

CHANGING THE

WITH
GATES
meetthe team
Editors-in-Chief: Ein Hong & Sahana Moogi

Connect with Us!

Meet the People behind this Issue
Noted Contributors from Around the World LITERATURE
Directors: Ryan Liu, Aminah Hedges, Sindhu Saggeri
Matías Mogetta Martina Cisterna Liz Lubelczyk
Penny McNeill
Thivina Edirisinghe
Ramitha Ramanan Raymond Wong Pedro Marin Alamino Pedro Marin Alamino Larissa Terto Alvim Theo Leão Larrieux Bruno Fernandes Iorio David Moeller Sztajnbok Miguel Bernáth Liao
Enzo Pereira da Cunha Carolina Yumi Farré Oura Rawan Yosef
Aryan Tiwari Ayaan Shaikh
Devansh Shah Liam Nguyen Dominik Eric Huang Miguel Balingit Liam Brady Alex Kim Emily Seoyoung KIm Hyun Seomun Wissam Al Ghabra Mohammed Yasser Akkad
Eman Omar Alhendi Dana Mershed Ritta Shahada
Aribah Hoque
Ranim Hammami Alexander Ahmed Haj Ahmed
Joanne Ngo Liam Nguyen Chau Dang Amelia Hoyos Mahirah Mohd Norazinan Kaitlyn Butcher
Ayaan Shaikh Dana Choi Gina Choi Rosie Chen Abdullah Albaitam Orabi Salman Stephanie Samame Maryam Ayadi
GRAPHICDESIGN&LAYOUT
Directors: Akshita Ponnuru, Rhea Jain, Vivek Atmuri, Serena Gandhi
Ein Hong Sahana Moogi Vivek Atmuri Rhea Jain
Akshita Ponnuru Moe Myint Tha
Tyler Louie Hayden McGowan Saurav Gandhi Jessica Wang
Javeria Ahmed Moe Myint Tha
Nabiha Jawad Victoria Israel
David Moeller Sztajnbok Hasitha Dangeti
Aarushi Shah Serena Gandhi
PHOTOGRAPHY&video
Directors: Sahana Moogi, Jessica Wang, Serena Gandhi
Sahana Moogi Jessica Wang
Sam Poder Artyom Sobolev
Morozov Vitaly Javeria Ahmed
ILLUSTRATIONS
Director: Aleena Bosky
Aleena Bosky Ynna Buriel
Allison Nguyen Kaitlyn Liu
Aakash Vetcha Serena Gandhi
REGIONALDIRECTORS
Darine Hamdoun Soha Ezzi Ahmed Haj Ahmed Qing Zhu Joshua Bernard David Sztajnbok
Selene Chiang Yihyun Nam Wei Rayden
Pheemapotwasu Kantakom Emmanuel Haankwenda Vimarsh Shah
OUTREACHTEAM
Victoria Israel Rawan Yosef Jang Choi Cindy Huang Magnus Muhall Rami Mhanna
Directors: Aarushi Shah, Hasitha Dangeti, Kaitlyn Butcher
Aarushi Shah Risha Koparde
Hasitha Dangeti Kaitlyn Butcher
Morozov Vitaly Javeria Ahmed
YESPCOMMITTEE
Director: Stephanie Samame
Stephanie Samame Wes Parkin Ahmed Haj Ahmed Serena Gandhi Niharika Uppalapati Koebe Nay
Isum Malawaraarachchi Chanul Pathirana Joanne Ngo Sooham Chauhan
Sahana Moogi Dana Marshed Jonathan Santosa Finn Owen Travis Leung Magnus Mulhall Cindy Huang Raymond Wong Enzo Pereira da Cunha Kaitlyn Butcher
Ankit Behera David Moeller Sztajnbok Ein Hong Sanjay Ravichandran Qi Qing Zhu Ritta Shahada Hayden McGowan Anvee Sharma Kendall Wilson
sponsors

community Partners








TECHNOLOGY TRANSFORMS
DearReader, trans·for·ma·tion(noun) athoroughordramaticchangeinformor appearance.
Backintheday,ifyouwantedtolearnthe definitionof“transformation”,youneededtolookit upinadictionary manyofushaveprobably heardthisfromourparentsorexperiencedit ourselves.Yearsofincredibletechnological progressadvancedustothefirstsearchengines toindexthecontentonwebpages,makingevery wordandphrasesearchable Thencamethe adventofhigh speedinternet,allowingforamuch highervolumeofdatatobetransferredatfaster speeds Now,wedon’tevenneedtogothroughthe hassleofmanuallytypingoutasearchforthe definition wecanjustaskAlexa.Hereitis:
laptops,scrollthroughsocialmedia,attend meetingsthroughvideocalls,andunwindaftera longdaybywatchingsomeTVorYouTube.Indeed, ifwecomparetheliveswelivedonehundredyears agototheliveswearelivingnow,itiscleartosee justhowessentialtechnologyisinoursociety today

Thisissueisacontinuationoftheprevious DigitalTransformationsIssueandfeaturesarticles onavarietyoftopicssuchastheInternetofThings, cybersecurity,networking,dataanalysis,andmore AsBillGatesputsit,“We’rechangingtheworld withtechnology”,andweaimtodiveintohow recentinnovationshavereinventedourwayof livingandthepathwearesettotakeinthefuture.
Theelectrifyingpaceoftechnological innovationhastriggeredastrikingtransformation inourworld.Infact,digitaltransformationsare happeningateverymoment,ofeveryday,during everyyear Asbreakthroughsaremadeand technologiesevolve,weandourdevicesbecome smarterevenastechnologybecomesmoreand moreembeddedinourlives
Asof2022,thereare585,000techcompaniesin theUnitedStatesalone(Zippia) Thetoptenlistof mostprofitablecompaniesintheworldis dominatedbytechgiantssuchasApple,Alphabet, Microsoft,andIntel(Investopedia),andtheU.S. techindustryemploysroughly12.2millionworkers asof2020(Zippia).However,youdon’tneedto lookatthestatisticsjusttoseehowmuchwerely ontechnologytoday.Wewakeuptothesoundof ourphonealarm,changethetemperatureinour roomwithadigitalthermostat,doourworkonour
... AND SO DO WE
Justastheworldhastransformed,wehereat STEMATIXhaveexperiencedshiftsaswell.We sincerelycongratulateourfounderandeditor in chief,SauravGandhi,whoispartoftheClassof 2026attheUniversityofPennsylvaniainthe JeromeFisherPrograminManagement& Technology HavingfoundedandrunSTEMATIXfor thepast5years,Sauravhasledthepublishingof 12issuesofthemagazine,alongsideleading workshopsandotheradditionaleventsforthe organization.Hisroleaseditor in chiefhasnow beenpasseddowntous,EinandSahana,andwe lookforwardtothefutureofSTEMATIXinthe comingyear!

issue xiii
table of contents
09INTERNET OF THINGS: THE EVOLUTION OF US
Amanda Kay writes about the rise and growing usage of smart applications, cars, personal objects, etc powered by the Internet of Things.

19
AN INTRODUCTION TO STEGANOGRAPHY
Wissam Al Ghabra writes about the history and current impact of steganography and cryptography in our current world
49
E = MC² THEORY OF RELATIVITY
Rita Shahada briefly dives into Albert Einstein, physics, the theory of structure of spacetime, and the theory of gravitation in her sort infographic style article.
14BEING SMART USERS OF SMART FARMS
Emily Seoyoung Kim discusses agriculture and the climate crisis, diving into the potential of smart farms as a solution.
32
CRISPR AND ITS FUTURE
Aryan Tiwari explores the history, advantages, achievements, applications limitations of a growing technology in the gene editing technology area of science
50
COVID-19 IMPACT & INNOVATION THROUGH THE CRISIS
Mahirah Mohd Noriznan provides an overview of innovation around the globe coming from the pandemic
INNOVATIONS


& CYBERSECURITY

THE INTERNET OF THINGS


Internet of Things
The Evolution of Us
By: Amanda KayWithout the Internet of Things, many conveniences that we have grown to expect and depend on would not exist Smart appliances, smart cars, smart personal gadgets, even smart doorbells; are all made possible by the Internet of Things

