
5 minute read
Cyberwarfare: an emerging global risk impacting our society By Vivek Seth
cyberwarfare: an emerging global risk impacting our society
by Vivek Seth
Advertisement
In the context of global risks faced by countries, the risk of materialization of large-scale cyberwarfare has become increasingly prominent in recent years. Broadly speaking, cyberwarfare refers to deliberate cyber-attacks like spreading of computer viruses and hacking by one or a group of nations on another nation state’s technological infrastructure. Key motivations of such attacks include political aspirations to disrupt the operational activities, digital espionage, spreading misinformation, physical sabotage, coercion in decision making process and financial gain at the expense of the target country or international organizations. With an ever-increasing interconnectedness of the world via internet and digital infrastructure, targeted cyber attacks can prove to be an effective tool for causing large scale harm to victim government, military and corporations.
Some of the common means of perpetuating cyberattacks include usage of botnets for distributed denial of service (DDoS) attacks, social engineering, phishing techniques as well as disruptions via insider staff with access to sensitive or critical information systems. A key reason why such attacks are becoming more prevalent is due to their covert nature, as often the outright involvement of participants is not apparent, which is in contrast with conventional military and intelligence exercises. While there has not been a categorically declared cyberwarfare yet, the world has seen a number of incidents that have caused serious disruption to countries’ infrastructures and which are suspected of being carried out by state-sponsored organizations. Some of these events are outlined in the timeline indicated below.
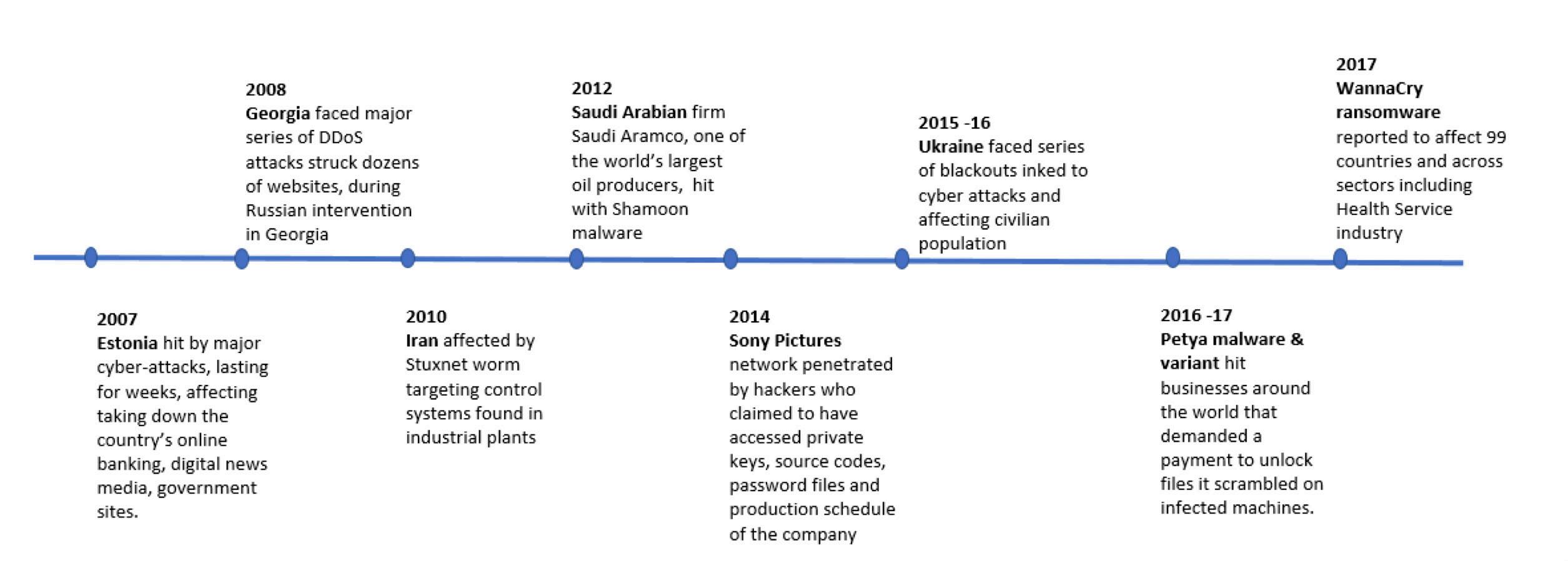
Key recent cyberattack events affecting serious disruption to countries’ infrastructure
While these recent cases of advanced persistent threats have so far not resulted in world scale physical conflict or violence, such computer network attacks do have consequences. Negative outcomes to a nation state could include financial and reputational damage due to disruption of services, loss of privacy of targeted individuals/organizations, civilian population daily lives affected by infrastructure operation failures, spread of phobia & misinformation affecting public trust on governments as well as weakening of national sovereignty. Currently, there are limited bilateral or multilateral agreements between countries on collectively curbing nation state targeted cyber-attacks and situations when such engagements get kicked off can be open to interpretations.
