scape becomes more sophisticated and cyber criminals evolve their techniques to maximize monetary gains with minimum complications and risk, the only way to effectively deal with this is to be one step ahead of the attackers.
“To achieve this, Trellix provides an open and native XDR platform that helps organizations gain confidence and resilience in their cyber security operations. The platform is aimed at going beyond the typical detection controls by using a holistic, yet simpler view of threats. XDR deals with realtime information and threat intelligence, which is delivered to business operations before the damage is done,” says Manish Sinha, Director Sales Engineering- India and SAARC, Trellix.
“We also announced some advancements in our XDR platform, providing security opera
tions teams with enhanced playbooks for guided investigations and upgraded threat intelligence. Additionally, in the year 2023, we also look for ward to launching “Trellix X-Console”, making it the control center for Trellix’s XDR solutions. It will simplify the user experience across Trellix XDR, providing a single interface for security operations teams. These updates and improve ments help us stay ahead of the curve in security solutions, making us the most up-to-date and advanced solution in the market,” adds Manish.
Towards Zero-Trust Model
In today’s highly digitalised world, data is any organisation’s most valuable resource. Amidst increasing cyberattacks, data-related risks are at an all-time high and are growing more complex in terms of scale and impact every day.
“To mitigate threats, enterprises can operate as a Zero-Trust Network and take a data-centric approach. To build such a network, security con trols should be as close to the data as possible. Under the Zero-Trust model, the administrator specifies a set of rules to enumerate permitted activities, and the software will evaluate every activity against that set of rules to determine
21SME CHANNELS OCTOBER 2022
“OUR SAAS-BASED APEX BACKUP SERVICES OFFERS END-TO-END SCALABLE, SECURE DATA PROTECTION WITH CENTRALISED MONITORING AND MANAGEMENT FOR SAAS , ENDPOINTS AND HYBRID WORKLOADS.”
RIPU
BAJWA, DIRECTOR AND GENERAL MANAGER, DATA PROTECTION SOLUTIONS, DELL TECHNOLOGIES INDIA
“WITH AI-POWERED CLIENT VISIBILITY AND INTEGRATED SECURITY ECOSYSTEMS, ENTERPRISES CAN PROVIDE A HOLISTIC EDGE-TO-CLOUD SECURITY TO CUSTOMERS. ”
PRAKASH KRISHNAMOORTHY DIRECTOR, INDIA, ARUBA
COVER STORY
whether it is on the ‘Allowed’ list. If it is not, the activity gets blocked,”Shuja Mirza, Director, Solu tions Engineering, NetApp India & SAARC.
Organisations should also employ multi-factor authentication for administrative and data access, as well as use encryption for data at rest, and in flight. Additionally, monitoring and logging all access to data can go a long way in improving security across networks.
“It is advisable for enterprises to work along with technical consultants to implement a robust data protection methodology across on-prem and cloud environments. Organisations must consider the latest tools and technologies like Blockchain and AI that help combat threats efficiently and cost-effectively in the long run,” advises Shuja.

Aligning Channel Strategy
Security players are aligning their channel strategy with the current market trends to make the most of it. “Recently, we announced Trellix Xtend at our event which is intended to offer a premium partner with a focus on profitability and partner enablement so we can enhance the customer
experience. We value their willingness to work with us in ways that directly benefit our custom ers because of the future initiative, Xtend, which centres on the premise that long-term customer success is best achieved through the channel,” says Manish.

With each level of participation in Trellix’s partner program come different tier benefits like market development funding, training credits, rebate calculation, and more. Through joint market development funds, we also collaborate locally with partners to identify new prospects and stay on top of current market trends.
Partner Upskilling
Security players are upskilling their partner eco system to provide a more ebullient security service to their clients. Manish says, “Partners are an important part of a business ecosystem that help keep our partner community engaged along with faster business growth. With their extensive net work, all-India teams, and technical know-how, they not only support us with a good customer experience and a quicker go-to-market, but they
also come full circle with business intelligence that helps us develop and deploy new and updated products in line with the needs and demands of the market. OEMs like us are partnered with an integral and expanded staff, and we work closely with them.”
It also adds to more revenue and quicker busi ness growth and gives a company the opportunity to reach customers through sales teams, channel partners, and co-marketing initiatives, making it a crucial element for an organisation to pursue.
“To further the partner experience, we announced ‘Trellix Xtend’, a partner focused strat egy aimed at offering a premium partner experi ence with a focus on profitability and partner enablement. With this, we aim to further enhance the customer experience. We value their willing ness to work with us in ways that directly benefit our customers because the premise of Xtend is that long-term customer success is best achieved through the channel,” says Manish.
Trellix’s Xtend comes with various levels of participation. With each level, come different tier benefits like market development funding, training credits, rebate calculation, and more. “Through joint market development funds, we also collaborate locally with partners to identify new prospects and stay on top of current market trends.”
Trellix Xtend, which will debut in early 2023, will prioritize the partner because the programme can be tailored to each partner’s business model and target market, it produces better customer outcomes.
Robust Growth Outlook
All players we talked to were bullish about their growth prospects for the current as well as the upcoming year. “We at Trellix are eager to assist our clients in developing and putting into practice their long-term XDR strategy. The customer’s activities are streamlined and informed thanks to the combination of various information sources provided by XDR, which will be a crucial com ponent of their cybersecurity strategy,” beams Manish.
“By increasing our clients’ security posture and operational capabilities through our products, platforms, and services, we also hope to facilitate their journeys toward adopting the cloud and undergoing digital transformation. By establish ing a solid ecosystem of channel partners and MSSPs, we hope to do this and provide our clients with the most recent in cyber technology. In 2023, Trellix aims to redefine the entire value chain, cus tomers, MSSPs, and channel partners – allowing us to redefine what cybersecurity means for the industry,” predicts Manish.
“WE REALIGNED OUR STRATEGIES TO HELP ORGANISATIONS ADAPT TO THE REMOTE WORK MODEL, ALLOWING ACCESS TO DATA ACROSS DIFFERENT LOCATIONS WITHOUT COMPROMISING ON SECURITY.”
“VPNS CONTINUE TO BE ONE OF THE WEAKEST LINKS IN CYBERSECURITY. THEIR ARCHITECTURE DEFICIENCIES PROVIDE AN ENTRY POINT TO THREAT ACTORS AND ENABLE THEM TO MOVE LATERALLY AND STEAL DATA.”
ARUN KUMAR J, REGIONAL DIRECTORSALES, MANAGEENGINE
DEEPEN DESAI, GLOBAL CISO, ZSCALER
SME CHANNELS OCTOBER 2022 22 COVER STORY
SHOWCASES AMD
POWERHOUSE PERFORMANCE WITH THE RYZEN 7000 SERIES DESKTOP PROCESSORS IN INDIA
Organized in partnership with leading OEMs including ASUS, MSI, Gigabyte, and ASRock, the exclusive event demonstrated the differentiated value proposition offered by AMD Ryzen 7000 Series Desktop processors and the new AM5 platform featuring DDR5 memory support PCIe 5.0 on an all-new socket that retails cooler compatibility
AMD hosted a deep-dive experiential session in Mumbai today featuring the recently launched Ryzen 7000 Series Desktop processors powered by the new “Zen 4” core architecture. This exclusive event organized in partnership with leading OEMs including ASUS, MSI, Gigabyte, and ASRock demonstrated the differ entiated value proposition offered by AMD Ryzen 7000 Series Desktop processors and the new AM5 platform featuring DDR5 memory support PCIe 5.0 on an allnew socket that retails cooler compatibility.


