GROWTH IN 2022 SUPPORTING NETWORKING
2022 will see adoption of solutions using cloud computing, machine learning, artificial intelligence, data science, software engineering, cybersecurity, running on networking platforms.
General Manager, TP-Link



2022 will see adoption of solutions using cloud computing, machine learning, artificial intelligence, data science, software engineering, cybersecurity, running on networking platforms.
General Manager, TP-Link


Oracle launched the Abu Dhabi cloud region inside UAE, making the country a redundant geography with two cloud regions including the previously launched Dubai Cloud region. The two regions are being beefed up to support 80+ Cloud services available from Oracle Cloud Infrastructure globally.
Speaking at the event, Oracle’s Ahmed Adly, pointed out that Oracle had one of its best ever quarter earnings ending in November 2021. We are pivoting at the right time, he pointed out.
Sean Murphy, Chargé d’Affaires at the United States Embassy, Abu Dhabi, pointed out that the launch of the cloud regions in UAE, are a model of Emirati and US business innovation. Oracle is an example of a US company dedicated to UAE, the regional digital hub. Oracle remains committed to promoting cross border, data transfer flows.
Symphony Technology Group announced the launch of Trellix, a new business delivering extended detection and response to organisations with a focus on machine learning and automation.
Trellix emerges from the previously announced merger of McAfee Enterprise and FireEye in October 2021. Trellix will deliver living security that learns and adapts to protect operations from the most advanced threat actors.
Enterprises are engaged in digital transformation and the attack surface they need to protect is growing rapidly and is very dynamic influenced by work from home and cloud adoption. That is absolutely one of the challenges that Trellix can help enterprises with, said Adam Philpott, Chief Revenue Officer, Trellix.
More than a month after the initial announcement of the vulnerability impacting Log4j on December 9, 2021, there are still medium- and long-term consequences to be considered. The biggest concern for CIOs and CISOs is the loss of trust in legacy vendors.
Roland Daccache from CrowdStrike says CISOs have concerns because of the recent security incidents and disclosed vulnerabilities that go beyond their ability to control, with the amount of budget and resources available at their disposal. It does not help the case that most exploitable vulnerabilities are coming from the sources that they need to rely on most.
Apache Log4j shines a bright light on the risky but necessary practice of relying on open-source code libraries to build enterprise-scale applications. Many organisations around the world rely on open-source libraries as a key element in their ability to bring applications to market quickly. Yet, these libraries often stop short of a security-first approach. This dependence on what is effectively a wild, wild west of code libraries will continue to leave organisations vulnerable until time and resources are invested to make them more secure, says Glen Pendley from Tenable.
And in our principal feature of the month, we look at how managing business continuity need to be integrated across the enterprise and is not a point function of one department and one executive.
Hoping that 2022 is moving forward on a positive note. Happy winter months ahead. ë
MANAGING DIRECTOR
TUSHAR SAHOO
TUSHAR@GECMEDIAGROUP.COM
EDITOR ARUN SHANKAR
ARUN@GECMEDIAGROUP.COM
CEO RONAK SAMANTARAY

RONAK@GECMEDIAGROUP.COM
GLOBAL HEAD, CONTENT AND STRATEGIC ALLIANCES ANUSHREE DIXIT
ANUSHREE@GECMEDIAGROUP.COM
GROUP SALES HEAD RICHA S RICHA@GECMEDIAGROUP.COM
EVENTS EXECUTIVE GURLEEN ROOPRAI
GURLEEN@GECMDIAGROUP.COM
JENNEFER LORRAINE MENDOZA JENNEFER@GECMDIAGROUP.COM
SALES AND ADVERTISING
RONAK SAMANTARAY
RONAK@GECMEDIAGROUP.COM
PH: + 971 555 120 490
PRODUCTION, CIRCULATION, SUBSCRIPTIONS INFO@GECMEDIAGROUP.COM
CREATIVE LEAD AJAY ARYA
GRAPHIC DESIGNER RAHUL ARYA
DESIGNED BY SUBSCRIPTIONS INFO@GECMEDIAGROUP.COM
SOCIAL MARKETING & DIGITAL COMMUNICATION YASOBANT MISHRA
YASOBANT@GECMEDIAGROUP.COM
PRINTED BY Al Ghurair Printing & Publishing LLC. Masafi Compound, Satwa, P.O.Box: 5613, Dubai, UAE
# 203 , 2nd Floor
G2 Circular Building , Dubai Production City (IMPZ) Phone : +971 4 564 8684
31 FOXTAIL LAN, MONMOUTH JUNCTION, NJ - 08852 UNITED STATES OF AMERICA PHONE NO: + 1 732 794 5918
A PUBLICATION LICENSED BY International Media Production Zone, Dubai, UAE @copyright 2013 Accent Infomedia. All rights reserved. while the publishers have made every effort to ensure the accuracyof all information in this magazine, they will not be held responsible for any errors therein.

20-21
SPECIAL REPORT
Oracle’s twin Cloud Regions in UAE are now operational supporting UAE’s Fourth Industrial Revolution Strategy
22-23
SPECIAL REPORT
Oracle Cloud regions to boost performance and innovation for businesses inside UAE


28-31
INNOVATION
INFINITE BLUE: Bringing business continuity into mainstream operations

32-33
INNOVATION
TRELLIX: EXCLUSIVE Adam Philpott on why Trellix, formed from merger of McAfee and FireEye, represents living security
34-34
INNOVATION
LOG4J: Vulnerabilities around Log4j library: In the rush, did we miss something?
45-47
ANALYST CORNER
48-49
GUEST COLUMN
Seven trends helping to make modern enterprises more secure
50-51
GUEST COLUMN
While CIOs manage transformation, CISOs navigate security overloads
52-54

BROUGHT TO YOU BY

Vendors have touted security as a key selling point and wonder why prospective customers do not seem to engage on that topic as much as anticipated.
Iwas recently perusing data from Gartner Peer Insights on content services platforms, when I noticed something surprising near the bottom of the priority list. Content security was hovering there near the bottom of the list of end-users reported priorities. It was in either #12 or #15 out of 15 priorities that could be selected depending on which time frame I looked at.
It is hard to imagine a content platform owner that would say security is not important, so why does security rate so low?
Indeed, security is a prominent feature on nearly all RFPs and is often weighted quite heavily. This finding is validated by conversations with vendors who have touted their security as a key selling point and wonder why prospective customers do not seem to engage on that topic as much as anticipated.

This seems to be an example of where a low rating means overlooked or taken for granted rather than being an explicit statement that something is bad or unnecessary.
Here is why:
l Buyers consider it a given or table stakes. Of course, security is important, but it is assumed no product could exist with bad security, so the other features are much more important as differentiating vendors.
l Buyers do not know what to ask or how to rate. This can be seen in evaluations that simply tell us about security or list a bunch of standards that may not even be applicable.
l Buyers outsource security considerations to the security team. Buyers of content service providers are experts in how the content will be created and consumed by the business. They are not security experts. In fact, they are often happy to have specialists in security handling those issues. If the surveys were taken by security personnel, I am sure security would rate at the top, but they do not own the content services platform.
What should content services platform vendors do about a feature that seems simultaneously critical and an afterthought? As with all messaging, the key is to understand your audience. And in this case, there are two: the content services platform buyer and their security team.
Product marketers need to use the primary messaging, which will be targeted at content services platform buyers, to describe security in terms
that those buyers will understand. That includes how the end user is engaged with security protocols and what their user experience will be. Then you also need to prepare separate in-depth messaging for the security professional that will be brought in during the process. And product leaders need to invest more in security than buyer interest would sometimes dictate. For security-minded buyers, content security will weigh heavily into the conversion. And even for less security-minded buyers, content security is a consideration factor – you won’t even get on the shortlist without a good security reputation. ë

Product leaders need to invest more in security than buyer interest would dictate
CRAIG ROTH, VP Analyst, Gartner.





Evolution in wireless is inevitable, with 24 billion connected devices and over half of these connected wirelessly and capable of transmitting HD content.
The role of the LAN is changing and will continue to do so for the foreseeable future. Failing to keep up will affect productivity, competitive position and reputation. So how do you keep up with the demands of new technologies, platforms, and users? Or ensure you have enough useful redundant spare capacity? Let’s take a look at the key drivers for change.
Just a few years ago, in-building resources were devoted to single functions, such as telephony, internet, or security. The technology and business drivers for bringing these services together on a single converged platform are here to stay. However, trends such as hot-desking and smart-desking are now being adopted more widely following Covid-19 measures.

More and more network managers are discovering the cost and efficiency benefits of having only one network to manage. An Everything over IP or All-IP approach, linking building management and devices to the building network over Ethernet, Internet Protocol, allows previously separate systems to merge. Cabling provides Power over Ethernet as well as a physical communication layer.
The fast global uptake of connected LED lighting, sensor technology, and IP-equipped devices are making Power over Ethernet a necessity. Providing current over Ethernet cabling allows devices to be installed and moved around without having to worry whether there’s an electrical outlet close by. Power delivered through new generations of PoE is more than six times the level of the initial PoE standard.
What IS more, some applications, for example in the areas of signage, lighting and security require continuous power. This means a significantly increase heat build-up inside cable bundles, which may disrupt network IP traffic. This requires a new look approach to planning, installing and operating the network.
Evolution in wireless technology is inevitable, with 24 billion web-con-
nected devices. Over half of these are connected wirelessly and are capable of transmitting HD content. Wi-Fi 6 is ideal for the Internet of Things and designed to connect the largest possible number of devices. As more devices share wireless bandwidth it can become increasingly diluted, even to the point of becoming unusable.
As Wi-Fi6 makes more advanced applications possible, the LAN needs to provide ubiquitous capacity, with plenty of bandwidth reserves, to the Wireless Access Point. To benefit from the higher speeds and lower latency Wi-Fi 6 brings, it is important that there are no weak – outdated – links in your connectivity chain. Wi-Fi 6 WAPs will often require compliance with the PoE+ standard 802.3at.
You may need to accommodate a large number of new devices to support IoT or edge computing applications. Or you might need to introduce a large number of new employees. Production plants may need to increase the number of connected devices or accommodate machine-to-machine communications.
A Fibre to The Office solution can help. It provides Gigabit Ethernet to end user devices by combining passive fibre cabling and active switches. High bandwidth reserves and availability of a single fibre bundle with up to 144 connections ensures readiness for future growth. Short link lengths 3-5m between switch and end devices, and the absence of cable bundles, reduce power and heating losses. ë

Implementing Kubernetes should improve collaboration and make room for DevOps teams to focus on innovation, rather than day-to-day management and maintenance.
The role of the LAN is changing and will continue to do so for the foreseeable future. Failing to keep up will affect productivity, competitive position and reputation. So how do you keep up with the demands of new technologies, platforms, and users? Or ensure you have enough useful redundant spare capacity? Let’s take a look at the key drivers for change.
Just a few years ago, in-building resources were devoted to single functions, such as telephony, internet, or security. The technology and business drivers for bringing these services together on a single converged platform are here to stay. However, trends such as hot-desking and smart-desking are now being adopted more widely following Covid-19 measures.

More and more network managers are discovering the cost and efficiency benefits of having only one network to manage. An Everything over IP or All-IP approach, linking building management and devices to the building network over Ethernet, Internet Protocol, allows previously separate systems to merge. Cabling provides Power over Ethernet as well as a physical communication layer.
The fast global uptake of connected LED lighting, sensor technology, and IP-equipped devices are making Power over Ethernet a necessity. Providing current over Ethernet cabling allows devices to be installed and moved around without having to worry whether there’s an electrical outlet close by. Power delivered through new generations of PoE is more than six times the level of the initial PoE standard.
What IS more, some applications, for example in the areas of signage, lighting and security require continuous power. This means a significantly increase heat build-up inside cable bundles, which may disrupt network IP traffic. This requires a new look approach to planning, installing and operating the network.
Evolution in wireless technology is inevitable, with 24 billion web-con-
nected devices. Over half of these are connected wirelessly and are capable of transmitting HD content. Wi-Fi 6 is ideal for the Internet of Things and designed to connect the largest possible number of devices. As more devices share wireless bandwidth it can become increasingly diluted, even to the point of becoming unusable.
As Wi-Fi6 makes more advanced applications possible, the LAN needs to provide ubiquitous capacity, with plenty of bandwidth reserves, to the Wireless Access Point. To benefit from the higher speeds and lower latency Wi-Fi 6 brings, it is important that there are no weak – outdated – links in your connectivity chain. Wi-Fi 6 WAPs will often require compliance with the PoE+ standard 802.3at.
You may need to accommodate a large number of new devices to support IoT or edge computing applications. Or you might need to introduce a large number of new employees. Production plants may need to increase the number of connected devices or accommodate machine-to-machine communications.
A Fibre to The Office solution can help. It provides Gigabit Ethernet to end user devices by combining passive fibre cabling and active switches. High bandwidth reserves and availability of a single fibre bundle with up to 144 connections ensures readiness for future growth. Short link lengths 3-5m between switch and end devices, and the absence of cable bundles, reduce power and heating losses. ë

Cabling provides Power over Ethernet as well as a physical communication layer
JAMES PETTER, General Manager, International, Pure Storage.

