We are thrilled to extend a warm welcome to you this April at Olympia London.
On behalf of the entire team, I would like to welcome you to the second-ever UK Cyber Week.
Cybersecurity is a crucial concern for every organisation in the private, public, and third sectors. The threat landscape is constantly evolving, with the number and types of threats growing every week. There are some organisations who run dedicated cyber security teams whilst there are others who rely on their IT departments or outsource their cyber needs to a third party Wherever the security in your organisation comes from there is one thing we can all agree on keeping up to date with everything is very difficult.
UK Cyber Week is on a mission to help level up cyber security knowledge for everyone – the cyber pros, the IT team and business leadership We have built an event with the aim to provide a superior content program which has something for everyone. And we welcome everyone no matter what your technical understanding, there is something at UK Cyber Week for you.
We cover everything from ransomware to cloud security as well as security culture, wellbeing and diversity This year we ’ re hosting some incredible cyber researchers who haven’t spoken in the UK before as well as the cyber rockstars who are always fascinating to listen to. We hope you come to UK Cyber Week to learn from our speakers, get inspired by our show floor full of cool tech suppliers and stay and network with the great and the good from the cyber community
And of course you are invited to the Cyber House Party which takes place at the Cybar from 5pm to 9pm on Wednesday you can donate here: https://bit.ly/3JE8
We are very proud of UK Cyber Week an your visit.
Bradley Maule-ffinch Managing Director

2|SEC Limited
Meet us on Stand D14
Appcheck
AppCheck is a Complete Security Testing Solution that provides up to the minute vulnerability coverage for your entire estate.
APH10
We help software developers prioritise security risks based on actual business impact so that they focus on what matters most.
Arco Cyber Ltd
Arco Cyber, an agentless data fabric, transforms cyber risk management by integrating threat data with compliance and KPIs, turning cyber data into actionable insights for effective transformation
Bob’s Business
Bob’s Business is the cybersecurity culture company. They help every organisation, big or small, to develop and embed a cybersecurity culture that protects their data.
Censornet
