

CIS



14.PATROL
-CIS
-MYTAG
15.INNOVATIONS
-PELCO
-REMARK
-BIOMETRICS
-DRONE

-MATADOR
-TERROR
-TRUCKSTOPPER BOLLARDS
-ROAD BLOCKER
-AUTOMATIC RAISED & STATIC BOLLARDS
-MANUAL PAS RATED BARRIER -HVM



1.ABOUT US
ABOUT US

Founded in 1969 by two former Police Officers, CIS initially operated as a security management and commercial investigation specialist, advising clients on matters relating to security practice and providing loss prevention.
In 1972, the company joined the Security Personnel industry after identifying a gap in the market focusing on providing professional, qualified, and trained personnel able to fulfil our customer requirements.
CIS Security Personnel Division was then formed and has organically grown to be an award-winning security company, with over 2,600 employees and a portfolio of over 200 clients.
Over the years we have continually added to our services offered and now provide in-house consultancy and managed security services to our customers, drawing on the vast knowledge of our people, based on 50+ years of industry experience.
In 2019, CIS Innovative Solutions was formed, to meet the needs of all our customer’s physical, technological, and strategic security requirements.
Our success reflects our core values: passion, determination and leadership and underpins all our business operations. Our mission is to be recognised as a leader in security excellence in all aspects of our business operations and we will achieve this through the introduction of best working practices, training, and development of our employees, and by the application of innovation and the best in new technologies, at all times striving to exceed our customers’ expectations while adding genuine value to their business.




CIS Innovative Solutions is one of three divisions of CIS Security.
Innovative Solutions is a Security Systems Integrator, that works on behalf of our customers and stakeholders to ensure the security systems used within their portfolios are enhancing the security provision provided by CIS.
CIS Innovative Solutions provides an end-to-end service, capable of supporting your operations in every phase of the security system lifecycle. A security systems integrator specialises in bringing together installers and subsystems into a whole and ensuring that those subsystems function together.
� Security risk or needs assessments
� System engineering and design
� Broad access to the leading product lines
� Custom engineering when required
� Alternate investment options
� Procurement
� Installation, commissioning, and training
� Full lifecycle service and maintenance
� System functional and technology upgrades.



This document is a catalogue of recommend products used by CIS Innovative Solutions. All products and services within this document are not exhaustive, tailored solutions and custom engineering are available to mitigate risk, we make recommendations through in-depth site surveys.




2.CCTV SYSTEMS

CCTV SYSTEMS
2.1 - VIDEO MANAGEMENT SYSTEMS (VMS)
Milestone XPROJECT
Why choose
XProtect?
Reliable
Avoid downtime or data loss with proven technology based on Milestone’s 25 years of market experience.
Scalable
Accept no limitations on your video capabilities with an open platform that can be adapted as your needs develop.
User-friendly
Gain full control over all your software and hardware with a complete and intuitive overview that allows easy collaboration.

you
There is no one-size-fits-all when it comes to video technology. Every operation is different, with needs constantly evolving. That’s why XProtect’s flexible open platform architecture makes it such a futureproof investment. You can adapt and scale your video solutions as well as update them with the latest analytics and AI technologies.
13,000+ supported cameras and other devices
Extensions include Smart Wall and Smart Map
1,000+ compatible third-party integrations.


Get full situational awareness
Thanks to a single interface, multilayer maps and advanced search, the task of protecting people and property and improving operations is made simple and centralized. XProtect helps staff to ensure everything is monitored, and that proactive or reactive measures can be quickly set in motion.
Whether you focus on security, operational efficiency, or customer experiences — XProtect keeps you informed in real time of events that may need your attention. It’s conveniently accessible from desktop computer and mobile device clients.


Program the Alarm Manager with specific alarm triggers.
Analyse and manage evidence

Get desktop and Smart Map alarm notifications Instantly access any connected camera or sensor

When an incident takes place, XProtect lets you condense and filter hours of footage to quickly resolve it. The tracking and monitoring functions not only assist investigations, but they also allow you to keep a virtual eye on objects and people.
� The Incident Manager streamlines incident reporting
� Evidence Lock ensures video can’t be prematurely deleted
� The Export Function ensures compliant third-party sharing.