As organisations across the globe are fighting against the novel variants of the Covid-19 virus, businesses are finding it extremely challenging to make way for new technologies to come in and revamp the organisation’s working culture, from bottom to top.
The Future IT Summit 2022 will be hosted on 17th March 2022 at The Address Hotel in Dubai, UAE. The Summit will also be held on GCF Virtual Arena live as well. The event will emphasize on future-defining technologies, high-end networking, virtual and face to face meetings, solution showcases, keynotes and much more. Catering to the emerging hindrances, FITS has designed its theme for 2022 as #evolvetechnology with a special focus on Cloud and artificial intelligence.
Brought out by Global CIO Forum, FITS is embellished with various segments and awards such as The Catalyst Marketing, Catalyst CIO, and Top Ten Best IT Companies to Work With, Titans Badge of Honour, Panel discussion and much more.
Currently in its eighth year, Future IT Summit and Catalyst Award 2022 is all set to transform lives through innovation and emerging technology such as artificial intelligence, Cloud, Big Data, IoT, futureproof your business and organisation.
The summit features enterprise use-cases, inspirational keynotes, panel discussions, tech-talks, artificial intelligence fireside chats, and awards with agenda enlisted key industry leaders to bring you stories of their successes, failures and to reveal the insights you need to embrace impactful technological change right now.
FITS 2022 is all set to take the event a notch higher with engaging topics and events such as:
l Welcoming the IT Geniuses by organising a dynamic platform to present the flawless cloud infrastructure for the better future with an access to the Big Data.
l Unique independent business and Technology focused on the state of the practice of artificial intelligence and Cloud in the enterprise, Cloud and artificial intelligence achieve the best of potential to create a better and secure future for all.
l Data Scientists are also invited to enlighten the best practices of artificial intelligence and Cloud to improve the ability of organisations to become pioneers of revolution since the competition of good vs better continues.
l The full-day Event will provide the opportunity for the IT Officials to understand the effective methods of monetising and quantifying the data losing and to learn the importance of investing in cloud infrastructure. l Catalyst Awards is geared up to recognise and honour the trailblazers of the industry who have been uplifting the brand and reputation of their respective organisations in these difficult times with various cutting-edge initiatives, platforms and market-penetration and truly acting as Catalyst in the ever-changing market landscape.
l The Top Ten Best IT Companies to Work for in 2022 is a one of its kind recognitions in the region for the IT fraternity that would celebrate the exuberance of the people working in an organisation. This special recognition felicitates and recognises both fast-growing and established companies in UAE that offer tremendous career advancement opportunities together with employee engagement.

Tech Mahindra, a provider of digital transformation, consulting, and business re-engineering services and solutions, announced its new Premier Consulting Partner status in the AWS Partner Network. This tier is awarded through successful demonstration of competence on multiple fronts such as technical proficiency, customer satisfaction, thought leadership, and revenue recognition.
This recognition reiterates Tech Mahindra’s
position as a dominant leader in cloud and reflects its differentiated industry expertise and notable success in helping customers design, architect, build, migrate, and manage their workloads on AWS. With this collaboration, Tech Mahindra joins a select group of 125 Partners who have achieved the Premier status so far out of the total 6,000+ global AWS Partners.
As an AWS Premier Consulting Partner and
Tenable, announced it has been named Vendor of the Year by Ingram Micro. The annual Ingram Micro Vendor of the Year awards celebrates the success of more than two dozen emerging and established-channel focused vendor organisations across several categories including technology, markets, and communities. The awards were presented virtually in October 2021 at Ingram Micro’s 2022 Marketing Experience Event.
As a channel-driven organisation, Tenable’s commitment to and investment in partners
is integral to addressing the evolving threat landscape and delivering on its holistic security mission. The Tenable Assure partner programme makes it easier for channel partners to build and deliver innovative solutions to help customers see everything, predict what matters and act to reduce risk.
Pulling from the industry’s most comprehensive portfolio of vendor brands, the Ingram Micro team selected 30 Vendor of the Year recipients as part of the 2022 Marketing Experience. Earning this title, Tenable is com-

AWS Managed Service Provider - MSP Partner, Tech Mahindra holds certified qualifications like Migration Consulting Competency, Well Architected Framework (WAF), and AWS Solution Provider. This allows Tech Mahindra to help customers become agile, lean, and build reliable platforms and applications on AWS.
Over the last five years, Tech Mahindra has built a strong AWS Practice with over 1700+ AWS-accredited associates, including more than 1,000+ AWS-certified engineers and architects across various streams of transformation and a dedicated AWS CoE - Centre of Excellence.
mended by Ingram Micro for its unwavering commitment to the channel and excellence at all levels of engagement, enablement and execution.

BNY Mellon and SNB Capital are pleased to announce a transformative data management solutions collaboration in the Kingdom of Saudi Arabia to help build a robust, market-leading and inclusive capital markets
ecosystem.
Building on the earlier strategic alliance to deliver securities services capabilities, SNB Capital will deploy BNY Mellon’s data platform within its IT infrastructure in the Kingdom.
The award-winning BNY Mellon data platform enables organisations to transform their data landscapes by centralising and effectively managing complex investment assets. Capabilities include providing user-centric solutions designed to deliver accurate and timely data, gauge risk exposure and provide system-wide security via a centralised data repository.
The solution is one of the first of its kind to provide services within SNB Capital’s IT infrastructure designed in accordance with the Kingdom’s data-localisation requirements, adding a unique value proposition. This latest collaboration is a significant development for Saudi Arabia’s financial sector and is set to deliver institutional clients of SNB Capital a single, unified solution for local and global assets.
BNY Mellon’s state-of-the-art data management platform, which aims to accelerate the optimisation of typically manual investment workflows, will offer SNB Capital’s clients in the Kingdom significant opportunities to improve their performance through enhanced data flows. This open-architecture software will connect all market participants and enable collaboration with leading technology providing clients the tools for using data in the front, middle and back offices.

Mastercard joined the Dubai Financial Services Authority, Threat Intelligence Platform, furthering Mastercard’s alliance with Dubai International Financial Centre. The collaboration cements Mastercard’s commitment to construct intelligence-led, public-private partnerships and boost cyber resilience across the Middle East, Africa and South Asia region.
The DFSA TIP facilitates the development of a community of information sharing for regulated and non-regulated companies operating in or from the DIFC.
In a continuation of Mastercard’s partnership with DIFC under Mastercard’s Cyber Forward programme, this step will help boost cyber resilience cross the financial industry and payments ecosystem. The Cyber Forward programme launched in January 2021 combines Mastercard’s cutting-edge capabilities in cybersecurity with those of leading public
sector organisations to create secure digital ecosystems at a national, local and city level.
This collaboration between the DFSA, DIFC and Mastercard sets out to foster greater and more advanced cybersecurity capabilities, including the provision of time-sensitive threat signatures and data patterns that provide for indicators of attempted or actual compromise of information or physical assets. These will culminate in the development of a comprehensive ‘threat library’ that will enable the DIFC and its institutions to recognise and respond to risk in real-time.
Research shows that trust in security is much needed as the digital economy expands. The Mastercard Recovery Insights in 2021 found that 20-30% of the Covid-related shift to digital commerce globally is permanent, with an additional $900 billion being spent in retail globally in 2020, further demonstrating the
need for a robust digital infrastructure capable of combatting increasingly sophisticated types of cybercrime. Mastercard revealed that it helped save stakeholders $3 Billion worth of fraud through its AI-enabled cyber systems in the last two years alone.

AppDynamics announced a significant shift in the company’s go-to-market strategy and introduced some important modifications to the existing Global Partner Programme to underpin that change. The market opportunity for full-stack observability continues to grow at break-neck speed as technologists battle on multiple fronts including, keeping pace with rapid digital transformation projects, managing increasing complexity across the IT stack and filtering overwhelming data noise.
KEY UPDATES TO THE PARTNER PROGRAMME INCLUDE:
l 100% channel-centric route to market: AppDynamics will transition from a mixed direct and indirect sales model to a 100% channel-centric route to market. This will provide closer alignment to Cisco’s sales motion and gives partners the confidence and opportunity to build out full-stack observability practices with AppDynamics and Cisco.
l A new Elite level added to the Global Partner Programme: To make this transition a reality AppDynamics has created a three-tier structure with
42 Abu Dhabi, the UAE capital’s innovative and disruptive coding school that provides a unique peer-to-peer, gamified learning methodology, will host six pre-selection events in 2022 as part of ongoing efforts to drive student intake and further fuel the emirate’s global coding capital ambitions.
High school graduates, university students, employees, and those looking for work across all industries with an interest in upskilling or reskilling are encouraged to apply irrespective of coding experience, there is no upper age limit; a high school certificate and a minimum age of 18 years old are the only stipulation.
With 42 Abu Dhabi already producing a hotbed of programming talent, the half-dozen
a new top-tier Elite’ partner category added to the existing Alliance and Titan levels. The Elite level is designed for the largest global partners and creates the optimal conditions to fully exploit the full-stack observability market opportunity across AppDynamics and the wider Cisco portfolio.
The modifications to the Global Partner Programme will benefit partners at all levels, offering more tailored support and improved opportunities for growth, enabling them to better serve customers and rapidly advance critical digital transformation projects. AppDynamics has changed the support model around all three tiers to make sure that it has the right sales engineering, channel engineering, marketing support and channel account manager support to meet the needs of every partner.
This range of new incentives is designed to reward partners for the additional effort and activity they put into opportunities and closing deals. The closer partners align with AppDynamics and the company’s processes, the more profitable their deals become. It is also intended to benefit partners across the globe as AppDynamics expands its global footprint.
series of pre-selection events called Piscines – which are intense and immersive assessments testing candidates’ computer programming aptitude, motivation, endurance, and commitment –will see more than 1,000 aspiring coders test battle for cohort places at the emirate’s revolutionary coding school next year.

The Piscines will be held at the 42 Abu Dhabi campus in Mina Zayed warehouses district. Successful Piscine candidates are required to complete 42 Abu Dhabi’s pre-selection ‘Game’ – an online assessment which evaluates cognitive capacity via logic and memory tests – and attend a virtual Check-in discovery session to be briefed on the Piscine and the learning methodology.
While no previous coding experience or academic qualifications are required to apply for 42 Abu Dhabi, candidates must be aged 18 years old and above, and display ambition, aptitude, commitment, proactivity, curiosity, creativity, and possess an innate ability to adapt and collaborate.
With the school’s first campus opening in 2013 in Paris, the 42 Network’s disruptive curriculum has equipped more than 12,000 students across 34 campuses around the world with essential digital and business skills.
Help AG, the cybersecurity arm of Etisalat Digital, announced its Platinum Level partnership with Trend Micro, a global leader in enterprise data security and cybersecurity solutions. The partnership will enable Help AG customers in the United Arab Emirates and Saudi Arabia to avail of Trend Micro’s security capabilities without sending their data to the cloud, alleviating concerns regarding data privacy.

This collaboration allows Help AG to service clients that may be reluctant to transfer sensitive endpoint data to the cloud environments of cybersecurity providers. When utilising Endpoint Detection and Response services, the client needs to provide complete and accurate endpoint data in order for the service provider to be able to detect threats and attacks. This can be problematic if an organisation’s users engage in confidential activities or access confidential websites.
Help AG’s partnership with Trend Micro addresses these challenges by delivering security services and capabilities without needing clients to send their data to a cloud-based environment. Due to the unique data model, it has in place, Trend Micro is one of the few vendors of its calibre to offer this option, answering the needs of a niche segment of customers with specific data privacy
concerns.
Now available to Help AG customers, the Trend Micro portfolio includes products and solutions related to Detection and Response, Network Security, User Protection, Cloud Security, Internet of Things Security, Enterprise Ransomware Protection, and Regulatory Compliance, among other areas within cybersecurity that are relevant to organisations today.
visualisation, vulnerability assessment, risk monitoring and threat detection in a single solution. The technology accelerates security and simplifies IT-OT convergence by delivering actionable intelligence to the business and operational decision makers.
Recognised as the market leader in OT and IoT security, Nozomi Networks is valued for superior operational visibility, advanced OT and IoT threat detection and strength across deployments. Nozomi Networks solutions support more than 57 million devices in thousands of installations across energy, manufacturing, mining, transportation, utilities, building automation, smart cities and critical infrastructure.
Nozomi Networks, and stc, announced they have partnered to address the growing demand for security services and solutions designed to holistically address IoT and OT cybersecurity requirements for customers in industrial automation, manufacturing, healthcare, public safety systems, smart cities, utilities and building management systems industries across the
Kingdom of Saudi Arabia. stc Group will offer Nozomi Networks’ advanced solutions for OT-IoT cyber resiliency and real-time network monitoring and visibility.

Nozomi Networks solutions are available through stc for clients who need deep insight into their industrial networks. With Nozomi Networks, they gain asset discovery, network
Recently, Nozomi Networks products are deployable onsite and, in the cloud, and span IT, OT and IoT to automate the hard work of inventorying, visualising and monitoring industrial control networks through the innovative use of artificial intelligence. Use cases stretch beyond cybersecurity, and include trouble shooting, asset management and predictive maintenance.
stc and Nozomi Networks partner in Saudi Arabia to address smart cities, utilities, building management
Kaspersky researchers issued 49 threat intelligence reports on investigations associated with APT groups targeting the UAE. The country has the highest number of reports coming out of all the Middle Eastern countries, making it one of the most targeted countries in the region.