During the event, AMD and 3rd parties provided examples of real-world comparative data based on various benchmarks and gaming tests for the new Ryzen 7000 Series Desktop processors demonstrating excellent performance and at the same time leadership energy efficiency.
This exclusive event brought together AMD’s part ners, subject matter experts, media, tech bloggers, influencers, and other AMD enthusiasts to hear more about and discuss AMD’s next generation of highperformance CPUs for gamers, enthusiasts, and content creators.
SME CHANNELS OCTOBER 2022 23 INDUSTRY WATCH
NIPPING INSIDER THREATS IN THE BUD
Insider threats from current and past employ ees have come to torment businesses on a big scale. In 2022, the issue has been accentuated phenomenally. Nearly four in every ten exist ing employees have been found to pose a threat to data theft and as much as 63% of employees leaving a company admitted to taking data from their respective workplaces. Thus, to deal with this precarious situation, a holistic investigation mechanism to identify and manage threats has become the crying need of the hour.
In a special interaction with SME Channels, Shashidhar Angadi, Co-Founder & Chief Tech

nology Officer, Exterro, reveals his organiza tion’s approach to leverage this highly promising technology, opportunities created by the Unified Legal GRC Software solutions, his forecasts for digital forensic solutions industry, the major factors responsible for the unhealthy surge in insider threats, how to curtail and prevent risks and his vision and plans for the industry. Edited excerpts…
As a Unified Legal GRC Software Provider, how do you think digital forensic solutions can help in-house
investigations?
Over the last few years, insider threats from current and past employees have increased. In 2022, business leaders say that nearly four in ten existing employees pose a threat to data theft and 63% of employees exiting a company admitted to taking data from their respective workplaces. With insider threats on the rise, businesses need a holistic investigation mechanism to identify and manage threats.
Since legacy forensic technologies can be hard to scale, it can create data silos. Now that investi gations span across departments and endpoints, collating and analyzing data can take up exor bitant amounts of time. Existing forensic tools and technologies can’t perpetually deliver the efficiency required to complete the investigative workload. Given these realities, businesses need integrated digital forensic solutions that foster collaboration without requiring unnecessary data movement, longer timeframes or higher costs.
There have been rising incidents of insider threats (both intentional and unintentional ones) in India. What
Digital forensic solutions can aid in-house investigations and processes and enable organizations to be more proactive in detecting and avoiding insider threats
SHASHIDHAR ANGADI CO-FOUNDER & CHIEF TECHNOLOGY OFFICER, EXTERRO
“WHEN INTEGRATED WITH SIEM TOOLS TO CREATE A SECURITY ORCHESTRATION AUTOMATION RESPONSE, DIGITAL FORENSIC SOLUTIONS CAN PROVIDE A PLAYBOOK FOR COMPANIES TO TAKE PREVENTIVE MEASURES BEFORE A BREACH OCCURS.”
SME CHANNELS OCTOBER 2022 24 DATA SECURITY
are the factors responsible for this unhealthy surge?
One of the primary reasons for the increase in Insider threats is the lack of visibility into all end points in a remote or hybrid work model. New organizational policies like work from anywhere and bring your own device, cloud migration and evolving privacy regulations have made investiga tions more complex. More remote endpoints have created more security vulnerabilities and organi zations have lesser control, and even lesser access to data and collaboration between teams for inves tigations. Besides, organizations in India have been slow in implementing policies, procedures, and training employees in carrying out investiga tions effectively using digital forensic solutions. With slow tech adoption, organizations face the challenge of not being able to identify and mitigate intentional and unintentional insider threats.
Additionally, insider threats can be of two types — unintentional and intentional. Most often, unintentional leaks occur due to phishing or social engineering attacks. When such attacks occur, threat actors access information across the board including that of contractors and third par ties working for the business. It could also be that malicious code was deployed into the system of a remote employee, giving cybercriminals access to the corporate network.
Intentional attacks occur when employees will ingly exfiltrate critical data or work product. This could be an employee exiting the company or a disgruntled one. It could also be employees who are incentivised to exfiltrate data like the ransom ware group Lapsus$, which identifies malicious insiders to install malware before demanding a ransom. Given the highly distributed nature of corporate networks and inclusion of employee personal devices, the amount of data generated too has increased significantly. Gaining visibility into employee personal devices is again a chal lenge and since home networks are now a part of the corporate network, a compromise of any one device has the potential to compromise critical business information and intellectual property. These are some of the most pressing concerns associated with insider threats.
What are factors that impede internal investigations currently existing among organizations?
Across all industries, inhouse investigations are becoming more collaborative and are drawing in staff who are not legal professionals to conduct these investigations. For instance, various depart
ments including HR, finance, compliance, and legal departments are increasingly playing a more active role in preserving data and analyzing it for investigations. Such cross-collaborations can make the investigation process complicated and time consuming. This is especially true when orga nizations have to collaborate not just internally but also with outside counsel, law firms or service providers for a probe.
With disparate sets of data scattered across vari ous functionalities and departments, managing data silos is a challenging task. In addition, gather ing data individually from remote endpoints can become extremely time consuming and expensive.
Why should organizations use digital forensics while trying to reduce risks brought on by insider threats?
Globally, insider threats have increased by 40% over the last 2-3 years and such an event costs companies an average of $13 million. Insider threats are clearly an expensive affair and if not monitored properly, may go unnoticed for weeks and sometimes months. Organizations need the capacity to react to insider threats immediately. This requires data to be collected from numerous endpoints across the network and remote loca tions. More often than not, it must be done with out detection. Once this data is collated, it needs to be analyzed swiftly with actionable insights on how to remediate the situation.
This is where digital forensic solutions can aid in-house investigations and processes. They can enable organizations to become more proactive in detecting and avoiding insider threats. When integrated with SIEM tools to create a Security Orchestration Automation Response, digital forensic solutions can provide a playbook for companies to take preventive measures before a breach occurs. Data gathered from digital forensic solutions can aid SIEM tools trigger workflows automatically to reduce the risk of data breaches.
At a time when organizations are generating petabytes of data, they need more powerful and flexible digital forensic solutions that can handle big, diverse data loads and work faster than existing platforms. But it’s not only about more processing power. Digital forensic solutions must enable better indexing, higher scalability and agile collection and analysis capabilities.
How will Exterro’s solutions reduce risk brought on by outsourcing investigations?
For any investigation to unveil the truth, it requires
unvarnished facts about the incident. This requires preserving, collecting, analyzing and reviewing data. When it is outsourced, such investigations can be an expensive and time-consuming process. This is because the process of identifying the right third-party vendor with expertise in digital foren sics and relying on it being forensically sound cre ates more contingencies. Besides, the outsourcing company would need to get access to the compa ny’s IT infrastructure and the devices that require data collection and analysis, opening up the attack surface further.
In addition, interviewing relevant people for the investigation and verifying the information they provide with the data, contextualizing and analyzing it becomes crucial and there can be no margin for error. In addition, the outsourcing companies will have to upload sensitive company data onto their own data centers to carry out the investigation. This poses a risk of data loss or theft too. Exterro’s solution can enable inhouse teams to get to the facts of the case faster, quicker in a cost-effective manner. The evidence generated is forensically sound and also avoids the risks of data movement and the use of non-defensible approaches of investigation that could render evi dence inadmissible.
How affordable are Exterro’s Legal Governance and Risk and Compliance (GRC) solutions? Does cost help you to gain market share?
Exterro’s technology is built on a core platform which can be customized before deployment. The platform is flexible, and modules can be built to suit requirements as and when needed. Each of the modules has built-in integration capabilities, providing complete visibility into data manage ment. Applications can be enabled as and when organizations need them without having to toggle between multiple apps. Exterro’s software has in-built connectors and integration capabilities ensuring existing investments within the orga nization are fully utilized and with no lost ROI. Exterro’s platform has a very flexible pricing model that is cost-effective for small, medium and large organizations. Flexible pricing models based on data usage helps organizations predict pricing on a need basis.
Exterro focuses on the overall ROI organiza tions can generate by getting to the facts of cases quicker and easier in a cost-effective manner. This is done by reducing the risk using ROT (Redun dant, Obsolete and Trivial ) strategies in the uni fied platform to get rid of unwanted data.
SME CHANNELS OCTOBER 2022 25 DATA SECURITY
HYBRID INTELLIGENCE LOADING: ARTIFICIAL INTELLIGENCE IS ALL SET TO GET A MAKEOVER
NEELESH KRIPALANI Chief Technology Officer Clover Infotech
PROFILE
As the Chief Technology Officer (CTO) at Clover Infotech, Neelesh is responsible for research and analysis of disruptive technologies which the Center of Excellence leverages to accelerate digital transformation of our customers. He also steers the automation initiatives in the organization, and quality, and capacity building across new-age technologies. Under his dynamic leadership, Clover Infotech has built a robust Cybersecurity practice.