Ensure cybersecurity

No organization wants to deal with the disruption, costs, and distress of cybersecurity breaches. That’s why XProtect is designed and independently tested to meet the highest security standards. And it’s supported by a security response team.
� Manage user access with tiered admin and user rights
� Features high-level encryption and password protection
� Receive patches, hotfixes, and security alerts

Reduce complexity and relieve workloads

Video technology can help take the pressure off staff and budgets. XProtect’s single interface, multi-layer maps and advanced search simplify and centralize operations. Third-party integrations such as access control and people counting analytics further optimize resources.
The intuitive interface can be adjusted to individual, or team needs
Centralized Search accelerates finding and sharing footage Proactive analytics enable preventative measures

AVIGILON AI-Enabled Video Management Software
Superior situational awareness

Secure, scalable, and easy to use, Avigilon’s video management systems provide an enterprisegrade, AI-enabled solution, equipped with integrated machine learning capabilities.




Find what you’re looking for faster
When every minute counts, video management software with advanced search technology speeds your investigations without sacrificing any level of detail.



See security in greater detail


Avigilon video management systems are equipped with advanced video analytics technology and features that bring all the details into focus.





Flexible video management software
Avigilon gives you the flexibility to deploy an advanced video management system that fits your unique security needs.



Alta Aware Cloud VMS
Avigilon Unity Video


Intelligence within reach. Our cloud-based AI video analytics software has the power to provide 360-degree awareness to your Avigilon Ava cloud IP cameras or to your existing cameras and sensors.
Powerful insights with Smart Presence
Add maps of all your locations in Avigilon Alta Aware to gain enhanced situational awareness. Classify and assign people, vehicles and other objects as they move on your premises.
Highlight relevant video with Spotlight
Powered by deep learning, Alta Aware automatically changes video streams with real-time alerts and notifications to describe the incident, the time and the place it occurred.
Speed investigations with Smart Search
Search by event and similarity, and perform appearance and image detection powered by machine learning capabilities to quickly comb through countless hours of video throughout your entire deployment.
On-premise VMS that highlights the most important security information at your fingertips, so that you are always kept instantly in the know for the moments that matter.
Next-Generation Video Analytics
Accelerate response times by quickly identifying people of interest with AI that delivers actionable results through advanced patternbased analytics, teach-by-example technology and facial recognition.
Focus of Attention
Make watching live video obsolete with an intuitive view of your site. The AI-enabled interface provides colorcoded alerts, indicating importance level, for events requiring attention.
Appearance Search
Expedite investigations and improve incident response time by initiating a search across multiple sites of a vehicle or person based on physical descriptions or by uploaded photo or video.

PELCO VideoXpert
The gateway to performance
Pelco’s VideoXpert video management system allows security professionals to easily see what they need to see, when they want to see it. Available in Enterprise and Professional packages, this VMS provides a scalable solution ranging from entry-level surveillance set-ups to systems that support tens of thousands of cameras across multiple continents. VideoXpert can be optimized with Pelco hardware or seamlessly integrated with third-party cameras, but it is always backed by an unparalleled level of support.







HikVision – HikCentral Professional
What Hikvision software can do

� Live view and playback – Identify if a security threat is real and quickly notify enforcement after hours, from the comfort of your home.
� Access control/video intercom – Decide who and when someone can enter buildings or spaces using key cards, keypads, or video intercom systems.


Hikvision’s Video Management System (VMS) is designed for the on-the-go, busy business owner who wants to promptly respond to security concerns from anywhere. The comprehensive VMS brings together powerful video surveillance and access control systems of any size, including third-party applications.
From an app on a phone to a desktop at your home or office, you will have access to the following features:

� Intelligent analysis – Filter through images and video looking for specific features, glasses, types of clothing, or vehicles.
� Network management – Set up a maintenance schedule to back up your video for both onsite and offsite retrieval, without interrupting your daily business operations.
This centralised and highly customizable management system allows users to pick and choose which applications and features best meet their needs. Included with the one-time purchase is a perpetual license that never needs renewed and includes technical support that is just a phone call away.