Kaspersky has found that these APT groups primarily target the UAE’s governmental and diplomatic institutions as well as educational organisations. Other targeted entities include financial institutions, IT companies, healthcare, law firms, military and defence. Some of the notorious APT groups investigated in the UAE are the SideCopy, MuddyWater, DeathStalker, Zeboracy, Turla and Lazarus.
The research team has found that Exploit Public facing Applications, Valid Accounts, and Phishing are the most commons attack vectors against the UAE’s infrastructures.
SideCopy APT group carries out malware campaigns targeting entities for espionage purposes.
MuddyWater, a Middle Eastern espionage motivated APT group targets government, telco and oil companies to derive information, using
compromised accounts to send spear phishing emails with targeted attachments to recipients.
Zeboracy is a trojan that is deployed as part of cyber espionage campaigns to collect initial data from compromised systems.
The Turla APT Group is popular for conducting watering hole and spear phishing campaigns. They infect websites regularly visited by organisations and lure them to a malicious website.
DeathStalker is a hacker-for-hire group and mainly focus on cyberespionage against law firms and organisations in the financial sector. The group is known for using an iterative, fast-paced approach to software design, making them able to execute effective campaigns.
The Lazarus APT group uses the watering hole attack strategy in which they observe which websites are frequented by an organisation and infects one or more of them with malware.
Kaspersky has kept a close eye on UAE for Advanced Persistent Threats and worked on 49 investigative reports related to 16 cyber gangs targeting the country since the start of the pandemic in 2020
Kaspersky has uncovered a previously unknown IIS module, a piece of software aimed at providing additional features to Microsoft web servers, they have since dubbed Owowa that steals credentials entered by a user when logging into Outlook Web Access; it also allows the attackers to gain remote control access to the underlying server.
Compiled sometime between late 2020 and April 2021, this module is a stealthy theft method that is difficult to detect with network monitoring. It’s also resistant to software updates from Exchange, meaning it can stay hidden on a device for a long time.
In 2021, advanced threat actors were increasingly exploiting vulnerabilities of Microsoft Exchange Server. In March, four critical vulnerabilities in the servers allowed attackers to gain access to all registered email accounts and execute arbitrary code. While searching for additional potentially malicious implants in Exchange, Kaspersky experts uncovered a malicious module that
allows the attackers to steal login credentials for Outlook Web Access and gain remote access control to the underlying server.
Kaspersky has dubbed this malicious module Owowa, and its malicious capabilities can easily be launched by sending seemingly innocuous requests – in this case, OWA authentication requests.
Kaspersky experts believe the module was compiled between late 2020 and April 2021, and it has been seen targeting victims in Malaysia, Mongolia, Indonesia, and the Philippines. Most of the victims were connected with government organisations and another to a state transportation company. It is likely there are additional victims located in Europe.


The cybercriminals only need to access the OWA log-in page of a compromised server to enter specially crafted commands into the username and password fields. This is an efficient option for attackers to gain a strong foothold in targeted networks by persisting inside an Exchange server.
Kaspersky researchers could not associate Owowa to any known threat actor. Yet, they did find that it was associated with the username S3crt, a developer that may be behind several other malicious binary loaders. However, S3crt is a simple derivation of the English word secret and could very well be used by multiple individuals.
Qualys, announced it is making its Web Application Scanning solution available free for 30 days, to help companies protect against Log4Shell. The Apache Log4Shell zero-day RCE vulnerability has raised alarms at companies around the globe, with US government officials calling it “one of the most serious flaws they’ve seen.” The vulnerability poses potential threats for almost every single web application, with the list of known exploits growing daily. Web Application Scanning capabilities are essential to detect these vulnerabilities as they simulate the attack of Log4Shell exploits. To help customers protect themselves from this threat, Qualys is making its WAS app, which scans web applications and APIs for the Log4Shell CVE-2021-44228 vulnerability, available free for 30 days.
Qualys WAS makes accurate detections of applications vulnerable to Log4Shell through its advanced out-of-band detection mechanisms. To identify vulnerable sites, WAS uses specially crafted payloads to simulate the same attack pattern malicious actors use. Vulnerable sites are quickly and easily identified for remediation, shutting the door on attackers before they ever know you are exposed.
Group-IB, has uncovered a worldwide scam campaign targeting users in over 90 countries all around the world, including the UAE, Oman, and Qatar. The fraudsters employ the tried and tested technique with fake surveys and giveaways purporting to be from popular brands to steal users’ personal and payment data, with the total number of big-name companies impersonated in the scheme exceeding 120.
The new wave of the scam is particularly persistent thanks to an innovation in the scammers’ toolset — targeted links, which makes investigating and tackling such attacks increasingly challenging.
The potential victim pool of a single scam network is estimated at about 10 million people, while the potential damage totalled about $80 million per month, according to Group-IB’s Digital Risk Protection unit.
Fraudsters trap their victims by distributing invitations to partake in survey, after which the user would allegedly get a prize. Each such offer contains a link leading to the survey website. For lead generation, the threat actors use all possible legitimate digital marketing means contextual advertising, advertising on legal and completely rogue sites, SMS, mailouts, and pop-up notifications.
To build trust with their victims, scammers register look-alike domain names to the official ones. Less frequently, they were also seen adding links to the calendar and posts on social networks. After clicking the targeted link, a user gets in the so-called traffic cloaking, which enables cybercriminals to display different content to different users, based on certain user parameters.

Fraudsters can use the data stolen to buy goods online, register fake user accounts on any online resources or simply sell the personal information on the dark web. Apart from revealing their data, users are sometimes asked to pay a tax or a test payment to receive the prize.
According to Group-IB DRP analysts, this type of fraud has been spotted in 91 countries, with cybercriminals exploiting at least 121 brands as bait. Based on the country of origin of the brands affected, the scam’s target regions are Europe 36.3%, Africa 24.2%, and Asia 23.1%.
In the Middle East alone, cybercriminals exploited 9 brands from Bahrain, Qatar, Oman, Kuwait and the UAE. Globally, cybercriminals mostly try to exploit the brands of leading telecommunications companies, which enjoy special love in this scheme, and make up more than 50% of the total number of brands exploited, followed by ecommerce and retail.
ASHRAF KOHEIL, Director of Business Development, Middle East & Africa at Group-IB.
As part of Oracle’s planned expansion of its cloud region footprint to support customer demand, Oracle will open seven additional cloud regions in 2022.
BY ARUN SHANKAROracle’s second cloud region in UAE located in Abu Dhabi has gone live. The Abu Dhabi cloud region, and the previously launched Dubai Cloud region, will offer Oracle Cloud services, Oracle Autonomous Database and Oracle Cloud Applications.
Speaking at the event, Ahmed Adly, Senior Director Cloud Solutions Engineering, MEA Oracle, pointed out that Oracle had one of its best ever quarter earnings ending in November 2021. “We are pivoting at the right time,” he pointed out.
Also speaking at the event, Sean Murphy, Chargé d’Affaires at the United States Embassy, Abu Dhabi, pointed out that the launch of the cloud regions in UAE, are a model of Emirati and US business innovation. “Oracle is an example of a US company dedicated to UAE, the regional digital hub.” Oracle remains committed to promoting cross border, data transfer flows.
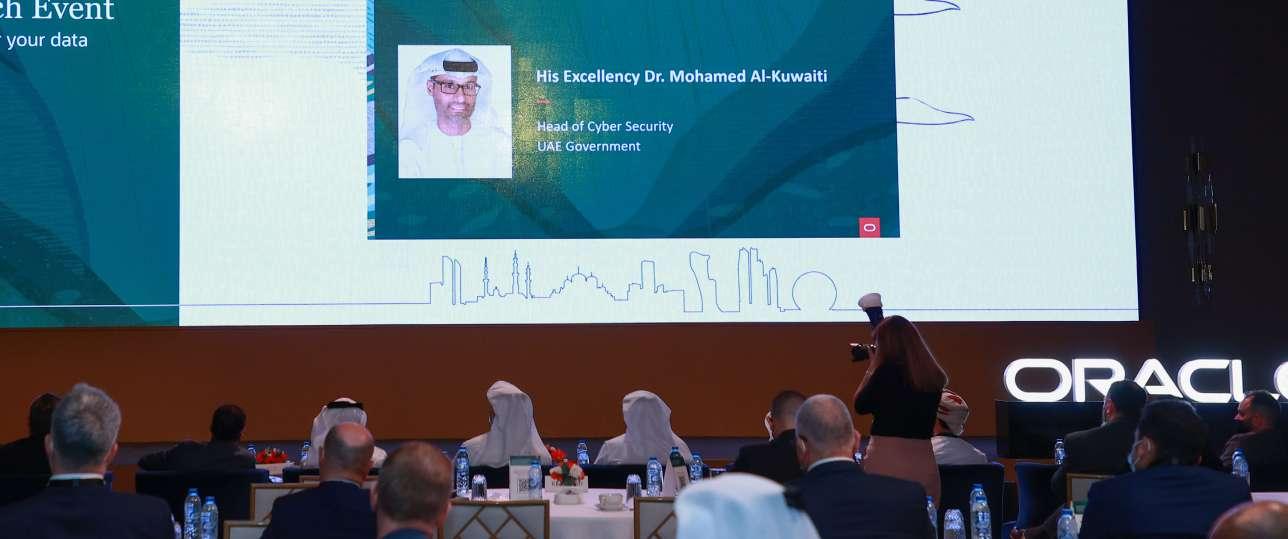
UAE Ministers were also present and spoke during the event, including His Excellency Dr Thani Al Zeyoudi, UAE Minister of State for Foreign Trade; His Excellency Dr Mohamed Hamad Al Kuwaiti, Head of Cybersecurity for the UAE Government; and His Excellency Mohamed Abdelhameed Al Askar, Director General, Abu Dhabi Digital Authority.

They were of the opinion that initiatives such as the Oracle cloud regions inside the county can enhance local activities and help to accelerate the GDP targets set for UAE. In-country data transfer flows will boost automation, data analysis, and enable digital transformation within the cloud regions. Many of the Abu Dhabi government institutions are already actively spending on cloud and the vision is no servers in the government.
Regis Louis, Vice President of Cloud Strategy, EMEA Oracle, pointed out that Oracle Cloud regions and Oracle Cloud Infrastructure datacentres, are the same all over the world. “They have the same architecture, same services, and this gives predictability to Oracle’s global operation.”
As part of Oracle’s planned expansion of its cloud region footprint to support customer demand for Oracle Cloud services worldwide, Oracle will open seven additional cloud regions in 2022, in Spain, Mexico, Colombia, Chile, France, Israel, and Saudi Arabia. Oracle plans to have at least 44 cloud regions by the end of 2022.
Oracle’s two cloud regions in UAE will provide secure, advanced, agile platform for organisations to leverage the full potential of digital technologies. IDC estimates public cloud services adoption is accelerating at CAGR of 28% YoY between 2020 and 2025 in the UAE. IDC projects this
growth momentum will continue.
The UAE’s Fourth Industrial Revolution Strategy focuses on advancing the national economy by driving innovation with latest emerging technologies.
Growing number of organisations in the UAE have migrated some or all their on-premises IT infrastructure deployments to IaaS and PaaS cloud environments and are realising a range of benefits. These include anywhere, anytime access, open-ended scalability, infrastructure flexibility, rapid deployment, and shorter time to market. One of the most sought-after benefits, not surprisingly, is cost reduction.
These significant cost savings are channelled back into the local
DATA COMPLIANCE
Data stays inside UAE, supporting local data regulations and data sovereignty.
HIGH AVAILABILITY
Companies benefit from architecture designed to maximize performance, and data security.
CLOUD SERVICES FOR EVERY WORKLOAD
UAE gets 65+ OCI services on a high-bandwidth backbone.
EASIER CLOUD MIGRATION
Businesses will enjoy a simpler cloud migration for all their IT workloads.
Businesses can take advantage of low-latency predictable costs.
Businesses get connectivity between cloud regions with Oracle FastConnect for use cases like data transfer or enduser access to cloud applications.
SUPERIOR RESILIENCY
Organizations get better disaster protection and additional security with two cloud regions inside UAE.
Leverage state-of-the-art intelligent energy management.
economy, thus making an important contribution to the national digital economy.
Oracle is fully aligned with Abu Dhabi Digital Authority’s mandate of delivering digital services, platforms, channels, and implementation of applied intelligence and cybersecurity solutions for government entities. Oracle’s new cloud region in Abu Dhabi will help accelerate the authority’s efforts.
Oracle has been working towards creating a strong local IT talent pool in the UAE. Under the recently completed skills development initiatives with the UAE’s Higher Colleges of Technology and its commercial arm, the Centre of Excellence for Applied Research & Training, Oracle has upskilled 1,098 students in emerging technologies. ë
Today, Oracle has 37 Cloud regions available and 7 more planned by the end of 2022. Inside UAE, two Cloud regions, Abu Dhabi and Dubai, are now live. Within these cloud regions, Oracle offers more than 80 cloud infrastructure and platform services. Most cloud regions also offer Oracle Cloud Application SaaS portfolio. With public and hybrid cloud options, Oracle is now supporting local access, regional compliance, and business continuity.
The roll out of global cloud regions is in proximity to customers who need to meet their data sovereignty requirements. Another consideration is providing true disaster protection with multiple geographically distributed cloud datacentres for every cloud region and at least two cloud regions per country.