In simple terms, the Internet of Things is when a device can connect to the Internet. However, this definition hides a global network of interconnected items used to improve lives. This network includes conventional items such as cellphones and unconventional items such as refrigerators and coffee makers. If your refrigerator makes a shopping list that can be accessed by your phone, if your doorbell knows whether or not to let someone in, all of that is the Internet of Things in action. Today, submarines, oil rigs, power plants, you name it, are all connected by IoT IoT ties machines to machines and creates a connected digital web that links people to valuable resources, services, and opportunities This network is rapidly growing, with more estimated interconnected devices than ever
Gartner predicts that the number of connected devices will exceed 26 billion by 2020. Others estimate this amount to be over 100 billion due to the quick rise in interconnected devices. Internet of things impacts almost everybody's life. Humans crave connection, and an interconnected web of machines increases our ability to connect and our conveniences. It is expanding at an astonishing rate, making leaps in terms of innovation. According to Forbes.com, in the future, a device may be able to memorize one ' s schedule so precisely that it could send a text to your boss saying that you'll be late or give suggestions for the best route to take Not only will this make life so much more convenient, but it will also change the way we live by cutting costs The quicker our lives move, the faster people can make money
This automation may have a small effect initially, but later on, it will save millions of dollars Consider this: a white collar worker is ready to go to work but wakes up late However, his phone sends a text to his boss as soon as he wakes up late and misses his alarm, allowing the boss to make plans for his tardiness He rushes through his morning routine, the water he needs already hot at his disposal. His car, recognizing that he is late, recalibrates to a new path. Although this seems small, the time saved over weeks can save days or even years of working time with millions of people.
Additionally, the Internet of Things can also help society as a whole in many different aspects For example, traffic management and pollution control can be improved if we could designate specific routes to be taken by cars on particular days, restricting traffic by spreading it out The Internet of Things is already helping us make life easier, with innovations such as trash cans of refrigerators, instantly recognizing when something is out of stock or is not present at home. No need to write down something else to buy at the store when you throw something away; it's all there on your phone.
Companies like Amazon are currently investing in items connected with the Internet of Things with technology, such as Alexa. By connecting to light sources, it creates a connection to the lightbulb, in return, creating a connection to the Internet of Things This goes for other home devices labeled as "smart" or can listen to your command and act on it These may not be items you usually expect to be a part of the Internet, but the use of it helps make life easier
Since items connected to the Internet of Things can often be desirable for


consumers, they help companies in many different ways Marketers can analyze what items sell best through cash registers connected to the Internet, a process that would otherwise be tedious
Also, the Internet of Things can help us with bigger ambitions and problems than simple convenience. For example, the Internet of Things can help measure energy usage across various segments of society and how much carbon dioxide is in the air with sensors. This data allows scientists to gain reliable evidence of what is happening to our environment and ways to fix it.
However, some downsides to the Internet of Things' widespread connectivity are an open gateway to hackers and other people with malicious attempts It makes it easier than ever for home invasion and secret recordings Although alarms are set, hackers who make it past these walls have an easier time making it into the home and causing harm
More worrying is that the entire government can be hacked, including valuable information needed for identity theft, such as a social security number. Instead of having to hack one person at a time, a whole network is now accessible. This interconnectedness could lead to our downfall, with the catalyst of society becoming so dependent on the Internet of Things that it can't possibly succeed without them.
Despite these dangers, the desire for interconnectedness on even the machine level continues to dictate our very lives It has helped us make strides where our species is, pushing us farther than we had ever considered The Internet of Things is a truly global web that has rocketed society into the future
PLATFORMS PLATFORMS
By: Serena GandhiAMAZONWEBSERVICESIOTPLATFORM
It is a highly scalable platform capable of supporting billions of devices and trillions of interactions.

MICROSOFTAZUREIOTHUB

They have developed their operating system for IoT devices, which indicates that they plan to become a comprehensive IoT solution provider.
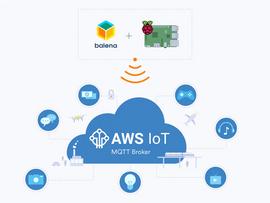

IBMWATSONIOTPLATFORM

With easy-to-use apps and interfaces, they strive to make their cloud services accessible to beginners.
Oracle is a platform-as-a-service provider that has a focus on manufacturing operations and logistics.
ORACLE
Salesforce specializes in customer relationship management. Their cloud platform is based on Thunder, designed to allow for fast and real-time decision-making in the cloud. The goal is to create meaningful customer interactions.

According to them, the Google Cloud Platform offers the best platform for IoT initiatives, taking advantage of Google's broad expertise in web scale processing, analytics, and machine learning.

Dedicated to security and efficiency, their IoT platform is flexible and based on open standards and open-source software.

They believe that tomorrow's opportunities lie in the cloud and have developed a new 'mobility cloud software suite.'

BEING SMART USERS OF
SMART FARMS
 By: Emily Seoyoung Kim Infographic by: Ein Hong
By: Emily Seoyoung Kim Infographic by: Ein Hong
Chief Cause of Climate Change: CHumans? hief Cause of Climate Change: Humans?
We have been discussing environmental issues for quite a long time, but we still hardly carry the solutions to real actions As a result, climate change has become a climate crisis now 2020 marked the year in which we heard Earth's voice As a result of the COVID 19 pandemic, it became apparent that human activities were the chief causes of climate change Moreover, during the summer, we had several exceptionally dangerous typhoons
Agriculture was among those affected by climate change in an immediate sense, so let's look at the current situation and see how smart farms are trying to solve our current problems
Agriculture vs. Climate Crisis
As the two keywords (agriculture, climate crisis) are both based on the environment, they cannot avoid interacting with each other We can classify the impact of the climate crisis on agriculture into three points first, the unusual weather events such as typhoons, droughts, floods Big disasters ruin the whole infrastructure of farms, while small ones still make agriculture difficult because of extreme water levels For instance, the enormous typhoon Haiyan (2013) in the Philippines required about USD 724 million for recovery in agriculture (according to FAO) Secondly, as an area ' s conditions rapidly change, many farmers face inevitable situations to find new markets lastly, the soil problem To cope with climate change, farmers have been relying on a lot of synthetic fertilizers and pesticides Unfortunately, this weakened the natural ability of soil, such as holding water or coping
with erosion. Because of these points, the agriculture industry is becoming more vulnerable, threatening a country's food security Therefore, this long fight between agriculture and climate change also involves governments
The Solution
Although the fight seems very complicated, one technology gave hope to farmers and governments: smart farms Smart farming is a system to increase productivity through precise environmental control and management based on Information Communication Technology (ICT)


Sensors collect fundamental data, and the IoT platform will diagnose the observation and suggest some treatments At last, autonomous products will carry out the treatments in action As you can realize, this system is helpful in that it can increase crops ' quality and optimize human labor required Also, smart farms aren't affected by natural environmental changes This feature is the main point where people thought smart farms could help our agriculture under the climate crisis Since a smart farm is an artificial place controlled with the perfect conditions for growing crops, unusual environmental disasters cannot disturb crops growing well
Moreover, we can locate smart farms anywhere, even where farming seems to be impossible For example, n thing (a Korean smart agriculture technology company) succeeded in growing lettuce in the United Arab Emirates The Arab Emirates has a representative desert climate where annual precipitation is less than 100mm


In other words, it's a dead land for agriculture. However, with the technology of increasing production per area while using much less water, they began growing lettuce This example shows the power of smart farms And since the fight between agriculture and climate crisis arose from the interactions between each other, this point of smart farming will be helpful
Are Smart Farms Always Smart?
As mentioned previously, smart farms have a remarkable ability to optimize the farming process and protect the crops from natural disasters of climate change However, it still has several challenges that we should overcome The biggest problem is the range of crops that smart farms can cover Since smart farming mostly focuses on greenhouse cultivation, especially paprika, tomatoes, or strawberries, smart farming has difficulties giving service for other crops That is, smart farming cannot protect all crops from environmental
issues yet. Another matter comes from the heavy pressure that the farmer has to take The initial cost is high, and the system is unstable due to an unfinished repair system In conclusion, we should research ways of developing this technology to cover more crops and be easily applied with a small burden to farmers.
How Can We be Smart Users of Smart Farms?
Although smart farming requires development, this technology can certainly work as a solution for an agriculture industry facing a climate crisis But to be enlightened users of smart farms, we must remember that smart farming only provides an ex post solution to minimize the effects of climate change. To effectively address this climate crisis and protect agriculture, it is essential to understand the primary causes of climate change and make ex ante solutions

DATA
IEEE Women in Engineering Fund

NONPROFITS NONPROFITS FOCUSING FON OCUSING ON WOMEN IN WSTEM OMEN IN STEM
Society of Women Engineers (SWE)

Aims to "stimulate women to achieve full potential in careers as engineers and leaders, expand the image of the engineering profession as a positive force in improving the quality of life, and demonstrate the value of diversity."
Technical professional organization with a mission of "advancing technology for the benefit of humanity."

Girls Who Code

Nonprofit organization on "a mission to close the gender gap in technology and to change the image of what a programmer looks like and does."
The National Center for Women & Information Technology (NCWIT)
Community and network of leaders that works to "increase the meaningful and influential participation of all girls and women in computing."