Headquartered in an innovation hub in Basingstoke, UK, Censornet gives midmarket organisations the confidence and control of enterprise-grade cyber protection. Its Autonomous Integrated Cloud Security platform integrates attack intel across email, web, and cloud to ensure cyber defences react at lightning speed
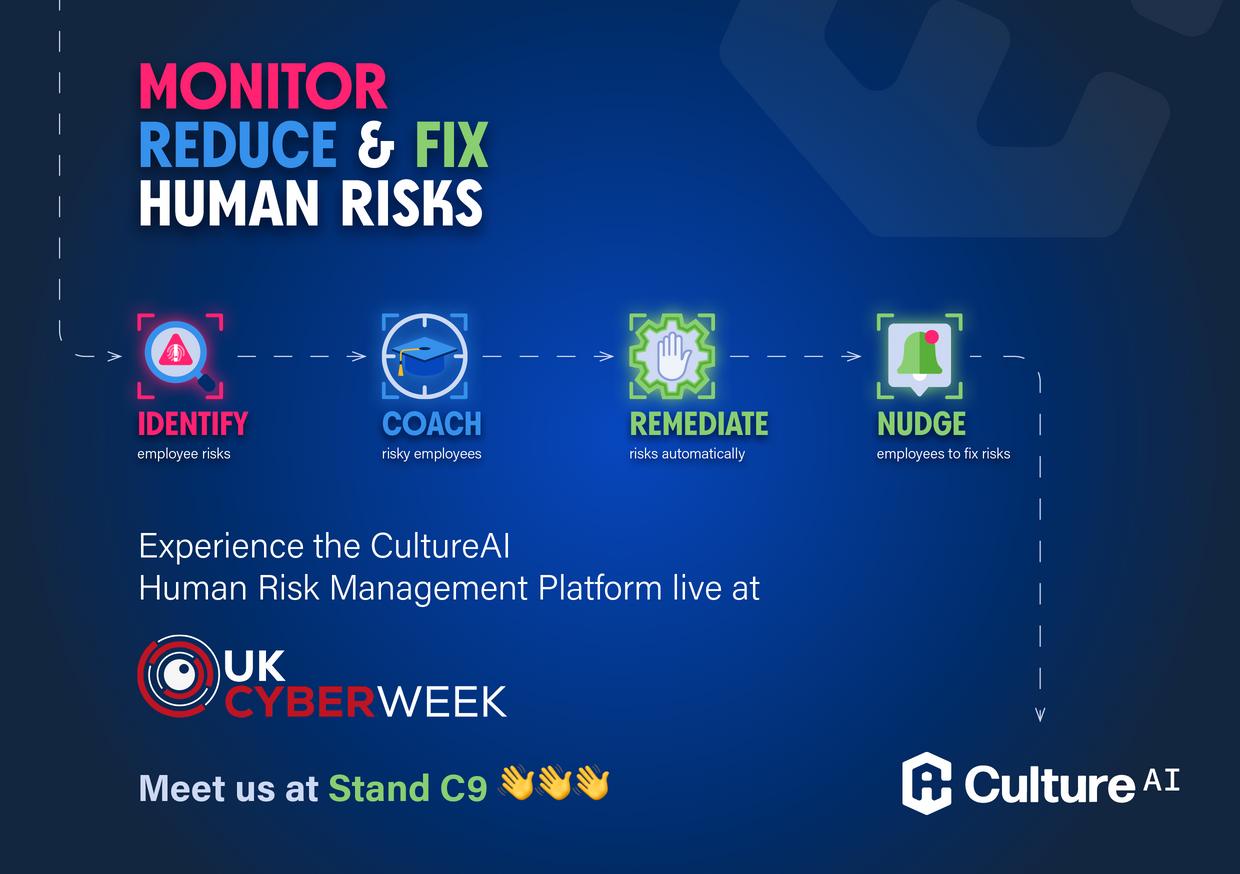
CultureAI
CultureAI’s Human Risk Management
Platform empowers you to identify security risks, educate employees in real time, and nudge employees to make immediate fixes
Cyber Chain Alliance
We are a boutique Cyber Security integration partner. Our amazing people are at the heart of everything we do - this ensures you get a unique service, excellent customer care and an outcome that gives you value.
Cyber Griffin
Meet us on Stand G1
Cyber Protect Team
Come and meet members of the team and see some of our gamified learning exercises.
Cyber Security Jobsite
Meet us on Stand D1
Cyber CX
CyberCX is a leading provider of professional cyber security and cloud services across the United Kingdom, United States, Australia and New Zealand With a workforce of over 1,300 professionals, we are a trusted partner to private and public sector organisations helping our customers confidently manage cyber risk, respond to incidents and build resilience in an increasingly complex and challenging threat environment.
CyberProof
Journey to the cloud, while transforming your business with CyberProof, a UST Company. In an era of cybersecurity uncertainty, we challenge the status quo on how to deliver effective security operations for your business.
Cytix is a continuous run-time testing platform for enterprise businesses that turns event data into dynamic testing actions. Resulting in truly continuous security without wasted time and spend
It solves the challenge of determining when, where and how to test, automatically. Driven by an intelligence engine, testing orchestration happens from within the Cytix platform itself, resulting in dramatically improved Mean Time to Detection (MTTD).
Crowdstrike
CrowdStrike (Nasdaq: CRWD), a global cybersecurity leader, has redefined modern security with the world’s most advanced cloud-native platform for protecting critical areas of enterprise risk endpoints and cloud workloads, identity and data.
Powered by the CrowdStrike Security Cloud and world-class AI, the CrowdStrike Falcon® platform leverages real-time indicators of attack, threat intelligence, evolving adversary tradecraft and enriched telemetry from across the enterprise to deliver hyper-accurate detections, automated protection and remediation, elite threat hunting and prioritized observability of vulnerabilities.