Imagine a situation wherein an artificial intelligence system (a BOT) does not understand ‘context’. Human supervision or assistance becomes critical at such points to enable the BOT to get through and ensure that the end-user receives a satisfactory response.
This is where hybrid intelligence comes in. Hybrid intelligence combines the power of human intelligence and artificial intelligence (AI) to create outcomes that ensure a response with accurate understanding of the context.
While the computer can be trained to understand predictable queries or patterns and responses can be accurately programmed, it may be difficult for the machines (devoid of emotion) to understand context and modulate responses according to situ ation. It is also a factor of experience, which means the number of times the AI-powered system may have gone through such instances and learnt from it.
A relatively new AI-enabled system too will take time to learn the nuances of context and become smart enough to give a response with apt under standing of context.
The third aspect here is scale. With the world going the digital way and technology becoming an integral part of each process and system, every AI-enabled system will be at a different stage of evolution.
Hence, most of the processes that an enterprise runs to make life better for its customers and its employees will run on hybrid intelligence. It combines the power of machine/ artificial intel ligence (the ability to go about a job tirelessly and meticulously) and human intelligence (to use the power of IQ and emotional quotient) to ensure that a response is a well-thought one and not a trained reaction.
Why is Hybrid Intelligence important?
While we build very efficient AI-powered systems,
the dynamic nature of input is something that an AI-based system can never be fully prepared for. It will help with scale, but there will always be an odd instance where it will need the human touch (liter ally). The human brain has the capability to adapt and respond differently to the same input based on multiple internal and external factors. The high level of cognisance that they bring in their comprehen sion makes it invaluable and essentially helps to enhance the efficiency of AI.
Thus, the people-robot collaboration will be the way of the future as it will be one of the most effi cient ways to bring accuracy and scale together. If that works, it can change the entire functioning of an enterprise, enhance operational efficiency, and accelerate business growth.
The ‘Hybrid’ way ahead
There is no doubt that AI is here to stay, grow, and evolve. It will increasingly become smarter too. However, it will be great for enterprises to incorpo rate the ‘hybrid’ way into their AI roadmap today to reap rich dividends in the years to come.
It can enable employees to rid themselves of mundane, repetitive, and redundant tasks. They can supervise BOTs and get a more detached perspec tive to their work through analysis of data gener ated by the interaction of AI-powered BOTs with the end-users. This, in turn, will create a smarter employee base which relies on data and analysis for decision making.
The ’Hybrid’ way will be the harbinger for a cultural shift to well-informed decisions backed by data. As the ‘Hybrid’ way of going about AI becomes more prominent, it can democratize the power of leveraging data and analytics to grow businesses and will create a level playing field for SMEs and proprietary firms to become as capable and efficient as their larger counterparts.
GUEST ARTICLE SME CHANNELS OCTOBER 2022 26
As the ‘Hybrid’ way of going about AI becomes more prominent, it can democratize the power of leveraging data and analytics to grow businesses
PROFILE
A highly energetic business leader in the ICT industry, Bakshish Dutta possesses over 20 years of rich and accomplished experience in transformation with significant experience in the areas of strategy, to overcome complex business challenges and deliver on high-impact decisions. He has built credibility and delivered on customer confidence through focused business initiatives and has led sales teams and initiatives in a crossfunctional matrix environment working closely with C-level executives.

10 REASONS WHY THE PUBLIC SECTOR SHOULD SWITCH TO SAAS
With the rise in awareness about SaaS, private companies in India are migrating to SaaS for ease of business, however, the public sector is lagging in terms of implementing SaaS
Business models are continually changing to meet the changing needs of users and the advancement of technology. SaaS acceptability is the new buzz and as time has passed, the software industry has developed stronger, more reliable solutions to assist businesses in carrying out their routine duties and operations with less aggravation.
SaaS or software as a service is one of the most recent paradigm shifts in the software sector. Almost every industry has adopted and used SaaS to streamline corporate processes and operations, therefore its effects are not limited to the software sector. It is also possible to think of the SaaS plat form as a mechanism to offer programmes via the Internet using a subscription fee model as opposed to the more conventional on-premises, licenced software solutions. Through the use of the Internet, companies can obtain software as a service, which eliminates the need to provision and maintain com plicated computing infrastructure.
The benefits of SaaS have gotten better and better. With the rise in awareness about SaaS, private companies in India are migrating to SaaS for ease of business, however, the public sector is lagging in terms of implementing SaaS. Over the years, SaaS has established itself as a viable business model with CRM on-demand and that makes it reliable for public sector companies as well.
Below are the 10 reasons why the public sector should switch to SaaS:
1. Affordability:
The SaaS model’s cost-effectiveness is the main factor driving the change. It will assist public sector enterprises in lowering their maintenance and oper ational expenditures. IT maintenance difficulties are no longer a concern for software buyers because of SaaS. Many companies have spent a lot of money attempting to fix faults and problems with their systems, but SaaS eliminates all of those problems because the software supplier takes care of it on the client’s behalf. The supplier takes care of problems like scale, performance, uptime, general mainte nance, and disaster recovery, so the company no longer needs to spend money on software problems.
SaaS business products are often more cost-effective and practical because renting pricey software via a subscription entails less financial risk than purchas ing it outright.
2. Effective: Compared to on-premise systems, cloud solu tion deployment takes less time. Since there is no hardware expense, organisations will save time by not having to purchase new IT equipment and set up VPN access on several systems throughout the company. As the organisation expands, they may add more users without ever considering installing or adding the hardware. In contrast to on-premise software applications where speed and performance are crucial to the operation of the programme, cloud-based systems are efficiently put together to ensure optimal network performance and are also adaptable to business needs.
3. Flexible: Software that is available as a service (SaaS) is very scalable in terms of upgrades or new versions. For customers with variable financial circumstances, businesses may provide a variety of personalised payment plans with several tiers. Customers can usually start and stop using a service based on their goals because subscriptions are typically easy to sign up for and cancel. Every time the SaaS platform receives a new update, the vendor or supplier acts quickly to implement it for customers.
4. Accessibility: The simplicity of SaaS’s accessibility from anywhere in the world at any time is among its most signifi cant characteristics. Customers can typically access current, useful programmes by simply opening and signing into them after connecting to the internet. This quick, simple access saves the client time and effort and does not require them to have IT knowledge.
5. Customization: SaaS enables businesses to quickly alter apps to meet their needs and specifications without disrupting the core infrastructure.
To access more info login to: https://www.smechannels.com
GUEST ARTICLE SME CHANNELS OCTOBER 2022 27
BAKSHISH DUTTA
Country Sales Manager - India & SAARC, Druva
In a special interaction with SME Channels, Debasish Banerji, Director, Sales and Service, Eaton Electrical Sector, India, reveals his organi zation’s modern approach to power management technology; his company’s key offerings in this space, changing security scape; opportunities and challenges, opportunities for channel growth; his forecasts for the industry; and his vision and plans for the channel community. Edited excerpts…
Would you please brief us on Eaton’s offerings in the India market?
Eaton’s mission is to improve the quality of life and the environment through the use of power management technologies and services.
Eaton provides sustainable solutions that help its customers effectively manage electrical and mechanical power – more safely, more efficiently, and more reliably. Eaton’s 2020 revenues were $17.9 billion, and the company sells products to customers in more than 175 countries. Eaton has approximately 85,000 employees.
Eaton firstly established a presence in the Asia Pacific region during the 1970s. Since then, the company’s presence has grown significantly with a fast-growing network of sales and marketing offices, manufacturing plants, service centers, and research facilities in the region. Eaton moved its Asia Pacific headquarters from Hong Kong to Shanghai in 2014.
Today, we have nearly 17,000 employees, 6 R&D centers, and manufacture in 34 manufactur ing facilities in countries and regions including China, India, Japan, South Korea, Singapore, Indonesia, Thailand, Philippines, and Australia for all of Eaton’s distinct business.
Eaton Power Quality Private Limited, India is a 100% subsidiary and a part of the electrical sector of Eaton Corporation. We are catering to every industrial segment with versatile solutions which include Switchgear: LV & MV Solutions, Fusegear: LV & MV solutions, UPSs, and software solutions.
Eaton has been at the frontline providing comprehensive cyber security services for operational tech nology (OT) to help keep operations and personnel safe, How have you been leveraging the recent hike in demand for security solutions?
Eaton is dedicated to providing comprehensive cybersecurity services for operational technology (OT) to help keep your operations and personnel safe. Eaton have designed hardware and software products for decades, along with providing the associated installation and maintenance services
POWER
MANAGEMENT REDEFINED
Through its power management technologies and services, Eaton help its customers effectively manage electrical and mechanical power – more safely and efficiently
positions as the most capable cybersecurity pro vider in the industry for electrical infrastructure and building systems. Our experienced team of cybersecurity leaders identify and address gaps in your processes and personnel training programs to minimize your overall attack surface.
Customers rely on Eaton to understand, dissect and alleviate cybersecurity risk. It starts with dedi cated people. Our team members meet and exceed competencies recognized by international stan dards organizations through rigorous, in-depth technical training programs. You can be confident that management, engineering and personnel have the knowledge and service capabilities to address advanced cyber threats.
Cybersecurity Center of Excellence Cyberse curity is a foundational element in the lifecycle of our products and services. Cybersecurity is at the core of our “secure by design” philosophy, and it’s embedded in all the Intelligent Power products and platforms we bring to market. The Cybersecu rity Center of Excellence team aligns our talented people with best practice processes and modern technologies, creating a program that trains others and helps our customers avoid the dangers of cyber-attacks. Eaton has the first research and testing facility approved to participate in UL’s Data Acceptance Program (DAP) for cybersecurity in Pittsburgh, Pennsylvania. Recently, UL approved a second Eaton lab to join the program — another industry first — in Pune, India. These accredited lab environments provide the global capability to test Eaton products with intelligence or embedded logic to key aspects of the UL 2900-1 standard.
How do you view the recent innovations in the field of UPS tech nology and what is Eaton’s market strategy for it in the India market? UPS is a transversal technology and can be used by any power consuming set-up which could
be a large data center or a small-scale industry. Of course, AI and Robotic Process Automation (RPA) adoption does encourage use of IT assets (servers, storage, switches etc.) which thereby result in the increased usage of UPS to provide clean continuous power to such critical assets.
Another interesting point here is that with the use of AI and automation, the UPS is itself becom ing more ‘Aware’ and ‘Smart’. For example, the Eaton EnergyAware UPS allows the customer to intelligently feed power back to the grid thereby accelerating the return on investment. Eaton has made these features possible by the adopting the latest digital and electronic hardware technologies in our UPS.
We have a R&D center in Pune who serves Eaton globally across its all range of businesses be it UPS, Switchgear or Aerospace. We are develop ing new technologies which would help in creat ing a better for all of us to live. We are focusing on digital solutions (Software suites and intelligent products) which help customers to better manage their businesses. Focus on Energy Transition (Building as a Grid, Data Center as a Grid solu tions), EV solutions and lastly Digitalization.
As businesses face insurmountable power management challenges, how does your company help address the critical power manage ment needs?
We’re in the midst of a significant transformation - the digital transformation of manufacturing. The 4th industrial revolution, or Industry 4.0, is the automation of traditional manufacturing prac tices using digital technologies like the Internet of Things (IoT), robotics, additive manufacturing, factory simulation and augmented and virtual reality. Manufacturing models are becoming autonomous and using algorithms and machine learning to become “smart.”
INTERVIEW SME CHANNELS OCTOBER 2022 28
By leveraging Industry 4.0 technology, we’re significantly improving our manufacturing opera tions and adding value for our customers— creat ing and developing systems and processes that are connected, flexible and optimized. Innovative, scalable and data-driven manufacturing models are resulting in higher product quality, decreased time-to-market, reduced environmental footprint and a safer and more productive workforce.
What product differentiation does Eaton brings to the table?

