





Visualise, inventory, and understand assets through continuous pentesting and manual exposure triage.
Measure your detective controls with customisable procedures run by our manual pentesting teams.
Secure your web, mobile, thick, and virtual applications.
Secure your internal, external, and wireless networks.
Secure your AWS, Azure, and Google cloud infrastructures.
Secure your ATM, automotive, medical, OT, and embedded devices and systems.

Uncover and understand blockchain security concerns.
Your business is only as secure as your last, best test.
Build a mature application security program.

Find application security vulnerabilities with SAST, SCR, triaging, and training.


Put your security controls, security policies, and cybersecurity training to the test.
Conduct email, phone, or physical security social engineering tests.





Arctic Wolf
Assured Data Protection
Beyond Identity
Capture the Talent Ltd
Chartered Institute of Information Security
Complete Cyber

10:0010:45
11:0011:30
11:45 -
12:15
12:30 -
13:15
13:2013:50
14:00 -
14:30
14:4515:15
15:3016:00
16:1516:45
Confessions of a Hacker #FYRA
<< Hacker >> Classified
The Contemporary Threat Landscape, and the Ever Diversifying eCrime Ecosystem
Stuart Wiggins, Strategic Threat Advisor, Crowdstrike
Breaking the cycle on Groundhog Day
Sarah Armstrong-Smith, Chief Security Advisor for Europe & Board Advisor, Microsoft
So Long and Thanks for all the Phish
Geoff White, Author and Investigative Journalist
Glenn Wilkinson, Consultant Hacker
Criticality of Bespoke Security and Utilising AI to Think Like an Attacker
Hanah Darley, Head of Threat Research, Darktrace
Stealing the Crown Jewels
Graham Cluley, Host, “Smashing Security” podcast, Cluley Associates Limited
A frank interview with Cecilie Fjellhoy, from Netflix’s The Tinder Swindler
Cecilie Fjellhøy, From Netflix’s Tinder Swindler
Into the Mind of the FBI: Give yourself the advantage
Miguel Clarke, GRC and Cyber Security - Ex-FBI, Armor Cybersecurity
From Offensive to Defensive – How Exposure to Counter-Terrorism Efforts in the Middle East Shaped my Career
Dan Gericke, Chief Technology Officer, ExpressVPN
10:0010:30
11:0011:30
11:4512:15
12:3013:15
14:0014:30
Fighting AI with AI: Tackling the ChatGPT cyber threat
Baldeep Dogra, Senior Director, Product & Technical Marketing, BlackBerry
Deception Via Perception (From Blue Tractors to A Blue & Black Dress)
Jayson E. Street, Hacker, Helper & Human
How to hire a hitman on the dark web
Jake Moore, Global Cybersecurity Advisor & Spokesperson, ESET
Hot or OT? The present and future threats to our hyper converged world
Rik Ferguson, Vice President Security Intelligence, Forescout
Biohacker The Human Threat
Len Noe, Technical Evangelist, White Hat Hacker & BioHacker, CyberArk






Our platform provides expert coaching, automated interventions, subtle security nudges, and much more to help empower your organisation to prevent breaches.



Join CEO, Founder, and ethical hacker James Moore for an insightful session at the Culture Theatre on April 4th, 12:30 PM. Immerse yourself in “Harnessing Behavioural Data for Comprehensive Human Risk Management”
HUMAN RISK MONITORING
SECURITY COACHING

AUTOMATED INTERVENTIONS


SECURITY NUDGES
ISSUES
11:0011:30
11:4512:15
12:3013:00
14:0014:30
14:4515:15
15:30 -
16:00
16:1516:45
From Asset Management to Asset Intelligence: Crossing the CAASM
Carl Curran - Axonius
Metaverse cybersecurity: benefits, challenges, security risks & the human factor
Zoe Edmeades Managing Director, The Security Company
Using behavioural data to drive end-to-end human risk management
James Moore, CEO & Founder, CultureAI

