VIDEO FOR COMPELLING CUSTOMER EXPERIENCES

 Loubna
Loubna

Winners of CISO Awards and Future Security Awards 2022 WWW.EC-MEA.COM PAGES 72 VOLUME O9 | ISSUE 10 JUNE 2022
If a picture is worth a thousand words, imagine the importance of video in creating lasting customer experiences.
Imenchal Head of Video Collaboration, Logitech.
BRILLIANT OP TIC S. AMA ZING DE SIGN.
Increase in video meetings in 20201
Grow th of UC meetings with video from 2019 to 20202
11% 400% 71% 274%
Information workers who rarely or never use video in meetings3
Information workers who use video at least once a day3
ADVANTAGE S OF R ALLY BAR
Superior Audio and Video: A video bar engineered for midsize rooms, featuring a motorized PTZ lens, adaptive beamforming mics, support for two


Flexible D eployment Options: Run meetings in appliance mode without a computer for Microsof t Teams, Zoom, GoTo, Pexip, or RingCentral Or, connect to a computer or laptop and use with any sof tware
Simple Setup and Cable Management: Place on a table or credenza, or add a wall or TV mount for a sleek space-saving set up Integrated cable management keeps connections tight

Easy to monitor, manage, and suppor t: Stay informed and ahead with metrics like people count
MAKE EVERYONE LO OK AMA ZING.
Medium room solution with Logitech Tap for Microsoft Teams Rooms
Mixing AI and video
In this month’s lead feature Loubna Imenchal from Logitech builds a case in favour of video. Loubna points out, if we want to create compelling customer experiences, the implementation of video is essential. Over the last few years, we have seen brands broadly using video to showcase their personality through social media and create connections with their customers by sharing interesting, engaging stories.
However, usage of video as a marketing tool is just one side of the coin. Video can in fact add value to customer experience in many more ways. Video’s full potential for improving customer experience has yet to be realised, but the opportunities are exciting.
To elevate customer experience, video must play a key role in an omnichannel strategy. Moreover, high quality video is a prerequisite so customer experience video production must meet high standards. And when it comes to interacting with customers via live video, the quality must be exceptional with virtually crystal-clear sound, says Loubna.
When paired with live video, conversational commerce can also take off. By leveraging the power of AI, if customers show interest in purchasing a product, a query can escalate from a chatbot to a video chat with a sales representative. This allows the company to better understand its customers’ needs and offer an enhanced service with recommendations, possibly leading to higher valued sales engagements.
An interesting feature this month is the correlation between Internet traffic and timing of Ramadan in various countries. Depending on the country, there are clear shifts and changing patterns in Internet use, particularly before dawn and after sunset.
In some countries, the impact is so big that you can see in Internet traffic charts when the sun sets. Sunrise is more difficult to check in the charts, but in the countries more impacted, people wake up much earlier than usual and were using the Internet in the early morning because of that.
Afghanistan, Pakistan, Indonesia, Morocco, Libya and Turkey had the biggest increase in traffic before sunrise. After sunset, it was Saudi Arabia, Tunisia, Bangladesh, Pakistan that showed a clear decrease in traffic after sunset.
On 17 May, the sixth edition of the annual CISO Awards and Future Security Awards 2022 were presented in Dubai, UAE. The annual mega event continued its tradition of recognising outstanding individuals and companies in the field of cyber security. The award recognises the top CISOs who are using technology to secure critical business information assets and minimise risk while delivering business value.
Turn these pages to see the 75+ winners of these awards, read our thought leadership guest columns and other features.
Happy reading and summer breaks. ë
ARUN SHANKAR, EDITOR
ARUN@GECMEDIAGROUP.COM
MANAGING DIRECTOR
TUSHAR SAHOO
TUSHAR@GECMEDIAGROUP.COM
EDITOR
ARUN SHANKAR
ARUN@GECMEDIAGROUP.COM
CEO
RONAK SAMANTARAY
RONAK@GECMEDIAGROUP.COM
GLOBAL HEAD, CONTENT AND STRATEGIC ALLIANCES

ANUSHREE DIXIT
ANUSHREE@GECMEDIAGROUP.COM
GROUP SALES HEAD
RICHA S
RICHA@GECMEDIAGROUP.COM
EVENTS EXECUTIVE
GURLEEN ROOPRAI
GURLEEN@GECMEDIAGROUP.COM
JENNEFER LORRAINE MENDOZA JENNEFER@GECMEDIAGROUP.COM
SALES AND ADVERTISING
RONAK SAMANTARAY
RONAK@GECMEDIAGROUP.COM
PH: + 971 555 120 490
DIGITAL TEAM
IT MANAGER
VIJAY BAKSHI

DIGITAL CONTENT LEAD
DEEPIKA CHAUHAN
SEO & DIGITAL MARKETING ANALYST HEMANT BISHT
PRODUCTION, CIRCULATION, SUBSCRIPTIONS INFO@GECMEDIAGROUP.COM
CREATIVE LEAD
AJAY ARYA
GRAPHIC DESIGNER
RAHUL ARYA
DESIGNED BY
SUBSCRIPTIONS
INFO@GECMEDIAGROUP.COM
PRINTED BY Al Ghurair Printing & Publishing LLC. Masafi Compound, Satwa, P.O.Box: 5613, Dubai, UAE # 203 , 2nd Floor G2 Circular Building , Dubai Production City (IMPZ) Phone : +971 4 564 8684
31 FOXTAIL LAN, MONMOUTH JUNCTION, NJ - 08852 UNITED STATES OF AMERICA PHONE NO: + 1 732 794 5918
A PUBLICATION LICENSED BY International Media Production Zone, Dubai, UAE @copyright 2013 Accent Infomedia. All rights reserved. while the publishers have made every effort to ensure the accuracyof all information in this magazine, they will not be held responsible for any errors therein.
















Upgrade Your Office With Smart ICT Devices Stocks Available, Delivery In 2 Weeks Contact Us: enterpriseME@huawei.com e.huawei.com/ae Please Scan for More Information Ideahub OceanStor Storage Enterprise Networking OceanStor Storage Wi-Fi 6 | LAN Access Switches | Data Center Switches | Routers IdeaHub Pro and IdeaHub Board Pro
SPECIAL REPORT
32-35
Impact of Ramadan on Internet traffic in Middle East and Asia
PRODUCTS
36-37
Synology: Deploying data protection for small businesses
41-43
IceWarp: Challenging the incumbents in collaboration


54-57
REAL LIFE
GUEST COLUMN


58-59
HR, IT need to jointly monitor inside threats
60-61

CASB, an organisation’s cloud cybercop
62-63
Building Zero Trust framework in anOT-IoT environment
64-65
Using AI to build online catalogues for marketplaces
66-69
SOCIALLY SPEAKING
70-71
EXECUTIVE APPOINTMENTS
CONTENTS 06 VIEWPOINT Product lifecycle management has never been more disrupted 10-21 EVENTS GCC Security Symposium announces 75+ winners of CISO Awards and Future Security Awards 2022 23-28 CHANNEL 30-31 CHANNEL STREET Yegertek: Managing endto-end customer experience 07 VIEWPOINT Cyber fusion centre replacing SOC 08 VIEWPOINT Complexity of customer service stack only increases 09 VIEWPOINT Getting IoT to support use cases in other industries
JUNE 2022 VOLUME 09 ISSUE 10
38-40 COVER STORY Logitech:
of video is more than a picture MEA 05 JUNE 2022
Power
PRODUCT LIFECYCLE MANAGEMENT HAS NEVER BEEN MORE DISRUPTED
Companies must recognise the importance of centralising data for better visibility across their operations to stay competitive in a recovering marketplace.
If the last twelve months are anything to go by, it is imperative for companies to show agility and adaptability to face the challenges of today and tomorrow. While these buzzwords are thrown around all too often, what has become evident is that data-driven insights that allow companies to obtain true visibility over their operations are the bedrock to make informed decisions when these obstacles arise.
With global supply chains impacted due to global conflict and sanctions, the continuing lockdown on China’s east coast, shortages of container and ship rotations, just to name a few, managing data and insights out of primary and secondary supply chains, is now absolutely vital.
As companies emerge from a prolonged period of uncertainty, how they perform over the next twelve months will be centred on finding operational efficiencies and their commitment to sustainability initiatives.
There has been signs of slow recovery in global supply chains in late 2021. Global freight expert DHL’s recent Export Barometer Report indicated that nearly two-thirds of local traders are expecting exports to rebound in the new year, and 59% are predicting export revenue will return to pre-pandemic levels by the end of 2022.
IDC predicts that manufacturers that are facing increased disruption will digitally transform and accelerate sustainable innovation to improve supply chain operations from concept to commerce, increasing revenue by 20% in 2025.
However, global supply chains will still be very fragmented for the foreseeable future.
Companies must understand the need for a centralised data infrastructure that allows them to have complete, aligned oversight across their processes in order to truly embrace the power of intelligent data.
While mining and manufacturing companies may initially feel impeded by sustainability regulations and investor pressure, there are ways for them to both increase their efficiency as well as their compliance through investment in intelligent data.
Adoption of data-based technology and data-driven insights will allow these companies to monitor entire asset lines in real-time, providing the basis for long term organisational objectives that will increase their capabilities to deliver on sustainability targets, while boosting revenue and profitability.
While some companies may feel that their current ERP, EAM and scheduling optimisation systems allow them to make informed analyticsbased decisions, what is clear is that system fragmentation is the single
largest impediment to transformation and innovation for assetintensive industries such as mining and manufacturing.
Companies must adopt greater oversight on product lifecycle management, at every point of the supply chain, which has never been more disrupted. Insights drawn from intelligent data can allow companies to reap the benefits in the long run.
Companies must recognise the importance of centralising data for better visibility across their operations to stay competitive in a recovering marketplace.
While many companies believe they have the right foundation, too many incorporate complex and disparate systems that are inefficient in gaining real-time oversight of processes. Given the complexities of solutions available to companies today, processes must be streamlined, and data centralised to optimise production, and reduce manual intervention.

Creating digital infrastructure that optimises efficiencies – such as AI,ML applications, ERP, S&OP, EAM and MES – can achieve greater transparency, while driving new efficiencies that extend product and asset lifecycles, reduce waste and provide feedback mechanisms to support the circular economy, that can only benefit in the long run on the road to recovery.
For companies to succeed, optimising performance – through greater visibility over their processes, and harnessing the power of insights driven by intelligent data – will be crucial both today and tomorrow. ë
JASON PEARCE
IFS APJ and MEA, Chief Technology Officer.
VIEWPOINT 06 JUNE 2022 MEA
Processes must be streamlined, and data centralised to optimise production
CYBER FUSION CENTRE REPLACING SOC
The cyber fusion centre is technologically agnostic, taking away heartaches that customers experience while being forced to upgrade during operations.
Traditional approaches to cybersecurity are falling short of meeting the demands of today’s rapidly changing threat landscape. Organisations worldwide are trying to cope with the threats by bringing multiple teams into the picture – including system security, IT security, and digital teams.
This has however, resulted in silos within organisations and other related operational challenges. The good news is that these challenges can now be greatly mitigated and dealt with thanks to the advent of the cyber fusion centre.

The cyber fusion centre brings together under the same roof different security functions such as event analysis, automation and orchestration, and incident response, strengthening a company’s ability to effectively respond in a timely manner when security incidents emerge. The cyber fusion centre is a cybersecurity saviour, acting as a next-generation security operation centre with much greater diligence and effectiveness than traditional security operation centres.
Traditionally, organisations host the security operation centre software and hardware themselves and build internal teams to run them. However, the cyber fusion centre takes away the burden of evaluating, procuring, hosting, implementing, configuring, and updating those other technologies require.
Instead, all of these are offered as a platform billed on a monthly basis. The highly skilled team of analysts and engineers do all the heavy lifting of monitoring, triage and analysis, notification and detailed remediation support. Where traditional security operation centres can take up to a year to be stood up and optimised, the cyber fusion centre can be deployed and delivering meaningful results in a matter of weeks.
Traditional security operation centres are built around the SIEM Security Information, Incident Event Monitoring foundation, the primary reporting and dashboarding toolset at the centre of information gathering. Many different technology systems help create the infrastructure of security operation centres, and typically their integration is a daunting task. Several people and teams are responsible for different aspects of the security tool-stack, such as network monitoring and endpoints.
This process can quickly become inefficient during an incident. The traditional security operation centre response is similar to that of a firefighting system. The system only reacts when something goes wrong. Teams take an assembly line approach – doing their individual part, passing on the incident to the next team. This is time consuming and often misses the
cohesive larger picture leading to a blame-game.
While traditional security operation centres may have proved successful in the past, modern threats are much more sophisticated and prone to do more damage in less time. Traditional security operation centre technologies get outdated quickly and are therefore unable to cope with the consistently evolving threats.
The cyber fusion centre is different by design and is proactive by nature. It utilises a collaborative intelligence-driven approach to stay ahead of emerging security threats. The cyber fusion centre is also technologically agnostic, taking away the heartache that customers experience whilst being forced to upgrade or swap tools whilst running their operations.
While it has been well known that it is essential to integrate people, processes, and technology, the cyber fusion centre as its name implies seeks to create a fusion of people’s mindsets, practices, and tools, resulting in a unified approach that produces significantly better output.
Cyber pandemics will continue with new variants of threats emerging every day. With the growth of these threats, defences against them must be expedited. Cyber fusion centre serves as an effective vaccine for businesses today, not only improving an organisation’s threat detection and protection capabilities but also streamlining systems and assimilating information into actionable strategies and tactics, reducing costs and improving productivity. ë
DENNIS OOMMEN
Senior Cybersecurity Product Manager, Injazat.
VIEWPOINT MEA 07 JUNE 2022
Modern threats are much more sophisticated and prone to do more damage in less time
COMPLEXITY OF CUSTOMER SERVICE STACK ONLY INCREASES
Here are three ways IT teams can cut costs without sacrificing the quality of customer experience being delivered for B2B and B2C customers.
With rising inflation costs and increasing customer expectations, delivering effective customer experiences is becoming more costly and time-consuming.
But this is not just a priority for customer-facing teams, IT teams also need to focus on how they can equip the organisation to deliver better customer experiences more efficiently.
In order to deliver excellent experiences customers are expecting on the front-end, IT needs to ensure that the backend technologies and systems run smoothly. But trying to manage and scale a complicated customer service technology stack will only prove more difficult as the business grows.
Instead, IT teams need to evaluate how they can operate more efficiently to both reduce cost-to-serve and improve the quality of the experiences delivered.
Decreasing cost-to-serve cannot not come at the expense of customer experience. Being able to deliver experiences more efficiently will be of no benefit if these experiences are not helpful to customers.
So here are a few ways IT teams can begin to increase internal efficiency and reduce customer service expenditures, without sacrificing the customer experience:
EMPOWER CUSTOMERS
Digital self-service is key to decreasing cost-to-serve. Self-service is not only the preferred method for customer interactions, but also helps businesses save more than $7 per interaction for a B2C company and $13 for a B2B company.
With self-service, customers are able to get the answers and information they need more quickly without needing to contact a sales representative. This approach enables customers to scale their customer service strategy more efficiently. So instead of relying solely on live channels, IT teams can leverage self-service to improve the quality and consistency of the experiences delivered, like making sure customers know where to find the products and information they need.
ACCELERATE WITH AUTOMATION
Another effective way to reduce costs is to identify opportunities to automate processes. For example, many B2B organisations have complicated and lengthy ordering and approval workflows. Automate and accelerate this process to both save time for the business and the customer.
Another critical process that can be improved with automation is

