





Academic Authors: Jatinder Kaur, Ayushi Jain, Chandani Goyal, Kashika Parnami, Anuj Gupta, Simran Singh
Creative Directors: Bhavna Tripathi, Mangal Singh Rana, Satish
Book Production: Rakesh Kumar Singh, Sakshi Gupta
Project Lead: Jatinder Kaur
VP, Learning: Abhishek Bhatnagar
All products and brand names used in this book are trademarks, registered trademarks or trade names of their respective owners.
© Uolo EdTech Private Limited
First published 2023
Second published 2024
Third published 2025
This book is sold subject to the condition that it shall not by way of trade or otherwise, be lent, resold, hired out, or otherwise circulated without the publisher’s prior written consent in any form of binding or cover other than that in which it is published and without a similar condition including this condition being imposed on the subsequent purchaser and without limiting the rights under copyright reserved above, no part of this publication may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form or by any means, electronic, mechanical, photocopying, recording or otherwise, without the prior written permission of both the copyright owner and the above-mentioned publisher of this book.
Book Title: Tekie Computer Science 7
ISBN: 978-81-978912-7-4
Published by Uolo EdTech Private Limited
Corporate Office Address:
85, Sector 44, Gurugram, Haryana 122003
CIN: U74999DL2017PTC322986
Illustrations and images: www.shutterstock.com, www.stock.adobe.com and www.freepik.com
All suggested use of the internet should be under adult supervision.
Standing at the forefront of the digital and AI revolution, the importance of coding and computational skills has reached unprecedented heights. In today’s professional landscape, whether it is in the fields of medicine, space exploration, education, science, or business, no sector remains untouched by this transformative wave. To thrive in the 21st century, basic computer literacy is no longer sufficient. Learners must evolve into ‘digital natives’ who can fluently read, write, and communicate in the languages that machines and AI comprehend.
Recognising this imperative, the National Education Policy (NEP) 2020 has strongly recommended the integration of coding skills, computational thinking, critical analysis, and problem-solving abilities into the curriculum. Moreover, forward-looking subjects like AI, Data Science, Computer Applications, and IT have been introduced as elective subjects from grade 9 onwards. It wouldn’t be surprising if further transformative measures are taken even at the elementary education level.
Uolo has introduced an innovative 360-degree program for a coding-focused computer science curriculum, known as Tekie, spanning grades 1 to 8. Tekie is a significant stride towards STEM education that aims at making learners future-ready—enabling them with skills needed in the ever-changing, technology-driven, and dynamic 21st-century world.
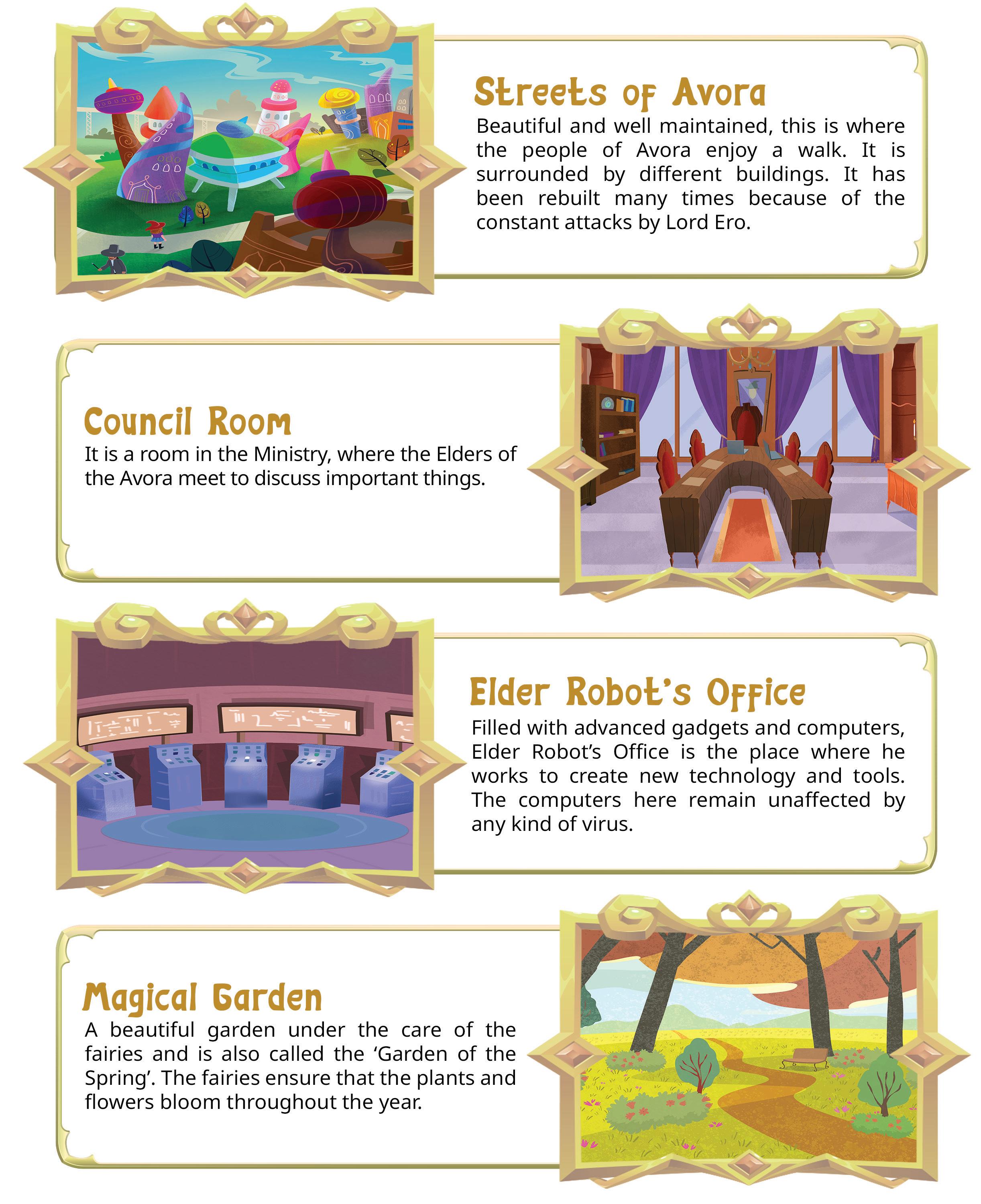
Tekie adopts a captivating and engaging approach to learning, in line with the recommendations of the National Curriculum Framework (NCF) 2023 and NEP 2020. The curriculum is ingeniously woven into the thrilling adventures of Mel and Conji, fictional characters from the enchanting land of Avora. The Mel and Conji series epitomises a modern method of acquiring computer science knowledge and honing computational thinking skills. The program includes chapters that provide a deeper immersion in computer science that both learners and teachers may find interesting.
Tekie is a technology-empowered curriculum that encompasses the following components:
• Main Content Books: These introduce learners to the theory of computer science and computer tools. Topics in AI are also covered, along with experiential and project-based learning resources.
• Coding Books: Specifically designed to nurture coding skills, this booklet aligns with the experiential and contextual learning approach of the coding curriculum, fostering critical thinking and problemsolving abilities.
• Animated Learning Videos: The program is powered by high-quality animation-based learning videos that deliver learning in an engaging manner.
• Teacher Manual: This valuable resource supports classroom instruction, ensuring that educators effectively deliver the curriculum.
Welcome to the captivating realm of Tekie! We hope you relish this educational journey as it equips you with the tools you need to thrive in the exciting and ever-changing world of the 21st century.
Tekie is an interactive, engaging, and experiential computer science program. It enables learners to attain mastery in computer science theory, new-age computer tools and coding. These are delivered through a storytelling-based coursebook and an experiential learningoriented coding book.
The learning experience is augmented by a digital platform that gives learners access to learning videos and experiential activities and projects that are rooted in the curriculum.
Engaging Textbooks
Comic Stories
Teacher Manual
Test Papers
Additional Projects
Test-paper Generator

Student and Teacher Platform
Learning Videos
Interactive Classroom and Homework Assignments
Byte-size Lesson Modules

The National Education Policy (NEP) 2020, introduced by the Government of India, represents a transformative shift in the country’s education system. It aims to create a more holistic, dynamic and multidisciplinary approach to education. The NEP highlights the need for early development of computational thinking, coding, and digital literacy as vital skills for students’ holistic growth. UOLO is fully committed to actualising the vision of NEP 2020 by meticulously adhering to its outlined recommendations.











1. Focus on conceptual understanding
2. 21st century skills, values, and dispositions
3. Computational and critical thinking
4. Application in real life
5. Holistic and integrated learning
6. Experiential learning
7. Enjoyable and engaging
8. Artificial intelligence and coding concepts
9. Digital literacy and emerging technologies
10. Factoids on India
Competency-based Education
NEP Pages 12, 17 and 22
Teaching and Learning Pedagogy
NEP Pages 3, 5, 11, 12 and 56
National Pride
NEP Pages 15, 16 and 43
11. Assessment of core concepts and application skills Assessments
NEP Pages 12, 18 and 22
Project-based Learning
Engaging hands-on projects encouraging practical application of computer science and coding
Story-based Approach
Enchanting tales that bring learning themes to life, making education a captivating adventure 5 7
Equipping the students with future-ready skills through exposure to the latest tools and technologies
Engaging activities to deepen students’ understanding and engagement with AI concepts
Test papers designed to evaluate understanding of core concepts and application of skills 3 4 11
Projects on the digital platform to deepen understanding and develop essential practical skills

Invites learners to discuss in small groups and present different perspectives
Story-style learning videos that deliver concepts to students.
Intellectually stimulating questions designed to encourage deep, analytical, critical, and evaluative thought process
Interactive quizzes that reinforce learning and assess students’ understanding
Think It Through
Probing question related to the concept that arouses curiosity
Tool to create customised assessments that align with the curriculum and help evaluate students’ progress effectively.
Artificial intelligence and coding concepts 9 Digital literacy and emerging technologies
Factoids on India 11 Assessment of core concepts and application skills
The National Education Policy (NEP) 2020 outlines essential skills, values, dispositions, and learning approaches necessary for students to thrive in the 21st century. This textbook identifies and incorporates these elements throughout its content, activities, and exercises. Referred to as “NEP Tags”, they are defined as follows:



INTEGRATED



Art Integration
Bringing creativity and fun into learning by combining music, drama, and art with other subjects CRITICAL

Sports Integration
Using games and sports in daily life to enrich computer-related activities
Cross-curricular linkages to make the learning experience more holistic, joyful and meaningful

SDG
Critical Thinking
Coding opportunities to apply higher-order skills like algorithmic and computational thinking, and problem-solving
Step-by-step activities to enable learners put theoretical knowledge into practice
Sustainable Development Goals
Applied computer science activities related to real-world issues and sustainable development

SEL Social Emotional Learning
Developing the skills to understand and manage emotions, build positive relationships with others and make responsible choices

The curriculum is thoughtfully mapped to introduce tools and technologies at each grade level, ensuring a smooth and progressive learning experience for students. Beginning with basic concepts in junior grades, the curriculum gradually incorporates more advanced tools and concepts in higher grades. This structured approach enables students to build on their knowledge each year, equipping them with essential skills in computer science and technology as they progress from grade 1 through grade 8. By the time they reach the higher grades, students are well-equipped to tackle complex projects, think critically, and apply their skills in real-world scenarios. The curriculum not only fosters technical proficiency but also encourages creativity, problem-solving, and a deeper understanding of the digital world.









































1

We
Theme Page: Lists the chapters covered under a unit



2
Comic Story: To introduce key concepts in a fun way
Did You Know: Interesting facts related to the topic
Discuss: A multi-faceted probing question related to the concept that arouses curiosity
4




3
Explore More: Short videos to find out more about the topic
Do It Yourself: Short exercises between the chapter to pause and assess comprehension
We see many things around us. Some things are present in nature like trees, animals, mountains, and rivers. These are called natural things.































Some things are made by humans. These are called human-made things. Buildings, cars, and umbrella are some human-made things.















































































Let us now learn to draw shapes in Paint.
Drawing an Oval
Follow these steps to draw an oval: 1. Open Paint and click on the Shapes group.
Project-based Learning: A project-based learning approach employed to foster an engaging and interactive learning experience

2. Click on the Oval shape. 3. After selecting the shape, go to the drawing area.

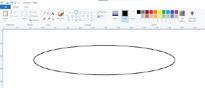
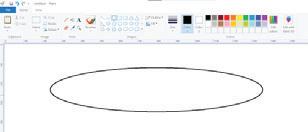
4. Hold the left mouse button, drag the mouse, and then release the mouse button. You will see that an oval has been drawn.
Points to Remember
smartphones.
Chapter Checkup: Chapter-end practice exercises aligned to different levels of Bloom’s Taxonomy
Points to Remember: Summary of the chapter

Apply your learning: Intellectually stimulating questions designed for higher-order thinking and analysis
Have you ever given a command to the speaker at your home to play a song, and it plays it?
Do you know what these speakers are known as?

These special speakers, which follow your voice commands, are smart speakers Smart speakers can do this because of AI.
What is AI?






AI stands for Artificial Intelligence
Artificial Intelligence: Chapters on Artificial Intelligence to explore the fundamentals of AI, including its principles and applications in various fields
It gives machines the ability to learn and do things on their own, just like humans do
AI Around Us
• Talking Toys: Some toys use AI to understand your voice and respond with sounds, songs, or even short sentences.

A. Fill in the blanks.
• Robot Helpers: These machines help us with daily tasks at home. They can clean floors, cook food, etc. They do work in the same way as a human does.
Fun with AI: Engaging AI activities designed to help students explore and apply AI concepts in practical ways




AI devices are all around us. There are many types of machines that use Artificial Intelligence (AI) to perform tasks or respond to us. Some examples of such AI devices are:

• Smart Speakers: These speakers respond to your voice commands. They use AI to understand your voice commands, like when you ask them to play music or tell you a story.
• Selfie Magic: Some phones use AI to edit your selfies. The AI can adjust lighting, smooth out backgrounds, or add fun filters.



Test Paper 1 (Based on Chapters 1 to 3)
Test Papers: Designed to evaluate understanding of core concepts and application of skills
1 Things that are present in nature are called
2 Some machines need to work.
3 Computers are used in to keep information of patients.
4 At restaurants, computers are used to order and pay for
B. Tick () the correct answer.
1 Which of the following is a human-made thing?
a Mountains b Trees
c Cars d Animals
2 Which machine helps us keep our food fresh?
a Refrigerator b Washing







• Creating a Spreadsheet
• Elements of a Spreadsheet
• Cell Naming
• Applying Formulas
• Functions
•
Database Management
• MySQL
Data Types in SQL
Types of SQL Commands
SQL Queries
• Introduction to Big Data
• Working with Big Data
• The Future of Big Data
• Fun with AI: Using Impact Filter
•
• How Do the Machines Learn?
• Types of Machine Learning
• Fun with AI: Using Teachable Machine
• Applications of Machine Learning
• Deep Learning • MIT App Inventor
•
•





We have learnt about measuring quantities in Science and Maths. We measure length in centimetres, metres, and kilometres. Similarly, we use grams and kilograms to measure weight.
But what do we use to measure and express these quantities? We use numbers.
But what are numbers made of? They are made of digits—0, 1, 2, 3, 4, 5, 6, 7, 8, and 9. These ten digits together form our Number System
A Number System is a way of representing and expressing numbers using a set of symbols or digits.
Different number systems can use different symbols and rules to represent a number in that number system.
The base of a number system is the total number of digits the system uses.
The number system that we use is the decimal system, also known as the base-10 system. The numbers are expressed using ten different digits: 0, 1, 2, 3, 4, 5, 6, 7, 8, and 9.

A question arises here: why do we need to learn about different number systems?
The answer is that the different number systems help us understand computers better as computers do not work on the decimal number system. We will later see which other number systems they work on.
Furthermore, learning about different number systems helps us to represent data in different number systems. They also help us to convert data represented in one number system to another number system.
There are four types of number systems that computers understand. Let us learn more about each one.
The Decimal Number System is the number system that we use every day.
The Decimal Number System is a base 10 number system that has combinations of the following 10 digits: 0, 1, 2, 3, 4, 5, 6, 7, 8, and 9.
When we deal with a decimal system, we write the base of the number system as the subscript of the number.
For example, if we want to write 70, 128, and 349 in a number system notation, we will write: (70)10, (128)10, and (349)10.
Digits used: 0, 1, 2, 3, 4, 5, 6, 7, 8, and 9.

The Binary Number System is a base 2 number system that uses only two digits—0 and 1. A binary number is called a Binary digit or a bit. We express binary numbers as (101)2, (1001)2, (101011)2, and so on.
Base is 2.
Binary Number System
Digits used: 0 and 1.
The Binary System forms the basis of data storage in computers. In fact, a bit is the fundamental unit of data storage. Different digital devices like calculators, TVs, cell phones, burglar alarms, and watches use this system. But how do these devices understand a bit?
Imagine you have a flashlight. It only has two buttons: one to switch it on and the other to switch it off. The state of an “on” flashlight is 1 and the state of an “off” flashlight is 0.
If we want to store this information:
The first flashlight is on and second one is off.
It can be depicted as “10”. This is how these digital devices store information using the Binary Number System.


Computers store data in binary form using electronic switches that can either be on (representing 1) or off (representing 0). This binary storage is the basis of all digital memory.
Acharya Pingala, a Vedic Scholar, was the inventor of the Binary Number System. Did You Know?

Each number in the decimal number system can be represented in the binary number system as well. This table shows the decimal numbers 0 through 15 in their binary forms:
The Octal Number System has a base of 8 and has eight digits: 0, 1, 2, 3, 4, 5, 6, and 7. We express numbers in the octal number system as (40)8, (214)8, (376)8, etc.
The Octal Number System is widely used in computer applications in the aircraft sector. The octal numbers are used in the form of codes.
Base is 8.
Digits used: 0, 1, 2, 3, 4, 5, 6, and 7.
Just like in the binary number system, all decimal numbers can be represented in the octal number system as well. This table shows the decimal numbers 0 through 15 and their octal forms:
The Hexadecimal Number System has a base of 16 and has digits from 0 to 9 and letters of the alphabet A to F, where A is 10, B is 11, and so on up to F as 15. We express numbers in this system as (CD)16, (129A)16, (A56)16, etc.
Letters used: A, B, C, D, E, and F. Base is 16.
Digits used: 0, 1, 2, 3, 4, 5, 6, 7, 8, and 9.
Imagine that you have a special way of counting on your fingers. Instead of just using your regular 10 fingers, you have 16 different symbols to count with. The first 10 symbols are just like your regular fingers, and they are represented by the numbers 0 to 9.
But this is where it gets interesting: after you’ve counted up to 9 on your regular fingers, you don’t stop. Instead, you start using your special symbols, represented by the letters A, B, C, D, E, and F. These symbols represent the numbers 10, 11, 12, 13, 14, and 15, respectively.
So, when you count with your fingers in hexadecimal, it goes like this: 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, A (which represents 10), B (which represents 11), C (which represents 12), D (which represents 13), E (which represents 14), F (which represents 15).
The Hexadecimal Number System is commonly used in computer programming and in microprocessors. It is used to describe locations in the computer memory.