NETWORKING

AN INTRODUCTION TO STEGANOGRAPHY
 By Wissam Al Ghabra
By Wissam Al Ghabra
Introduction
In 2018, a Twitter account uploaded two seemingly innocent memes. Embedded within these memes were commands that instructed a piece of malware to take screenshots of the infected computer, collect information about running processes, capture clipboard data, and gather information to be sent to a server What seemed to be random images lurking on the internet was the unlikely accomplice in a cybercrime This is a very recent example of a practice that goes back as far as ancient Greece. Steganography is the practice of concealing data by embedding it into seemingly innocuous cover objects. It aims to hide the fact that secret information is being communicated. Steganography has been around for centuries. It was used by everyone from friends writing to each other letters with lemon juice (a popular type of invisible ink) to spies transmitting vital information during World War II With today's modern technology, steganography has evolved to utilize computers to hide
information from the prying eyes of those who aren't supposed to see it, and the practice of digital steganography came to life.
History
The term steganography originates from the Greek word steganographia, which literally translates to "covered writing" or "concealed writing." The first recorded use of the term was in 1499 by the German polymath Johannes Trithemius, in his work Steganographia, which disguised its actual topic of cryptography and steganography as a book about magic. However, the practice of steganography goes back even further, dating as far back as 440 BC An ancient Greek historian named Herodotus created The Histories, a record of the Greco Persian wars (499 BC 449 BC), in which he mentioned the two earliest documented examples of steganography. The first one is when Histiaeus, a Greek ruler in the late 6th century BC, shaved the head of his most trusted servant and marked a secret message onto his scalp. He then sent him to deliver the message after his hair grew back. The Histories also mentions Demaratus, king of Sparta, who sent a warning of an attack on Greece by removing the wax from a wax tablet (a common writing surface during antiquity and the middle ages) and then
writing a secret message directly on the wooden backing of the tablet before reapplying the wax coating.
Steganography & Cryptography
Cryptography aims to render secret data incomprehensible to those who aren't intended to see it; however, this encrypted data's communication is still discoverable. On the other hand, steganography aims to hide the fact that secret data is being communicated to begin with, which gives it an advantage over cryptography because it doesn't attract attention. No matter how unbreakable the encryption is, visibly encrypted data can still raise suspicions and can even be incriminating in some cases Steganography doesn't alter the message being sent, while cryptography converts it to a ciphertext, which is later decrypted by its intended recipient It is possible to combine the two practices For example, a secret message is first encrypted before embedding it in a cover object, like an image, using steganography. The cover image is slightly modified with an embedding algorithm to obtain the final image containing the hidden data, known as a stego image. The embedding algorithm may utilize a secret stego key, which controls the embedding process ' s details, such as the pixels being altered in the cover image Applying both steganography and cryptography ensures extra layers of security; however, this depends on how undetectable the steganographic process is. The resulting stego image should be indistinguishable from the original cover image, even if both the embedding algorithm and the cover image are available. In other words, the steganographic system should adhere to Kerckhoffs's principle: A cryptosystem should be secure even if everything about the system, except the key, is public knowledge
Digital Steganography
Steganography can be applied to digital objects. Text documents, media files, license keys, and even file extensions can all be used to hide information. Media files (images, audio files, videos, etc.) are the most convenient, as they are usually large in size, which allows hiding more data than text documents, for example. Information can be added to a file's metadata (information about the file itself, for example, the file's size), and it can be hidden directly within the contents of the file Many of the methods used in concealing data within files depend on the limitations of the human senses. For example, the human eye can't detect a vast range of colors, and it's very easy for the alterations made on an image as a result of steganography to go unnoticed. Similarly, data can be hidden in sound frequencies that can't be heard by the human ear, like ultrasounds (sounds with frequencies higher than 20,000 Hz) and infrasounds (sounds with frequencies less than 20 Hz) These sounds can be used along with cover audio
to deceive the unintended receiver. A very popular technique is LSB (Least Significant Bit). This is the simplest and most common way of concealing data in files From a computer's point of view, everything is represented using binary This includes media files like images, videos, and sounds For example, an image is made up of a vast number of pixels, with each pixel displaying a certain amount of red, green, and blue. The value for each color ranges between 0 (which is 0000 0000 in binary) to 255 (which is 1111 1111 in binary). These values are represented using bytes, and each byte is made up of 8 binary digits, or bits. The least significant bit in a binary number is similar to the one ' s position (rightmost digit of a number) in the decimal number system If the least significant bit is changed, it will not result in a noticeable or 'significant' difference in the value
Here's an example: (1111 1101) would give us the square on the right as a result (the visibility of the difference in color varies from one screen to another, depending on its color accuracy). Using this method, it is possible to replace the least significant bit in each byte of the cover object with a bit from the data we want to conceal, allowing us to hide things like ASCII characters or even entirely different images inside the selected cover object. The receiver can extract the hidden message by using the least significant bits to reconstruct it However, this method is easy to detect if the original unaltered file is available or if someone is specifically looking for hidden data within the cover object Some other techniques that are used with image steganography are DCT (Discrete Cosine Transform) and DWT (Discrete Wavelet Transform). It is also possible to hide an image or text by rendering it as a sound file, which is then analyzed using a spectrogram to reveal the hidden data.
The square on the left has the RGB (Red, Green, Blue) values of (255,0,0) Changing the value of red from 255 (1111 1111) to 253
Spectrogram analysis of a sound file using the digital audio editing software Audacity. The sound file was created using a software called Coagula. As shown in the spectrogram, the audio was used to hide the word "STEGANOGRAPHY "

Detection & Steganalysis
Today, various people still use steganography, including spies, cybercriminals, and human rights activists In the context of cybersecurity, malicious hackers often use steganography to hide code within commonly shared media like pictures of celebrities and popular songs
According to Kaspersky Labs, a global cybersecurity company, steganography in cyber attacks makes it difficult to identify threats. While in most cases, proven security solutions can discover the presence of a threat because of the tracks it leaves (logged connections to unknown addresses or blacklisted IPs), the use of trivial images and videos to hide a certain payload (malicious code, data exfiltrated by spyware or information concerning the communication between malware and its command and control server) doesn't trigger security solutions, thus making it difficult to detect attacks As a result, there's been a surge in the use of steganography by malware developers because it enables them to conceal the communication of data and the ability to bypass security systems. Steganalysis is the practice of attacking stego systems; in other words, it aims to detect the communication of concealed data within a carrier. The phases of a steganalysis including the development of algorithms that can detect carrier objects and stego
images, identifying the applied embedding algorithm (for example, LSB), identifying the steganography software (Outguess, Steganos, F5, etc ), finding the stego key, and extracting the hidden data Steganalysis is a complicated process as it depends on statistics and probabilities for deciding if a particular file was altered to hide a payload. It involves working with large sets of files and reducing them to a subset of files that have a high probability of being altered. Steganalysis also depends on the fact that stego tools tend to leave specific carrier patterns and characteristics. This can be used to identify whether a file was used to conceal data Steganography and steganalysis both continue to grow and have new methods or techniques When it comes to the end user, since an image or an audio file can't, by itself, be a fully functioning malware, but rather is used by another malicious program executed on the victim's machine, protection from the growing trend of using steganography in attacks is possible by following standard security procedures. These include only downloading files and installing applications from trusted sources, having a robust security solution that can detect suspicious activities on a computer, and, of course, maintaining carefulness and consciousness with how they use their computer
STEGANOGRAPHY
CRYPTOGRAPHY




A
A N
A
Living in a world governed by computers, phones, and other digital devices, as helpful as they are, come with serious issues. Cyber threats are incredibly prevalent today and are a significant threat to national security and privacy
They can result in electrical blackouts, military equipment failure, theft of sensitive records, phone networks, and operations disruption. As our current society relies on each of these elements functioning correctly, there could be dire consequences if our everyday infrastructure is attacked.
A news article can include accounts of eyewitnesses to the happening event It can contain photographs, accounts, statistics, graphs, recollections, interviews, polls, debates on the topic, etc There are various ways cyberattacks are carried out in cyberspace, but the commons ones are:
W H A T
W H A T
Malware: Malicious software developed by cyber attackers with the intent of performing damaging activities such as corrupting data and systems or gain unauthorized access to a network. A variant of malware called spyware can obtain information on a victim covertly