Building Cybersecurity Into Your Corporate Culture

Tanmoy Hossain, CTO, Bob’s Business
Developing Cyber Capability Within Your Organisation
Amanda Finch, CEO, Chartered Institute of Information Security (CIISec)
Can we change behaviours in real-time? A behavioural science approach
Tim Ward - CEO & Co-Founder, Think Cyber
The human element: Fixing the behaviours that lead to breaches
Jack Chamman - Egress
11:0011:30
11:4512:15
12:3013:00
14:0014:30
14:4515:15
Effectively fending off cyber crime - how to create a sustainable security culture
Richard Jerome, Director UKI, Awareness Specialist, SoSafe
In-the-moment nudges – what? How? Applying nudge theory to awareness
Tim Ward, CEO & Co-Founder, Think Cyber
Changing human behaviours
Bebe Lees, Head of Communications, The Security Company
Cyber Security Skills: Low Supply, High Confusion?
Professor Steven Furnell, Professor of Cyber Security, University of Nottingham
Professionalisation of the Security Testing industry – the wild west is being tamed
Debi McCormack, Marketing & Communications Director, The Cyber Scheme

The game changer in the world of privacy and securing your sensitive data.
This enhancing technology protects data and applications whilst in use. It enables collaborative data processing without compromising data privacy requirements.

11:0011:30
11:4512:15
12:3013:15
14:0014:30
14:45 -
15:15
15:3016:00
16:1516:45
11:0011:30
11:4512:15
12:3013:00
14:0014:30
14:4515:15
15:3016:00
Sponsored by
Remote Access Made Safe
Majid Mohammed, Channel Sales Manager, Wallix
Nicolas Moskal, Presales Engineer, Wallix
Frictionless Authentication in Banking – Is There Such A Thing?
Ruhan Basson, VP of Pre-sales and Customer Success, Keyless
Brought to you by WiCys TBC
What is the future of equity in Cybersecurity? What concrete steps do individuals and organisations need to make to create a fairer, more open and more equitable profession
Eleanor Dallaway, Co-founder & Content Director, Assured Intelligence
Lorna Armitage, Co-founder, CAPSLOCK
Marc Dean Avery, CISO and Managing Partner, Cyber Chain Alliance Ltd
Suid Adeyanju, CEO, RiverSafe
Hybrid Mesh Security : Manage Security ANYWHERE AND EVERYWHERE
Erik Van Harten, Senior Sales Specialist Security - EMEA, Juniper Networks
Cybersecurity in life and death: Examining implanted and interconnected medical technologies through the lens of patient care
Dr Isabel Straw - NHS
How to unlock your company’s DevSecOps potential?
Peter Murray, Principal Technical Architect, International, Github
Essential Endpoint Security Strategies to Counter Cyberattacks
Leonard Jayakumar, Head of Enterprise Product Support, ManageEngine
R4IoT: When Ransomware meets the Internet of Things
Rik Ferguson, Forescout Technologies
Cybersecurity: How to Reduce the Risk of Cyberattacks
Chris Thorpe, EMEA Cloud Solutions Architect, Quest Software
Procuring Assured Security Services – CREST Approved
David Allen, Managing Director, CYSIAM
API security - what is it, why you should care, and how to protect your org
Jeremy Snyder, CEO, FireTail

IT/OT Convergence: A New Approach to Security
Trevor Dearing, Director of Critical Infrastructure, Illumio

11:0011:30
11:4512:15
12:3013:00
13:1513:45
14:0014:30
14:45 -
15:15
15:3016:00
16:1516:45
11:0011:30
11:4512:15
12:3013:00
13:1513:45
14:0014:30
14:4515:15
Sponsored by

Demystifying Confidential Computing – the game changer in the world of privacy and securing your sensitive data
Richard Searle, Vice President of Confidential Computing, Fortanix
Data Sovereignty - Unleashed
Nikhil Srivastava, Cyber Security Consultant Thales, CPL
Puzzling through the XDR Jigsaw Pieces: Buzzword or genuine security movement?
Elliott Went. Senior Security Systems Engineer, SentinelOne
Navigating The Dark Corners of Social Engineering Attacks
Graham Thomson, Chief Information Security Officer and Partner, Irwin Mitchell
Robyn Savage, Customer Success Director, Tessian
Security Laggard to Leader: How to harness cloud-native technology & crowdsourced intelligence to bring
24/7 Managed Threat Detection & Response to every organisation
Nick Dyer, Senior Systems Engineer, Arctic Wolf
How a “Digital Twin” could Simplify your Security Posture Management
Bob Vickers, Sales Director, Northern Europe and Middle East, Skybox Security
How Quantum Technology Will Improve Security?
Professor Rob Young Director, Quantum Technology Centre, Lancaster University United Kingdom
Cyber Crime Post Pandemic - immunity starts with you
Neil Sinclair, Formerly National Cyber Lead of Police Digital Security Centre
Security Automation – It’s not if I Automate, It’s When I Automate
Toby Van de Grift, Vice President Europe, Swimlane
Baseline 3.0
PC Andy Robinson, Cyber Griffin at City of London Police
Is NDR a cost… or an investment?
Adrian Jones, Country Manager UKI, GATEWATCHER
The rapid evolution of Cloud Security - A Zander Letter to my Future Self
Brian Laing, VP of Strategic Alliances, Orca Security
Jed Kafetz, Head of Assurance Services, Claranet
Attack of Zones
Gary Cox CISSP, Technical Director, UK and Ireland, Infoblox
Cyber insurance: debunking the headlines – interview with a broker
Graham Hawkey - Osirium
Wondering how to change behaviours in real-time?
Support people with gentle nudges to guide behaviours at the point of risk
Engage your people making security relevant to their role and personal lives



