
















Ghelamco is a family-owned international real estate investor and developer operating in Belgium, Cyprus, France, Poland and the UK. Founded in 1985 and with assets now totaling over €2.6 billion , the company has an impressive track-record building spectacular, high-quality, BREEAM-certified residential and office buildings particularly in Poland, where it has been instrumental in establishing Wola, western Warsaw’s new thriving business district.
Ghelamco Poland has built various skyscrapers in the area: the 220m high Warsaw Spire,
with hyperboloid glass facade and 109,000m2 of space, along with The Warsaw HUB complex. Completed in 2020, this features two 130m towers – purchased by Google for €583 million – along with a third building, home to two IHG Group hotels – a Crowne Plaza and Holiday Inn Express – as well as a conference center.

Warsaw UNIT is Ghelamco’s third flagship project which opened in 2021. Standing at 202m, it combines office and retail space, and is one of the most technologically advanced green buildings in central Europe. It uses 30% less energy compared with similar developments. A fourth
skyscraper project called The Bridge is underway and expected to open in early 2025.
The buildings are multi-tenanted by blue-chip corporate clients. To support this, Ghelamco’s physical access control strategy focused on selecting solutions to guarantee secure entrance while offering maximum flexibility and future proof upgradeability.
“We prepare the shell and core of each building, provide access to these common areas via speed gate turnstiles, lifts and the car parks, and then support clients with
bespoke fit outs depending on their specific needs. This means the base building access control technology we use must work with numerous other systems – which may even include other access control products that clients choose to install themselves. Easy integration, updating and management over time was therefore, key,” Łukasz Stępień, Ghelamco Poland’s project manager, explains.
Ghelamco is also progressively deploying smartphone-based access control throughout its portfolio – a process that started with its office in Warsaw Spire and was next fully implemented in The Warsaw HUB.

“Innovation is our hallmark, so we want to use the latest technology on projects. Many of our tenants want mobile access today. Others, however, still prefer physical cards, so selecting a vendor that supports both in tandem was an imperative,” Michał Nitychoruk, Ghelamco Poland’s communications manager, says.
Furthermore, Ghelamco wanted to integrate mobile access with an intuitive smart building software platform and app to augment and add value to how users interact with each building and enable a productive and seamless experience. The requirement was to manage not only physical access control, but offer an easy-to-use way to link lift and parking systems, closed-circuit TV, visitor management and – in the future – other building management
systems and sensors that monitor air and water quality, for example.
In Poland, HID has become Ghelamco’s preferred partner of choice for mobile and physical access control across its prestigious sites, with the developer standardizing on its solutions.
“HID was chosen because it is the best-known physical access control company in the world. This gives us the confidence – a warranty if you like – that our tenants will accept their solutions when they move in. They trust HID because it is the market leader,” Stępień says.
A combination of mobile-enabled HID iCLASS SE R10 and R40 smart card readers have been installed throughout The Warsaw HUB and Warsaw UNIT. Specialist subcontractor GEO-KAT fitted 1,400 readers in HUB, with Tech Lab working in UNIT to implement 1,200 devices.
In Warsaw Spire – while physical cards are still predominately used – HID® iCLASS® SE™ readers with Bluetooth® and NFC modules have now been fitted for testing to support a phased transition to mobile access in Ghelamco premises. Moreover, mobile-ready HID Signo Readers will be deployed in the new Bridge skyscraper leveraging Seos® as its underlying credential technology.
“We love using smart phones for access as they’re just so flexible. It’s much easier to issue, revoke
and manage credentials not only for us, but our facility management partners, tenants and owners, too,” Stępień adds.
In addition, feature-rich enterprise applications have been implemented from Signal OS, a Polish proptech software development company based in Warsaw.
Utilizing the Google Cloud Platform™ at the backend, Signal OS provides a wide array of functionalities within three key applications and a solution called ‘Edge’ which is a middleware used to integrate all the building systems.
Supporting stringent GDPR rules, Signal OS’ ‘Wayin’ application automates mobile access credential delivery with privacy control in mind. The system supports both Android and iOS devices. ‘Wayin’ is connected via an API to HID Origo - which is cloud-based - to provide HID Mobile Access credentials.
The main advantage of ‘Wayin’ is a self-management panel for the tenants to then manage access privileges and credentials of employees. “Wayin is a crucially important component of our solution as it sits on top of the building and the tenant’s own access control systems to consolidate it, so there is one holistic view per building and between buildings at the same time” Tomasz Felczyk, Signal OS’ chief executive officer explains. “It then manages the privacy policies so – if required – tenants can view personal employee data but facility managers
and third-parties only see critical data involving base building security. Each party gets a dedicated panel to manage their own staff and set up badges, rules and access privileges.”
“The Ghelamco buildings are complex and like small cities in terms of the number of occupants. Simply put, using `Wayin` we democratize them so that tenants can use and manage access control themselves and move about more freely and easily,” Felczyk, says.
The ‘Parkiza’ parking application has been installed in both the Warsaw HUB and Warsaw UNIT buildings, with access control linked to it. This allows parking access based on car plate recognition technology, smartphones running HID Mobile Access or physical cards. The system has a complex rules engine to manage nearly 400 car plates in UNIT and 1,000 in HUB given the high ratio of users per parking place.
In addition, the ‘Visitor’ module provides a secure web-based guest invitation system for employees and receptionists.
To date, 9,000 active users are registered in the Signal OS system in The Warsaw HUB and 4,500 in Warsaw UNIT, with about half using HID Mobile Access in both buildings. Given the number of people, two-factor authentication is used to automatically onboard users

based on their corporate domain and email addresses. This has avoided unnecessary paperwork and queuing.
The benefits of using HID Mobile Access in combination with Signal OS have been immediate. It has enabled Ghelamco to attract new clients who want to lease space in efficient and green buildings. Ghelamco is also saving money by not having to issue PVC access cards, which are commonly lost and then create a security risk.
Visitor management has also been simplified. In Warsaw Spire, for example, 10% of all cards issued to visitors per month were never returned. This has been addressed as the QR code functionality within the ‘Visitor’ application is now used to invite people for their meetings. QR codes are emailed in advance so access to buildings and lifts can now be done remotely without time-consuming involvement from office or facility managers. As guests arrive and the QR code is scanned, the person they are meeting receives a notification alert. “It is the flexibility of mobile access combined with Signal OS, which everyone benefits from,” Nitychoruk adds.
As the first developer in Poland to join the Science Based Target Initiatives, Ghelamco has set targets
to be a zero-emission company by 2025 and is aiming to have its office buildings powered from renewable sources by then. To support this, the firm announced it is building its first solar farm – capable of generating 10 megawatts – which will power Warsaw UNIT and other sites.
The shift to mobile access control directly supports this ambitious ESG policy as it removes waste and carbon emissions associated with producing and replacing PVC access cards. Smartphone use is ubiquitous today, so having the mobile credential on a device makes logical sense.
“HID is focused on sustainability. Features in the HID door readers like Intelligent Power Mode mean they go into standby mode when not used. Substantial power savings can be gained when you consider the numbers of them installed in our buildings multiplied by the 15-to-20year life span of each,” Sępień adds.
Looking to the future, Ghelamco is looking at how best to extend and augment the access control approach in its estate by adding support for digital wallets to enhance speed of access and user convenience.
For further information visit www.hidglobal.com/solutions/ mobile-access-solutions
















With the new SX800, Fujinon combines both in one for the first time: camera and lens. For long range surveillance at the highest level with 40x optical magnification and constantly sharp images. www.fujifilm.eu/fujinon. Fujinon. To see more is to know more.





Connectivity and convenience are key themes in the latest edition of the biennial Wireless Access Control Report.