H6X DOME CAMERA

The ultimate deployment flexibility is in the palm of your hands with the H6X Dome. To help you easily meet privacy requirements, the H6X Dome has been designed without a built-in mic. Stay effortlessly aware with onboard Adapt AI video analytics to proactively flag critical events. The dome camera’s modular design means a fast deployment in virtually any area.


H6A BULLET

Elevate your situational awareness to new heights with the H6A Bullet. Instantly know when something isn’t right with onboard Adapt AI video analytics to proactively flag critical events. Extend your awareness beyond video with a built-in mic to alert you of auditory disturbances. See far and wide with the bullet’s long-range detail, making it perfect for large areas.



adjustable sensors provides you with one powerful solution. The Avigilon H5A multi-sensor camera can monitor virtually any area in all lighting conditions to protect building corners, parking lots, intersections and more.








� Analytics-enabled to detect critical events and increase situational awareness
� Enhanced imaging quality for excellent video with sharp details.
� Robust modular design simplifies installation time
� ONVIF compliant so you can easily integrate with any third-party VMS.



Spectra Enhanced IR Look Up 7 30X
� Look-up cameras feature the ability to look 30 degrees above the horizon so you can monitor larger areas
� Integrated IR illumination allows you to see up to 200m in the dark.






Sarix Multi Enhanced In-ceiling Mount
� The in-ceiling mount option delivers superior situational awareness in a lowprofile design that’s tailored for indoor areas
� Integrates with leading VMS brands through ONVIF Profile S, T, G and M
� Manages bandwidth efficiently with H.264 and H.265 Smart Compression technology

Sarix Multi Enhanced Surface Mount

� The surface mount option offers maximum versatility and can be deployed indoors and outdoors
� Grants the option to add an IR illuminator to see clearly in low-light areas
� Offers an easy upgrade from the Sarix Multi Pro with backward compatible parts






4 MP AcuSense Fixed Bullet Network Camera
� High quality imaging with 4 MP resolution

� Clear imaging against strong backlight due to 120 dB WDR technology
� Efficient H.265+ compression technology
� -U: Built-in microphone for real-time audio security
� Water and dust resistant (IP67)
� Focus on human and vehicle targets classification based on deep learning



2 MP AcuSense Built-in Mic Fixed Dome Network Camera
� High quality imaging with 2 MP resolution
� Clear imaging against strong backlight due to 120 dB WDR technology
� Efficient H.265+ compression technology
� Built-in microphone for real-time audio security
� Focus on human and vehicle targets classification based on deep learning
� Water and dust resistant (IP67) and vandal resistant (IK10)

12 MP Fisheye Network Camera
� 360° 100% Visibility image, a fisheye network camera capable of providing a 360-degree panoramic image of its surveillance scene


� Multi dewarping modes, the image can be dewarped to normal image to view intuitively
� Built-in mic and speaker, it supports two-way audio to realize real-time security by hearing sound and speaking through the camera
� IP66/IK10 , water resistant and vandal proof, there is no need to worry about water ingress when it is used in outdoor scenarios
� With up to 12 MP high resolution lens, the image is very clear even dewarped into 4 PTZ images






3.ACCESS CONTROL SYSTEMS


ACCESS CONTROL SYSTEMS
LENEL S2

Whether you’re operating a small business or a global enterprise, LenelS2’s security access control systems support your evolving needs in the ever-changing security landscape.
Unify Access Control Systems With Other Infrastructure
A feature-rich access control system is only the beginning. By unifying your LenelS2 access control system with video management, intrusion alarms, building systems, business systems and more, you can synthesize data in a single user interface to enhance security, safety, building health and operational efficiency.
Choose Your Deployment Setup
Your business, IT and system operator requirements should inform your security system setup. With a range of deployment options that include browser-based applications, easy-toinstall network appliances and the cloud, we can help you meet your needs.
Custom Security Optimizations
With over 200 certified product interfaces and an open API, you can truly optimize your LenelS2 access control system to meet your security and operational needs for a variety of third-party products from human resource databases to elevator control.
Modernize Aging Access Control Systems