Phishing: Mostly seen in emails where the cybercriminal provokes the victim to click on a link with malicious malware or reveal sensitive information about themselves, such as bank details
DoS (Denial of Service): Overflooding the server with information; therefore, the system's resources and bandwidth is overwhelmed and exhausted, and unable to co operate
Man in the Middle (MitM): The hacker inserts themselves in a position between two or more communicating parties and hijacks the conversation by intercepting and possibly altering the transmits
Structured Query Language (SQL) Injection: The attacker utilizes malicious code to compel the server to reveal confidential information.
Many dangers are lurking in cyberspace, and basic knowledge of cyber safety rules can go a long way to protecting your safety and everyone else The basic rules of choosing complex passwords, changing them consistently, and ignoring and not clicking on suspicious emails and links can make a massive difference to the number of cyber attacks carried out globally In 2019, 4 1 billion records of confidential information were breached Many of these could have been prevented if the companies involved took better care of their cyber safety and were warier regarding internet matters. This situation's reality is that hackers attack every 39 seconds, which is approximately 2,244 times a day Cyber threats are universal and must be taken seriously to fortify ourselves from attacks we can't necessarily see Additionally, if you are interested in cybersecurity, studying computer science can give you a better understanding of cyberspace's intricacies and complexities, allowing you to gain better judgment in matters attaining to cybersecurity It's a broad field and equips you with knowledge of hardware, software, network, security, etc These factors play a part in combating cyber attacks and could help you fortify yourself and others against malicious hackers. We live in a computer reliant world, and to survive and prevail in the concealed world of cyberspace, we need to make cybersecurity one of our top priorities
CYBERSECURITY THREATOP TCYBERSECURITY OP CYBERSECURITY THREATS THREATS
CYBERSECURITY THREA
PHISHING A common cyberattack in which individuals/uncredible organizations send fraudulent emails pretending to be from reputable companies in hopes that recipients will input personal information into their fake email forms/sites.
PDF SCAMS A cyberattack similar to phishing in which scammers send an email with a PDF attachment. If clicked on, the PDF exposes the recipient's device to malware or ransomware.
DATABASE EXPOSURE A security breach in which database information is hacked or stolen. Personal information, including contact information, financial information, and salaries, have been made public due to this threat.
CREDENTIAL STUFFING An attack that aims to steal user's account access and information through login credentials (e.g. usernames and passwords). Because many programs are now digital, credential stuffing is one of the largest anticipated threats this year.
ACCIDENTAL SHARING - An accidental threat caused by human error in which one accidentally shares personal or business date through emails, unsecured forms, messaging, or social media to name a few. There isn't a way to solve accidental sharing right now, especially because it isn't due to hacking/malware.
THE BENEFITS OF 5GTHE BENEFITS OF 5G
by Kaitlyn Butcher10x
Decrease in Latency
Delivering latency as low as 1 ms.
3x
Spectrum Efficiency
Reaching more bits per Hz w/ advanced antenna strategies.
10x
Experienced Throughout
Greater uniform, multi-Gbps peak rates.
10x
Connection Density
Efficient signaling for loT connectivity.
100x
Traffic Capacity
Network hyper-densification w/ more small cells everywhere.
100x
Network Efficiency
Network energy consumption w/ better efficient processing.
ZOOMALTERNATIVES ZOOMALTERNATIVES ANDCOMPETITORS ANDCOMPETITORS














DATA

BIG NUMBERS IN COMPUTATION: BUSY BEAVERS
BRUNO FERNANDES IORIOIn our early years, when we finally discover the basis of math, it is very common to find ourselves wondering so as to what is the largest number we could find? Big numbers have always been a mystery for us and are considered a measure of human intellectual abilities. Many scientific and mathematical discoveries are closely tied to our ability to describe large numbers
Busy Beavers are a 'kind' of enormous numbers related to computation theory in some ways. But before we can comprehend them, we need to know what Turing Machines are The story starts with Alan Turing (1912 1956), a British mathematician who had always loved combinatorial problems While working on a formal logic problem, he ended up defining how machines would work and how they would perform algorithms, so here is a summary of what he proposed:
Think of a tape (as long as necessary) divided up into squares, and each of them either has a 0, or a 1, or nothing written on it.
Then, think of a machine that has n possible states and put it on one of the squares Depending on the state that this machine is, it will change the number written on the square into 0 or 1 or nothing, and then it will move to another square also changing its current state
The machine stops when we reach the desired string of 1’s and 0’s

This is the Turing machine mentioned before, so let's see an example: think of a 2 state machine (represented by the red box) placed above the central 0 of the tape 01010 below
Finally, the machine stops because it reached the string 01100, as desired
Furthermore, Turing machines are so interesting, because it is the basis of computation: anything that a cellphone or television does, for example, could be performed (in theory) by a Turing machine
The states of the machine are: red and green. When it is red, it changes the number on the square into 1, it turns into green and moves one square to the right, but when it is green, it changes the number on the square into 0, turns into red, and moves one square to the left. So, if we aimed to reach the combination (01100), we would require three simple steps:
However, the number of steps required to reach 01100 in the previous example can vary or even be infinite (if the machine starts to loop), depending on the box's initial position. In 1962, Tibor Radó, a Hungarian mathematician, proposed the Busy Beaver Game: consider an n state Turing Machine knowing that one of its states orders the machine to stop at a certain condition, then put this machine on an infinite tape only with 0's. Then find the maximum numbers of 1's that this n state machine can write before it stops (note that we are only considering the machines that stop)



For small values of n, the answers to this problem are considerably small For instance, n=3 and n=4 have solutions 6 and 14, respectively. Nevertheless, for n > 4, the answers become so big that we couldn't even write them using all the STEMATIX edition pages, which we call a ' super exponential function'. As its name says, it is a function that grows so fast that it isn't even countable!

CRISPR AND ITS FUTURE
H I S T O R Y
In 1987, while just casually fiddling with yogurt bacteria, a group of researchers stumbled upon a pattern in its DNA There seemed to be a particular sequence of base pairs, or DNA letters, that repeated periodically in a portion of the yogurt bacteria DNA Perplexingly, the repeated portion was like a spacer or marker, and between two such sequences, the bacteria stored the DNA of viruses they had encountered in the past. Thus, the bacteria can immediately identify that a virus has attacked it as if it had a memory and quickly initiate an immune response. The DNA markers were named Clustered Regularly Interspaced Short Palindromic Repeats or simply CRISPR By 2002 the CRISPR markers were discovered in all kinds of bacteria They were found to transmit the CRISPR DNA to the next generation pretty effectively By 2008 it was clear the CRISPR DNA is merely a storage system, but the real highlight is that the CRISPR Associated Protein or Cas protein can cut foreign viral RNA or DNA like a pair of scissors all by itself This year's Nobel Prize winners studied the CRISPR Cas protein: Jennifer Anne Doudna, an American biochemist, and Emmanuelle Marie Charpentier, a French professor of microbiology, genetics, and biochemistry
W O R K I N G
A CRISPR Cas system is a molecular tool that lets scientists edit DNA It has two parts: an enzyme that cuts the DNA at a specific point and an RNA guide that helps that enzyme to find and reach the right place to cut The breakthrough was when the research duo realized that the Cas protein could be extracted from the bacteria and used as a Gene Editing tool They published their research paper in 2012 and patented the editing system In a nutshell, the CRISPR Editing system/process works through the CRISPR Cas protein, and a popular choice is a Cas 9 Protein A predetermined short RNA sequence (called the guide RNA) is fed into the Cas protein, which then searches the cell's full genome along with DNA and RNA in the cytoplasm (body) of that cell. Once a matching sequence is found, the Cas protein binds to that gene and precisely cuts it just like a pair of scissors In real life all genes get damaged from time to time so enzymes and various mechanisms constantly fix and repair the genes Naturally, the cell mechanisms try to recover the part of the gene cut by the Cas protein This is when a new sequence is externally introduced into the cell, and it gets attached to the gene automatically
By: Aryan TiwariBUILD A BABY
D V A N T A G E S
CRISPR can therefore be used to edit genes quickly and efficiently Previous generations of gene editing tools were remote, in the sense that it took days for even simple edits to be done and that one had to send all the genes to an external company to be edited by that company With the discovery and adaptation of CRISPR, researchers can edit genes within minutes, that too, inside their labs The CRISPR system can be used inside living cells without disrupting normal functioning It can be inserted into a virus and using this virus, a genome of an entire organism can be changed
A C H I E V E M E N T S