Oracle offers more than 80 cloud infrastructure and platform services, with most cloud regions also offering Oracle Cloud Application SaaS portfolio.
By launching the Abu Dhabi and Dubai Cloud regions inside UAE, Oracle has made these Cloud regions an extension of the datacentre of many enterprises inside the country, says Regis Louis, Vice President Cloud Strategy, EMEA Oracle.
“These Cloud regions give full resilience inside the country and all cloud services can be accessed inside the country,” adds Louis.
He cites the example of UAE based Landmark Group. “They moved 80% of their business to Oracle Cloud Infrastructure in 12 months.”
Inside these regions, Oracle has a unique hybrid cloud option, Dedicated Region Cloud@Customer, which offers Oracle Cloud services on the customer’s premises. This range of options provides customers access to all cloud services, with the same SLAs for availability, performance, and management, as well as consistent APIs for simplified management.
Louis tells UAE based businesses, “Cloud@Customer brings the cloud to you, and the full Oracle Cloud Infrastructure to your datacentre.”
For the Cloud regions inside UAE, Oracle provides SLAs on availability, performance, manageability, points out Louis. A high level of performance assured by these SLAs, implies that a faster business throughput is possible at a lesser cost.
Another plus point for businesses inside UAE adopting Oracle Cloud is that security is in-built inside every service and every application, hosted on Oracle Cloud Infrastructure. “It is always on and not provided as an option. It is fully automated, and data is always encrypted,” says Louis.
The Saudi Arabian Mining Company moved its on-premises E-business suite to Oracle Cloud Infrastructure and received a 36% savings in their direct cost, cites Louis, as an example of the savings that can be generated by working within Oracle’s Cloud regions.
Oracle is also actively using AI and ML to manage the functioning of its Autonomous Database Manager. Oracle data management offers freedom from silos of information, making it easier to access and extract value from data. Automation of security, patching, and configuration with Oracle Autonomous Database eliminates time-consuming administrative tasks and human error. With these tools, “there is no human error,” says Louis.
Oracle Cloud Infrastructure’s physical and virtual network design maximises performance and security and enables the fast provisioning and on-demand consumption of more than 80 cloud services, including unique bare metal GPUs, clustered databases, and Oracle Exadata database-optimised shapes.
Each Oracle Cloud region contains at least three fault domains, which are groupings of hardware that form logical datacentres for high availability and resilience to hardware and network failures.
Oracle Cloud Infrastructure’s, cloud services are open, and embrace standards
Oracle has a goal of achieving 100% renewable energy use in all its Oracle Cloud Infrastructure datacentres by 2025.
Oracle Cloud datacentres align with Uptime Institute and Telecommunications Industry Association ANSI, TIA-942-A Tier 3 or Tier 4 standards and follow a N2 redundancy methodology for critical equipment operation. Datacentres use redundant power sources and maintain generator backups in case of widespread electrical outage.
Oracle Cloud datacentres incorporate physical access, alarms, CCTV monitoring, 24X7 onsite guards.
Temperature and humidity are controlled to align to industry standards, enabling optimal performance. Server rooms are equipped with feature fire-suppression systems to protect Oracle’s equipment.
Datacentre sites undergo a risk evaluation that considers environmental threats, power availability and stability, vendor reputation and history, neighbouring facility functions including high-risk manufacturing and high-threat targets, and geopolitical considerations, among other criteria.
Oracle Cloud Regions are regularly assessed as part of Oracle Cloud Infrastructure’s compliance programs.
like Kubernetes, CloudEvents, and Terraform so that customers can enjoy portability, lower overhead, and lower costs. Oracle Autonomous Database is available for both existing and new applications, which is optimised for transaction processing, data warehousing, or JSON, with automatic tuning, scaling, and patching.
By having visibility and control over the hardware at the end of its useful life in Oracle Cloud, Oracle is also able to repurpose equipment more effectively, harvest spare parts, and maximise the recycling of materials.
Within these Oracle Cloud regions, customers can run applications they migrate, applications they build, and a broad range of horizontal and industry SaaS, all out of the same cloud. Oracle Cloud Regions can not only run customer workloads, but also offer enterprise SaaS like Oracle Fusion Cloud ERP, Oracle Human Capital Management, and Oracle Supply Chain Planning.
For the demands of multicloud, Oracle Cloud Infrastructure and Microsoft Azure have a strategic partnership that enables joint customers to run workloads across the two clouds.

This partnership provides a low latency cross-cloud interconnect between Oracle Cloud Infrastructure and Azure in six regions, federated identity for joint customers to deploy applications across both clouds, and a collaborative support model. Customers can run full stack applications in a multi-cloud configuration, while maintaining high performance connectivity without requiring re-architecture. ë
They have been assessed by independent assessors to meet the requirements of the Security, Breach Notification, and Privacy Rules of the Health Insurance Portability and Accountability Act of 1996, as amended, in accordance with the Standards set forth in HIPAA Administrative Simplification Regulation Text 45 CFR Part 164 Subpart—Security Standards for the Protection of electronic Protected Health Information, Subpart—Notification in the Case of Breach of Unsecured Protected Health Information, and Subpart—Privacy of Individually Identifiable Health Information, as amended. The number of audit checks for Oracle Cloud datacentres can be as high as 800.







2022 will see adoption of solutions using cloud computing, machine learning, artificial intelligence, data science, software engineering and cybersecurity.
From the year 2019, there has been a lot of uptick in cloud. We have seen a lot of digitalisation that has happened and that has led to a lot of growth in IT Industry. Vendors have a significant pipeline now and it looks lucrative. The overall IT services sector at this point is going through golden times that we have not seen in the past.
Growing demand has created a new kind of opportunities for all the networking vendors. Growth is going to happen more towards digitalisation, smart home, mesh connectivity for smooth remote working and digital learning.
TP-Link has been recognised in 2021 Gartner Magic Quadrant for Enterprise Wired and Wireless LAN Access Infrastructure. TP-Link has received acceptance for business networking and due to high demand are in the process of taking SMB business to Enterprise level.
Secondly, TP-link consistently ranked as the number one global provider of WLAN devices for 10 years, according to the IDC Quarterly Wireless LAN tracker, Q4 2020.
The shift from workplaces to home offices, schools and colleges to virtual classrooms, and theatres and gaming arcades to home entertainment solutions has caused a consequential and considerable rise in the demand for enhanced networking solutions, speeds, and bandwidths.
TP-Link solutions have always been designed to do just that, and the pandemic has resulted in the demand for TP-Link offerings rising consistently in the past year. That is TP-Link
biggest achievement for the year that prove to be challenging and disruptive for quite some enterprises.
Owing to this, TP-Link digital engagements with TP-Link partners and customers have been on the rise, and TP-Link have regularly conducted digital meetings with TP-Link partners throughout the lockdowns.
What turned out to be a challenge for most businesses - making the sudden switch to a hybrid working policy – actually turned out to be business growth opportunity for TP-Link.
Rapidly increasing demand for reliable Wi-Fi and connectivity at home, home offices, e-learning, and entertainment has resulted in TP-Link hi-tech products being in high demand as these are the kind of requirements that they have been designed to cater to. This has opened up a lot of new markets and opportunities for us and TP-Link are looking to capitalise on them in the new year.
2022 will see an enhanced demand and interest towards the adoption and integration of solutions using emerging technologies like cloud computing, machine learning, artificial intelligence, data science, software engineering and cybersecurity. The need for improved cybersecurity, in particular, is gaining accelerated momentum due to the rapidly multiplying cyber threats of the ever -digital world.
TP-Link will remain focussed on GCC countries, to strengthen the brand presence further in the markets TP-Link is popular in. With a
range of future-proof networking solutions already in the pipeline, TP-Link would also be focusing on growing the presence of TP-Link surveillance and security solutions.
For the regional economy to thrive, TP-Link strongly believes that SMBs across industries in the Middle East need to be supported through effective technology solutions and continuous business innovation. In 2022, TP-Link will focus on encouraging channel partners to take advantage of dynamic opportunities that are presenting themselves and work on meeting business needs that SMBs seek in the wireless networking and IP surveillance space.
TP-Link’s aim for 2022 is to help them to widen their reach through TP-Link solutions that enhance connectivity and optimise user networks to boost productivity. TP-Link will be focused on driving the growth of TP-Link SOHO, Business Networking Solution and VIGI offerings and on ensuring that TP-Link partners thrive in the market.
TP-Link will be investing in evolving TP-Link resources and enhancing TP-Link channel network. TP-Link has planned out a number of initiatives in 2022 that will focus on expanding TPLink customer base and catering to the rising demands for TP-Link innovative solutions. TP-Link is preparing and enabling new partners for its complete product line in 2022. ë

INFINITE BLUE

Business continuity can never be effective if it is being set up by a single department and you need to be able to see it working across the entire enterprise.
VINCE WILLIS, COO at Infinite Blue.IIn today’s modern world, the nature of disruptive events that are occurring, whether they are climate change, extreme weather, supply chain, pandemic, earthquakes, volcanic explosions, and others, are beginning to have fundamental impact on businesses. These events are happening more frequently and sometimes they are occurring in a compounding manner, with more than one such event taking place at the same time.
“What we are seeing across this space is that people are exhausted. There is just a lot of fatigue and people are looking for reliable solutions to solve their challenges,” says Vince Willis, COO at Infinite Blue.
Businesses want a programme to engage within the enterprise. Business continuity is evolving from a limited function within an enterprise into a critical business function.
“You need a tool that can scale quickly and is easy to use, that is really what we focus on. Giving organisations clarity and control across their event spectrum and the ability to engage with their entire workforce rapidly,” says Willis.
Business continuity has always been regarded as specialised, point function, within an organisation. However, in the face of continuous external disruption and the need for business continuity to work across the organisation, it has now spread across the organisation, and reached the board and C-suite.
Business continuity can never be effective if it is being set up by a single executive or a single department. To do business continuity really well, you need to be able to see it working across and engaging the entire enterprise.
“Which is what our solutions tend to do as a group,” says Willis.
Infinite Blue’s business continuity software, BC in the Cloud, has been built by a team of domain experts. BC in the Cloud, quickly enables organisations to plan, prepare, test, manage, and notify teams how to respond to any potential business disruption. Through a team of industry experts and a software suite with a 99.99% guarantee in uptime, Infinite Blue gives organizations clarity and control over disruptions that can impact their day-to-day business.
“We give people an added layer of confidence because our software is the most reliable solution on the market,” says Willis.

Business continuity must work and address organisational risk correctly. “You have to be able to engage your entire enterprise to be able to do business continuity correctly and to become really prepared. Preparation is very important to us,” says Willis.
Infinite Blue is able to plan for disruptive events that will happen and build human and machine intelligence around those events.
Infinite Blue helps in addressing business continuity across the organisation, in the following manner:
l What are the risks?
l How do you manage them effectively?
l Which parts are external and which parts are internal?
l What should you be doing to become resilient?
l How do you engage the entire organisation?
Infinite Blue helps to bridge the gaps inside an enterprise and gets all the teams to start communicating. Implementing Infinite Blue’s software makes all teams share clean, proper data, across all levels. It then becomes a repository, benchmark, baseline and grows with the overall business continuity efforts. The software produces dependency maps and hierarchical structures, features of functionality, gap analysis, to help the enterprise move forward.
l Business continuity is evolving from a limited function within an enterprise into a critical business function.
l Business continuity can never be effective if it is being set up by a single executive or a single department.
l To do business continuity really well, you need to be able to see it working across and engaging the entire enterprise.
l Infinite Blue helps to bridge the gaps inside an enterprise and gets all the teams to start communicating.
l Infinite Blue has the ability to pull data sources together using the IB Connect tool.
l To keep up with the requirements of digital transformation, Infinite Blue is adding artificial intelligence, machine learning, and analytics to the software.
l By using Infinite Blue, enterprises can begin to rightly position IT in the hierarchical flow of business continuity activities across the entire organisation.
l Inside the Middle East, Infinite Blue has started developing its tier-one channel model as well.
l Infinite Blue is looking for partners who understand business continuity risk and can bring their talent to the partnership table.
l One of the key success factors in rolling out a successful business continuity programme, is getting the right people that know the right information.
According to Matt Cox, Vice President of Alliances at Infinite Blue, implementing Infinite Blue is more of a process and change management, rather than a tool.
Infinite Blue has the ability to pull data sources together using the IB Connect tool. “We can connect with 400 other systems and pull all of that data into one place,” says Willis.
Another strength is its ability to use workflows and add information sources to the tool. As an example, threat intelligence across a broad spectrum of risks and markets, can be viewed under a single dashboard.
“We are very good at workflows and being able to customise the workflows as they exist in other organisations, where we are going to deploy the application,” indicates Willis.
To keep up with the requirements of digital transformation, Infinite Blue is adding artificial intelligence, machine learning, and analytics to the software.
“We are moving deeper into the world of predictive analytics, with data insights making systems more reliable and supporting faster responses,” continues Willis.
At a global level, AWS is one of the most important hyperscale cloud partners for Infinite Blue. “We do a lot of work with AWS and we are comfortable and operate global datacentres with AWS,” says Cox. “When we enter new markets, we work with local partners for local datacentres to hold the SaaS solution.” Inside Saudi Arabia, Infinite Blue is setting up local datacentres.
In the past, the information technology department has always driven backup and recovery functions of data and ensured data integrity. But sometimes the efficacy and benefit of the role played by the IT department is not visible to the rest of enterprise. Has the IT department spent
too much or too little on this role?
By using Infinite Blue, enterprises can begin to rightly position IT in the hierarchical flow of business continuity activities across the entire organisation. Using Infinite Blue, IT can demonstrate whether it is ready with its disaster recovery process and the impact on the rest of the enterprise.