This table shows the decimal numbers 0 through 15 and their hexadecimal forms.
Think and Tell
Is the value of 0 and 1 the same in different number systems?

Identify the systems that these numbers belong to.
A number in one particular number system can be converted into another with some specific rules. Let us learn how to do it.
Let us learn to convert a decimal number to its binary, octal, and hexadecimal form using the given example.
We will convert (35)10 to its binary form.
Step 1: Divide the number repeatedly by two and note down the remainders. See below:
Step 2: Write the remainders in reverse order.
The final number with only the 0 and 1 digits is the required number. So, (35)10 (100011)2
Or, we can also represent the above method in a different way. Remainders 110001
Step 1: Create a table and place the number to be converted in the first row.
Step 2: Write the base of the system, as shown. Here, we want to convert 35 into binary. So, we write 2.
Step 3: Now, divide the number by the base of the target system and write the quotient in the next row. Write the remainder in the cell next to it.
Step 4: Repeat the process till you get a 0 as quotient.
Step 5: Take the remainder from bottom to top. That is the desired binary number. So, we again get (100011)2.
We will take the same step-by-step approach. This time, we will use 8 as divisor instead of 2. Let us write (435)10 in its octal form. We follow the same approach. So, (435)10 in octal is (663)8.
We will repeat the same process. This time the divisor will be 16, because the base for hexadecimal is 16. We will try to write (846)10 in the hexadecimal form. So, (846)10 in hexadecimal is (34E)16.

Convert (442)10 into binary, octal and hexadecimal form.
To convert a number in a given base to a decimal.
Let us use (101011)2 to understand the step-by-step approach.
Step 1: Write the number in a row and note the position of the digits from right to left, as shown:
Step 2: Now make a third row and write the values of base to the power of the position.
Step 3: Make a fourth row and write the products of the digits in each place with the base power number.
Step 4: Find the sum of the numbers found in each place. In this case we get:
32 + 0 + 8 + 0 + 2 + 1 = 43.
So, we get (43)10.
What is the decimal equivalent of (1705)8?
We repeat the same process:
We get, 512 + 448 + 0 + 5 = 965.
So, (1705)8 is (965)10 in decimal.
What is the decimal equivalent of (1AC7)16?
We repeat the same process:
We get, 4096 + 2560 + 192 + 7 = 6855.
So, (1AC7)16 is (6855)10 in decimal.
Convert the following numbers into the decimal form.
There is a standard method to convert a binary number into its octal or hexadecimal form.
We will convert (1110101)2 into its octal form.
Step 1: We will group the digits of the binary number. We will form groups of 3, because: Base of octal = 8.
Base of binary = 2 and 23 = 8.
So, we form groups of 3 starting from the right. If 1 or 2 digits are left, we put them in a new group. See below:
Step 2: Now, treat each group as a separate binary number and convert into the decimal form. So, we get:
Step 3: We join the decimal numbers formed from the grouped digits. The number formed is the desired number.
So, (1110101)2 = (165)8
Why are we forming groups of 4?

This time, we form groups of 4 starting from the right.
Binary Number 110101011
Grouped Digits
Decimal number from grouped digits 1 10 (= A in hexadecimal) 11 (= B in hexadecimal)
We get (1AB)16.
So, (110101011)2 = (1AB)16.
Convert (1001001001)2 into its octal and hexadecimal form.
The method to convert hexadecimal and octal numbers into their binary form is also very similar. We will also use the concept of groups of digits that we learnt in the previous section.
Let us use the hexadecimal number (1A7)16 to go through the process.
Step 1: We take each digit of the number separately.
Step 2: We then convert each digit into its binary form.
Step 3: Write each derived binary number in groups of 4.
Again, we are writing digits in groups of 4 because:
Base of hexadecimal = 16.
Base of binary = 2 and 24 = 16.
So, we get:
of 4
Step 4: We now join the different 4-digit binary numbers derived. These final numbers is the desired binary number.
We get 000110100111.
So, (1A7)16 in the binary form is (000110100111)2 or simply (110100111)2.
We follow the same steps while converting an octal number into its binary form. We need to make the group of three instead of four in case of octal numbers.
Convert the following numbers into binary form.
a (174)8
b (B12)16
Converting hexadecimal numbers into octal numbers, and vice versa, has to be done via other number systems.
Let us say we want to convert (721)8 into its hexadecimal form.
We first find its decimal form. The decimal form of (721)8 is (465)10.
Now, convert this decimal form into the hexadecimal form. The hexadecimal form of (465)10 is (1D1)16
So, the hexadecimal form of (721)8 is (1D1)16
We follow the same steps while converting a hexadecimal number into its octal form.
Convert the following:
a (764)8 into its hexadecimal form.
b (2B1)16 into its octal form.
Binary addition is similar to the addition of decimal numbers.
When we add (0)2 and (0)2, we get 0. So, (0)2 + (0)2 = (0)2
When we add (0)2 and (1)2, we get (1)2. So, (0)2 + (1)2 = (1)2
But what happens when we add (1)2 and (1)2? (1)2 is basically 1 in decimal as well. So, (1)2 + (1)2 = (2)10 = (10)2.
So, a new place is created and 1 is carried over.
We can summarise the rules of binary addition as follows:
If we are adding x and y:
In a binary system, only 1 can be carried over. In the decimal system, what numbers can be carried over? Think and Tell


So now, we can add bigger binary numbers by this method. For example, let us add (101101)2 and (10110)2
So, the sum of (101101)2 and (10110)2 is (1000011)2.
Carry Result
Following from the previous section, the rules of binary subtraction are as follows:
For example, let us subtract (11010)2 and (1100)2
So, the subtraction of (11010)2 and (1100)2 is 01110.
(101101)2 + (111111)2
Borrow Result
(1111)2 – (0001)2
(1110001)2 + (1010101)2 (110011)2 – (01010)2
A Number System is a way of representing and expressing numbers using a set of symbols or digits.
Every number can be expressed in different number systems. But the value remains the same.
Base is the number of digits the number system uses. The base of binary is 2, octal is 8, decimal is 10, and hexadecimal is 16.
We use the Decimal Number System in our daily lives.
Binary Number System uses two digits: 0 and 1. Each binary digit is also called a bit.
The Octal Number System is a base-8 number system that uses digits from 0 to 7.
The Hexadecimal Number System has a base of 16. It uses digits from 0 to 9 and letters of the alphabet A to F where A is 10, B is 11, and so on.
We have different rules to convert the number expressed in one number system to another.
A. Fill in the blanks.
The Binary Number System uses two digits: and .
The Binary digit is also known as a .
The Decimal Number System is a base number system.
In Octal and Hexadecimal Number Systems, we have and digits, respectively.
When converting binary numbers to their octal form, we put digits together in groups of .
B. Tick () the correct option.
Which number system uses only two digits, 0 and 1?
a Decimal b Binary c Octal d Hexadecimal
The Decimal Number System is also known as the system. a Base 2 b Base 8 c Base 10 d Base 16
What does “A” represent in the Hexadecimal Number System? a 7 b 9 c 10 d 12
Which number system is used by digital devices like computers and calculators? a Binary b Decimal c Octal d Hexadecimal
When converting a binary number into a hexadecimal number, we will form groups of how many digits?
C. Who am I?
I only understand two digits, 0 and 1. Computers use me to store and process information.
I am used in counting and doing calculations every day. I have 10 digits, starting from 0 to 9.
I am a number system that uses base 8.
I am unique as I let you use letters of the alphabet as my digits too. Programmers love using me.
I am common to all number systems. My value is also the same in all the number systems.

D. Write T for True and F for False.
The Decimal Number System is based on the digits 0 to 10.
In the Hexadecimal Number System, the letter “D” represents the digit 10.
The Binary Number System is the foundation of how computers understand and process information.
Computers can only perform addition, not subtraction.
(D716240234)16 is an octal number.
E. Answer the following questions.
What is a number system?
What is the base of a number system? Why is it important?
What does the term “hexadecimal” mean in the context of number systems?
Why do we need to convert a decimal number into binary?
F. Apply your learning.
Convert the following decimal numbers into their octal, hexadecimal, and binary forms.
Convert the following binary numbers into their decimal, octal, and hexadecimal forms.
Convert the following numbers into their decimal and binary forms. a (1B)16 b (561)8 c (717)8 d (B28)16 e (D4E)16
Add the following binary numbers. a (101)2 and (110)2 b (10101)2 and (1010)2 c (1110101)2 and (110110)2
Subtract the first binary number from the second binary number. a (11)2 and (110)2 b (1010)2 and (10101)2 c (110110)2 and (1110101)2











When we talk about technology, the first thing which comes to our minds is the internet. The internet has brought the world closer. It has changed our lives. But nothing is perfect because just like in the real world, the world of the internet also has its share of crime, called cybercrime.
The word cyber means internet-related, and crime is something that is illegal. Therefore, cybercrime means crimes that happen on the internet.
Cybercrime is considered a serious offence as it can harm many users of the internet across the world. It is a wrong and harmful action done through digital devices.
Some examples of cybercrime are:
• using the internet to steal another user’s personal information;
• breaking into, or hacking, websites and accounts;
• infecting other computers by creating or sending viruses; and
• bullying others on social media platforms.
Awareness of the different kinds of cybercrime helps us avoid them.
Cybercrime can be classified into different categories based on the nature of the criminal activity.
These crimes include the theft of personal information, such as credit card numbers, Aadhaar card numbers, and passwords. Here are a few kinds of cybercrimes committed against individuals.
Awareness about the different kinds of cybercrime helps us avoid them.





1. Phishing: It is the attempt to trick a user to get his or her personal information. This is generally done through fake emails. The stolen information can be used for:
a. Email spoofing, or identity theft: where the criminal will pretend to be someone else on the internet to fool and steal more information from other users.
b. Scamming: where the criminal will send believable-looking emails or advertisements to steal banking information and money from the users.
2. Cyberbullying: Targeting a user on social media and emotionally harming him or her by:
a. creating fake accounts of that user; or
b. spreading lies, incorrect information or rumours about that user; or









c. shaming or abusing that user for his or her views.
d. extortion, or forceful taking of money by blackmailing or harassing a user, sometimes after stealing his or her personal information.
3. Cyberstalking: Using the internet to follow another user’s location, monitoring his or her actions, and harming that person’s privacy.
Did You Know?
When a website’s URL starts with ‘https://’ instead of just ‘http://’, it is more secure.

These crimes involve the theft of intellectual property, such as trade secrets, sensitive information, and ownership of an invention or idea.
These crimes can be of the following types:
1. Corporate Espionage: Espionage means to spy or secretly monitor a person, company, or a government without their knowledge. Corporate means relating to offices or businesses. Therefore, corporate espionage is the illegal spying on a business or office to steal their information.
This can be done through hacking, or gaining access to a person or organisation’s computer or computer network in order to spread viruses or steal information.
2. Denial of Services: Purposely flooding the office or business’s computer or network with so much data transfer, or traffic, that it becomes slow, creates network downtime or stops working altogether.
Network downtime is the inability of a network to function as a result of a specific system or an application failure. This disturbs the normal functioning of an office or a business, thereby disrupting work.
1. Ransomware Attack: In these, hackers encrypt government systems and demand a price to provide the decryption, possibly causing huge disturbance in government operations.

Did You Know?
In 1961, MIT Professor Fernando Corbato invented the first digital password for secure access to a giant time-sharing computer.

























































































































These crimes involve the theft of sensitive data of a country’s government such as information about their military, policing, economy, tax, and citizens. They can also involve cyberwarfare, which is the use of cyber attacks to disrupt or disable government systems.

2. Insider Attack: An insider attack is a cybersecurity threat that comes from employees or contractors within government offices who may intentionally or unintentionally leak important information and use that information to commit cybercrimes.
If a hacker locks your friends files in his computer and demands money to unlock them, what kind of cyber threat is that?

The internet can also be used to create a negative impact on the general public or various social groups. These crimes often exploit the interconnected nature of the digital world to cause harm, spread fear, or disrupt the functioning of society.
1. Cyberterrorism is the use of computers and the internet to attack or frighten large numbers of people.
2. Spreading Fake News is the spreading of false or misleading information presented as actual news with the intent to manipulate public opinion, leading to confusion and discord in society. It can be shared on social media, websites, messaging apps, and even traditional media outlets.
Share some tips you can give your friends on staying safe while using public Wi-Fi networks.





I got an email which has a message that my account will expire soon…

I have to fill in this form. They are asking for my bank account number and address.
I got low grades in Mathematics. One of my classmates is calling me loser on social media.

He has even tagged me in one of the posts, calling me bad names.
Column A
Cybercrime
Corporate Espionage
Ransomware attack
Phishing
Column B
Tricking a user to steal his personal information.
Stealing government information and demanding money for its return.
The act of breaking the law using the internet.
Illegally spying in a business.
Just as you lock your doors and windows to keep thieves out of your house, cybersecurity serves as a lock for your computer and the internet.
Cybersecurity functions like a digital shield, ensuring that your computer and personal information remain safe and secure from threats on the internet. It is all about safeguarding your online activities from harmful users and hackers.
Cybersecurity is the practice of protecting computers, systems, and networks from digital attacks.
Here are a few ways that can help you protect your computer better.
A password is a secret code that only you know and that can keep your online accounts safe from hackers. A strong password guards your computer and information like a fortress can guard a city.
To create a strong password, use the following tips:
1. Have at least 12 characters in your password.
2. Use a combination of symbols, numbers, and capital and small letters.
3. Avoid passwords that can be easily guessed, like your nickname, your phone number, or your date of birth.
4. Change your password frequently.
Multi-Factor Authentication (MFA) is a security process that requires users to provide two or more forms of verification to gain access to a system or an account. This adds an extra layer of protection beyond just a username and a password.














You must have seen some emails or links saying things like “Your account will be deleted” or “You won a prize; click here now!”. Take a deep breath and don’t rush to click on it. Never click on these types of links or emails. Simply delete it instead and inform your parents or your teachers about it.
To keep your personal information on your computer, you can install antivirus software which saves your computer from viruses before they can harm your computer. Some popular antivirus software are McAfee, Quick Heal and Norton.
Always be cautious of the website you are visiting. Securing your browser by changing its setting to filter out harmful links and sites can make your net surfing enjoyable and safe.
Our computers also have a firewall. A firewall is a network security device that monitors and controls incoming and outgoing data in the network. The main function of a firewall is to filter and block harmful content when you are using the internet.


Hacking is not always bad. Ethical hacking helps to keep the online world safe. Know more about it here!

Read the paragraph and answer the following questions.
As time goes by, families sometimes move to different cities. We can stay in touch with them even if they are far away using the internet. We can also make new friends online, but we need to be careful. Not everyone online is who they say they are. Since we cannot see them in real life, it is best not to share personal things like our name, where we live, or our phone number with them. Some people might want to make us uncomfortable or trick us, so it is important to let the elders we trust know if something feels strange.
We should never share passwords of our online accounts with anyone. A strong password has a mix of letters, numbers, and special characters. Also, it is a good idea to have different passwords for different things. If one gets compromised, the others will still be safe. By being cautious and using the internet responsibly, we can have fun and stay safe at the same time.
Questions:
What’s an important thing to remember when making new friends online? Why?
Why is it risky to share personal information like your name, address, or phone number with people you meet on the Internet?
If something feels strange while you are using the internet, what should you do?
Why is it a bad idea to share your online account passwords with anyone, even your friends?
Imagine you met someone online who was really nice, but he started asking for your personal information. What should you do in that situation?
The internet has changed our lives but also brought in cybercrime.
Cybercrime involves harmful actions done through computers, like stealing information or bullying online.
Cybercrimes against individuals involve the theft of personal information, such as credit card numbers and passwords.
Crimes against businesses involve stealing intellectual property, hacking, denial-of-service attacks, and data theft.
Crimes against governments include theft of sensitive government data.
Crimes against society involve spreading fake news and cyber terrorism.
To protect ourselves from cybercrime, we need to follow good cybersecurity practices.
Using strong passwords, enabling multi-factor authentication, avoiding suspicious links, installing antivirus software, and using secure networks are some ways to stay safe online.
Cybersecurity is essential to protect ourselves from online threats and enjoy a safer internet experience.
A. Fill in the blanks.
Cybercrime is a wrong or harmful action done through Cybercrimes against individuals can involve the theft of personal information like is where the criminal pretend to be someone else to fool the user. involves using digital platforms to harm others through aggressive and hurtful messages.
on your computer can help protect it from viruses.
B. Tick () the correct option.
What should you do if you encounter cyberbullying?
a Ignore it and don’t tell anyone
c Report it to a trusted adult and seek help
What is the goal of cyberterrorism?
a To bring peace and harmony to society
c To cause direct physical harm or casualties.
b Stand up to the bully and respond with hurtful messages
d Get worried and panic
b To create fear, panic, and disturbance using technology and the internet
d To improve cybersecurity

How can you protect your online accounts?
a Use weak and simple passwords
c Create strong passwords and enable MFA
What can antivirus software do for your computer?
a Provide entertainment and games
c Increase computer speed and performance
What is the purpose of MFA in cybersecurity?
a To block access to all websites
c To slow down internet connection speed
C. Who am I?
b Avoid using Multi Factor Authentication (MFA)
d Share your passwords only with your close friends
b Protect against viruses and malware
d Help to play games easily
b To help hackers steal your data
d To make your computer more secure by adding layers of security
I am a cybersecurity threat that comes from someone within the organisation who has authorised access to its resources and can carry out harmful actions.
I am a cybercrime aimed at tricking people into giving away personal information or money.
I am a network security device that monitors and controls incoming and outgoing data in the network.
I am a strong code that only you know and can keep your online accounts safe from hackers.
I am a cybercrime that hackers use to encrypt organisational systems and demand a price to provide the decryption.
D. Write T for True and F for False.
Multi Factor Authentication (MFA) adds extra security to online accounts. It is safe to click on any links or download files from unknown sources. Email spoofing is a safe and harmless activity. Ransom attacks involve stealing sensitive government data.
E. Answer the following questions.
What do you mean by corporate espionage?
F. Apply your learning.
Pranav receives an email from a bank asking him to verify his account details urgently. The email looks official, but something seems suspicious. What do you think: is this an attempted cybersecurity breach, and if it is then what type of security breach is it?
Raman is at a coffee shop with free Wi-Fi and wants to check his social media accounts. What do you think, should he connect with the coffee shop’s Wi-Fi and start working on his project or should he not connect with the Wi-Fi? If your answer is no, explain why.
Geeta has created a new online account and needs to set up a password. What are the essential elements of a strong password?
Malin comes across a website that promotes illegal activities and harmful content. Should he open that website on his system?
Ritu receives an email claiming that she has won a big prize and needs to click on a link to claim it. The email looks convincing, but something feels off. What should she do?