CRISPR has revolutionized microbiology, particularly gene based research Many brilliant and hardworking researchers pioneered CRISPR, but chief among them was Jennifer Duodena and Emmanuelle Charpentier It usually takes thirty years for a published paper to be recognized and applied to the extent that the author receives a Nobel Prize However, the fact that CRISPR was produced in about seven years and is now being used for cutting edge research across the globe is a breakthrough for humanity This is the first time a pair of female scientists has won the Nobel Prize in the field of sciences, showing that female scientists have a promising future.
C U R R E N T
A P P L I C A T I O N S
With enough research, scientists may be able to create horses with horns, or maybe even Blast Ended Skrewts, though that's not on the priority list So what are the current areas of research where CRISPR plays a trivial role? In its initial days and even today, CRISPR gene editor is being used to study every gene's effects and purpose in all organisms It allows for the precise removal of a specific gene from the genome of an organism in its embryonic form Now scientists can observe the changes in that organism's structure and behavior as it grows in the absence of that gene Thus, by studying the absence of a gene, its function can be inferred and speculated Drought resistant crops, better yield from modified seeds, non browning apples, and larger juicier fruits are now a reality thanks to CRISPR Some human diseases are caused by a small change in the entire genome, like a single letter change, addition, or removal of a few bases CRISPR technology can be incorporated into regular medicine that targets reachable cells and changes their genome to treat diseases. Blood cells are the easiest to reach, and CRISPR editing in blood cells is quite practical. A significant area of research today is based on finding a cure for blood diseases cystic fibrosis HIV sickle cell anemia cancer and blindness through CRISPR medicine Like hypertrophic cardiomyopathy (enlargement of a part of the heart) genetic cardiovascular diseases are caused by a small change in a specific gene Researchers are using CRISPR modified live tissues to determine whether that particular genetic change causes that disease In this way, after many trials, customized CRISPR based heart treatments may become available Limb regeneration in tadpoles and fat metabolism in flies have been studied with the help of CRISPR A slightly modified version of this gene editor, in
which
Cas 9 enzyme is
finds a particular DNA sequence location without cutting it This d Cas 9 enzyme is a marker which helps to navigate any cell Eradicating malaria yellow fever and dengue can be achieved by genetically modified mosquitoes Recently, Florida announced to release 750 Million GMO mosquitoes in 2021, hoping to wipe out Aedes aegypti There is even a CRISPR based COVID test!
L I M I T A T I O N S
However, the seemingly perfect CRISPR does have its limitations For one, a CRISPR system can make a small change at a time in the genome of the entire DNA sample But, multiple CRISPR systems can be employed simultaneously in a single sample of DNA CRISPR is very precise in cutting and editing genes, but "off target effects" do show up quite often Off target effects occur when the CRISPR Cas enzyme cannot distinguish between two very similar DNA sequences, so both are cut This leads to unwanted changes in the sample DNA Off target effects are relatively rare: on average, 2 3% of the sample is contaminated by these wrong edits
G E N E D R I V E S
CRISPR modified genes might not survive even a few generations in nature, but what if the next generation's genes were automatically modified without external intervention? Enter Gene Drives. Through a long and tedious process, an organism's genome can be modified to produce Cas proteins, which will modify the genome automatically in the next generations. Gene drives are segments of DNA, artificially attached to an organism's genome, which will produce CRISPR Cas proteins in the coming generations For example a single GMO mosquito with a red body and a corresponding gene drive can transmit the gene drive to all its offspring Thus when released in the wild all wild mosquitoes' will be automatically modified to have red bodies This has vast implications Now, humans have the power to change entire species at will, even produce GMO human embryos and rekindle extinct species There are a lot of moral dilemmas that threaten existence and nature itself
E T H I C A L I S S U E S
"I don't think it is acceptable to manipulate the human germline for the purpose of changing some genetic traits that will be transmitted over generations" Emmanuelle Charpentier, co inventor of CRISPR Cas9 Soon after CRISPR's power was realized, both Doudna and Charpentier globally called for all human embryo and germline related CRISPR research to a pause There were several meetings and conferences with international scientists, researchers, and stakeholders, which aimed to come up with all the ethical issues surrounding CRISPR and come up with guidelines to prevent the misuse of this powerful technology The realm of genetics is relatively new, and a lot of research is required to understand, standardize, and apply CRISPR's inner workings and repercussions The world of molecular biology and genetics is evolving at such an exploding rate that there are breakthroughs and new inventions every month worldwide CRISPR is a crucial part of this process
Pressing issues, such as finding a viable and effective cure for cancer, are closer to reality than sci fi "The power to control our species' genetic future is awesome and terrifying Deciding how to handle it may be the biggest challenge we have ever faced" Jennifer A Doudna, A Crack in Creation: Gene Editing and the Unthinkable Power to Control Evolution
E N E E D I T I N G T E C H N I Q U E S
S O M A T I C
G E R M L I N E
 AleenaBosky
AleenaBosky
THE NOBEL TMEMORIAL HE NOBEL MEMORIAL PRIZE IN PECONOMICS RIZE IN ECONOMICS
By: Devansh ShahPAUL R. MILGROM AND ROBERT B. WILSON

The Nobel memorial prize in economics 2020 was jointly awarded to Stanford economists Paul Milgrom and Robert Wilson "for improvements to auction theory and inventions of new auction formats"
TYPES OF AUCTIONS continue, and the bidder with the highest bid wins. Dutch Auctions: These auctions are the other way round, the price starts high and decreases with each round until somebody bids at that price, and he/she will win the auction Sealed Auctions: In the previous two auctions, the auctions are public, and every bidder knows where his/her competing bidder stands But in this auction, every bidder submits their bid in a sealed envelope and the highest bidder wins
English Auctions: These are the auctions you should know about as they start low and go up in price as the bidding rounds
WINNER'S CURSEAlthough it may seem otherwise, winning an auction is not always good for the bidder. There are two prices of an item in an auction:
1. The common value: The value that everybody agrees upon, e.g., while bidding for a house, everybody agrees that the house is worth $200000.
2. Private value: The value every bidder privately has for the house. For instance, a property developer who plans to build in the area can fork over $300000 for the house. That is the developer's private value.
There are problems in all three of the auctions mentioned above; while caught up in a bidding war, not knowing the intrinsic value of the item or lack of knowledge of fellow competitors' bids leads to the bidder overbidding, i e , paying more than the real value of the item "The bidder with the most optimistic evaluation of that asset may overpay, "according to There also are other problems with these auctions Let's say that the property developer needed not only that plot but the one beside it too Additionally, the neighboring parcel owners would not be ready to sell! The neighbors would raise their prices after getting this information; these factors would dissuade the developer from bidding!
WHAT DID THEY DO?
The economists formulated the Auction Theory, which, as explained above, included the Winners Curse. Apart from the Winners Curse, which made bidders bid conservatively, many other problems plagued the Auctions! They included lobbying politicians to favor one bid over another, corruption and another big problem was bidder collusion. To use the example above, the developer would probably tell the other bidders they would win anyway because they have deep pockets, so why don't they take the $5000 and not bid at all? This would reduce the lot's price by $150,000 for the property developer, saving him money and giving the other bidders $5000 extra. This is a collusion between bidders. The economists solved all these problems with SMRA, their masterstroke
THE SMRA
What is it, you may ask? SMRA, or the Simultaneous Multi Round Auction Format, is the auction format both the economists put forward to solve all of the problems plaguing the other auction formats. We have to take a little more complex example for this one. This auction type is mainly used to auction frequency bands; hence we will assume that example. Frequency bands are sold district wise. i.e., the operator has only licensed the rights to use the frequency bands to that particular district Hence, if an operator wants to offer statewide or nationwide coverage, he must ensure that he wins auctions there too, or he will have only one district's license, which is almost useless Another worry they have is spending too much on the license, i e , overbidding Another possibility is that a competitor is corrupting officials to favor their bid All these problems are solved using SMRA In SMRA, all districts' licenses are auctioned simultaneously All bids for all districts are placed secretly at the beginning of a round, and all districts' results are publicly shared after each round After this, all bidders are given a chance to withdraw their bids or place higher ones; this continues until only one bidder remains and all other bids are withdrawn. This gives all bidders a fair idea of where they stand in each district, removing fears of not getting other districts. As information is publicly shared, every bidder can see their

IINNOVATIONS NNOVATIONS
LOOK TO THE PAST
TO UNDERSTAND THE FUTURE

INVENTING 101
By: Kaitlyn Butcher"WHAT IF...?"
Have you ever came across a "what if" question that quickly sparked your interest? Often times in classes, teachers are asked these "what if" questions by their students However, most teachers tend to suggest that students should think more practically rather than figuratively. While this effectively keeps the class on track with their work, this also diminishes the student's creativity All of the greatest inventions began with a small problem and evolved over time into the revolutionary pieces we know today

THE DESIGN THINKING PROCESS


Coming up with a novel idea is not as easy as one might think The process of creating an innovative product today is based on design thinking The process of design thinking is defined as an iterative, repeatable process that seeks to understand people's everyday challenges The end goal of using design thinking is to develop a solution to the users ' problems by designing, testing, and iterating
PHASES
Phase one of the design thinking process addresses who the user is and what challenges they face. To clearly define what challenges they face, the inventor observes what daily conflicts the user encounters After the problem is addressed, the user can move onto phase two of the design thinking process, emphasizing the user The inventor must place themselves in the user ' s shoes to fully decode the problem. To do this, interview the user or merely observe all the ways this challenge affects them Once the inventor fully envisions what the user goes through, they can move onto step three brainstorming During the brainstorming period, the engineer's job is to break down the problem and find possible solutions. These potential solutions are later turned into ideas.
During the brainstorming period, the engineer's job is to break down the problem and find possible solutions These potential solutions are later turned into ideas To select which ideas to develop, the inventor has to weigh all the possible solution method's pros and cons After the ideas are narrowed down, the engineer moves onto the fourth step rapid prototyping. This phase is where the inventor starts bringing the ideas on paper to life by creating scaled down models of their design The engineer goes through multiple sets of prototypes to see which approach to the problem works best Finally, after each key solution is prototyped, the engineer goes to the fifth stage testing. In the testing stage, one will see which prototypes are most effective in solving the user ' s problem. After pursuing the tests, the engineer can build off their existing ideas to see what is working and what can be improved
Once the engineer can clearly see what improvements can be, they will move to the final step of the design thinking process, which is iterating. Iterating is the continuous cycle of the design thinking process. In other words, it begins with addressing the problem once more and seeing what other issues are not fully developed with the product

The inventor will continue this process of designing and iterating until they are satisfied with their work The most successful pieces of work go through multiple cycles of designing. As famously said by Thomas Edison, "I didn't fail a thousand times. The light bulb was an invention with a thousand steps " In other words, Edison's words are saying that satisfaction of a product does not come the first time; to reach satisfaction, you must go through 10's or 100's or even through 1,000 different designs to learn which is the most effective.