onboarding. Onboarding customers is incredibly important, as the success of onboarding will play a key role in whether the customer decides to stay or not.
However, B2B onboarding takes roughly three months and involves 4-6 different tools. It is no wonder customers are having a difficult time onboarding and getting started quickly.
With automation, businesses can accelerate many of the forms, processes, and workflows needed to onboard customers properly.
PROVIDE A SINGLE SOLUTION
These different cost-saving tools will become costly to manage and difficult for customers to navigate. Bring everything together under a single solution to resolve both of these problems.
With a unified customer portal, businesses are able to deliver a single, secure solution for customers to access the content, information, and processes they need. Customers can quickly find what they need without having to go through different touchpoints.
Additionally, unifying systems and applications together makes it easier for businesses to manage and update. Instead of managing an unruly customer service tech stack, businesses can save time and effort by delivering an effective customer portal.
While delivering excellent customer experience should be a business’s main priority, it does not need to be your main expense. With the right strategy and tools in place, you can provide the experiences your customers are looking for more efficiently. ë
MOUSSALAM DALATI General Manager, Liferay Middle East.
VIEWPOINT 08 JUNE 2022 MEA
B2B onboarding takes roughly three months and involves 4-6 different tools
GETTING IoT TO SUPPORT USE CASES IN OTHER INDUSTRIES
IoT remote monitoring is already being used for connected sustainable equipment, so what can equipment makers in other industries learn from their success.
Operating fine-tuned machines located in harsh, remote environments is not for the faint-hearted, but the Internet of Things can make it easier. Wind power is a great example of this. Imagine giant turbines sitting offshore. Every day there are potential hazards – wind, waves, heat, cold. Hardware can be damaged, sensitive electronics destroyed, resulting in customers being deprived of reliable power.
There are some lessons to be learned from this industry. IoT remote monitoring is already being used for connected equipment to deliver greater efficiency, cost performance, uptime, and customer value. So, what can equipment makers in other industries who want to make smart, connected products learn from their success? Forrester outlines three of them for industrial IoT.
#1 COMMUNICATING WITH REMOTE ASSETS
Wind power is an extreme example, most industrial facilities are not located dozens of miles offshore. Factories may be closer, but it is impractical to connect hundreds or thousands of sensors to the cloud for collecting and analysing the data. Instead, processing data on the edge, close to the source of information, reduces latency, increases security and cuts networking costs. IoT edge computing is the key to fast analytics, no matter where your asset is located.
#2 INTEGRATING HARDWARE WITH SOFTWARE
Information technology, the domain of enterprise systems and data processing, and operational technology, which manages and controls industrial operations in near-real time, are two very distinct environments in a factory. Bridging that IT-OT gap can generate deeper insights from IoT edge data and take actions to deliver better services. IoT application and data integration is key to generate the most value from industrial IoT.
#3 ABOVE ASSET MANAGEMENT
While it is true that most smart equipment makers start with remote monitoring to learn how products are being used, Industrial IoT can deliver value far beyond that. From there, predictive maintenance is a natural next step by analysing the data from IoT remote monitoring including applying machine learning to anticipate problems before they arise and reduce downtime for customers.
And, with overall equipment effectiveness, smart machine makers can deliver the trusted standard for measuring machine availability, performance and quality. But that is just the start. As they climb the IoT maturity
curve, they can differentiate their products through new services and performance.
At the height of this IoT maturity curve, manufacturers can transition from equipment sales to equipment-as-a-service, EaaS business models. Customers see reduced up-front expenses and costs that scale with their needs, manufacturers can build a longer-term relationship that includes high-margin services. The Roi for smart products starts here and many customers are moving up the IoT maturity curve.
Nordex, one of the world’s largest wind turbine manufacturers, is using IoT remote monitoring at the edge to improve real-time operations at its wind farms. With a platform that enables it to manage up to 5,000 real-time parameters, it can monitor, gather, and process real-time data, and remotely manage equipment. It has been able to cut the cost of energy by 2% through minimisation of operations and maintenance and increase total annual energy production by 1-2%.

Dürr, which makes, and services robotic paint stations used by major vehicle manufacturers, is using IoT at the edge to seamlessly record all data from the automotive painting process. With this approach it is reducing errors, lowering manufacturing costs, and accelerating the speed of decision-making.
SMC, which specialises in manufacturing pneumatic equipment for manufacturers, is using IoT at the edge to deliver predictive maintenance and real-time insights. With smart field analytics, SMC can deliver the granular data that its customers demand and help them achieve their sustainability, money saving, and efficiency goals, plus much more. ë
VIEWPOINT
DR JUERGEN KRAEMER, General Manager for IoT and Analytics, Software AG.
MEA 09 JUNE 2022
Customers see reduced upfront expenses and costs that scale with their needs
GCC Security Symposium announces 75+ winners of CISO Awards and Future Security Awards 2022

EVENTS
10 JUNE 2022 MEA
On May 17, the sixth edition of the GCC Security Symposium and CISO Awards 2022 presented by Global CISO Forum and GEC Media Group was successfully held at Conrad Hotel Dubai, UAE. The annual mega event continued its tradition of recognising outstanding individuals and companies in the field of cyber security. The event witnessed participation of top IT leaders and decision makers who exchanged critical knowledge on the modern-day vulnerability landscape.
GCC Security Symposium and CISO Awards 2022 official event partners were Cloud Box, Human, BeyondTrust, Cohesity, Infinite Blue,

Digital Track | Paesslar,
The Cyber Sentinels CISO Awards 2022 recognised the hard taskmasters of security in the digital enterprises and felicitated their unwavering commitment towards their organisation’s security infrastructure. The award recognised the top CISOs who are using technology to secure critical business information assets and minimise risk while delivering business value.
EVENTS
Cloudsek, Multipoints | HCL, RNS, Checkmarx | Cyberknight, Atos, Finesse, Help AG, Valto | Accops, Redington | DigiGlass, and Cybereason.
MEA 11 JUNE 2022
CISO Awards 2022
The winners of the CISO Awards 2022 include Abbas Sabuwala, Hafiz Sheikh Adnan Ahmed, Zaheer Kadir Kazi, Bader Husni Zyoud, Mhd Wail Khachfa, Kamal Setty Iyappan, Jacob Mathew, Hamed Shahbar, Zaheer Shaikh, Ahmed Nabil Mahmoud, Mohammed Ahmed Al Doseri, Tushar Vartak, Ashok Prasanna Tharmia Gnanasekaran, Shahab ud din, Shoeb Adhoni, Hussain AlKhalsan, Mohammed Alshamrani, Amrut Sugandh, Nitin Shingari, Mohamad Mahjoub, Goutam Pudota, Philippe Lopez, Ayoub Fathi, Rajabali Wishiwala, Manoharan Mudaliar, Sheridan Moodley, Bilal Ahmad, Hesham Saad Aly, Salman Hussain, Glen Thomas, Marzouq Al Nuaimi, Saghir Ahmad Khan, Ashish Khanna, Aliasgar Bohari, Awais Bin Imran, Mudassar Ali, Samer Abu Hayah, Padam Sundar Kafle, Ramakrishnan Natarajan, Jamal Mohammed Abdul Sattar, Amit Bhatia, Hoda AlKhezaimi, Finto Thomas, Tilak Ratnayake, Neil Haskins, Jeevan Badigari, Ahmad Darwish Ali, Velmurugan Segamani, Mario Foster, Meshal Alotaibi, and Anoop Paudval.



EVENTS 12 JUNE 2022 MEA





EVENTS MEA 13 JUNE 2022





EVENTS 14 JUNE 2022 MEA





EVENTS MEA 15 JUNE 2022





EVENTS 16 JUNE 2022 MEA





EVENTS MEA 17 JUNE 2022





EVENTS 18 JUNE 2022 MEA





EVENTS MEA 19 JUNE 2022
Future Security Leaders Awards 2022


As the threat landscape becomes increasingly vulnerable these days, there is no end to innovation and no limit to betterment when it comes to enterprise security solutions. During the sixth edition of the GCC Security Symposium, the Global CISO Forum Future Security Awards 2022 recognized the security vendors, VADs, System Integrators and Resellers who has walked the extra mile in innovating their solutions and services for the customers and redefined the term value in security offerings.

The winners of the Future Security Leaders Awards 2022 include Help AG, Axon Technologies, Accops Systems, Atos, Human Security, CyberKnight, Cloud Box Technologies LLC, Valto Information Technology LLC, Potensia Systems and Checkmarx.
The award ceremony was a platform to showcase their achievements, share their expertise and knowledge.

20 JUNE 2022 MEA
EVENTS






EVENTS MEA 21 JUNE 2022





CELEBRATING ENABLING ◄ ► SECURING DIGITAL TRANSFORMATION Al Chatbots • Bl & Analytics • Blockchain • CRM/CEM • Robotic Process Automation • Managed IT Services • DIGITAL TRANSFORMATION • Digital Risk & Compliance • Zero Trust • Cloud & Application Assurance • Digital Identity • Data Protection & Privacy • Managed Security Services MENA I APAC AMERICAS 400+ ProfessionalTeam I 300+ Enterprise Clients I 50+ International Awards I 10+ Global Locations I 20+ Nationalities
Evanssion to stage cyber drills to test regional resiliency through partnership with CYBER RANGES
Evanssion, a value-added distributor specialised in Cloud Native and Cybersecurity across the Middle East and Africa, has announced its distribution partnership with CYBER RANGES by Silensec, a next-generation military-grade full-contentlifecycle cyber range for the development of cyber capabilities and the assessment of competencies and organisational cyber resilience. As per the terms of the partnership, Evanssion will deliver the full extent of CYBER RANGES’ portfolio of world-class cybersecurity training and capability development exercises to enterprises in the Middle East region.

Human behaviour continues to be the biggest cause for security breaches, amounting for up to 95% of them. The evolving business models and changing market circumstances are also further expanding the attack surface leaving security teams stretched thin. Regional businesses must evaluate their preparedness should an attack happen and assess if their resources are capable to handle those incidents efficiently.
Gartner predicts that by 2022, 15% of larger enterprises will be using a cyber range to develop the skills of their security teams, up from less than 1% currently. CYBER RANGES can help regional organisations prepare and withstand cyberattacks by creating exercises with real-life attack scenarios in an isolated secure environment.
Evanssion together with its extensive partner network will create awareness and large-scale cyber drills for organisations in the region to test their cyber resiliency through CYBER RANGES offerings. The distributor will also hold training sessions for its partners to help them get well versed with CYBER RANGES solutions to be better equipped to position it to regional customers.
stc, Alibaba Group, eWTP Arabia, Saudi Company for AI, Saudi Information Technology, launch Alibaba Cloud

stc Group, announced the establishment of Alibaba Cloud in Riyadh, for high-capacity cloud services in partnership with the Chinese technology giant, Alibaba Group, eWTP Arabia for Technical Innovation, the Saudi Company for Artificial Intelligence. and the Saudi Information Technology Company.
The establishment of the new company in the Saudi capital, Riyadh, came in response to the significant increase in demand for cloud computing services and solutions in the region. The company will provide advanced cloud computing services to companies operating in the Kingdom of Saudi Arabia, ensuring that they employ the highest standards of security and protection.
CHANNEL MEA 23 JUNE 2022
Navneeth Ramanan Assistant Vice President Sales for Evanssion.
AVEVA partners with Kent, a global energy services partner, to design new digital frameworks

AVEVA, signed a memorandum of understanding with Kent, the leading international integrated energy services partner, to mutually explore and design new frameworks for applying digital solutions across the energy industry. The partnership will allow energy customers around the world to leverage both companies’ strengths to drive their digital transformation and sustainability objectives in innovative ways. Kent will utilise AVEVA’s platform to reinforce its position as a top global energy services firm with enhanced digital offerings. AVEVA will support Kent’s digital design and service offerings so its customers can tap into the power of advanced technologies to fuel their transformation journeys.
The collaboration unlocks new opportunities for innovation in digital asset delivery and unleashes the potential of EPC4.0 and digital twin solutions based on AI, big data, cloud, and immersive technologies. Customers can now tap into the combined strengths of AVEVA and Kent to implement novel and tailored digital solutions and gain comprehensive support across the full lifecycle of an asset. Together, the companies offer a data-centric approach, from speedy asset design to smart construction and unified operations.
Better awareness about the environmental impact of fossil fuels and a global mandate to achieve global net-zero goals have led to increased pressures on industrial enterprises to
embrace environmental sustainability. Energy companies are adopting digital technologies to optimise the design, engineering and construction of new projects, increase operational efficiency and safety, and adopt green processes to reduce overall emissions. They are seeking cutting-edge solutions that can leverage data and apply advanced analytics to meet their sustainability objectives and execute capital projects effectively.
The AVEVA and Kent collaboration is well timed to help energy customers address their evolving sustainability targets. Both companies have a proven track record of successfully delivering innovative projects in the energy sector on a continuous basis. Kent has developed deep proficiency in industry processes and plays a key role in creating innovative solutions for efficient project execution, while AVEVA is the leading technology expert housing end-toend lifecycle tools, platforms and expertise.
Indian enterprises hosted and on-premises at Yotta datacentre can now access Virsec’s Deterministic Platform

Yotta announced its partnership with Virsec, through which enterprises across India that are either hosted at Yotta data center or their captive on-premises data center or any public cloud can now get access to Virsec’s patented Deterministic Protection Platform. It is the only security solution that ensures precise protection against zero-day, ransomware and evolving cyber-attacks to workloads deployed in production. DPP precisely maps what an application or software is intended to do and stops them instantly when they behave abnormally within milliseconds.

CHANNEL
(Left to right) Dave Furneaux, CEO, Virsec; Bobby Gupta, SVP & MD, International Business at Virsec; Sunil Gupta, Co-Founder & CEO at Yotta.
24 JUNE 2022 MEA
(Left to right) Tush Doshi, Chief Operating Officer at Kent; Peter Herweck, CEO, AVEVA.
Taeknizon’s deploys Pure as a Service, IT team saves an average of 12 hours per week
Pure Storage announced that Taeknizon, a fast-growing private cloud services company, has deployed Pure’s infrastructure and Pure as-a-Service to enhance the performance and availability of its cloud services for UAE businesses. The solutions also enable Taeknizon to onboard new customers in under half a day and extend powerful ransomware protection to its entire cloud customer base as it’s included in Pure’s solution as standard.
Recognising the pressing need for UAE organisations to digitise their operations through the pandemic, Taeknizon established its cloud business in 2020. Overwhelming demand for these services has driven more than 30% year-over-year growth but momentum was hampered by the need for constant storage upgrades. To keep its growth on track, Taeknizon turned to Pure as-a-Service.
With Pure fully managing the infrastructure, Taeknizon’s IT team saves an average of 12 hours per week. Freedom from capacity constraints also gives the team confidence to constantly seek out new customers without concerns of delays to onboarding. With Pure, the company can complete cloud migrations for its customers in under two weeks, and onboard greenfield customers in less than half a day.
Pure provides Taeknizon with proven availability, and consistent single-millisecond latency for its clients’ most demanding workloads, while features such as SafeMode speed recovery and mitigate the effects of ransomware, enabling Taeknizon to provide its customers with powerful ransomware protection as a complimentary service.

emt Distribution to sell AionIQ, Gatewatcher’s detection and response platform in MEA
emt Distribution announced an enhanced partnership with Gatewatcher, Europe’s leading cybersecurity software company specialising in the detection of advanced cyber threats. Gatewatcher publishes a suite of solutions based on next-generation technologies that effectively protect
organisations against intrusions. Thanks to a 360° view of cyber threats, Gatewatcher’s solutions, based on artificial intelligence, offer a flexible cloud, on premise, hybrid, and scalable approach. They also facilitate the operations of cybersecurity teams for a better efficiency in the

CHANNEL MEA 25 JUNE 2022
Omar Akar Regional Vice President, Middle East & Emerging Africa, Pure Storage.
CyberKnight is now Entrust’s newest regional distributor for GCC, Levant, Egypt and Pakistan
Entrust, a global vendor in trusted identity, payments and data protection, announced its new distribution partnership with CyberKnight, a Dubai-based cybersecurity-focused value-added-distributor, empowering security professionals to address compliance and simplify cyber threat management.