Using data gathered from a new survey of 400 security, facilities management and IT professionals, the Wireless Access Control Report 2023 identifies trends which will shape this market and customers’ experience over the coming years. The Report was published by IFSEC Insider and includes expert contributions from analysts Omdia and Digital Access Solutions leaders at ASSA ABLOY Opening Solutions.
“We are delighted once again to offer fresh insights into the ongoing digitalization of access,” says Richard Sharp, Director, Product Line Management, Digital Access Solutions at ASSA ABLOY Opening Solutions. “A particular focus of the 2023 Report is access control’s potential impact on the wider business — as an enabler for business intelligence, cost efficiency and of course better sustainability performance.”
“The Report highlights ways for security departments and consultants to contribute directly to business strategy — and indeed, reveals data which makes it clear this process should happen sooner rather than later.”
Convenience, connectivity and a seat at the table for forward-thinking security managers Convenience has triumphed. End-users prize flexible, scalable technologies which are easy to use and to integrate with building systems. In the Report survey, 93% of respondents agreed that compatible, integrationready standards are important when choosing or recommending access control.
“Security is often assumed these days,” adds Sharp.
“The role of access control is now to help the business work smarter, saving time and costs in the process.”
One key technology for convenience is the smartphone. Data from the Report highlights fast-growing deployment of mobile credentials in organizations of almost every size and type.
Alongside convenience, the Report reveals an urgent business case for connected intelligence — within and across organizational functions — including by combining cyber and physical security under one internal roof.
For example, only 12% of survey respondents said they were fully prepared for the implications of forthcoming European cyber-security legislation. “The cyber-security knowledge gap in ‘traditional’ security and facilities management departments is real,” says Sharp. “As the Report highlights, combination cyber–physical security attacks are on the rise. Now is a good time to upgrade both systems and knowledge.”
The current economic climate has brought increased focus on cost and workflow efficiencies to almost every organization, of all sizes and types. This presents an opportunity for security managers and directors to show how they can contribute to business success.
“Data gathered from security systems can be used in many other areas of the business, such as managing the hybrid working patterns of the staff and improving energy efficiency by only heating and/or lighting areas of the building which are occupied,” notes the Report.
“Security can escape its silo,” Sharp adds. “Indeed, it must, if organizations are to thrive.”
To download your free copy, visit our website
A new market report analyses how wireless access control is evolving — and how security managers can benefit

MEMS (microelectromechanical systems) sensors really are multitalented. These tiny “all-rounders” provide convenience, safety, and security in everyday life. They can detect mechanical, magnetic, and even chemical changes reliably and with great precision, and convert these into electrical signals. This innovative technology is now also finding its way into security technology. Thanks to the MEMS sensors used in them for the first time, the Bosch Commercial Series (Gen2) motion detectors recently launched in the EMEA region boast even better catch performance and false-alarm immunity. They also deliver all the triedand-tested benefits of TriTech detectors, which have a detection range of up to 15 meters and are used inside commercial premises with a moderate to high security risk, such as office and factory buildings, banks, and retail outlets.
The MEMS sensors Bosch is using in the Commercial Series (Gen2) motion detectors are ultra-small high-performance acceleration sensors like those used in smartphones, for example. “With even better impact and vibration compensation and no mechanical contacts, these sensors offer maximum false-alarm immunity,” explains James Mottorn, a sensor expert and product manager at Bosch Building Technologies. Since there is therefore also no need for a mounting screw for the tamper contact, the anti-mask version now takes even less time to install. What’s more, the MEMS sensors make it even easier to spot attempted tampering at the place of installation, whether someone is trying to pull the detector off the wall or remove brackets and swivel joints. As part of the update, Bosch has also further enhanced the detector’s RF (radio frequency) immunity. In the new devices, this is now up to 6 GHz, providing the motion detectors with even better protection from interference caused by Wi-Fi
routers, which typically operate in this frequency range. Another plus point of the new generation is that the integrated EOL resistors can now be selected more quickly during installation because the jumpers have been replaced by user-friendly switches. Last but not least, the innovation boasts further optimized anti-mask monitoring for the sensors, which is now more sensitive to attempts to block the sensors using paper or spray paint, for example. Likewise, the improved anti-mask monitoring can also identify objects such as advertising banners that have been inadvertently placed in front of the detector.
The new Commercial Series (Gen2) motion detectors share the established benefits of TriTech technology – a combination of PIR and microwave Doppler radar technology plus advanced signal processing. After all, especially in a setting with an elevated security risk, any movement in an area needs to be detected quickly and reliably without triggering any false alarms – even in challenging environments such as locations with strong air currents, moving objects, and difficult light or temperature conditions. Like all Bosch motion detectors, the Commercial Series (Gen2) models are easy to install, which cuts installation costs. They are also built to last. Bosch motion detectors come with a five-year guarantee as standard. In the EMEA region, TriTech detectors even come with an eight-year guarantee.
Bosch is one of the biggest suppliers of MEMS sensors for vehicles and consumer electronics worldwide and has already produced more than 18 billion sensors. For example, it is MEMS sensors that enable fitness trackers to count steps, ensure airbags open at the right moment, and activate brake assistance systems in vehicles. Thanks to these properties, MEMS sensors are also ideal for use in safety applications in buildings
Demand for high-performance video solutions among independent stores warrants greater focus from integrators and distributors
Convenience stores are a valuable “forgotten market” for many systems integrators and installers, justifying greater focus says IDIS, South Korea’s largest in-country surveillance manufacturer.
Although the overall contract value for a single store will be less than for a multi-site retail project, the spending-per-store is often higher, says IDIS - particularly where family-owned businesses are concerned. IDIS estimates there are approximately 100,000 British independent retailers and more than 400,000 across EU member states, with many in need of CCTV upgrades as they look to tackle violence and aggression against staff, customer theft, and fraud.
In the UK alone, the combined annual spend on security among convenience stores – including franchises and buyer groups, as well as independents – was recently estimated at almost £250m (ACS Crime Report 2022). Of this, the highest proportion was spent on security staff. But, outside of big brand supermarketowned stores, most family-run and independent businesses do not employ security officers; for them, video surveillance is the most important investment because it allows staff to multi-task and maintain vigilance.
IDIS cites one recent upgrade at British, family-run suburban store that included 28 of its 5MP IR dome cameras, four 5MP bullet cameras with SD card failover; PoE switches; installation accessories; a 32-channel NVR recorder; two specialist display monitors; and its cost-free video management software (VMS).

Another example – proving that these are not ‘budget’ contracts - is a Belgian family-owned-andmanaged DIY store that deployed a high-performance solution that comprised 20 UHD fisheye cameras
providing complete domain awareness across the store to tackle shrink, and domes covering cash desks to detect fraudulent activity. The owner also wanted car park coverage using a range of bullets and domes, with a view to adopting license plate recognition. With all the cameras connected to a 64-channel NVR, the system is managed by scalable, enterprise-class VMS.
“Our experience in this sector is that while customers want good value, they aren’t looking for cut-price systems,” says James Min, Managing Director, IDIS Europe. “Buyers are typically owner-managers who see video as a key investment for their businesses, and something to be proud of, so they want high-quality equipment that’s quick to install and guaranteed to work well for years, while offering a futureproof infrastructure.”
He adds that, typically, businesses in the sector are also well networked and will share supplier recommendations: “We’re seeing that our systems integrators who do a good job are likely to get maintenance and follow-on contracts, particularly since the vast majority of independent retailers are outside of city centres, and tend to look for a proven, local professional security partner they can trust.”
IDIS says it’s worth more integrators getting to know this market, focusing on their local communities, particularly as store owners often belong to local business groups and associations where they share best practice and recommendations.
“IDIS is working systems integrators to give these practised video users exactly what they want – highdefinition coverage of their complete stores, including the most vulnerable locations at the ends of aisles, and the ability to track suspect movements seamlessly in real time,” adds James Min.
For more information go to www.idisglobal.com
Convenience stores willing to invest in higher quality video solutions, says IDIS











Hanwha Vision, the global vision solution provider, recently put its new TNO-7180RLP high-speed camera through its paces at Chambley Grand Est racing track in France, where it successfully identified sports cars being driven at speeds of up to 265kph, even at night.

