Thought Leadership Compendium
ARTICLES



 BY:
BY:
Global Public Health Supply Chain Practice
BY AMENTUM
The Impact of Rising Inflation on Employee Benefits 2022

 BY AON
BY AON
Understanding Cybersecurity Maturity Model Certification (CMMC) 2.0 Compliance

 BY DELTEK
BY DELTEK
The Challenging Road to Securing the Perimeter
BY LEIDOS
© Professional Services Council 2022
Table of Contents 03
08
15
22
Global Public Health Supply Chain Practice

3
Amentum Global Public Health Supply Chain Practice

Topic: Diagnostics Supply Chain Agility, Resilience, Equity and Localization in Low and Middle Income Countries
Author: Farouk Adams UMARU, PhD. Director, Global Health Technical Programs, Amentum
1.0 Introduction
Many in developing countries, in hard to reach and conflict threat zone, still lack access to quality assured medical products, diagnostics, vaccines, and health care. Building resilience and agile health supply chain in lower and middle income countries (LMICs) is a growing challenge for public health policymakers, partly because of misaligned priorities of national governments and donor communities Decades of investments by the United States Government and stakeholders to strengthen supply chains around the wor ld have yielded noteworthy results, but more still needs to be done (1,2)
Diagnostics, as a first step to treatment and care, is a driver of patient, financial and health systems impact, but it is also the weakest link in the care and treatment cascade of health delivery (3). Lower and middle income countries are disproportionately affected due to the lack of integrated network of laboratory infrastructure for broad spectrum of detection, testing and surveillance of primary health and emerging infectious diseases. At the center of this neglect is the lack of essential diagnostics supplies and commodities to test, detect and respond to emerging pathogens. Sourcing, procurement, transportation, and delivery of essential commodities in the right quantity, delivered at the right place at the right time are basic functions of health supply chain. And yet, laboratories across resource limited nations face chronic stock out of basic essential supplies to respond to emerging pathogens .
The COVID 19 pandemic is a testimony of the significant role diagnostics play in pandemic preparedness and response. Globally, there were heightened need for reliable, accurate and responsive need for diagnostic technologies and laboratory capacities to detect SARS CoV 2 virus. Diagnostics suddenly became the center of attent ion, elevating clinical research institutions such as US CDC, NIH, Africa CDC and WHO to the frontline of testing, control, and management of COVID 19. Suddenly, though, African countries continue to struggle in leveraging COVID 19 investments in technologies, testing platforms (e.g., for PCR testing) to strengthen their diagnostics capacities and the overall access to essential health commodities ( 4).
In this article, we propose solutions to professional service practitioners, policymakers, and health supply chain procurement service agencies on achieving resilience, sustainable and equitable service delivery. Integrating diagnostic services and supply chain into the national health strategic plans, engaging national public health laboratories, and optimizing tiered network, are approaches to deliver lifesaving diagnostics, testing, detection, and surveillance of routine and emerging pathogens.
4
2.0 Managing Diagnostics Commodities Supply Chain
Sourcing, forecasting, storage, delivery, and use of diagnostics commodities require s a set of skills, knowledge, and expertise to manage as supplies are not directly consumed by patients, in the same way as medicines. Rather, diagnostics supplies are used to operate laboratory equipment and analyzers to detect pathogens and produce test results. Therefore, collecting and measuring actual commodity consumption data for evidence based procurement and supply decisions are a growing challenge to the supply chain manager. In the absence of actual consumption information, analyzer operation data, quality control run data, electronic laboratory notebooks, and logbooks are proxies with excellent data for procurement and service delivery. Other ways of streamlining diversi ty and multiplicity of diagnostics supplies and improved data driven decision is by tiered harmonization, standardized test menus and optimized networks integrated with other health commodities supply sys tems.
3.0 Approaches to Laboratory Diagnostics Supply Chain
The current laboratory supply chain approach is disjointed and uncoordinated . Supply chain managers lack appreciation of the uniqueness of laboratory commodities procurement. For example, whereas procurement regulations (e.g., ADS 312) encourage competition, price comparison, and diversify sources; most laboratory reagents are “closed systems” bringing it in direct conflict with procurement regulations. Closed systems work the same way as branded products because reagents, consumables, and accessories for one manufacturer’s equipment cannot be used on the another. In the comm ercial world, Apple® accessories and parts cannot be used on Samsung® smartphones Consequent to this inequity, unskilled procurement managers tend to neglect appropriation and sourcing of lifesaving reagents leading to long lead time and chronic stock out.
3.1 Resilience, agile and localized laboratory supply chain
i. Integrate diagnostics commodities into national supply chain strategies Global health supply chain actors must include diagnostics services in national health supply chain strategies. Typically, this would involve a joint design workshop with extensive stakeholder consultations, including laboratory professionals, who are skilled in the use of and application of commodities for each type of test, to outline procedure and standards menus of services. Some Africa countries, including Zambia, Zimbabwe, Nigeria, Rwanda, Uganda, and Tanzania have successfully adopted this approach, allowing laboratory professional to assume leadership of diagnostics supply chains within the national health strategy
ii. Adopt and Implement diagnostics network management (DNM) Laboratory Diagnostics Network Management begins with standardization of national test menus and align with harmonized tiered network levels to address variations and complexity of testing services (5 and 6). Network optimization management allows visibility to testing demand, instrument utilization, and inventory management within the network. Nations adapting network