In line with evolving regional compliance regulations and standards, Entrust’s new partnership with CyberKnight as its newest regional distributor, will see the two companies jointly build solutions for the Middle East market that achieve the highest standards of cyber security.
Entrust and CyberKnight are strategically aligned on their security vision with a Zero Trust philosophy at its core. With the aim of increasing access to the highest standards of security for Middle East customers, Entrust’s new partnership with CyberKnight will further enable the delivery of digital security solutions to customers, by tapping into CyberKnight’s local network to offer advice, education, expertise and confidence.
Entrust’s certificate solutions, PKI, identity and access management, encryption key management and hardware security modules are available to local customers through the partnership.
Later this year, Entrust will join CyberKnight’s annual roadshow, set to take place in November, 2022. The roadshow will cover seven cities across the region
including Dubai, Riyadh, Doha, Kuwait City, Amman and Cairo. Entrust will also be joining the CyberKnight stand during the upcoming MENA Information Security Conference in Riyadh, set to take place in September.
Honeywell’s new Catalyst Partner Programme to boost partner access to Building Management Systems
Honeywell announced the launch of its new Catalyst Partner Programme, a customercentric global framework to better support the growth and success of its system integrator, distributor and original equipment manufacturer partners in the Middle East, Turkey and Africa. The new global programme for Honeywell Building Technologies streamlines previous channel partner programme experiences across the company’s Fire, Security, Electrical Products and Building Management Systems businesses to help improve end customer standard of care and create greater efficiencies through a new digital platform.
Designed to improve customer experience touchpoints and better meet end customers’ needs, the CPP leverages best practices from the previous programs and helps drive business
growth for channel partners, while aligning on shared strategic goals. The new programme includes a new digital Partner Relationship Management PRM platform that offers partners a digital resource to manage their portfolio as well as track their progress, incentives and benefits.
The CPP features a tiered approach to support participants’ achievements and recognizes the performance of channel partners based on capability, strategic alignment and purchasing history. The tiered levels of rewards and recognitions increase based on sales volumes, business results, customer service, product training and engagement. Programme benefits such as account service levels, preferred pricing and marketing support correlates with the partner’s programme tier.
Sultan Chatila
Avinash Advani
Founder & CEO of CyberKnight.
CHANNEL 26 JUNE 2022 MEA
Chief Commercial Officer, Honeywell Building Technologies, Middle East, Turkey and Africa.
R&M appoints Mindware as value added distributor for Gulf and Levant regions
Mindware, announced it has been appointed as a Value-Added Distributor by Reichley & DeMassari for the Gulf and Levant regions. Mindware will promote and distribute the vendor’s innovative cabling systems for high-end data and communication networks.

R&M is a top tier solution provider in the structured cabling industry and a smart innovator in data centre, LAN and telecom verticals.
The company’s large portfolio of state-of-theart solutions is based on well-established Swiss quality standards. R&M is renowned for its agility in customising solutions in response to various customer needs, in contrast to just selling off-the-shelf products. It’s globally distributed network of production plants and competence centres provides consistent and stable customer support.
Qualys enhances partner programme to enable partners to leverage Qualys Cloud Platform

Qualys announced that it is reinforcing its commitment to the channel with the launch of an enhanced channel and integration partner programme. Qualys is committed to the creation and distribution of meaningful integrations with technology partners across the ecosystem to reduce risk and accelerate the path to continuous security for modern enterprises. The programme has been uniquely designed to foster close collaboration and enable partners to realise significant value when leveraging the power of the Qualys Cloud Platform.
THE QUALYS PARTNER PROGRAMME:
l Enriches structured benefit and protection programs for partners who identify new opportunities.
l Offers technical certifications and opportunities to deliver value through professional and consulting services.
l Works with a variety of partner types to enable access to a broad set of companies and market segments. Qualys welcomes MSSPs, MSPs, VARs, distribution partners and vendors throughout the cybersecurity space.
l Grants access to the Qualys Cloud Platform which provides continuous visibility into today’s ever expanding threat landscape.
R&M will support Mindware in providing turnkey technology solutions to the market, especially in the datacentre segment. The vendor’s renowned, state-of-the art offerings will be now made available across the region via Mindware’s seven warehousing hubs. The distributor and their reselling partners will have access to an extensive database of knowledge, including the ability to enrol in the R&M Academy, providing a variety of courses covering various technology topics in different verticals. The vendor will also provide international and local support of senior technical consultants and technical engineers.
CHANNEL
Nicholas Argyrides, General Manager - Gulf at Mindware (Left) and Nabil Khalil, Executive Vice President - Middle East, Turkey and Africa at R&M (right) at the partnership signing ceremony.
MEA 27 JUNE 2022
Suzanne Swanson senior vice president of Global Partners, Qualys.
BeyondTrust introduces all-in-one global programme, removes region-specific requirements

BeyondTrust, announced that it has enriched and streamlined its partner programme into an all-in-one global programme. Programme enhancements include the introduction of MSP, GSI and Service Delivery Partner tracks to complement the existing Reseller track. The enhanced partner programme offers more choices for partners to sell, implement and support BeyondTrust solutions, leading to maximised profits, and improved business outcomes for their customers.
The addition of the MSP, GSI and Service Delivery tracks give partners the ability to pick a model that is a better fit for the market they are operating in. With a focus on outcomes,
partners opting for one of these tracks will have a unique opportunity to build more strategic relationships with BeyondTrust and up-level their value proposition to customers. The changes will also streamline partner engagements and provide customers with more ways to optimise their technology investments.
The enriched and refined, all-inclusive programme removes region-specific requirements and benefits and discount structure for partners. The new global approach simplifies all partner and BeyondTrust interactions, allowing BeyondTrust channel managers and partners to devote more time to developing strategic, mutually-beneficial sales plans.
Rob Spee Senior Vice President, Global Channel and Alliances at BeyondTrust.

As they grow their business, Authorised, Silver and Gold partners in Europe, Middle East, India and Africa, will also see increased programmatic discounts for Deal Registration, providing them the opportunity to make higher margins.

Spire Data partners with Krista Soft to combine automation and big data solutions
Spire Data, an emerging leader in data analytics and governance in the Middle East and Africa region, has partnered with Krista Software, a leading AI-led intelligent automation solution provider. The partnership will see “Krista”, Krista Software’s AI-led automation platform being delivered through Spire’s big data portfolio to enterprise customers for automating business processes, improving efficiency, and reducing costs.
Krista is a modern intelligent automation platform designed to easily leverage existing IT assets and SaaS apps in automated business workflows. Krista’s unique approach enables business process owners to quickly build new automation without having to wait for expensive IT resources. Creating automation in Krista is as simple as describing a conversation between people and apps.
CHANNEL
(Left to right) Tausif Sayyed, Head of Business, Spire Data; and Kiran Karri, VP of APJ and MEA, Krista Software.
28 JUNE 2022 MEA
MANAGING END-TO-END YEGERTEK
CUSTOMER EXPERIENCE
Yegertek has spent years creating a platform that manages the customer experience journey with technology provided by Microsoft for its flagship IP Engage365.
technological backbones, enterprises expect to not only address existing pain points but also stay nimble for future eventualities.
Yegertek specializes in data-led CRM, experience-centric mobility, end-to-end loyalty solutions and wholistic user engagement, customised as per industry and individual requirements and needs. Differentiating itself from its counterparts, Yegertek emphasizes keeping customers at the core of its offerings and collating cross-channel data.

With proprietary solutions such as Puzzle, a best-in-class custom rule engine, and cuttingedge analytics, Yegertek is positioned as a solutions provider that can streamline operations and enhance efficiencies in industries such as hospitality, dine-in business, e-commerce, B2B, B2C. This distinction is from the ability to harness data, be receptive to emerging technologies, and stay adept in customised implementation.
Yegertek has spent years creating a wholistic platform that manages an end-to-end customer experience journey. Its key technology platform is Microsoft, on top of which the flagship IP Engage365 sits. In addition, Yegertek has spent considerable time evaluating and forming strategic partnerships with key companies that complement the loyalty and CX domain.
Enterprises find themselves at an inflection point where customers are unlearning some of the pandemic ways, retaining some, and tracking back to a few pre-pandemic ones. So, there are multiple touch points, and consequently numerous data points, distinctive channel preferences, and shopping behaviours to synthesize.
For enterprises with obsolete and siloed technologies, effectively collating data, analysing the same, and deriving accurate insights can be challenging. So, their expectations from solutions providers revolve primarily around effective customer segmentation, AI,ML-powered hyper-personalisation, and insight-based loyalty programs and services. In fortifying their
From integrating with a strong marketing automation platform to creating an end-toend SaaS ecommerce platform, Yegertek has attempted to map all customer touchpoints with tools that can capture engagements across multiple channels. This approach has allowed Yegertek to offer customers the complete nine yards of the customer experience domain, covering everything from a loyalty engine to
CHANNEL STREET 30 JUNE 2022 MEA
ZAIN SHAIKH Co-Founder and Director, Yegertek.
a VOC engine, to advanced data analytics, to recommend engines, to marketing automation.
Clients include luxury department store Harvey Nichols in Qatar, cab-hailing leader eCabs in Malta, a global casual dining restaurant chain in GCC, a renowned high-end jeweller in UAE, a ceramics business, and a premium grocer.
Technology has given retailers a clear, granular, contextualised, and holistic view of their customers. At Yegertek, the focus is on the bigpicture; to give omnichannel, cross-functional, and holistic value to organisations throughout the customer journey, combining advanced technological capabilities with domain-specific expertise.
The ultimate goal is to ensure that Yegertek enters into customer relationships where Yegertek can create avenues for partners to grow revenue, optimise their growth, and further expand their regional, global presence. As Yegertek accelerates its operational footprint, the focus remains on starting every relationship with a promise to offer a premium customer experience for clients.
Yegertek has had a steep learning curve in the last two years, underpinned by data proliferation, dramatic shifts in consumer behaviour, digitalisation across industries, and changing
market dynamics. The most notable takeaway was the need to be technologically innovative and operationally agile, so as to build fundamental business resilience in the face of disruptions.
From what Yegertek gathered, brands that were digitally mature before the pandemic were best equipped to adapt and maintain business continuity. As a result, when the pandemic changed the equations, digitally mature brands saw opportunities where their less-mature counterparts saw challenges. Enterprises have also subscribed to the knock-on impact of employee experience on CX, leading to a reassessment of archaic practices and business models.
Microsoft Dynamics CRM-powered loyalty solutions, which are currently finding takers from all business quarters, will find greater traction in the next couple of years as enterprises increasingly seek efficiency in how, when, and where they reward customers. Concurrently, digitalisation will continue its breakneck pace, underscoring the need for sophisticated data analytics, mobility solutions, and greater AI, ML, and automation adoption.
While standalone technologies will generate their fair share of patronage, the uptake will be rather high for one-stop-shop offerings, with enterprises developing a penchant towards full suites that can handle end-to-end processes, from collating data to executing insight-led actions. ë
Enterprises find themselves at an inflection point where customers are unlearning some of the pandemic ways
CHANNEL STREET MEA 31 JUNE 2022
IMPACT OF RAMADAN ON INTERNET TRAFFIC IN MIDDLE EAST AND ASIA
Analysis by Cloudflare Radar indicates how Internet traffic varies around the period of sunrise and sunset during Ramadan and after Eid al-Fitr.

What happens to the Internet traffic in countries where many observe Ramadan? Depending on the country, there are clear shifts and changing patterns in Internet use, particularly before dawn and after sunset.
This year, Ramadan started on April 2, and it continued until May 1, 2022, dates vary and are dependent on the appearance of the crescent moon. For Muslims, it is a period of introspection, communal prayer and also of fasting every day from dawn to sunset. That means that people only eat at night - Iftar is the first meal after sunset that breaks the fast and often also a family or community event, and also before sunrise Suhur.
In some countries, the impact is so big that you can see in Internet traffic charts when the sun sets. Sunrise is more difficult to check in the charts, but in the countries more impacted, people wake up much earlier than usual and were using the Internet in the early morning because of that.
Afghanistan, Pakistan, Indonesia, Morocco, Libya and Turkey had the biggest impact in an increase in traffic before sunrise. After sunset, it was by order of impact Saudi Arabia, Tunisia, Bangladesh, Pakistan that showed a clear decrease in traffic after sunset.
EARLY MORNING TRAFFIC
There’s a clear pattern in most of the countries, Internet traffic was much higher than usual between 04:00 to 04:59 local time whereas usually it is the time with the lowest traffic.
The same early spike is seen in Turkey and the United Arab Emirates. In the case of the United Arab Emirates, the time before sunrise for the Suhur meal had more mobile usage than usual so people were using their mobile devices to access the Internet more than usual at that time.
That’s also the case for Pakistan, where traffic is 119% higher on the 04:00 to 04:59 hour on April 3, than on the previous Sunday, but also in Qatar sunrise at 05:25 and a spike of 35% for Afghanistan. In the latter, the spike is 203% higher.
We also saw the same trend in Indonesia, sunrise was at 05:55 local time at the beginning of April, and there’s a clear spike in traffic in the 04:00 to 04:59 hour with a 98% growth in requests.
Northern African countries like Egypt, Tunisia, Morocco or Libya sunrise at 06:54, show the same 04:00 to 04:59 hour spike. In Libya, traffic was 81% higher on Sunday, April 3, than it was the previous Sunday at the same time. Usually, the 04:00 to 04:59 hour is the lowest point in traffic in the country, but on April 3 and the following days it was at 08:00.
SPECIAL REPORT 32 JUNE 2022 MEA
Cloudflare Radar data shows that Internet traffic was impacted in several countries by Ramadan, with a clear increase in traffic before sunrise, and a bigger than usual decrease after sunset. All times are local. The data in the charts is bucketed into hours. When we show an increase in traffic at 0400, we are showing that an increase occurred between 0400 and 0459 local time.
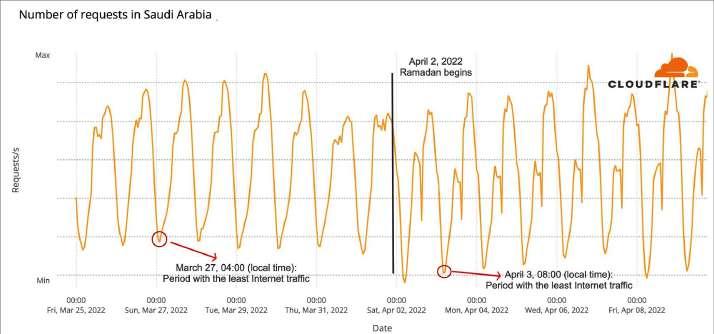
Saudi Arabia shows a similar pattern in terms of Internet traffic on Sunday, April 3, 2022, sunrise was at 05:44, and there was 55% more Internet use than at the same time on the previous Sunday, before Ramadan.
DAILY INTERNET TRAFFIC

The short answer is that it depends on the country, given that there are examples of a general increase and decrease in traffic in the most impacted countries. We see similar trends for the sunset and sunrise times of day, but it is a different story throughout the 30 days of Ramadan.
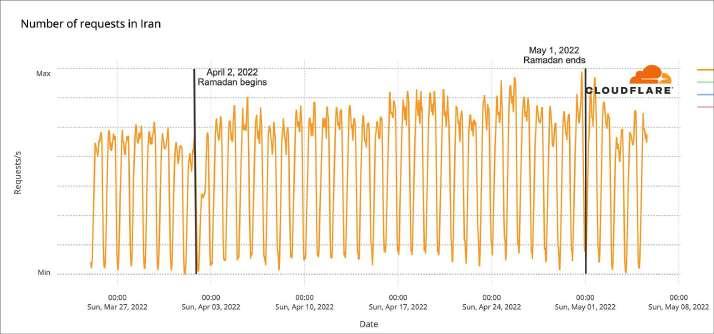
Iran, in general, shows an increase in traffic after Ramadan started on April 2, and a decrease after it ended on May 3 of around 15%. Something similar is seen in Pakistan, that had a general decrease in traffic the week after Ramadan ended, but during the 18:00 to 18:59 hour, May 4, had 13% more traffic than at the same time on the previous Wednesday, when Ramadan was being observed and the iftar meal would have happened during the 18:00 to 18:59 hour.
The opposite happens in Libya, where traffic, generally speaking, declined during Ramadan and picked up after — comparing Wednesday, May 4, 2022, with the previous one during the

ALL GRAPHICS: Cloudflare SPECIAL REPORT Middle East MEA 33 JUNE 2022
SUMMARY OF INTERNET TRAFFIC DURING RAMADAN IN VARIOUS COUNTRIES
In the table, we show country ranking by order of impact. Here, we include traffic changes before dawn and after sunset. In the last column, you can also see the change in traffic after Ramadan ended, right after sunset. In this case, we are looking at 04 May, right after the Eid al-Fitr, with 02-03 May, a holiday of breaking the fast, in a comparison with the previous Wednesday at the same time when Ramadan was ongoing.
SPECIAL REPORT
INTERNET TRAFFIC: RAMADAN’S IMPACT BEFORE SUNRISE AFTER SUNSET POST-RAMADAN, 4 MAY AFTER SUNSET Afghanistan +203% -28% +20% Pakistan +119% -39% +13% Indonesia +98% -13%Morocco +90% -36% +44% Libya +81% -27% +48% Turkey +78% -19% +22% Bangladesh +62% -40% +12% Saudi Arabia +55% -45% -5% United Arab Emirates +52% -13% +4% Bahrain +44% -31% +21% Malaysia +41% -8% -9% Qatar +35% -23% +5% Egypt +31% -32% +56% Tunisia +25% -43% +101% Iran +24% +10% -12% Singapore +8% -5% +4% India - -15%34 JUNE 2022 MEA
19:00 to 19:59 hour, traffic grew around 48%. The same trend is seen in another North African country: Morocco growth of 44% after Ramadan ended.
POST RAMADAN TRAFFIC
Another pattern, unsurprisingly, is how the sunset period changes when Ramadan and the holiday that follows ends, in most cases clearly increasing traffic at around 18:00 or 19:00.
Of the 16 countries with a bigger Ramadan impact, only four had a decrease in traffic after sunset on 04 May: Iran, Indonesia, Saudi Arabia and Malaysia. All of these countries had an increase or sustained traffic in daily traffic during Ramadan and lost daily Internet usage after it ended in May.
A zoomed-in Indonesia chart after Ramadan ended 01 May, shows not only the general decrease in traffic, but also how the sunset period does not have a clear drop in requests as seen in the Ramadan period.