Aging access control systems can be limited in functionality, exposed to vulnerabilities and costly to maintain. Our modern access control systems provide modern features, ongoing cybersecurity enhancements and automated software updates. An upgrade can utilize existing infrastructure, reducing costs and minimizing downtime.
The Power of the Cloud
Cloud technology offers the advantages of large-scale computing resources in an on-demand model, simplifying product and service delivery as well as minimizing costs. LenelS2 cloud-based solutions allow you to remotely manage your installed products or deploy an access control system.


OnGuard

Comprehensive physical access control systems for organizations of all sizes.
Proven, Trusted and Open Access Control
The OnGuard physical access control system exemplifies our commitment to providing a superior, integrated, and customizable security management system that meets your evolving needs. The OnGuard system delivers solutions that seamlessly unify access control and video monitoring for a wide range of industries.


Why Choose OnGuard for Physical Access Control?
Complete Situational Awareness


Providing the means to aggregate, visualize and share security data from multiple sources, the OnGuard system helps companies recognize context and analyze inputs from a number of simultaneous events. Seamlessly synthesizing information from access control, video and other sensors, the OnGuard system delivers complete line-of-sight to all aspects of security and facilitates intelligent responses and outcomes.
Ease of Integration
The OnGuard system integrates seamlessly with a wide range of existing business systems. The OnGuard system can bi-directionally exchange cardholder data with many HR platforms, ERP systems and/or elevator systems, coordinate alarm/ event data with emergency response systems, and provide/receive event information with various building management, network management and third-party security systems.
Unlimited Scalability
Adaptable and scalable, the OnGuard physical access control system is appropriate for small localized environments as well as large global enterprise applications that span a wide geography. For businesses starting small and anticipating growth, the OnGuard system is ideally suited to meeting their expanding needs. Our physical access control system delivers unlimited scalability, flexibility, and industry-leading performance.
Browser-based Clients and Mobile Apps
Leveraging OnGuard clients and apps in your OnGuard system turns an excellent security management solution into an exceptional one. These OnGuard utilities improve your overall user experience and provide a path to view, manage and authorize in an increasingly mobile and remote workplace.

Johnson Controls

CIS Innovatiove Solutions partners with Johnson Controls and subsiderary Envison Intelligent Solutions. Johnson Controls owns the access contorl product C-Cure 9000 and Envision provide vacant premises mitigation and ARC services.
C-CURE 9000
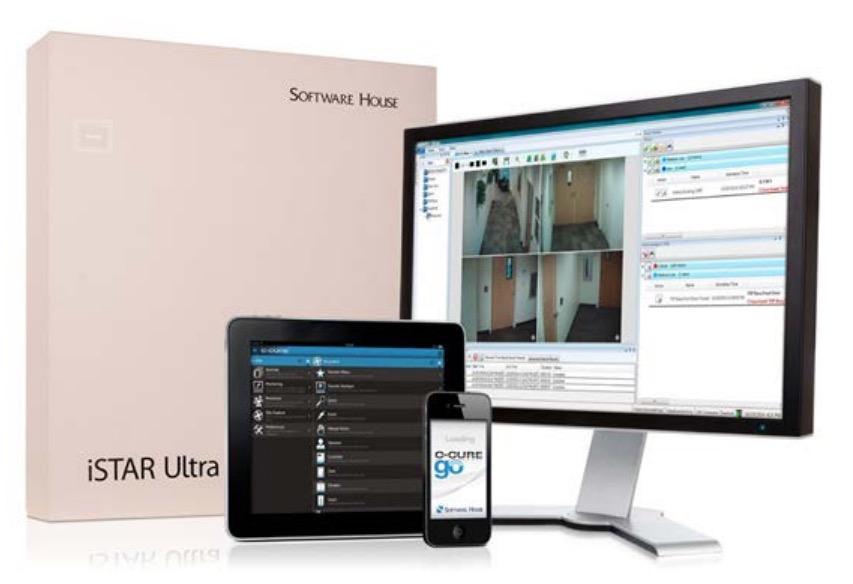
C•CURE 9000 is one of the industry’s most powerful security management system providing 24x7 mission critical security and safety protection for people, buildings and assets. It provides a standard approach to physical access authorization throughout all your buildings, regardless of age, layout or location that you can access on your workstation, laptop or mobile device. The native interfaces combined with the Connected Partner Program helps us to deliver seamless integrations with over 300+ third-party security and business technologies.