5
optimization have successfully reshaped priorities, align with funding priorities, and reduced redundancies for efficient management of their laboratory supply chain.
iii. Transition to multi diseases analytical equipment, analyzers and point of care integration. Moving from one disease to multi diseases emerging technologies that can detect multiple pathogens reduces redundancies in instrument procurements. For instance, using the same PCR (Polymerase Chain Reaction) machine to detect HIV viral load, syphilis, TB resistance, and HPV (Human Papilloma Virus) present added advantage of dealing with recognized brands and eliminate duplicity and subsequent reduction in number of commodities to manage. Using reliable integrated machines helps procurement managers to negotiate long term, volume based pricing with prequalified ven dors to realize cost efficiencies and reduce stock outs
iv. Engage local private providers into national network Public and private service providers have segregated their services to the detriment of their population. The private sector has successfully rolled out demand driven solutions worth replicating in the public sector . For example, national insurance schemes, standardized test costs, volume prices and equipment rental agreements have been used in the private sector with proven success. Private public engagement in laboratory services is therefore essential to fulfill the healthcare needs of populations in lower and middle income countries.

4.0 Conclusion
Diagnostics laboratories played a significant role during the COVID 19 pandemic. Supply chain management is a major driver of timely availability of essential reagents, eliminate stock out and prevent service disruption. The practice of disjointed and parallel procurement of one health commodities to the detriment of the other is dated. Transformative integration of diagnostics services into national supply chain strategies, adopting network optimization, moving to emerging multi disease technologies and engaging private sector are essential approaches towards attaining universal health care goals .
6
References:
1. Webster, P., (2018). PRPFAR at 15 years. The Lancet World Report. Vol. 239 (10143) pg.200. Available at: https://doi.org/10.1016/S0140 6736(18)31642 8 accessed July 31, 2022
2. Adepoju, P. (2022). New Leadership for PEPFAR. The Lancet World Report. Vol. 9 (8) pgs. E530 531. Available at: https://doi.org/10.1016/S2352 3018(22)00200 4. Accessed July 31, 2022
3. In vitro diagnostics Global (who.int)

4. Umaru, F. (2020). Scaling up testing for COVID 19 in Africa: Responding to the pandemic in ways that strengthen health systems. African Journal of Laboratory Medicine. Vol 9(1) a1244. Available at: https://doi.org/10.4102/ajlm.v9i1.1244
5. Alajimi, A., Adlan, N., Layhiyan, R. (2021). Assessment of supply chain management resilience within Saudi medical laboratories during COVID 19 pandemic. Procedia CIRP 103 (2021) 32 36. Elsevier B.V. available at: https://10.1016/j.procir.2021.10.004 Accessed July 31, 2022
6. Williams, J., Edgil, D., Wattleworth, M., Ndongmo, C., Kuritsky, J. (2020). The network approach to laboratory procurement and supply chain management: Addressing the system issues to enhance HIV viral load scale up. African Journal of Laboratory Medicine. Vol 9(1, a1022). Available at: https://doi.org/10.4102/ajlm.v9i1.1022 Accessed July 28, 2022.
7
The Impact of Rising Inflation on Employee Benefits 2022