Says Willis, “Disaster recovery is only a subset of business continuity. Disaster recovery typically involves getting IT systems up and running following a disaster. Business continuity is much broader than just the technical part of disaster recovery.”
During the pandemic, organisations had to move away from centralised IT systems into distributed IT systems. But success was dependent on the rest of the organisation redeploying business processes to map to the new IT processes.
In the past, those executives or departments that took the lead in business continuity had mandates from regulators and Boards to do it. “Now you are seeing boards and CEOs reaching out to us directly and to our partners to say, we need to have this,” explains Willis.
When Infinite Blue started nine years ago, it began with a direct sales model. Traditionally Infinite Blue has followed a direct to customer sales model, while selling to the Fortune 100 and Fortune 500. However, in the Middle East, Infinite Blue has started developing its tier-one channel model as well. As the business continues to grow, Infinite Blue is looking for very strategic and qualified partners.
“We are very fortunate with the channel partners that we have today,” says Cox. But inside the region Infinite Blue is learning. “We are pretty new to the alliance ecosystem here,” he adds. But the preference is for partners with a consulting strength to engage with business in enterprises, rather than channel partners with strength in IT.
Infinite Blue provides a low-code development platform and enterprise applications for the business continuity and disaster recovery industry. Infinite Blue Platform is at the heart of countless business applications running in a wide variety of industries worldwide.
Applications built on Infinite Blue Platform can be hosted on-premises or in a public or private cloud. Infinite Blue customers use the platform to build custom applications and to extend existing applications, customising them to meet their needs.
Infinite Blue provides automated tools and services for building business continuity and disaster recovery plans that streamline and simplify continuity, governance, and risk management programmes. As an organisation’s needs grow, the solution evolves to increase resiliency, mitigate risk, and adhere to deadlines. Infinite Blue offers speedto-market and scalability in an all-in-one solution. BC in the Cloud is currently used worldwide by more than 500,000 users.
According to Cox, successful business continuity requires business impact planning. There is a lot of data that needs to be collected and then incorporated into BC in the Cloud, he points out. It is for this reason Cox feels selling BC in the Cloud through channel partners, “is definitely a solution sell.”
Regional channel partners with consulting strength who are trusted advisors for their customers are now calling Infinite Blue to become partners to implement the solution. “They are seeing the need within their customer base and they do not have a business continuity capability to offer,” says Cox.
These consulting companies have been using spreadsheets and documents previously and now want to use Infinite Blue’s BC in the Cloud application. Infinite Blue is looking for partners who understand business continuity risk and can bring their talent to the partnership table.
Infinite Blue will be using its long baseline of eight years of service and implementation experience, to train the next generation of channel part-
ners, that it plans to onboard.
“We do have that talent in-house, but there is going to be a hybrid approach, where our indirect team is going to have to help with partners. This includes expanding the Infinite Blue brand, overall customer success, and customer retention,” explains Cox.
Some of the regional channel partners working with Infinite Blue include, Centre Systems Group, Elements, Epic Lanka, Foot Print Africa, Global Concept Emerge Technologies, The QAED.
One of the key success factors in rolling out a successful business continuity programme, is getting the right people that know the right information. “We have a methodology that we follow for our best practices, which has been very successful,” says Willis. “Generating huge user adoption is key to a lot of companies,” he adds.
Trellix represents the best of McAfee and FireEye and looks to alleviate pain points for enterprises by adding automation and reducing complexity.
BY ARUN SHANKARSymphony Technology Group announced the launch of Trellix, a new business delivering extended detection and response to organisations with a focus on machine learning and automation.
Trellix emerges from the previously announced merger of McAfee Enterprise and FireEye in October 2021. Trellix will deliver living security that learns and adapts to protect operations from the most advanced threat actors.
Enterprises are engaged in digital transformation and the attack surface they need to protect is growing rapidly and is very dynamic influenced by work from home and cloud adoption. “That is absolutely one of the challenges that Trellix can help enterprises with,” says Adam Philpott, Chief Revenue Officer, Trellix.
Another challenge for enterprises is the growing sophistication and sheer volume of threat attacks and attack frequencies. Trellix has been built to take over mundane remediation operations leaving the analysts to focus on more sophisticated responses.
“When you think about it, there are not enough people. There is not enough talent in the cyber domain, so we need to use technology to augment human capacities. Those things are exactly what Trellix will focus on,” continues Philpott.
The core strength of Trellix has been built around extended detection and response or an XDR foundation, which plays the role of an architecture and system.
Trellix’s XDR ecosystem is designed to accelerate the effectiveness of security operations by providing customers with the capability to
With a combined product portfolio that spans endpoint, network, messaging, data protection, and cloud services, Trellix has a multi-technology portfolio to address the promise of XDR.
ingest over six hundred native and open security technologies. By providing security analysts with better insight, granting more control, and delivering comprehensive threat context, analysts can save time and act decisively to remediate threats.
The promise of XDR dramatically improves security efficacy, and the vendors that can deliver on that promise will capture market share.
“It is our way of integrating the threat tools into a common system instead of lots and lots of
complicated individual tools. Lots of tools does not help anyone,” adds Philpott. “We need to give enterprises holistic visibility over the threat landscape, as there are shifts and changes and then help them respond to that in an automated orchestrated way.”
The approach of Trellix is to offer a holistic solution rather than a point product. Point products only challenge other point products and keep increasing the complexity inside an enterprise.
Trellix addresses some of the pain points of enterprises by providing holistic visibility, eliminating complexity.
Philpott reiterates that the Trellix XDR is not a product or feature – it is an architecture in a system. Equally important, it has to be an open system, to integrate with an enterprises’ own infrastructure.
“There are other components that a customer may have. They may have created their own capabilities. Or they are midway through investment cycles in other capabilities,” he points out.
“So, it is really important that we integrate not only into their threat telemetry, but also into their infrastructure and into the cloud applications they consume,” says Philpott.
The XDR market is also under penetrated and likely to yield growths of 20% to 40% YOY, over the next four years for Trellix.
Another strong capability of Trellix is active usage of data sciences, algorithms, and automation. These are capabilities that can help improve the productivity of the SOC teams, allowing them to focus on threat hunting, while analytics automates out the low value, high volume incidents.
Integrating context and delivering outcomes takes resources and work. With a combined product portfolio that spans endpoint, network, messaging, data protection, and cloud services, Trellix has a multi-technology portfolio to address the promise of XDR.
With the combined market entry capability of McAfee and FireEye, Philpott expects Trellix, to do well in government and enterprise market segments.

And the new channel partner programme from Trellix is expected to make grounds in the managed services space.
“We see a huge opportunity with our MSSP partners, and that is not something we have embraced at the scale that we would like to do today. So that is a new change that I see coming forward as well,” summarises Philpott. ë
l Trellix emerges from previously announced merger of McAfee Enterprise and FireEye in October 2021.
l Trellix will deliver living security that learns and adapts to protect operations from advanced threat actors.
l The core strength of Trellix has been built from an XDR foundation, which plays the role of architecture and system.
l Trellix’s XDR ecosystem provides customers with the capability to ingest over six hundred native and open security technologies.
l By providing security analysts with insight, analysts can save time and act decisively to remediate threats.
l The promise of XDR dramatically improves security efficacy, and vendors that can deliver on that promise will capture market share.
l The approach of Trellix is to offer a holistic solution rather than a point product.
l Point products only challenge other point products and keep increasing the complexity inside an enterprise.
l Trellix has a multi-technology portfolio to address the promise of XDR.
l With combined market entry capability of McAfee and FireEye, Trellix is expected to well in government and enterprise markets.
Providers of software, cloud, need to shoulder responsibility with customers, since they own the code and the infrastructure that hosts it.
More than a month after the initial announcement of the vulnerability impacting Log4j on December 9, 2021, there are still medium- and long-term consequences to be considered.
Log4j is an open-source Java logging library that is widely used in a range of software applications and services around the world. The vulnerability can allow threat actors to take control of any Java-based, Internetfacing server and engage in remote code execution attacks.
Most login screens in the world typically audit failed login attempts, meaning that virtually every authenticated page using Log4j is vulnerable. Browser search bars are also often logged and expose systems to this flaw.
Exploiting the flaw is fairly trivial. An attacker can exploit the vulnerability by simply sending a malicious code string that gets logged by Log4j. At that point, the exploit will allow the attacker to load arbitrary Java code and take control of the server.
From a global security attitude survey done recently, supply chain attacks constitute a unique headache for security leaders. A staggering 63% of respondents said their organisation is facing a crisis of trust in legacy IT vendors, such as Microsoft, due to frequent security incidents.
Only 36% believe they have been able to vet new and existing suppliers for security purposes in the last 12 months.
While at this stage a comprehensive security strategy is hard to achieve, CrowdStrike advises organisations to reduce internal friction and accelerate the process of patching and hardening.

CrowdStrike also advises improving the visibility and detection across all IT infrastructure and keeping the conversation going with vendors. Vendors need to shoulder part of the responsibility and it is not possible for companies to perform the due diligence fully on their own.
Throughout recent Internet history we have had open-source code libraries with vulnerabilities of globally disruptive level, such as Heartbleed, Shellshock and most recently Log4j. What makes the latest Log4j vulnerability so concerning, is that it is so ubiquitous and embedded in a countless list of customers’ applications and environments. If exploited, this software can provide damaging access to customers’ infrastructure with just few lines of code.
From an open-source developer community, CrowdStrike needs security to be incorporated into the early stages of software creation and maintained throughout the software lifecycle. However, to be fair, some software is beyond their shelf life and maintenance has become expensive over the years. The best way out of this would be to have active global software alliances that looks into the security of older code and provides adequate funding for it.
CrowdStrike has spoken to CISOs who are up in arms because of the recent security incidents and disclosed vulnerabilities that go beyond their ability to control, with the amount of budget and resources available at their disposal. It does not help the case that most exploitable vulnerabilities are coming from the sources that they need to rely on most.
The threat landscape is increasingly complex, and organisations are held back by legacy software that often cannot be upgraded. The Board of organisations needs to step up the game, making sure digital infrastructure is maintained and regularly updated.
Another step to achieve is investment in detection and response capabilities across all assets, cloud, on-premises, SaaS, as well as selection of reliable security partners to alleviate the problem and accelerate the time to respond to incidents. A strategy that includes logging every activity in the environment and segmenting the network and identity stores into a zero-trust model would go a long way.
l 63% of respondents said their organisation is facing a crisis of trust in legacy IT vendors, due to frequent security incidents.
l CrowdStrike advises improving visibility and detection across all IT infrastructure and keeping conversation going with vendors.
l Vendors need to shoulder part of the responsibility and it is not possible for companies to perform the due diligence fully on their own.
l Security needs to be incorporated into early stages of software creation and maintained throughout the lifecycle.
l CISOs are up in arms because of recent security incidents and disclosed vulnerabilities that go beyond their ability to control.
l It does not help the case that most exploitable vulnerabilities are coming from sources they need to rely on most.
l The threat landscape is increasingly complex, and organisations are held back by legacy software that often cannot be upgraded.
l The Board needs to step up the game making sure digital infrastructure is maintained and regularly updated.
l The latest Log4j vulnerability has been a stark reminder that one vulnerable application can jeopardise the most advanced digital infrastructures.
l Providers of common software and SaaS applications need to shoulder responsibility with their customers, since they own and maintain the code and the infrastructure thathosts it.
The latest Log4j vulnerability has been a stark reminder that one vulnerable application can jeopardise even the most advanced digital infrastructures, as a real-world Achille’s heel. Providers of common software, cloud infrastructure and SaaS applications need to shoulder responsibility with their customers, since they own and maintain the code and the infrastructure that hosts it.
CrowdStrike cannot realistically ask organisations to perform full due diligence and vetting of software that they consume. ë