UPS is often referred to as the “heart” of the elec trical network. Eaton has recently introduced UPS using EnergyAware technology that allows large Data Center operators to give back energy to the grid. The UPS’s primary role doesn’t change, but by creating UPS as a Reserve (UPSaaR) through EnergyAware, organizations can enable Energy Transition. UPSaaR organizations can offset both their capital expenditure while reducing the carbon footprint and boosting renewable energy. This is installed along with UPS to regulate demand from the grid i.e, responsible for upstream and downstream charging to discharge the bat tery back to the grid. It compensates the data center companies/operators for reducing energy consumption when required to maintain the grid frequency and contributing to green energy, thus
generating revenue from their UPS investments.
Demand for UPS systems is increasing due to the growing adoption of cloud servers. Manufac turers are more focused on developing systems with lower ownership cost, greater efficiency, and increasingly investing in developing reliable tech nology to fulfill demand for cloud computing.
Edge Data Center – The new wave “Edge computing” has become an IT buzz-phrase about data produced by the internet of things (IoT) devices. It reduces latency and creates faster connections than sending the data across long routes to data centers or clouds. Small data centers providing cloud computing support and process ing by expanding the Edge of the network can be categorized as Edge data centers. At times, a single Edge data center may be connected to many other Edge data centers that can be used to store, process, and cache data and deliver the required information when needed – at the right time at the right place.
We are the leader in edge computing technolo gies. We offer power management solutions for distributed IT edge environments to keep missioncritical applications and devices running longer and prevent servers from data loss. These tools include uninterruptible power supplies (UPS), power distribution units (PDU), and intelligent power management with environmental moni
toring, advanced notifications, remote control capabilities, and automated responses for graceful shutdown. These tools are designed to satisfy the needs of ever-evolving digital infrastructure.
What Partner Upskilling Programs do you run to help upskill your partners?
We help our partners to grow business by con stant learning and development through product trainings, technical sessions and business strategy guidance. We firmly believe in the development of the partner ecosystem as it leads great business partnerships.
How does your channel strategy align with today’s market trends?
We have new product launches and product upgrades planned in 2022 in 1PH & 3PH UPS which will help channels boost their sales.
To access more info login to: https://www.smechannels.com
DEBASISH BANERJI DIRECTOR, SALES AND SERVICE, EATON ELECTRICAL SECTOR, INDIA
“WE HAVE DESIGNED HARDWARE AND SOFTWARE PRODUCTS FOR DECADES, ALONG WITH PROVIDING INSTALLATION AND MAINTENANCE SERVICES, POSITIONING OURSELVES AS THE MOST CAPABLE CYBERSECURITY PROVIDER FOR ELECTRICAL INFRASTRUCTURE AND BUILDING SYSTEMS.”
INTERVIEW SME CHANNELS OCTOBER 2022 29
ACCELERATING THE PACE OF AI
The Artificial Intelligence (AI) market in India is all set to witness a surge of 20% over the next five years. India is also among the top three talent markets, producing 16% of the world’s AI talent pool, agrees a joint study conducted by Microsoft and the Internet and Mobile Association of India (IAMAI).
AI no longer remains a fringe technology for Indian companies. It has come to the mainstream. The AI market is expected to grow at the secondfastest rate of 20% among major economies over the coming five years, next only to China.
Although Data quality, scale infrastructure and sensitivity or risks still pose as major obstacles for enterprises for large-scale AI adoption, AI seems to have come of age in the country. As per the joint study we discussed earlier, AI or ML has been able to found extensive penetrations across enterprises, with nearly 80% of enterprises found to have at least one AI model in their production. While large enterprises have adopted AI at a much higher rate. Nearly half of the large enterprises are planning to build their own AI models in the next three years.
Currently, India produces more talents than it consumes. However, enterprises still lack domainspecific expertise, data visualization or analysis talents and data engineers. In the summer of 2018, NITI Aayog came out with an AI strategy for the country. With this, India became one of the first countries to inch towards using artificial intel ligence to address inclusion and social challenges. The adoption of AI across all relevant sectors and value chains is also progressing at a faster pace.
At this backdrop, we have embarked upon scal ing the latest state of AI adoption, the promise this next-gen tech has brought to the table and the opportunities it has created for the channel business.
To take a sneak peek into the AI landscape, we had caught up with Dr. Shreeram Iyer, Chairman
and Group Chief Executive Officer, Prisma AI. A Visionary and expert, Iyer has been instrumental in developing and executing business strategies to achieve short- and long-term goals of Prisma AI. Under his stewardship, Prisma has successfully maintained positive and trust-based relations with its business partners, shareholders, and authorities. He has been responsible in oversee ing the company's business operations, financial performance, investments, and ventures.