8
The Impact of Rising Infation on Employee Benefts 2022

9
Introduction
As price infation in many parts of the world reaches levels not seen for 40 years, the impact is being felt across the economy – and the world of employee benefts is defnitely not immune. This is unchartered economic territo ry for most companies with many factors combining to make it very diffcult to navigate.
Firstly, as we emerge from the shadow of the global pandemic, the health and wellbeing of employees is a priority for all employers and we have seen many of our clients beginning to enhance their beneft programs to ensure all employees and their families have the support they need.
Secondly, strong global economic growth in the months coming out of the pandemic has led to talent shortages in many industries driving up salaries (which is one driver of high price infation) with a knock-on impact for employee benefts that have a link to those salaries.
Finally, governments and central banks are trying to bring infation under control by raising interest rates which is slowing economic growth and putting further pressure on employers to save costs. Rising interest rates will also have an impact on pension costs and premium rates.
The situation is complex and fuid. Responses from organizations have tended to be reactive, and vary signifcant ly by industry, geography, and company. There are also numerous organization-specifc factors which infuence the decisions being made - such as cost-base, proft margins, risk appetite, and wider people strategy - but there are some common trends emerging both from Aon clients and the wider market.
In this paper we summarise the key impacts of infation on the full spectrum of employee benefts and what em ployers can be doing to mitigate this impact.
i e Infation o n t e o l
High infation is affecting all regions around the world, with the exception of Asia. Rising energy prices, rising sal aries and supply chain issues are the primary factors driving the high infation and the more exposure an economy has to these factors then the higher the infation is likely to be.
e Infation Impa t
Talent and Pay
Infation and salary growth are intrinsically linked. Historically, high infation has driven corresponding wage increases; and it is expected that as companies navigate macro-economic conditions wages will increase – but potentially not as fast or high as infation measures. However, for many employees, their real income may still be lower on a net basis. 2021 saw some signifcant increases in salaries due to talent scarcity along with unprecedent demand for hiring. This has been compounded by low unemployment levels and increased talent mobility.
The cost of retaining and attracting good talent has inevitably increased. Invariably, this is sector-specifc; not all companies are able to support salary adjustments due to higher fxed cost-base or a reduction in income as a result of decreasing consumer buying power. As rising living costs start to impact consumers, discretionary spend decreases – for example, we are seeing some global technology frms starting to take early intervention to reduce costs by cutting headcount.
10
Medical Benefts
In this paper we are not considering the impact of “medical trend” as this is an important topic in its own right which is dealt with in Aon’s annual medical trend study. Insured medical benefts are a key beneft for employees and their families and we continue to see employers (particularly in segments with talent shortages) increasing these benefts and expanding coverage in many markets around the world.
Medical insurance providers, administrators (and intermediaries managing the plans) will be affected by the overall infationary increases on their own core businesses (salaries, energy prices, etc) and so administration and other premium loadings are likely to increase. Rising interest rates have a minor effect on medical insurance pre miums as insurance companies do not hold large reserves to support these plans. From a beneft design perspec tive, the changing talent agenda has led to an increased focus on diversity, equity and inclusion (DE&I) initiatives like family forming benefts, mental health and chronic condition support, and expanding virtual care to a wider range of practitioners such as mental health clinicians and physiotherapists. In addition, the rise in mental health claims may lead to increases in maximum beneft levels available, a wider array of eligible practitioners, a shift towards virtual solutions and a greater uptake of mental health frst aid training for employees.
Pensions
Note: The impact of infation on pensions is complicated, and will differ by location and pension scheme type. The below is only a high-level, global, summary. For the majority of companies their defned beneft balance sheet position has improved as a result of rising inter est rates, despite current high infation and the recent market downturn. This is because DB benefts are longterm and the market expectation is that the current high levels of infation will be relatively short lived (or for many countries the pension benefts are not infation linked).
These signifcant rises in global interest rates have led to a reduction in defned beneft service costs, offsetting the negative impact companies may be seeing in their P&L (proft and loss) from rising healthcare costs. As a result of balance sheet improvements, some companies are in the unexpected position of being able to remove DB balance sheet risk entirely through the purchase of insurance with no additional funding. Indeed, many multi national organizations now have surplus assets trapped in their defned beneft pensions schemes which they are looking to use either to improve benefts for members struggling with cost of living increases or, in more cases, take back into the business.
From a beneft design perspective, we are yet to see changes in approach. In other words, we are not seeing organizations providing increases that are higher than those required or those that have become customary through prior discretionary practice. In most countries employees have the option to access their pension early if they need additional funds over the next 12 to 18 months. However, this could lead to a lack of savings in later life, particularly if they are drawing on DC (defned contribution) funds at a time when equity markets are low. Instead of encouraging this, some companies have agreed they will continue to pay the maximum company pension con tribution even if employees need to stop paying their own contributions as a result of stretched fnances.
Risk Benefts (Life, Accident, Disability)
In this paper we are not considering the impact of “medical trend” as this is an important topic in its own right which is dealt with in Aon’s annual medical trend study. Insured medical benefts are a key beneft for employees and their families and we continue to see employers (particularly in segments with talent shortages) increasing these benefts and expanding coverage in many markets around the world.
Medical insurance providers, administrators (and intermediaries managing the plans) will be affected by the overall infationary increases on their own core businesses (salaries, energy prices, etc) and so administration and other premium loadings are likely to increase. Rising interest rates have a minor effect on medical insurance pre miums as insurance companies do not hold large reserves to support these plans. From a beneft design perspec tive, the changing talent agenda has led to an increased focus on diversity, equity and inclusion (DE&I) initiatives like family forming benefts, mental health and chronic condition support, and expanding virtual care to a wider range of practitioners such as mental health clinicians and physiotherapists.
In addition, the rise in mental health claims may lead to increases in maximum beneft levels available, a wider ar ray of eligible practitioners, a shift towards virtual solutions and a greater uptake of mental health frst aid training for employees.
11
Perquisites, Leave and Wellbeing
These traditionally less prominent benefts are often overlooked but in the current climate they can be incredibly valuable to employees looking to optimise their outgoings. This is covered more in the Conclusions section and we have seen a steady increase in employers providing access to discount portals or voluntary insurance products. In some parts of the world – notably the Middle East and parts of Asia – housing and other allowances are common and there is a lot of pressure for these to increase in line with the overall infationary trends.