Ramadan has a clear impact on Internet traffic patterns as humans change their habits. The Internet may be the network of networks, where there are many bots friendly and less friendly, but it continues to be a human-powered network, made by humans for humans. ë
Cloudflare Radar data shows that Internet traffic was impacted in several countries by Ramadan, with a clear increase in traffic before sunrise, and a bigger than usual decrease after sunset. All times are local. The data in the charts is bucketed into hours. When we show an increase in traffic at 0400, we are showing that an increase occurred between 0400 and 0459 local time. ALL



SPECIAL REPORT
GRAPHICS: Cloudflare
Asia MEA 35 JUNE 2022
DATA PROTECTION
DEPLOYING FOR SMALL BUSINESSES
According
be detectable by anti-malware software until it is too late. Once infected, a business can be locked out from its own data, and there is no guarantee that the data can be retrieved even after paying a ransom.
Small businesses are the backbone of every growing economy, bringing growth and innovation to the communities in which they are established. However, these businesses are often vulnerable when conforming to the new standards of remote work.
Today, one of the greatest threats to small businesses is a cyberattack. According to the Wall Street Journal, companies with less than $10 million in annual revenue are less likely to be prepared for cyberattacks. FireEye also reports that while 77% of all cybercrimes are directed toward small businesses, only 42% of small business owners are concerned with cyber security.
The National Small Business Association reports that as many as 60% of small businesses will fail within six months of experiencing a significant cyber breach. These findings clearly show that most small businesses lack the ability to defend against this growing threat.
According to WSJ, many small businesses don’t even know when they’ve been the victim of a cyberattack because they don’t have the tools to identify them. Encryption-based ransomware encrypts files stored on computers and can spread across the network, preventing businesses from accessing their own data.

These types of ransomwares are becoming increasingly sophisticated and may not
Another common challenge for small businesses is scattered and redundant data. Many modern businesses have adopted remote work policies, spreading their data across multiple platforms and devices. While these new working models might aid in business productivity, scattering your data across servers, virtual machines, personal computers, and cloudSaaS applications like Google Workspace and Microsoft 365 may actually put your data at risk.
To secure data and meet governance and compliance regulations such as GDPR, all devices and platforms must be backed up in a unified manner. However, this type of data management can get complex when certain platforms are only compatible with specific backup solutions. In addition, it can be hard to avoid expensive licensing fees whenever software and hardware storage devices are purchased separately.
With these issues in mind, your company may need a new approach when considering data protection. Small businesses need a data protection solution that enables them to centralise and protect business data distributed across platforms, and perform multi-version backups with flexible, rapid restoration options to minimise damage when a disaster occurs.
If you are looking for a new and intelligent backup solution to replace your existing system, you will want to make sure it supports these three key functions:
#1 CENTRALISED MANAGEMENT
First, a centralised data management system needs to support comprehensive backup tasks from a single console. IT staff can deploy and monitor backup tasks and stay alert with instant notifications and detailed reports.
The best backup solutions offer intuitive backup management for all endpoints, including servers, virtual machines, and SaaS applications. Backups are less effective without fast and easy restoration options. Today’s leading solutions offer near-instantaneous restoration to minimise costly service downtime.
With an easy-to-use centralised backup solution, individual employees can even be trusted to restore their own data using flexible recovery options without burdening IT admins, speeding up the recovery process.
to the Wall Street Journal, companies with less than $10 million in annual revenue are less likely to be prepared for cyberattacks.
PRODUCTS 36 JUNE 2022 MEA
JOANNE WENG Synology HQ Sales Director.
#2 SMART BACKUP TECHNOLOGY
Second, a smart data backup solution should provide efficient backups for all company devices without occupying extra storage space with duplicate pieces of data. This would include incremental backup technology, which only saves a copy of files that have been changed or newly added since the last backup. Additionally, this would include data deduplication, a technology that eliminates identical data blocks across backup workloads. The ideal backup solutions offer both options while also considering existing storage deployments. It is essential to find a solution that is flexible and scalable enough to meet the needs of growing businesses without requiring the replacement of existing IT infrastructure.
#3 MEET SECURITY BUDGET REQUIREMENTS
According to Foundry’s Security Priorities Study, 90% of security leaders believe they’re falling short in addressing cyber risks and attribute these shortfalls to not investing enough in security budgets. Business data security can be expensive, with costs including Infrastructure construction, security analytics, network monitoring, routine maintenance, firmware, software updates, and recurring license fees.
Having a backup service that integrates hardware and software can mitigate these costs. Some storage providers offer built-in backup applications that achieve comprehensive data protection, including backup tasks for physical and virtual environments, and even saving off-site copies to the cloud.


By consolidating acquisition, deployment, and technical support with one vendor, IT admins can have a comprehensive backup and recovery plan in place without paying additional license or maintenance fees. A backup solution that aligns with your business’s digital transformation
The ownership and management of data is a crucial part of today’s growing businesses, and whether or not a business can protect its data plays a major role in its success. Having a smart backup solution can provide businesses with a competitive advantage, put them a step ahead in this modern era. ë
This content has been sponsored by the vendor.
PRODUCTS MEA 37 JUNE 2022
FireEye reports that 77% of cybercrimes are directed toward small businesses, but only 42% of small business owners are concerned with cyber security
POWER OF VIDEO
IS MORE THAN A PICTURE
If a picture is worth a thousand words, then imagine the importance and worth of a video. The truth is that our brains love to be stimulated. We process and absorb visual information faster.
According to University of Rochester vision scientists, more than 50% of the cortex, the brain’s surface, is devoted to processing visual information. Additionally, MIT neuroscientists have found that our brain can process and identify images shown to us rapidly, for as little as 13 milliseconds each.
Thus, looking at the world today, the popularity of video comes as no surprise. We consume many minutes or even hours of video daily through numerous sources, while we also harness the power of video to communicate with our friends and family or do business with our colleagues. The pandemic has accelerated its adoption for sure, but the trend was already there. After all, for millennials and the younger generations, video communication is considered more of a necessity than a novelty.
Consequently, if we want to create compelling customer experiences, the implementation of video is essential. Over the last few years, we have seen brands broadly using video to showcase their personality through social media and create connections with their customers by sharing interesting, engaging stories. But nowadays, the use of video as a marketing tool is just one side of the coin. In fact,
video can add value to customer experience in many more ways.
Embracing video to communicate with customers in real time is going to drive customer experience forward. One of the first sectors that utilised video chat to offer personalised services was the healthcare industry. Although initially developed to help people living in rural areas, telehealth use surged during the pandemic, and patients realised that video chats with doctors and physicians are in many cases more convenient and just as thorough as visiting a hospital or a local clinic.
Likewise, universities and educational institutions jumped on the video collaboration bandwagon as well. Through offering synchronous and asynchronous learning, institutions were able to reach students who could not otherwise attend classes in person.
Banks and financial services providers have also adopted video as a means of communication. Offering customers, the option to speak with agents using their smartphone or computer, at their convenience, greatly enhances customer experience. Video communication is an excellent option when someone wants to avoid visiting a branch, but still needs to have a face-to-face conversation with their advisor. In the financial services industry, building long-term quality connections and developing trust with customers is critical –and it is impossible without adding the human touch to the equation.
Video’s full potential for improving customer experience has yet to be realised but video must play a key role in an omnichannel strategy.
COVER STORY 38 JUNE 2022 MEA
Use of video as a marketing tool is just one side of the coin and video can add value to customer experience in many more ways


When it comes to interacting with customers via live video, quality must be exceptional with clear sound
COVER STORY
LOUBNA IMENCHAL Head of Video Collaboration, Africa, Middle East, Turkey and Central Asia, Logitech.
Furthermore, video communication allows companies and organisations to vastly improve their customer support. When a customer deals with an urgent problem that needs to be solved immediately, being able to chat via video with a representative is highly appreciated.

In the case of technical support, for instance, customers do not have to go through the process of writing about the problem and trying to find the right words to describe it. They can simply use their smartphone’s camera or webcam to show the customer support team what exactly they are dealing with. Communication isn’t impersonal and customers feel that their voices are heard.
When paired with live video, conversational commerce can also take off. By leveraging the power of AI, if customers show interest in purchasing a product, a query can escalate from a chatbot to a video chat with a sales representative. This allows the company to better understand its customers’ needs and offer an enhanced service with tailored recommendations, possibly leading to higher conversions.
At the same time, customers are able to ask any questions they have in real time, and receive the attention they deserve, just as they would in a store.
Video’s full potential for improving customer experience has yet to be realised, but the opportunities are exciting. To elevate customer experience, video must play a key role in an omnichannel strategy. Moreover, high quality video is a prerequisite so customer experience video production must meet high standards. And when it comes to interacting with customers via live video, the quality must be exceptional with virtually crystal-clear sound.
While there are an abundance of solutions available, it’s worth noting that Logitech has been named the Market Leader in Video Conferencing Devices by Frost & Sullivan, recognising the company that has achieved the greatest market share as a result of outstanding performance, products, and services.
What makes Logitech stand out is that it provides a complete ecosystem, including video conferencing hardware, software, services, and official partnerships with the world’s leading video conferencing platforms. Logitech products can adapt to any environment and company size and offer easy implementation.
From advanced conference cameras like Logitech Meetup and Rally Camera, to the Logitech business webcams and audio-conferencing headsets with high resolution and frame rate, as well as RightLight and RightSound technologies that ensure the users look and sound their best in video calls, Logitech solutions empower the evolution of customer experience. ë
This content has been sponsored by the vendor.
COVER STORY 40 JUNE 2022 MEA
Video communication is an excellent optionwhen someone wants to avoid visiting a branch
CHALLENGING THE INCUMBENTS IN COLLABORATION
IceWarp has built its network of hosting centres to avoid conflict with hyper scalers and is offering an alternative to incumbents in the workflow space.

IceWarp offers proprietary cloud orchestration to eliminate dependencies and privacy concerns. It also uses an intelligent traffic management system to automatically route user requests to the closest server, ensuring optimal performance for global end-users. The company constantly monitors and upgrades its infrastructure to ensure that its platform is always available and scalable.
In terms of sync, IceWarp offers real-time synchronisation across all devices and platforms. Changes made on one device are immediately reflected on all others, whether it is a calendar event, contact modification or a new email. IceWarp’s platform is designed to be highly performant and responsive, even under heavy load.
IceWarp builds advanced communication and collaboration platform, operating data centres in Middle East for data localisation. IceWarp’s solution is hosted on multiple global platforms, this allows the company to offer its customers a high level of flexibility and choice. IceWarp also offers support to its customers via phone, email, and live chat.
IceWarp’s Email to TeamChat Integration feature is a differentiating factor. Integrated TeamChat allows users to securely share files of any size
with anyone - inside or outside the company. Conveniently drag and drop files directly into chats or choose specific channels for team projects. Files are stored in the cloud and can be easily accessed from anywhere.
From email through team chat to audio and video conferences, from calendar and contact syncing through document sharing to collaborative editing. With IceWarp, users can enjoy flexibility with Outlook on personal devices. Emails, Calendars, Contacts, Tasks as well as Notes including colour categories and HTML content seamlessly sync with Outlook as well.
 PRAMOD SHARDA CEO IceWarp, India and Middle East.
PRAMOD SHARDA CEO IceWarp, India and Middle East.
PRODUCTS MEA 41 JUNE 2022
IceWarp
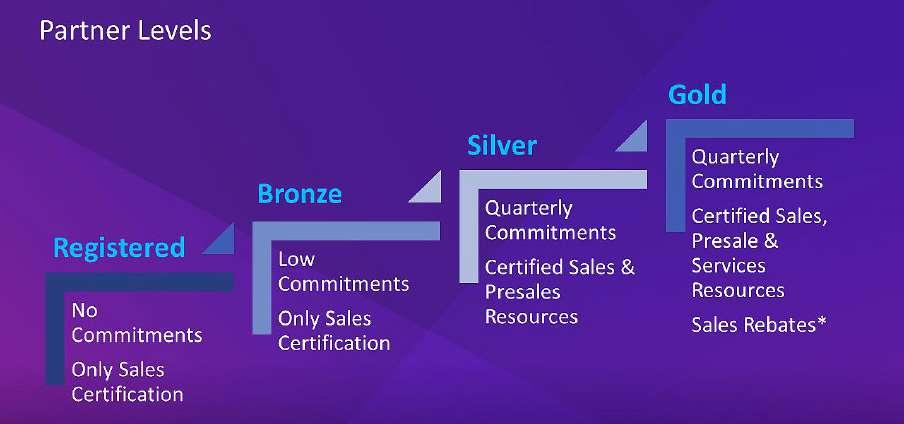
OVERVIEW OF PARTNER PROGRAMME


PRODUCTS
42 JUNE 2022 MEA
KEY PRODUCT FEATURES
ADVANCED SECURITY
Signature-based AntiVirus, online CYREN AntiSpam, and IceWarp Authenticator for two-factor authentication. Multi-layered security meets the world’s most stringent industry standards and legislation. Moreover, by integrating everything users need under a single login - Email, TeamChat, and Storage, IceWarp is able to provide them with a superior and safer communication experience at work.
OUTLOOK COMPATIBILITY

Emails, Calendars, Contacts, Tasks as well as Notes including colour categories and HTML content seamlessly sync with Outlook. Enjoy true freedom and flexibility with Outlook on personal devices with IceWarp mobile sync for all leading smartphones.