The camera features Hanwha’s newly launched Road AI solution, which not only captures number plate details (ANPR), but also uses AI video analytics to identify the make, model and colour (MMCR) of detected vehicles, across 70 different automotive brands, 600 models, and 10 colours. The camera features a global shutter for greater accuracy and clarity of captured number plate images and a high frame rate of up to 60fps.
While the solution is designed to detect number plates and the make, model and colour of vehicles travelling at up to 200 kph (125 mph) across two lanes of traffic, in tests conducted on the closed racing circuit, it exceeded expectations by consistently identifying Porsche 911 GT3 and a Ferrari 488 models driven at speeds of up to 265kph (165mph) - not only in daytime but also at night!
The test was held at a recent Hanwha Vision customer event held at the Chambley Grand Est circuit and Planet’air, near Metz. The on-site team set up the camera on the day with ease, using its onboard ANPR Setup Tool to correctly position and angle the camera for number plate capture. Entering the camera height and distance from the centre of the road, they quickly obtained the correct vertical, horizontal and roll angles to use, while a Road AI Setup Wizard tool – part of the Road AI application – confirmed the optimum plate capture area.
Professional racing drivers were then invited to take to the 3.3 kilometre (2.1 mile) track in a range of highperformance cars to see if the system could recognise the cars travelling at speeds well beyond national limits. Capturing information on vehicles being driven at such high speeds presents a challenge for lesser cameras and systems; however, Hanwha Vision’s system worked perfectly, correctly identifying cars travelling at 265 kph (165 mph), equivalent to 74 metres per second!
The ability to search for vehicles by make, model and colour is a great help to investigating teams when looking to find footage of a vehicle involved in an incident.
“Our test confirms that the solution performs even at the very highest of speeds, and this is reassuring for law enforcement officers given that criminals frequently swap the licence number plates on vehicles in order to avoid ANPR identifying them as stolen,” said Mevlut Korkmaz, National Sales Manager at Hanwha Vision France.
“With our Road AI solution and high-speed camera, Police have reliable access to make, model and colour search criteria to cross-reference footage against reports of stolen vehicles”, Mevlut continued.
The camera can identify number plates and vehicle make/models from different regions ‘out of the box’, including Europe and the UK, Canada, the USA, Australia and New Zealand, Vietnam, Indonesia, the Middle East, South Africa, and Russia.
Learn more about the TNO-7180RLP by visiting https://hanwhavision.eu/product
Access control should not stop at doors: In shared spaces, valuables and other personal items deserve the same protection as offices, treatment rooms or server racks. Many access solutions are limited to the door environment. This is where the new Aperio KL100 comes in: It integrates seamlessly with more than 100 access control systems, bringing security to many access points beyond just doors.
Managing the security of additional access points outside a security system increases risk, complexity and workload. The battery-powered Aperio KL100 solves this problem. It secures lockers, cabinets, cupboards, drawers. Almost any small opening quickly becomes an integral part of an access control system.
An Aperio KL100 fitted at these points gives personal valuables, medicines, sensitive documents, retail stock, sports kit and more the security they deserve. It deters unauthorized access and theft.
With two different lengths and several CAM options, the KL100 is a straightforward retrofit solution. It suits almost any locker, cabinet or drawer, whether wooden or metal. Powered by one battery, this wireless lock consumes very little power — it only “wakes up” when a credential is presented — and needs no specialist maintenance.
In line with every device in the Aperio range of battery-powered locks, this protection does not require the hassle or inflexibility of physical keys.
An Aperio KL100 can be operated with mobile keys via Bluetooth Low Energy and NFC, as well as smartcards and fobs using all major RFID technologies. For added user convenience, the device accepts multiple credential technologies simultaneously, in parallel, so
security managers can roll out mobile keys at their own pace.
Easy hardware integration for greater efficiency and convenience
The Aperio KL100 is designed for minimal disruption to furniture. A tiny footprint and wire-free operation ensure it’s fitted quickly without causing damage or visual impact.
Yet within this small package is a powerful device which integrates seamlessly with any new or existing access control and security system — from over 100 different manufacturers and counting. Existing user credentials do not need to be replaced.
A KL100 may be connected Online, Offline or via OSS compliant integration — and switched between them at any time. Online management enables real-time control over every KL100 lock, with easy access rights administration and instant availability of audit trails for any opening or user — which makes incident investigation fast and accurate.
The Aperio KL100 Locker and Cabinet Lock joins a family of trusted wireless, battery-powered devices which includes cylinders, escutcheons, handles, security locks, server rack locks and more.

With its contemporary, low-profile design and power provided by a single, standard lithium battery, the KL100 is the modern choice for securing any site’s valuables and sensitive small spaces.
To learn how easy it is to extend access control with the Aperio KL100, download our free brochure

As an integral part of the Huntsville School District’s future sports complex, the new AT and Georgia Mae Smith Activity Centre serves as the hub for student activities across the district. Located on a remote site that’s home to the Huntsville Eagles Sports Complex, it is the future location that will house the district’s football and track stadium, baseball facilities, activity center, and other buildings that will be used to host activities and high school graduations.
Safety was the top priority when considering an access control solution. Having used Paxton’s Net2 since 2015 on other school buildings elsewhere, the district had a pretty good idea of what style and method of access control they wanted. Their main goal was to secure the premises while channeling people in and out of various activity center areas.
The district installed Paxton’s Net2 access control solution, which is a user-friendly and flexible networked access control system. It is designed to make the management of any site straightforward and that’s exactly what the district found when they installed and configured the system.
Net2 allowed the district granular control over its security, especially when it came to access control.
They can manage who has access to certain doors at specific times. For instance, they can limit access to contractors who work from 7:30 am - 5:00 pm to where they have no access on weekends or evenings.
With the addition of PaxLock, the wireless, electronic battery-powered door handles have also been beneficial. The activity center contains specific areas where installing a traditional hardwired system is not convenient or feasible. PaxLock makes securing those areas easy.
Net2 and PaxLock have allowed the Huntsville School District to customize access control to suit their specific needs – making the activity center a safe and secure place for their students and staff.
Bailey Cotton, Director of Technology at Huntsville School District, said: “I appreciate everything Paxton has offered us in terms of security and access control. We highly recommend Paxton, and any time a school asks what we use for access control, we encourage them to explore Paxton because it’s been such a great solution and experience for us. The flexibility of integrating other features and systems with Paxton is a no-brainer.”
Join Paxton’s free product training to learn more about their access control systems.
One of the most versatile work utility vehicles on the market, the Carryall 500 has the power to replace pickup trucks at a fraction of the cost. With a rustproof, aircraft-grade aluminum frame, and cargo box, along with best-in-class ergonomics, the Carryall 500 is the perfect solution for your industrial and commercial jobs.


Tech specialist Advantex has won a six-figure contract to provide an advanced new digital surveillance and security system for the ancestral London home of the Dukes of Northumberland.
The move sees the Gateshead-based firm supply Syon House in Hounslow, West London with a new IP (Internet Protocol) Milestone IP surveillance system, complete with more than 30 external Axis IP cameras. Remotely linked to development and investment company Northumberland Estates’ central control room at Alnwick Castle in Northumberland, the technology will provide improved monitoring capabilities of the house, a visitor centre and pedestrian access roadway areas.
Advantex is Northumberland Estate’s longestablished digital security partner and a key feature of the Syon House work has been the installation of modern IP cameras using the existing coaxial infrastructure.

This approach has delivered ‘significant’ cost and time saving benefits while minimising disruption to daily site operations and meeting the demands of working on an historic property, said Tony Easingwood, Advantex’s senior account manager.
“This is a very prestigious project for us, showcasing our expertise in delivering challenging installations for heritage-style projects,” he added. “We continue
to be at the forefront of delivering advanced and high-performance services, helping clients expand and develop their business and operational activities.”
The work is part of a major refurbishment of the 18th century-built Grade I-listed property, which today is used mainly as a venue for weddings and corporate events.
Shane Elliott, security manager based at Northumberland Estates in Alnwick said: “We are very pleased with the new system. Advantex were particularly sensitive to our conservation needs, delivering a cost-effective solution to meet not only our immediate surveillance and security needs but also the future needs of a large estate.”
The Northumberland Estates work comes as Advantex continues to recruit for additional electricians, data cabling engineers, project managers, support desk staff and various other operational and commercial roles to work on new contracts and bolster the current 60-strong workforce.
Other tech projects have been completed recently at County Durham garden furniture supply company Maze and automotive bearings manufacturer NSK. A £2 million project earlier this year saw schools and academy trusts across the North East access funding to refresh their Wi-Fi under the DfE’s ‘Connect the Classroom’ programme thanks to Advantex.
Mayflex, the distributor of Converged IP Solutions, is now distributing Secure Logiq, the experts in specialised servers for the IP Surveillance market.

Secure Logiq workstations and servers are built from the ground up to provide the fastest performance with up to 4000 Mbps, the biggest storage of over 1 petabyte in a single 4U server, the most resilience with up to RAID60 and the best value and are specifically designed for the complexities of IP video surveillance.
Secure Logiq products are manufactured from the highest quality components and all servers have dual redundant PSUs as standard. They also come with OS and application on 2 x SSD’s in Raid1 and Battery backed RAID as standard with options for RAID5 + Hot Spare, ensuring the very highest resilience.
Adam Herring, Security Director at Mayflex commented ‘We are delighted to be distributing and working with Secure Logiq. Their products provide the perfect and trusted server solution for our customers. With so many features and benefits, and the fact that they are built in the UK means that the carbon footprint and environmental impact of their servers is kept to a minimum, particularly when compared to many servers that are shipped around the world before getting to the
final customer.’
Adam continued ‘With the inclusion of their ‘Logiqal Benchmark’ utility it allows users to create a complete virtual environment replicating their entire IP Surveillance system and providing proof that the server hardware is fit for purpose, something that is unique to Secure Logiq and also contains a ‘camera replicator facility’ saving a considerable amount of set up time, amongst many other benefits. Our customers can check out which server is right for their requirements by using the handy ‘Logiqal Calculator.’
Robin Hughes, Secure Logiq Co-Founder commented ‘Having worked with Mayflex in previous roles I’m excited to once again be working with the Mayflex team to distribute the Secure Logiq range. Secure Logiq and Mayflex are both companies that strive for the very best in service and support and putting the customer at the heart of everything that we do, so we are well aligned, and we are very much looking forward to a long and successful partnership.’
For more details on Secure Logiq please visit the Mayflex website



SALTO’s newest model is perfect for effortless installation and retrofitting standard doors.
SALTO Systems has announced the launch of the new XS4 Mini Metal Model, a cutting-edge solution for upgrading and modernizing access control systems. This innovative electronic door lock offers a range of advanced features and an easy-to-install design that simplifies the transition from traditional mechanicalkey-operated locks to state-of-the-art electronic access control.