In the past few years, wellbeing has become a critical component of people strategy and is now a top priority for all leading organizations. While we see fnancial wellbeing emphasized in the current climate, other areas of well being will continue to be high on the agenda of those companies seeking to lead their markets. Employers are in creasingly seeking to capitalize on low-cost beneft opportunities that can deliver an out- sized positive impact for their employees; for example, low-cost wellbeing apps that support employees with their physical and psychologi cal wellbeing along with integrating fnancial wellbeing through the inclusion of pension and insurance support.
ppo tin Employees ana e t e Infationa y Impa t
Employees are invariably feeling the fnancial impact; how can employers provide appropriate support, whilst balancing rising business costs?
A focus on reinforcing employee resilience is more important than ever, as people face tough economic condi tions both in their work and personal lives. Each organization is different and our advice to clients is typically anchored around the following:
1.Undertake regular employee research
Understanding your workforce needs can help you tailor your strategy into providing better support. Employee surveys and focus groups – across different segments and different geographies – will help you build a compre hensive picture of how your existing benefts are performing and any gaps that need attention. The research can also be used to assess the impact of a new beneft post implementation.
2.Review your fnancial wellbeing strategy and benefts
When compensation budgets are tight, companies can implement cost-effective approaches to help employees better manage their money. Running fnancial education sessions, better signposting to available existing benefts and pivoting to benefts which have an immediate impact on their personal fnances – such as retail discounts, childcare support and lower-cost insurance benefts – can all provide some immediate relief.
The link between poor fnancial wellbeing and mental health should not be overlooked. Employees struggling with their fnancial health are more likely to have poor mental health; people experiencing mental health problems are three and a half times more likely to be in problem debt than people without mental health problems. Compa nies should ensure that all employees are aware of Employee Assistance Programmes and any available mental wellbeing support. One way of improving fnancial wellbeing is the use of fnancial technology; apps such as Well One Money are available to employers to cement their fnancial wellbeing programs. By providing an aggregat ed overview of an individual’s fnancial situation, it can help users understand both their everyday spend and their holistic short-term and long-term fnancial health. The use of machine-learning and Artifcial Intelligence is embedded within the platform to help users identify saving opportunities and provide an alert if fnancial activity does not align with pre-populated goals.
3.Engage employees with their benefts and improve utilization
In a competitive employment market with tight salary budgets employers should consider the full experience that employees experience from their reward programs. It’s important to meet employees where they are. From bene fts awareness, through to access and service delivery, the experience of utilizing corporate programs should be seamless. A global technology platform (such as The Benefts Solution) can help multinationals create a consist ent experience in a user-friendly way, whilst virtual delivery can provide support to employees when they need it. Businesses should also consider how inclusive their benefts are for a diverse workforce – do all your employees and families have equal access to the programs your company offers? Utilizing voluntary benefts platforms where employees have the fexibility to choose the benefts that ft their lifestyles can provide better outcomes and achieve higher engagement than a one-size-fts-all approach.
12
on l sions a i atin is Infationa y to m
We are in an unprecedented infationary environment that comes straight on the back of a global pandemic that has transformed the way organizations and economies operate. The future outlook is also unknown and volatile. What is clear is that organizations, their leaders and their employees will need to remain agile and resilient to nav igate the coming months successfully. Each organization will face a different set of challenges but our advice to clients in mitigating the impact of infation on employee benefts is anchored around the following three areas:
1.Get the basics right
Ensure your beneft spend is optimized. There are a number of factors associated with beneft spend that an em ployer can control and these need to be managed tightly in the near term.
The list of actions here is long but all are important; ensure fees and expenses are in line with market rates, elimi nate duplicate coverage, review benefts regularly to ensure they are at market levels, review utilization of benefts to ensure value, look at fnancing solutions like multinational pooling or captives to capture global scale and make sure decisions about benefts are taken with appropriate governance.
Aon acts as a global benefts partner to hundreds of multinationals and our primary task is to make sure our cli ents are getting these basics right.
2.Defne your strategic position and pursue it
The last few months have shown many companies that there is always a competitor that is willing to pay more and chasing the market is an unsustainable strategy. Our advice to clients is to set a talent, reward and benefts strategy that is aligned to your business culture and then align the tactical programs with this.
We are seeing organizations place a much greater focus in their core business on DE&I and ESG but their beneft programs are not always aligned to support this. Ethnic minorities, low paid employees, women, disabled employ ees report facing more serious issues across several areas in the current environment — notably, they are more likely to report not having enough emergency savings. Benefts play a critical role in ensuring that corporate strat egy trickles down to make a positive impact on employees.
We are helping organizations review their beneft programs against these priorities and then drive their alignment. In many cases the changes to the beneft plans cost very little but have a huge impact on employee perception of the overall beneft program.
3.Put wellbeing at the heart of your beneft strategy
Prior to the pandemic wellbeing was typically seen as a perquisite or a top-up to the main beneft program, but we have seen a revolutionary shift as wellbeing and preventative healthcare grows increasingly prioritised. Aon is advising clients to be at the centre of why they provide employee benefts and each beneft program should have a clear link back to improving employee wellbeing.
Financial wellbeing is critical in this infationary environment and there are a number of relatively small and cost-effcient benefts that can be provided to employees that can make a big difference. The rapid development in the use of technology in this area has led to app-based solutions that can be integrated into the main suite of beneft programs.
Aon is working with companies to review and set their wellbeing strategy and also ensure they are making the most of the tactical programs that are on offer.
Sources:
Ethnic minorities: Commission on Race and Ethnic Disparities: The Report - https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_ data/fle/974507/20210331_-_CRED_Report_-_FINAL_-_Web_Accessible.pdf
https://www.hsph.harvard.edu/news/press-releases/poll-high-u-s-infation-rates-are-having-a-more-serious-impact-on-black-americans-than-white-americans/ Low paid employees: https://www.tuc.org.uk/blogs/tale-two-pandemics-low-paid-workers-hit-hardest-covid-class-divide
Women: https://www.cnbc.com/2019/11/18/women-are-still-lagging-behind-men-when-it-comes-to-saving.html
Disabled employees: https://www.bristol.ac.uk/news/2022/september/disabled-households-and-cost-of-living-crisis.html
13
Contact Us Carl Redondo Global Benefts Consulting Leader carl.redondo@aon.com Janet Faircloth Senior Vice President janet.faircloth@aon.com Doug Ries Global Broking Chief Strategy Offcer douglas.ries@aon.com Olly Walker Senior Partner oliver.walker@aon.com John McLaughlin Chief Commercial Offcer, EMEA Dr Avneet Kaur Head of Advisory and Specialty Practice EMEA avneet.k.kaur@aon.co.uk Jill Malila Senior Vice President jill.malila@aon.com
Aon plc (NYSE: AON) exists to shape decisions for the better—to protect and enrich the lives of people around the world. Our colleagues provide our clients in over 120 countries with advice and solutions that give them the clarity and confdence to make better decisions to protect and grow their business. ©2021 Aon plc. All rights reserved. Aon UK Limited is authorised and regulated by the Financial Conduct Authority. Registered in England and Wales. Registered number: 00210725. Registered Offce: The Aon Centre, The Leadenhall Building, 122 Leadenhall Street, London EC3V 4AN. Copyright 2022 Aon UK Limited. 14
About