SMART MULTITASKING
Compose multiple emails while chatting with a co-worker, reviewing a document, or searching through TeamChat rooms. All of this during a conference call. IceWarp’s solution delivers an innovative, cost-effective, all-in-one collaboration platform comprising of an entire family of apps that offer real-time collaboration tools, simplified sharing options, and smooth integration of various virtual office functions.
SMART PLANNING
Know immediately if you can accept a proposed meeting. The interactive invite dialogue shows an overview of your schedule around the indicated time. Check free, busy times for team members and resources with just a few clicks. Schedule rooms, audio, video conferencing, and other resources directly from the invite.
SMART ATTACHMENTS
SmartAttach uploads large files such as videos or presentations to our cloud and automatically includes a link in the email body. So, your file is delivered fast and doesn’t clog your recipient’s mailbox. Users can also attach documents to any TeamChat message for quick retrieval by coworkers. Versioning ensures that you are always working on the latest version of a document. Document access can be easily controlled with user groups and permissions.
SMART DELAYED SEND
Sometimes you remember to add an attachment right after hitting the Send button. It has happened to all of us. With delayed send, you get five extra seconds for when you change your mind. The message will be held in your outbox for the specified time and then delivered automatically.
ADMINISTER AND CUSTOMISE
Manage your domains and user accounts using multi-tenant architecture. Configure DKIM to avoid email spoofing and enhance security. Set up DNS records with the relevant DRF file or use white labelling options. ë
PRODUCTS MEA 43 JUNE 2022
Check free, busy times for team members and resources with just a few clicks
Software AG releases ARIS for sustainability with compliance, tracking and reporting
Software AG announced ARIS for sustainability, a new package that supports the planning, implementation and measurement of sustainability initiatives. This free package puts processes at the centre of its customers’ sustainability strategies, helping to execute and making them verifiable and transparent.
The ARIS for sustainability accelerator package includes ready-made process models and ESG-relevant templates, reports and dashboards. They can be directly used in ARIS and connected with all company data already stored there — from strategy definition to operating processes.
The package covers:
l Assessments of sustainability maturity, operational readiness, and regulatory requirements
l Strategic Insights for robust sustainability initiatives with concrete goals, KPIs and governance
l Operational compliance, change management, roll-out, and audit-proofed confirmations
l Tracking and reporting of operational and financial sustainability
In April 2022, Software AG signed the UN Global Compact UNGC, the world’s largest initiative for responsible and sustainable corporate governance. In line with the ten principles of the UNGC, Software AG pledges to support and comply with sustainable business practices and will align its Helix transformation strategy even more closely with the environment, social and governance ESG criteria in the future.
Oracle Labs will open branch in

focused on Explainability, PGX Parallel Graph, MySQL Heatwave
Oracle announced it will establish a new branch of Oracle Labs, Oracle’s advanced research arm, at Casanearshore Park in Casablanca to house up to 100 researchers. Researchers at the new

facility will use Oracle’s cloud, AI, and machine learning technologies to tackle the most pressing challenges facing business, science and the public sector.
The new Oracle facility will be part of Oracle’s global R&D innovation network. In these centres, researchers apply novel approaches and methodologies using cloud-based technologies to create meaningful solutions. This work includes research, consulting, and product incubation with most projects involving university collaborations and interns from over 50 universities worldwide.
The new Oracle Centre in Morocco will work on a wide range of R&D projects focusing on technologies such as automated Machine Learning and Explainability, the PGX Parallel Graph Accelerator solution, and Oracle’s MySQL Heatwave ML.
Taking advantage of its new state-of-the-art facility, the team will collaborate with Morocco’s vibrant technology sector to support the identification, exploration, and transfer of new technologies that can advance Oracle’s customer’s businesses worldwide. This effort will include expanding intern and graduate recruitment programs, undertaking joint research with local universities and working with the local start up ecosystem so they can be part of this global program.
PRODUCTS
Sanjay Brahmawar CEO of Software AG.
Casablanca
44 JUNE 2022 MEA
Safra Catz Chief Executive Officer, Oracle.
Nozomi Networks’ Guardian
Remote Collector now embedded in Siemens
Nozomi Networks and Siemens, extended their partnership by embedding Nozomi Networks’ Guardian Remote Collector software into the Siemens Scalance LPE local processing engine, a hardware platform designed for data processing for edge and cloud applications in manufacturing environments. Customers can now easily deploy the leading OT & IoT continuous monitoring solution to their industrial networks leveraging the power and simplicity of the Siemens Scalance LPE hardware.
The Scalance LPE hosts the newly released Docker containerized version of the Guardian Remote Collector to bring local data collection, pre-processing and analytics to operational technology deployments. It offers an effective way to distribute processing power over large manufacturing operations and enables more efficient analysis and data aggregation by any
Scalance
centralised application, including Nozomi Networks Vantage cloud-hosted security platform.

The solution seamlessly delivers highly scalable continuous monitoring and intrusion detection to the network edge via the Scalance LPE. Data is forwarded from the edge to the Nozomi Networks Remote Collector hosted on the Scalance LPE to monitor and analyse industrial network protocols such as PROFINET, EtherNet/IP, and EtherCat for anomalous behaviour and potential threats.
What’s unique about this integration is that using the Siemens reference network architectures, even traffic from parallel PROFIsafe production cells can be collected. Nozomi Networks analyses data from the industrial process or global enterprise to provide insights and actionable intelligence to address security threats and speed up effective response and
Dynabook Satellite Pro C40 now using AMD Ryzen 5 and 7 series processors with Radeon Graphics
Dynabook Europe announced expansion of its Satellite Pro C40 range to include AMD Ryzen 5 and 7 series processors with Radeon Graph-

ics, broadening its range of budget-conscious business laptops. Carefully engineered with a variety of productivity, connectivity, and
remediation efforts. The Scalance LPE supports large-scale factory automation with distributed local processing capabilities at the edge, making it an ideal complement for Nozomi Networks, the most scalable OT cybersecurity solution in the industry.
security-enhancing features in an attractive, slimline package, the Satellite Pro C40D-B offers an outstanding level of price and performance for all day working, wherever that may be.
Weighing up to 1.52kg and with an 18.9mm compact form factor, the Satellite Pro C40D-B is easy to carry and amongst the slimmest in its class, making it suitable for all types of modern working styles – in the office, at home or on the move.
The new device has been updated to offer the most important technology for everyday business use. Powerful AMD Ryzen 5 5600U and Ryzen 7 5800U processors, up to 32GB fast DDR4 memory in two configurable slots, and SSD storage options up to 512GB mean the device can easily perform even the most demanding tasks, ensuring business continuity anywhere. For an enhanced user experience and improved productivity, the C40D-B is also equipped with an extra-large ClickPad, and an impressive battery life of up to 11.5 hours1, perfect for users working on the move.
Chet Namboodri Vice President of Business Development at Nozomi Networks.
PRODUCTS MEA 45 JUNE 2022
Cloudflare D1 serverless database using SQLite to build applications using Cloudflare Workers
Cloudflare announced Cloudflare D1, a simple and instant serverless database. Cloudflare D1 will enable developers to start building database-backed applications using Cloudflare Workers with just a few clicks. Data will be stored close to where their users are, providing lightning-fast performance without any of the complexities of installing or managing a traditional database.
Everything from the apps in your phone to SaaS applications for the enterprise to frameworks like Ruby on Rails use databases for storage. And SQL is the dominant language used to query and update those databases, large and small. Cloudflare’s D1 will offer instant access to one of the most widely deployed database technologies in the world, SQLite, directly from Cloudflare Workers. By combining Cloudflare’s serverless development platform with instant databases, developers can build rich, database-
backed applications without ever worrying about deploying or managing a database.
Unlike other databases on the market, Cloudflare D1 will use Cloudflare’s global network to optimise a businesses’ database by locating it as close as possible to their customers, providing the fastest possible experience to users. Additionally, by pairing storage solutions with Cloudflare’s serverless compute platform, Cloudflare is streamlining the developer experience for building full stack applications. Cloudflare D1 will be compatible with the SQLite API—one of the most popular and broadly used APIs in the world. With Cloudflare D1 developers will be able to:
l Intelligently locate data wherever your users are: With Cloudflare D1 there is no need to pick a region. Instead, Cloudflare will automatically store your database wherever your users are, resulting in
lightning-fast performance.
l Easily spin up a database with Cloudflare Workers: No need to figure out complex databases, just create a Cloudflare Worker and spin up a database in a few clicks.
l Import data from other providers to Cloudflare: With Cloudflare D1, developers will be able to seamlessly move data from other database providers.
l Unlock the power and scale of Cloudflare Workers within their applications: Cloudflare D1 is fully integrated with Cloudflare Workers, making building full stack applications incredibly easy.
l Slash their data transfer fees: Cloudflare’s goal is to make Cloudflare D1 the least expensive option for a simple and secure database for developers. That’s why Cloudflare will not charge data transfer fees, allowing developers to easily move data between services.

PRODUCTS
46 JUNE 2022 MEA
Matthew Prince co-founder and CEO of Cloudflare.
Lenovo releases ultra-slim Yoga Slim 9i, Slim 7i Pro X, Yoga Slim 7 Pro X, Slim 7i Carbon, Slim 7 Pro, Yoga 7
Lenovo unveiled the next generation of premium, ultra-slim Windows 11 Yoga laptops featuring:

l The flagship 14-inch Yoga Slim 9i, a carbon neutral certified laptop that offers smarter productivity and incredible portable entertainment
The Yoga Slim 7i Pro X and Yoga Slim 7 Pro X, fuelled by Lenovo X Power that enables creation anywhere, anytime
l The Yoga Slim 7i Carbon that fuses powerful mobility with durable style.
The new Yoga line also offers refreshes of the 14-inch and 16-inch Yoga Slim 7 Pro, the Yoga Slim 7i Pro, and the Yoga 7. To meet the needs of the new hybrid home office, Lenovo has also announced today the new Yoga AIO 7, a new 4K 27-inch desktop PC that features an ergonomic hinge for endless adaptability, collaboration across multiple devices, and modern engineering for the contemporary home.
Western Digital announces 22TB CMR, 26TB UltraSMR HDD data storage for cloud customers
Building on the expertise cultivated over 50 years of creating industry-leading technologies, Western Digital introduced new flash and HDD products for cloud, client and consumer customers.
l The Cloud: Western Digital unleashed powerful new data storage solutions for cloud customers, including the industry’s first 22TB CMR and 26TB UltraSMR HDDs, and a new family of high-capacity PCIe Gen4 NVMe SSDs to help them
design tiered-storage solutions more efficiently, and generate more value out of their infrastructure to help their customers’ data thrive.
l The Way We Work Now: The new PCIe Gen4 Western Digital PC SN740 NVMe SSD addresses the unique needs of the hybrid workforce and elevates the computing experience with sequential read speeds up to 5,150MB/s in a thin, light, low-power design.
l Creativity: Western Digital introduced the new SanDisk Professional PRO-BLADE Modular SSD Ecosystem. Designed to meet the demands of capturing, transferring and preserving increasingly higher resolution content, the PRO-BLADE solutions enable professionals to save hours on transfers, save money for equivalent capacity, and reduce the volume and weight of their gear.
l Gaming: Western Digital unveiled two additions to its award-winning WD_ BLACK gaming portfolio. Designed with performance and style in mind, the new WD_BLACK SN850X NVMe SSD and WD_BLACK P40 Game Drive SSD, offer gamers more options to elevate their gaming experience so they can play at their best.

At its What’s Next Western Digital event, Western Digital detailed its mission to unlock the potential of data by harnessing the possibility to use it. In a series of keynotes delivered by company leaders, Western Digital unveiled breakthrough HDD and Flash innovations inspired by the ways individuals and businesses use data to create what’s next.

PRODUCTS MEA 47 JUNE 2022
Nexans launches SMARTCONVERGE structured cabling system to support smart building devices
Nexans Telecom Systems has proposed a new solution for connecting smart building devices. SMARTCONVERGE would allow a truly application independent structured cabling system to be installed, providing the flexibility to connect either standard 4-pair Ethernet devices using RJ45, or using a port splitter to connect 4x Single Pair Ethernet devices.
The push for office buildings to become smarter poses several challenges for IT and facility managers on how to achieve that, with the need to manage significant increases in the number of connected devices resulting from the Building Internet of Things. In addition, demands for bandwidth, Wi-Fi, and power supply over the network are also increasing.

Smart Buildings have a large number of installed operational technology devices like climate, motion, heat and smoke sensors. Designing the placement of network cabling is the next challenge, with wireless access points and Wi-Fi are helping to reduce congestion. However, Wi-Fi and 5G transmission speeds are increasing, which reduces the gap between access points, increasing both the number of access points and congestion in the ceiling.
Lenovo releases Yoga Tab 13 with 13-inch 2K display and Dolby Vision HDR
Lenovo announced the launch of its Yoga Tab 13 in the UAE, delivering a supercharged audio-visual experience in a sleek and elegant form factor. The introduction of the company’s latest premium tablet offering comes during a time in which more consumers are investing in portable devices to enhance the hybrid worlds of work, learning and play.
The Lenovo Yoga Tab 13 features a large 13-inch 2K display with 400 nits of brightness and 100 percent RGB colour gamut. The panel is also powered by Dolby Vision HDR, which delivers ultra-vivid picture quality and detail. As a new Android tablet, the Yoga Tab 13 features Entertain-


ment Space from Google, the new home for free and paid content services. Users can enjoy up to 12 hours of playback 1080p and use Lenovo’s 30W quick charge to keep powered at all times of the day.
With quad JBL speakers, including the two built into the Yoga Tab 13’s innovative soundbar, users can enjoy a captivating listening experience. The audio journey is made more immersive still thanks to Lenovo Premium Audio tuning and Dolby Atmos®, alongside a lower audio chamber with up to 450Hz bass performance for cinematic sound that can actually be felt.
PRODUCTS 48 JUNE 2022 MEA
Arafat Yousef, Managing Director – Middle East & Africa, Nexans Data Network Solutions.
Intel introduces independent trust authority around security verification named Project Amber

Intel has turned its focus to how it will meet the growing security needs of organisations today and help them prepare for the challenges of tomorrow. Focusing on one of the most critical security elements for any organisation – trust –Intel introduced an independent trust authority in the form of an innovative service-based security implementation code-named Project Amber. The company also demonstrated its focus on enabling secure and responsible AI and outlined its strategy to further build quantum-resistant cryptography for the coming quantum computing era.
Businesses operate in and depend on the cloud to support remote workforces that require multiple devices, uninterrupted access and collaboration tools. Technology solutions need to secure data not only in memory and in transit, but also in use – protecting valuable
assets and minimising attack surfaces. Project Amber provides organisations with remote verification of the trustworthiness of a compute asset in cloud, edge and on-premises environments. This service operates independent of the infrastructure provider hosting the confidential compute workloads.
Confidential computing, the protection of data in use by performing computation in a hardware-based trusted execution environment TEE, is a growing market. Intel Software Guard Extensions available on the Intel Xeon Scalable platform is one of the main technologies powering confidential computing today, enabling cloud-use cases that are beneficial for organisations that handle sensitive data on a regular basis.
The foundational basis of trust in a confidential computing environment is established via
Riverbed begins beta testing for SaaS-based Alluvio unified observability solution

Riverbed will begin a Beta for a SaaS-based Alluvio unified observability solution in May 2022, with a general release expected later this year. To date, several organisations, including Fortune 500 companies, are trialling the solution, and providing valuable, positive feedback, highlighting that the Riverbed vision and approach to unified observability will eliminate data silos and alert fatigue, as well as improve decisionmaking, apply expert knowledge broadly and continuously improve digital service quality, all with a simple user interface.
Riverbed also launched a new brand identity, including the introduction of Alluvio by Riverbed, reflecting the evolution of the company and technology, and strong market momentum as evidenced by over 30% year-over-year bookings growth for its visibility and observability solutions in the last three quarters.
According to Riverbed’s Hybrid Work Global Survey, 75% of business decision-makers say their organisations struggle to glean actionable insights from data that is generated by their technology infrastructure. Furthermore, IT still relies on siloed tools to manage performance and user experience and are overwhelmed by massive amounts of disparate data and alerts that provide little context or actionable insights.
Observability is meant to solve these problems, but current solutions fall short. Observability tools that limit or sample data rather than capture everything leave IT blind to potential issues or opportunities for proactive improvement. Even so-called “full-stack” observability solu-
a process called attestation. The verification of this trustworthiness is a critical requirement for customers to protect their data and intellectual property as they move sensitive workloads to the cloud. To raise trust assurance and drive forward the promise of confidential computing for the broader industry, Intel announced Project Amber as the first step in creating a new multi-cloud, multi-TEE service for third-party attestation:
Dan Smoot
 President and CEO.
President and CEO.
tions fail to capture all relevant user, network, and application telemetry to effectively troubleshoot problems at scale for today’s complex, hybrid, and distributed infrastructures.
To address this industry challenge, Riverbed has invested and focused the company’s R&D efforts in the last year to develop technology and a unique approach to unified observability that is comprehensive, unified and easy-to-operate. Alluvio by Riverbed, the Company’s Unified Observability software portfolio, is being designed to provide IT with a unified view to see through massive complexity and transform data into actionable insights across the entire digital ecosystem and enable automated self-healing. This will enable organisations to provide seamless digital experiences that drive enterprise performance for both the employee experience EX and customer experience CX.
PRODUCTS
Riverbed
MEA 49 JUNE 2022
ServiceNow introduces Service Operations Workspace, App Engine Management Centre, Public Sector Digital Services