Apache Log4j shines a bright light on the risky but necessary practice of relying on open-source code libraries to build enterprise-scale applications. Many organisations around the world rely on open-source libraries as a key element in their ability to bring applications to market quickly. Yet, these libraries often stop short of a security-first approach. This dependence on what is effectively a wild, wild west of code libraries will continue to leave organisations vulnerable until time and resources are invested to make them more secure.
It is becoming increasingly more important for CISO’s to have line of sight in not only the Software Bill of Materials for software their own organisation is writing, but also for the software they are buying from vendors. Whether it is managed or hosted, there is inherent risk introduced into your environment based on the decisions other people have made when building their services.
The impact from this vulnerability is quite profound. It is included in a number of business-critical applications and used by a number of cloud services. Exploitation is straightforward, and attackers have plenty of publicly available proof-of-concept exploit code at their disposal. The fact that it has come to light means we are in a race to find and fix it before bad actors take full advantage of it.
For organisation’ security teams, it is about identifying what in their infrastructure is impacted by this vulnerability, their systems and applications, and either patching or taking remedial measures that limit the impact if threat actors try to exploit this flaw.
We are aware that attackers are scanning for vulnerable servers and so far, we have seen a number of different exploits, everything from ransomware to DoS attacks, and we anticipate that this malicious activity will continue to ramp up in the coming weeks and months.
Everyone is impacted because it is so ubiquitous. It really does touch so many different types of software and services. Unlike most vulnerabilities, which typically require a specific attack vector and criteria to be in place to be able to take advantage of, this vulnerability is extremely simple to exploit. There are so many different ways you could potentially exploit it that it makes it extremely difficult to try and protect yourself against it.
The best bet for anyone to do is try and identify where the vulnerability sits in your environment and work to patch it as fast as possible.
l Organisations around the world rely on open-source libraries to bring applications to market quickly.
l These libraries stop short of a security-first approach.
l This dependence on what is effectively a wild, wild west of code libraries will continue to leave organisations vulnerable.
l CISO’s mist have have line of sight in Software Bill of Materials for their organisation, also for the software they are buying from vendors.
l Managed or hosted, there is risk introduced into your environment based on decisions other people have made when building their services.
l It is about identifying what in their infrastructure is impacted by this vulnerability, taking remedial measures that limit the impact.
l Everyone is impacted because it is so ubiquitous and touches so many different types of software and services.
UAE-based smart and green facilities management company Farnek has launched its remote monitoring solution using the Internet of Things with a pilot project at select Aster facilities in UAE. Sensors, located at the select Aster pharmacies and clinics, will record temperature changes and energy consumption based on current voltage, amongst other data which includes footfall. These statistics are then collated by a remote management system, which provides live readings for Farnek technicians.
The data is then subsequently driven by Machine Learning and an artificial intelligence based analytical platform, producing timely alerts, analytical reports and dashboards utilised for day-to-day and predictive maintenance, forecasting and planning.
Thresholds can then be set and benchmarked against similar facilities and assets and if there is a breach of those standards, alerts are sent in real time to a 24x7 command centre and technical teams who by using mobility solutions can take appropriate action. The platform also uses encryption protocols safeguarding the data with bank grade security.
Hi-tech initiative will monitor energy demand, room temperature and footfall providing data analytics in real time across 5 Aster Clinics and 21 Aster Pharmacies
PROW, a Dubai-based provider of system integration and professional IT and ICT services, has implemented the Revealx solution from ExtraHop, the leader in cloud-native network detection and response NDR, for United Arab Bank UAB to ensure visibility within its network and improve cyber security across its applications and services.

PROW announced the partnership where they presented an award to Ayman AlQudsi, Chief Information Officer at United Arab Bank, for being the first to implement the NDR solution from ExtraHop in the region.

PROW also launched its Managed Security Operations Centre SOC service, a combination of state-of-the-art technologies that can be tailored to each client’s individual needs, as well as announcing the addition of Enigma, a real-time business, services and network analytics platform, to its portfolio of solutions.
United Arab Bank is among the longest-standing and most innovative banking and financial services firms in the United Arab Emirates. Based in Sharjah, United Arab Bank was incorporated in 1975. United Arab Bank operates six corporate and retail branches throughout the country.
Infor, announced that Supertech Group, has digitally transformed with the help of Infor LN, enhancing its ability to meet growing demand for industrial products and discrete manufacturing across sectors.
Supertech Group is one of the leading businesses in the Middle East and India for the supply of industrial products & services in sectors including oil & gas, petro-chemical, power generation, primary steel, alternate energy, food & beverage, automotive, and marine & shipping.
Supertech Group has transformed its sales, engineering, distribution, and after-sales support operations with Infor LN, a powerful, industry-focused, enterprise resource planning ERP application. The solution has enabled the company to increase visibility, reduce complex-

Infor announced that Abudawood Logistics, a subsidiary of Abudawood Group, the exclusive distributor for Proctor & Gamble, Ferrero, Quaker Oats, and other global brands in Saudi Arabia, has deployed Infor WMS warehouse management system. The project was completed by Infor’s Middle East partner SNS, a leading provider of supply chain consultancy and software implementation. Supporting warehouse operations for the fast-moving consumer goods FMCG brand partner, Infor WMS will help maximise the utilisation of pick locations through expedited demand replenishment, while streamlining picking processes.
As a multi-billion-dollar enterprise, operating more than 130 facilities across six countries, Abudawood’s warehousing operations are vast. With complex shelf-life requirements

ity and boost efficiency across its business, supporting its evolution into a value-added service provider that designs, builds, and installs customised solutions for customers.
Supertech Group also transformed its human capital management HCM, with bespoke HR solutions especially built into Infor LN. These solutions enhance the way Supertech Group manages its large and rapidly growing workforce, enabling it to increase the efficiency of its HR practices, raise productivity and improve customer service.
With Infor LN, Supertech Group is now able to capture and manage product warranty information, which is essential when its customers visit for quality audits. The solution has transformed integration between the engineer-to-order cycles, improved sales and
finance processes, and increased visibility of complex supply chains. As a result, stock values are now 100% accurate.
The implementation of Infor LN, which is for 80 users across Supertech Group’s operations in the UAE, Qatar, Oman, and India, was managed by Infor partner Piersoft.
based on order type, account type and brand, Abudawood relies on efficient and dynamic replenishment of full pallets into pick locations based on variable shelf-life windows.
Infor WMS was selected based on its vast capability to support third-party logistics 3PL activities as well as demand replenish-
ment capabilities that support the dynamic assignment of pick locations, and auto move functionality that supports the defrosting cycle of Ferrero products. SNS was chosen based on its in-depth warehouse management experience and expertise and understanding of Abudawood’s business nuances and challenges.

Esharah Etisalat Security Solutions, a subsidiary of UAE government entity Professional Communication Corporation, Nedaa and the Official Secure Systems Provider of Expo 2020 Dubai, has deployed its state-of-the-art, mission-critical communication solution at the Expo site where it currently runs its Operations Centre.
Esharah has made available thousands of Airbus TETRA handheld communication devices to first responders assigned to the Expo to help ensure safety and security at the ongoing grand global event.
Dubai Police, Dubai Civil Defence, Dubai Corporation for Ambulance Services DCAS, and Expo security and site management teams, among others, that are operating at Esharah’s command and control centre can easily connect with their staff on the field who are carrying the handheld mobile communication technologies. Esharah’s system also allows various agencies to communicate via the solution’s shared Talkgroups feature for faster collaboration during daily operations and emergencies. With enhanced performance, the deployed
modern equipment has wider coverage and are equipped with advanced voice and data communication functionalities. They ensure reliable and secure connectivity among mission-critical users wherever they are positioned across the 4.38-square kilometre venue.
Esharah has also set up a dedicated Service Centre at the Expo site to provide support to all users of TETRA and Nedaa’s LTE private mobile radio networks. Located at the back of Expo 2020’s main office and is close to the main operations centre, the facility is manned by a team of specialists ready to programme, reprogramme, and repair the radio devices, as well as support other related needs on-site.
Additionally, Esharah has installed two UV sanitising machines into the facility in compliance with the UAE Government’s COVID-19 guidelines.
Aside from the Service Centre, whose operation hours follow that of the Expo’s, Esharah has put in place a service team at each Zone Operations Centre of the Sustainability, Opportunity and Mobility Districts, Expo’s

Finesse has successfully implemented Automation Anywhere’s Intelligent Automation platform for Fujifilm. FUJIFILM uses Microsoft Dynamics GP to manage their logistics processes and Finesse has seamlessly integrated the Automation Anywhere Digital Workers with the CRM to ensure smooth process runs each time. In addition to the manhours saved, implementing RPA has also further strengthened the process sta-
three main districts, to guarantee fast support to all device users.
Esharah, which was named the Official Secure Systems Provider in early 2020, is an expert in the field of wired and wireless telecom networks Tetra and Public Safety LTE and security solutions. Its top clients in Dubai include Dubai Police, Dubai Airports, DP World, and the Roads and Transport Authority.

bility by eliminating human dependencies, translating into continuous value generation. Prior to RPA, the processes were done manually and involved review, reconciliation, and reporting of large volumes of data. This was not only time consuming, but also ridden with innumerable possibilities for human error. This, in turn, would significantly reduce the aggregate operational productivity.
Effective Solution design is the backbone of a successful RPA implementation. Finesse recognises this as a key driver in the overall RPA lifecycle and therefore, the focus of any implementation is Optimised Process Automation. Finesse designed and developed highly efficient digital workers, or bots, that deliver the expected output accurately, consistently, on-time and on-demand. At any given point in time, these digital workers are capable of multi-tasking and moving between processes as scheduled.
Third-party certifications and attestations serve as industry-defining standards that help demonstrate a security program’s effectiveness, allowing organisations to provide assurance over the security of their products and services. At Zoom, third-party certifications and attestations are integral to our security program’s foundation and allow us to provide customers with transparency into our security program and control environment. The expanded list of industry-recognised certifications and attestations with two new additions: ISO IEC 27001:2013 and SOC 2 + HITRUST.
Zoom Meetings, Zoom Phone, Zoom Chat, Zoom Rooms, and Zoom Video Webinars are now certified as International Organisation for Standardisation (ISO) International Electrotechnical Commission (IEC) 27001:2013 compliant.
Zoom has expanded the scope of its existing SOC 2 Type II report to include additional criteria to meet Health Information Trust
Alliance Common Security Framework (HITRUST CSF) control requirements. HITRUST is a security framework that leverages nationally and internationally accepted standards and regulations such as GDPR, ISO, NIST, PCI, and HIPAA. Zoom’s SOC 2 + HITRUST report provides a transparent look at the controls in place that protect the security and availability of the Zoom platform as they align with the American Institute of Certified Public Accountants (AICPA) Trust Services Principles and Criteria and the HITRUST CSF. This attestation applies to Zoom Meetings, Zoom Phone, Zoom Chat, Zoom Rooms, and Zoom Video Webinars.
Red Hat announced Red Hat Ansible Automation Platform on Microsoft Azure. It builds on Red Hat’s standard for hybrid cloud automation that has been refined for the evolving realities of computing at hybrid cloud scale. The collaboration between Red Hat and Microsoft delivers a powerful solution that provides customers flexibility in how they adopt automation to deliver any application, anywhere, without additional overhead or complexity.
According to an IDC report, virtually 97% of organisations see major barriers to their ability to effectively employ automation across their enterprise. Through 2023, many IT automation efforts will be delayed or will fail outright due to underinvestment in creating IT, Sec, DevOps teams with the right tools and skills. The end goal is to deliver consistent, coherent and cooperative automation at scale.
Customers can more easily automate across

hybrid clouds, IoT and edge deployments with Red Hat Ansible Automation Platform on Microsoft Azure
Red Hat Ansible Automation Platform on Azure helps IT organisations perform these challenging tasks at scale while minimising user error. The integration with Azure services, including Azure compute, network and storage can further increase the ROI of automation, allowing customers to scale their IT operations.
Red Hat Ansible Automation Platform on Azure enables enterprise IT teams to achieve greater scale, speed and standardisation with automation practices for their hybrid cloud. This helps to remove the infrastructure maintenance and operational burden from IT teams, enabling them to focus purely on delivering automation strategies for a more efficient, flexible and scalable business.
The latest version of Ansible Automation Platform added self-contained automation
JOE FITZGERALD, Vice President and General Manager, Ansible Business Unit, Red Hat.capabilities to deploy at massive scale across hybrid clouds and edge environments, while shifting automation more deeply into the application development lifecycle. Its flexible foundation, tools, services and capabilities offer a whole new level of customisation and control that expands the boundaries of what is possible for enterprises.

HP and Dynagraph have announced their collaboration to introduce HP Indigo and PageWide Press technology for the first time to the UAE market. HP Indigo 7K digital press will be the company’s first product installed at Dynagraph premises. Like all other HP Indigo presses it offers endless applications using the widest range of media and over 30 specialty inks and aims to meet the changing world demands whilst maintaining agility, productivity, and innovation.
Mass customisation is the next frontier for both global brands and smaller companies, and HP is already helping brands, like Shutterfly and ePac take their customisation further. Design runs that used to number in the tens of thousands can now be customised by unit, which makes labels, cases, POS materials and direct mail more relevant and personal than before. Through the speed and agility of HP Digital Presses, brands are able to interact with real world events, for example Cadbury creating a limited-edition Liverpool Football Club Champions Bar.