Experience the cutting-edge technology of the XS4 Mini Metal Model that is designed to fulfill all physical security and digital access needs. The XS4 Mini Metal Model offers unparalleled functionality and convenience including an impressive range of SALTO core technologies. This electronic smart door lock integrates SALTO SVN, BLUEnet Wireless, and JustIN Mobile
technologies, including Apple Wallet.
One of the standout features of the XS4 Mini Metal Model is its effortless installation and retrofitting capabilities. Combining appealing design and sophistication with robustness and smart access technology, this door lock is the perfect solution for any building.
The XS4 Mini Metal Model is designed for seamless compatibility with European, Scandinavian, and Australian standard doors which makes it easy to retrofit an existing installation, allowing for a swift upgrade from traditional knob or handlesets, without the need for door replacement or drilling.
For more information, please visit our website at www.saltosystems.com
After a string of live events in Belgrade and Zagreb which broke attendance records, Adria Security Summit Powered by Intersec 2023 goes back to the EU with a show in Ljubljana scheduled for October 25-26 2023. It’s the Summit’s second outing in Ljubljana, which is only fitting considering that it has now established itself on the roadmap of the key European industry events.
The venue is Gospodarsko razstavišče (Dunajska cesta 18), a place that will bring together leading regional and global industry leaders in the fields of security, cyber security, IoT, ICT, smart solutions, mobility, and automation.

This year, the event will put a twist on its triedand-tested formula by focusing on innovations in the most hands-on sense – making the innovations serve the market without intermediaries by helping it take the existing challenges in stride and integrate diverse solutions into a single system that works across national legislations.
By focusing on innovation, Adria Security Summit will reinvent itself while building upon what worked for it in the past and what drew in the record-breaking numbers of attendees, sponsors, and exhibitors. This year, the projections go beyond what was achieved last year in Zagreb, so the organizers expect to see over 150 exhibitors, 3000+ visitors, 20+ event partners, 3600+ meetings, and a conference program built around panel discussions, podcasts, keynotes, case studies, startup and showroom presentations.
Speaking of innovations, Adria Security Summit will also streamline its important facet of serving as a business hub that brings together partners within and beyond the scope of industries it covers and helps them gain a foothold in the local and regional markets, propel their investments, build lasting business alliances and get to know the cutting-edge technologies.
Information on Adria Security Summit 2023 is available at www.adriasecuritysummit.com



When it comes to budgeting, physical security technology has been historically regarded as a sunk cost, an operational necessity focused on protecting people and assets. Technology advances and the digital transformation of organisations are beginning to change that perspective as executives become more aware of the value unlocked by data-driven insights.
Having sufficient data management and structure is key to unlocking the value of physical security data.
It requires a shift from siloed, standalone systems to open, unified platforms that unify video management (VMS), access control (ACS) number plate recognition (ANPR), intrusion monitoring, pointof-sale (POS) reporting, and other functions in a single interface.
A unified physical security system can deliver insights that go far beyond improving security, to help improve operations and shape the enterprise overall. The challenge is in demonstrating that potential to executives. The key to selling a unified security platform to the C-suite is in elevating it from a
departmental cost to an enterprisewide investment and showing how it impacts the business interests they value.
While security may not be a daily topic of discussion among C-suite members, the heads of all functions and departments understand the need to provide a safe and secure environment for employees and visitors, maintain ‘duty of care’ standards, and comply with government and industry regulations. Any proposal to the C-suite must address those concerns comprehensively to win approval. Where the conversation needs to

expand is in how the project delivers advantages beyond security.
Bring your C-team up to speed on the industry’s shift from siloed, standalone systems for VMS, ACS, ANPR and other functions to open, unified platforms. With unification, all of those systems are built as one and enable access to the entire security operation from a single screen. It’s important to distinguish between systems that are integrated with an SDK or API, giving them some connectivity, and those that are truly unified on the back end, at the data level, which enables not only access and views, but the ability to interact with events and information across all of the sub-systems.
When all elements of a physical security system work together in a unified way, they not only secure an enterprise, but yield actionable business intelligence that can be leveraged and combined with operational data to improve efficiency.
Have the conversation about ROI
You need to provide a tangible return on investment (ROI) for your security system, but you must also help executives understand the overall security investment in the context of enterprise-wide risk management. ROI is often a question of goals.

Where does the leadership team want to take the organisation in the next five or 10 years? What data, features, or insights would be most meaningful to support these goals? A unified software platform enables better tracking of key metrics and more collaboration between departments. This in turn enables better decisions and potentially a greater ROI.
What pain points could be resolved with better collaboration, automation, visibility, or operational changes? What could your organisation gain if you eliminate redundant systems and processes? Could you reallocate those resources? When all systems bring data into one unified platform, companies can realise important cost savings. Operational expenses go down, the cost of maintenance is reduced, training is simplified, and employees can get their work done more effectively and efficiently.
It’s equally important to highlight the value of a system based on open architecture, which will give the organisation flexibility to choose best-of-breed components without being locked into any one particular hardware vendor, and to benefit from innovations and new technologies as they emerge.
Data can provide actionable insights that lead to greater efficiency and improved guest experiences. It’s also important to consider ROI
through the lens of the total cost of ownership. A seemingly cheaper option can cost more in the long run.
As the keeper of the sation’s technology stack and network, the C-team member from IT is an important ally, and it’s critical that they understand the potential of a unified physical security system in the context of the organisation’s technology priorities overall.
Demonstrate how an open, unified security system streamlines maintenance and upgrades, gives them agility and flexibility around hardware and software, enables cloud deployment, and improves cybersecurity.
Dealing with maintenance and system configurations on multiple security systems can be expensive and inefficient. Many required configurations are redundant, forcing administrators to repeat the same tasks across all systems. Upgrades can also potentially render a part of a security system incompatible with the others. A unified physical security system makes this job easier because all system updates and configurations are managed within the same platform.
Cloud readiness is also a hot button for IT. With support for cloud, hybrid-cloud and on-premises
deployments, modern, unified physical security systems enable the organisation to extend the functionality of server-based systems or create a bridge to the cloud to modernise existing infrastructures. This can be done by adding cloudconnected appliances, adding devices with cloud-based software and storage, implementing remote sites with cloud solutions, or running specific applications in the cloud.
A hybrid solution allows organisations to keep on-premises servers for existing technologies and uses as well as add other security and business components or systems as needed. The sheer flexibility and scalability of the cloud simplifies expansions by accommodating many different objectives, uses, and durations.

Finally, with cyberattacks rising across all geographies and industries as IoT devices proliferate,
cybersecurity is a top IT priority. Take the time to demonstrate how cybersecurity and privacy protection are built in at every level of a modern unified physical security solution. As the software vendor is responsible for monitoring cyber threats, then patching and updating software as required, this lifts the load off IT as well as security teams, since they don’t need to manually update multiple systems.
Conversations for Facilities: Improved operations and in-building experiences
Facility management has been significantly changed by digital transformation, and C-suite decisionmakers in that arena need good data to support novel solutions. When your data is divided by siloed systems, it’s hard to see the full scope of the opportunity. A unified platform allows organisations to combine and track data so you can see trends and how one event is linked to another.
One example is office space. With workers dividing their time between home and office, it’s challenging to know how much office space is needed. With a unified platform, facilities managers can leverage data from ACS and video analytics to get a detailed picture of how office space is used without compromising privacy.
Data from an access control system can also alert facility operators when a door has been opened a certain number of times and the hardware is due for
maintenance. This can allow for preventive maintenance. Data on the use of space can even be used to optimise and reduce utility costs when physical security systems are connected to HVAC and electrical systems.
How a physical security system can help improve operations
Data from physical security systems can be leveraged for operational benefits across several departments in all industries. With a modern unified physical security platform, each department or person can create their own dashboard to track the metrics that matter most to them making it quicker and easier to spot trends, threats, and opportunities. For example, restaurants, retail stores, and large venues successfully use video analytics to flag management when queue lines are too long. They can send staff to open new checkout lanes which can help reduce cart abandonment. From ANPR data retailers, for example, can get information on whether they’re getting a lot of out-of-state customers; information they can use to target marketing campaigns. Casinos can see when VIPs drive onto the property and greet them proactively. Airports can track when parking lots are filling up so they can re-direct people to overflow areas by changing digital signage as soon as the need arises.
For further information please visit www.genetec.com

Maxxess eFusion software opens up limitless possibilities, taking you beyond feature-rich, enterprise-level access control to give you all the benefits of a total security and safety management platform – without the cost or complexity.
Ready-made to integrate more than 60 leading technologies, off-the-shelf, Maxxess eFusion now lets you combine access, video, fire, intruder, visitor management, building systems, widely used databases and site-specific applications.

Protect Duty, also known as Martyn’s Law, is proposed legislation that will soon be working its way through parliament. The legislation has been named after Martyn Hett, one of the 22 victims of the Manchester Arena terrorist attack in 2017, and aims to ensure stronger protections against terrorist attacks in public places.
This will be achieved by placing a stronger requirement on those responsible for certain locations to have appropriate measures and mitigations in place in case of a terrorist attack. This includes ensuring that the relevant security
teams are better prepared and know what to do in the event of an attack. Improved security systems, better staff training and clearer processes will all help to accomplish these objectives.