At Knowledge ’22, ServiceNow introduced three new solutions built on the Now Platform to help enterprises advance their digital transformation efforts. Service Operations Workspace, App Engine Management Centre and Public Sector Digital Services work across organisations and within the public sector to digitise complex processes and accelerate productivity.
l Service Operations Workspace gives service desk agents and operations teams a single place to manage work, collaborate, and have shared visibility into issues. It includes a unified user experience for agents and operations teams to work on the same problem at the same time and solve issues faster. This helps reduce downtime, improve customer satisfaction, and increase productivity across multiple groups.
l App Engine Management Centre AEMC unleashes co-innovation between business and IT with low-code app development governance. As the number of citizen developers creating lowcode solutions grows, the role of IT must evolve to empower co-innovation at scale while maintaining governance protocols. AEMC is a turnkey low-code governance solution to successfully scale and safeguard app development across an organisation with App Engine. Platform admins can set guardrails, apply standards, enable co-innovation between business and IT, and check for compliance in a single place without any friction.
Additionally, AEMC helps centrally manage all aspects of low-code app dev, from app intake to collaboration requests, to pipeline monitoring and deployment tasks.
ServiceNow has also published a new Citizen Development Centre of Excellence CoE website, making it easy for customers and prospects to find the content they need to build a successful citizen development program with App Engine.
l Public Sector Digital Services provides governments with a digital foundation to deliver consumer-grade experiences from request to resolution. For many people, requesting standard government services often requires visiting a local office, filling out paper forms, and submitting additional documentation, with poor visibility into the status of these requests. Within governments, fulfilling these requests can be slow and require personnel to navigate multiple aging systems and manual processes. Public Sector Digital Services provides out-of-the-box public sector data models and workflows to help governments speed innovation, deliver better experiences, and resolve requests faster. Constituents benefit from increased convenience¬¬, transparency, and responsiveness.
The three new innovations were announced in tandem with Knowledge 2022, ServiceNow’s annual event providing networking, roundtable discussions, demos and more centred around the latest power, predictability and flexibility of the Now Platform.
PRODUCTS
50 JUNE 2022 MEA
ServiceNow Service Operations Workspace module.
Cloudflare integrates Zero Trust with CrowdStrike Falcon Zero Trust Assessment
Cloudflare, is expanding its partnership with CrowdStrike. Cloudflare is integrating its Zero Trust platform with CrowdStrike Falcon Zero Trust Assessment to give joint customers simple and powerful controls to ensure employees have secure access to applications wherever they are working. Through this integration, Cloudflare and CrowdStrike are bringing together world-class technologies to provide joint customers with Zero Trust capabilities that are unmatched in the industry.
According to an October 2020 commissioned study conducted by Forrester Consulting, 76% of businesses are struggling to shift to a Zero Trust security posture due to complex user access needs. As employees continue to work from anywhere and businesses continue to navigate the transition to a hybrid approach to work, security teams are moving away from legacy security architecture towards a modern Zero Trust approach. Together, Cloudflare and CrowdStrike are working to simplify the adoption of Zero Trust solutions for IT teams. With this expanded partnership, joint customers can now:
l Enable secure conditional access to applications from any endpoint, regardless of the user or location: Cloudflare Zero Trust Network Access ZTNA and Cloudflare Secure Web Gateway SWG are now integrated directly with CrowdStrike’s real-time device posture assessments – Falcon ZTA – to strengthen the Zero Trust posture of joint customers.
l Identify and mitigate threats with unparalleled threat intelligence: Cloudflare is a part of CrowdStrike’s CrowdXDR Alliance, combining the insights from Cloudflare’s global network, spanning more than 250 cities and blocking an average of 86 billion cyber threats each day, with CrowdStrike’s endpoint data to help mutual customers identify and stop cyberattacks.
l Enhance visibility with logs: Cloudflare and CrowdStrike will advance their logs integration, allowing customers to correlate their Cloudflare logs with the CrowdStrike’s EDR telemetry for timely detection and mitigation of sophisticated threats.
l Get rapid support in under attack situations: CrowdStrike is an incident response partner of Cloudflare. During an incident or attack, CrowdStrike works with Cloudflare to help get customers’ web properties and networks back online.

Pure Storage FlashBlade’s Object Store to integrate with Snowflake Data Cloud in 2H 2022

Pure Storage announced a partnership to develop a solution that increases data accessibility for global customers with on-premises data. Pure Storage FlashBlade is a dynamic, high performance unified file and object platform purpose-built for modern analytics, offering real-time response for data with cloud-like agility.
Once available, Pure and Snowflake customers will be able to analyse multiple data sources stored on Pure Storage FlashBlade with the Snowflake Data Cloud, while keeping their data local. This will enable enterprises to work with data directly stored on FlashBlade object storage using Snowflake in the cloud — eliminating the need to create separate copies of data shared with other tools or workflows.
This solution will go into public preview by the second half of 2022.
PRODUCTS
John Graham-Cumming Chief Technology Officer at Cloudflare.
MEA 51 JUNE 2022
Rob Lee Chief Technology Officer, Pure Storage
Yellow.ai adds low code AI agents to its marketplace to enhance faster time to value
Yellow.ai, announced that it has augmented its Marketplace with pre-built, low-code Dynamic AI agents, enabling faster time-to-market and quicker time to value for enterprises. In line with its commitment to foster continuous innovation through its product offerings, the addition of pre-trained, ready to deploy vertical AI agents is aimed at helping enterprises accelerate their TX automation journey.

According to Gartner, digital business acceleration is putting pressure on IT leaders to increase application delivery speed and time to value. Addressing this challenge with greater solution accuracy, the centralised solution library of Yellow.ai’s Marketplace enables enterprises to deploy AI Agents in just a few clicks, reducing time-to-market by up to 50%.
It offers Prebuilt Industry Templates sup-
porting use-cases across key industries including retail and automotive; Prebuilt Channel Integrators supporting 35+ channels including WhatsApp, Facebook Messenger, WeChat, Slack, Twitter, MS Teams, Instagram and Prebuilt Solution Templates for use cases across customer support, customer engagement, conversational commerce, HR and ITSM automation.
Enterprises can also leverage the pre-built Dynamic AI agents for employee experience EX to automate end-to-end EX journeys, right from hire to retire including onboarding, training and routine employee engagements. Supporting seamless integrations with existing HCMs, ITSMs such as SuccessFactors, Service now, the pre-trained AI agents result in improved employee productivity by up to 30%
Oracle’s Exadata Cloud X9M offering 8,064 database server CPUs, 3.1 PB database capacity
Oracle announced availability of Oracle Exadata Cloud Infrastructure X9M, the latest generation of the most powerful Oracle Database platform in Oracle Cloud Infrastructure OCI. With Oracle Autonomous Database Service or Oracle Exadata Database Service running on Exadata Cloud Infrastructure X9M, customers can run existing workloads faster, with greater scale, and at a lower cost than previous generations. In addition, when upgrading from X8M to X9M, organisations can reduce costs by consolidating hundreds of OTLP, analytics, and mixed database workloads onto a single cloud service.
Exadata Cloud Infrastructure X9M offers up to 8,064 database server vCPUs, 2.5 times more than X8M, and up to 3.1 PB of uncompressed database capacity, a 28 percent increase. Together with 80 percent faster internal networks, and twice the bandwidth to application server clients, customers can run OLTP workloads with extremely low sub-19 microsecond SQL IO latency and up to 87 percent more
IOPS. Exadata Cloud Infrastructure X9M on OCI also accelerates analytics workloads in the cloud with 80 percent faster scan rates of up to 2.88 TB/s.
Exadata’s fault-tolerant hardware and integration with Oracle Real Application Clusters RAC provides continuous operations across failures and enables infrastructure to be expanded, upgraded, and updated without interruption. The scaling of other cloud databases often requires downtime when moving from one pre-defined virtual machine shape to another.
Exadata Cloud Infrastructure X9M supports scaling up consumption on database servers and scaling out the number of database servers used—all without migrating databases or taking downtime. With the ability to use four to 252 vCPUs per database server and two to 32 database servers per system, enterprises can consolidate mission-critical databases in the cloud without running out of resources.
Organisations and developers deploying
and employee satisfaction by up to 40%. Currently offering over 40 prebuilt accelerators, the company aims to offer over 100 prebuilt accelerators on its Marketplace spread across industries, channels and solutions by the end of the second quarter.
Autonomous Database on OCI can now increase performance and reduce costs by using more database and storage resources than previously possible on the X8M system. Autonomous Database customers have the flexibility to deploy the full range of Exadata Cloud Infrastructure X9M configurations in dedicated Autonomous Database environments. This enables customers to use additional vCPUs to execute more OLTP queries concurrently and more storage servers to parallelise analytics workloads with up to 38 times more scan throughput than possible with X8M.
 Rashid Khan CPO and Co-founder, Yellow.ai.
Ashish Ray
Vice President, Product Management, Oracle.
Rashid Khan CPO and Co-founder, Yellow.ai.
Ashish Ray
Vice President, Product Management, Oracle.
PRODUCTS 52 JUNE 2022 MEA
Global sales of 11 premium Samsung Smart Monitors surpasses one million
Samsung Electronics announced that the accumulated sales of its Smart Monitor series surpassed one million devices globally, making it a million seller. The new do-it-all screens support Smart Hub, providing a perfect home office and schooling environment without the need to connect to a PC or any other external device. In addition, the monitor allows users to enjoy a variety of OTT services such as Netflix, Samsung TV Plus and YouTube.
On the back of the popularity of its first Smart Monitor launched at the end of 2020, Samsung has enhanced its line-up this year. Now, Samsung offers 11 premium Smart Moni-
tors including the M8, M7 and M5.
In particular, the versatile new M8 features Samsung’s iconic slim design and comes in four, eye-catching new colours - Warm White, Sunset Pink, Daylight Blue and Spring Green. The stylish design of the M8 blends well into any surrounding, satisfying a range of different consumer requirements.
In addition, the M8’s removable SlimFit Cam, video conferencing solution app and other innovative display technologies are major drivers of its popularity, as people adapt to new lifestyles – such as working from home and home schooling.
The Smart Monitor M8 earned CES 2022 Innovation Awards Honoree from the CTAConsumer Technology Association in recognition of a wide array of its display technologies. Samsung started taking preorders for the M8 in the U.S., Germany, France and many other countries on March 28, 2022.
Preorders for the product exceeded the company’s expectations, reflecting the product’s popularity across the world. In the first quarter, sales of the Smart Monitor series, including the preorder sales of the M8, increased by approximately 40% compared to the same period of last year.

PRODUCTS MEA 53 JUNE 2022
Nokia implements Oracle Cloud HCM connecting every process across employee lifecycle

Nokia has selected Oracle Fusion Cloud Human Capital Management to consolidate and replace its Human Resources systems in the cloud as part of its global digitalisation program. Nokia will use a worldwide deployment of Oracle Cloud HCM to manage all HR
processes, including recruitment, compensation, and performance management, for the company’s global workforce in its 130 countries of operation.
In 2021, Nokia launched its ‘One Nokia Digital’ strategy to support the company’s competi-
Rotana Hotels in UAE migrates 30+ properties to 25Mbps Aruba Wi-Fi, Zigbee IoT sensors
Aruba announced that Rotana Hotels and Resorts has deployed the vendor’s Wi-Fi technology to deliver high-speed and uninterrupted connectivity for guests, staff, and business applications, while creating a platform on which to continuously deliver innovative, differentiated guest experiences. The implementation has enabled increase in allocated bandwidth per session from 8mbps to 25mbps, resulted in an average of 25% increase in guest satisfaction with wireless services, and saves an average of 35% of man-days required for solution management and administration.
Aruba’s integration with Zigbee has made it possible to consolidate IoT gateways with
the network. Doing so has allowed the Rotana Hotels and Resorts to leverage smart sensors and devices such as digital locks that make guest experiences more convenient and effortless.
Full wireless access to Guest Services Management greatly enhances staff mobility and flexibility, improving their efficiency, and productivity. The technology provides reliable, efficient, and secure connectivity for point of sales terminals critical to conveniently billing guests and has enabled the introduction of Chromecast Solutions that offer guests high-quality media streaming.
In hospitality today, Wi-Fi is considered to be an essential amenity and any disruption or
tiveness by digitalising its operations. As part of these efforts Nokia will replace its on-premises HR systems with Oracle Cloud HCM. Nokia selected Oracle Cloud HCM for its ability to standardise HR processes on a common data platform, which will enable Nokia to provide a consistent employee experience across teams and more easily manage and scale HR services globally.
Oracle Cloud HCM will enable Nokia to connect every process across the employee lifecycle, helping improve decision-making and reduce operational costs. With AI-powered technology such as digital assistants and hundreds of new capabilities added each quarter, Oracle Cloud HCM will also enable Nokia to take advantage of the latest innovations and best practices to operate its business more efficiently and better empower Nokia employees, people managers and HR professionals.
Wael Othman Corporate Director of IT and Business Solutions at Rotana Hotel Management Corporation.
degradation of the service can significantly impact guest satisfaction. As a leading brand, Rotana Hotels and Resorts recognises the role that reliable, high-speed connectivity plays, not only in fulfilling this expectation, but also in serving as the platform on which it can continuously deliver innovative, differentiated guest experiences.

REAL LIFE
54 JUNE 2022 MEA
Abu Dhabi Dept of Economic Development partners with SAP to become cloud services provider
The Abu Dhabi Department of Economic Development signed a memorandum of understanding with SAP. As part of the agreement, ADDED and SAP shall explore collaboration opportunities to enhance industry innovation and digital transformation, develop advanced

business models, nurture Emirati talent, and foster local digital competencies, particularly through supporting start-ups and small business enterprises SMEs.
In terms of the MOU, ADDED intends to leverage SAP’s UAE cloud offering while simul-

UAE oil firm Bunduq switches to Arcserve OneX afe’s immutable storage architecture
Arcserve, the world’s most experienced data and ransomware protection pro vider, announced that UAE-based oil firm Bunduq Company has switched to Arcserve OneXafe as its backup and storage solution. Bunduq can now leverage OneXafe’s scale-out immutable storage architecture technology to improve scalability, simplify its backup and replication process and enable substantial cuts to its storage footprint.
Before switching to OneXafe, Bunduq had a scale-up storage environment in place that had since proved inadequate for its needs. Limitations inherent in scale-up technology meant that the company could only store data within a fixed upper limit. At this point, they would be forced to add more storage controllers or look to system upgrades and newer models with higher capaci ties. With a growing volume of data, the solution was expensive and became increasingly complex to manage, with severe inefficiencies in data migration and workload resource allocation.
taneously enabling SAP to accelerate expansion in the region as an authorised cloud services provider. Both parties also intend to work together to develop emerging talent by training UAE nationals through in-country, global and virtual programs on technology, business, and behavioural skills. In addition, ADDED and SAP aim to support job seekers and freelancers through a new SAP-designed platform that will bridge the gap between supply and demand for full-time and freelance opportunities.
The support that ADDED and SAP will offer to SMEs and start-ups as part of the MoU will be delivered through “SAP.io” and “Grow by SAP” initiatives. In addition, both parties are exploring the feasibility of establishing a regional innovation centre in Abu Dhabi to deliver support to both public and private sector entities, and services.
ADDED and SAP have also stated their intention to explore and launch Industry 4.0 initiatives within Abu Dhabi, where SAP aims to create a Point of View POV document to propose mutually beneficial strategic initiatives. The POV document will focus on the main pillars of the Abu Dhabi’s strategy , including healthcare, education, economy, defence, security, and government efficiency. In addition, SAP intends to train individuals in the manufacturing sector in digital skills to succeed in Industry 4.0 while developing an emirate-wide framework to adopt consistent manufacturing standards.
REAL LIFE MEA 55 JUNE 2022
Muayad Fahmawi IT Supervisor, Bunduq.
Financial institutions can now connect to SWIFT through AWS, Google Cloud, Microsoft Azure
SWIFT announces it will enable financial institutions to connect to its network and applications through public cloud providers Amazon Web Services, Google Cloud and Microsoft - a move that will streamline access to the world’s
leading financial messaging service to enable new innovation while ensuring robust resiliency and security.
Customers will be able to connect to the SWIFT network through Alliance Connect
Riyad Bank implements Red Hat OpenShift, Ansible Automation for open hybrid cloud
Red Hat, announced that Riyad Bank, a financial institution in Saudi Arabia, implemented a hybrid cloud strategy built on Red Hat’s portfolio of open hybrid cloud technologies, including Red Hat OpenShift. Red Hat’s open innovation is a keystone of the bank’s drive to speed up innovation and time-to-market of digital services and products.
Riyad Bank is on a digital transformation journey aiming to boost its competitiveness in an expanding fintech market as well as contribute to achieving the Kingdom’s Vision 2030. To do this, the bank is working to increase financial inclusion and support development, growth and diversification in the banking sector, efforts that are driven in part by emerging IT advancements.