A problem is a challenge or a task that needs to be solved.
Puzzles are problems that challenge our thinking skills.
There are many types of puzzles that we solve, such as jigsaw puzzles, Sudoku, riddles, maths puzzles, and more.
Let us solve this maths puzzle. You need to identify the hidden pattern and enter the correct number at the place of the question mark.
Let us try to solve it.
Step 1: Let us first break the problem into smaller parts and notice the hidden pattern by looking at the first row of the grid. You can observe that by adding the first two numbers of the row and multiplying their sum by 2 will give you a number given the third and the fourth cells of the row.
(3 + 2) × 2 = 10
Step 2: Similarly, look at the other two rows:
(1 + 9) × 2 = 20
(7 + 5) × 2 = 24
Step 3: By following the same pattern, you can find the number to be given at the place of the question mark.
(0 + 8) × 2 = 16
So, the correct answer for the above puzzle is number 6.
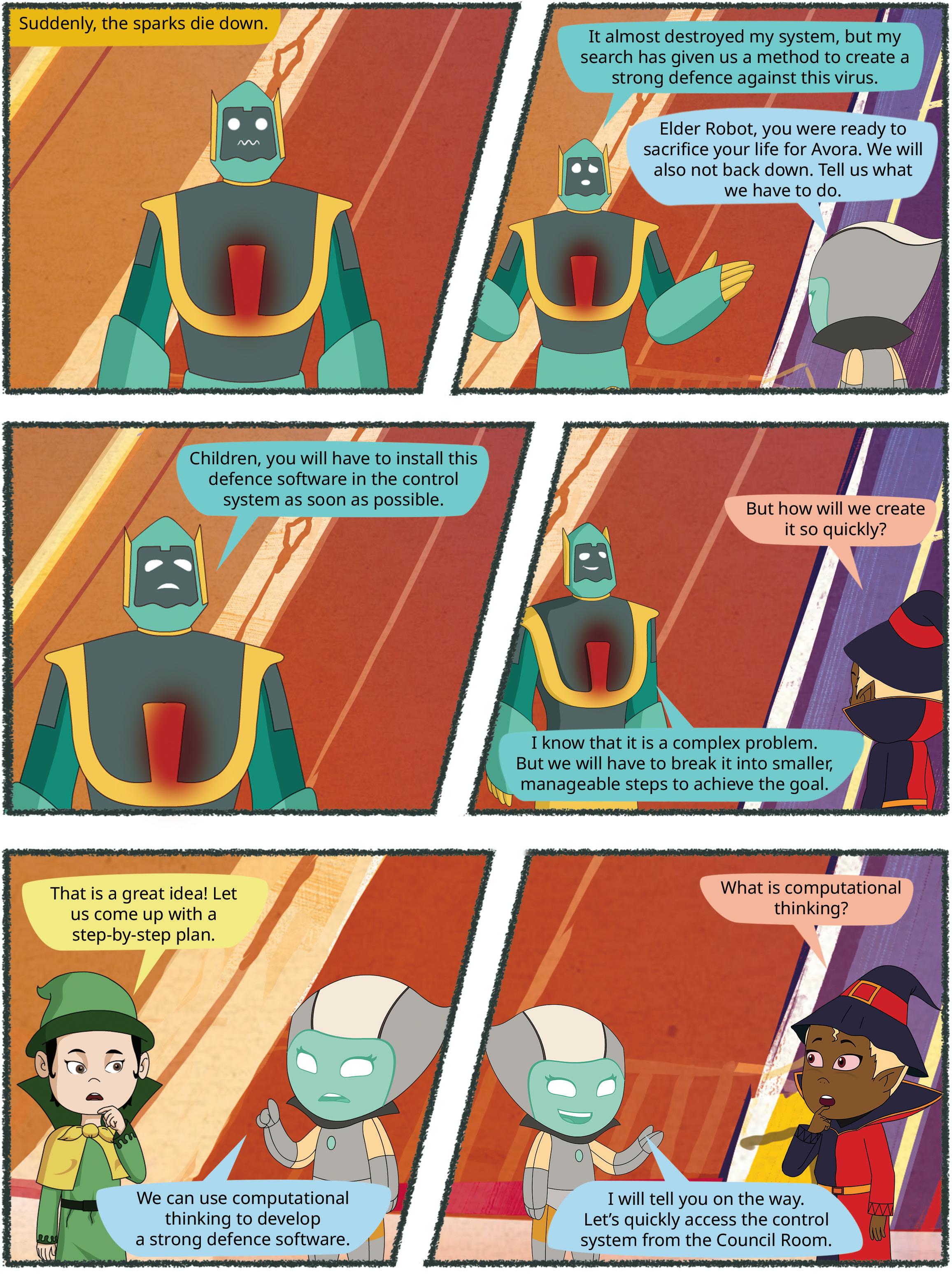
The process of breaking down a problem into smaller parts and recognising a pattern to efficiently solve it is called Computational Thinking.
Computational thinking is not only limited to the field of mathematics or computers, it can be applied in various fields such as engineering, medicine, social sciences, agriculture, and other.

Computation means performing mathematical or logical calculations to solve a problem or process data. When we apply this concept to solve a particular problem, we must investigate the other aspects of problem solving, which also involves breaking down complex problems, applying logic, and designing algorithms to solve them. This is the approach that we follow for computational thinking.
In the previous section, while solving the maths puzzle, you must have followed certain steps, like dividing the problem into sub-problems, then applying a method to solve the sub-problem, and then finally combining all the solutions together to provide the solution to the main problem.
These are the core concepts of computational thinking. Let us learn about them one by one.

The following are the core concepts of computational thinking.
Decomposition: Break a problem into smaller, easier parts.
Pattern recognition: Identify links or repeated parts in a situation.
Abstraction: Focus on the important details while ignoring useless information.
Algorithmic design: Create a step-by-step plan to solve the problem.
Let us learn about these concepts one by one.
Decomposition means breaking down a big, difficult task into smaller, easier ones.
Suppose you are organising a school fair. This task looks like a very big task. But by breaking it down into smaller tasks, it becomes more manageable.
Now, let us break down this problem into smaller subproblems:
1. Planning the layout of stalls
2. Arranging food vendors
3. Organising games and activities
4. Setting up ticket booths
5. Coordinating volunteers
Each smaller task can then be assigned to different teams or handled step-by-step, making the overall task less overwhelming.
In a similar manner, on computers, large programs are also divided into smaller, easier tasks to reach the solution.

Now, let us learn how to apply decomposition to solving issues:
Step 1: Identify the big problem
First, determine the main problem you wish to solve.
Step 2: Break it down
Next, split the major problem into smaller, more manageable sub-problems. These sub-problems should be simpler and easier to address on their own.
Step 3: Solve each sub-problem
Tackle each sub-problem one by one. Write methods or step-by-step tips to solve them.


Organising School Fair
Step 4: Combine solutions
Planning the layout of stalls
Arranging food vendors
Organising games and activities
Setting up ticket booths
Coordinating volunteers
Arranging Coupons
Snacks vendor
Ice-cream corner
Printing of coupons
Distribution of coupons
Once you have solved all the sub-problems, merge their solutions together to solve the original, huge problem at hand.
Step 5: Test and refine
Test your answer to make sure it works as planned. If you find any challenges, go back and change your techniques.
Let us look at some everyday examples of decomposition:
Example 1: Making a sandwich
Big Problem: Make a delicious sandwich.
Decomposition:
- Chop vegetables.
- Prepare the sauce for sandwich filling.
Put it all together to make a delicious sandwich.
Example 2: Solving a math problem
Big Problem: Solve a complex math equation.
Decomposition:
- Break it into smaller equations or steps.
- Solve each small equation.
- Combine the solutions to get the final answer.

Decomposition is a basic skill in computer science and problem-solving. Here are some of its advantages:
1. Simplicity: By breaking a big problem into smaller parts, it becomes easier to understand and solve.
2. Collaboration: Decomposition makes collaboration more feasible. Various individuals may work on various portions of an issue, and when you bring all the solutions together, you solve the complete problem.
3. Reusability: Once you have solved a significant piece of an issue, you may apply that answer again and again in other situations. This saves time and work.
4. Efficiency: Smaller hurdles are typically simpler and faster to handle than major ones.
Look at the adjoining picture. Can you find the next image in this given pattern? You must have solved this puzzle by identifying a pattern in the shapes.
Pattern recognition is the process of identifying patterns in data or information.
Let us again consider our Organising a School Fair problem.
You can talk to your seniors and teachers who have organised the school fair in the past, to get the idea about the type of activities and food items children prefer in the school fair. Following the same pattern, you can include such activities and food items in your list.
In computer science, it is about discovering links or patterns in data. Computers use mathematical formulas to find patterns in data. Let us look at some examples of pattern recognition.
Here are a few examples of pattern recognition in different contexts:
1. Speech recognition: Software that identifies speaking patterns by listening to spoken language and turns it into text are examples of speech recognition. For instance, voice assistants like Alexa, Siri, and Google Assistant detect speaking patterns to understand and carry out your requests.
2. Handwriting recognition: There are software applications that study handwriting patterns and turn scribbled characters into digital text. This is a common method for digitising handwritten notes or signing digital documents.
3. Image recognition: Many applications and software are there for image recognition to find patterns and items in pictures and videos. This is applied in several ways, like face recognition in smartphones, recognising objects in self-driving cars, or even in medical imaging for spotting diseases.
4. Natural language processing (NLP): To find trends in written or spoken material, NLP methods are applied. For instance, sentiment analysis examines the text’s emotional tone, while robots apply pattern recognition to grasp and respond to human contacts.
5. Credit card fraud detection: To find abnormal credit card buying trends, banks and credit card companies apply pattern recognition software. The system may flag a transaction as a likely scam if quick and bulk purchases are made with it somewhere else.
Now, you have solved some problems by decomposing them into small parts. Think of a huge, complex problem with hundreds of small sub-parts. To solve it step-by-step would be impossible. However, at times, if you look at the larger picture and ignore the minute unnecessary detailing, then your bigger problem may seem easy to solve. For example, while driving a car, you will be concerned only with the performance and the comfort provided by the car instead of its inner details like engine type, etc.
This is called abstraction.
Abstraction refers to disregarding the minute details of a problem and focusing on its major issues.
Abstraction is applied in our daily-life situations without us ever knowing about it. Let us look at a few common examples:
1. Maps: Maps are simple images of real-world places. It is not possible to show each and every place and landmark on the map. For teaching, they show roads, towns, and essential information rather than every tree and building.
2. Recipes: By splitting the cooking process into steps, we may make it easy to follow a process. We focus on which materials to use and how to mix them, rather than having to focus on the chemistry processes working behind them.
3. Language: Language is a great example of abstraction. Language and words make it easier for us to express difficult ideas and feelings without going into the details of the formation of words and sentences.
The following are the advantages of abstraction:
1. Simplification: Abstraction simplifies difficult problems, making them more understandable and doable.
2. Reusability: Abstracted components can be reused in different situations, saving time and effort.
3. Modularity: Abstraction supports modular design, where each part of a system can be built and tested separately.
4. Scalability: As problems become more complicated, abstraction helps us grow our answers successfully.

Let us think about baking a cake. We can divide the entire process into the following steps:
Collect the ingredients.
Mix them in proper proportions.
Switch on the oven.
Bake for the suggested period of time.
This step-by-step procedure for baking a cake is called an algorithm.
Algorithms can be defined as step-by-step instructions to be followed for a machine to carry out a particular task.
Algorithmic design is the process of designing and analysing algorithms to solve computational problems. It involves creating a step-by-step set of instructions or a well-defined sequence of operations that can be followed to solve a specific problem or perform a task. These algorithms can be implemented in various programming languages and executed by a computer. Algorithms may have multiple solutions to a problem and can be adapted or modified according to the situation.

Can we solve all problems by creating algorithms for them?

Now, let us explore some real-life examples of algorithmic design that impact our daily lives:
1. GPS navigation: When you use a GPS device or a smartphone app to find directions, it estimates the best way for you to reach your location. This includes complicated computations and programs that consider things like traffic, road limits, and your chosen mode of transportation.
2. Online shopping: When you shop online, websites offer product recommendations based on your previous purchases and viewing habits. They study your preferences using recommendation algorithms to offer things you might like, making your buying experience more customised.
3. Social media feeds: Social media sites like Facebook and Instagram use algorithms to decide which posts to show you. They consider things like your connections, hobbies, and the reach of the content to create a customised page for you.
4. Search engines: When you search the internet using a search engine like Google, it uses algorithms to scan billions of web pages and show you the most appropriate results. This needs fast processing and organising methods to give quick and accurate results.
Follow the rules while writing an algorithm:
An algorithm must start with a Start step.
It must end with a Stop step.
The language should be simple.
There should be proper sequence marking for all the steps of a problem.
If there are some steps that need to be repeated, then this should be marked properly in an algorithm.
Let us design an algorithm for grocery shopping:
1. Start
2. Make a shopping list
3. Go to the grocery store
4. Collect the items that you want to buy
5. Pay the amount
6. Get the items packed
7. Return home
8. Stop
Let us look at another example:
1. Start
2. Input two numbers, num1 and num2
3. Take another variable sum
4. Initialise the sum to 0
5. Perform the calculation, sum=num1+num2
6. Display the result
7. Stop
Do It Yourself 3A
Design the algorithms for the following problems:
a Getting ready for school.
b Making a cup of tea.


To learn more about algorithms, scan the QR code.
c Convert a temperature in Celsius to Fahrenheit.
[Hint: °F = (°C × 9 5 ) + 32]





Rina was riding her bicycle to school when her bicycle tyre got punctured. She fell off the cycle, but she didn’t get hurt. However, her pen fell out of her bag.
Match the following:
Concept Name Example
Decomposition She had a flat tyre before, and she knows a shop close by where she can get it repaired.
I should take the bicycle to the nearby mechanic.
Pattern Recognition
1. Punctured tyre.
2. Lost pen.
Abstraction
To get the tyre fixed:
1. Go to the tyre shop.
2. Ask the mechanic to fix the tyre.
3. Pay the mechanic and get your bicycle back.
Algorithmic Design She identified the subproblems:
1. Punctured tyre.
2. Lost Pen.
Out of the two problems, she decided to focus on getting the tyre fixed because she needed to reach school on time.
A problem is a challenge or a task that needs to be solved.
Computation means performing mathematical or logical calculations to solve a problem or process data. The main concepts in computational thinking are decomposition, pattern recognition, abstraction, and algorithm design.
Decomposition means breaking down a big, difficult task into smaller, easier ones.
Pattern recognition is the process of identifying patterns in data or information.
Abstraction refers to disregarding the minute details of a problem and focusing on its major issues.
Algorithms can be defined as step-by-step instructions to be followed for a machine to carry out a task.
A. Fill in the blanks.
Hints simple sub-problems pattern algorithm decomposition
1 In computational thinking, we break down a complex problem into smaller to make it easier to solve.
2 means breaking down a big, difficult task into smaller, easier ones.
3 An is a set of step-by-step instructions that a computer can follow to solve a specific problem.
4 When writing an algorithm, it is important to use language to ensure that the computer understands the instructions.
5 Computers use mathematical formulas to find a in data.
B. Tick () the correct option.
1 What is an algorithm?
a A type of computer hardware
c A computer program
2 Which of the following is NOT an example of an algorithm?
a A recipe for baking a cake
c Steps to tie your shoelaces
b A step-by-step procedure to solve a problem
d A mathematical equation
b Instructions for assembling a piece of furniture
d A list of your favourite movies
3 In computational thinking, what does “decomposition” mean?
a Breaking down a problem into smaller, manageable parts
c Combining two problems into one
4 Which of the following is an example of abstraction?
a Following a map
c Using a recipe to make dinner
b Making something more complex
d Ignoring unnecessary details
b Watching a TV serial
d Playing games
5 Handwriting recognition is an example of .
a Abstraction
c Decomposition
b Pattern recognition
d Algorithm design

C. Match the following.
Column A Column B
Algorithm Includes moving away from the detailed details and focusing on the important aspects of a problem
Computation By breaking a big problem into smaller parts
Decomposition
The process of solving a problem using a computer
Abstraction A step-by-step procedure for solving a problem
D. Write T for True and F for False.
1 An algorithm is a step-by-step set of instructions for solving a specific problem.
2 Computation refers to the process of performing calculations and solving problems using computers.
3 Algorithms can be used to solve real-life problems, such as finding the shortest path between two locations on a map.
4 Pattern recognition involves breaking down complex problems into smaller, manageable steps that can be solved systematically.
5 Algorithms always have a single, fixed solution to a problem and cannot be adapted or modified.
E. Answer the following questions.
1 What is an algorithm? Provide a simple example of an algorithm.
2 Define abstraction. Give an example.
3 Why is it important to break down complex problems into smaller, manageable steps when solving them?
4 Can you name three common tasks in your daily life that can be simplified or improved by applying the concepts of computational thinking?
5 What is pattern recognition?
1 Anamika’s father has been financially duped by some criminals. Which step of computational thinking would be helpful for him to find out about this fraud?
2 Arun wants to prepare for a competition. How can the decomposition steps of computational thinking be helpful for him to prepare?
3 Lovey has applied a face lock in her mobile phone. Which example of pattern matching is this?
4 Tarun uses Alexa at his home for managing devices. His mother gives instructions to Alexa to perform various tasks. What types of patterns does Alexa recognise here?
5 Pari is trying to write an algorithm to solve a mathematical problem, but she does not know the rules of writing an algorithm. Suggest some rules to her to design the algorithm.











Do you help your parents to plan the household budget? Suppose your mother wants you to learn budget planning. So you decide to assist her in maintaining the monthly budget. Which application do you think is the most suitable for this task?
Yes, you can use a spreadsheet.
A spreadsheet is a tool that helps you organise data in rows and columns and do calculations. Spreadsheets also allow you to analyse and visualise data.







There are many spreadsheet software options available, such as Microsoft Excel and Google Sheets.
While Excel is a licenced software, you can use Google Sheets without purchasing any licence. Google Sheets lets you create spreadsheets online and collaborate with others.
Let us create a spreadsheet to plan the monthly budget. To do this, follow the given steps:
1. Open the Google Chrome browser and visit the link: https://docs.google.com/spreadsheets/
2. The home page appears, as shown below. Click on the plus ‘+’ sign to open a blank spreadsheet.
3. In your new spreadsheet, go to the Rename textbox given at the top left corner of the sheet and rename the file as, “Monthly Budget”.

A spreadsheet consists of a grid-like structure. The various components of a spreadsheet are discussed as follows:
Column/Field
Row: The horizontal set of boxes is called a row or record.
Column: The vertical set of boxes is called a column or field.
Cell: The intersection of a row and a column is called a cell.
Row/Record Cell

A cell is a rectangular block in a spreadsheet that can hold data.
Data can be numbers, strings, or symbols.
To refer to a cell, we use cell names. A cell name is a combination of letters and numbers. Letters represent the column, and numbers represent the row.
For example, look at the adjoining image. The first cell will be called A1, where A stands for the column and 1 stands for the row.