Main Features
� OSDP support for reader to panel communications on iSTAR Ultra Series controllers
� Supports up to 5,000 readers per single server and 60 satellite application server scalabilities for Enterprise systems
� Enterprise system remains operational throughout upgrade process with multi-version software support
� Access to C•CURE 9000 from any internet browser with C•CURE Web
� Administer and monitor C•CURE 9000 from your mobile device with C•CURE Go
� Software House Connected Partner Program for standards-based integrations
� Part of the Cyber Protection Program to reduce the risk of vulnerabilities
What’s New in C•CURE 9000 v3.0
� Support for iSTAR Ultra G2 and iSTAR Ultra G2 SE door controllers with advanced embedded cybersecurity
� C•CURE Web-based Client – Dynamic Access and Video Monitoring Views and Layouts, Swipe & Show, Health Dashboard, etc. (Phase III)
� C•CURE ID HID SEOS and MIFARE DESFire EV1/EV2 support, for card encoding of multiple applications simultaneously (up to 5)
� C•CURE Portal moved to the latest Angular web framework, meeting latest in cyber security
� Email template customization for C•CURE Visitor Management and Access Management Workflow
� As an option, C•CURE 9000 version 3.0 and later supports SQL database hosted by Amazon Relational Database Services (RDS)™ powered by Amazon Web Services (AWS)™





Additional Benefits of integration options, but not limited to:
� Unification with American Dynamics’ victor Professional provides a multidimensional single-point event management
� Single server for managing security and events for video, access control, intrusion, central station, fire, real-time location, and other supported systems
� Reduced footprint to decrease required rack space, power, cooling, and overall cost and maintenance
� Single server database for advanced cross-pollination of events across multiple supported systems
� Run C•CURE 9000 and victor Professional efficiently as native 64-bit applications
� Single unified security client provides an all-inclusive real-time alert notification GUI with advanced event management and superior interactive mapping for situational awareness
� Minimizes learning curve by consolidating requirement of multiple singledimensional client applications
� Event linking and cross-product association for event activations across dispersed security systems with associated time-synchronized video
� Integrated policy management with advanced auditing capabilities
GALLAGHER SECURITY
Gallagher’s industry leading security solutions are designed to meet the unique access control needs of sites varying in size and scale from one door to thousands. Whether it’s a small business, large enterprise organization, or sites with critically sensitive infrastructure, we have a solution that will keep your people and assets safe.
Management
Complete site management
Gallagher Command Centre is a powerful operator-friendly security management system that enables you to:
� Manage cardholders, including their access, credential and photo identification
� Monitor alarms and control all system aspects
� Retrieve and report on stored system information
� Interface to and exchange information with third party systems
� Configure the site and all system component






Control

Extended control capacity
Gallagher controller devices can greatly expand the control capabilities of a security system:
� Remove the risk of one compromized connection taking down all downstream devices
� Monitor and report the state of balanced inputs
� Enforce decisions to switch output relays
� Manage multiple access points efficiently
Access
Secure access control
Gallagher’s reader range provides contactless proximity card readers for access control management delivering:
� Rapid and secure access decision responses
� Support for multiple card technologies and mobile credentials
� A diverse selection of reader mounting and protection accessories
BRIVO ACCESS CONTROL
Access
Control Built for Corporate and Enterprise
The Brivo enterprise solution protects 70,000 business locations around the world – discover how we can protect yours











Brivo Provides a Comprehensive Enterprise and Corporate Physical Security Solution.
Design and implement an effective security plan. Use Brivo’s scalable enterprise cloud-based solution to satisfy the most stringent compliance and IT requirements.