Riyad Bank chose to build a flexible platform based on containers and Kubernetes, seeking to improve IT team productivity and better respond to evolving business demands. The bank wanted a comprehensive, cloudnative solution that encompassed open-source code and open standards while also enhancing interoperability with current and future IT investment and limiting the total cost of ownership.

To meet these varied needs, Riyad Bank selected the industry’s leading enterprise Kubernetes platform in Red Hat OpenShift for cross-organisational deployment along with Red Hat Ansible Automation Platform to provide IT automation at scale. The bank has also enlisted Red Hat Consulting and used Red Hat
Virtual – a new connectivity option that enables users to deploy SWIFT VPN connections with the selected public cloud providers instead of hosting hardware in their own data centres. The new connectivity option continues SWIFT’s long track record of supporting its customers’ cloud strategies as part of its own vision to enable instant and frictionless crossborder transactions anywhere in the world.
SWIFT has worked with a number of early adopters – from new digital banks to global financial institutions – to shape its public cloud offering and final stages of testing are now underway. The new Alliance Connect Virtual service will become generally available later in 2022.
Learning Subscriptions to establish a framework for repeatable microservices and create a comprehensive training plan. The end goal is to foster a more open organisational culture and up-skill teams in agile methods like DevOps to help generate further efficiencies.
Ali Al Shami Country Manager, Saudi Arabia and Bahrain, Red Hat.
REAL LIFE 56 JUNE 2022 MEA
Athens Airport implements SITA Information Display, Airport Management, Operating Database

SITA completed the implementation of its airport management solution at Athens International Airport, delivering significantly improved airport processes, as well as operational and cost efficiencies. Using SITA’s Airport Management, Athens International Airport is, for the first time, able to share key operational data by opening its Airport Operating Database to its stakeholders – airlines, government agencies, air navigation service providers, and other entities – providing all parties with the same real-time, data-rich view of the airport.
Sharing event milestones, airport stakeholders have an extremely precise view of how various activities across the airport are integrated and can impact the overall operation. The airport operations team can, for example, see when a flight has departed from its desti-
nation, with better visibility of the expected arrival time in Athens. This allows the airport to plan ground operations more efficiently, assigning aircraft parking stands, gates, and other resources, ensuring on-time performance and avoiding unnecessary delays.
The system provides configurability like no other on the market. The newly launched system has already proven its value during the heavy snowstorms earlier this year – an unusual event for Athens that called for extensive de/anti-icing of aircraft. Within hours the Athens airport team managed to configure the tracking grid so that all stakeholders could plan the de/anti-icing processes effectively.
With a web-enabled application in place, the airport is also able to quickly inform and deploy employees and equipment where they are needed most, while gathering real-time
data on tasks completed – data that is shared with all stakeholders. The airport can now better plan key activities such as push-back times and align with air traffic control for ontime performance, avoiding long wait times on taxiways and runways.
Through SITA Information Display System screens installed throughout the terminals, Athens International Airport now provides tailored information to passengers’ frequently asked questions, from the location of ticket sales counters to walking times to the gate. This has further enhanced the passenger experience and improved navigation through the airport.
Moreover, the airport now has in place the technology to achieve its immediate goal of EUROCONTROL Airport Collaborative Decision-Making A-CDM certification.
REAL LIFE
MEA 57 JUNE 2022
HR, IT NEED TO JOINTLY
MONITOR INSIDE THREATS
In a threat landscape dominated by news of the latest ransomware attack, or unpatched vulnerability, it is understandable that IT teams focus a great deal of their efforts on hardening defences against external threats. And while this is certainly justified, and most definitely required, it is essential that a comprehensive security program also considers the threat from within.
Insider threats can take many forms though most commonly, the perception is that they are perpetrated by jilted employees who are keen on retribution for the wrongs they have suffered. This is one aspect of the threat as disgruntled employees with the right privileges can certainly wreak havoc.
But insider threats are not only made possible by malicious motivations – often, but it is also nothing more than negligence that results in employees unwittingly placing their organisations in the crosshairs of cyber criminals. Understanding the different kinds of insider threats is the essential first step in preparing to defend against them.
Not all disgruntled employees have the skills to be a threat, but they can be co-opted by external threat actors and enabled to cause damage such as launching a ransomware attack. In a survey of 100 IT and security executives on how hackers were approaching employees, undertaken by Pulse and Hitachi
ID in late 2021 and early 2022, 65% reported that they themselves, or one of their employees, had been approached to help launch a ransomware attack. That figure has risen substantially over recent surveys, likely because of the changed working environment created by the pandemic.
The State of Network Security 2021 report by Barracuda found that 81% of respondents said their organisation had been the victim of a security breach once in the last year. Indeed, companies with staff working predominantly from home had a significantly higher network security breach rate 85%, compared to companies with staff working predominantly in the office 65%. A full 74% of those surveyed said their organisation has been the victim of at least one ransomware attack in the last year.
Today, many people reveal much about their lives and their feelings on social media. Those expressing dissatisfaction with their employer or work environment make easy targets for criminals to co-opt into their activities and provide with the tools needed to mount an attack.
Resentment is not the only motivation for an insider attack: ambition can also be a motivator. An employee might steal information or inflict damage to harm another employee in the hope it will advance their own career.
And the motivation could be as simple as money: industrial espionage. An employee could steal proprietary information to sell to another company or do so at the behest of a competitor.
NEGLIGENT INSIDERS
Any insider who fails to follow security protocols and practices can become a threat. There are many reasons why they might do so: deliberate negligence many security protocols are seen as standing in the way of getting work done; occasional inadvertent lapses; inadequate training.
COMPROMISED INSIDERS
Compromised insiders are those who have unwittingly enabled an attack, most often by falling for a phishing exercise, and then either downloaded malware or revealed their log-on credentials.
Once an attacker has compromised an insider, they can take their time to exploit the access gained. They can add the compromised device to a botnet and then use it to mount a DDoS attack or use it to mine cryptocurrency.
However, they most frequently use this compromised device to explore the corporate network behind it, moving laterally to other devices and other accounts, gathering more credentials until they gain sufficient access to steal valuable data, launch a ransom attack or sabotage critical systems.
HOW TO COMBAT INSIDER THREATS
There are many steps organisations can take to counter insider threats, either stopping them at source, or detecting and blocking those that do breach cyber defences.
KEEP EMPLOYEES HAPPY
It will never be possible to keep ever employ
GUEST COLUMN
IT is rarely in a position to identify a disgruntled employee, until that employ vents on IT systems, while HR is much better placed to recognise this.
58 JUNE 2022 MEA
happy all the time, but should be the aim of every organisation, regardless of security issues. This means having first rate HR practices to ensure promotions and pay rise decisions are fair and reasonable. It means having clear and honest communications from leaders to subordinates at every level of the organisation. Every employee that does not become disgruntled is one less potential threat.
HR AND IT MUST WORK TOGETHER

IT is rarely in a position to identify a disgruntled employee, until that employ vents their displeasure on the IT systems. HR is much better placed. Therefore, HR and IT should meet regularly so IT can be briefed on any employees they need to keep an eye on, perhaps even implementing more restrictive access requirements. HR should routinely tell IT about any employees who have transgressed and been disciplined or passed over for a promotion.
While IT cannot detect employee displea-
sure, it can detect activity that might precede an insider attack, for example, an employee logging in or entering the premises at abnormal times or accessing data not relevant to their role. It should then identify these individuals to HR for further monitoring.
TRAINING IS PARAMOUNT
Security awareness training has progressed by leaps and bounds in recent years in parallel with the rise in phishing and other deceptions. Once it was a case of getting employees to watch a video and sit some sort of test once or twice a year.
Today’s security awareness programs are much more sophisticated. They simulate phishing attempts to determine employees’ susceptibility and identify those most needing training. They include focussed and personised training that targets the weaknesses identified in those employees.
Aside from these approaches, gamification has become a popular tool to build and
maintain a high level of cyber vigilance among staff. Organisations stage monthly or quarterly games where simulated phishing emails are sent to staff and prizes are awarded to those who detect and report them. Such exercises can motivate the most cynical employees and help to maintain a high level of threat awareness across the workforce.
The adage trust but verify is widely used but makes no sense: it really means don’t trust, verify instead. The bar for trusting has been progressively raised: from simple passwords to single sign-on SSO, role-based permissions, and multi-factor authentication MFA, but ultimately these are all trust-based access controls. Once the applicant has passed these hurdles, they are trusted: trusted with access to sensitive information and vital applications.
If an attacker has managed to gain access to the required credentials, they are free to wreak havoc. Or if a legitimate user is compromised after they have passed the access hurdles, they become a danger.
There is no way to eliminate insider threats completely, but the steps outlined above will greatly reduce their incidence and enable an organisation to a much better job of detecting and countering. ë
GUEST COLUMN
TONI EL INATI RVP Sales, META and
CEE,
Barracuda Networks.
MEA 59 JUNE 2022
Those expressing dissatisfaction with their employer or work environment make easy targets for criminals
CASB AN ORGANISATION’S
CLOUD CYBERCOP
resources, but it can also enable the organisation to identify what flows in and out of the cloud.
access to sensitive data. Security features such as data leakage prevention and access control minimise the possibilities of data leakage.
#4 THREAT PROTECTION
In 2018, shortly before leaving his job, an engineer who worked for a US Navy contractor transferred over 5,000 files to his Dropbox and emailed a few of the documents to himself. These documents contained sensitive information about company finances and intellectual property pertaining to product designs.
Incidents of data leakage like this have assumed more significance in the present hybrid workforce era. The proliferation of cloud applications used by employees has brought productivity, ease of use, and scalability to work. At the same time, however, it has also brought an increased risk of shadow IT, data exfiltration, and insider threats.
Simply put, organisations may not know which of the numerous SaaS applications their employees are using contain sensitive data. Considering this situation, it’s essential that organisations broaden their security approach with cloud protection capabilities. A cloud access security broker cloud access security broker can help with precisely this.
Analyst firm Gartner first defined the phrase cloud access security broker in 2012. A cloud access security broker is a solution that sits between an organisation’s users and the various cloud services they access. Because of where it sits, a cloud access security broker can not only help an organisation authenticate and authorise users as they attempt to access cloud
Listed below are four key capabilities offered by a cloud access security broker:
#1 VISIBILITY
While the cloud makes it easier for teams to collaborate, employees still use different unauthorised and unknown cloud applications, known as shadow applications, for better and quicker results. However, the use of shadow applications is a big issue for the IT team. A cloud access security broker helps IT security teams overcome the issue of shadow applications by providing visibility into cloud app usage, apps accessed from unmanaged devices, users accessing and modifying data on the cloud, and much more for holistic cloud security monitoring.
#2 COMPLIANCE
A cloud access security broker helps with meeting compliance requirements by ensuring the security of data, both in transit and in storage. It also safeguards organisations from data exfiltration by monitoring data leakage from the cloud. A cloud access security broker helps meet a variety of compliance standards, including the GDPR, CCPA, HIPAA, and LGPD.
#3 DATA SECURITY
One of the core objectives of a cloud access security broker is to ensure data security. A cloud access security broker monitors access to data on the cloud and identifies unauthorised
A cloud access security broker provides security against both internal and external threats that organisations face. It learns behaviour patterns of users and develops a baseline. Whenever a deviation from the baseline is noticed, the cloud access security broker alerts the security team to remediate the threat.
An organisation’s security operations centre may be highly reliant on a security information and event management SIEM solution today. Within the next two years, you need to ensure that your SIEM solution either integrates seamlessly with an external cloud access security broker or has built-in cloud access security broker capabilities.
There are five strong reasons for doing so: to address the high uptake of cloud applications, correlate events that happen in different parts of the network, prevent data leaks, provide visibility into shadow IT, and offer visibility into identity and access management.
#1 ADDRESSING THE HIGH UPTAKE OF CLOUD APPLICATIONS
Research suggests that the average employee uses 10 SaaS applications every day, and organisations on average use 254 applications. These applications could range from third-party analytics tools that ingest customer data sets to consumer versions of approved enterprise apps like Microsoft 365 or Google workspace. On top of that, they may use some of these
GUEST COLUMN
A cloud access security broker provides security against both internal and external threats that organisations face, learning behaviour patterns of users and developing a baseline.
60 JUNE 2022 MEA
applications on their own mobile devices.
As if the risks posed by utilising all these tools were not enough, most organisations nowadays use a multi-cloud environment with various PaaS and IaaS delivery models. This is why organisations need a cloud access security broker enabled SIEM solution that gives visibility into the applications in use and how they are being used. With such a solution, organisations will know the level of risk posed by a particular application.
#2 CORRELATING EVENTS THAT HAPPEN IN DIFFERENT PARTS OF THE NETWORK
Cyberattacks have become sophisticated in recent times; there have been instances of living-off-the-land attacks, cloud malware with initial access in an on-premises server, cloud ransomware and disruption ware, and insider attacks. Organisations need the ability to see patterns and correlate seemingly unrelated events that happen in different parts of the network, and to group them together as a single security incident.
#3 PREVENTING DATA LEAKS
With the advent of cloud apps, there is a substantial risk of both intended and unintended
data leaks. For example, an employee in the marketing department may use an app called Font Candy to create vibrant typography. However, this app may be unsanctioned within the organisation, and the employee may have private contact details and classified information stored within it at risk of being leaked. In such a scenario, managing unauthorised uploads of sensitive data and preventing data leaks is crucial. With a cloud access security broker, one can enforce cloud security policies and controls to prevent data from being transferred over the internet.
#4 PROVIDING VISIBILITY INTO SHADOW IT
Nowadays, most organisations have a list of sanctioned cloud apps that employees can use if they wish. These applications could have become sanctioned after the organisation deemed them to be secure and effective for employee productivity. The sanctioned applications are either owned or controlled by the organisation. On the other hand, shadow applications fall outside the ownership or control of IT teams. Shadow applications may have vulnerabilities and loopholes that could be exploited by attackers. A cloud access security broker provides visibility into the usage stats of
RAM VAIDYANATHAN Product Manager, ManageEngine.

these applications and the identity of users who use these applications frequently.
#5 OFFERING VISIBILITY INTO IDENTITY AND ACCESS MANAGEMENT
According to Erik Wahlstrom, Research Director at Gartner, organisations should not replace their identity and access management programs with CASBs, but rather intersect the two for increased governance and access control of cloud applications.
A cloud access security broker can provide better identity and access management through adaptive authentication and userbased risk analysis. By bringing this capability within SIEM, organisations will be able to see the risky behaviour of users in a single console and use playbooks and workflows to respond to these threats.
A cloud access security broker has become an integral part of any organisation’s defence strategy. It can help defend against the use of shadow applications and data exfiltration into the cloud. An effective cloud access security broker will integrate seamlessly with a SIEM solution, and will provide network visibility, data security, compliance management, and threat protection. CASBs can help improve the security posture of organisations. ë
GUEST COLUMN
MEA 61 JUNE 2022
Most organisations use a multi-cloud environment with various PaaS and IaaS delivery models
BUILDING ZERO TRUST FRAMEWORK IN AN
OT-IoT ENVIRONMENT
A Zero Trust architecture, prior to allowing a machine or user to connect to the network, should verify whether that connection can be made safely.
KHALID ALJAMED
Regional Director for Middle East and Africa, Nozomi Networks.