Now, let us start entering the data in the sheet. Follow these steps:
1. Select a cell where you want to add data using the mouse or the arrow keys.
2. Type in numbers, text, or any other information you want, to add data.
3. Press the Tab key to move to the next cell in a row.
4. Press the Enter key to move to the next cell in a column.
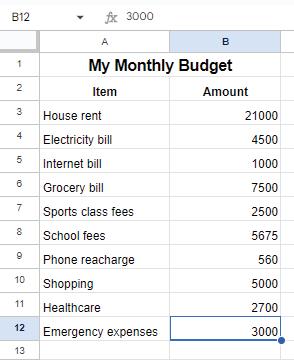
Now, type the data as shown in the given image.
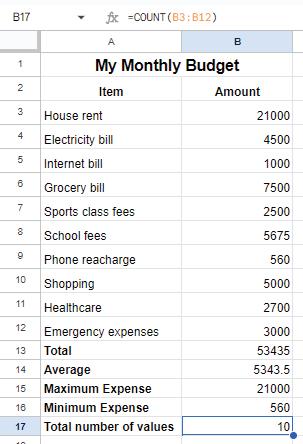
In Google Sheets, a formula is an expression used to perform calculations and obtain results within the cells of the spreadsheet. Formulas always begin with an equal sign (=) followed by the mathematical expression. Now that you have added the details of your expenses, let us apply a formula to find the total expense.
Follow the given steps to do so:
1. Select the cell where you want the total to appear, for example, cell B13.
2. Type the equals sign ‘=’.
3. Now, click on the cell B3, type a plus ‘+’ symbol, and click on cell B4.
4. Repeat this process up to cell B12 and then press the Enter key. The sum of cells B3 to B12 will appear in cell B13.


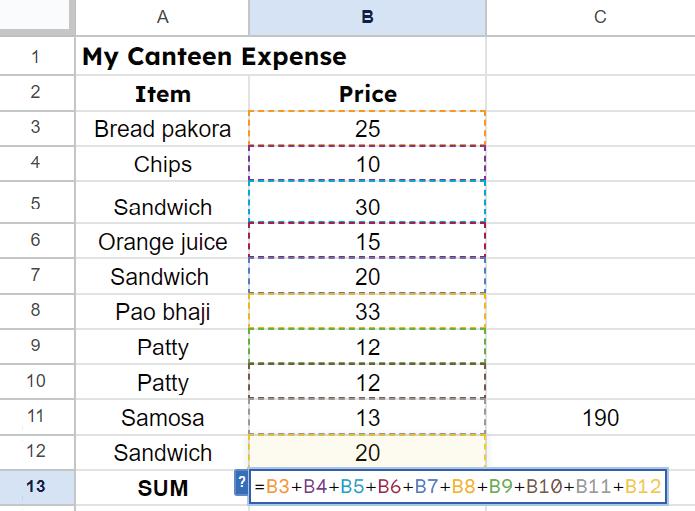
To know how you can also insert images in the cell, scan this QR code. Match the highlighted cells with their correct cell names.

Write the formula to calculate the total of cells A1, B1, C1, and D1 in cell E1.


You have learnt in the previous section how to calculate the total amount using formulas. However, you could have simplified your formula by using functions.
Functions allow you to calculate more efficiently using cell ranges instead of typing out the name of each cell
A cell range is a group of cells selected together. You can use cell ranges in the functions instead of selecting individual cells.
Functions are like built-in formulae in Google Sheets. They perform calculations, handle data, and analyse information.
When we want to use a function on a range of cells, we type the range instead of typing the name of each cell. To type a cell range, first we type the name of the first cell, then a colon (:), and then the name of the last cell. For example, A1:A4.
To use a function, first type the ‘=’ sign, then the function name, followed by cell names or cell ranges inside the brackets.
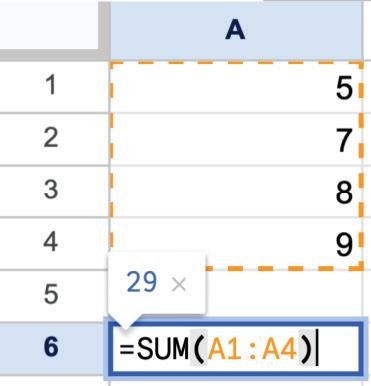
For example, =SUM(A1:A4)
Let us try functions in place of formula to find the total monthly expense.
The SUM function is used to add the values given in a specific cell range. To use the SUM function, follow the given steps:
1. Click on the cell where you want the sum to appear, for example, cell B13.
2. Type an equal to symbol ‘=’ and then the function name SUM
3. Type the opening parentheses ‘(‘ after the function name.
4. Inside the brackets, add the cell range for which you want to calculate the total. For example, B3:B12.
5. Press Enter to complete. You can see the result in the cell B13.
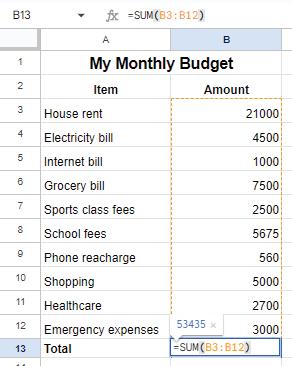
A group of friends went on a trip. Their individual expenses are given in the table below. Calculate the total expense of the trip in the cell B10.
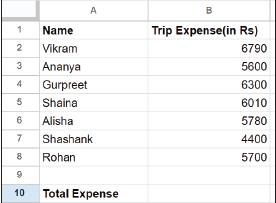
The Average function calculates the average of a range of numbers. To find the average monthly expense, you can use the average function as shown here:
=AVERAGE(B3:B12)
This function calculates the average of all the values from cell B3 to B12.
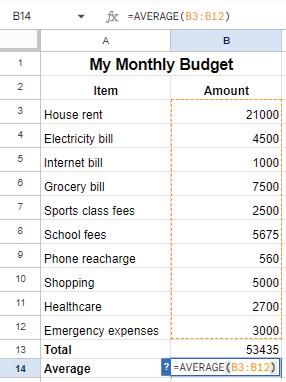

The Max function finds the maximum value in a range of numbers. To find the highest monthly expense, use the Max function as given here:
=MAX(B3:B12)
This function returns the highest value from cell B3 to B12.
You can use the Min function in a similar way to find the minimum value in a range of numbers. To find the lowest monthly expense, use the Min function as given below:
=MIN(B3:B12)
This function returns the lowest value from cell B3 to B12.
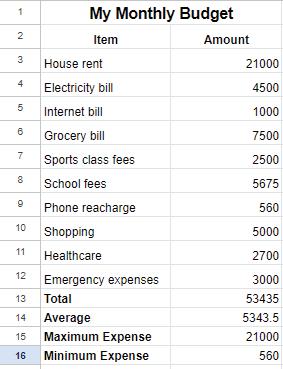
The Count function counts the number of cells that contain numbers. To find the number of cells that contain numbers in a given range, use the Count function as given here:
=COUNT(B3:B12)
This function counts the number of cells with numeric values from B3 to B12.
Let us learn about some more functions used in Google Sheets.
Apart from the functions used in the previous section, there are many functions that you can use to perform mathematical calculations.
Let us learn more about these functions.
This function returns remainder when the dividend is divided by the divisor.
Syntax: =MOD(Dividend, Divisor)
Example: =MOD(100, 5)
Result: 20
This function returns the square root of a number.
Syntax: =SQRT(Value)
Example: =SQRT(100)
Result: 10
This function rounds a given number down to the nearest integer.
Syntax: =INT(Value)
Example: =INT(5343.5)
Result: 5343
This function is used to raise a number to a specified power.
Syntax: =POWER(Value)
Example: =POWER(10, 3)
Result: 1000

This function returns the absolute or non-negative value of a given number.
Syntax: =ABS(Value)
Example: =ABS (-243)
Result: 243
Apart from the mathematical functions, there are several text functions that can be used in Google Sheets. Let us learn about some commonly used text functions.
The CONCATENATE function is used to join multiple text strings into a single string. This function is useful for combining data from different cells into one cell.
Syntax: =CONCATENATE(“text_string1”, “text_string2”)
Example: =CONCATENATE(“Hello”, “World”)
Result: HelloWorld
This function counts the number of characters in a cell, including letters, numbers, spaces, and punctuation.
Syntax: =LEN(“text_string”)
Example: =LEN(“Hello”)
Result: 5
This function converts all the text in a cell to uppercase letters.
Syntax: =UPPER(text)
Example: =UPPER(“Hello”)
Result: HELLO
This function converts all the text in a cell to lowercase letters.
Syntax: =LOWER(text)
Example: =LOWER(“Hello”)
Result: hello
You are tracking the number of hours you study, for different subjects, in a Google Sheet. Which function would you use to find the subject that you have studied the longest?

In order to work with dates and time, Google Sheets provides two important functions. Let us see how these functions work.
This function returns the current system date.
Syntax: =TODAY()
Example: = TODAY()
Result: 01/08/2024
This function returns the current system date along with time.
Syntax: =NOW()
Example: = NOW()
Result: 01/08/2024 10:30

How are formulas and functions

d POWER(20, 2) 1 2 Do It Yourself 4C
Label the parts of the given function.
a
b
What will be the output of the following functions?
a MAX(12, 34, 87, 32, 52, 43)
b CONCATENATE(“My “, “ “, “Rules “)
c ABS(-23)

1 A spreadsheet is a tool that helps you organise data and do calculations.
2 A cell is a rectangular block in the sheet that can hold data.
3 A cell name is a combination of letters and numbers.
4 Functions are pre-built formulas that you can use to perform various calculations or operations on your data.
5 A cell range is a group of cells selected together.
6 Some common functions used in Google Sheets are: SUM (adding numbers), AVERAGE (finding the mean value), MAX (finding the highest value), MIN (finding the lowest value), and COUNT (counting the number of cells with numbers).
7 Some common text functions are: CONCATENATE(joining text strings), LEN(finding length of string), LOWER(converting string to lowercase), and UPPER(converting string to uppercase).
8 Two important date and time functions are: TODAY(returns today’s date) and NOW(returns today’s date and current time).
A. Fill in the blanks.
Hints
Max Average cell Now numbers
1 A is a rectangular block in a spreadsheet that can hold data.
2 To refer to a cell in a spreadsheet, we use a combination of letters and
3 The function finds the maximum value in a range of numbers.
4 The function is used to find the average of a range of numbers.
5 The function returns the current date and time.
B. Tick () the correct option.
1 Which function is used to find the minimum value in a range of numbers?
2 How do you create a cell range for cells A1 to A4?
to A4
3 Which function would you use to join text strings together?
a UPPER b CONCATENATE
c LEN d SUM
4 To get the current system date in a cell, which function would you use?
a NOW() b TODAY()
c DATE() d TIME()
5 The function =SQRT(16) returns: a 4
c 16
C. Who am I?
1 I return the highest value from a set of numbers.
2 I count the number of cells that contain numeric values in a range.
3 I add all values in a specified cell range together.
4 I convert all text in a cell to lowercase letters.
5 I provide the current date and time.
D. Write T for True and F for False.
1 Google Sheets is a licensed software like Microsoft Excel.
2 The COUNT function counts the number of cells that contain text.
3 The SUM function adds up all the values in a specified cell range.
4 The MOD function returns the remainder when one number is divided by another.
5 The LOWER function converts all the text in a cell to uppercase letters.
E. Answer the following questions.
1 What is the purpose of the LEN function in Google Sheets?
2 How do you move to the next cell in a row after entering data?

3 What is a cell range in Google Sheets?
4 Which function calculates the square root of a number?
5 Describe the process to find the total expense using the SUM function.
F. Apply your learning.
1 You have a list of your monthly grocery expenses in cells C3 to C10. Create a formula to calculate the total amount spent using the SUM function.
2 Sunny recorded the daily high temperatures for a week in cells D5 to D15. How can he find out the average temperature for that week?
3 Smriti has entered a value in a cell, E2, with the name “john smith.” Which function can she use to convert this name to uppercase?
4 Raima wants to find out how many apples are left after each person takes 3 apples from a total of 20 apples. Which function can she use?
5 Seema needs to add the current date to a report. Which function will be useful for her?






You have created a Google spreadsheet in the previous chapter for your monthly budget. However, analysing and drawing conclusions from the numbers in the sheet can be challenging. What if you could ‘see’ the data visually to help analyse and interpret the results? Yes, that is possible in Google Spreadsheets. You can organise your data, group sheets, filter information, and create charts based on the data in your spreadsheet. In this chapter, we will explore these concepts in detail.
Sorting means to arrange data in a particular sequence based on specific criteria. It allows us to reorganise data in rows or columns, making it simpler to locate, analyse, and understand.
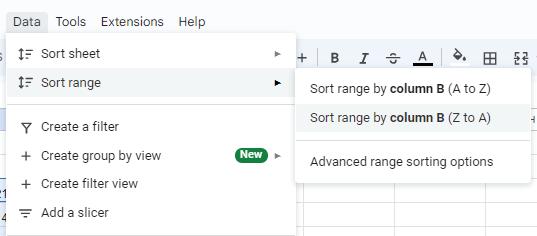
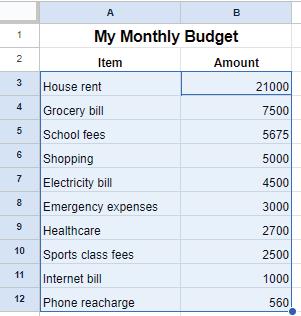
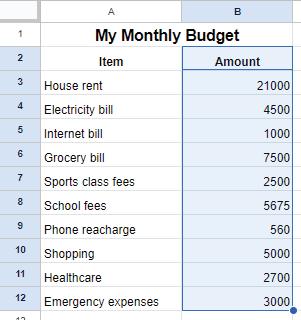
Let us again consider the example of the monthly budget sheet. Suppose you want to find out which item is the most expensive. Then, you can sort the data of the sheet in descending order. To do so, follow the steps:
1. Choose the range of cells that contains the data you want to sort.
2. Go to the Data menu.
3. Select Sort range > Advanced range sorting options from the menu.
4. A dialog box appears. In the Sort by drop-down, select Column B and then check Z to A checkbox to arrange data in column B in the descending order.
Suppose you are interested in finding out how many entries for bills are there in the monthly budget sheet. This way, you can display each bill entry just once, without repeating it multiple times. This is done with the help of grouping of data
In Google Spreadsheets, grouping means putting similar things together. Grouping keeps things tidy and helps you find what you need faster.
Follow the steps to group data in the monthly budget sheet:
1. Select the rows that you want to group. Then, go to the View menu.

2. Select the Group option >
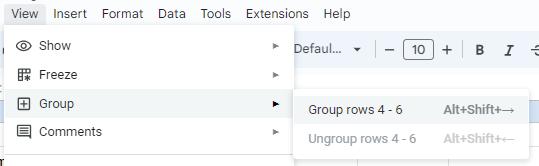
3. Use the plus ‘+’ button to show the group and the minus ‘−’ button to hide the group.


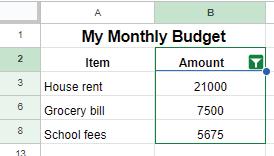
Suppose you want to see only those items that cost more than ₹5000. To resolve this, we use the Filters. Filters are a useful feature used in Google sheets that enable you to display data according to specific criteria. Filters can help narrow down the options to what we want and hide the rest. Filtering allows us to focus on specific parts of our data that meet certain conditions. By using filters in spreadsheets, you can easily find specific data, answer specific questions, and understand information in a better way. Let us try to filter data to find items that cost more than ₹5000 in the monthly budget sheet.
1. Select the range to which you want to apply the filter.
2. Go to the Data menu and choose Create a filter option.
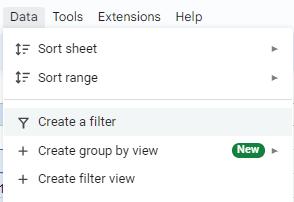

3. Click on the Filter symbol and select Filter by condition and choose your rule.
4. Here, we must select the Greater than condition and put 5000 in the Value or formula box.
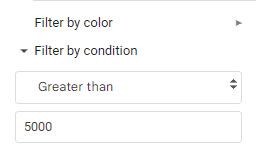
5. After selecting the required rule, click OK.
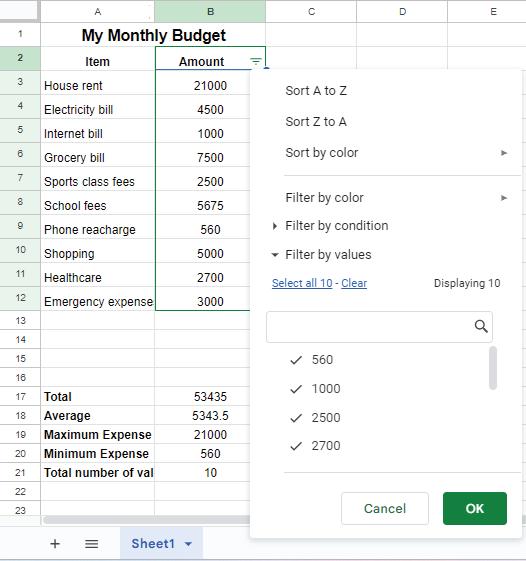
6. The spreadsheet hides unmatched rows, showing only the data that fits the selected criteria.

How is filtering different from


You have a list of animals in a spreadsheet, and you want to see only the ones that are mammals. What should you use?
a Sorting
b Filtering
c Formatting
d Deleting
Write T for True and F for False.
List of Animals
Animals
Class
Lion Mammals
Crocodile Reptiles
Shark Fish
Tortoise Reptiles
Giraffe Mammals
Elephant Mammals
Kangaroo Mammals
a You have created a list of cars and their speeds in a Google Sheet. You can use the sorting feature to put them in order from the highest to the lowest speed to view the fastest car at the top.
b Grouping data is only useful when working with numbers, and it does not apply to other types of information.

Charts help us look at data in the form of pictures. This helps us to understand the data in a better way.
Charts are common in everyday life, such as weather forecasts on TV. These charts use colourful images and symbols to display daily temperatures or chances of rain. Just like looking at the weather without too many numbers, charts help us see information in pictures, making it easier for our eyes and brains to quickly understand.
In Google Sheets, there are various types of charts available to visually represent data. Let us explore some common types of charts:
Column Chart: It uses vertical bars for comparing data or showing quantities. Each bar represents a category, and its height shows the value or amount.
Bar Chart: It is similar to a column chart but with horizontal bars. Each bar represents a category, and its length shows the value or amount.
Pie Chart: It displays parts of a whole as slices of a pizza. Each slice represents a category, and its size shows the proportion or percentage.
Line Chart: A line chart uses lines to show how something changes over time by connecting dots. This helps us spot trends, such as temperature changes throughout a year or the progression of a plant’s growth.
Follow the given steps to create a chart:
1. Choose the cells that contain the data you want to present in the chart.