The proposed law will impact all publicly accessible locations that meet certain criteria. They are:
• That the premises is an eligible one – i.e., a building or group of buildings and events with a defined boundary or that share similar activities.
• That a qualifying activity takes place at the location; and
• That the maximum occupancy of the premises meets a specified
threshold – either 100+ or 800+
The Martyn’s Law factsheet produced by the Government specifically states education as a key sector that will be impacted should the legislation become law. Those in charge of campus security need to familiarise themselves now with current position of the Protect Duty so that they are fully prepared should it become enshrined in law.
As noted in the bullet points above, all premises that meet a maximum occupancy of 100+ will be impacted by the law, and those with a
maximum occupancy of 800+ will be subject to additional requirements.
Businesses and venues in the standard tier (100+ maximum occupancy) will be required to complete free training courses and ensure that security information is shared with all relevant staff, with the end goal to complete a preparedness plan. The hope is that through a few relatively simple steps, staff will be better trained on how to prevent and deal with a terrorist incident. This could include everything from locking doors to prevent the progress of an attacker, to providing lifesaving support while emergency services are on the way.
The high-capacity locations in the enhanced tier (800+ maximum occupancy) will need a risk assessment and security plan that allows security teams to assess the balance of risk reduction against the time, money and effort required to

achieve a successful level of security preparedness.
Many University campuses will fall
into the enhanced tier.
While we can’t say for certain what the proposed law will specifically compel estate teams to do, we have a pretty good idea from the Protect Duty consultations and factsheet.
All higher education and University sites should already have a robust risk assessment and security plan in place. So for many, this proposed legislation acts as a timely reminder to re-evaluate those plans and ensure they are still relevant.
Furthermore, many Universities are now welcoming more students back to campus as they dial down on remote lectures. Campus occupancy is returning to pre-pandemic levels, which in itself is another good reason to ensure that security processes are up to date.

One area of security that has advanced in recent years – and that may need addressing in existing security plans – is technology. Improved security systems were highlighted by the Government as one way of improving preparedness for a terror attack, and for sites in the enhanced tier, situational awareness software will be a key tool in any security plan.
University campuses are often sprawling sites comprising numerous buildings and outdoor areas. The ability for all stakeholders
to view real-time insight, and communicate with each other, cannot be understated. In the event of a terrorist attack, this type of system could be the difference between averting a crisis or not.
Software can be utilised to record all planning for potential future events, share risk assessments across estates and shareholders, and demonstrate ‘reasonably practicable’ protective security and organisational preparedness measures – exactly what is likely to be required for Martyn’s Law.
Through a centralised platform, all security team members are empowered to track security resources, flag incidents, record key decisions and communicate critical information across all locations in real time.
Critical knowledge can be shared on a continual basis, minimising duplicated, unnecessary or ineffective activity, ensuring all security personnel always have the same understanding on current incident status.
This also allows for reduced corporate level risk and a more effective allocation and use of resources that can help to reduce overall costs.
Improved communication is also a key benefit of real-time situational awareness software. It is able to eliminate the potential for misunderstanding by overhauling communication and coordination efforts. It can guarantee seamless communication and information sharing so that an appropriate, timely and seamless response can be coordinated and delivered in dealing with a variety of potential threats, enhancing critical incident management to counter terrorism efforts.
Without such software, there is a chance that the right information will fail to get to the right people at the right time – an outcome that is simply unacceptable in modern security and safety procedures.
Software, such as Amulet’s Project Blueprint, can provide a live-time picture of operational activity and create a record of decisions taken that may be used to support investigations and enquiries as evidence in the aftermath of incidents. It is the predominant situational awareness tool used by UK emergency services, providing an opportunity to maximise the efficiency of their response in partnership with university security teams. This can also be useful in
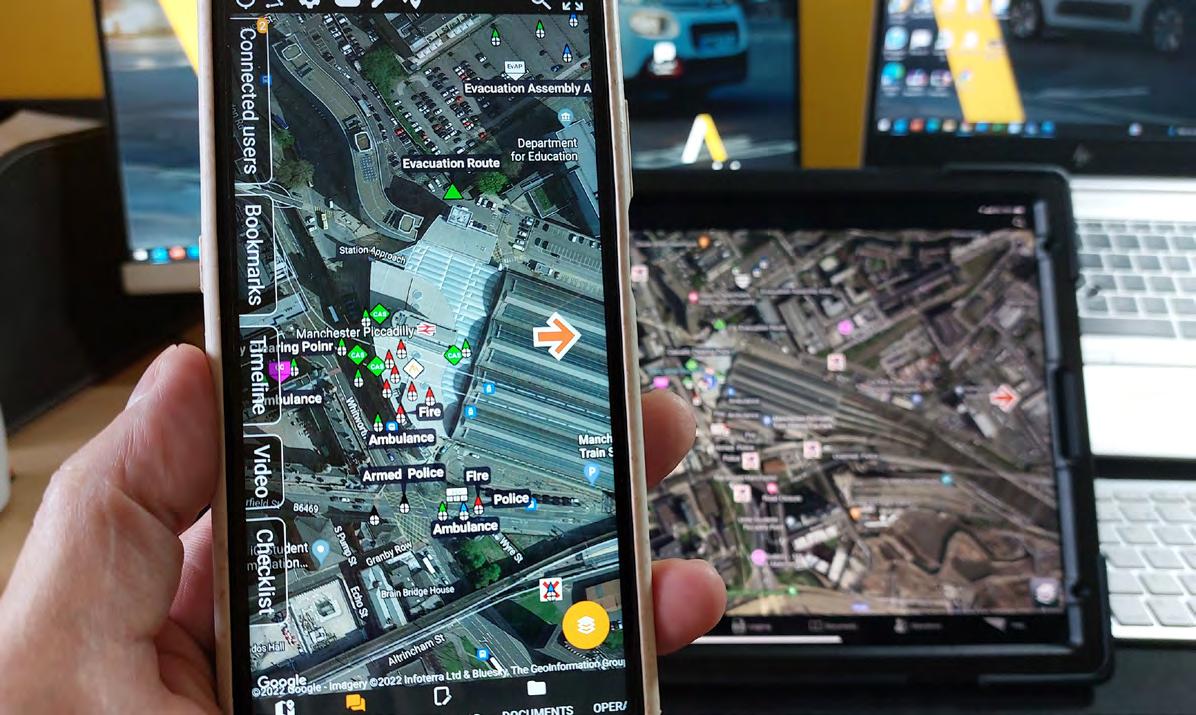
demonstrating that a sound security policy has been reviewed, practiced and implemented should an audit be required.
This will also be very useful when needing to evidence that a campus is abiding by Protect Duty, as there will be a range of as yet undisclosed sanctions for sites that fail to adhere to the law.
As with all proposed legislation, there is no fixed timeline for when it will be introduced to Parliament and when (or if) it will become law. That said, many of the suggested actions within the legislation are best practice that campus security teams should already be implementing.
My advice is that regardless of the legislation and its passage through Government, the education sector should use Martyn’s Law as a catalyst to ensure that risk assessments and security processes are fully updated and airtight. Even if Protect Duty doesn’t become law, educational institutions will be able to ensure that their employees and students are as safe as possible.
For further information please visit www.amulet.co.uk