DigitalXRAID
DigitalXRAID is an award-winning managed security services provider with 25+ years ’ experience, dedicated to providing our clients with state-of-theart cyber security solutions We specialise in Vulnerability Management, Threat Intelligence, Information Security, PCI-DSS, Penetration Testing, Managed Security Services, Security Consultancy, and offer a fully managed Security Operations Centre (SOC) for your complete cyber security protection.
Exponential-e Group
SECURING UK ENTERPRISES AND PUBLIC SECTOR ORGANISATIONS
Forescoute Technologies
Meet us on Stand D8
HCL Software
HCLSoftware develops, markets, sells, and supports product families in the areas ofDigital Transformation, Data, Analytics & Insights, AI & Automation and Enterprise Security platforms
Hello Fresh
Home Delivery Food Subscription
We're building a Threat Intelligence platform that's driven by a global network of thousands of CVE Honeypots, capturing everything, from the tactics, procedures, tools and payloads used by attackers in the wild. Solving the industry’s problem of stale, unreliable and complex intelligence.
We're bridging the gap for analysts to better understand attacks, with clear attack chain visuals articulating how to spot an attack in the wild, and what related logs, alerts and activity look like, better informing detection rule creation and risk-based decisions
Come have a chat with us to learn more and join our free beta program!
IBM is the global leader in business transformation through an open hybrid cloud platform and AI, serving clients in more than 170 countries around the world. With 28 consecutive years of patent leadership, IBM is committed to being a responsible innovator and a force for good in the world
Intel 471 arms enterprises and government agencies to win the cybersecurity war using real-time insights from the cyber underground. Organizations leverage our TITAN platform to gain real-time monitoring of threats to protect their organization from costly, debilitating security breaches and cyber incidents. We enable security and intelligence professionals to solve realworld cyber use cases including attack surface protection, third-party risk management, security operations, brand protection, fraud and more. Our threat intelligence solutions empower enterprises and agencies to identify, prioritize, and prevent attacks. Learn more at www intel471 com
At Kivu, we don’t just understand threats; we specialise in identifying, containing, and mitigating cyber threats. With deep knowledge of threat actors, their evolving tactics, and the dynamic threat landscape, we are uniquely qualified to strengthen your defenses against sophisticated cyberattacks.
Step into the world of cyber espionage and infiltration at the Covert Operations Zone, proudly hosted by KSEC during UK Cyber Week Nestled within the "Cover Ops Zone" lies an array of challenges designed to test and enhance your covert skills.
Embark on a journey through the renowned hacker hardware store, where cutting-edge gadgets and tools await to empower your Red Teamers. From state-of-the-art penetration testing devices to covert ops equipment, discover the arsenal of the modern OffSec operative.
Maltego is the world’s most used cyber investigation platform It has empowered over one million investigations worldwide since 2008.
Maltego empowers investigators worldwide to accelerate and simplify their investigations through link analysis It is the all-in-one tool with easy data integration in a single interface, powerful visualization and collaborative capabilities to quickly zero in on relevant information Maltego is used by a broad audience, from cyber security professionals and pen testers to forensic investigators, investigative journalists, and market researchers, to make the world a safer place.
Massage the Senses creates pit stops for events and festivals for when you are feeling tired to help you rejuvenate throughout the day Our fully qualified therapists can specifically work on one area of concern and this is done over clothes with no oil.
MOBSTR (mobile application security testing and ratings) is a next generation mobile security assessment and ratings SaaS platform that addresses Governance, Risk Management and Compliance (GRC) challenges in mobile apps Cyber Security.