HISTORY
HISTORY
Now that the design thinking process has been explored, one can fully understand how great inventions come to be Over time, works of inventors may modernize, but the design thinking process will always remain an important factor in new inventions' progression A few great inventors of the 1800s were Thomas Edison, Alexander Graham Bell, Albert Einstein, and many more. All of these successful inventors started with a question that sparked an idea that later came into production Inventors need not be engineers; they are someone who is curious and uses their imagination For instance, in the 1800s, Margaret Knight created the paper bag Despite her background of working at a cotton mill at one point and not be identified as an "inventor," especially for being a woman, she still pondered phenomenons. Her curiosity drove her to the creation of the essential item today, a paper bag A simple idea can lead to the creation of a revolutionary device that helps thousands of people But it must start with a question, even if it's a "what if "
PENICILLIN PENICILLIN PENICILLIN

 By Dana Choi
By Dana Choi
Penicillin, one of the most useful and advanced medications in history, was discovered by accident Alexander Fleming, the attributed discoverer of Penicillin, was a Scottish born scientist who had already built a reputation as a brilliant researcher. However, he was very untidy, and in September 1928, Fleming returned to his laboratory, having spent August on holiday with his family. Before he left, he had stacked all of his staphylococci cultures, something he was investigating since the previous year. Upon his return, Fleming noticed that one of the cultures was contaminated by a fungus, and the colonies of staphylococci in the dish had been destroyed Fleming then spent his time studying the fungus and its possibilities, resulting in the discovery of one of the most useful drugs in medicine
Fleming grew the mold in pure culture and found that it affected bacteria such as staphylococci and many other bacterias After discovering the amazing effects the mold, now cited as Penicillin, could have on bacteria and could eliminate illnesses, Fleming published his discovery in 1929, but little attention was given to the article However, Fleming continued to study Penicillin and its effects Eventually, in the 1930s, Fleming’s tests showed promise, but Fleming abandoned the work. In March 1942, Anne Miller became the first person to receive successful treatment through Penicillin. She avoided death following an infection, proving the positive effects Penicillin could have
Thediscoveryof penicillinwasatriumphof accident,afortunate occurrencewhichhappened whileIwasworkingona purelyacademic bacteriologicalproblem. AlexanderFleming
Howard Florey and Ernst Boris Chain of Oxford decided to mass produce Penicillin, funded by the U S and the British governments They mass produced it after the bombing of Pearl Harbor, and by D Day in 1944, so much Penicillin had been produced, all of the wounded in the Allied forces could be treated
Howard Florey and Ernst Boris Chain of Oxford decided to mass produce Penicillin, funded by the U S and the British governments They mass produced it after the bombing of Pearl Harbor, and by D Day in 1944, so much Penicillin had been produced, all of the wounded in the Allied forces could be treated
Penicillin was in such short supply during 1943, there were only 400 million units available, but by the time World War II ended, U S companies were making 650 billion units a month, and it is the most widely used antibiotic in the world

Penicillin is used to treat infections caused by bacteria and is used by being either taken orally or injected, and it works by interfering with bacteria walls There are several different antibiotics in the penicillin class, but all work similarly by preventing peptidoglycan from cross linking in the last stages of bacterial cell wall synthesis This causes the bacteria to weaken and burst open Penicillin directly kills bacteria
Since its first use, Penicillin has become a popular antibiotic It is well known for being the first antibiotic that doctors used and is still a popular medication today The medication is very effective While it does have many side effects, it is a powerful medication that can save lives and is especially popular because less than one percent of people are dangerously allergic to Penicillin
Fleming, Howard Florey, and Ernst Boris Chain were all awarded a joint Nobel Prize in 1945, under the category of Physiology or Medicine The three men were known as heroes to many for their achievements and the discovery of Penicillin and its effect on various infectious diseases
In Fleming’s Nobel Prize speech, he warned that the overuse of Penicillin might one day lead to bacterial resistance, and this has since become a problem
Although Penicillin is still effective and is one of the most widely used antibiotics, it has proved its effectiveness for a long time Penicillin proved itself to be one of the most powerful and popular drugs in history (e Thanks to Alexander Fleming’s messiness, millions of deaths were prevented, and there are millions more to be prevented in the future
PENICILLIN TO THE RESCUE
According to CDC What is antibiotic resistance?
Antibiotic resistance happens when the germs no longer respond to the antibiotics designed to kill them. That means the germs are not killed a continue to grow. It does not mean our body is resistant to antibiotics.
Bacteria and fungi are constantly finding new ways to avoid the effects the antibiotics used to treat the infections they cause Infections caused by antibiotic resistant germs are difficult, and sometimes impossible, to treat In many cases, antibiotic resistant infections require extended hospital stays, additional follow up doctor visits, and costly and toxic alternatives.
THE LIGHTBULB BYGINACHOI
VOLTAIC PILE
THEGREATESTINNOVATION
It has been argued that the light bulb was the greatest invention of all time, and it's not hard to see why The revolutionary technology is ever prevalent throughout societies worldwide, and life as we know it would be vastly different without it. Just imagine how unfamiliar Paris, the city famed for its lights, would be at night or how unusual the New York skyscrapers would look without the light bulb It would be beyond recognition
THEPATHOFINNOVATIONS
ELECTRIC ARC
Contrary to popular belief, Thomas Edison was not the only one that led to the lightbulb development Throughout history, many others had worked on electric batteries, lamps, and other technologies that were essential to the lightbulb its creation. Alessandro Volta developed the voltaic pile as early as the 19th century, which conducted electricity using zinc, copper, and saltwater

LIGHTBULB
Next, Humphry Davy invented the electric arc lamp, which was the first electric lamp It implemented voltaic piles and charcoal electrodes but burned out very quickly. In the 1840s, Warren de la Rue and William Staite created their own versions of a more efficient lightbulb, but the cost of the materials needed prevented them from being commercialized
THEPATHOFINNOVATIONS
Edison its lightbulb led to the creation of Light emitting diodes (LEDs), which are cheaper and have a longer lifespan than their traditional counterparts LED technology has since been improved so that it can change hues, become voice activated, and sync with movies. Today, large organizations such as NASA are working on smart light bulbs that automatically sense the light level and adjust accordingly. Many home lights are now being activated through robotic assistants such as Alexa and Google Home As is evident from the development of the first light bulb to the advancements in the technology field, the possibilities are endless.
FUNFACTS
The world's longest-lasting light bulb is the Centennial Light, located in California. It has been burning since 1901!
Unlike incandescent bulbs, LED light is designed only to emit visible light, making it far more efficient.
LEDS
SMART ASSISTANTS
The first light bulbs to shine on Niagara Falls were installed in 1879, using lights equivalent to 32,000 candles.
The brain operates on the same amount of power as a 10-watt to a 15-watt light bulb.
WORLD WIDE WEB
In 1989, Sir Tim Berners Lee laid out the first ideas for what would become the World Wide Web (www) to his boss at CERN
Fun Facts
Berner Lee was knighted by Queen Elizabeth II in 2004.
The first website that Berners Lee created is still on the World Wide Web.
The number of devices connected to the web far exceeds the human population in its numbers.

The World Wide Web was close to being named Information Mine? Or Information Mesh?
The email service came to be known as Gmail (before Google acquired it)
By: Rosie ChenAt the time, the internet was already making breakthroughs to connect people regardless of geographical location The internet's infrastructure was what ultimately made it possible to create and support the World Wide Web Using another emerging technology, hypertext, Berners Lee sought a way to allow people a new way to share information The idea was thus seeded for the creation of the World Wide Web
To understand how the World Wide Web works, it is essential to look at how other technologies laid the foundation for the World Wide Web