Backed by more Government agencies and industry partners than ever before and showcasing the widest range of solutions designed to improve the security and resilience of businesses, people and critical infrastructures. In the face of ever-changing threats to global security, International Security Expo (ISE) will welcome a high-quality vetted audience of over 10,000 active buyers to London’s Olympia, and will play host to 300+ exhibiting brands offering the latest security solutions devised by the world’s leading suppliers.
The market-leading security event, chaired by former UK Security Minister Admiral Lord West, is once again co-located with International Cyber Expo, which brings an additional 5,000+ visitors who have free and open access across both events.
Exhibitors will be showcasing innovative products and solutions from across the entire security spectrum, including: hostile vehicle mitigation, perimeter protection, access control & biometrics, intruder detection / monitoring, communication, drone / counter drone, IT / command & control, CCTV & surveillance and much more. Exhibitors this year include:
This year’s Premier Partners include Apstec Systems, Astrophysics, Audax Global Solutions, Gallagher Security, HS Security/ATG Access, Leidos, LINEV Systems UK, Mitie, Pitagone, Rapiscan Systems, Rohde and Schwarz, Smiths Detection Group and Weytec. ISE is also supported by over 50 leading associations and media publications, such as ASIS UK, ADS, The Emergency Planning Society, IPSA and The Security Institute.
The event is the most interactive of its kind and will offer live demonstrations throughout both days of the show. British Transport Police will be showcasing a wide range of their equipment and tools including firearms and less lethal devices; the LPCB Live Testing Lab, in association with LPCB, supported by the PSSA and sponsored by Barkers Fencing, will feature professional forced entry specialists who will be put up against a range of physical security products, such as windows, fencing, and doorsets; and Counter-EO UK, CBRN-UK and DPAC will be conducting a series of counter threat scenario-based demonstrations.
A Perimeter Protection Zone, International Risk and Resilience Zone and Drone and Counter UAV Zone will help visitors expand their
knowledge in these key areas, with the dedicated SCEG Pavilion also highlighting a number of companies that deliver security in challenging and complex environments on land and at sea. The Government Zone is back bigger than ever in order to accommodate the overwhelming and continued support from UK Government. The larger space will provide a central meeting point for practitioners to network with key Government departments and agencies and find out about the latest projects and plans for the future.
Martyn’s law updates you won’t get anywhere else
Across the Conferences and Summit there will be essential updates for those looking to make sure they know how to comply with the Terrorism (Protection of Premises) Bill when it becomes law, including from those who drafted the legislation, those who will be implementing and enforcing it, alongside those who have been campaigning for it.
Shaun Hipgrave, Director Protect and Prepare for the Home Office, Office for Homeland Security, will discuss Martyn’s Law from a policy perspective and how it fits into the priorities for the Office for Homeland Security. This is a unique opportunity to understand the Government’s thinking behind the legislation that has been passed to Parliament.
NaCTSO (National Counter Terrorism Security Office) have been charged with ensuring Martyn’s Law is implemented once it hits the statute books, with preparations already underway to ensure they
are ready. They will be at the event to talk about those preparations and how people can get real practical advice to ensure they are ready. Elsewhere, Amanda King, the new head of NaCTSO, will talk about how they support business and their events through counter terrorism measures.
Looking at the legislation from a different perspective, a panel discussion featuring Tobias Ellwood MP, Chair of the Commons Defence Select Committee, Chris Medhurst-Cocksworth, Head of Pool Re Solutions and a senior member of NaCTSO, will explore the practicalities behind Martyn’s Law from a parliamentary, implementation and insurance perspective.
Figen Murray OBE and Nick Aldworth will return with a panel delving into some of the areas within the draft legislation that may require amendment or clarifications, asking
how the wider security community can help in the delivery of Martyn’s Law.

International Security Expo has built a reputation for its world-leading content programme, all CPDcertified, and this year is set to be no different.

The Global Counter Terror & Serious and Organised Crime Summit will deliver high-level policy updates and strategic insights addressing the latest global terror and security trends and priorities.
Counter Terror Police UK will provide an operational overview of counter terror priorities, whilst the role of cyber espionage in terrorist activities and to how to detect and prevent such activities will be put under the microscope by Joel Aleburu from Microsoft. From NaCTSO, Helen Williams, National Coordinator Protect and Prepare, will discuss the national security and terrorism challenges in the UK today, whilst then new head of JSaRC (Joint Security and Resilience Centre) Abu Ahmed, will also be providing an update.
The popular realities of terror thread returns this year, with a panel of victims of terror discussing their experiences and the personal impacts it has had on them.
Participants include Figen Murray OBE, Ann Travers, Advocacy Officer for the South East Fermanagh Foundation (SEFF) and former Irish Senator Máiría Carhill. This will offer insights from a perspective that is
essential to consider.
From a serious and organised crime perspective, the National Crime Agency will give an overview of their priorities and recent successes.
Lina Kolesnikova from ICPEM will explore narco-terrorism in Europe via case studies from the ports of Antwerp and Rotterdam, whilst William Dill from Invisible Traffick NI will talk about enhancing security awareness around human trafficking. Other areas to be explored include OSINT, advanced persistent threats and how evolutions in information communication technologies are a critically important factor in determining global jihadist organisation and their targeting.
The International Security Conference, sponsored by Everbridge and CSL DualCom, will look at the practical implementation of new policies and how these should be applied within different areas. SCEG (Security in Complex Environments Group) will run a panel on each day, featuring its members discussing the challenges and opportunities supporting the efforts to keep Ukraine safe and prepare for the future.
Satia Rai, CEO of IPSA and Head of Diversity, Inclusion & Belonging for Securitas UK, will host a panel discussion on diversity and how it is essential to stop groupthink, which can be disastrous when developing a security ecosystem. Peter Drissell,

Director of Aviation Security for the UK CAA (Civil Aviation Authority) and Frederick Reitz from SAFEsky Inc. will both give talks exploring aviation security.
Thomas Vonier from Chesapeake Strategies Ltd looks at security in public places, with case studies from Paris and Washington DC, whilst Brooke Tapsall from DroneALERT discuss the importance of adversarial testing (red teaming) for increased asset or location protection, using the FIFA World Cup as a case study.
The International Risk & Resilience Conference, in partnership with Resilience First and Crisis Response Journal, will give the latest thinking and practical insights from individuals and organisations who live, eat and breathe risk and resilience.
Jamie Shea, former Deputy Assistant Secretary General of Emerging Security Challenges for NATO, will host a panel discussion focusing on global challenges from a security, resilience and economic perspective. Lianna Roast from the Cabinet Office Emergency Planning College will talk about learning and resilience and turning lessons into action, Verity Davidge, Director of Policy for Make UK will discuss navigating supply chain resilience through complex and troubling times with Resilience4Ports, whilst Ed Morrow from Lloyd’s Register Foundation will talk about their
World Risk Poll – the first global study of perceptions and experiences of risk to people’s safety – alongside Caroline Field from PA Consulting.
Commenting on the event, ISE Group Event Director Rachael Shattock explained: “International Security Expo 2023 will be an unmissable event for global security professionals. The content on Martyn’s Law will ensure visitors are in the best possible position to plan for and understand the legislation, but the overall quality and level of content this year is truly fantastic, and it’s all available for free.”
Former Security Minister and Chair of ISE, Admiral Lord West GCB DSC PC adds: “We are delighted to welcome back hundreds of the industry’s leading brands making ISE the best place to meet innovative global suppliers who can solve all of your security needs. The added value that comes from full access to the co-located International Cyber Expo allows visitors to see the full security picture. We really hope to see you at Olympia this year on 26-27 September.”
ISE is completely free-to-attend, including invitation to the Networking Drinks Reception at the end of Day One.
For more information and to register to attend International Security Expo on 26-27 September 2023, visit www.internationalsecurityexpo.com





































Since the start of the pandemic, the way business is conducted has changed permanently, with many workforces continuing to work remotely as restrictions have eased. As companies relax and rules have eased, life is expected to return to a form of ‘new normal.’ But, the issues around cybersecurity are here to stay, and the gas pedal
must not be eased – especially with the increased risks associated with continued remote working.
If anything, security should be more reinforced now than ever before to ensure all aspects of a business are secure. But this isn’t the case. Rob Hancock, Head of Platform at Giacom and Kelvin Murray, Threat Researcher, Webroot, detail the importance of embedding a trilogy

security approach into organisations, and this is where a strong CSP/MSP relationship can be invaluable.
Despite lockdown restrictions easing, cybersecurity risks remain and are likely to grow as COVID-19 continues to change the working landscape. With indoor spaces back open, employees will want to venture
out to new spaces to work, such as coffee shops and internet cafes – but working on open networks and personal devices creates unlocked gateways for cyberattacks to take place. Since this hybrid and remote way of working looks like it’s here to stay, businesses must ensure they have the right infrastructure in place to combat any cyber threats.
For instance, research by the National Cyber Security Centre shows that there has been a rise in COVID-19 related cyber attacks over the past year, with more than one in four UK hacks being related to the pandemic. This trend is not likely to ease up any time soon either. And, going forward, hackers could take advantage of excited travellers waiting to book their next holiday, deploying fake travel websites, for example.
Aside from the bad actors in this
wider scenario, part of the problem here is that many IT teams are not making use of a holistic and layered approach to security and data recovery; which can lead to damaging consequences as data is stolen from organisations. Such issues continue to resonate strongly across businesses of all sizes, who will, therefore, turn to their MSPs for a solution.
Cybersecurity is not a one-stop-shop. A full trilogy of solutions is required to ensure maximum effect. This includes a layered combination of DNS networking, secure endpoint connections, and an educated and empowered human workforce.