2. Go to the Insert tab and select the Chart option.
3. A chart will appear along with a Chart editor menu on the right-hand side of the page.
4. Select the appropriate type of chart from the Chart editor menu. In this example, we are creating a column chart.
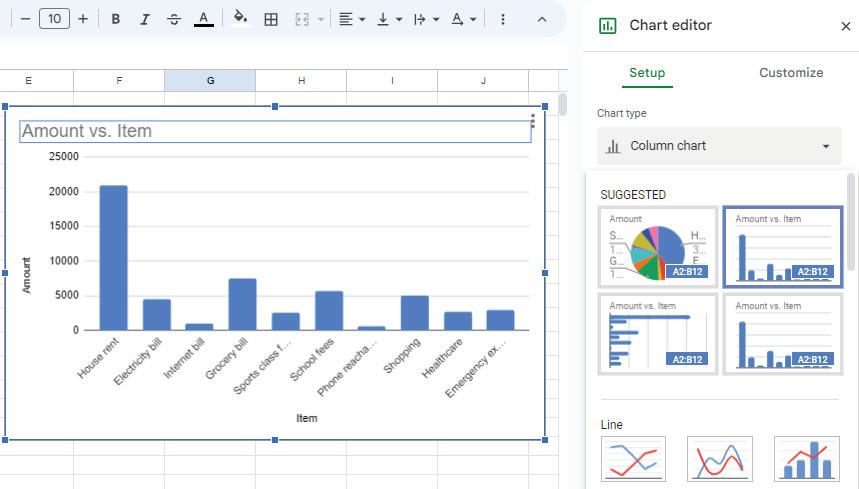

5. Once you have selected a chart type, you can customise it from the Customize tab in the Chart editor menu. As you can see in the image, the background is changed to light yellow, and the 3D version of the chart is enabled.
So far, you have been working on the monthly budget sheet. If you want to track your subject marks throughout the year, you do not need to create a new spreadsheet. Instead, you can keep adding new sheets in the same spreadsheet.


Scan this QR code to know about plenty of different types of charts in Google Spreadsheets.
To add a new sheet tab in Google Sheets, follow the given steps:
1. Click on the plus ‘+’ symbol at the bottom left corner of the Google sheet.
2. A new sheet tab will appear, ready for you to work on.
Colouring sheet tabs in a Google Spreadsheet means giving different colours to the names of the sheets. Let us colour-code the sheet tabs to organise the spreadsheet, making it easier to find the information you need.
The steps for colouring sheet tabs are:
1. Right-click on the tab you want to colour.
2. Click on the Change color option.
3. A palette of colours will be displayed. Select the colour you like by clicking on it. The sheet tab will be coloured.
Tick () the correct answer.
1 Why do we use charts in Google Sheets?
a To make the data look fancy
b To make the numbers bigger
c To help understand and analyse data more easily
d To hide the data from others
2 Which type of chart looks like a pizza divided into slices?
Sorting refers to arranging data in a particular sequence based on specific criteria. In Google Spreadsheets, grouping means putting similar things together.
The purpose of filters in Google Sheets is to help you view and analyse specific subsets of data within a larger dataset.
Charts are a method of presenting data as visual representations that make understanding information easier.
Column Chart uses vertical bars for comparing data or showing quantities.
Bar Chart is similar to a column chart, but with horizontal bars.

Pie Chart displays parts of a whole as slices of a pizza.
A line chart uses lines to show how something changes over time by connecting dots.
Colouring sheet tabs in a Google Spreadsheet means giving different colours to the names of the sheets.
A. Fill in the blanks.
A bar chart is like a graph made up of colourful rectangular bars, where each bar represents a category, and its shows the value or amount.
data helps to organise data in rows or columns based on specific criteria.
Charts are representation of data.
data means putting similar things together to keep the data tidy.
A chart uses lines to show how something changes over time by connecting dots.
B. Tick () the correct option.
Which type of chart would you use to display the progression of a plant’s growth?
a Column chart
c Pie chart
Grouping in spreadsheets refers to:
a Colouring sheet tabs
c Combining related rows or columns together
What do charts do in spreadsheets?
b Bar chart
d Line chart
b Arranging data in a specific order
d Creating formulae to perform calculations
a Perform calculations b Show data visually and help understand it
c Sort data alphabetically d Change the font style of the spreadsheet
What symbol is used to show a grouped set of rows in Google Sheets?
What feature in Google Sheets helps you display only items that meet certain conditions?
I help you to reorganise data to make it simpler to locate and understand.
I put similar items together to keep things tidy in a spreadsheet.
I am a type of chart that uses colourful and rectangular vertical bars to compare quantities or values.
I am a process in spreadsheets that enable you to display data according to a specific criteria.
I am a symbol used to add sheet tabs in Google Sheets.
D. Write T for True or F for False.
Pie charts are suitable for comparing quantities or values, while line graphs are used to show changes over time.
Filtering data in spreadsheets permanently removes hidden rows or columns from the dataset.
Sorting in spreadsheets refers to arranging data in a specific order based on certain criteria, making it easier to locate and analyse.
You can colour sheet tabs in Google Sheets to organise different sheets better.
Grouping data helps you to display items without repeating them multiple times.
E. Answer the following questions.
How does grouping data help in organising a spreadsheet?
What is a line chart used for?
Describe the steps to apply a filter in Google Sheets.
How can you add a new sheet tab in Google Sheets?
What type of chart would be appropriate to display the names of different sports and the number of students who like each sport?


F. Apply your learning.
Ishita has to organise a list of words in dictionary order. What methods should she use to convert List 1 into List 2?
Arjun has recorded the prices of various canteen items in a spreadsheet. Which option can he use to find out the most expensive item in the list?
Ravi is a sales person in an organisation. He maintains the sales data in a Google spreadsheet. Which feature of spreadsheets should he use to display only those items that have sold more than 50 units.
Suppose you are creating a mathematics project based on distances of different places from your school. You are recording the data in a spreadsheet. Now, you want to create a similar type of project for science subject where you have to record the distance of different planets from the Sun.
How will you add a new sheet in the same spreadsheet?



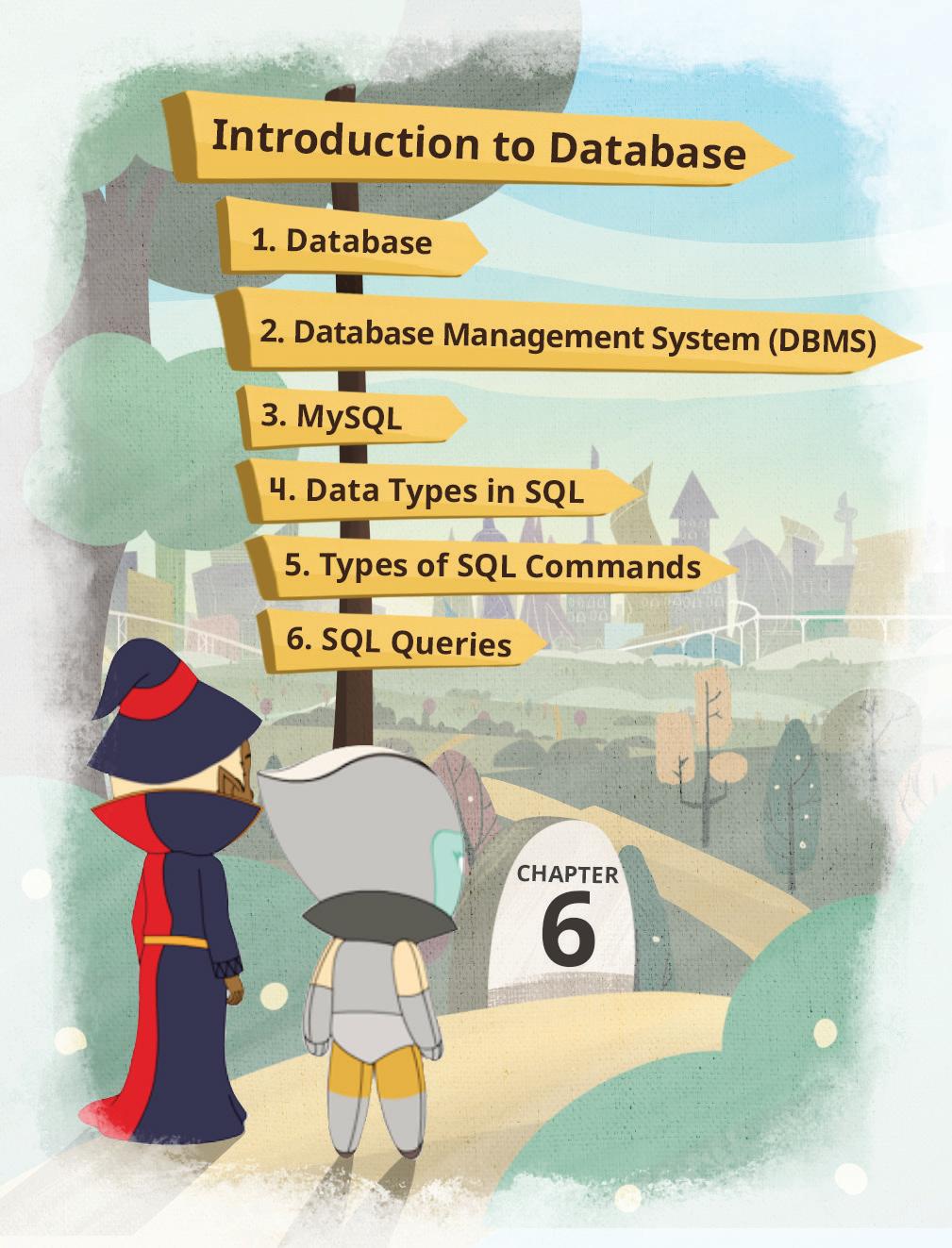



We are in an age where we are surrounded by a huge amount of data. Data helps us maintain and improve systems. Think about your school. Your school needs to maintain data about all the students, like their names, ages, grades, library card numbers, parent’s names and many other details so that the school can run without any problems. Similarly, data helps shopkeepers to keep track of their sales. Large businesses benefit from data by being able to understand their customers and create products that will be helpful to them. Additionally, it aids scientists in their many scientific endeavours.
However, storing and maintaining this data on the computer becomes a challenge if we do not have a structured system.
It leads to various problems like having the same information in different places, information not getting updated everywhere, and security and privacy issues.
To resolve these problems, we use databases.
A database is a collection of information or data, stored electronically in a computer system.
Most databases store data in the form of tables. A database can contain multiple tables to store related data.
For example, your school’s database might contain separate tables containing students’ data, teachers’ data, library data, and so on.

The column headers in the table are known as attributes and the rows are known as records. We use DBMS (Database Management System) to organise and manage the databases. It acts as an interface between the database and user applications.
We will learn more about DBMS later in this chapter.
Did You Know?
The first DBMS was developed in the early 1960s by Charles Bachman.

In this digital age, computers are used everywhere to store large amounts of data to keep track of personal and professional needs whether it is a local grocery shop or the stock market. Today, we all rely on some form of database to store information.
Let us learn more about the importance of database:
Organised Information: Databases help to keep information organised and make it easier to find. Most databases store related data using multiple tables. This information is recorded in rows and columns, making it easy to access.
Quick Access: Without a database, you would need to manually search through various files and documents to find data. Databases make it simple to add, delete, or modify data because they store data in rows and columns, allowing quick access to specific information.
Centralisation: Centralising information also structures data and prevents duplication. It saves space and allows you to work better and faster, ultimately increasing your overall productivity.
Large Volumes of Data: Databases can store and organise a huge amount of data easily. That makes it easy to quickly find the specific information as needed.
Data Security: Your data is secure when it is kept in the database. Only authorised persons can access the information which prevents unauthorised access to data.
Ensures Data Integrity: Data integrity is a process that makes sure the data is correct, whole, and the same as long as it exists in the database.
The database ensures data integrity by providing accurate information, even if multiple users are working in the system at the same time. This means you will always get the right information, even when there are multiple users.
For example, Book Id, Book Name, Genre, Price, and Publisher would be the same throughout, and anyone can access it. Data integrity helps to set rules on how this data can be accessed, used, and modified.













Reduction of Data Redundancy: Data redundancy occurs when we have multiple copies of the same data. Databases help us reduce data redundancy by making sure you do not have copies of the same data spread all over the place. This is important because it can get tricky to update data everywhere it is stored.


Big Data is a huge collection of information. Companies use it to recommend movies and songs you might enjoy. Scan the QR code to know more about it.
A DBMS (Database Management System) is a software that helps us to store, retrieve, and manage data in a database.
To retrieve data means to obtain the data from the database.
DBMS provides an interface between an end-user and a database, which allows users to create, read, update, and delete data in the database. It also provides protection and security to the database. In case of multiple users, it can restrict access to different databases for unauthorised users.
Imagine you have a big collection of books and you need someone to keep them neat and tidy for you. That’s what a DBMS does for databases.
It helps organise the data, makes it easy to search for specific things, and ensures that everything is safe and secure. So, whenever we want to find something in our database, the DBMS helps us quickly locate the exact information we need.


Database Management System consists of six main components. These are:
1. Hardware
2. Software
3. Data
4. Procedures
5. Database Access Language
6. People
1. Hardware: The hardware of computers consists of physical components such as a keyboard, mouse, monitor, and processor. Hardware is used to capture the data and present the output to the user.
When we try to run any database software like MySQL, we can type any command with the help of our keyboard. Storage devices, such as the hard disk, RAM, and ROM, are also the part of our computer system.
2. Software: Software is a set of programs that help hardware do its job. It is made up of procedures and programs that can understand the language used to talk to databases.
This software then turns those instructions into real commands for the database and makes things happen.
Some examples of DBMS software are MySQL, Oracle, SQL Server, dBase, FileMaker, and Microsoft Access.


Smarthome gadgets, like those controlling lights and music, rely on databases to deliver great experiences.
3. People: People interacting with the computers are also referred to as the “live-ware” of the computer system.
They form the most crucial part of the computer system.
These individuals control and manage databases, performing various operations within the Database Management System (DBMS). This group comprises the database administrator, software developer, and end-users.
4. Procedures: A procedure is a form of general instructions or guidelines for using a DBMS. These instructions include how to set up the database, install it, log in and out, manage it, create a backup, and generate reports from the database.
5. Data: These are the actual pieces of information, like numbers or text, that are input into a computer system.
Data refers to the collection of raw facts stored in a database.
Data is the fundamental building block for creating useful information. It is a crucial part of a DBMS. The database contains both the actual data and metadata, which is information about the data.


For example, when you want to store data in a database, you need to identify the attributes to organise that data, such as the data’s size, name, and other related details. These specific pieces of information about the data to be stored are known as metadata

6. Database Access Language: Database Access Language is a language that allows users to give commands to a database to operate the data stored. You can use this language to ask the database to do many things, such as getting data, modifying it, or removing it.
The most widely used Database Access Language is SQL. SQL stands for Structured Query Language
Match the Columns.
Column A
Database
Data Integrity
Database Management System
Data Redundancy
Column B
Occurrence of duplicate copies of similar data
A special computer program for managing databases
A collection of organised data
A process that makes sure data is accurate, complete, and consistent over the data’s lifecycle
MySQL is a database management system that allows us to create our own databases. It allows us to create, update, and retrieve data using SQL. It is open-source, which means it is free to use. It is popular for its speed, reliability, and scalability.
SQL (Structured Query Language) is a language that lets us access and manipulate databases. It allows us to perform operations on the data stored in the database, such as updating, inserting, deleting, and modifying data, etc.
SQL works on structured data. As a database holds data in a structured way, it is easy to retrieve information from the database using SQL.
SQL is not a database management system, but a query language.

With SQL, we can state our query using commands and ask the database to find specific data, like “Which book has the maximum price?” or “How many books do I have in my collection?”. The database then understands our questions and gives us the right answers.
SQL is simple but a powerful language to deal with databases.
Before we learn more about SQL and create our database, let us learn about keys.
Keys are used to uniquely identify any row of data from the table. We know a database can have multiple tables. Keys are also used to establish and identify relationships between tables. We will learn about four kinds of keys in this chapter.
1. Primary Key: The primary key is the attribute or set of attributes in a table that uniquely identifies a row in that table. There should be only one primary key in a table. The value of the primary key in each row should be unique, there should be no repetition.
Let us observe the Students table. Student_ID is the primary key. Student_ID uniquely identifies each row in the table. In tables, the underlined attribute is the primary key.
Primary Key
Priya Sen 4
13 LIB015
2. Candidate Key: There might be multiple attributes that can uniquely identify a row in a table. In our example, both Student_ID and Library_ID can uniquely identify a row in the table. But we had chosen Student_ID as the primary key.
Candidate key is the attribute that uniquely identifies a row in the table, but is not considered as the primary key. In our example, Library_ID is the candidate key.
3. Composite key: A primary key can consist of more than one attribute. In the Students table, Grade, Section, and Roll_Number when combined together can identify a row uniquely. Hence, it can be a primary key. When a primary key consists of more than one attribute, it is called a composite key.
4. Foreign key: We have previously learnt that a database can have multiple tables. Foreign keys help us to establish a relationship between these tables. Consider the following tables: Students table: Foreign key for Students table
Anuj Bhatnagar 3

House table:
Primary key for House table
House_ID House_name
H001 Red house
H002 Yellow house
H003 Green house
Both the tables have the attribute named House_ID. House_ID is the primary key in the House table but it is not a primary key in Students table. House_ID is considered as a foreign key in the Students table.
Let us learn the basic concepts of SQL and then create queries.
In SQL, data types define the type of data that can be stored in a column of a table. The following are the most common data types of SQL:
Numeric data types are used to store a numeric value in a field column. It may be decimal, integer or real value.
Syntax: NUMBER(n, d)
where n specifies the number of digits and d specifies the number of digits to right of the decimal point.
Example: age NUMBER(2), salary NUMBER(6, 3)
Text data types are used to store a string value in a field column. It can be a single character or a set of characters.
CHAR: This data type is used to store fixed-length character strings. If the string is shorter than the specified length, it is padded with spaces.
Syntax: CHAR(size) where size represents the maximum (255 Characters) number of characters in a column.
Example: name CHAR(15)
VARCHAR/VARCHAR2: It is used to store variable length alphanumeric data.
Syntax: VARCHAR(size) / VARCHAR2(size)
where size represents the maximum (2000 Characters) number of characters in a column.
Example: address VARCHAR2(50)
Date and time data types are used to store date and time values.
DATE: It is used to store date in columns. SQL supports the various date formats other than the standard DD-MON-YY.
Example: dob DATE
TIME: It is used to store time in columns. SQL supports the various time formats other than the standard hh-mm-ss.
Example: joining_time TIME
Did You Know?
Every DATE and TIME can be added, subtracted, or compared as it can be done with other data types.

SQL (Structured Query Language) is used for managing and manipulating databases. SQL commands are broadly categorised into two main types:
• Data Definition Language (DDL)
• Data Manipulation Language (DML)
DDL commands are used to define and modify the structure of database objects, such as tables, indexes, and views. These commands deal with the schema and structure of the database.
The following are the main DDL commands:
1. CREATE: Used to create new database objects like tables, views, and indexes.
2. ALTER: Used to modify the structure of an existing database object.
3. DROP: Used to delete an existing database object.
DML commands are used to manipulate data stored in the database. These commands deal with the actual data in the database.
The following are the main DML Commands:
1. SELECT: Used to retrieve data from the database.
2. INSERT: Used to add new rows of data to a table.
3. UPDATE: Used to modify existing data in a table.
4. DELETE: Used to remove rows from a table.