15
Understanding Cybersecurity Maturity Model Certification (CMMC) 2.0 Compliance

GUIDE Understanding Cybersecurity Maturity Model Certifcation (CMMC) 2.0 Compliance A Government Contractor’s Guide to Preparation and Assessment Basics TABLE OF CONTENTS The History of CMMC The New Maturity Level Guidelines Key CMMC Players Day-to-Day Impact for Government Contractors Preparing for CMMC 2.0 2 3 4 5 6 16
The History of CMMC
The Cybersecurity Maturity Model Certification (CMMC) was created to safeguard sensitive unclassified information across the Defense Industrial Base (DIB) by addressing the gaps in prior regulatory requirements. The Department of Defense (DoD) found that private sector organizations doing business with the federal government were not satisfying the requirements specified in Defense Federal Acquisition Regulation Supplement (DFARS) 252.204-7012. The requirements included implementation of National Institute of Standards and Technology (NIST) SP 800-171 for systems processing Covered Defense Information, but did not include official certification or compliance reporting mechanisms. This resulted in organizations not fully implementing controls to a consistent maturity level, ultimately putting the government supply chain at risk. Since an official certification or compliance reporting mechanism did not exist, many companies fell short of their security control obligations, putting the government supply chain at risk.
DFARS 252.204-7021, published Sept 29, 2020, introduces CMMC, which was intended to introduce a tiered standard based off data sensitivity as well as a certification component, validated by external auditors, to assess organizations’ controls against a variety of compliance standards.
Driven by feedback across the industry, CMMC has since reworked into a hybrid certification model. This new version, referred to as CMMC 2.0, was announced on