Brivo mobile-centric platform supports security leaders who directly manage security systems while improving the experience for all users.
To keep you secure, Brivo offers an integrated security platform which includes access control, mobile credentials, mobile administration, video surveillance, identity and visitor management and elevator control. Brivo also offers an open API to build custom integrations that bring your entire physical security ecosystem together.




PAXTON Net2
Net2

Security made simple.


Net2 is our networked access control system. It can be administered using one or more PCs and can be monitored and managed from a central location. It is a complete solution that encompasses wireless door handles and door entry.


Why choose Net2?
� Convenient end to end security that eliminates the need for keys.
� Start simple, expand as and when you need to.
� A powerful all in one solution that works with a range of systems.
� License free.
� Free upgrades.
� Integrates with a vast range of leading security brands.
� Easy to quote, easy to install, easy to deal with.






4.INTRUDER ALARM SYSTEMS


INTRUDER ALARM SYSTEMS
HONEYWELL GALAXY
Galaxy Dimension – Integrated intrusion and door control panel range.
The Galaxy® Dimension series of security systems is a fully integrated intrusion and door control security solution for mid to large commercial security installations. It offers your customers a user-friendly system in a cost-effective and fully compliant Security Grade 3 package.
With innovative wireless capability and user-friendly remote management options, the series provides high quality, reliable security solutions, with the flexibility to meet the needs of every commercial and industrial application.


Flexible & reliable communications


To ensure fail-safe communications, multiple path communication options for alarm signalling include GPRS, Ethernet and standard telephone line (PSTN). These options also allow maximum flexibility and customisation to capitalise on existing network infrastructures and minimise disruption for customers.
Attractive user interfaces and Mobile App
A choice of LCD Keypad and Keyprox options including the MK8, with a modern design and all the familiarity and functionality of the MK7, for ease of programming across the range. In addition, all user interfaces feature a proximity function allowing quick and secure set and unset without PIN code. The GX Remote control mobile App allows control of the system from anywhere in the world from your preferred smart device (requires E080-04 Ethernet module).
Audio verification (‘Listen-in’ Facility)
With Galaxy® Dimension, an Alarm Receiving Centre (ARC) can listen in using independant audio channels to identify the specific location where the alarm has been triggered and verify source and cause. This reduces false alarms and increases system reliability.
Programming software compatibility
The Remote Servicing Suite (RSS) is a maintenance tool enabling complete remote control of the panel, allowing installers to give customers instant support. Installers can complete remote routine inspection reducing the need for time consuming and costly site visits. The RSS software uses a common database to communicate with all Galaxy® panels from one programme. A networked version of the Remote Servicing Suite offers access to up-to-date records for all users. This guarantees the secure management of information in one central location. Both wired and wireless components can take advantage of the easy remote diagnostics and maintenance functionality in this software.

The right choice

Galaxy Dimension offers customers a user-friendly, integrated security solution that is flexible and upgradeable to meet specific security needs. Honeywell provides sales and marketing support and organises frequent training to boost



TEXECOM


Texecom is trusted by professional installers to protect the world’s most important properties and the people who use them.
Premier Elite
More speed. More flexibility. More choice.
The Premier Elite 48-W is a wireless control panel suitable for a wide variety of security applications. Combining class-leading Premier Series control panel architecture with Ricochet mesh network wireless technology, the Premier Elite 48-W is compatible with Texecom’s entire range of peripheral devices.
� Suitable for premium residential and commercial applications
� Expandable to 48 zones with 4 partition areas
� Accepts up to 32 Ricochet enabled wireless devices – No wireless expander required
The Ricochet wireless technology has been invented to provide reliable wireless communications in commercial environments. The Premier Elite 48-W features Signal Security™ and self-healing functions delivering unparalleled communications reliability.