AVEVA launched Vision AI Assistant 2021, an image classification-based analytics tool. The artificial intelligence solution, which can be integrated into AVEVA System Platform and Operations Management Interface and AVEVA Insight, enables customers to use video and images from existing general-purpose cameras and convert them into user-friendly information and timely alerts.
Designed for low latency industrial environments, Vision AI Assistant leverages deep learning to train and deploy 24×7 artificial intelligence models to enhance situational awareness to help operators focus on the task at hand without continuously monitoring live camera feeds.
Vision AI Assistant enables organisations to improve operations, quality, and maintenance capabilities across industrial enterprises by using cameras to determine visual anomalies,
assess quality, and vigorously monitor production, optimising efficiencies and improving sustainability in the process. Product applications include:
Standard digital cameras can be used with Vision AI Assistant to ensure quality control, such as by analysing the quality of water treatment fluids, by gauging if a hopper is full or empty, or by identifying defective products on a production line.
Vision AI Assistant can also scan thermal or infrared camera feeds so operations teams can uncover visual inconsistencies. For example, by locating compressed air or fluid leaks, it can reduce failure and efficiency loss, and by spotting hot spots in a datacentre, it can prevent overheating of critical equipment.
The AI solution assists maintenance efforts through continuous monitoring of plants and machinery and diagnosis of equipment issues


NetApp, unveiled evolution of its all-flash storage system array portfolio with the NetApp AFF A900, powered by NetApp ONTAP Enterprise Edition. The new AFF A900 offers organisations the highest data storage performance to accelerate their business-critical enterprise database and application needs, the security and reliability to keep customer data highly available and secure, and the simplicity and flexibility that agile organisations require.
NetApp AFF A900, the more performant next generation of the highly resilient AFF A700 system, is offered exclusively with NetApp ONTAP Enterprise Edition data management software. ONTAP Enterprise Edition leverages the world’s leading data management software and is delivered pre-packaged with all the components enterprises need, including unified support for SAN, NAS, NVMe-oF, and S3, built-in data protection with optional cutting-edge anti-ransomware capabilities, and the high performance and resiliency required to support the most critical business workloads.
With the most flexible and complete hybrid multi-cloud offerings in the market, companies can extend and scale to any cloud as needed with ONTAP’s deep, market-leading integrations with public cloud providers.
The AFF A900 delivers an enhanced user experience for managing
weeks, or months before failure.
Vision AI Assistant is offered as an exclusive extension for AVEVA System Platform purchases through the AVEVA Flex subscription initiative. The flexible payment and usage program spans any mix of cloud, hybrid, and on-premises solutions across AVEVA’s portfolio – enabling simple license purchasing, usage and management.
organisations’ most important enterprise databases like Oracle, SAP HANA, Microsoft SQL Server, and virtualised applications. Touting extremely low latency around 100?s, the AFF A900 increases performance by up to 50 percent over previous models (AFF A700 with like protocols).
Enterprises can take advantage of modern network connectivity without new hardware investments in networking infrastructure with first-to-market enterprise-grade NVMe TCP in addition to NVMe FC. Organisations can also scale and grow with unified multi-protocol support for SAN, NAS and Object storage, delivering maximum flexibility for enterprise storage needs while increasing reliability and reducing performance tuning and support costs.
There is a positive trend in how organisations respond to cybersecurity breaches from an HR perspective, according to a recent Kaspersky study. In 2021 across the META region, though the number slightly increased in the laid off senior IT staff, 15% in 2021, compared to 13% in 2018, the figure for senior IT security roles actually decreased, 5% in 2021 compared to 15% in 2018, if a data breach occurs. Amid a challenging cybersecurity environment and growing IT complexity, the demand for IT and cybersecurity specialists remains high.
According to the Gartner 2020 Board of Directors Survey, by 2025, 40% of boards will have a dedicated cybersecurity committee overseen by a qualified director. While cybersecurity risks become the second most critical source of risks for enterprises, behind only regulatory compliance risk, the role and responsibilities of IT security executives are crucial. And with a continuing skills gap in the market, it should be important for organisations to save experts in their positions.
IT Security Economics 2021: Managing the trend of growing IT complexity reveals that fewer enterprises globally now fire employees

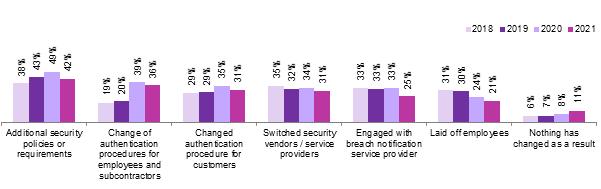
because of data breaches. In the META region this common measure in responding to data breaches actually witnessed an increase when comparing the numbers to 2018, 22% to the 27% in 2021.
The split of employees that could lose their job as a result of a cybersecurity breach has also changed. In addition to senior IT and IT security roles, C-level executives are likely to be exposed to dismissals too – 3% in 2021 similar to 3% in 2018. The trend is also relevant for non-IT senior staff. As a result, the overall split across IT and non-IT, senior and nonsenior roles, became flatter than a few years ago.
The demand for retaining and nurturing expertise is seen, for example, in budget planning: 30% of enterprises report the need to improve the level of specialist security expertise as the top reason to increase their IT security budget. In fact, this is the second most common reason, followed only by increased complexity of IT infrastructure 38%. Furthermore, by investing in internal specialists, employers are interested in retaining their knowledge within the company so that employees could leverage their skills in future.
By 2025, chip shortages and trends such as electrification and autonomy will drive 50% of the top 10 automotive original equipment manufacturers to design their own chips, according to Gartner. As a result, it will give them control over their product roadmap and supply chains. Automotive semiconductor supply chains are complex. In most cases, chip makers are traditionally Tier 3 or Tier 4 suppliers to automakers, which means it usually takes a while until they adapt to the changes affecting automotive market demand. This lack of visibility in the supply chain has increased automotive OEMs desire to have greater control over their semiconductor supply.
In addition, the on-going chip shortage is primarily with mature semiconductor technology node devices that are fabricated on smaller 8-inch wafers, where capacity expansion is difficult. “The fact that the automotive industry has been conservative in qualifying older devices on larger wafer sizes has also hurt them and will likely motivate them to take chip design in-house,” said Gupta.
This model of bringing chip design in-house, or popularly known as OEM-Foundry-Direct,
is not unique to the automotive industry and will intensify among tech companies as some changes are happening in the semiconductor market. Semiconductor chip foundries, such as TSMC and Samsung, have provided access to cutting-edge manufacturing processes, and other semiconductor vendors have given access to advanced intellectual property that makes custom chip design relatively easy.

Trend Micro announced that it has been named a leader for its Trend Micro Vision One platform in The Forrester New Wave: Extended Detection and Response Providers, Q4 2021 report. Trend Micro was nominated as a leader amongst 14 other vendors and scored the highest in the current offerings’ category. As per the Forrester report, it is the best fit for companies that need a robust, easy-to-operate security suite. Organisations that want a platform to deliver cross-telemetry integration of traditional security tools and top customer service will benefit from a relationship with Trend Micro.”
The New Wave report also highlighted that Trend Micro possesses loyal customers who are highly confident in the security efficacy of their solutions.
Of the 14 vendors evaluated, Forrester gave Trend Micro’s XDR solution differentiated scores in seven out of ten criteria: Visibility, Detection, Investigation, Product architecture, Threat hunting, Product security, and Product vision.
Trend Micro Vision One goes beyond any other XDR offering or legacy EDR solution to connect email, endpoints, servers, cloud workloads, and networks – and uses powerful security analytics to correlate data with Trend Micro’s global threat intelligence. The result is fewer, higher confidence alerts and earlier detection, all from a single location.
It also enables integrations with third-party Security Information and Event Management SIEM and Security Orchestration, Automation and Response SOAR tools as well as Azure Active Directory to maximise value for customers.
By 2023, at least 85% of governments without a total experience strategy will fail to successfully transform government services, according to Gartner. Governments that continue to focus on citizen and employee experience initiatives separately will miss out on essential synergies to effectively transform their services.
Over the past two years, most governments increased their investments in digital initiatives to respond to pandemic-induced operations disruptions. However, many digital initiatives are still occurring in silos.
Governments must move from a siloed approach to a cohesive strategy encompassing employee experience and citizen experiences across multiple platforms, channels, and technologies in the most intuitive user experience. This can drive digital adoption, improve outcomes and mitigate the effects of underwhelming service experience which
can otherwise lead to a failure of government’s digital transformation initiatives.”
A TX approach combines the disciplines of user experience UX, citizen experience CX, employee experience EX and multi-experience MX into one holistic approach toward service design and delivery. A TX strategy ensures that resources across CX, EX, UX and MX disciplines collaborate to uncover new opportunities for improved service delivery that increases both citizen and employee satisfaction and improves the government’s mission outcomes.
Government CIOs need to prioritise investments in capabilities that can be leveraged by both employees and citizens. For example, using voice of the citizen and voice of the employee input to identify common pain points and, therefore, potential to refine the experiences for both through one initiative. CIOs need to focus on supporting effortless
APEKSHA KAUSHIK, Principal Research Analyst at Gartner.experience across multiple touchpoints by linking datasets as digital solutions can help employees be more citizen-centric and improve overall governance.

Governments must
Veritas Technologies unveiled research finding that office workers in the UAE are not always quick to admit their errors when losing data from cloud-based applications, such as Microsoft Office 365, which they have been asked to adopt in the wake of the COVID pandemic. As a result, their employers are losing critical business information, including customer orders and financial data, through accidents and ransomware attacks.
In its new research, which polled 11,500 office workers across nine countries, including 500 from the UAE, Veritas found that seven in ten 72% UAE-based office workers have accidentally deleted shared data such as Word documents, presentations or spreadsheets, with as many as 24% accidentally deleting shared data multiple times a week.
According to the research, UAE employees are more willing than their global counterparts to come forward and admit their mistakes, with 89% saying they have owned up to accidentally deleting data from cloud applications such as Office 365 or Google Docs, compared to 84% globally. Of those that weren’t so quick to come forward, 36% said no one noticed their error, but in the cases where the accidents were discovered, almost a fifth 19% of respondents reported that the data was lost for good.
Employees are even less forthcoming with ransomware incidents. Just 18% of UAE respondents said they would immediately alert their IT department if mistakes they made introduced ransomware into their organisations. Another 43% said they would either do nothing or pretend it had not happened.
l 72% of office workers in the UAE have accidentally deleted shared data such as Word documents, presentations, or spreadsheets
l 96% of respondents thought their cloud provider would be able to restore their files for them
l UAE employees more likely to own up to accidentally deleting data than their global counterparts
The research also highlighted that there are misconceptions around how much help the cloud companies hosting their files would offer, in the event that their data is lost. In fact, nearly all UAE-based respondents 96% thought their cloud provider would be able to restore their files for them, either from a cloud copy, their deleted items folder or a backup.
 JOHNNY KARAM, Managing Director & Vice President of International Emerging Region at Veritas Technologies.
JOHNNY KARAM, Managing Director & Vice President of International Emerging Region at Veritas Technologies.
While Boards are doing a lot to bridge the gap between themselves and the CISO here are some strategic measures to make enterprise more agile and secure.
For the Boards of global and regional organisations, cybersecurity and managing digital transformation alongside, are promising to be amongst the most challenging. While Boards are doing a lot to bridge the gap between themselves and the CISO and the security organisation, here are some other technology and strategic measures that can help make the enterprise more agile and secure.
What is the biggest and most immediate change required in an organisation’s security policies? It is the fact that majority of its employees are no longer employees but more like remote workers. Or in other words, remote workers are now the workers and remote work is now the organisation’s work. In other words, enterprises need to reset their entire security policies and tools to be able to manage risks from this new organisational reality.
How will security be deployed for the modern hybrid organisation, where workers are switching between multiple modes of working. At times they will be onsite inside the office firewall, at other times mobile and on the move, and at other times working from home. All the while accessing the wireless networks, Internet or private VPNs. How will an organisation’s security architecture continuously adjust for its workers as they move across its fabric?
Today’s enterprises are being turned inside out with these challenges of managing workers requiring multiple modes and levels of security access. All organisations will need to have a defensive posture and welldefined security policies and risks with regard to onsite, remote and mobile workers.
One of the approaches is to develop and deploy a cybersecurity mesh, which enables a distributed enterprise to deploy and extend security where it is required the most.
Other than the pandemic, digital transformation is also responsible for connecting industrial, operational, IT assets that are distributed across the fabric of the organisation. These assets could be located at the edge, inside the network, at the core, and even inside other networks.
Gateways and middleware are now effectively and efficiently connecting disparate networks inside enterprises that were not feasible a
decade ago. To manage all these challenges, security needs to be flexible, agile, scalable and yet robust enough to deliver for workers and protect for the organisation.
As workers move across the enterprises’ security fabric, their security access levels need to keep changing. More importantly so should their identity-based security, with zero-trust being a dominant requirement. While zero-trust identity access is not new, it gains renewed importance in the face of hybrid worker access as well integration of disparate networks driven by digital transformation.
Social engineering to gain identity access is a dominant activity for sophisticated global threat actors. Hence, identity management techniques and practices need to be further elevated in terms of importance.
Along with human identities, we also have machine and robot identities, that are adding additional complexities in the overall identity access management operations. Digital technologies such as robotic process automation are driving automation of processes and each of these automated process or Bots requires a sign-on into the network and application stacks. APIs are another vulnerable hot spot where access is granted to users across multiple applications via APIs.
To better manage digital transformation, enterprises need to relook at their end-to-end identity credentials across all humans, Bots, devices.
Boards are now alerted to address the challenges thrown up by ransomware, advanced persistent threats, and other supply chain malware that are having disastrous effects on some global businesses. Board members
We also have machine and robot identities adding additional complexities in the overall identity access management
have been in the spotlight for being unable to speak the same language as CISOs and therefore unable to bridge the gaps from top to bottom. Now they are forming dedicated committees headed by security experts and selected board member to bridge the gap and address the challenge.