November 4, 2021. The changes are intended to reduce barriers to compliance for small and mid-sized firms while maintaining the goal of protecting the Defense Industrial Base from cyber attacks. CMMC 2.0 focuses on the most critical requirements and streamlines the model from 5 to 3 compliance levels.
CMMC addresses requirements for the protection of FCI and CUI data:
• Federal Contract Information (FCI) - Information not intended for public release. It is provided by or generated for the government under a contract to develop or deliver a product or service to the government. FCI does not include information provided by the government to the public.
• Controlled Unclassified Information (CUI)Information the government creates or possesses, or that an entity creates or possesses for or on behalf of the government, that a law, regulation, or governmentwide policy requires or permits an agency to handle using safeguarding or dissemination controls.
As stated by Acquisition & Sustainment, Office Under the Secretary of Defense, CMMC 2.0 requires that companies entrusted with national security information implement cybersecurity standards at progressively advanced levels, depending on the type and sensitivity of the information. The program also sets forward the process for information flow down to subcontractors.
Understanding Cybersecurity Maturity Model Certification (CMMC) 2.0 Compliance
17
The New Maturity Level Guidelines
CMMC 2.0 streamlines the maturity model from 5 to 3 compliance levels:
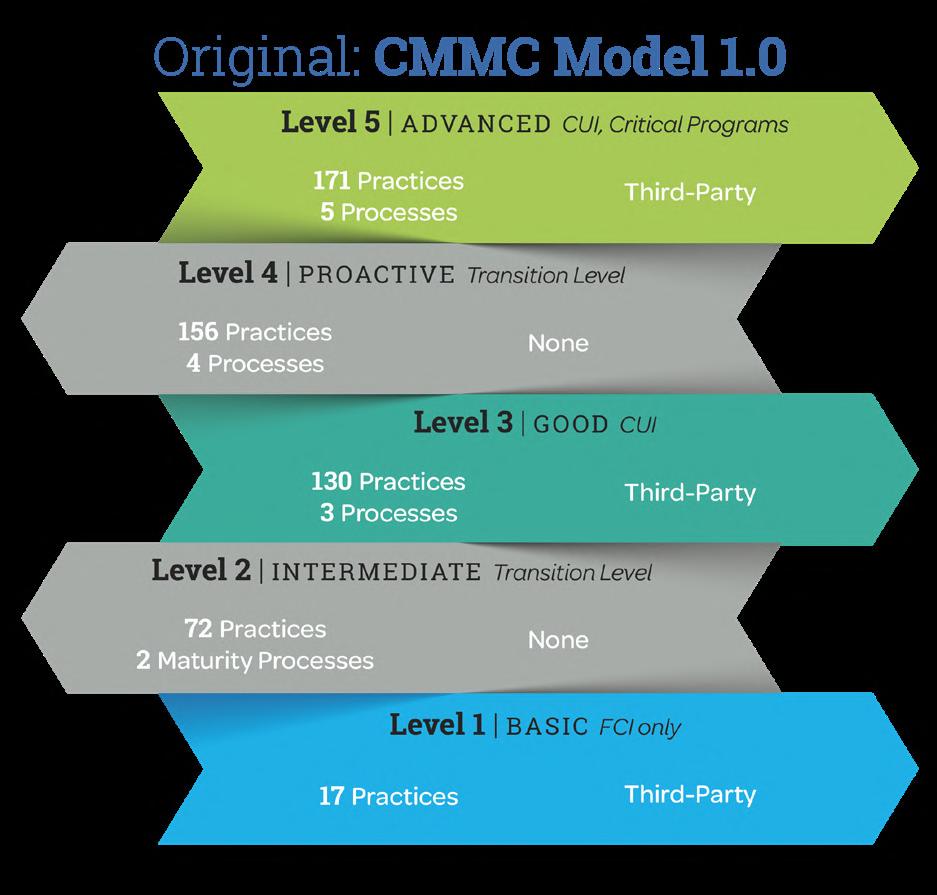
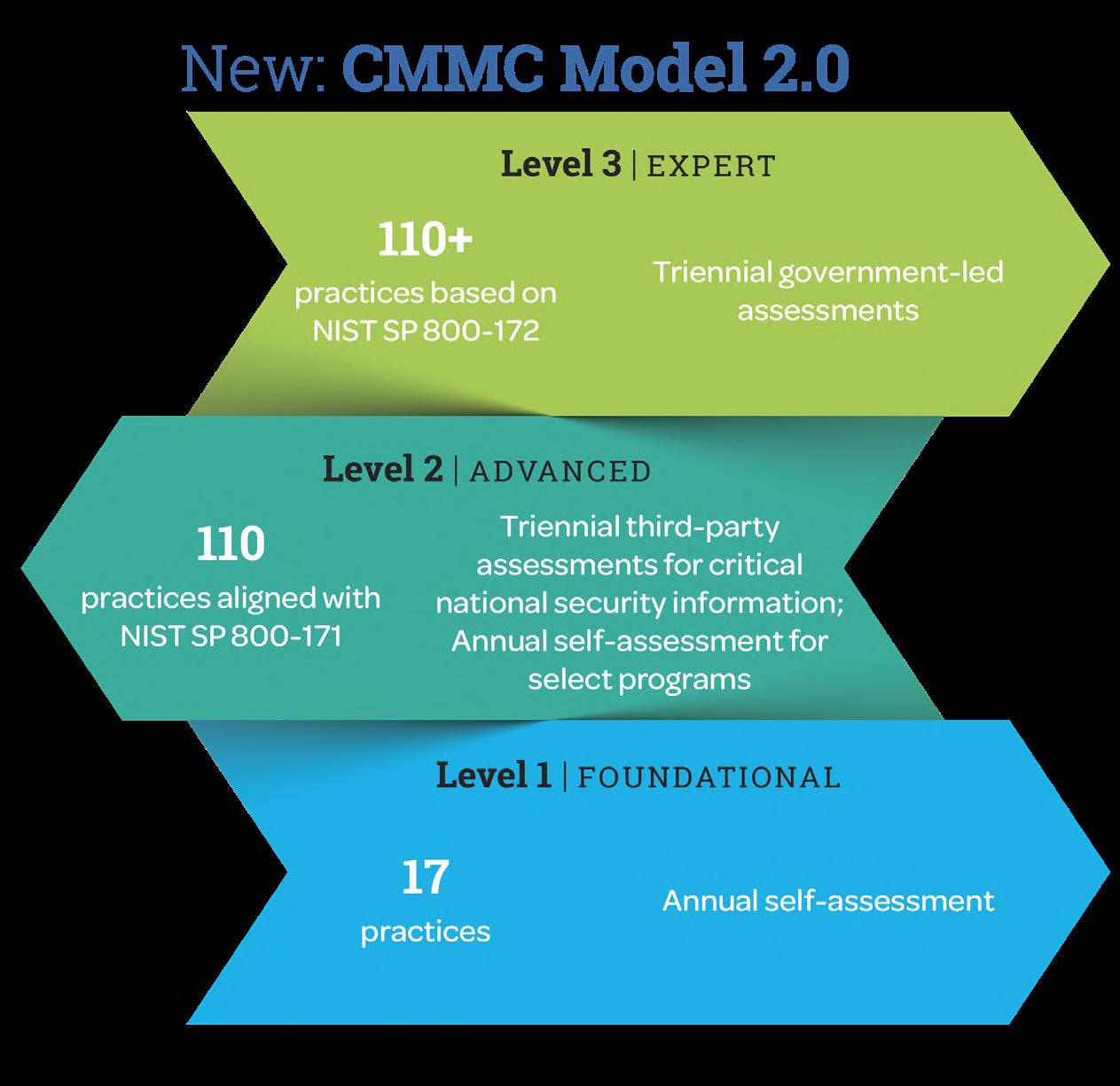
• Maturity Level 1 – Foundational, which allows organizations to conduct self-assessments, against FAR 52.204-21.
• Maturity Level 2 – Advanced, includes 110 practices from NIST SP 800-171 and allows for self-assessment for Controlled Unclassified Information (CUI), but requires Certified Third Party Assessment Organization (C3PAO) to conduct assessments when working with sensitive controlled information.
• Maturity Level 3 – Expert, requires CMMC 2.0 L2 C3PAO certification, adds NIST SP 800-172, and requires an assessment from the DoD when working with the most sensitive controlled information
*The New CMMC 2.0 Maturity Levels Map Directly to NIST 800-171 Controls.
The Maturity Level certification requirements will be driven by the type of data being stored to support a contract with the DoD. In general FCI and basic CUI such as government-provided PII and financial data will require Maturity Level 1 certification. More sensitive covered defense information (CI) such as purchase orders, parts lists, and inventory may require Maturity Level 2, and technical documentation such as a blueprint for the F18 program which may Maturity Level 3. Contracts will be required to specify the CMMC Maturity Level needed to work with any government information provided or created as part of a contract.
The DoD has adjusted and streamlined the CMMC accreditation program with CMMC 2.0. This new version will be focusing on the most advanced cybersecurity standards while minimizing barriers to compliance. This new approach will require additional accountability for organizations to implement critical cybersecurity standards to meet the challenges of evolving threats and take the necessary steps to protect national security information.
Understanding Cybersecurity Maturity Model Certification (CMMC) 2.0 Compliance
18
Key CMMC Players
Assessors: Individuals who have successfully completed the background, training, and examination requirements as outlined by the CMMC Accreditation Body (AB), and to whom a license has been issued. Assessors are not employed by the CMMC-AB and may or may not be employed by the Certified Third Party Assessment Organization (C3PAO).
Certified Third Party Assessment Organization (C3PAO): An entity with which at least two assessors are associated and to which a license has been issued to engage with organizations seeking certification (OSC) to complete their associated CMMC assessment.
CMMC Accreditation Body (AB): The accreditation body that establishes and oversees a qualified, trained, and highfidelity community of assessors that can deliver consistent and informative assessments to participating organizations against a defined set of controls/best practices within the CMMC program.
Organizations Seeking Certification (OSC): The organization that is going through the CMMC assessment process to receive a level of certification for a given environment.
Cloud Service Providers (CSP): A third-party company offering a cloud-based platform, infrastructure, application, or storage services. CSPs may be storing sensitive unclassified information that is subject to CMMC certification. government websites to focus on the most important areas of the project and deliver the most relevant, actionable information directly to you, in language that you understand.