Let us now learn how to use the SQL queries to create tables and work upon them.
The Create Table command is used for creating tables. Syntax:
Create Table table_name ( column_name_1 data_type_1, column_name_2 data_type_2, ……… column_name_n data_type_n
);
Here is an example of creating a table Students using various data types:
CREATE TABLE Students (
Student_ID VARCHAR(6), Student_Name VARCHAR(50), Grade INT, Section CHAR(1), Roll_Number INT, Library_ID VARCHAR(7), House_ID VARCHAR(4), Enrollment_Date DATE
); This query will create a table with the following structure:
Student_ID Student_Name Grade Section Roll_Number Library_ID House_ID Enrollment_Date
The Create Table command is used to create a new table in a database. When defining a table, you can set a primary key to ensure each record is unique.
Syntax:
Create Table table_name ( column_name_1 data_type_1 PRIMARY KEY, column_name_2 data_type_2,
column_name_n data_type_n
); Example:
CREATE TABLE Students (
Student_ID VARCHAR(6) PRIMARY KEY, Student_Name VARCHAR(50), Grade INT, Section CHAR(1), Roll_Number INT, Library_ID VARCHAR(7), House_ID VARCHAR(4), Enrollment_Date DATE
);
In the above created Students table, the Student_ID field is the primary key and will contain only the unique values in it.
Now, we have created a table. Let us insert the values in the created table, Students.
Syntax:
INSERT INTO table_name (column1, column2, ...) VALUES (value1, value2, ...);
Example:
INSERT INTO Students (Student_ID, Student_Name, Grade, Section, Roll_Number, Library_ID, House_ID, Enrollment Date) VALUES (‘STU001’, ‘Riya Das’, 7, ‘A’, 23, ‘LIB007’, ‘H001’, ‘24-07-2024’);
This command will insert the values in the Students table. Student_ID

The SELECT statement is used to query the database and retrieve specific data.
Syntax
SELECT column1, column2, ... FROM table_name
WHERE condition;
Examples
Let us select all columns for all students from the Students table:
SELECT * FROM Students;
To select specific columns, such as Student_Name and Grade, we use:
SELECT Student_Name, Grade FROM Students;
To filter the results and retrieve only students from Grade 7:
SELECT * FROM Students WHERE Grade = 7;

There are other Database Management Systems besides MySQL like Microsoft SQL Server and MongoDB. Scan this QR code to know more about them.

To create a table, we use command to define its structure.
To show data from a table, we use command.
Identify and write down the field names with their data types if you have to create a table named Library
4 Identify the given commands as DDL or DML and write their type in the blank space. a select
5 Look at the structure of the given table. Which field according to you should be a primary key?
Table name: Library_Inventory
Book_ID Title Author Year Publisher ISBN
1 Database is a collection of information stored electronically in a computer system, organised in tables with rows (records) and columns (attributes).
2 DBMS (Database Management System) is a software that helps store, retrieve, and manage data in a database. Examples include MySQL, Oracle, and SQL Server.
3 Primary key is an attribute or set of attributes that uniquely identifies each row in a table. It ensures data integrity by preventing duplicate entries.
4 SQL (Structured Query Language) is a language used to manage and manipulate databases.
5 DDL (Data Definition Language) is a type of SQL commands used to define and modify the structure of database objects. For example, CREATE, ALTER, and DROP.
6 DML (Data Manipulation Language) is a type of SQL commands used to manipulate data stored in the database. For example, SELECT, INSERT, UPDATE, and DELETE.
7 Data types in SQL define the type of data that can be stored in a column. For example, NUMERIC, CHAR, VARCHAR, and DATE.
A. Fill in the blanks.
A is a collection of information stored electronically in a computer system.
The is the software that helps us store, retrieve, and manage data in a database.
In a table, the column headers are known as
A key uniquely identifies each row in a table.
The SQL command used to insert values in the created table is

B. Tick () the correct option.
Which of the following is a numeric data type in SQL?
a CHAR
c INT
What does DML stand for?
a Data Modification Language
c Data Manipulation Language
What is the purpose of the primary key in a table?
a To store text data
c To perform calculations
b VARCHAR
d DATE
b Data Management Language
d Data Mining Language
b To uniquely identify each row
d To store date values key help us to establish a relationship between different tables.
a Primary b Composite
c Foreign d Candidate
Which of the following is an example of DBMS software?
a MySQL b Python
C. Who am I?
I am the software that acts as an interface between the database and user applications.
I ensure that the data in a database is correct, whole, and consistent.
I am a language used to manage and manipulate databases.
I am a command used to create a new table in a database.
I am a type of SQL command used to define and modify the structure of database objects.
D. Write T for True and F for False.
Databases are used to keep information organised and make it easier to find.
A primary key can have duplicate values.
SQL stands for Structured Query Language.
The SELECT command is used to insert data into a table.
A
and security to the database.
E. Answer the following questions.
What is a database, and why is it important?
Explain the role of a Database Management System (DBMS). What are the different components of a DBMS?
Give an example of a SQL query to create a table with a primary key.
F. Apply your learning. HOTS
Create a table named ‘Teachers’ with columns for Teacher_ID, Teacher_Name, Subject, and Contact_Number. Make Teacher_ID the primary key.
Insert a new row into the “Teachers” table with the following values: Teacher_ID: ‘T001’, Teacher_Name: ‘John Doe’, Subject: ‘Math’, Contact_Number: ‘1234567890’.
Vijay has started his own movie theatre. He wants to keep a record of the movies he plays in his theatre. Write SQL commands to create a database and table for the same.
Rahul is a video game player. He wants to create a leadership board with each player’s name, score, and level achieved. Write the SQL commands to create a leadership board table and add records in it.
Describe a real-world scenario where you would use a composite key in a database table.








Canva is a free graphic design platform used to create graphics and presentations. The word ‘graphics’ refers to visual art or images. Using graphics and text, we can easily convey ideas and information to a reader.
Canva is used for making various types of visuals that can be used in posters, on social media, presentations, flyers, infographics, and many more.
To get started with Canva, follow the steps:
1. Open a web browser.
2. Type www.canva.com in the address bar. The home page of the website opens.

3. Create a new account by clicking on the Sign up button. Or, log in to Canva by using your existing mail address by clicking on the Log in button.
To log in to an existing account To create a new account





After you log in, the first screen will look like the image given here. You can see a variety of design templates and tools that you can choose from.
Let us create a card on the topic, ‘Digital India.’
Follow the given steps to create a card:
1. Click the Create a design button in the top left-hand corner of the screen. The Create a design window will appear.
2. Type ‘card’ in the search bar. The options related to card appear.

3. Select the size of the card that suits your requirement.
4. A new window opens where you can design the card.
To set the background image for your card, follow the steps:
1. Scroll down the left-hand sidebar and then select the Apps option. The Apps panel will appear.
2. Choose the Background option from the list. Various background options will appear. Choose a suitable background from the list.
Elements in Canva are colourful images, stickers, icons, and shapes that you can easily add to your designs to make them interesting.
Let us follow these steps to add some elements on the card:
1. Click the Elements option on the sidebar. A drawer menu appears.
2. Browse the various elements displayed in the menu
3. You can also type a keyword in the Search elements box and press Enter.
4. The elements related to the keyword will appear.
5. Select an element to add. The selected element appears in the design area.
6. You can select the added element by clicking on it and move it anywhere on the card. You can also rotate the element by clicking on the Rotate button.

Other than elements, you can also add text to your design. Follow the given steps to add text to your project:
1. Click the Text option on the sidebar. A drawer menu appears.
2. Select the Add a text box button.
3. A text box with default settings appears in the design area.
4. You can select the font style and font size from the text options displayed in the options bar above the design area. Now, type the desired text in the text box.

In a similar manner, add more elements and text to your design.

A layer can be considered as a transparent sheet. Suppose you need to create a drawing with various elements. There are multiple transparent sheets with one element drawn on each sheet. Now, put these sheets on top of each other. You can observe a complete drawing with multiple elements.
When you add new elements to Canva, they get placed on top of each other, creating layers of elements.

After all the elements are placed in the design area, you can position them as required. Let us explore the various ways to position an element or a layer.
1. Click on an element.
2. Click on Position in the Options bar.
3. A sidebar opens on the right-hand side, consisting of two tabs, Arrange and Layers.

Let us learn about the various options in the Arrange and Layers tabs.
a. Arrange Tab
In the Arrange tab, the general settings for arranging various elements appear. This panel is further divided into various sections.
Layers Arrangement Section
The first section helps us with the arrangement of layers.
Forward—moves the selected layer a layer above.
To front—moves the selected layer to the top of the stack.
Backward—moves the selected layer a layer below.
To back—moves the selected layer to the bottom of the stack.
This section helps you to align the elements on your page.
For vertical alignment, use the options Top, Middle, and Bottom
For horizontal alignment, use the options Left, Centre, and Right.
Let us align the text ‘Digital India’ to the top of our design:
1. Select the text to be aligned.
2. Then, select the top option, to position the element vertically on the top of the design page.
The Advanced section lets you move, turn, or resize elements in your design, using exact values.
Width refers to how wide an object is, and height refers to how tall an object is.
In Canva, you can type the values to specify the exact object size.
You can change the values of width and height by typing the required values in the Width and Height fields. Here, px stands for pixels.
Rotate
The Rotate option in Canva allows you to turn the element around at the required angle. You can use this feature to show elements from various angles.
Follow the given steps to rotate an element:
1. Select the element to be rotated.
2. Change the value of the Rotate field to the required angle.
Alternatively, you can also rotate elements with the help of the Rotate icon.

Hold the Rotate icon and move it to change the angle of the element.
b. Layers Tab
You can use the Layers tab to view the list of the layers in your project. By dragging the layers using a mouse, you can arrange the layers from this tab as well.
Using the All Tab
Go to the Layers tab and select the All tab under it.

Using the Overlapping Tab
Top Layer
Different layers in the design
Bottom Layer
If there are multiple layers in a project, it becomes difficult to select the exact layer on which you want to work. In such a case, the Overlapping tab is helpful.
1. Go to the Layers tab and select the Overlapping tab under it.
2. This tab shows only the layers that overlap with a selected layer. Select the layer you are looking for and make the required changes.
Imagine you are creating graphics in Microsoft Paint. You have added a few shapes and text overlapping each other. Later, you realise that the text is hiding behind the shapes. Is it possible to correct it without re-creating it in Paint? If you create the same project in Canva, how would it be helpful?

Duplicating a layer means creating a copy of it. This can save a lot of time when you want to use the same element multiple times in a project. What if you want to add two mobiles? You will simply duplicate the layers.
Follow the given steps to duplicate a layer:
1. In the Layers tab, right-click the layer that you want to duplicate. A drop-down menu appears.
2. Select the Duplicate option.
3. The selected layer is duplicated.



Deleting layers that are not needed helps maintain an organised design. To delete an element from your design, delete its corresponding layer.
Follow the given steps to delete a layer:
1. In the Layers tab, right-click the layer you want to delete.
2. Select the Delete option.
3. The selected layer is deleted.


As of 2023, 80 crore designs were created using Canva since its launch.
Create a similar design in Canva and guess the alignment of the text ‘Happy Birthday’ in the following designs.


a The Middle and Center alignment options serve the same purpose.
b The To Front option is different from the Forward option.
c The To Back option places an element immediately behind the other element.
d You can change the order in which the elements are layered.
Tick () the correct option.
The Align to Page feature helps you to:
a Make elements invisible.
c Align the elements on page.
Have you ever seen a flipbook?
b Create complex designs.
d Change the colour of the element.
It is a small book with a series of images at various positions on separate pages. When you quickly flip through such a book, it creates the illusion of movement of the objects drawn on the pages.
The cartoon movies that you watch are created in a similar fashion. Many images are drawn and flipped through at a fast pace so that the characters seem to be moving. This is what we call animation
Animation is a method in which figures or objects are manipulated to appear as moving images


“Snow White and the Seven Dwarfs”, released in 1937, is Disney’s first full-length animated movie!
After creating a design in Canva, you can make it look interactive by adding animations. Canva has many useful tools using which you can create interesting animations. Let us learn how to use them.
Page animations decide how your page will enter the screen. Follow the given steps to add page animation:
1. Select the page. (Make sure you select only the background, not the other elements.)

2. Click the Animate option on the top bar. A sidebar with the tab Page Animations opens showing a list of animations.

3. Place the mouse cursor over the effects to see what they look like on your page.
4. Click the Play button, at the top right-hand side of your screen to observe the effect of the animation.

You can animate specific texts and elements present on a page in the same way as you can animate the entire page.
Follow the given steps to add element animation:
1. Click the text/element you want to animate.
2. Select the Element Animation tab from the sidebar and apply the desired animation effect to your element.
Applying transparency means making the elements look see-through. In Canva, all elements are fully visible by default. This means that Transparency is set to 100.
To apply transparency:
1. Select an element from your design, for example, the mobile.

2. Click the Transparency icon from the options bar above the design area. The Transparency slider appears.
3. Move the slider to the left to decrease the transparency of the element and to the right to increase it.
4. Observe the effect on the element’s transparency.

Suppose you like the style of an element or a page, such as font, colour, effects, or transparency. You can apply the same styles to other elements or pages as well.
To copy and apply a style, follow the given steps:
1. Let’s say, you like the mobile for its transparency and want to copy the same to another element.
2. Right-click the mobile. A context menu appears.
3. Click the Copy style option. The style is copied.
4. Click the element where you want to apply the copied style. For example, click the image of the laptop.
The laptop becomes transparent with the same transparency value, just like the mobile.

Locking an object makes sure that the object remains on its place while you work on the other parts of the design. You can either lock an individual element or the entire page.
To lock the entire page:
1. Select the thumbnail of the page from the bottom and click on the More option (three dots).
2. A context menu will appear. Select the Lock page option to lock the page.

How can the Lock feature be helpful when you are creating a project?

To lock the specific elements, right-click the element and select the Lock option from the context menu. The element is locked. Note that another Lock symbol appears near the locked element.
To unlock the element, click the Lock symbol again.




Fill in the blanks.

Wonder how animation works practically? Scan this QR code.
a Page Animation decides how the will enter the screen.
b To see how your animation looks on an element, you use the button.
c The feature is used to copy the style of an element to another.
Match the following: Task Icon
When you want to make sure that the object remains on its place.
When you want to make the elements look see-through
When you want to have the same style as the current element


Canva is a free graphic design platform that is used to create various visual contents, such as graphics, presentations, posters, social media graphics, flyers, and more.
Canva has a wide variety of design templates and tools to choose from for your projects.
Canva offers colourful images, stickers, icons, and shapes as elements that you can easily add to the designs to make them more engaging.
You can also add text to your design using the Text option from the sidebar. You can choose various options for fonts, sizes, and types.
When you add new elements in Canva, they are placed on top of the ones you have already added, creating layers of elements.
You can use the Position option to adjust the layering, alignment, and size of elements.
You can make your designs look interactive by adding animations.
You can use the Copy Style option to copy the style of one element and apply it to other elements.
You can use the Lock option to lock specific elements or the entire page to prevent accidental changes while working on other parts of your design.
A. Fill in the blanks.
Hints Create a design Transparency Position shapes visuals
Canva is a popular online tool used for creating various types of
To create a design in Canva, you need to click the button.
Elements in Canva include graphics, stickers, icons, and
The option in Canva allows you to control the arrangement of various elements in your design. means making the elements look see-through.
B. Tick () the correct options.
What can layers in Canva NOT be compared to?
a Transparent sheets kept on top of each other b Jigsaw puzzle
c Layers of paint d Images put on top of each other
In Canva, all elements are fully visible by default. This means that the Transparency setting is at what value?
a 0 b 50
c 100 d 75
Which tab helps you set the background image for your card in Canva?
a Text b Apps
c Draw d Background
What does adjusting transparency in Canva do?
a Changes the font size of the element
c Makes a layer see-through
How does the Copy Style feature in Canva help your design?
a It changes the animation effects.
c It duplicates the entire design.
C. Who am I?
I prevent unwanted changes in the project. 1
I make layers see-through, creating visual effects and overlays.
I can save a lot of time when you want to use the same element multiple times in a project.
b Rotates the element
d Duplicates the element
b It applies the same style from one element to another.
d It adds comments to the design.

I help you position the element at the top, middle, or centre of the design area.
I am used to turn elements around by a desired angle.
D. Write T for True and F for False.
Canva is difficult to use and requires professional design skills.
The Layers tab in Canva helps order the elements like a stack.
Locking objects in Canva prevents any changes to that element.
The element will not be visible if the transparency value is 100.
The Forward option brings the layer to the top of the stack.
E. Answer the following questions.
What is the purpose of the Position option in Canva?
Explain the difference between the Forward/Backward and To Front/To Back arrangement options.
What is animation?
What are layers? Give an example.
Why would you use the Lock option for an object in Canva?
F. Apply your learning.
Aleena is making a poster for Diwali. She placed various elements in her design. Which Canva feature can she use to put the elements exactly in the centre?
Archita made a crossword puzzle for her classmates, using Canva. However, she made some adjustments to the project, causing the crossword to become nearly invisible. What do you think she must have done?
Maya is creating a design with lots of elements. She wants some objects to be in front while others hide behind them. Which Canva feature can she use to control the layers and make her design look like a playful scene?
Imagine you are a young chef who wants to share your favourite recipes. You have designed a digital recipe card using Canva. You have created multiple layers of elements in the recipe card. The text of the recipe card is hidden behind the images. What might be the problem?
Rani created a card for her friend’s birthday. She was showing it to her younger brother Anuj. Anuj was very curious and deleted the text in the card by mistake. How could have Rani prevented this mistake?







We live in a world filled with data. Think about all the things you do in a day—sending text messages, watching videos online, playing games, or even searching for something on the internet. Each of these activities generates data. Now, imagine the amount of data created by everyone in the world doing these activities every single day. That is what we call big data.
Big data refers to extremely large sets of data that can be analysed to reveal patterns, trends, and associations, especially relating to human behaviour and interactions.