With this initiative, CISOs can expect much better information flow with the Board, as well as much deeper conversations about security spending, policies, proactiveness, risks and governance, strategy.
An ongoing challenge that continues into the next year is the complexity of security tools that are being managed by CISOs and IT managers. Global surveys by research firm Gartner have found that 78% of CISOs are managing 16 or more tools across their cybersecurity vendor portfolio. While 12% of CISOs are managing more than 46 tools.
The harsh reality is that cybersecurity organisations have far too many tools, from far too many vendors, leading to complex management routines, continuously high demand on skills and increasing security headcount.
Under these circumstances, CISOs need to begin extended vendor consolidation activities, realising that such activities take time and there is no short-term solution while heading in this direction. Another reality check is that reduction of capex spending may not be a direct, realisable benefit, but rather reduction of indirect costs and increase in operational efficiency are more achievable and realisable targets.
New tools are being added to the portfolio of solutions that can be used to validate an organisation’s security vulnerabilities. One such area is breach and attack simulations that does continuous testing and validation of security controls and tests the ability to withstand external threats. It also highlights risks to high-value assets such as highly confidential data.
Another area that is developing is the ability to protect data while it is being read and used, in comparison to protecting data in motion or at rest. This enhanced security allows secure data processing, secure sharing, and cross border transfers without risks. ë
Business transformation is the way forward for business but is creating the cyber-time paradox, with CISO’s struggling with too many things to secure.
In the past year tensions have grown between many CIOs and CISOs. Why? The changing needs of businesses have created what we refer to as the cyber-time paradox. Technology has for many been seen as the business path forward, a way to open new markets and drive greater business efficiencies - for the CSIO this means more things to secure.
With the shift to working more flexibly, there is a considerable volume of connected devices now outside the business, leveraging a new range of collaboration tools. This requires new security capabilities that generate new kinds of telemetry for the security team to comprehend and correlate into actionable outcomes.
Equally, the threat landscape continues to expand both in volume and complexity as well. These factors inevitably also become force multipliers on the workload of any business’ Security Operations Centre.
Whilst the workload on the security teams is increasing, businesses become more dependent on the processes that they have now digitised, and the amount of down time allowed has been shrinking - particularly during the pandemic. This then creates the paradox of less time to act, but more work for any SOC team to complete.
They are already having to adapt to working from home and now have to deal with another headache. The only solution is to better automate the SOC to empower scale, but the main challenge for many organisations is balancing the time to shift processes and capabilities with managing the current workload – like juggling and sprinting at the same time.
In some ways this is an old problem, there simply are not enough security staff to cope with the growing business demands. This can result in security teams looking for quick fixes to keep pace with the business and the accelerated shift to the cloud.
Often the quickest solution to the problem can also be the simplest, but not always the best - in this case the native security provided by the cloud, be it infrastructure or SaaS. Quick as it is, this option effectively creates vendor lock-in, the very thing that most CISOs wish to avoid.
There is also a domino effect on the CISO’s work as the native security is inconsistent, each cloud or SaaS solution has its own interpretation of what security they provide and how it is delivered, creating longer-term challenges for the security team. A simple example of this is credential management.
For years many companies have worked towards single sign-on solutions to simplify user experience and, with rapid adoption of SaaS solutions, suddenly many are back to requiring multiple accounts. More
accounts add more complexity, and with complexity comes mistakes, which in turn create work for the security teams, and likely business impact.
The key for any security team is having broad visibility across their IT ecosystem. Yet if they cannot take that viability and apply it into actions, which typically takes correlation between both differing IT systems and security tools, the quick fix becomes a legacy drag that will continue to hamper the ability to keep pace with business needs.
Today most CISOs strive for best of integrated solutions, a change from the historical best of capability. That said, in recent times demand has often led to accepting satisfactory standards taking precedence to keep pace, but it is important not to lose sight of the strategy goals. CISOs are looking to simplify what has become a complex problem space, that means being able to integrate data from the security tools they use as well as adopting actionable processes.
Most critically, this is required if they are to automate some parts of the daily security tasks. If we cannot scale up human capacity at the rate required, we have to find smarter ways to keep pace with business demands.
CISOs should always have a long-term strategy in place, which ensures that when business plans are accelerated, they are ready with their own strategies to support them. The aspect that may have caught some off guard is remote working and the associated growth in shadow IT. Whilst legacy security only looked from the inside out, now they must do both.
CISOs must consider three imperatives to meet the cyber-time paradox problem and the increasingly distributed shift left cloud world:
Multiple CISOs utter the mantra for every new solution, remove two legacy solutions but in terms of costs and scale, consolidation is king.
While CISOs want to build digital trust, CIOs are concerned about business continuity, speed, agility
Teams get more alerts than they can process - Being able to correlate, consolidate and, more importantly, convert alerts into actionable outcomes is critical. Otherwise, there is no means of extending capabilities.
Any incident typically has many follow-up procedures and automation is not just a big singular STOP-GO button, it is much more about the augmentation of human skills. Teams must first identify the highly repetitive steps in every process that can be automated to shorten the process timeline.
At this moment in time, many organisations are undergoing digital transformation, making technology and infrastructure shifts quicker and on a larger scale than normal. To ensure security needs are being
properly met, organisations require more frequent updates on how this impacts their risks, which are often amplified by the interoperability in these changes.
Whilst CISOs want to build digital trust, CIOs are concerned about business continuity, speed, and agility. With cloud migration at the top of the CIO’s agenda, it is in their best interest to evade the cyber-time paradox, but they do not always realise the extent to which the security team is drowning in data and struggling to keep up.
Therefore, the most effective means of eliminating tensions between business leaders is understanding the languages of their stakeholders to have a meaningful conversation; always keep in mind that every part of any business has its own language, priorities, and procedures.


Avaya has appointed Sheikha Na’amah Al Qassimi as General Manager for the UAE, expanding her previous role as General Manager for Dubai and the Northern Emirates. In her new role, Sheikha Na’amah Al Qassimi will work closely with Avaya’s customers and partners across the country to support their increased focus on delivering superior customer and employee experiences.
With the country’s economy having benefited from a recovery in global travel, as well as a pick-up in domestic and external demand, Sheikha Al Qassimi will work with organisations to help them quickly adapt to a new period of growth through delivering outstanding experiences for their customers and employees.
Cohesity, announced appointment of James Worrall as head of EMEA channels. Worrall has extensive experience in building sales channels, having been in leadership roles for networking, enterprise IT and technology start-ups over the last 20-plus years.
In his role at Cohesity, he will report into the Cohesity global partner organisation, led by Mike Houghton. Worrall has responsibility for scaling the company’s EMEA partner ecosystem while advancing the company’s go-to-market strategy in the region.
EMEAR
Cisco AppDynamics announced the promotion of David Noël to the role of General Vice President, EMEAR, Europe, Middle East, Africa and Russia, with responsibility for leading sales operations and growing the AppDynamics business in the region. David joined AppDynamics in 2016 and has held a variety of leadership positions during his tenure. Most recently, he was the Regional VP SEMEA, Southern Europe, Middle East and Africa.



Schneider Electric appointed Sebastien Riez as the Cluster President for the North East Africa and Levant region, which includes several countries that are key to Schneider Electric’s presence in the Middle East and Africa, including Egypt, Iraq, Jordan, Lebanon and Malta.
Sebastien, who has over fifteen years of experience in energy management with a strong international background, will be responsible for accelerating Schneider Electric’s growth across the region and supporting customers with the company’s range of digital transformation and sustainability solutions.

Dataiku, the platform for Everyday AI, announced that David Tharp has joined the company as SVP Ecosystems and Alliances. In this role, Tharp will be responsible for driving the strategy, development, and field operations of Dataiku’s global partner programme including Technology Alliances, Global Systems Integrators, and Channel Partners. He will report to Chief Operating and Revenue Officer, Romain Fouache. Prior to Dataiku, Tharp served as the VP, Worldwide Partner Organisation at Anaplan, where he led the build and scale of the partner and alliance ecosystem at the company from its early stage through IPO, to its current multibillion-dollar valuation.

Tenable, the Cyber Exposure company, announced that it has appointed Brian Goldfarb as Chief Marketing Officer. Goldfarb will spearhead Tenable’s global marketing organisation, positioning the company for its next phase of growth across all areas of its portfolio, especially cloud security, risk analytics, OT, and identity. Goldfarb is a widely respected industry veteran who has held senior executive roles at some of the most important category-defining companies in the world including Splunk, Salesforce, Google and Microsoft.
He joins Tenable from Amperity, the world’s number one enterprise customer data platform. Goldfarb was CMO and senior vice president of business development at Chef Software, which was sold to Progress Software.
He led Splunk through a major digital marketing transformation, serving as chief marketing officer for critical years in the company’s growth. Prior to Splunk, he was senior vice president of marketing for Salesforce, leading a global marketing team responsible for generating more than $1 billion in revenue.

Vectra AI announced that it has appointed Steve Cottrell as its EMEA CTO. Steve will work to strengthen relationships with customers and prospects, security communities, and government and intelligence agencies to identify key security pain points, while helping evolve security strategies in support of digital transformation and cloud adoption.
Steve will also help security decision makers communicate the value of AI-driven threat detection and response tools to their teams and senior stakeholders.

BeyondTrust, the worldwide leader in Privileged Access Management, announced that Rob Spee has been appointed SVP of Global Channels. He brings more than 25 years of experience leading successful channel organisations. Rob joins BeyondTrust from OutSystems where he was the RVP of Americas Channels, where he helped modernise the global partner strategy and partner ecosystem, including resellers, regional and global system integrators, MSPs and cloud providers.
At BeyondTrust, Rob will lead the global channel strategy, with a focus on expanding market share through its global partner ecosystem. BeyondTrust will continue to build on its momentum in the channel and looking at how it engages and enables partners, utilising intellectual property, and helping partners strategically and financially. These are attributes of a world-class channel framework and critical to BeyondTrust’s commitment to the channel.


Multinational Corporation Acer has appointed Massimiliano Rossi as Regional Vice President for Middle East and Africa alongside his ongoing role as Head of Product Business Unit for Europe, Middle East, and Africa. Acer has also appointed Michele Montecchio as Country Manager for Middle East following the decision of Paul Collins who, after a successful tenure of driving the Acer Middle East and Africa business for 7 years, has decided to retire.
Under Paul’s leadership, Acer has been focused heavily on strengthening its operations in the region and has taken various measures to develop its business locally. The changes in upper management personnel reflect a continuation of the company’s unwavering commitment to support the MEA region.
Rossi has been serving as Vice President EMEA PBU since 2017. A long-time Acer employee, he has been with the firm since 2007, having started in product development. During his nearly 15-year association with Acer, Rossi has worked in different leadership capacities.
Aruba, a Hewlett Packard Enterprise company, has appointed Zeeshan Hadi to the role of Country Manager, UAE to drive the company’s growth in the market. Zeeshan will assume responsibility for leading the sales and pre-sales teams as well as planning and executing channel and marketing strategies.

Zeeshan is an ICT industry veteran with over 17+ years of experience in various roles including territory manager, channel manager, sales manager, systems analyst, corporate trainer and software engineer. He has worked for over a decade at Aruba the last five being in Canada and has a strong track record of building profitable business relationships with a diverse set of enterprise customers.
In one of his previous roles as corporate trainer, he has contributed to skills development in the region by helping a significant number of executives build their knowledge and expertise in the technology field.
In Zeeshan’s new role, one of his key priorities will be to expand the channel ecosystem and build stronger relationships with Global System Integrators. There will also be a special focus on investing and growing business in Abu Dhabi and engaging more closely with public sector agencies with a view to building value and long-term partnerships within the government segment.
AVEVA, announced the expansion of its Middle East executive leadership team with the appointment of Nayef Bou Chaaya as the company’s Vice President Sales and Head of Middle East and Africa. The new appointment strengthens AVEVA’s partner and customer relations at a time when the company is facilitating digital transformation for an increasing number of industrial businesses in the region and around the world. Bou Chaaya is a seasoned executive management professional with three decades of software sales experience, focused on the oil & gas, energy, infrastructure and food & beverage sectors. He joins from Schneider Electric, where he led Process Automation Business Development in the Middle East, preceded by various senior sales and operations leadership positions within Schneider Electric and Invensys.
Raised in Lebanon, Bou Chaaya holds a bachelor’s degree in computer science from Lebanese American University and will be based in Dubai. AVEVA will leverage his deep expertise to lead the MEA organisation and to help partners around the world to strengthen their operational and environmental sustainability.
March 17, 2022

Address Dubai Marina, Dubai - UAE
BY