2.0
Understanding Cybersecurity Maturity Model Certification (CMMC)
Compliance
19
Day-to-Day Impact for Government Contractors

Most organizations fulfilling government contracts for the DoD will need to address CMMC requirements in requests for information (RFIs) and requests for proposal (RFPs) bids for DoD acquisitions, with the potential exception for commercial items.
The various cybersecurity standards and best practices upon which the CMMC is based are largely self-certified. The CMMC represents a major change to that by introducing the C3PAO requirement to review systems and processes for certification. To standardize this process, the DoD established the non-profit, independent organization, CMMC-AB, to define the assessment and administration needed for certification. Currently, the CMMC-AB is in the process of licensing assessors and the firms that will serve as C3PAOs.
Government contractors will initially see DoD requirements to satisfy Maturity Levels 1 and 2 for anyone handling FCI or CUI. The majority of contractors will need to certify first at Maturity Level 1 and then Maturity Level 2. Maturity Level 3 will be required for organizations working with the most sensitive CUI or confidential data, however, it will be required to first certify at Maturity Level 1 and Maturity Level 2 before Maturity Level 3. Maturity Level requirements will be specified in contracts and are expected to flow down only to subs that are working with the controlled information. Therefore, it is important to know what type of data you are storing. Once an organization is CMMC certified, the certification is expected to be valid for three years.
Understanding Cybersecurity Maturity Model Certification (CMMC) 2.0 Compliance
20
Preparing for CMMC 2.0
To ready their organizations, government contractors should ensure they cover the following steps.
• Step 1 – Identify and classify the type of data you store to support existing or new contract awards.
• Step 2 – Understand the Maturity Level your firm will likely need to satisfy based on the type of data you store and identify the gaps that could prevent achieving certification.
• Step 3 – If you are unsure and work with CUI, start with Maturity Level 2, based off the 110 controls from NIST 800-171.
• Step 4 – Make sure you have the documentation of formalized processes and controls.
• Step 5 – Be familiar with all of the major definitions and compliance standards that make up CMMC 2.0.
Better software means better projects. Deltek is the leading global provider of enterprise software and information solutions for project-based businesses. More than 23,000 organizations and millions of users in over 80 countries around the world rely on Deltek for superior levels of project intelligence, management and collaboration. Our industry-focused expertise powers project success by helping firms achieve performance that maximizes productivity and revenue. www.deltek.com
US & Canada 800.456.2009 UK +44 (0) 20 7518 5010 EMEA + 45 70 20 33 18 APAC/AUNZ +61 2 9911 7740
© Deltek, Inc. All rights reserved. All referenced trademarks are the property of their respective owners. REV-040422 - 17890
21
Questions? Contact us today
The Challenging Road to Securing the Perimeter

22

The Challenging Road to Securing the Perimeter Zero Trust in a Changing World 22-Leidos-0223-24101 | 22-504900 | Leidos Creative 23
The COVID-19 pandemic, as well as recent highprofle cybersecurity breaches, has rapidly shifted the computing environment away from traditional architectures where heavily defned and defended perimeters kept networks, data and users safe. Instead, computing today has evolved to operate within a fully distributed environment where boundaries no longer exist, and where the majority of government employees work from home using their own personal devices. Nothing could make clearer the idea that the network perimeter is quickly becoming obsolete.
Government and industry thought leaders recently discussed this evolving security environment on Government Matters, sharing their insights on how to adapt and utilize zero trust protocols to strengthen their assets and protect their users.
Government Agencies Are No Longer Castles and Moats
“It used to be that the perimeter was the castle wall. That was where all the attacks were going to be stopped, and everything on the inside was good and trusted,” said Scott Rose, a computer scientist at the National Institute of Standards and Technology (NIST). “If you were inside, if you got inside, you could then access everything else that was inside.”
Rose is one of the authors of NIST’s Special Publication on Zero Trust Architecture. He said that work began on defning a structure for zero trust at the Federal CIO Council.
The signifcance of zero trust is that communications between devices internally or on-premises are no more trusted than something coming from outside on the internet. The same set of security policies are applied and checks performed before any communication is opened, regardless of the source. That way, an enterprise can enhance its protections against cyberattacks from within, where an increasing number of breaches originate.
Steven Hernandez, Chief Information Security Offcer with the U.S. Department of Education agreed. “The perimeter is rapidly evolving, that’s the best way to describe it,” he said. “Where before we were very much the castle moat, and then hopefully not a soft interior...that model’s been turned inside out.”
And it’s not just government that is embracing zero trust, although it’s critical for most agencies. “World enterprise IT is broken into the world of service providers and [the world] of service consumers,” said Peter O’Donoghue, Civil Group CTO, Leidos. “What zero trust really attempts to do is govern the connection of the consumer to the provider; it looks at the data and applies policy...to make decisions in real time.”
Know Where to Begin with Zero Trust
NIST’s Rose suggested that agencies invest the time to fgure out where to get started. Implementing zero trust calls for an incremental approach rather than a “big bang,” by identifying the right use cases and users.