The industry-endorsed climate action platform built for your business
Meet us on Stand E6-3
Orca Security
Orca Security provides instant-on security and compliance for AWS, Azure, and GCP without the gaps in coverage, alert fatigue, and operational costs of agents or sidecars Simplify cloud security operations with a single CNAPP platform for workload and data protection, cloud security posture management, vulnerability management, and compliance Orca Security prioritizes risk based on the severity of the security issue, its accessibility, and business impact. This helps you focus on the critical alerts that matter most
OSINT Industries
Meet us on Stand 16-1
Pentiq
Pentiq are a UK based Cyber Security company offering a comprehensive portfolio specialising in innovative solutions for Penetration Testing, Training, Compliance, Consulting, and Managed Services. Our experienced consultants are considered experts and thought leaders, accredited by CREST (Council of Registered Ethical Security Testers), Offensive Security, or the IASME Consortium.
Plextrac
PlexTrac is The Premier Cybersecurity Reporting and Collaboration Platform that makes security data aggregation, red and blue team reporting, purple team collaboration, and remediation tracking more effective and efficient so security teams can become more proactive and drastically improve their security posture.
Repel Cyber Security
Meet us on Stand H8
SecAlliance
SecAlliance delivers cyber threat intelligence services to banks, central banks, financial market infrastructures, governmental and EU agencies, international organisations, and critical national infrastructure operators (telco, power grid, transport). We help these organisations and their ecosystems to strengthen their cyber resilience and make the right decisions
Secarma
Secarma is an independent cybersecurity consultancy and penetration testing house that specialises in advising, certifying and testing the strength of your organisation’s security posture. Our specialists have the skills and experience needed to identify vulnerabilities within your systems before these undetected issues can be exploited by cyber-criminals We’re here to help you take your organisation to the next level of security maturity.
Seidea
Meet us on Stand C2
SentinelOne
SentinelOne (NYSE:S) is pioneering autonomous cybersecurity to prevent, detect, and respond to cyber attacks at faster speed, greater scale, and higher accuracy than human-powered technology alone. The Singularity Platform empowers enterprises to achieve greater visibility of their dynamic attack surfaces, including endpoints, cloud workloads, containers, identity, and mobile & networkconnected devices, and take action in real time with AI-powered automation and cross-platform correlation.
Sentrium Security
Meet us on Stand D6-3
SonicWall is a cybersecurity forerunner with more than 30 years of expertise and is recognized as a leading partnerfirst company. With the ability to build, scale and manage security across the cloud, hybrid and traditional environments in real-time, SonicWall provides seamless protection against the most evasive cyberattacks across endless exposure points for increasingly remote, mobile and cloud-enabled users. With its own threat research center, SonicWall can quickly and economically provide purpose-built security solutions to enable any organization enterprise, government agencies and SMBs around the world For more information, visit www.sonicwall.com
Stellar Cyber’s Open XDR platform delivers comprehensive, unified security without complexity, empowering lean security teams of any skill to secure their environments successfully. With Stellar Cyber, organizations reduce risk with early and precise identification and remediation of threats while slashing costs, retaining investments in existing tools, and improving analyst productivity The company is based in Silicon Valley. For more information, contact https://stellarcyber.ai.
Stream Security pioneers Cloud Twin, a real-time simulation model that captures all cloud activities and dependencies. It is the only real-time model fully aware of posture, behavior, and business impacts to help security teams mitigate cloud threats before they escalate.
Stott and May are a professional search firm with a passion for helping leaders achieve complete confidence that they have hired the right talent, first time, in fiercely competitive markets
We believe you should never have to make the choice between quality of candidate and time to hire. As a result, our business has been founded on the principle of offering a premier standard of search service delivered in vastly accelerated timescales, that our competition simply cannot match. Because after all this is about more than just recruitment, it’s about turning your business vision into reality
techUK
Meet us on Stand C1
ThinkCyber deliver measurable secure behaviour change for their customers, empowering people to protect themselves against cyber threats. Their multi-award winning Redflags® Real-time Security Awareness software applies behavioural and learning science theory to deliver context-sensitive, justin-time security guidance. For example, when users are about to click links, visit certain web pages, enter their username into a web page, handle attachments, etc.