Baseline behaviours with or without interventions
Reinforce and embed awareness, with short tips and reminders.
Measure risk and behaviour change
thinkcyber.co.uk


11:0011:30
11:4512:15
12:0013:00
14:4515:15
15:3016:00
16:1516:45
Welcome to the socially engineered jungle
Javvad Malik, Lead Security Awareness Advocate, KnowBe4
Why AI is the Solution for the Threats of Tomorrow
Hanah Darley, Head of Threat Research, Darktrace
Hacking Things Faster
Nick Dyer - Arctic Wolf
Back to the future: 2022 Tales of Arctic Wolf’s Global SOC & AW Labs Threat Research findings for 2023
Holly Grace Williams, Managing Director, Akimbo Core
Beyond the Ransomware Task Force: Examining Government Responses to the Ransomware Scourge
Jen Ellis, Cybersecurity advocate and community convenor
5 Steps to Reducing Cyber Risk
Stuart Coulson, Cyber Security Consultant
11:0011:30
11:4512:15
12:3013:00
14:0014:30
15:3016:00
Tracking the Adversary: What we can learn by watching an Advanced Persistent Threat group in action
Christiaan Beek, Senior Director, Threat Analytics, Rapid7
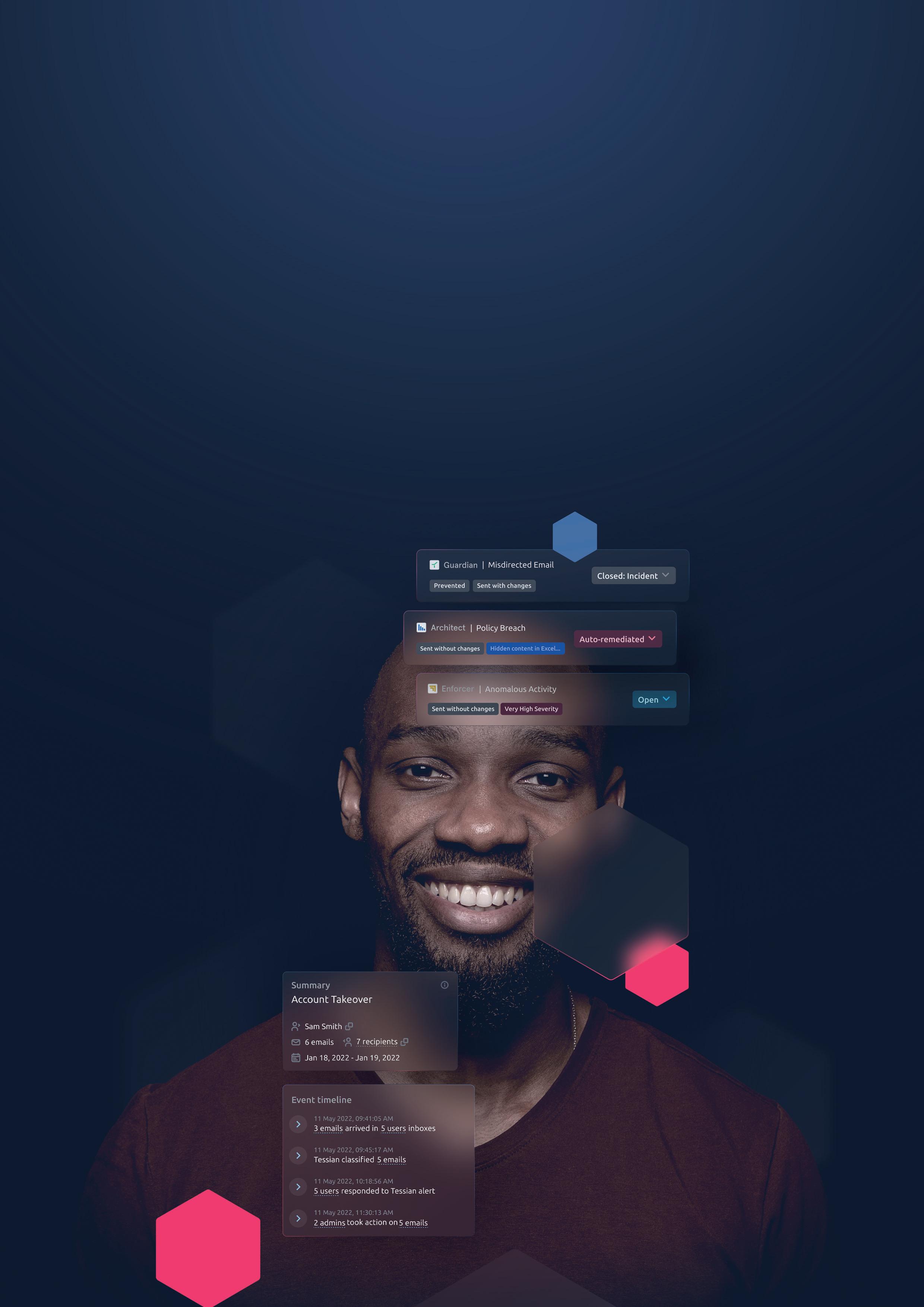
Your data has left the building.
Andy Brown, Product Director, Kocho
Managing the PR crisis – behind the scenes of cyber-attack
Chris Gilmour, Co-founder, Tigerbond
MFA - it’s not a silver bullet
Drew Perry, Tiberium
The Queue (cybersecurity edition): how mentoring gets the queue of cybersecurity talent moving to reduce your organisations’ risk
Michala Liavaag, MD | CISO advisor | vCISO | Information Governance & Cybersecurity Consultant, Cybility Consulting Ltd
We believe that cyber security should cover you from all angles, all the time It’s why Darktrace detects threats, responds to them, and helps proactively prevent them And it’s all powered by our industry-first Cyber AI Loop — which uses Self-Learning AI to constantly optimize your state of security.