GUEST COLUMN
62 JUNE 2022 MEA
Zero Trust is a framework that disallows connectivity by assuming there is risk unless proven otherwise
Zero Trust is not a clearly defined standard. Each vendor seems to take liberties to match their focus. This makes it a very fluid conversation. What should it do? What problems should it solve?
Zero Trust somehow switches the mentality of the network from allowing access by default, to blocking access by default unless required.
A lofty goal, but what does it really imply?
Context is very important for Zero Trust policies. A Zero Trust architecture, prior to allowing a machine or user to connect to the network, should verify whether that connection can be made safely. The connection should be established to be the minimum number of resources that it needs. These checks should be done on a per-session basis instead of once-off at the start.
Incorporating context into Zero Trust policy decisions stands in stark contrast to the usual allow-list approach of Zero Trust implementations. Obviously, identity is important to verify but it still does not really help assess whether the connection can be made safely and should be allowed, especially if the device has been compromised.
Zero Trust is a framework that disallows connectivity by assuming there is risk unless proven otherwise. Rather than simply defining a minimalist access policy, security posture and context can play a role in improving Zero Trust security. This helps significantly reduce risk by making more informed decisions about connectivity.
Now how do you do this in an OT-IoT infrastructure?
ZERO TRUST FOR OT-IOT
Here is a basic check list:
l Does micro-segmentation make sense for OT?
l What about user agents?
l Where do you start?
l What if traffic is blocked?
l What impact will that have on the process?
It is totally normal in IT to block traffic, but in OT-IoT, this is risky. Simply blocking it might just impact production more than allowing traffic. Many OT-IoT devices such as controllers, sensors, robots, and so forth are headless. Very often, security was not a consideration when these products were developed.
To make better-quality decisions about connectivity, you need better information. Understanding what you are trying to protect is where it all starts. It is identical to IT, but the method of getting there differs.
It is about knowing the type of devices, what hardware and software is used and what the expected behaviour of those devices is. It is also about knowing how the entire OT-IoT environment behaves, which machine speaks to another machine? With what protocol? What payload is exchanged? At what frequency?
If you understand this in real-time, you are well on your way towards an optimal Zero Trust for OT-IoT environments.
DECISION MAKING FOR OT-IOT
Gathering information must lead somewhere – it should be converted into actionable intelligence and, ultimately, actions. Knowing hardware and software versions will lead to knowing what vulnerabilities apply to those monitored devices, whether those devices are still supported by their vendors, and how they should act on the network.
Knowing the behaviour of entire OT-IoT networks also implies the ability to detect and alert upon anomalies.
If, suddenly, devices that never communicated with one another start doing so or if there were communications before, but it is now displaying entirely different behaviour, it justifies investigation into the legitimacy of it. It is very possible that this is the start of a breach.
Data gathered towards Zero Trust should not just be an observation or a statement on what the likely issue is. It should help determine what impact it has on the entire OT-IoT network.
With regards to enforcement of a Zero Trust policy, even in OT-IoT, sometimes it is justified to automate interventions by blocking traffic. The suite of tools that form the cyber defence mechanism should play nice and exchange information to act as fast as possible, so that each function can be fulfilled effectively.
Pair all of this with digital transformation in OT-IoT and we have the perfect storm on our hands, which a Zero-Trust approach can help to mitigate. ë
GUEST COLUMN
MEA 63 JUNE 2022
USING AI TO BUILD ONLINE
CATALOGUES FOR MARKETPLACES
An increasing number of people are buying online and that is why e-commerce strategies revolve around how they can create and manage detailed catalogues.
The use of artificial intelligence is quickly increasing, and many major breakthroughs are being made in the business world. In today’s era of digital commerce, the applications of artificial intelligence in product cataloguing and management have become critical. Artificial intelligence is not just available for creating customized shopper experiences, it is also revolutionizing the way a company operates internally.
The booming growth of the e-commerce industry is a testament to its validity. Especially after Covid, an increasing number of people are buying online because they find it convenient and easy. This is why most e-commerce businesses’ entire strategies revolve around how they can create and manage detailed catalogues to attract and help customers make informed purchase decisions. Moreover, to stay ahead of the competition, businesses need to create differentiated catalogues to connect with customers and develop trust, credibility, and engagement.
A star catalogue hits all the right chords to sell the product, but it also increases the cost
manifold. From the production cost of photoshoot to the manual tasks of editing, publishing, and managing a catalogue, there are challenges that can significantly slow the time-to-market leading to diminishing margins.
Integrating artificial intelligence in the cataloguing workflow can help businesses create appealing catalogues at speed and at scale. Artificial intelligence can also automatically recognise visuals, generate tags on product images, and leverage consumer data and patterns to create personalized pricing strategies.
Product images signify 86% of the consumer’s purchase decisions across all the industries including auto, food, fashion, retail. When product images decide the sell ability, setting up an online marketplace with no images or low-quality images, only pushes you back in the competition.
The biggest challenge that businesses face is planning the entire photo shoot to image uploading process that is both time-taking and expensive.
Currently, the only solution that exists across the industry is building and booking a physical studio and hiring professional photographers and editors. This exposes merchants to multiple challenges that only delay their product’s go-tomarket timelines.
An easier and less expensive alternative to product photoshoots by professionals is
taking pictures from smartphones. Given the advancement in camera technology in today’s smartphones, anybody can do a self-shoot of their product right from their phone.
There are also multiple photo editing apps that promise realistic, professional finished images. However, they are not standardized for
GUEST COLUMN
64 JUNE 2022 MEA
It is adept at processing things much faster than humans could and has the competency to automate repetitive tasks to create higher efficiency
commercial photography and may not adhere to standard marketplace image guidelines.
Advancements in artificial intelligence technologies enable anyone to click product images through the smartphone and instantly process them into studio-finish images.
In this process, artificial intelligence is
helping identify and solve challenges with smartphone-shot images that could match with the actual professionally shot studio images. Challenges such as background removal and replacement, shadow generation, colour corrections, image clipping, angle perspective corrections, etc are the differentiating factors that
SANJAY KUMAR

are now being solved with artificial intelligence.
These artificial intelligence-powered solutions in photoshoots and post-production for cataloguing are now enabling businesses and marketplaces to create high-quality studiofinish images at scale, up to 500x faster process, and at a fraction of cost without a physical studio.
There are more ways in which artificial intelligence solves the challenges of cataloguing. It can automatically recognize images, generates tags on product images, and leverage consumer data and patterns to create personalized pricing strategies.
The list does not end here, there is a need for a more efficient repository of data, smart product classification, and faster catalogue publishing. Artificial intelligence is already cracking these codes. ë
GUEST COLUMN
Co-Founder and CEO, Spyne.
MEA 65 JUNE 2022
You probably interact with artificial intelligence every day and do not even realize it
What’s trending






SOCIALLY SPEAKING


SOCIALLY SPEAKING
What’s trending




SOCIALLY SPEAKING



SOCIALLY SPEAKING
Bader Almadi moves from Dell to join Google Cloud as Country Manager, Saudi Arabia

Google Cloud announces the appointment of Bader Almadi as Country Manager, Kingdom of Saudi Arabia at Google Cloud. Based in Riyadh, Bader is responsible for leading Google Cloud’s strategy across the Kingdom. His professional remit covers growing Google Cloud’s team in Saudi Arabia and supporting the growth and scaling of customers across a variety of industries spanning Retail, Healthcare, Financial Services, Entertainment and several others. Bader will also focus on scaling Google Cloud’s partnership ecosystem in the kingdom.
Bader brings 16 years of information technology and tech sales leadership and expertise to this role. He joins Google Cloud from Dell Technologies, where he was Country Enterprise Director for Telecom, Cloud and Financial Services’ industries leading the relationship with Saudi conglomerates such as STC, Zain and Mobily, and customers in Banking and Cloud Services providers.
Lumenore, a cloud-based business intelligence and advanced analytics solutions provider, announced that it had appointed a new EMEA Sales Director to lead the expansion and growth of the company in the region through increased client acquisitions. In a statement, Lumenore said that Simon Karacinski, who will now lead the EMEA sales team, comes from a versatile background of expertise and experience across the technology spectrum.
Cloud Box Technologies announced the appointment of Biju Unni as Vice President. His vast experience is a value add especially at a time when the company is set to accelerate its entry into multiple new business streams that will focus on Cloud adoption by both the enterprise as well as SMB sectors.

Speaking on the appointment, Ranjith Kaippada, Managing Director, Cloud Box Technologies said, “Biju brings with him a wealth of experience especially in areas that are a part of our immediate and future growth plans. His overall management skills spanning across operations, service and delivery as well as change business management will help us in supporting and building on our customer portfolio and taking that quantum leap ahead.”
Biju brings a total of over 23 years of experience spanning across the IT sector and has been a true leader with strong commercial business capabilities that have resulted in robust financial results. Coupled with his valuable people skills, he is known to inspire and bring out the best from his team.
Anthesis Group expanded its Middle East service offering with the strategic appointment of Arvind Gautam, as Principal Consultant. Based in Dubai, UAE, Arvind brings over 11 years of sustainability and green economy expertise to Anthesis in the Middle East, having previously advised Governments and private organisations across India and the Middle East, on sustainability issues regarding oil & gas, transport, power & utility, and manufacturing.
Prior to joining Anthesis, Arvind held the roles of Chief Sustainability Specialist at the Roads & Transport Authority Dubai, Energy & Sustainability Manager at Protiviti, and as a Senior Consultant for PwC India.

As Principal Consultant, Arvind will build upon Anthesis’ global sustainability expertise in ESG and Net Zero, to bring innovative sustainability services to the Middle East region as organisations increasingly recognise the importance of sustainability as business imperative. His appointment also further strengthens Anthesis’s ability to deliver for clients across the UAE, Qatar, Saudi Arabia, Oman, Bahrain, Kuwait, and further afield.
Simon started his career in the UK in 2007, working for one of the leading B2B IT, Technology telemarketing companies with clients across the technology spectrum. He has been lauded as one of the top salespersons in the industry, and he boasts a vast repertoire of experience that spans from hardware to software and from blue-chip vendors to tech start-ups.
At Lumenore, Simon’s role will be to execute the EMEA GTM strategy, build a team and an enterprise channel, and drive growth through new business and existing customers.
Simon moved to Dubai in 2014 and joined K2 Middle East, the global enterprise digital process automation vendor under the Nintex umbrella. Engaging with a broad range of enterprise customers, prospects, and partners, Simon successfully developed his regional knowledge and experience in the enterprise sector.
 Simon Karacinski joins advanced analytics solution provider Lumenore as EMEA Sales Director
Biju Unni joins Cloud Box Technologies as Vice President
Simon Karacinski joins advanced analytics solution provider Lumenore as EMEA Sales Director
Biju Unni joins Cloud Box Technologies as Vice President
EXECUTIVE MOVEMENT 70 JUNE 2022 MEA
Arvind Gautam joins Anthesis Group in Middle East as Principal Consultant
Cloudflare opens regional office in Dubai, Bashar Bashaireh joins as MD Middle East and Turkey
Cloudflare, announced that Dubai, UAE, will be the home of its first office in the Middle East, to further support its growing EMEA operations. Dubai represents a growing Cloudflare team presence in the Middle East and Turkey, following the company’s EMEA headquarters in London, and offices in Munich, Paris, and Lisbon. Cloudflare’s Dubai-based team will help the company grow brand awareness, acquire and support customers, and recruit new talent.
As part of the announcement Cloudflare is welcoming its first managing director of the Middle East and Turkey, Bashar Bashaireh, an experienced regional leader with more than 25 years of industry experience in software and technology, who will lead this new office and team.
Cloudflare started to invest in the region by expanding its network into the Middle East and Turkey in 2015. Now with data centres spanning more than 270 cities in over 100 countries worldwide, the company continues to grow its presence to be even closer to Internet-connected users everywhere. In the MET region Cloudflare has 27 data centres located in Bahrain, Iraq, Jordan, Saudi Arabia, Kuwait, Lebanon, Oman, Qatar, Turkey, and UAE.
Nutanix announced the appointment of Rukmini Sivaraman as Chief Financial Officer. Sivaraman will succeed Duston Williams, who is leaving to become CFO of a pre-IPO company in a different space. Williams will remain with Nutanix through April 30, 2022 and work closely with Sivaraman to facilitate a seamless transition.

Sivaraman joined Nutanix in 2017 and currently serves as Senior Vice President of Financial Planning & Analysis. In this role, Sivaraman has been responsible for financial and strategic planning, budgeting, capital allocation and business analytics and insights. Sivaraman has held several roles instrumental to the Company’s growth and transformation, including Chief People Officer, and before that Senior Vice President of People and Business Operations, focusing on revenue growth, capital allocation, and all aspects of human resources.

Veeam announced it has appointed John Jester as Chief Revenue Officer. Jester will lead Veeam’s go-to-market growth strategy and help build upon Veeam’s position as the #1 provider of Modern Data Protection solutions spanning Cloud, Virtual, Physical, Hybrid, SaaS and Kubernetes.


Jester joins Veeam from a successful tenure at Google Cloud where he helped build the go-to-market organisation through his leadership of the Customer Experience organisation; in this role, he drove cloud adoption and business value for customers, supporting Google Cloud’s growth to over $23B ARR. Prior to Google, Jester spent 20 years at Microsoft leading sales organisations and reimagining the GTM across the customer lifecycle.
Alteryx, announced that Jason Janicke has been appointed as senior vice president of Europe, the Middle East and Africa. Janicke will report directly to Alteryx president and chief revenue officer Paula Hansen and will lead Alteryx’s business strategy, business activities, and operations in the region. He will play a crucial role in driving the company’s next phase of growth and accelerate its presence in the cloud as Alteryx strengthens its position as the leader in analytics automation.
Janicke brings more than two decades of experience in building and leading high-performing, customer-centric teams across EMEA and the Americas as a SaaS sales veteran at some of the world’s largest enterprise technology companies. He joins Alteryx from Conga where he was responsible for developing successful customer, partner and alliances focused go-to-market initiatives, driving significant new recuring revenue growth across EMEA. Prior to Conga, Janicke was area vice president of sales at Salesforce.
Rukmini Sivaraman takes over from Duston Williams as Chief Financial Officer of Nutanix
John Jester moves from Google Cloud, joins Veeam as Chief Revenue Officer
EXECUTIVE MOVEMENT MEA 71 JUNE 2022
Jason Janicke moves from Conga, joins Alteryx as Senior Vice President EMEA
2022 ROADSHOW
JULY-NOVEMBER
2022
World's largest technology excellence program
#LeadX
WHERE TECHNOLOGY IS BORDERLESS, AMBITIONS ARE FEARLESS, AND LEADERSHIP IS LIMITLESS

Algeria
Bahrain
BOTSWANA
Canada
China
Egypt
Estonia
France
Germany
Ghana
Hong Kong
India
Indonesia
Italy
Ivory Coast
Japan
KSA
Kuwait
40 COUNTRIES 4000 C-LEVEL EXECS
Mauritius
Malaysia
Morocco
Nigeria
Oman
Pakistan
Phillipines
Qatar
Russia
300+ SESSIONS
200+ EXHIBITORS
Singapore
Slovenia
South Korea
South Africa
Spain
Srilanka
Switzerland
Tanzania
Thailand
Tunisia
Turkey
UAE
Uganda
UK
USA
Vietnam
BROUGHT TO YOU BY

 Loubna
Loubna


















































































































 PRAMOD SHARDA CEO IceWarp, India and Middle East.
PRAMOD SHARDA CEO IceWarp, India and Middle East.


















 President and CEO.
President and CEO.




 Rashid Khan CPO and Co-founder, Yellow.ai.
Ashish Ray
Vice President, Product Management, Oracle.
Rashid Khan CPO and Co-founder, Yellow.ai.
Ashish Ray
Vice President, Product Management, Oracle.
































 Simon Karacinski joins advanced analytics solution provider Lumenore as EMEA Sales Director
Biju Unni joins Cloud Box Technologies as Vice President
Simon Karacinski joins advanced analytics solution provider Lumenore as EMEA Sales Director
Biju Unni joins Cloud Box Technologies as Vice President