ThreatLocker® improves enterprise-level server and endpoint security with zero trust controls, including Allowlisting, Ringfencing™, Elevation, Storage, Network Control, Configuration Management, and Operational Alert solutions
Women in Tech & Cyber Hub (WiTCH) is bringing magic to cyber security, where we look to break down barriers for women in industry.
YUDU Meet us on Stand C7

Simply scan the QR code using your phone or click on the buttons for either Apple Store or Google Store.
Log in with the email address you've registered with to attend UK Cyber Week.
Password: ucw2024



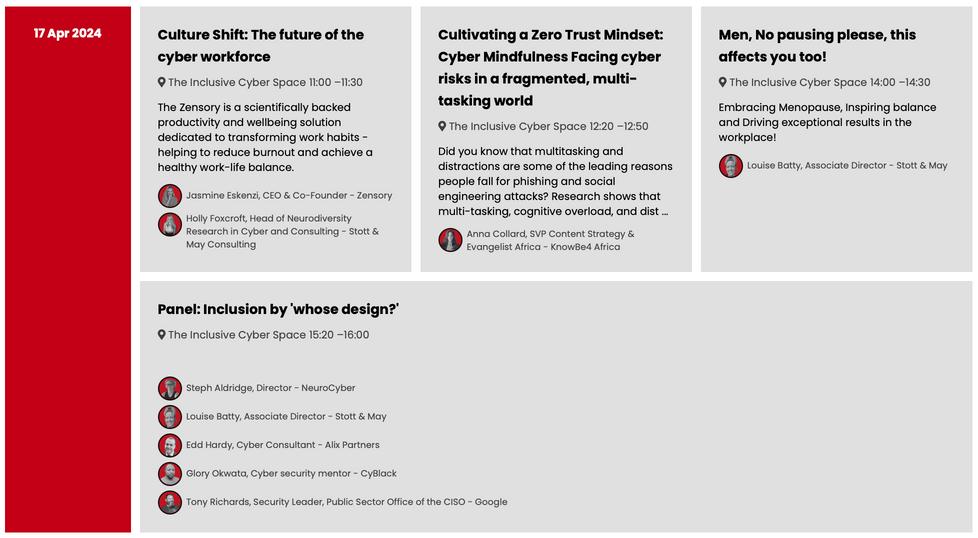
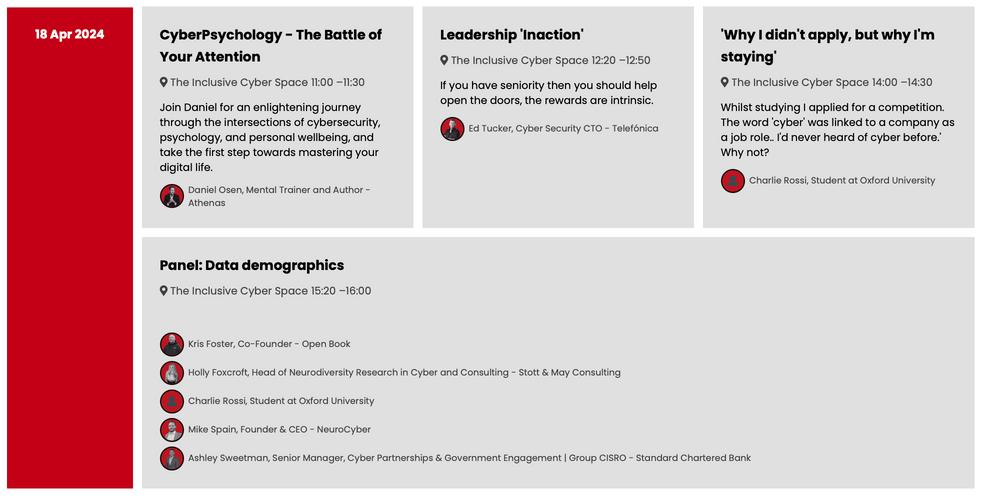
In partnership with NeuroCyber
Across two immersive days, The Inclusive Cyber Space is designed to provide actionable insights for implementation at work, engaging activities for selfknowledge, and opportunities to hear from industry leaders. Drawing from lived experiences and research, the focus is on the vital link between cultivating personal resilience and bolstering overall business security governance.