In a special interaction with SME Channels, Dr. Shreeram Iyer, Chairman and Group Chief Exec utive Officer, Prisma AI, reveals his organization’s approach to leverage this highly promising tech nology, opportunities created by the AI market for channel growth, his forecasts for the AI industry, the major growth drivers and his vision and plans for the channel community. Edited excerpts…
Please brief us about the AI Solutions offered by your company.
Prisma AI offers a variety of Visual AI-based solu tions, each utilizing computer vision to assist in various tasks, such as surveillance, access, analyt ics, and more. These solutions include products such as object detection, body behavioral analysis, facial recognition, video recognition, sentiment analysis and more. Each of these products have various applications such as Access surveillance, Illegal object detection, Theft detection, and many more.
All our AI products and solutions can be adapted as client’s requirements.
How is your company leveraging AI - the Next-Gen Tech - to address business pains?
Prisma AI believes that Artificial Intelligence is the next step to technological evolution and build ing an empowered society that makes full use of the potential AI provides. We leverage AI and computer vision to build Visual-AI based prod
ucts and solutions using our patented computer vision platform Gryphos, to develop and train state-of-the-art solutions for almost every techno logical hurdle. Prisma AI leverages AI to provide several core products such as object detection, body behavioral analysis, facial recognition, video recognition and sentiment analysis. We empower traditional technology like manual surveillance, entry gates in various industries, and more, with AI-powered solutions which automate their functions, ensuring less manpower is used and diverted to more important tasks.
For instance, one of the leading kitchens in an airline industry approached Prisma AI towards the late 2019 to help them with kitchen surveil lance, wherein, they could monitor the body behavior of staff to ensure all standard procedures were followed. Prisma AI’s technology, Gryphos acted as a vigilance for quality control in this case.
We also developed an effective Automatic Number Plate Recognition (ANPR) system for one of our clients to detect the license plates of any speeding vehicles not following the road or traffic safety rules.
Prisma AI uses the already existing CCTV and camera infrastructure, creating ease of use and functionality, thus saving revenues. All of Prisma AI’s products and solutions can be customized uniquely for each of our clients, are easy and fast to deploy, making them unique and the first
Offering a variety of Visual AI-based solutions, which utilizes computer vision to assist in various tasks, such as surveillance, access, analytics, and more, Prisma AI braces to write a new chapter
SME CHANNELS OCTOBER 2022 30 NEXT-GEN TECH
DR. SHREERAM IYER CHAIRMAN AND GROUP CHIEF EXECUTIVE OFFICER, PRISMA AI
once seemed far-fetched.
Efficiency: A lot of complex tasks are already being done more efficiently by AI than traditional systems and it’s only going to be onwards and upwards from here.
Personalization: Adapting the AI solutions as per the industry and client requirements is crucial and is a key element when it comes to growth.
Prisma AI focuses on these 3 major drivers of growth while developing and distributing our AI solutions. We’re constantly focused on innovat ing, delivering with efficiency and every solution provided by us is tailored according to the clients’ needs.
How do you ensure partner profitability in this emerging technology vertical?
Partner profitability is an integral part of the AI solutions market. Prisma AI offers varied pricing models to ensure that every partner investing into these solutions also gain maximum out of it.
The pricing model ranges from providing a percentage of amount specifically for the partners, decided as per their involvement in a project to a cost plus pricing model to allow the partners to markup their price.
their initial few pitches to the clients to assist them wherever needed.
Continuous Updates – Updates are constantly shared with the partners through Data Manage ment System and emails.
Which industry vertical is currently witnessing the largest application of your solutions?
Currently, the aviation and transport industry is benefitting the most from our solutions, namely our object detection and body behavioral analysis products which assist airport staff and security in detecting and tracking down lost and abandoned baggage and returning them to their owners, as well as keeping an eye on suspicious individuals, or individuals in need of assistance for moving around the airport.
How do you look at the future of AI in India? How is AI going to mold the tech landscape in the days ahead?
choice of customers for visual AI solutions.
Prisma AI is continuing to innovate and come up with more solutions for emerging market requirements.
What key mega trends do you foresee in the AI Solutions market?
As Artificial Intelligence continues to gain trac tion and grow, many mega trends can be foreseen in the near future for the AI Solutions market:
• Greater emphasis will be placed on automa tion and machines for completing tasks that require manpower
• AI-enabled point solutions and use-casebased solutions will start gaining mainstream adoption.
• The focus on multimodal AI will increase to unlock data potential.
• The focus on ethical AI as a core implementa tion aspect will increase
What are the major drivers of growth in the AI Solutions market?
AI solutions have a huge potential for growth in the market. A number of major industries are already utilizing it to better their functions, and the major drivers that contribute to this better ment are:
Innovation: AI Experts are constantly innovat ing and introducing solutions to problems that
What is the greatest strength of your products? Is it Scalability, Friendly User Interface, flexible development environments, or flexible pricing structure?
All of Prisma AI’s products are developed using our in-house patented platform, Gryphos which allows scalability and flexibility to each prod uct and solution to be trained and improved as required or adapted to any client’s requirements easily. We possess a library list of APIs which gives our clients the flexibility to choose their desired applications as they see fit and allowing us to better tailor our offerings to their needs.
What sort of Partner Upskilling do you impart to effectively market your solutions?
The exponential growth in AI definitely demands upskilling of partners. Prisma AI imparts the same through:
Data Management System – Prisma AI has a live Data Management System where we update the most recent documents, videos, etc. for the partners to go through and be in touch with the latest advancements.
KT Sessions – Prisma AI organizes Knowledge Transfer sessions periodically for training the partners.
Help during pitch presentations – Experts from Prisma AI accompany the partners during
AI in India is already gaining increasing awareness amongst the end users, as they now know more about the benefits and potential of artificial intel ligence in upgrading infrastructure and present technologies. Artificial Intelligence has the poten tial to grow indefinitely in the coming years. Com puters are already excelling in terms of performing repetitive and complex calculation tasks better than humans. However, our objective is to make every camera intelligent and elevate the scope of AI and make it capable enough to recognize, perceive, and make decisions like a human brain. If even 50% of this is achieved, we would see a surge in growth across industries. We can already see multiple industries recognize and accept the applicability of AI and it is only going to get bigger and better with time. We already have self-driving cars, which are only reserved for certain classes of people. Eventually, we would have different types of self-driving cars that would be more widely accessible to the population.
We can expect accurate automation of tradi tional human workflows, leading to machinery eventually supplementing manual labor. In the near future, we could get to see actual humanoid robots, smart technology that instantly scans a person’s face for their details to enable seamless and instantaneous payments, alongside a face-asa-ticket to enter public spaces.
“PRISMA AI BELIEVES THAT ARTIFICIAL INTELLIGENCE IS THE NEXT STEP TO TECHNOLOGICAL EVOLUTION AND BUILDING AN EMPOWERED SOCIETY THAT MAKES FULL USE OF THE POTENTIAL AI PROVIDES.”
SME CHANNELS OCTOBER 2022 31 NEXT-GEN TECH
KEVIN REED CISO, Acronis