The internet contributed immensely to the development of the World Wide Web In August 1962, J C R Licklider of MIT outlined a method to create social interactions through networking Licklider's vision of interconnected computers by which people could access data is surprisingly similar to today's internet
The first significant step was proving the feasibility of using packet switching instead of circuit switching Circuit switching was the basis of many telephone lines at the time Unlike circuit switching, packet switching allows users to share
bandwidth equally The first significant step along a long road was proving the feasibility of using packet switching instead of circuit switching Circuit switching was the basis of many telephone lines at the time Unlike circuit switching, packet switching allows users to share bandwidth equally
Still, there is no promise regarding quality or latency, which is a useful feature when real time responses are not a priority In the next step, a small but clearly functional computer network was built The next few years were devoted to the design and construction of the ARPANET
By 1972, hundreds of computers were connected to the ARPANET, and the first electronic mail was sent
The ARPANET was only the beginning Soon, packet satellite networks, ground based packet radio networks, and other networks emerged, resulting in what we now know as the internet Now, the question is, how does the World Wide Web fit into the picture?
When Berners Lee was working at CERN, he realized that not only were scientists from all over the world coming to use CERN's particle accelerators, but they found it easier to travel around the world to share information Each computer had different information on it; there was no easy way to share all that information An emerging technology, hypertext, was the answer to Berners Lee's problems Hyperlinks interconnect hypertext documents, typically activated by a mouse click or a keypress set It was the interconnect ability that allowed people on different computers to access the same document
Berners Lee saw the potential of this technology combined with a group of computers already connected to ARPANET All the computers had to do was click on a hyperlink for all the computers to access the same information As of 1990, Berners Lee had written the three fundamental technologies that remain the foundation of today's web: HTML (HyperText Markup Language), or the formatting language for the web; URI (Uniform Resource Identifier or URL), which is a kind of "address" that is unique and used to identify to each resource on the web; and HTTP (Hypertext Transfer Protocol), which allows for the retrieval of linked resources all across the web
Berners Lee also took the time to create the first web page and the first web server By the end of 1990, the first web page was on the internet As more and more web pages began to appear on the internet, an age of collaboration that was unheard of began Using the internet and the web, people could finally access information and share information regardless of geographical location
As you may imagine, the creation of the World Wide Web has enabled
"We know the World Wide Web to be a massive collection of websites. Nevertheless, it is astonishing to realize that the entire World Wide Web, every last website, can be downloaded onto a billion DVDs "
us to do so much We often take being able to click on a website and get information for granted Nevertheless, there would be no websites in the world without the World Wide Web
The World Wide Web enables communication to take place on a worldwide scale Communities from around the globe could collaborate on the same web pages Online shopping and e business emerged from the World Wide Web Marketing now targets people around the world Social interaction with strangers became possible, since websites allowed instant connection with everyone The World Wide Web makes communication for business, school, marketing, socializing, and more attainable Furthermore, it is the development of the World Wide Web that made search engines necessary Several large businesses nowadays rely on the Internet's availability and the World Wide Web's information There are even websites that help the user design websites, from small business owners to hobbyists The World Wide Web affects our daily lives and impacts our daily jobs, our research, our recreation, and even our relationships

Amruta Bhate
Postdoctoral Fellow Jin Billy Li Lab Genetics Department School of Medicine Stanford University
INSULIN TO THE RESCUE!
You are living in 1910 and are diagnosed with diabetes. What are your treatment options? How long can you expect to live? The sad answer at the time was that there were no viable treatment options other than a very extreme low calorie diet restricting all carbohydrates, all this only buying you a couple of years!
SWITCH TO THE PRESENT

We take a diagnosis of diabetes in our stride There are plenty of treatment options. With careful lifestyle management and taking medication on time, millions of patients enjoy healthy and longer lifespans. One big reason that diabetes is not the death sentence that it once was the discovery of the hormone ‘Insulin’ by a team of scientists led by Dr. Fredrick Banting in 1921.
For over 500 years, it was well known that erratic blood sugar levels somehow caused diabetes, but what caused these fluctuating blood sugar levels were unknown By 1890, German scientists Oskar Minkowski and Joseph von Mering discovered a link between ‘pancreatic secretions’ and diabetes by removing the pancreas from dogs These dogs had high blood sugar, glucose in their urine and died soon By 1913, Sir Edward Sharpey Schäfer suggested that many specialized cells in the pancreas, Islets of Langerhans, secreted a substance ‘insulin’ that might control blood sugar levels Scientists were still unable to isolate insulin from crude pancreatic extracts due to degradation by digestive enzymes.
THE BREAKTHROUGH


The breakthrough came in the early 1920s, when Frederick Banting, an orthopedic surgeon, and his assistant, Charles Best, a chemist working at the University of Toronto, isolated insulin for the first time. Banting realized that cutting off the blood supply to the pancreas in dogs would lead to all cells' death except Islets of Langerhans, protecting them against digestive enzymes Insulin could now be successfully extracted! Once this pancreatic extract was injected into a diabetic dog, there was a
remarkable 40% drop in glucose levels within an hour. Banting presented these findings to Dr. John Macleod, head of Physiology at the University of Toronto, who provided Banting with additional funding and lab equipment As extracting insulin from dogs was challenging and resulted in small amounts of insulin, Banting and Best decided to use fetal calves as a source of insulin McLeod recruited James Collip, a biochemist, to help with purifying and testing insulin on rabbits Once the scientists established a process to purify insulin, they conducted the first human trial in 1922. They injected two rounds of insulin into a 14 year old diabetic boy his blood sugar level miraculously stabilized, and he lived until the age of 27! Soon after, insulin was made available to the general public in 1921 by Eli Lily, a pharmaceutical company. The discovery of insulin and the subsequent treatment that emerged from it was so momentous that Dr Banting and Dr John Macleod were awarded the Nobel Prize in Medicine in 1923
In those early days, insulin was produced from animals, leading to allergic reactions in some patients. The next breakthrough occurred in 1978 with the synthesis of genetically engineered human insulin in E coli bacteria, helping bypass problems of an allergic reaction. Genentech funded this research, and by 1982, the biosynthetic form of human insulin, ‘Humulin,’ was commercially available Nowadays, insulin comes in various forms regular human insulin, rapid acting, and long lasting insulin packaged in easy to use insulin pens or pumps. Though insulin is not a cure for diabetes, millions of patients have this lifesaving drug thanks to decades of dedicated and painstaking research by scientists like Banting
November is National Diabetes Awareness Month, and the International Diabetes Federation has dedicated the birthday of Dr. Frederic Banting (November 14), as World Diabetes Day.

STANFORD SDIGITAL TANFORD




TRANSFORMATION TRANSFORMATION CERTIFICATE CERTIFICATE
ENRICHMENT
OVERVIEW
The program encourages techniques to fundamentally change how work is done to ensure the organization grows and remains competitive. The self paced, year-long series of 9 courses brings together proven tools and techniques, covering topics ranging from HR, Finance, Marketing, Manufacturing, and Sales.
skills to build excelling teams in digital culture collaboration skills with efficiency and agility leadership and analytical skills customer service skills
COMMITMENT
9 total courses certificate (375 day access) and 5 8 hours to complete each course Individual courses (60 day access) and 2 hours per week recommended
E mc= 2
Tof heory
Relativity
by Rita ShahadaImagine that you are overshooting the Earth at the speed of light, crossing the galaxies, stars, and planets, figuring out the future across very long distances in just a few days while your family grows many years older. Is it a strange and imaginary thing?
ALBERT EINSTEIN
Albert Einstein is considered one of the greatest minds of this century. He is a German physicist, born on 14 March 1879. He had the honor to discuss and prove the most complicated issue that has influenced the world.
PHYSICS
Physics is one of the natural sciences and deals with substance, energy, the movement of molecules, and the causes of those movements It is divided into classical physics and modern physics
Classical physics deals with topics on the macroscopic scale, which can be studied with the largely unaided five human senses In contrast, modern physics focuses on the nature and behavior of particles and energy at a submicroscopic level In general, the laws of classical physics are not applicable or can only be applied as approximations to the laws of modern physics
Special RelativityTheory of the Structure of Spacetime
Albert Einstein, in his theory of special relativity, determined that the laws of physics are the same for all non accelerating observers, and he showed that the speed of light within a vacuum is the same no matter the speed at which an observer travels This led him to conclude that space and time are interwoven into a continuous continuum known as space time Events that occur at the same time for one observer may occur at different times for another
General Relativity -
Theory of Gravitation
General relativity explains the law of gravitation and its relationship to other natural forces It applies to cosmology and astrophysics, including astronomy
Energy equals mass times the speed of light squared.
COVID-19 CIMPACT OVID-19 IMPACT AND AINNOVATION ND INNOVATION THROUGH THE TCRISIS HROUGH THE CRISIS
BY: MAHIRAH MOHD NORAZINANAn Employee wearing VF helmet monitors at Turkey's Istanbul Airport

The Fisher Fine Arts Library at the University of Pennsylvania

MESSAGES
As reported by the World Health Organization (WHO) website, the number of confirmed cases of COVID-19 has reached more than 105 million, and more than 2 million people have died as a result. In response to the deadly effects of the pandemic, people worldwide must now adapt to new norms to be safe from this crisis. Some of the new norms include wearing a mask, maintaining a reasonable social distance, practicing personal hygiene such as washing hands with soap or hand sanitizer, avoiding crowded places, closed-contact settings, and confined spaces. With the advent of the new pandemic era, many innovations have been developed to mitigate the COVID-19 impact to help people and businesses survive for a more extended period of time. Several innovations have been seen in the healthcare, education, and technology industries.
MESSAGES