End the day with The Cyber House Party which kicks off at 5 30pm on Wednesday 17 April 2024 with DJs, dancing, drinking and networking until late.
Meet the industry whilst giving back, supporting this not-for-profit and NSPCC
Scan the QR code to donate:


Meet peers from across the cyber and IT sectors at the 'Cy-Bar' open all day for networking and meetings.
Continue the conversation after the conference sessions at the networking zones outside the Culture and Prevention Theatres.
Explore Targeted Connections: Join Dedicated Meet-ups Alongside General Networking
Discover specialised meet-ups tailored for more focused networking in addition to our general networking areas
Review the list below and secure your spot by registering. Ensure you've registered for the main event before signing up for these exclusive meetups




KEYNOTE THEATRE - 17th April 2024
KEYNOTE THEATRE - 18th April 2024
11:00 - 11:20
Nudges: From Risk to Fix in a Single Click
James Moore - Culture AI
13:20 - 13:40
Securing Tomorrow’s Software: Emerging trends in Application Security, AI Generated Code and the Software Supply Chain
Matthew Brady - Synopsys
15:20 - 15:40
Risk Minimisation: Managing the Legal and Regulatory Risks Posed by a Major Cyber Security Incident
Simon W Davis - Womble Bond Dickinson (UK) LLP
Jess Mant - Womble Bond Dickinson (UK) LLP
11:30 - 11:50
From Quantum to AI: Redefining Cybersecurity for the Next Decade
Sam Hector - IBM
14:30 - 14:50
In the Moment Nudges – What? How? Applying Nudge Theory to Awareness
11:30 - 11:50
Complexity of Automated Web App Scanning
Nick Blundell - Appcheck
14:00 - 14:20
Know Your Enemy: The Power of Cyber Intelligence
James Rees CISM - Razorthorn Security
15:50 - 16:10
How to Demonstrate the Value of Cybersecurity Awareness to Stakeholders
Neil Frost - Bob’s Business
12:50 - 13:10
How to Communicate Cybersecurity
Alice Violet - Alice Violet Creative
15:20 - 15:40
Threat-Informed Defence. What is it and how to Implement it?
Ronan Lavelle - Validato 1
Tim Ward - Think Cyber Security Ltd
12:20 - 12:40
From 'Awareness’ to ‘Measurable Behaviour Change’; A Behavioural Science Perspective
Tim Ward - Think Cyber Security Ltd
14:30 - 14:50
Building a Business Aligned Strategy, Security Culture and Diverse Security Organisation
Tim Grieveson - Bitsight
16:20 - 16:40
Brewing the Kubernetes Storm Center: Open Source Threat Intelligence for the Cloud Native Ecosystem
Dr James CallaghanControlplane
14:00 - 14:20
Cyber Security Support for SMEs: Bringing Clarity or Confusion?
Steven Furnell - University of Nottingham
15:10 - 16:10
Unlocking Best Practices for SMEs Entering the Cyber World
Annabel Berry - UKC3
11:00 - 11:20
Balancing User Experience with Cloud Security
Chalire Milton - Censornet
12:50 - 13:10
Ransomware – Top Technical Actions you can do to Reduce the Risk and Impact to your Business
Terry Mee - Kivu Consulting
14:30 - 14:50
How to be Successful with SecOps in a Downturn
Martin Panter - Stellar Cyber
16:20 - 16:40
Out of the Frying Pan Into the Cloud: A Red Teamer's View of Your Cloud Estate
Max Corbridge PCSP - JUMPSEC
11:00 - 11:20
Can AI Help the Year of Cyber Insecurity?