Preparedness against such persistent attacks rests on fundamental cyber hygiene basics such as timely identification of IT vulnerabilities, patch management, upgrade of obsolete systems, network monitoring of anomalous activities, and strong identity and access management controls. On top of these fundamentals, vigilance is also crucial against suspicious network probing activities, communication from high risk countries known for cybercriminal perpetuators and vulnerabilities emanating from emerging technologies such as Deep Fake driven media. Adequate resourcing is also of paramount importance for a robust strategy on analyzing and risk assessment of cyber threat environment for early detection and prevention of such attacks. Cyber defense strategies should also include network segregation of sensitive IT infrastructure, containment of detected threats and usage of encryption framework, strong password and multifactor authentication culture.
A statewide cyber incident management plan should be established that outlines crisis mitigation strategy for countries to defend themselves against future cyber war threats especially for critical components of a nation such as banking, railways, hospitals, stock exchanges, power stations, and food supply infrastructure. Cyber risk training and awareness among organization staff and in public media also helps in deterrence of such attacks. Many developed nations and international organizations prepare against cyberwarfare with simulation cyber defense wargames. For example, in 2019 US and Taiwan held the first joint cyber-war exercise #. NATO nations address cybersecurity concerns via Locked Shields events@.
This rising trend of nation-targeted cyberattacks poses the risk of a new cyberwar arms race, with dedicated spending on stockpiling of cyber-attack strategies like that of tangible arms race. Such programs could be developed in secrecy, thus lacking transparency, governance, and agreed rules of engagement between nations. Accidental or deliberate leakage of such digital attack tools to criminal organizations can prove to be damaging to overall world stability. The Internet allows malicious cyber actors to deliver weaponized tools on a real time pace and at an exponential scale. While many nations are seeking to acquire and test digital attack and defend capabilities, they should also keep in mind widespread impact of such digital skirmishes, especially to civilian population. Thus, a widespread binding international agreement among countries to restrict the development and use of offensive cyber weapons is required that emphasize development of defensive rather than offensive capabilities. Just like in non-digital warfare, there can’t be winners in a large-scale cyberwarfare, but only losers.

conclusion
Both developed and developing parts of the world are becoming heavily dependent on the Internet and digital infrastructure for delivery of its critical economical activities. Such dependency calls for a robust cybersecurity strategy for the smooth functioning of a nation state. This is especially crucial when such cyber attacks are persistent, organized by a large-scale organization or rival country or advance cybercriminals. Mitigating emerging vulnerability and attack vectors for cyber crimes at a national scale requires international cooperation and agreement, robust internal IT infrastructure and vigilant staff and civilian population. Only via this long-term strategy of bringing attention to the dangers of cyber-weapon proliferation, international diplomacy, public shaming, and taking collective actions against suspected cyber attackers, can the world achieve peaceful advancements in digital arena.
1. www.bbc.com (link) , 27 April 2017, “How a cyber attack transformed Estonia”. Sources used for preparing timeline chart:
2.
3.
www.bbc.com, (link), 20 February 2020, “UK says Russia’s GRU behind massive Georgia cyber-attack”.
www.bbc.com, (link), 22 November 2010, “Stuxnet ‘hit’ Iran nuclear plans”.
4.
www.bbc.com, (link), 17 August 2012, “Shamoon virus targets energy sector infrastructure”.
5.
6.
www.bbc.com, (link), 25 November 2014, “Sony Pictures computer system hacked in online attack”.
www.bbc.com, (link), 11 January 2017, “Ukraine power cut ‘was cyber-attack’”.
7.
www.bbc.com, (link), 29 June 2017, “Cyber-attack was about data and not money, say experts”.
8.
9.
www.bbc.com, (link), 13 May 2017, “Massive ransomware infection hits computers in 99 countries”.
www.bbc.com (link), 4 November 2019, “US and Taiwan hold first joint cyber-war exercise”.
10. https://ccdcoe.org/about-us/
author
Vivek Seth
Vivek Seth is a Singapore citizen, working in the Risk Management discipline in the financial industry for over 15 years. His work experience spreads across Singapore, Dubai, and Australia along with business assignments carried out in Hong Kong and Switzerland. He holds an M.B.A. and also the PRM™ professional certification. This article presented here represents the author’s personal views and not that of his current/previous employers or any professional bodies he is associated with.