Big data is not just about having a lot of data. It is about how we handle and use this data to make decisions. There are six main characteristics of big data, often called the six Vs:
1. Volume: This means the amount of data. For example, all the photos, videos, and messages that are sent on social media every minute. That is a huge volume of data.
2. Velocity: This refers to the speed at which data is generated and processed. For example, every second, thousands of tweets are posted on Twitter. The faster we can process this data, the more quickly we can react to trends.
3. Variety: This means different types of data. Data comes in many forms, like text, images, videos, and even sounds. For example, a video of a cute cat is different from a text message about dinner plans, yet both are valuable data.
4. Veracity: This refers to the quality or accuracy of the data. It is important to ensure that the data we use is reliable and trustworthy. For example, data collected from a broken sensor might not be accurate.
5. Value: This means the usefulness of the data. Not all data is equally valuable. For example, data about what people buy online can help companies decide what products to stock.
6. Visualisation: Visualisation is often considered as the sixth V of big data. Visualisation is crucial in big data because it allows complex data to be presented in a more understandable and accessible way. By using graphs, charts, and other visual tools, we can interpret and analyse large datasets more effectively, helping to uncover trends, patterns, and insights that might not be immediately apparent from raw data alone.
Let us take the example of Smart City and how we can apply the concept of 6 Vs to it.
Volume: A smart city generates enormous amounts of data from various sources, such as traffic sensors, surveillance cameras, social media, weather stations, and public transportation systems. For instance,

thousands of cameras and sensors installed across a city can generate terabytes of data daily, providing insights into traffic patterns, crime rates, and environmental conditions.
Velocity: In a smart city, data needs to be processed in real-time to be effective. For instance, traffic management systems rely on real-time data from traffic lights, road sensors, and GPS devices in vehicles to manage congestion and reroute traffic efficiently. This real-time processing helps reduce traffic jams and improve commute times.
Variety: A smart city collects a wide variety of data from different sources. Structured data might include numerical data from utility usage, semi-structured data might involve XML files from sensors, and unstructured data might consist of social media posts, video feeds, and images. For instance, data from social media can help city officials gauge public sentiment and respond to concerns more effectively.











































Veracity: In a smart city, ensuring the accuracy and reliability of data is crucial. For example, data from weather sensors must be accurate to predict weather conditions effectively and prepare for natural disasters. Similarly, accurate data from health sensors can help monitor the spread of diseases and manage public health resources efficiently.
Value: The goal of collecting and analysing big data in a smart city is to derive valuable insights that improve urban life. For instance, analysing data from energy consumption can lead to more efficient energy use and cost savings for residents. Data from public transportation can be used to optimise routes and schedules, making commuting more convenient for citizens.
Visualisation: At the end, presenting this data through visualisations, such as interactive maps and dashboards, helps decision-makers and citizens understand and utilise the information effectively.
Match the characteristic of big data with its description.
Column A
Volume
Velocity
Variety
Veracity
Value
Visualisation
Column B
The speed at which data is generated and processed
The accuracy and reliability of the data
Presenting data in an understandable and accessible way using visual tools
The amount of data generated
Different types of data, such as text, images, videos, and sounds
The usefulness of data for making decisions
To work with big data, we need to first collect it from various resources and then interpret it to analyse. Let us learn how to do it.
Big data is collected from various sources. Here are some common ones:
1. Social media: Platforms like Facebook, Twitter, and Instagram generate tonnes of data through posts, likes, comments, and shares.


2. Sensors: Devices like weather stations, GPS systems, and even smart home devices collect data continuously. For example, a fitness tracker records your steps, heart rate, and sleep patterns.
3. Transactions: Every time you buy something online or use a credit card, data is collected about what you bought, where you bought it, and how much you spent.
4. Websites: Websites collect data on what pages you visit, how long you stay on them, and what you click.

5. Surveys and forms: When you fill out a survey or form, you provide data that can be analysed to understand trends and preferences.
Collecting big data is just the first step. To make sense of it, we need to analyse and interpret it. Here are some ways this is done:
1. Data Mining: This is the process of discovering patterns and relationships in large sets of data. For example, a grocery store might use data mining to find out which products are often bought together.



2. Machine Learning: This involves teaching computers to learn from data and make predictions or decisions. For example, a machine learning algorithm might learn to recognise spam emails based on patterns it finds in previous emails.
3. Data Visualisation: This means creating visual representations of data, like graphs and charts, to make it easier to understand. For example, a line graph might show how sales have increased over time.
4. Statistical Analysis: This involves using statistics to analyse data and make conclusions. For example, calculating the average score of a class in a test to understand overall performance.
Consider a weather app. It collects data from weather stations and satellites, and then uses data visualisation to show you a map with the current weather conditions. It also uses machine learning to predict the weather for the next few days based on patterns in the data.
Big data is used in many different fields. Here are some examples:
1. Healthcare: Big data plays a crucial role in healthcare. It helps doctors predict diseases outbreaks, understand patient symptoms, and improve treatments. For example, during flu season, hospitals can use big data to prepare for more patients.
2. Transportation: Big data helps cities manage traffic flow, reduce accidents, and improve public transport. For instance, by analysing traffic data, cities can change traffic light timings to reduce congestion.
3. Shopping: Big data helps stores understand what products are popular, manage inventory, and personalise shopping experiences. For example, an online store might suggest items you might like based on your previous purchases.
4. Finance: Big data enhances risk management and fraud detection by analysing market trends and transaction patterns in real-time, preventing potential risks and fraudulent activities. It also provides valuable customer insights, allowing banks to offer personalised services and improve customer satisfaction.
5. Retail: In retail, big data enables personalised marketing and targeted campaigns by analysing customer behaviour and purchase history. It optimises inventory management by predicting product demand and allows for dynamic price adjustments based on market trends and customer preferences.
6. Entertainment: Big data helps streaming services recommend films and shows and helps video game developers understand player behaviour to improve games.
7. Education: Big data can help teachers understand how students learn best and create personalised learning plans. For example, educational apps can track how students interact with content and provide feedback to teachers.
8. Environment: Big data aids climate change analysis by processing large volumes of environmental data, helping understand climate patterns and develop mitigation strategies. It also supports wildlife conservation through data from sensors and tracking devices and facilitates real-time pollution monitoring to maintain air and water quality.

Big data continues to grow and evolve, and it will play an even bigger role in the future. Here are some ways it might affect our lives:
1. The future of big data is set to revolutionise how we collect, analyse, and utilise information, driven by several key trends. Data generation will surge due to the rapid growth of IoT devices, social media, and sensors, providing vast amounts of information for analysis. For example, smart home devices will continuously generate data on energy usage, contributing to more efficient home management.
2. Integration with advanced analytics and AI will enable predictions that are more accurate and automate decision-making, such as using machine learning to forecast market trends.
3. Real-time processing will enhance decision-making speed and efficiency, as seen in fraud detection that identify suspicious transactions instantly.
4. Edge computing will reduce latency by processing data closer to its source, crucial for applications like autonomous vehicles that require immediate data analysis.
5. Enhanced data security and privacy measures will be essential, with advanced encryption protecting sensitive information like personal health records.
6. Greater interoperability between platforms will facilitate seamless data integration, for instance, combining data from various healthcare systems to improve patient care.
7. Ethical and responsible data use will gain prominence, ensuring fairness and privacy in analytics.
8. Industry-specific applications will drive innovation, such as using big data in agriculture for precision farming and crop management.
9. Big data will also aid sustainability efforts by analysing environmental data to develop strategies for reducing carbon footprints.
10. Collaboration between humans and machines will enhance decision-making, such as AI-assisted tools providing insights that improve business strategies.

Big data could help create ‘smart cities’ where self-driving cars communicate with traffic lights to reduce congestion and accidents. These cities will use real-time data from various sources to improve everything from public transportation to energy consumption.
Let us perform the following activity to understand how AI learns from data.
Objective: The Impact Filter experiment has a huge data base of images of various species. While performing this experiment, one can experience how rising temperatures affect the survival of various species and how it would affect our daily lives.
Follow the given steps to learn how this application works.
1. Visit the link: https://artsexperiments.withgoogle.com/impactfilter/
2. The following screen appears.
3. Click on the CLICK TO START button.
4. You will be redirected to a tutorial. If you wish to take the tutorial, then follow the steps. Otherwise, you can exit it.
5. Now, from the top bar, select any of the various categories of species, such as insects, birds, reptiles and amphibians, and so on. Let us click on the INSECT category.

6. Another web page with the option of insects will appear. Click on any of them, for example, BUMBLEBEE

7. A web page opens, showing the percentage of bumblebee that will disappear at the current temperature of the Earth, which is already increased by 1.2 °C.
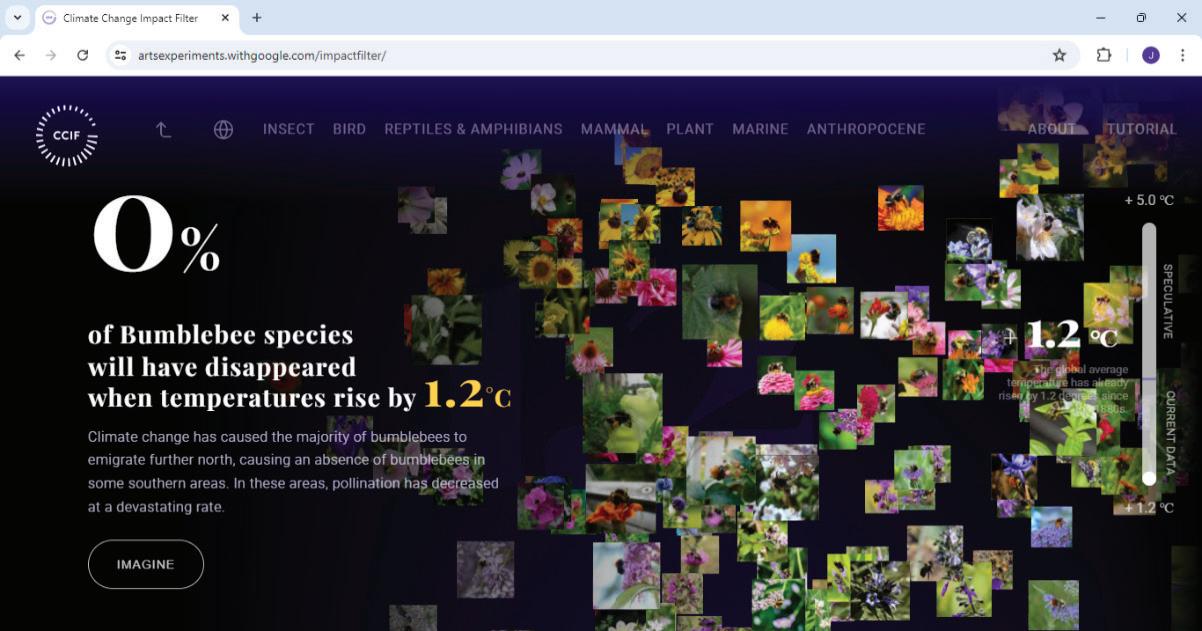
8. Look at the bar on the right side displaying the temperature. It can be used to increase or decrease the temperature by moving the slider upwards or downwards.
9. You can observe the impact of rising temperatures on the population of bumblebees as you increase the temperature.
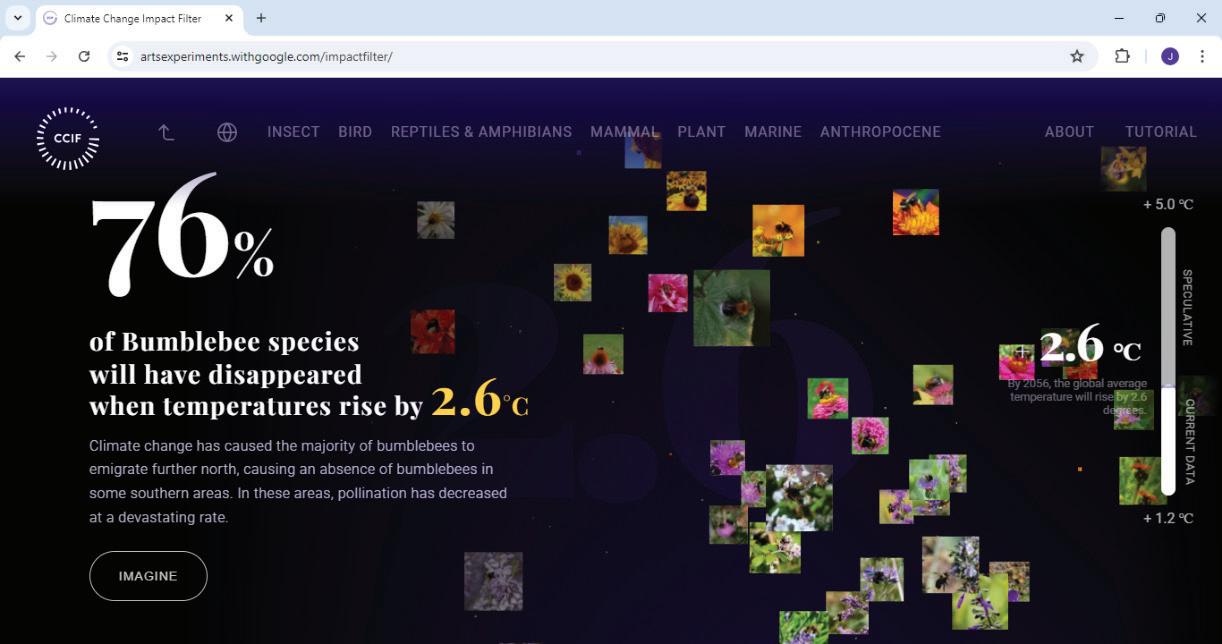
10. You can try the same with the other species as well, and understand the impact of rising global temperature on these species.




Create a table to analyse the performance of your classmates in a weekly test. Record the values in the given table and complete it. A sample entry has been done for you. After that, answer the following questions.

1 Big data refers to extremely large sets of data that can be analysed to reveal patterns, trends, and associations.
2 The amount of data generated, such as photos, videos, and messages.
3 The speed at which data is generated and processed, like the rapid posting of tweets.
4 The different types of data include text, images, videos, and sounds.
5 The quality and accuracy of data, ensuring reliability and trustworthiness.
6 The usefulness of data, determining how valuable it is for making decisions.
7 Presenting complex data in a more understandable and accessible way using graphs, charts, and other visual tools.
8 Big data is used in various fields like healthcare, transportation, shopping, finance, retail, entertainment, education, and the environment.
A. Fill in the blanks.
Hints volume patterns visualisation variety velocity
1 Big data refers to extremely large sets of data that can be analysed to reveal .
2 The of data means the amount of data generated.
3 refers to the speed at which data is generated and processed.
4 Different types of data are referred to as
5 is crucial for presenting complex data in a more understandable way.
B. Tick () the correct options.
1 Big data can reveal patterns, trends, and:
a Numbers b Associations
c Colors d Shapes
2 The of big data involves ensuring the data is reliable.
a Volume b Veracity
c Variety d Visualisation
3 An example of the of data is the rapid posting of tweets.
a Velocity b Value
c Visualisation d Variety
4 Data that includes text, images, and videos is an example of: a Volume b Veracity c Variety d Velocity
5 Presenting data using graphs and charts is an example of:
a Volume b Visualisation
c Velocity d Veracity
C. Who am I?
1 I am the characteristic of big data that ensures the accuracy and reliability of data.
2 I refer to the speed at which data is generated and processed.
3 I represent the usefulness of data for making decisions.
4 I involve presenting complex data in an understandable way.
5 I refer to the amount of data generated.
D. Write T for True and F for False.
1 Big data only includes text data.
2 Volume refers to the speed at which data is generated.
3 Visualisation helps in making complex data more understandable.
4 Value determines the usefulness of data.
5 Veracity refers to the variety of data types.
E. Answer the following questions.
1 What is big data?
2 Explain the concept of volume in big data.

3 What is data mining?
4 What are the ways through which you can collect big data?
5 Give an example of how big data is used in healthcare. F. Apply your learning.
1 Riya is analysing traffic data in a smart city. Explain how volume, velocity, and variety play a role in her analysis.
2 Arjun is managing a public transportation system. Discuss the importance of veracity and value in his work.
3 Priya is working in retail. Describe how visualisation can help her business.
4 Kabir is studying the future trends of big data. How might these trends affect his daily life?
5 Ananya is reflecting on how big data is collected. Give an example from her life where big data might be collected and used.








Have you ever wondered how your phone unlocks itself with your face or fingerprint, and how some apps suggest words while you type, or recommend TV shows that you might like? All of this is possible because of Machine Learning (ML). Let us learn more about machine learning in this chapter.
Machine Learning (ML) is a branch of AI that makes machines learn from large amounts of data. By identifying patterns in this data, machines can make predictions or decisions without needing explicitly programmed instructions. Machine learning enables a computer system to learn from this experience of using the provided data, and making accurate algorithms for predictions or decisions from them.



To better understand how machines learn, let us take an example of fruits. Let us take an apple and a banana. How do we differentiate between them? When we look at an apple, we know it is spherical in shape and red in colour. However, when we look at a banana, we see that it is curved in shape and yellow in colour.
Just as we can differentiate the two fruits by looking at their shapes and colours, computers too can differentiate them from the data we provide, such as images of apples and bananas. We show the computer a lot of images of each fruit. The computer identifies the patterns. It appears that all the images of apples follow a certain pattern (in terms of colour and shape), whereas the images of bananas follow a different pattern. We call these images of apples and bananas as training data, as we use these images to train the computer to learn about the patterns of the fruits.
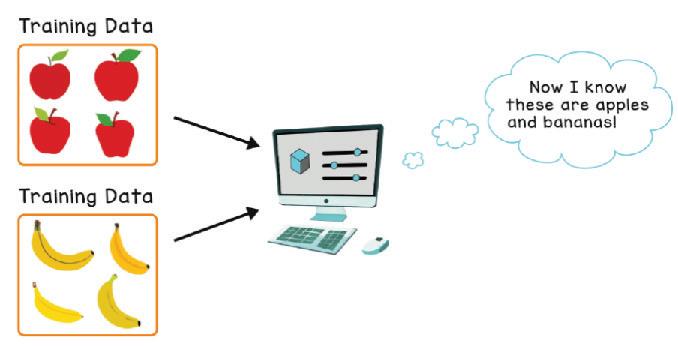
Training Data
Now I know these are apples and bananas!
Training Data
Once the computer has learnt to identify and understand the pattern, we use test data, which is any new image of an apple or a banana, and give it to the computer to identify the image based on its learning.
It’s an apple!
Data
It’s a banana!
Data
Machine learning involves showing a large volume of data to a machine so that it can learn and make predictions, find patterns, or classify data. The three types of machine learning are supervised, unsupervised, and reinforcement learning.
Supervised learning is a machine learning method that uses well-labelled datasets to train algorithms to predict outcomes and recognise patterns.
In supervised machine learning, we know the data really well. We provide this known data to the machine learning model, which then learns from the data. Here, the model refers to the algorithms or programs, which can be trained to give intelligent outputs and solve our problem statement. Once the model learns the relationship between the input and output data, it becomes capable of classifying new and unseen datasets, as well as predicting outcomes.
The identification of apples and bananas as different fruits is a great example of supervised learning.
Since we knew the data really well, i.e., apples are spherical and red, while bananas are curved and yellow, we ‘feed’ this data to the computer by providing a large number of images of both apples and bananas. This is then reasoned into the statements, “Given an image of an apple, we know it as an apple”, and “Given an image of a banana, we know it as a banana”.
Thus, the computer learns this information, and applies it on new images, thereby starting to make predictions.