11:0011:30
11:4512:15
12:3013:00
14:0014:30
14:4515:15
15:3016:00
16:1516:45
11:0011:30
11:4512:15
12:3013:00
14:0014:30
Sponsored by
Approaching OT Security with Self-Learning AI
Gabriel Seemungal, Senior Cyber Analyst and ICS Specialist, Darktrace
Shut The Front Door
Kurt Johnson, VP of Strategy & Business Development, Beyond Identity
Role of IAM and Log forensics in thwarting insider threats
Vivin Sathyan, Senior technology consultant, ManageEngine
The True Threat to Identity by Modern Attackers
John Spencer, Crowdstrike
Why SOCs Fail
Brad Freeman, Director of Technology, SenseOn
Pain, Policy and Pentesting: Connecting Penetration Testing to Business Value
Sam Kirkman, Director of EMEA Services, NetSPI
Is it Time for AI to Drive our Cyber Defenses?
Ronnen Brunner, SVP of International Sales, IRONSCALES
Enhancing Cyber Investigations with Maltego
Vusat Baghirov, Sales Development Rep, Maltego Technologies
Must be this tall to ride: A story of application security minimums
Chris John Riley, Senior Security Engineer and Tech Lead, Google Switzerland
Attack Paths: Confidently know your riskier entry points
Jennifer Cox, Security Engineering Manager, Tenable Network
A modern-age approach, to modern-age threats
Ryan Pullen, Director of Cyber Security, Stripe OLT










/ SESSION TRACEABILITY
/ PASSWORD PROTECTION
/ STRONG AUTHENTICATION
/ SECURE REMOTE ACCESS


/ LEAST PRIVILEGE MANAGEMENT
VISIT US ON STAND A25


Get better security effectiveness for your organisation with the Arctic Wolf ® Platform and Concierge Security ® Team
Expert security operations center
Concierge Security™ engineers and analysts act as an extension of your team
24x7 eyes-on-glass monitoring through Arctic Wolf ™

Managed Detection and Response
Vulnerability management with Arctic Wolf ™ Managed Risk
We’re here to help. Get in touch to schedule an introductory call with one of our team members and learn more about how Arctic Wolf can benefit your organisation.
arcticwolf.com/uk
END CYBER RISK