PROFILE
Experienced Chief Information Security Officer with a demonstrated history of working in the computer software industry. I work with tech companies focusing on the real-life risk mitigation instead of checkbox compliance.
Experienced with DevSecOps and Alige approaches. Strong information technology professional with a Master of Business Administration (MBA) from Kingston University.
IN CYBERATTACKS, SMBS FACE AN EXISTENTIAL THREAT
Cyberthreats, and ransomware in particular, have generated considerable news coverage this year. The attack on the Colonial Pipeline resulted in wide spread gasoline shortages and mass transit disrup tions, while a strike against JBS disrupted supply chains worldwide.
We are not only seeing troubling new develop ments in the threat landscape from the first half of the year: It’s also clear that SMBs are now at signifi cant risk — and service providers must react.
SMBs face greater risks than ever before SMBs may feel safe in the supposition that they’re “too small to target.” In reality, they’re increasingly vulnerable due to increases in attack automation and supply-chain attacks against their IT service provid ers. Cybercriminals are eagerly targeting managed service providers (MSPs) in a bid to compromise scores of their clients at once. For most SMBs, just one such incident could sound their death knell.
During the first half of 2021, four out of five orga nizations experienced a cybersecurity breach that originated from a vulnerability in their third-party vendor ecosystem. During that same period, the average cost of a data breach rose to around $3.56 million, and the average ransomware payment topped $100,000 — a 33% jump. While these figures would be a significant financial hit for any company, they’re simply fatal for the average small or medium business.
Here are a few more of our key findings from the Acronis Cyberthreats Report Mid-year 2021:
• Phishing attacks are rampant. The use of social engineering techniques to trick unwary users into clicking malicious email attachments or links rose 62% from Q1 to Q2. That spike is of particular con cern since 94% of malware is delivered by email.
• Data exfiltration continues to increase. Last year, more than 1,300 ransomware victims had their data publicly leaked after an attack. Cybercriminals are looking to maximize their financial gain, and these tactics increase the pressure on victims to pay up. During the first half of 2021, more than 1,100 data leaks have already been published — at this rate, we’ll be looking at a year-end increase of 70% over 2020.
• Remote workers continue to be a prime target. The COVID-19 pandemic drove a major shift to remote-first work that continues today. Two-thirds of remote workers now use work devices for per sonal tasks and use personal home devices for busi ness activities — and attackers have taken note.
SMBs turn to IT service providers because they lack the resources or technical expertise needed to counter today’s rapidly evolving cyberthreats. As an MSP, your clients depend on you not only to turn to solutions that effectively defend against cuttingedge attacks, but also to stay abreast of the latest developments in the cyberthreat landscape and react accordingly.
GUEST ARTICLE SME CHANNELS OCTOBER 2022 32
SMBs are increasingly vulnerable due to increases in attack automation and supply-chain attacks against their IT service providers
WEAK CYBER RESILIENCY: BLOCKING THE ROAD TO PROGRESS IN THE DATA ERA
RIPU BAJWA
Director and General Manager, Data Protection Solutions Dell Technologies India
PROFILE
As Director & General Manager, Data Protection Solutions, Dell Technologies, India, Ripu Bajwa has been associated with the organization for more than 14 years. Ripu is responsible for the data protection solution business in India.

In a career spanning for more than a decade, Ripu has been associated with leading technology organizations like HCL, IBM, and Microsoft, prior to his association with Dell Technologies.
While India Inc. has progressed exponentially with digital transformation, securing mission-critical data remains an area where business leaders lack confidence. Data management cannot be an after thought in the data era especially as cyber-threats and ransomwares become increasingly sophisti cated. The first step for drawing a future ready cyber resiliency action plan is recognising the gaps exis tent in the organisation.
Cyber resilience involves a strategy to mitigate the impacts of cyberattacks and resume operations after systems or data have been compromised. Cyber resiliency requires addressing the areas of the business where a threat or incident can do the most damage to critical data.
While cybersecurity solutions are focused on protecting systems and networks from malicious attacks, cyber resiliency helps ensure that the damage from attacks is minimised.
Ransomware threats have made over a 13% jump over the last year globally with an average of over 11 million attacks everyday. India continues to be one of the countries most at risk with over 200,000 attacks recorded every day by the Indian Computer Emergency Response Team (CERT-In) in early 2022. Recent reports share that there have been over 18 million cyberattacks in India in just the first quarter of 2022, out of which over 30,000 were tech support scams.
It is clear that cyber attackers recognise the value data has over businesses. The impact could be worse if the attackers hold a business at ransom, use the data for corporate espionage or sell business data for commercials. Hence it is crucial to work on areas where a business might be lacking in a strong IT action-plan. Some of the areas where businesses will need to draw their attention to, are:
1. Security is far too siloed – Cybersecurity has gotten defined within the confines of different development teams each building to their narrow
functional lens, so it doesn’t play well across an organisation. Security has to be purpose-built to detect and mitigate threats, aligned with overall business objectives.
2. Digitising without security infrastructure - As organisations hasten their pace of digital trans formation, many of them make rapid technology changes without considering the security implica tions. In this data era, security transformation must accompany digital transformation.
3. Afterthought on security integrationSecurity applications have long been bolted-on and some have been an afterthought when creating new technologies. Often, security integration is not con sidered until after applications and processes have been developed, and then the framework is adapted to fit over existing operations as best it can.
4. Starting business IT roadmap with miscon ceptions around security - There is a misconcep tion that only certain sized businesses or industries are targeted for cyber-attacks. Organisations over look their security planning and only focus on preventing an attack. Organisations must instead operate with the assumption that an attack is just a matter of time, in spite of the best defences possible, and have a rapid recovery strategy in place.
As Indian businesses progress in the era of digital transformation, it will be crucial to assess the cyberresilience framework in their organisation. A cyber recovery solution solves these challenges by provid ing analytics and forensics to quickly determine the last known good, trusted copies to recover. The most effective cyber resiliency strategies involve using best practices involved in protecting data. This includes ensuring the right level of access controls, immutable copies of data, anti-virus and anti-mal ware.
GUEST ARTICLE SME CHANNELS OCTOBER 2022 33
The most effective cyber resiliency strategies consists of best practices involved in protecting data, ensuring the right level of access controls, immutable copies of data, anti-virus and anti-malware
ARUN KUMAR J REGIONAL DIRECTOR - SALES MANAGEENGINE
EFFECTING A SECURE CLOUD
As October is being celebrated as International Cybersecurity Aware ness Month, there’s improved col laboration between government and private industry to raise awareness about digital security and empower everyone to protect their personal data from digital forms of crime.
The month of October is dedicated to creating resources and communications for organizations to talk to their employees and customers about staying safe online. The Cybersecurity Awareness Month reminds us all that there are viable ways
BY SANJAY MOHAPATRA sanjay@smechannels.com
to keep our data secure and protected. Sticking to certain security best practices can make a huge difference to our data security.
As part of our effort to raise awareness and explore current state of the threat landscape, we have started a series of interactions with the who’s who of Indian Cybersecurity Industry.
In a special interaction with SME Channels, Ram Vaidyanathan, Cybersecurity Evangelist, ManageEngine and Arun Kumar J, Regional Director - Sales, ManageEngine, reveal their orga nization’s approach to cybersecurity; ManageEn gine’s key offerings in this space, changing security scape; opportunities and challenges, opportunities for channel growth; their forecasts for the indus try; and their company’s vision and plans for the channel community. Edited excerpts…
As a frontline cybersecurity player, how has your company been leveraging this uptick in demand?
Ram Vaidyanathan:
• Zoho’s wide range of products are designed to address the surge in demand for a secure cloud environment that enables hybrid or remote work. ManageEngine, the IT management division of Zoho, offers software solutions that ensure enter prises stay secure and continue to offer satisfying user experiences.
• Log360, ManageEngine’s unified security information and event management solution, recently introduced features like anomaly mod elling and peer group analysis to keep track of suspicious user behavior. It’s built-in security orchestration, automation, and response (SOAR) capabilities make Log360 the right choice for security operations center (SOC) teams responsi ble for the security of both on-premises and cloud infrastructures.
• One of the core advantages of SOAR is automated incident response, which drastically reduces the mean time to respond, giving SOC teams time to address other important tasks or incidents.
• ManageEngine facilitates integration and deep
linking between all its products by displaying them in a single dashboard, creating a seamless user experience.
Choosing the correct solution from a crowd of solutions is like searching for a needle in a haystack. So, what sort of product differentiation do you bring to the table?
Ram Vaidyanathan:
What makes Log360 unique is its ability to bring multiple security capabilities into one console, making it easy for analysts to access information conveniently and make policy decisions.
The preferred choice for enterprise security includes monitoring changes to your AD environ ment in real time along with:
• Automating response workflows for faster incident response.
• Managing incidents for efficient resolution.
• Collecting and parsing logs from various sources.
• Conducting log forensics from the collected logs.
• Leveraging user behaviour and analytics to detect anomalous activity.
• Using threat intelligence to identify new types of threats.
Apart from this, Log360 also offers seam less integration with popular ticketing tools like ManageEngine ServiceDesk Plus to help you effectively manage security incidents.
What key cybersecurity mega trends do you foresee in the security market?
Ram Vaidyanathan: Technology is ever evolving and, as a result, there’s a parallel shift in cybersecurity trends. Here are seven trends we predict:

1. Ransomware, including Ransomware as a Service, and cloud ransomware
2. Internet of Things threats—especially Inter net of Medical Things threats
3. Supply chain attacks
4. Attacks against operational technology
ManageEngine offers an integrated suite of IT infrastructure management solutions, both on-premises and cloud-based
“WE REALIGNED OUR STRATEGIES TO HELP ORGANISATIONS ADAPT TO THE REMOTE WORK MODEL, ALLOWING ACCESS TO DATA ACROSS DIFFERENT LOCATIONS WITHOUT COMPROMISING ON SECURITY.”
SME CHANNELS OCTOBER 2022 34 PARTNER CORNER
How is your channel strategy aligning with the current market trends?
Arun Kumar J:
We have seen a huge increase in cloud adoption post pandemic. Before the pandemic, cloud adop tion and digital transformation existed, but they weren’t a high priority for organisations. However, after the pandemic, with the remote work model resulting in employees being distributed across multiple locations and the seamless transfer of data required to ensure business continuity, moving to the cloud essentially became a top pri ority overnight. Since cloud technology enables seamless transfer of data across multiple locations, employees could access data and maintain busi ness operations.
ManageEngine offers an integrated suite of IT infrastructure management solutions, both onpremises and cloud-based. We already had these product offerings before the pandemic; however, we realigned our strategies to focus on the solu tions that could help organisations adapt to the remote work model. We had specific solutions for remote work operations that ensured employees could access data across different locations with out compromising on security. We predict these trends in the IT solutions and services market:
• The hybrid model will continue even after the pandemic, as most organisations will be adopting a hybrid work model.
• Cloud adoption will continue increasing in
the coming years.
• IT teams will prioritise ensuring data is simul taneously secure and accessible to offer a seamless customer experience, since data will be accessed on multiple platforms across various locations.
• Security will continue gaining importance because of the evolving threat landscape. Organ isations will invest in tools like endpoint manage ment and security, privileged access management, remote access, and Zero Trust.
How do you upskill your partner ecosys tem to provide a more ebullient security service?
Arun Kumar J: We invest a lot in training our partners and con duct regular training programs on the latest prod uct enhancements and market trends. Along with the product training programs, we also ensure all our partners are certified on our products. While most organisations work with a channel ecosystem to acquire customers and drive growth, it’s important to structure the partner program with defined objectives, like offering consulting and delivery services, etc. This, to a great extent, helps both organizations and the channel ecosystem scale the business and embrace a win-win partnership.

When it comes to selling a product, customer experience weighs over the rest. So, what sort of pre-sales and post-sales services do you offer?
Ram Vaidyanathan:
Our goal is to understand our prospects’ business requirements, their current business models and workflows, and their pain points. We also aim
to educate them about our products, including features and services, to help them make the best buying decisions for their organisation.
We offer:
• Customized demos to help them understand our products.
• Webinars elaborating on the features of our products.
• Workshops to demonstrate how to use the products.
• 24/7 chat support to address their queries. We make sure to guide and support the customer every step of the way. We are dedicated to accom plishing our customers’ goals and ensuring a smooth post-sales experience.
We offer:
• 24/5 customer support via email and phone.
• We aim to respond within three hours of rais ing a service question or request during business hours.
• Free one-on-one demos, training, and implementation.
Are you planning any major investment towards channel expansion or in terms of expanding your head count in India?
Arun Kumar J:
We are growing at 50% both on our revenue and customer count year over year in the India market and are looking to double those numbers by 2023. We have already begun hiring and are expanding locally across all major metros. We are moving towards building value-added partners on the channel strategy and not just being transactional, as customers today expect partners to not only implement the product offerings but also to provide domain intelligence by solving their busi ness challenges. Our investments are focused on enabling partners to deliver value to customers based on their business needs and market trends.
What would be your growth outlook for the current year?
Ram Vaidyanathan: Our objective is to help customers investigate, detect, and respond to threats in a timely fashion. To achieve this, we need to stay relevant in this era of digital transformation and sophisticated attacks. We prioritize investing in superior prod uct design and contextual integrations so that our customers can accelerate their own digital trans formation while securing their hybrid networks. We will continue to add newer capabilities for the C-suite, such as threat hunting and metrics-based dashboards. Currently, our main markets are the United States and the United Kingdom, but we are fast expanding our business in other markets across the globe.
RAM VAIDYANATHAN CYBERSECURITY EVANGELIST MANAGEENGINE
“ZOHO’S WIDE RANGE OF PRODUCTS ARE DESIGNED TO ADDRESS THE SURGE IN DEMAND FOR A SECURE CLOUD ENVIRONMENT THAT ENABLES HYBRID OR REMOTE WORK.”
5. Attacks against mobile devices 6. Adoption of Zero Trust network architectures 7. Adoption of security solutions with SOAR capabilities to automate detection and response
SME CHANNELS OCTOBER 2022 35 PARTNER CORNER
A HOLISTIC HYBRID NETWORKS APPROACH TO SECURING
Tenable offers customers a contextual view of all assets and
associated software vulnerabilities, configuration vulnerabilities and entitlement vulnerabilities, whether on-premises or in the cloud
As October is being celebrated as Interna tional Cybersecurity Awareness Month, there’s improved collaboration between government and private industry to raise awareness about digital security and empower everyone to protect their personal data from digital forms of crime.
The month of October is dedicated to creating resources and communications for organizations to talk to their employees and customers about staying safe online. The Cybersecurity Awareness Month reminds us all that there are viable ways to keep our data secure and protected. Sticking to certain security best practices can make a huge difference to our data security.
As part of our effort to raise awareness and explore current state of the threat landscape, we have started a series of interactions with the who’s who of Indian Cybersecurity Industry.
In a special interaction with SME Channels, Glen Pendley, CTO, Tenable, reveals his organi zation’s approach to cybersecurity; Tenable’s key offerings in this space, changing security scape; opportunities and challenges for channel growth, his forecasts for the industry; and his company’s vision and plans for the channel community. Edited excerpts…
As a frontline cybersecurity player, how has Tenable leveraged the uptick in demand for security solutions?

We recognize that today’s organizations are oper ating on distributed, hybrid networks that stretch across many data centres in multiple geolocations, cloud-based infrastructures, applications, virtu
alized platforms and services and much more. There are more types of technologies, assets and services in every organization and each and every one of them is vulnerable to some sort of attack or threat beyond a simple, exploitable vulnerability caused by a missing patch.
It is for this reason that we recently launched Tenable One an Exposure Management Platform to help organizations holistically look at the entire attack surface and operationalizes preventive security practices.
Choosing the correct solution from a crowd of solutions is like searching for a needle in a haystack. So, what sort of product differentia tion do you bring to the table?
As an exposure management platform, Tenable One provides customers with data about con figuration issues, vulnerabilities and attack paths across a spectrum of assets and technologies — including identity solutions (e.g., Active Direc tory); cloud configurations and deployments; and web applications. This analytics not only gives organizations a complete picture of their environ ment and its weaknesses but maps how a breach could happen, providing actionable intelligence to tangibly reduce risk.
As of today, no other company is able to pro vide the breadth of coverage, context and action able reporting that Tenable can.
What key cybersecurity mega trends do you foresee in the security market?
We are going to see more and more organizations shift from traditional vulnerability management to exposure management. Traditional vulner ability management focuses on the act of enu merating flaws in software that could be exploited (CVEs). Exposure management extends beyond this where exposures of any type across any asset can be identified, put into proper business con text, prioritized for remediation, and drive the engine that allows organizations to protect them selves from compromise, reduce overall risk and shrink the potential number of targets an attacker has anywhere on their attack surface.
To access more info login to: https://www.smechannels.com
GLEN
PENDLEY CTO, TENABLE
“AS AN EXPOSURE MANAGEMENT PLATFORM, TENABLE ONE PROVIDES CUSTOMERS WITH DATA ABOUT CONFIGURATION ISSUES, VULNERABILITIES AND ATTACK PATHS ACROSS A SPECTRUM OF ASSETS AND TECHNOLOGIES.”
SME CHAT SME CHANNELS OCTOBER 2022 36
THE
HOLLYLAND MARS 4K WIRELESS TRANSMISSION SYSTEM
BY MANAS RANJAN info@smechannels.com
HOLLYLAND MARS 4K UHD WIRELESS VIDEO ttransmission system combines high performance and upgraded user experience at an affordable price.
The Mars 4K effectively improves the user experi ence by requiring fewer devices, more simplified deployment, and higher flexibility. The device from Hollyland makes professional shooting accessible everywhere and everyone by higher integration and lighter weight in product develop ment and design.