Odyssey X External Sounders
Elevate your brand, deliver the highest quality security. The Odyssey X range brings innovation and a modern twist to external sounders, providing unparalleled performance and extensive features to benefit installers and end users alike.











5.VACANT BUILDING MITIGATION

VACANT BUILDING RECOMMENDATIONS
Guidance, Responding to Squatting
Figures show that unauthorised vacant property was up by 25% in 2020 in the UK. This coupled with the increase in homelessness, (Shelter report every 1 in 206 are homeless. Since the pandemic there are 180,00 households now homeless, with 91 families a day adding to this number). The increase in resources for accommodation in terms of families not being able to afford the current rents is also a factor. The numbers for current known squatters in the UK are stated at 200,000. This figure changes depending on sources. However, with websites that actively encourage how to squat, the rights, law and processes, this information to encourage squatting puts our customers properties at risk.
While we understand that this is a desperate situation, we need to look at the risks this poses to our customers and their business. Any vacant property that may be under your portfolio will need to be assessed and appropriate discussions with the customers regarding vacant property protection. Squatters themselves have numerous tactics. These are some that CIS team have experienced:
1. Some groups will occupy buildings, open communications to stay in those properties and come to agreements with the owners that the building will be taken care of, and they will agree to leave at specified dates. This gives them a home for free and protects the building from other less scrupulous squatters. (rare)
2. Will occupy, have no open comms and then it is down to luck as to what state the building is in when they are removed
3. Will occupy and then the immediate area becomes a sudden crime hotspot, parties, ASB, drug use and dealing, theft etc.
4. Severe building damage, theft of metals, cabling, and other valuable construction materials, potentially leaving the building structurally unsound.
5. May barricade themselves in, set booby traps and have limited access/ egress from the property, including utilising the security measures applied to keep them out. All to make repossession as difficult as possible




There are many difficulties in dealing with squatters in terms of what their rights are and what we can do. Below is an overview for your information:
Squatting and the law
Squatting is when someone deliberately enters property without permission and lives there or intends to live there.
This is sometimes known as ‘adverse possession’ or ‘occupying a building’.
Squatting in residential buildings (like a house or flat) is illegal. It can lead to 6 months in prison, a £5,000 fine or both.
Anyone who originally enters a property with the permission of the landlord is not a squatter. For example, if you’re renting a property and fall behind with rent payments you’re not squatting if you continue to live there.
Although squatting in non-residential building or land is not in itself a crime, it’s a crime to damage the property.
It’s usually a crime not to leave land or property when you’re instructed to do so by:
� The owner
� The police
� The council
� A repossession orders.

Squatting in non-residential properties
A non-residential property is any building or land that is not designed to be lived in.
Simply being on another person’s non-residential property without their permission is not usually a crime. The police can act if squatters commit other crimes when entering or staying in a property.
Crimes include:
� Causing damage when entering the property
� Causing damage while in the property
� Not leaving when they’re told to by a court
� Stealing from the property
� Using utilities like electricity or gas without permission
� Fy-tipping
� Not obeying a noise abatement notice
Remove squatters

You can remove squatters using an interim possession order (IPO) or making a claim for possession.
Do not try to remove the squatters yourself using force or the threat of force – you’re committing a crime if you do.
Interim possession orders
You can only apply for an IPO if it’s been 28 days or less since you found out your property’s been squatted.
Fill in an application for an IPO and send it to your local county court.
The court will send you confirmation of your IPO within a few days. They will also send you documents that you must give to the squatters within 48 hours.
After being served with an IPO squatters can be sent to prison if they do not:
� Leave your property within 24 hours
� Stay away from your property for 12 months.
To get final possession of the property, you must make a claim for possession. You can do this on your IPO application form or separately online.
Exceptions
You cannot use an IPO if:
� You’re also making a claim for damages caused by the squatters –instead you should make an ordinary claim for possession
� You’re trying to evict former tenants, sub-tenants, or licensees.
Claim for possession
Make a claim for possession if it’s been more than 28 days since you found out about the squatters.
How to Mitigate against Occupation
CIS Innovative Solutions can provide the following services to help you mitigate against occupation of the buildings.