AreportfromtheMinistryofHealthMalaysiasummarizes aninnovationbyDr.LaiHsienyungcalledtheAerosolBox, whichisatransparentplasticcubewithtwoarmholesthat doctorscanusetoperformintubationswhileprotecting themfromtheCoronavirus Itwasdevelopedinresponse totheshortageofpersonalprotectiveequipment(PPE)for physicians.Thisboxcanbereusedifitisthoroughly cleanedwithalcoholorbleach
SomehospitalsintheUnitedStatesofAmericausea similarboxcalledaPlexiglasboxforintubationandother aerosolproducingprocedures.Anotherinnovationinthe healthcareindustryis3Dprintedearguardscreatedbya 13yearoldboynamedQuinnCallander(WorldScouting, 2020).Thepurposeoftheearguardsistoreducepain causedbywearingmasksfortoolong Thisearguardis designedtobeprintedusinga3Dprinterandhas differentshapedheadsandfacesthatcanbeadjustedto fitthemaskcomfortably,especiallyforhealthcare workerswhomustwearthemaskforanextendedperiod oftime.Also,therewere3Dprintedfaceshieldsand ventilatorvalves Crossfunctionalteamsconsistingof scientists,physicians,andwebdevelopershave establishedcentralizeddataanalyticsandvisualization hubstodeterminetheextentoftheCoronavirusvirus outbreakworldwide.Theprimaryinnovationin healthcareisthedevelopmentoftheCOVID19vaccine. Thevaccinedevelopmentprogramshaveinvolvedpublic privatepartnershipsandcollaborationswith biotechnologycompanies,globalpharmaceutical companies,andacademicinstitutions On2December, theCOVIDvaccinemadebyPfizerandBioNTechhas becomethefirstfullytestedimmunizationthathasbeen approvedbyFoodandDrugAdministration(FDA)under EmergencyUseAuthorization(EUA)tobeusedfor coronavirusprevention(SolisMoreira,2020) Asaresult ofthehighdemandandurgencyoffunding,thisvaccine wasdevelopedveryquicklycomparedtoothervaccines.
Technological innovation during Coronavirus has also caused the use of robots to do a specific task. In their article, Luo and Galasso (2020) stated that in China, robots were designed to send medicines, meals, collect rubbish, and bedsheets in the hospital. They also gave the example of a big e-commerce company that uses a drone to drop parcels and spray disinfectants. The refugees developed a LEGO robot at the refugee camp in Jordan to reduce the risk of infection by automatically dispensing hand sanitizer. In Japan, "Ugo," the remote-controlled robot, can be used to kill viruses as it has a UV-C sterilization band to clean surfaces. Not just that, robots are also being used for food deliveries. In the US, COVID-19 delivery robots carry food delivery boxes on wheels to various areas from Milton Keynes, England, to Fairfax, Virginia, U.S. In the fighting of this pandemic, people need to be reminded about social distancing when going out. A robot dog in Singapore is used to remind visitors to stand at least one meter apart for the people's safety and for people in the surroundings to protect themselves from the spread of infection (World Economic Forum, 2020). As a precautionary step, some countries like China, Italy, and Dubai have applied the smart helmet to monitor people with symptoms of COVID-19, like a fever, from a distance of two meters (Ghosh, 2020). Police, health staff, transport workers are among the people who use this helmet. In Turkey, some employees at the Istanbul Airport use similar helmets, a thermal imaging VF helmet to scan the people's temperature that might have the possibility of

Thecurrentcrisisalsoimpactstheeducationsector Despitelockdownsandquarantines,whichareintended tolimitthespreadofCoronavirus,educationshouldnever beputonhold Thedistancelearningclasshasreplaced thefacetofaceclass.Teachersandstudentsinteract usingonlinelearningtools.Therearetelevisionchannels inMalaysiawitheducationalprogrammingthatallows studentstolearnfromhome,especiallythosewhodonot haveaccesstotheinternet Additionally,theMinistryof EducationofMalaysiahaslaunchedanonlinelearning platformcalledEduwebTVforstudentsfrompre kindergartentosecondaryschool,withdigitaltextbooks availableonline,whichenablesstudentstoacquire knowledge(Karim,2020).Educatorsuseotheronlinetools forassessmentandhomework,includingGoogleForms, Kahoot,andMoodle.Educatorsusuallyusevideo conferencingtoolslikeGoogleMeet,ZoomMeetings, CiscoWebexMeeting,andSkypeMeetNow Aninnovative ideademonstratedbyagroupofstudentsfromStanford Universityinvolvescreatingagamifiedvirtualcampus called"ClubCardinal"Throughthisplatform,studentscan experienceuniversitylifeeventhoughmanycampuses havebeenclosedduetothepandemic ClubCardinalisa freewebsitethatperformsinteractiveactivities,lettingits userscreatetheiravatarsandselectitemsfromthevirtual store UserscanalsoexplorethevirtualStanfordcampus viaamap AccordingtooneofClubCardinal'screators, AllisonZhang,incomingstudentsusethesitetoknow theirfutureclassmates(Matchar,2020) Studentsfrom otheruniversitieslikeMIT,UCLA,ColumbiaUniversity,and theUniversityofMinnesotahavealsobuilttheirvirtual campusesontheMinecraftvideogame(Anderson,2020)
There has been a significant impact of the Coronavirus on all people in the world. People need to think creatively and develop new strategies to adapt to the scenarios we are facing now. Individuals must become more aware of their personal hygiene and take additional precautions to prevent infection. The Coronavirus has sparked health care, education, and technology innovations in the past few years. The innovations made through this crisis are really unique and helpful to the population. The new norms must be followed for perhaps a few more years. Still, we need to fight this virus together in some ways, such as staying at home, going outdoors only when absolutely necessary, maintaining physical distance, following the guidelines from WHO, and obtaining a vaccination if needed. Our hopes will live on, and we will be able to conquer this COVID-19 one day, and eventually, we'll be able to go back to normal life.
CLUB

WHAT IS FEMINISM?
By Rawan YosefI think you have heard that word before, and maybe you know what it means or not, but today I will explain to you more than you can imagine.
Feminism is a group of social theories, political movements, and moral philosophies centered on female issues It is present in various human pursuits, from the arts to the sciences, although with varied activity and interest levels In the area of political rights, the struggle by feminist movements for equality with men was one of the oldest and most important for women ' s movements. Nevertheless, gender equality didn't become a common practice in global politics until the mid-1980s. It originated from progress in development policy and research related to peace. At the end of the eighties, the first wave of work on gender equality arose, which can be reduced to four main variations or branches.
The first branch, "The liberal theory of equality between the sexes, " asked the following question: Where were women in international politics? This theory served to highlight the extent of women ' s involvement in global politics, how they were excluded from power, and from playing an active role in political life, and how they fought back to ensure that women enjoy the same rights and opportunities as men. The second branch of the theory of gender equality is "Socialist / Marxist equality." Marxist equality implies inequality between men and women is the outcome of capitalism, while socialist equality emphasizes the historical oppression of women and patriarchal systems. As per this theory, overthrowing capitalism is the only way to achieve equality, given that it is an oppressive system for women The third branch would be "postmodernism," which is essentially a social structure for the differences between women and men and not on women specifically. It highlights the role assigned to both women and men in global politics and how international politics has contributed to the production of certain women men. The liberal theory of gender equality shows the extent of women ' s involvement in global politics and the methods of excluding them from power. The fourth branch is "forward looking equality between the sexes. " Here, the central goal is to re describe the truth from a female perspective and construct a female version or vision of the truth and the world.
FIRST FEMINIST
Christine de Pisan challenged prevailing attitudes toward women with a bold call for female education.
FEMINIST HISTORY
Feminist history refers to the re reading of history from a woman ' s perspective.
The tradition of writing about feminism as an idea related to women ' s struggle for rights, their unfair treatment, and demeaning of their status far predates the field of politics and international relations by centuries. It started as an idea at the beginning of the fifteenth century. It was first emphasized by the French secularist, Christine de Pizan, in her book, "The Book of the City of Ladies," where she stressed, "The value of the individual in life is not in the body as a gender but in the perfection of behavior and virtues." Similar writings continued during the next 400 years from several women who did not define themselves as "feminists." The word or term "feminism" did not appear until the nineteenth century
Among the recent books issued on contemporary feminism, which dealt with the above topics, is the book of Professor of Languages and Communication at Worcester College Oxford / Deborah Cameron. The first edition was published in English in 2018, under the title "Feminism." It focused on the Western experience, particularly the Anglo American, and did not mention feminist experiences outside the Western knowledge system. The author has worked on Western women ' s issues, starting with economic and social equality issues in the workplace and wages, sexual exploitation and abortion rights, and several other issues that are typically silenced outside the Anglo American society It also includes the views of some Muslim feminists in the West, especially regarding women ' s dress, the burqa and the niqab, and the influence of extremist movements and populism in the West, Russia, India, and Turkey on restricting feminist movements. It will help if you read this book regardless of whether you are male or female.
Lastly, not many are involved with and support the feminist movement. Still, the fundamental idea that women are human beings first and foremost will persist regardless of whether we believe in it or disregard it. I hope you enjoyed reading my article and learned something new.
"Any sufficiently advanced technology is indistinguishable from magic"

- Sir Arthur C. Clarke, Author of A Space Odyssey