Its an apple!
These are apples.
As the name suggests, unsupervised learning is a machine learning technique in which models are not supervised using datasets. In unsupervised machine learning, machines do not know any patterns in the data. Instead, the model itself finds hidden patterns and insights from the given data.
Imagine showing a computer various picture of fruits—apples, bananas, and grapes. We do not tell the computer anything about these images, including which one belongs to which fruit. We simply display all the images on the computer. The computer automatically finds a pattern in these images.
For example, it understands that all the apple images have similar properties, like red colour and spherical shape. All the bananas have similar properties, like yellow colour and curved shape. Similarly, all the grapes have similar properties, like green colour and small and round shape.
Hence, it creates clusters (groups) and separates these images into three different groups.
Now, every time you give a new image of apple, banana, or grapes, the computer can ‘separate’ them into one of these three groups. This is an example of unsupervised learning.

I can see a pattern.
Reinforcement learning is a type of machine learning where an agent learns to take actions in an environment to maximise a cumulative reward. The agent learns through trial and error, receiving rewards for good actions and penalties for bad ones. In our fruit recognition problem, the computer learns to recognise fruits by identifying images. When the computer correctly identifies a fruit, it receives a reward. However, if it guesses incorrectly, there is no reward. With each attempt and its corresponding feedback, the computer becomes ‘smarter’. It starts recognising the key features that distinguish different fruits. For example, it learnt that apples are red and spherical, while bananas are curved and yellow. This process helps it understand which actions, like identifying specific features, are effective and which can be ignored.
The learning and accuracy of the machine learning model are dependent on various factors, like:

• Quantity of Data: The more images of apples and bananas we feed to the computer, the better it will learn from this data and predict more accurately.
• Quality of Data: Depending on how good the images of apples and bananas are, the accuracy of the model will vary.
Let us do the following experiment using the application Teachable Machine to understand how machine learning works.
Objective: Teachable Machine is a web-based tool that makes the creation of machine learning models fast, easy, and accessible to everyone. It helps train a computer to recognise images, sounds, and poses. Follow the given steps to explore how this application works.
1. Visit this link: https://teachablemachine.withgoogle.com/
2. The following window opens. Click on the Get Started button.


3. You will be directed to a web page, as shown. From the window that appears, you can use any of the following options to teach your machines:
• Images: To teach a model to classify images using files on your system or your webcam.
• Sounds: To teach a model to classify audio by recording short sound samples.
• Poses: To teach a model to classify body positions or poses using image files on your system or striking poses in your webcam.

4. Let us create a pose project. For this, click on the Pose Project option.
5. Collect images of random people’s sitting and standing poses, as shown. Here is the training data, in the form of images of standing and sitting poses, for your reference.













Machine learning can help predict earthquakes. By analysing seismic data, these algorithms can find patterns that might indicate an impending earthquake, providing early warnings and potentially saving lives.
6. Click on the Upload button to upload the images related to these poses.
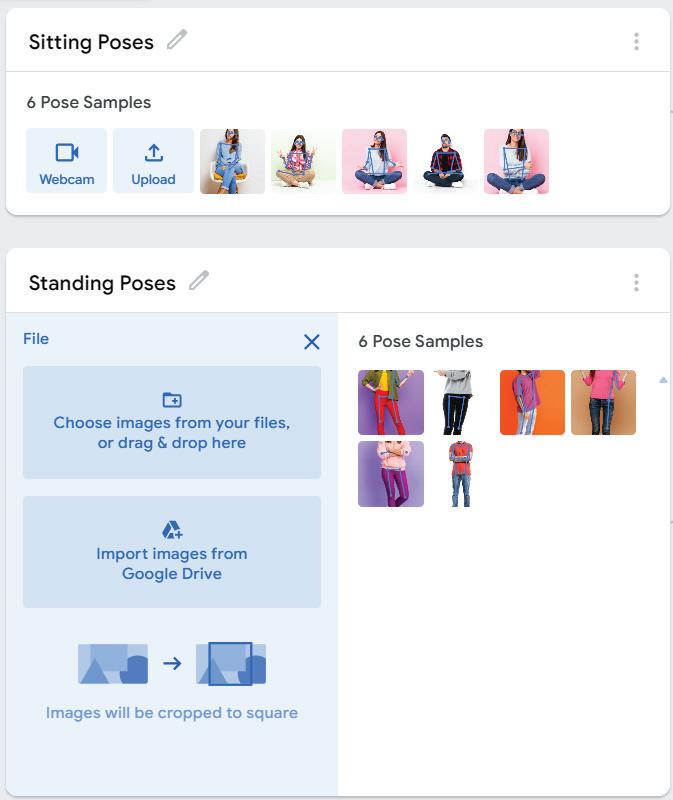
7. The results of any machine learning model depend on the examples or the sample data you give it. So, if it’s not working as you had intended, then add more samples in the training data that was provided to your computer.
8. After uploading the training data, click on the Train Model button.
9. Now, test your machine learning model by posing in front of the webcam and see what Output (standing or sitting pose) it displays in the Preview window.
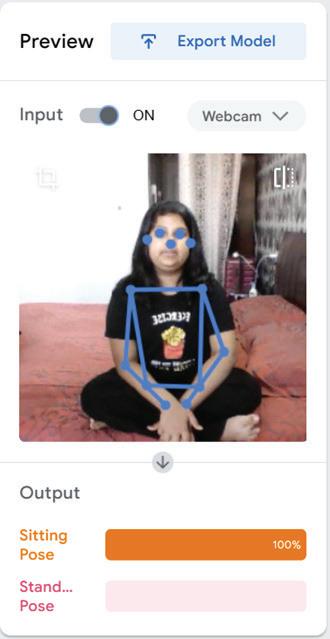


Match the following.
Column A Column B
Supervised Learning
Unsupervised Learning
Reinforcement Learning
Classification Problem
Clustering Problem
Trial and error learning
Predict outcomes from labelled data
Finding hidden patterns
Separating data into clusters
Identifying images of apples and bananas
From self-driving cars to personalised recommendations, machine learning is transforming our daily lives. Here are some exciting applications of this technology.
Recommendation Systems: Imagine that you have been watching a lot of videos on YouTube that are on computer programming. The machine-learning algorithms on YouTube track your choices. By analysing this data, they can recommend programming videos that align with your interests.

Language Translation: Google Translate, a translation app, uses machine learning to understand and translate text instantly, enabling us to communicate in different languages. It learns from millions of translated texts to understand the patterns and meanings in different languages.
Customer Service Chatbots: Have you ever wondered how the chatbots seem to get smarter with every new conversation? It is because of machine learning. By analysing the questions that the customers ask, these chatbots learn to provide increasingly helpful and accurate answers.


Image Recognition: Applications like Snapchat or Instagram can add fun effects to your photos by analysing your facial features using machine-learning algorithms. A machine learning application looks at your face in the camera and figures out where your eyes, nose, and mouth are. Then, it puts the filter on the right spot to make it look like it is part of your face. For instance, Snapchat might overlay a dog’s nose and ears on your face or add funky glasses.
Self-driving Cars: Self-driving cars use both computer vision (to see the road, pedestrians, vehicles, etc.) and machine learning (to make decisions). A self-driving car learns from all the different situations it encounters on the road, like slowing down on detecting pedestrians, stopping at a red light, or navigating around other vehicles.


Banking: Machine learning makes banking safer, more personalised, and easier for everyone. It helps banks detect unusual activity that may be fraudulent. It also helps banks decide who can get loans by looking at their borrowing history and their likelihood of repaying them. Also, there are chatbots on banking apps that provide customer support by answering questions effectively.
Weather Prediction: Machine learning helps predict the weather by analysing historical weather data, like temperature, precipitation, wind, etc., to find patterns. It makes use of these patterns to make better guesses about what’s going to happen next.

Deep Learning is a subset of machine learning in which a machine is trained with vast amounts of data which help it to train itself around that data. Some practical applications of deep learning includes virtual assistants, computer vision for driverless cars, detection of money laundering, face recognition, and many more. It is an AI function that mimics the working of the human brain in processing data and uses it in detecting objects, recognising speech, translating languages, and making decisions.
Deep learning is the most advanced form of artificial intelligence. Then there is machine learning, which is intermediately intelligent, and artificial intelligence which covers all the concepts and algorithms that, in some way or other, mimic human intelligence.





Unscramble the given words from 1 to 6. Then, form the term given afterwards by picking up the numbered letters from the unscrambled words.
MIT App Inventor is an online platform for creating apps for mobile phones and tablets. It is a very easy and simple platform to learn app creation and coding. This platform focuses on making everyone, especially young children, create their own apps. No coding skill is required to build your own app using MIT App Inventor. Apps are software programs that can be downloaded and installed on electronic devices.

MIT App Inventor was initially developed by Google and later released as an open-source project.
MIT app inventor can be accessed from the link: https://appinventor.mit.edu/ Here, you will learn the easy steps to create a mobile app to recognise the user’s speech. The components used for the application will be as follows:
1. A button to display ‘Start Speech Recognition’.
2. A label to show ‘Recognised text’.
3. Another label to display the recognised speech.
Step 1: Set Up MIT App Inventor
1. Go to the MIT App Inventor website (https://appinventor.mit.edu/).
2. Log in with your Google account. If you do not have one, ask your teacher or parents to help you create one.
3. From the Palette on the left side, drag a Button component into the viewer.
4. Set the Text property of the button to “SpeechRecognition”.

5. Drag a Label component onto the viewer.
6. Set the Text property of the Label component to “Recognised Text” and the FontSize property to 18.
7. Drag another Label component onto the viewer. This label will display the recognised speech.
8. Set the Text property to blank “ “ and the FontSize property to 18.
9. Rename this label to “RecognisedText”.

10. Now, from the Palette under the Media section, drag a SpeechRecognizer component into the viewer. This will appear in the “Non-visible components” area.
1. Click on the Blocks button in the top right.
2. Find the Button1 block under Screen1 and drag out the when Button1.Click block.
3. Inside this block, add the call SpeechRecognizer1.GetText block from the blocks drawer of the SpeechRecognizer1 component.
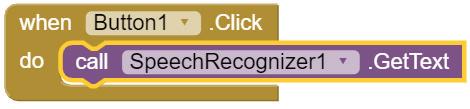
4. From the SpeechRecognizer1 blocks drawer, drag out the when SpeechRecognizer1. AfterGettingText block.
5. Inside this block, drag the set RecognisedText.Text to block.
6. Attach the get result block from the SpeechRecognizer1.AfterGettingText block.
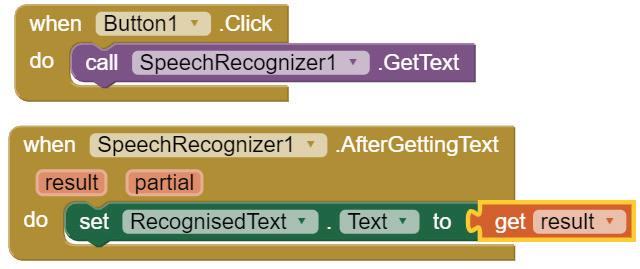
1. To connect to the companion, click on the Connect drop-down and select AI Companion.
2. A Connect to Companion window will open with a six-character code.
3. You can either scan the QR code or fill in this six-character code on the mobile phone app.
4. The app will now open on your mobile.
5. Click on the button that you have created, “Start Speech Recognition” button, and speak into the microphone.
6. The app will display the recognised text.

1 Machine Learning (ML) is a branch of AI where the machine makes predictions and decisions based on the data that we provide it.
2 In supervised ML, we give data to the machine on which it is already trained, and it learns from that data.
3 In unsupervised ML, we do not give any data that has patterns in it. Instead, the machine adapts itself to find the hidden patterns and insights from the given data.
4 In reinforcement learning, machines learn from the feedback on the predictions they make. They are rewarded for correct guesses. They learn about the nature of actions that are necessary or unnecessary.
5 Machine learning algorithms learn from your past choices or preferences and make recommendations for films, songs, articles, etc., tailored to your interests.
6 Google Translate, a translation app, makes use of machine learning to understand and translate texts instantly.
7 Machine learning helps chatbots function more efficiently by making them learn from the different types of questions customers ask and get better at giving helpful answers.

8 Self-driving cars use both computer vision (to see the road, pedestrians, vehicles, etc.) and machine learning to make decisions.
9 Deep Learning is a subset of machine learning where a machine is trained with vast amounts of data which then help it to train itself around the data. It is the most advanced form of AI.
10 MIT App Inventor is an online platform for creating apps for mobile phones and tablets.
A. Fill in the blanks.
Hints Google Translate test data supervised chatbot Machine Learning
1 is a branch of AI that uses large amounts of data to make predictions.
2 makes use of machine learning to help us communicate in different languages.
3 A interacts with you online to answer your queries or assist during online shopping.
4 In machine learning, we know the data really well.
5 Once the computer learns, we use or any new image, and the computer can identify these new images based on its learning.
B. Tick () the correct options.
1 In learning, a computer gets feedback on whether it is right or wrong.
a Reinforcement b Supervised
c Unsupervised d Superlative
2 How does machine learning helps in banking?
a It helps banks detect unusual activity.
b It helps banks decide who can get loans by looking at borrowing history.
c It provides customer support on banking apps.
d All of these.
3 Machine learning involves feeding a large volume of to a machine so that it can make predictions.
a Outputs b Data
c Noise d Algorithms
4 Which among the following is the most advanced form of AI?
a Supervised Machine Learning b Machine Learning
c Deep Learning d Unsupervised Machine Learning
5 In learning, the model can classify new datasets and predict outcomes after learning the relationship between input and output data.
a Supervised b Unsupervised
c Reinforcement d None of these
C. Write T for True and F for False.
1 Deep learning is a subset of machine learning.
2 Machine learning does not have the capability to predict the weather.
3 A self-driving car uses both computer vision and machine learning.
4 The accuracy of the machine learning model depends only on the quality of the data.
5 YouTube is an example of a recommendation system.
D. Answer the following questions.
1 Define machine learning.
2 Differentiate between supervised and unsupervised machine learning.
3 Explain any three applications of machine learning.
4 What is deep learning?
5 Differentiate between training data and test data.

E. Apply your learning.
1 When Neelam first heard about self-driving cars, she was curious about how she would manage to navigate on the road. Explain to Neelam how self-driving cars achieve this.
2 Yashika visits Germany, but she cannot speak German. You have suggested using Google Translate to communicate effectively there. Explain to her how the app can help her communicate with ease.
3 Avartika and her grandmother like adding filters to the pictures they click using Snapchat. Curious, Avartika’s grandmother asks her how these filters work. What should Avartika tell her grandmother?
4 Avni’s grandfather has found weather prediction apps on his phone. He is curious to know how those apps predict the weather. Explain the process to him.
5 Lovey wants to open her restaurant, for which she needs to create an app that can understand the language of foreign customers as well. Which platform can she use to create this app?


A. Fill in the blanks.
1 The octal number system has a base of .
2 An attempt to trick a user to get his or her personal information through fake emails is called .
3 in computational thinking refers to disregarding the minute details of a problem and focusing on its major issues.
4 The function in Google Sheets counts the number of cells that contain numbers.
B. Tick () the correct option.
1 A is a secret code that only you know and that can keep your online accounts safe from hackers?
a QR code
c Lock
b Password
d Computer program
2 Which term is used for breaking down a big, difficult task into smaller, easier ones in computational thinking?
a Abstraction
c Algorithm design
b Pattern recognition
d Decomposition
3 Which of the following functions returns remainder when the dividend is divided by the divisor?
a Max
c Min
C. Write T for True and F for False.
b Mod
d Average
1 The hexadecimal number system uses numbers from 0-9 and letters from A-F.
2 There is no harm in sharing our date of birth with strangers online.
3 In abstraction, we should focus on the important details while ignoring useless information.
4 You cannot use cell references in a function in Google Sheets.
D. Answer the following questions.
1 Define a number system.
2 Write three rules to create a strong password for your online accounts.
3 Describe the importance of the algorithmic design step of computational thinking?
4 Define the following functions used in Google Sheets:
E. Apply your learning.
1 Sheena is trying to decipher a number written in a series of 0s and 1s. She does not know how to convert the number to a decimal number. Help her convert the number.
2 Avi’s father is a businessman and has become a victim of online fraud. What should Avi tell his father about cybercrimes against businesses?
3 Shalini wants to check today’s date and time using a function in Google Sheets. Which function is suitable for this?

A. Fill in the blanks.
1 means to arrange data in a particular sequence based on specific criteria.
2 is a process that makes sure the data is correct, whole, and the same as long as it exists in the database.
3 an object makes sure that the object remains on its place while you work on the other parts of the design.
4 is a branch of AI that makes machines learn from large amounts of data.
B. Tick () the correct option.
1 means putting similar things together.
a Sorting b Grouping
c Filtering d Deleting
2 occurs when we have multiple copies of the same data.
a Data redundancy b Data Security
c Database d DBMS
3 refers to the quality or accuracy of the data.
a Value b Velocity
c Volume d Veracity
C. Write T for True and F for False.
1 Charts help us look at data in the form of videos.
2 A database is a collection of information stored electronically in a computer system.
3 Unsupervised learning uses labelled data to train algorithms to predict outcomes and recognise patterns.
4 The backward option brings the layer to the bottom of the stack.
D. Answer the following questions.
1 What is SQL?
2 What do you mean by duplicating a layer?
3 What is reinforcement learning?
4 Write the syntax of the create table command with the primary key.
E. Apply your learning.
1 Pranjal is organising a survey and wants to visualise how many participants selected each option in a questionnaire. Which feature can she use to accomplish this?
2 Tanay wants to know about big data. Help him by explaining a real-life example of big data.
3 Palak is teaching her little brother, and she is explaining to him the concept of machine learning. However, she forgets to tell him about applications of machine learning. Help her by mentioning two applications of it.

This book embodies the principles outlined in the National Curriculum Framework (NCF) and the National Education Policy (NEP) 2020. It unveils the world of computer science through a unique and captivating pedagogical approach— seamlessly integrating curriculum content into the mesmerising adventures of Mel and Conji, fictional figures hailing from the enchanting world of Avora. Our aim is to prepare learners for the dynamic and technology-driven landscape of the 21st century, equipping them with the essential skills they need to thrive in an ever-evolving world.
• NEP Tags: To showcase alignment with NEP skills and values.

• Explore More: QR codes to explore an exciting application of the concept.
• Discuss: Questions to trigger engaging group discussions in the classroom.
• Think and Tell: Probing questions to stimulate thinking at an individual level.
• Did You Know? Interesting facts related to the application of a concept.
• Fun with AI: Engaging AI activities to explore and apply AI concepts in practical ways.
• Do It Yourself: Milestone exercises to practice specific concepts.
• Chapter Checkup: A pool of questions catering to all topics and skills covered in the chapter.
• Test Papers: Designed to evaluate understanding of core concepts and application of skills.
Uolo partners with K-12 schools to provide technology-enabled learning programs. We believe that pedagogy and technology must come together to deliver scalable learning experiences that generate measurable outcomes. Uolo is trusted by over 15,000+ schools across India, Southeast Asia, and the Middle East.
ISBN 978-81-978912-7-4