“We see that the agencies and departments that are doing particularly well are the agencies that have already started thinking through, ‘Okay, I really need to modernize my ICAM [identity, credential and access management] solution. I need to recognize that my identity repositories need to be cloud-ready.’ And they actually have gone through that kind of cleansing and hygiene process to make them really supportive for cloud,” he said.
Ross said there are two critical use cases for zero trust that NIST has seen.
LEIDOS / THE CHALLENGING ROAD TO SECURING THE PERIMETER
24
“The frst is the worker from home dealing with the pandemic or post-pandemic issues, where the VPN architecture...was never really sized or scoped for what just happened,” he said. “Actually trying to provide a better experience for workers from home, providing frankly, a more cost-effective experience and taking the friction out of it, while also improving the integrity, that’s clearly one set of use cases.”
The second set of important use cases is based on getting past the view that departments and agencies are monolithic.
“The reality is that oftentimes organizations and agencies need to collaborate heavily with peers. For example, when I’m wanting to share information, I want to pass data or information or videos or fles. That type of interagency use case is also an excellent application for an early project related to zero trust,” Rose said.
Security for Everyone Across the Board
Hernandez suggested that different groups of employees in a variety of positions, with different responsibilities, who are using various kinds of technologies, need what he termed “equitable security.” In an equitable security model, cybersecurity takes more of a holistic approach to defenses rather than relying on specifc products such as a frewall to protect the perimeter.

“What that means is really getting down to, are we talking about technology, or are we talking about outcomes?” he asked. “Oftentimes, we get caught up in this idea that we need a certain technology to provide a certain solution, when actually, in reality we need an outcome.”
Hernandez said the rapid changes imposed by the events of the past year or more have led cybersecurity professionals to focus on the two most important outcomes – protecting users and agency data. He suggested that all future discussions about cybersecurity and protection should at least initially focus on keeping data and users safe, and then see what technologies can help to achieve those goals without any preconceived notions.
Hernandez noted that one major component of the new security landscape is the focus on using zero trust architecture to ensure users’ protection. He recommended the NIST guidance as a good starting point. It is necessary to look at system architecture in completely new ways. “For example, instead of a stationary house I want a big RV, so I can move my home wherever. Before we had guards at each entrance and exit. We have an open foyer now, but we’re using other programs to identify people as they come in and out. They have wireless technology with their badges; we know who all the employees are, and we know who are not.”
LEIDOS / THE CHALLENGING ROAD TO SECURING THE PERIMETER
25
Leidos’ O’Donoghue noted that there is an inherent mindset shift required to adopt zero trust.
“I harken back to the days when we were frst moving to private clouds and...we used to kind of worry about what we called server-huggers,” he said. “Part of what they were resisting was their fear about what the unknown was like. I feel the same thing is true for zero trust as a concept. Trust has to be built that all this technology is going to work.”
Zero Trust Can Be Implemented Anywhere
Renee Wynn, former Chief Information Offcer of NASA, suggested that agencies need to consider supply chain risk from a cyber perspective, to ensure that nation-states aren’t using the supply chain to attack their networks, or use their networks to get into another federal agency. NASA has done this with its space-based assets, which is one of the most challenging computing environments in the world.
“The United States’ infrastructure depends upon satellites’ basic locations. Weather satellites are relied upon for military operations as well as logistical operations, moving stuff around the globe, things like that,” said Wynn. “So speaking of updated operating systems and devices millions of miles away, cybersecurity in space is a very serious issue. There’s been a lot of rethinking that space is, in fact, a cyber [environment], and we need to start investing in cyber protections in space.”
Using robotic processing automation and artifcial intelligence to look for risk – behaviors out of the norm, for instance – bolsters cyber protection by providing insight “on data that is relevant and important to deal with, and data that is noise and just interesting,” she said. “So your security operation centers and your people can focus on the value, and the really important work of what is really going on within your network.”
Wynn promoted the value of zero trust as a way to improve security throughout the entire system, but noted that the federal budget cycle can make introducing the approach more diffcult.
“A lot of it comes down to the availability of funding associated with network infrastructures, because for a CIO and a CISO, you have many funding priorities that you need to deal with,” she said. “You begin with the architecture, that’s a fairly inexpensive project to sort of draw up where you need to go. But then you need to start changing out your hardware and software in order to do that. You do have your regular refresh cycles, which offer a natural opportunity for you to step in and change it over.”
The Time for Zero Trust Is Now
The federal government has never faced a more challenging environment in terms of cybersecurity. With millions of federal employees and contractors working remotely and a serious uptick in advanced attacks and high-profle breaches, the old methods of perimeter security or relying on devices like frewalls to protect agencies will no longer work.
The federal government needs to embrace zero trust moving forward to protect its users, data and assets in today’s modern computing environment. On one hand, it makes practical sense from a modernized security perspective. One the other hand, recent legislation and executive action suggests zero trust architectures will soon be mandatory. But no agency needs to make that journey overnight or without guidance. In fact, zero trust is better implemented in stages so that the relatively huge undertaking is more manageable. Help can be found in places like the NIST Special Publication on Zero Trust Architecture and with experienced government contractors who have already helped agencies begin their zero trust journey.
With a methodical and thoughtful approach, zero trust can become a reality for any agency, regardless of how many users they serve, where their assets are located, or what kinds of technology they currently employ. The true danger is not getting started with the process of implementing zero trust, because the old defenses can no longer stand against today’s threats to protect the modern computing environment.
LEIDOS / THE CHALLENGING ROAD TO SECURING THE PERIMETER
26
WWW.PSCOUNCIL.ORG 27



 BY:
BY:

 BY DELTEK
BY DELTEK