Hollyland’s Mars 4K wireless video transmission system supports 4K UHD video transmission at 30fps for the discerning videographer looking for high-resolution production capability. Its HDMI supports up to 3840x2160 30p, and is also com patible with 1080p and 720p formats. Mars 4K also supports decimal-point frame rates input from SDI such as 23.98, 29.97, 59.94, and output from the receiver’s HDMI and SDI out port. Its upgraded dual-core codec chip is capable of a data
rate ranging from 8 Mbps to 20 Mbps, with 12 Mbps as the default. This new product offers 450ft (150m) LOS range, and latency of 0.06s.
The Mars 4K features superior corrosion and wear resistance for outstanding durability. The well-thought-out design optimises oper ational functionality for fast configurations with disassembly-free, bullet-styled anten nas attached. Power supply options include DC, batteries and USB-C chargers.
PRICING AND AVAILABILITY:
THE MARS 4K IS PRICED AT AN MRP OF INR 48,000 AND IS AVAILABLE THROUGH CINESCOPE , ITS LOCAL DISTRIBUTOR IN INDIA.
PRICING AND AVAILABILITY: The Mars 4K is priced at an MRP of INR 45,000 and is available
distributor Cinescope.
Hollyland’s
MARS M1 IS AN ALL-IN-ONE TRANS MITTER, RECEIVER, AND LOW-LATENCY MONITOR SOLUTION. THE BRIGHT 5.5INCH TOUCH LCD SCREEN SUPPORTS REC. 709 COLOR GAMUT, PROFESSIONAL COLOR CALIBRATION, COLOR TEM PERATURE ADJUSTMENT, AND COMES WITH FIVE 3D-LUT PRESET FILES. THIS NEW PRODUCT OFFERS 450FT (150M) LOS RANGE, AND LATENCY OF 0.08S. IT FEATURES A COLOR LCD AND A NEW USER-FRIENDLY UI DESIGN. IN ADDITION, THE MARS M1 SUPPORTS 4K/30FPS HDMI INPUT AND OUTPUT, SDI INPUT, AND DC POWER OUT FOR EXTER NAL DEVICES, PLUS A USB-C INTERFACE FOR EXPANDED CONNECTIVITY AND COMPATIBILITY. AUXILIARY FUNCTIONS INCLUDE 4X ZOOM, FOCUS ASSIST, EXPOSURE ASSIST, AND WAVEFORM DISPLAY. THE MARS M1 CAN BE USED WITH HOLLYLAND’S MARS 4K, MARS 300 PRO, MARS 400S PRO, AND THE FUTURE MARS PRO/4K SERIES. REVIEW MARS M1 WIRELESS TRANSCEIVING MONITOR
through
local
37 PRODUCT SME CHANNELS OCTOBER 2022
AORUS TACHYON
GIGABYTE’s Z690 AORUS TACHYON motherboard runs on the latest 12th generation Intel Core i9 12900K processor. The device has LN2 liquid nitrogen heat dissipation and has passed the CPU-Z Validator test at 8 GHz super-high frequency, using 0x13 microcode of Intel processors tested by the latest rev.1.98 CPU-Z.

Featuring up to 20+1+2 phases digital power VRM design with each phase holding up to 105 amps and an improved Fins-Array III heatsink design, GIGABYTE’s Z690 AORUS lineup is geared with the best power design. It has good thermal management to unleash better performance and opti mized overclocking ability on the new generation multi-core K series Intel Core processors. The PCIe 5.0 PCBs, slots, and components are also imple mented in GIGABYTE’s Z690 AORUS motherboards for enhanced perfor mance and stability. The SMD memory slots with metal shielding mask for anti- interference and the BIOS setting of DDR5 memory overclocking offer more stable signals to memory.
GIGABYTE Z690 AORUS motherboards offer feature-rich I/O with an integrated I/O shield as well as the newest Thermal Guard III design, Smart Fan 6 and much more. Performance, power management, thermals, audio, GIGABYTE Z690 AORUS motherboards check all the boxes for users seek ing to take their computing firepower to the next level.
It has advanced layout design, and remarkable memory overclocking. It introduces DDR5 memory starting from Intel Z690 consumer mother boards with downward support of DDR4. GIGABYTE Z690 AORUS moth erboards offer a diverse range of enticing features to be a compelling choice for high-end computing and gaming platform.
SAMSUNG
SAMSUNG GALAXY BOOK 2 PRO 360
The Galaxy Book2 Series of laptops are designed to be double-duty devices and can help accomplish professional tasks smoothly and combine the necessary screen size and graphics for entertainment needs.
The Samsung Galaxy Book 2 Pro 360 is a slim and light 13.3-inch 2-in-1 laptop. Weighing little over 1kg, it’s easy to carry. The device is based on Intel’s 12th Gen CPUs with heterogenous cores, and boasts of impressive battery life. It also packs a stylus as well as a fast charger in the box.

Design-wise, it’s modern and slick. However, the laptop turns rather warm even when it isn’t stressed. Besides, there are a few ergonomic issues which renders it difficult to use as a tablet. There are also a huge amount of preloaded software. Some of the software has to do with integrating func tionality with Samsung’s smartphones, tablets, and wearables.
We recommend that buyers should try one themselves at a shop before buying one.
Key Features:
• Display: 33.78 cms (13.3 inches), FHD OLED
• Memory: 16GB LPDDR5 RAM, 512GB SSD ROM
• Processor: Intel Core i5 12th Generation
• OS: Windows 11 Home
• Graphics: Intel Iris Xe
• Included Software: MS Office Home & Student 2021
• Warranty: 1 Year Onsite
n Price: The Samsung Galaxy Book 2 Pro 360 13.3 has a starting price of 99,680.
can deter intruders and alert users of a detection.

D-LINK DCS-8302LH
HD OUTDOOR WI-FI
D-Link’s new DCS-8302LH Full HD Outdoor Wi-Fi Camera features AI edge-based person detection. This intelligent camera can identify human motion, reducing false alarms, so that users receive more relevant detection notifica tions. The DCS-8302LH offers unlimited sur veillance in Full HD 1080p clarity. It can capture things even at night.
With its built-in microphone and speaker for two-way audio and siren functionality, the camera
The DCS-8302LH is weather resistant for outdoor installation and also suitable for indoor installation, with an included stand as well as sup port for mounting via screws or cable-ties. Wi-Fi support and a wide operating temperature toler ance provide installation flexibility.
In addition, the DCS-8302LH has a built-in Ethernet port for the option of wired connection. It supports the Google Assistant and Amazon Alexa voice commands, IPv6 for future network compatibility, and ONVIF-Profile S to record video to a NAS or NVR. The DCS-8302LH pro vides the latest Wi-Fi security for more protection with support for WPA3. Simple, rapid Bluetooth setup, as well as remote viewing and management with the free mydlink app offer extra convenience for users.
n Availability: The DCS-8302LH is now available for purchase from D-Link resell ers and distributors
AORUS GIGABYTE Z690
FULL
CAMERA D-LINK
SME CHANNELS OCTOBER 2022 38 PRODUCTPRODUCT










25TH NOVEMBER 2022 EROS HOTEL, NEW DELHI HONOURING 100 TOP CHANNEL PARTNERS IN INDIA 2 DAY EVENT NETWORK WITH MOVERS AND SHAKERS OF IT CHANNEL ECOSYSTEM PARTICIPATE AND GROW YOUR CHANNEL BUSINESS MOST PREMIUM CHANNEL EVENT CHANNEL ACCELERATOR AWARDS 2022 12th
























 BY SANJAY MOHAPATRA sanjay@smechannels.com
BY SANJAY MOHAPATRA sanjay@smechannels.com





