The need for DNS security cannot be ignored, especially with the rise of remote workforces, in order to
monitor and manage internet access policies, as well as reduce malware. DNS is frequently targeted by bad actors, and so DNS-layer protection is now increasingly regarded as an essential security control – providing an added layer of protection between a user and the internet by blocking malicious websites and filtering out unwanted material.
Similarly, endpoint protection solutions prevent file-based malware, detect and block malicious internal and external activity, and respond to security alerts in real-time. Webroot® Business Endpoint Protection, for example, harnesses the power of cloud computing and real-time machine learning to monitor and adapt individual endpoint defences to the unique threats that users face.
However, these innovative tools and solutions cannot be implemented without educating users and
embedding a cyber security-aware culture throughout the workforce. Humans are often the weakest link in cybersecurity, with 90% of data breaches occurring due to human error. So, by offering the right training and resources, businesses can help their employees increase their cyber resilience and position themselves strongly on the front line of defence.
This combination is crucial to ensure the right digital solutions are in place – as well as increasing workforces’ understanding of the critical role they play in keeping the organisation safe. In turn, these security needs provide various monetisation opportunities for the channel as more businesses require the right blend of technology and education to enable employees to be secure.
Businesses, particularly SMBs, will look to MSPs to protect their businesses and help them achieve cyber resilience. This creates a

unique and valuable opportunity for MSPs to guide customers through their cybersecurity journeys, providing them with the right tools and data protection solutions to get the most out of their employees’ home working environments in the most secure ways. Just as importantly, MSPs need to take responsibility for educating their own teams and clients. This includes delivering additional training modules around online safety through ongoing security awareness training, as well as endpoint protection and anything else that is required to enhance cyber resilience. Moreover, cyber resilience solutions and packages can be custom-built and personalised to fit the needs of the customer, including endpoint protection, ongoing end-user training, threat intelligence, and backup and recovery. With the right tools in place to grow and automate various services – complemented by technical, organisational and personal support – channel partners will then have
the keys to success to develop new revenue streams too.
Conclusion
Hackers are more innovative than ever before, and in order to combat increasing threats, businesses need to stay one step ahead. Companies must continue to account for the new realities of remote work and distracted workforces, and they must reinforce to employees that cyber resilience isn’t just the job of IT teams – it’s a responsibility that everyone shares. By taking a multilayered approach to cybersecurity, businesses can develop a holistic view of their defence strategy, accounting for the multitude of vectors by which modern malware and threats are delivered. Within this evolving cybersecurity landscape, it’s essential for SMBs to find an MSP partner that offers a varied portfolio of security offerings and training, as well as the knowledge and support, to keep their business data, workforces and network s


According to international market research firm, Fortune Business Insights, the smart automation sector is estimated to increase by around 20% between 2021 and 2028 (https://www. fortunebusinessinsights.com/ industry-reports/smart-homemarket-101900). The growth in
demand is coming from both the commercial and residential sectors, and a rising number of end users are seeking integrated solutions that combine the convenience and energy-efficiency of smart automation with security.

The ongoing cost-of-living crisis is unfortunately perpetuating a long-standing perception among
many buyers that robust professional security systems are preferable rather than necessary, with many residential property owners still opting to install low quality DIY products themselves.
Yet a new wave of professional integrated security alarm and smart automation solutions are providing installers with the opportunity to
offer end users a cost-effective system, amalgamating smart automation with an enhanced level of security.
These new integrated solutions also provide customers with a superior degree of security to that offered by autonomous security systems. Users may create event rules, whereby intruder detection triggers a series of “proactive protections” such as the switching on of outdoor lights, that deter burglars from attempting to access a building. They may also establish time-scheduled rules designed to make thieves believe that a vacant property is occupied, programming the system to turn lights on and off at certain times of day.
Integrated scenes can be preconfigured, not only saving occupiers time when they leave a building, but also precluding security omissions caused by human error. At the point at which a property is vacated, the security system automatically locks doors, windows and gates, generating peace of mind.
Installers too stand to gain a great deal from integrated solutions, not least the opportunity to expand their offer to include security as well as smart automation. It is quicker and easier to fit a single combined system than autonomous products, and cost-effective projects help installers to achieve healthy margins even within the context of the cost-ofliving crisis when end user budgets are squeezed.
The comprehensive new solutions require contractors to carry only a relatively small amount of stock, which both enables them to save on storage space required and facilitates a simpler, swifter procurement process less vulnerable to the vagaries of a supply chain which in some areas has yet to fully recover after the global pandemic.
Contractors also make savings in the time it takes to train their engineers in the correct and efficient installation and maintenance of equipment, providing instruction on one product instead of two.

The number of integrated systems available on the market is growing, and the choice can be bewildering, especially for smart automation installers new to the field of security. But by following a few simple
guidelines, contractors can make the decision-making process easier and less time-consuming.
Integrated solutions manufactured by security specialists tend to feature high-level security as the bedrock of their functionality. They provide installers with the opportunity to offer their customers a professional system, fully differentiated from lower quality options available on the DIY market. Many of these producers stock a range of compatible devices such as locks, lights and garage doors, facilitating ease of purchase.
The best manufacturers will also be able to provide installers not only with reliable after-care, but also comprehensive – and in the best cases, bespoke – online
and face-to-face training for their engineers, designed to enable them to fit and maintain the solutions with effectiveness and efficiency. As well as allowing installers to guarantee the cost-effective delivery of efficacious systems, robust product training helps to enhance their engineers’ capabilities. By offering enrichment opportunities to their staff, installation firms can help to boost their employees’ level of job satisfaction and so too their loyalty; this is of particular importance while the UK continues to face a shortage of engineers.
It is vital that contractors select a security alarm of the correct grading, reflecting the value of a property’s contents and the associated risk of intrusion. Not only is this necessary
to safeguard contents and people, but it is also vital to meet the criteria stipulated by insurance policies. Security grades begin at one and rise to four for the highest risk facilities.
Open-source solutions present a series of advantages over proprietary ones, facilitating easy integration with customers’ existing devices, irrespective of brand. They also allow flexibility in the future expansion of combined systems, enabling installers to select devices that meet their customer’s needs precisely.
Scalable products allow the efficient increase of the number of zones covered, permitting straightforward adaptation in the event of property evolution or extension or the incorporation of new buildings.
Installers should look for a solution that connects the controller to the alarm via Bus, the most flexible wiring topology available.

Bus enables devices to be quickly and easily wired in a single-line “daisy-chain” protocol in addition to or in place of a conventional “star” layout, minimising the quantity of cabling and zone expanders required. Our customers have made time and material savings of up to 75% on projects incorporating this protocol. Ultimately of course, installers want to be able to provide their customers with an exceptional user experience that will not only meet their immediate needs but also encourage repeat business and referrals to friends and business associates. Ease of operation is a big part of this, and integrated solutions that enable residential and commercial users to effortlessly manage security and smart automation remotely from a single control panel and via app permit simplification of their daily routines. And of course, voice activation control is rapidly becoming an
expectation rather than a preference. Earlier this year, RISCO utilised its 45 year experience in the manufacture of security solutions to create the RisControl Controller for Alarm and Smart Automation, an integrated security alarm and smart automation solution for commercial and residential installers that may also be supplied as a standalone automation controller.
RISCO has a national distribution agreement with leading global security distributor, ADI Global Distribution, and on 29th September, ADI will host a webinar for installers keen to discover more about the operational scope and business benefits of adding combined systems to their portfolios, as well as technical advice.
For further details please visit www.smarthome.riscogroup.com




Safety and Security is taking an increasingly leading role in society and in organizations, has ceased to be the “necessary evil” that only generated costs without contributing to the profitability of the company, its importance is such, that today there are at least 3 types of security in all organizations: occupational safety, patrimonial security and operational safety, although two others can be added: health safety derived from the recent pandemic of SARS-CoV-2 and cybersecurity for those companies that manage their processes with computer systems (which today are
the majority).
Highly specialized industries such as aeronautic, food and nuclear have very particular safety and security systems that are also added to the previous ones. Can we imagine how complicated is for an organization to manage so many security systems? What are the differences and similarities between one type of safety/security and another? What is the relationship between them?
How can a change in one type of safety/security in others impact me?
Imagine that each type of security is a piece of puzzle and that we do not know how to clear each one to put it together, the answer to this dilemma