Gareth Lockwood - Censornet
12:50 - 13:10
Brought to you be Exponential-e
11:30 - 11:50
Building Cyber Resilience: Prioritization In A Rapidly Shifting Threat Landscape
Katie Ralph - SonicWall
13:20 - 13:50
Party Crashers: The Unconventional Geniuses Shaping the Cyber Industry
Kunjal Tanna - LT Harper
Laure Lydon - Flo Health
Rebekah Makinde - Reliance Cyber
Jon Niccolls - Lodstone Security
15:20 - 15:40
How to Manage Governance, Risk and Compliance for Mobile App Cybersecurity in 2024
Maxim Frolov - Mobstr.io
James Hitchcock - Mobstr.io
15:20 - 15:40
The Weakest Link: Safeguarding Supply Chains from Third-Party Threats
Stuart Barnett - Orpheus Cyber
11:30 - 11:50
Complexity of Automated Web App Scanning
Nick Blundell - Appcheck
14:00 - 14:20
Mitigating Risk in a Dynamic Threat Landscape: The Imperative of Continuous threat Management for Corporate Resilience
Jaimon Thomas - CyberProof
12:10 - 12:40
Who is Behind the Ransomware Negotiation?
Dave Ross - Intel 471
14:00 - 14:20
Fortifying Digital Ecosystems: Navigating Application Security Posture Management and Supply
Chain Security
Raveesh Dwivedi - HCL Software
15:50 - 16:10
Enhancing Cyber Investigations with Maltego CTI Package
Vusat Boghirov - Maltego Technologies
12:20 - 12:40
Simplifying Security
Tim Holman - 2-sec
14:30 - 14:50
Mixology, Multidimensional Information Spaces, and Risk Management
James Bore MSc CSyP - Bores
Chris Bores - Bores
11:00 - 11:20
From the Keyboard to the Catastrophe: Targeting OT Infrastructure for National Disruption
Ian Thornton - CYJAX
12:50 - 13:10
Cracking the Code: Hijacking Phone-as-Key Systems in Vehicles via BLE DoS Exploits
Kevin Mitchell - ETAS
14:30 - 14:50
The Biggest Cloud Security Threats to Watch Out for in 2024
Bar Kaduri - Orca Security
16:00 - 16:40
Zero Click iOS Exploit – Deepdive into Operation Triangulation
Marco Preuss - Kaspersky
11:00 - 11:20
Getting the Board Onboard with Information Security
Jennifer Williams - Secarma Ltd
14:00 - 14:20
Back to the Future: 35 Years of OT Attacks and Beyond
Ric Derbyshire - Orange Cyberdefense
11:30 - 11:50
Information Security
Management: Considerations for the future
Luke Griffiths - Secarma Ltd
13:20 - 13:40
Brought to you be Exponential-e
12:20 - 12:40
The Security Outcomes Canvas: A Tool for Aligning Security and Business Outcomes
Christine Bejerasco - WithSecure
14:00 - 14:20
Achieving Preemptive Protection by Leveraging Curated Threat Intelligence
Fergal Lyons - Centripetal
15:00 - 15:20
Anatomy of a Cloud Threat: Unveiling SCARLETEEL Attack
Alberto Pellitteri - Sysdig
15:30 - 15:50
Cyber Resilience, do you know what’s lurking in your data?
Ian Shave - IBM
12:20 - 12:40
Why Cloud Teams Need to Think Like An Attacker
Or Shoshani - Stream Security
15:20 - 15:40
Brought to you by Telefónica
12:50 - 13:10
The Cyber Resilience Architect
Anton Angione
15:50 - 16:10
Securing the Cloud Workforce: Tips to Attract and Retain Top Talent
Dean Charlton - Scott and May