is the integration of all types of safety and security in a single management system called: Integral Safety and Security Management System.
Until recently, the only experience in terms of integration of management systems was that of ISO 9001 Quality Management Systems, ISO 14001 Environmental Management System and ISO 45001 Occupational Safety and Health Management System, but there was nothing about how to integrate all safety and security systems into a single management system. The experience in integrating the three management systems mentioned above has laid a firm foundation for
integrating all types of safety and security, however, the process must be reversed, In other words, all types of safety and security should first be integrated into a single management system and once this system is mature, integrate it with other systems such as quality and environmental systems.
The key to integrating any management system is the following:
1. Process-based approach- All processes must be documented.
2. Risk-based thinking- Any activity within the organisation must be assessed in terms of its risk.
3. Follow the Deming cycle or continuous improvement cyclePlan, Do, Verify and Act.
4. Having the ISO High Level Structure (International Organization for Standarization):
• Organizational context.
• Leadership.
• Planning.
• Support.
• Operation.
• Performance Evaluation.
• Continuous Improvement.
The task is not easy, because bringing any system to the ISO High Level Structure requires knowledge and experience from the staff who lead the process and resources from the organization, however, the incentive is great, consultants specialized in integrating management systems such as Integrated Compliance Solutions, estimates that the savings are 30 to 50% in operating costs in companies that have their systems tegrated. The benefits include:
1. Saving in material, human and financial resources due to not duplicating functions.
2. Reduction of workload and documentation, increasing staff productivity.
3. Clear instructions with the consequent mitigation of costs resulting from misinterpretation errors by the person executing them.
4. Efficient communication between the various safety and security areas.
5. Mitigation of sanctions by authorities and trading partners.
6. Increased confidence of authorities, customers and other
interested parties, which may attract more revenue to the company.
7. More profitable, safe and secure organizations.
8. Policies aligned with each other.
9. Comprehensive risk management that facilitates strategic decisionmaking.
10. Facilitates the certification process of various organisations such as ISO, CTPAT, AEO, BASC, TAPA, etc.
But not everything is honey on leaflets, the integration process can take 10 to 24 months depending mainly on the following factors:
1. Size of the organization in terms of the number of employees, production plants, distribution centers, bases of operation, etc.
2. Level of maturity of the organization that have a direct relation with the safety and security culture of its collaborators, which can be determined with the help of the document AENOR (Spanish Association of Standardization and Certification) UNE 66177:2005: Management systems: A guide for the integration of management systems.
3. Lack of interest in management systems by managers.
4. Resistance to change by the leaders of the various security and safety areas.
5. Lack of accompaniment and follow-up of the person responsible for the integration process.
6. Unmotivated and uncommitted work teams.
7. Low awareness of the importance of management models.
8. Lack of knowledge and little experience in management processes.
9. Misperception that management processes increase workloads
10. Difficulty in choosing the level of integration appropriate to the maturity level of the organisation.
The integration of security and safety systems involves:
1. Establish a comprehensive safety and security policy instead of having 3 or 4 different, fully aligned to the mission and vision of the organization and the
corporate objectives of the same.
2. To define objectives together, especially in those processes that impact on more than one type of safety and security, aligned with the corporate objectives of the company and the comprehensive security policy.
3. Incorporate topics common to all types of safety and security into staff training programmes, optimizing training times and increasing their productivity.
4. The assessment of risks jointly, identifying in a collegiate manner those hazards and threats that impact on more than one type of safety and security using the same risk assessment methodology.
5. The preparation of first part audits in conjunction with approved criteria, identifying those tasks that impact on more than one type of safety and security to be evaluated under the same criteria and quantifying the result of the audit at a level of risk of the process, area and organisation as a whole.
6. The definition of common performance indicators in processes that impact more than one type of safety and security.
7. The definition of competencybased job profiles, so that safety and security personnel have a comprehensive view not only of their specialty, but of the rest of the safety and security areas in order to estimate the impact of their processes on the rest of the system.
8. Continuous improvement through frequent review of system performance by senior management through a Comprehensive Safety and Security Committee, to be able to have visibility of the advances of the system and of the collegiate establishment of strategies of mitigation of the diverse risks in each of the areas of safety and security and its impact on the others.
Today, thanks to the principle of synergy where the whole is greater than the sum of its parts, safety and security has to be seen as a holistic process in which the administration by silos falls more and more into
obsolescence and unproductivity, the leaders of the various safety and security areas must be open to change, in effect, the integration of safety and security systems will not be welcome at the outset, as some will think that they will lose power or level of influence within the organisation, putting their work at risk, this is not the case, and we must work to make leaders aware first of all of the benefits of the system, this is one of the main challenges to be overcome, since we must count on their support for the success of the process.
Another very important factor is the commitment of senior
management, the CEO is responsible for the management system and the allocation of resources for its integration. The costs associated with the integration of management systems in general are not onerous, on the contrary, many times when duplicating functions also duplicate resources and in that sense from the integration process can already start to have savings and be visible, its effect is almost immediate. What effectively increases and greatly during the integration process is the workload, the task of reviewing in detail each procedure in each safety and security area and establishing a correspondence matrix to define the relationship of a procedure with other safety/security systems, is time-consuming and tiring. This is the most complicated part of the process, however, once the system is integrated and mature, the workload of the staff is substantially reduced by being more productive. Raising awareness of an enterprise’s operating staff of the benefits of an integrated management system may not be as clear to them, it is advisable to use awareness strategies such as reducing the risk of suffering an accident at work or having savings derived from the implementation of the system, will have greater profits at the end of the year, undoubtedly, arguments like the previous ones, are the ones

that generate the greatest impact on staff, we must design strategies that aim effectively, to show the benefit of integration based on their priorities.
Let us not be afraid to implement a Comprehensive Safety and Security Management System, let us be open to changes and see the benefits of the company and our area in the short, medium and long term, let us be creative and disruptive, because today it is the only way to survive our competition in a globalized world that in terms of safety and security, It needs to effectively anticipate new hazards and threats and to deal with them with intelligence and clear strategies that allow us to be safer and more secure but also more profitable.
Author’s profile:
Eduardo Reyes is an Aeronautical Engineer and holds a Master’s degree in Strategic Management and Innovation Management. He has held management positions in safety and security areas of the most important companies in the aeronautical sector such as Aeromexico, Aerounion, Serviseg and currently the Pacific Airport Group. He is teacher of the National Polytechnic Institute in Mexico and author of the book: “Integral Safety and Security in Companies. Integral Safety and Security Management System” published by Alfaomega.




The ASSA ABLOY Group is the global leader in access solutions. Our offering covers products and services related to openings, such as locks, doors, gates and entrance automation solutions. This also includes expertise in controlling identities with keys, cards, tags, mobile and biometric identity verification systems.

www.assaabloy.com
azena accelerates the next generation of smart security and safety solutions through joint innovation with customers and partners. Our goal is to be the leading open platform and marketplace for smart security and safety solutions. The platform we offer is based on a camera operating system that powers cameras from various manufacturers on the market.



www.azena.com

Club Car boasts nearly 60 years of industry-leading innovation and design, initially focused on golf cars and then expanding to commercial utility vehicles and personal-use transportation.
www.clubcar.com


Hanwha Techwin Europe, formerly Samsung Techwin Europe, offers robust and reliable video surveillance products designed to meet the current and future needs of security professionals. Our cameras, video recorders and other devices are built to exacting standards which reflect the heritage of precision engineering associated with the Samsung brand.
www.hanwha-security.eu




Innovating for a smarter, safer world by combining intelligent technology and human imagination, at Axis Communications we offer solutions based on sight, sound and analytics to improve security and optimize business performance.

www.axis.com
Buildings today don’t only provide a safe, functional place for people to live and work. They can also cater for – and even respond to – their needs, while helping them work more efficiently and sustainably. At Bosch Building Technologies, we are at the forefront of these new developments.
www.boschbuildingtechnologies.com

With a full HD camera and an optically stabilized, 40x zoom lens from FUJINON, two high-performance components are integrated into one system. This innovation is the result of years of experience in digital cameras and a dedication to the highest optical quality.


www.fujifilm.eu/fujinon
HID powers the trusted identities of the world’s people, places and things. We make it possible for people to transact safely, work productively, and travel freely. We are passionate about helping people use a verified, trusted identity to make it more convenient and safer for them to get to where they need to go and achieve what they want to do in everyday life.
www.hidglobal.com
Maxxess Systems delivers innovative SaaS and security management software solutions that combine otherwise disparate physical security, communications, business intelligence and data integration capabilities onto one unified management platform.


https://maxxess-systems.com

Panasonic i-PRO Sensing Solutions Corporation of America a global leader in professional security solutions for surveillance and public safety, is launching their new name, i-PRO Americas Inc., and taking a unique approach to best navigate the evolving business environment and technology demands of the professional security industry.
https://i-pro.com/eu/en
As a trusted advisor and reliable partner, as a system integrator, service provider and a product vendor, Siemens offers energy-efficient, safe and secure buildings and infrastructure. With our people, our global footprint and our technical expertise, it's our passion helping you to create the perfect place – your perfect place.


www.siemens.com
Transforming teaching and learning with creative solutions to engage and inspire every student. Learning’s becoming more interactive. More immersive. More collaborative. At Sony we’re working with universities, colleges and schools to create richer, more rewarding educational experiences for today’s students and teaching staff.
https://pro.sony.com
At Mayflex we lead the way in the distribution of Converged IP Solutions. Bringing together ‘best-in-class’ Infrastructure, Networking and Electronic solutions. We’re a growing international force, enriched by the skills, expertise and unique personalities of our people. Globally owned but with a family and local feel.

www.mayflex.com

With over 30 years of experience, we design and manufacture marketleading security solutions for a range of buildings. Around 25,000 buildings each year are secured globally with Paxton products. Our global Head Office is based in Brighton, we have colleagues in 12 countries and we export to over 60 countries worldwide.
www.paxton-access.com


From its inception in 2001, SALTO was created with one objective: to devise a world-class access control system that was simple to use and extremely efficient, giving users the ability to control all their access needs and secure all their doors without complex and expensive wiring.

www.saltosystems.com
Videx Security is a leading manufacturer and supplier of access control systems across the UK. We are experts in the door entry market. Videx and our team of estimators, technical support and designers are focused on making and providing high quality products and support to customers.


www.videxuk.com
One system for all requirements of an intelligent building