Securing Your Building
Boarding-Up Options for Vacant Property
Effective physical security is based on the concept of defence in depth, the creation of multiple layers of security.
Defence in depth is characterised by interdependent concentric layers of security controls, with each layer consisting of increasingly complex measures designed to protect people, property, and information.
In the case of void property this would consist of the following:
� Perimeter fencing – boundary marker denoting ownership
� Concrete barrier blocks – to prevent vehicle access to the site
� External mounted Video verification systems – detection
� Windows and doors boarding-up –delay intruders
� Internal video systems / intruder alarms – adversary path confirmation.
Different types of Boarding-up Options
Steel Perforated Sheets.
Steel perforated sheets provide a heightened level of security when compared with timber. The benefits of PS screens include:

� Visible deterrent to criminals

Boarding up of windows and doors is one layer of a physical security system, the primary purpose of which is to both deter those that can be deterred and to delay those that can’t. There are a variety of options available to property owners and landlords when considering boarding up a vacant property.
� Creates a steel barrier over the window
� Perforation lets light through to allow internal viewing
� Resistant to arson attack
� Cut to size to fit into window reveals
� Fairly cheap long-term solution


The benefits of Perforated steel screens over timber boarding are obvious, however similar to timber they are fitted directly into either the window frame or brick wall, once again damaging the fabric of the property.
There are also limitations in using Perforated Steel sheets on listed properties, often resulting in Perforated Steel screens being fitted to the inside of the window (internally), which significantly reduces the effectiveness of this solution due to the ease with which such screens can be kicked out once the glass has been smashed.
SITEX (Type) Security
Screens:
Sitex security screen panels became popular in the 1990’s after their introduction by a leading security company. They quickly became the preferred solution for securing vacant properties requiring a heightened level of security.
Sitex security screen panels are secured by either drilling holes in the window frame and inserting cables which are then secured internally across the window by a steel bracket, which is then attached to the panels creating a very strong seal, or more commonly the glazing is removed when using this method of boarding up solution.
The benefits of utilising Sitex security screen panels include:

A highly visible deterrent to
Robust and long lasting Perforations allow light and
Installed from the inside for maximum security and minimum
Arson-resistant
Can be fitted over doors, windows, and other entry points.

Compression Security Screens:
Compression security screens are fitted within the window’s reveal through the use of jacks positioned horizontally to create an incredibly secure seal. The jacks form the frame to which security steel panels are securely fixed.

This innovative method of boarding up has the following benefits:
� Quickest method of installation
� Multiple contact points create a rigid secure barrier
� Bolted panels cover all shapes of enclosure
� Rapid removal and re-use of panels
� No requirement to remove windows
� No drilling into window frames or brick work
� Damage free secure barrier
� Maintains environmental seal
Compression security screens have been designed to provide a rapidly deployable boarding solution that is as secure as Sitex security screen, as quick to install as Perforated Steel screens, but doesn’t require the timeconsuming removal of windows or cause damage to the property.







How does it work?

The wireless camera system uses passive infrared (PIR) sensors and signal analysis to track thermal signatures across the monitored area. All monitored from the ARC as part of the service and cost of hiring the cameras.

Rapid Speed Domes


The wireless camera system uses passive infrared (PIR) sensors and signal analysis to track thermal signatures across the monitored area. All monitored from the ARC as part of the service and cost of hiring the cameras.

How Does It Work?
A 4G Re-deployable CCTV Infra-Red Speed Dome design specifically to deliver live and recorded high-definition images via 4G mobile transmission.


How does it work?
Eco Solar Towers provide live 24/7 site security with a dedicated account manager, helpdesk and qualified engineers will be on-hand to offer support. The cameras will be monitored from the ARC as part of the unit higher fees.






6.REMOTE MONITORING



REMOTE MONITORING
CSOC | CIS Security Operations Centre
Our Control Room constantly undergoes transformations with newer user requirements as well as newer technologies. We adopt cutting edge technologies to provide access to the most accurate, up-to-date information available. Our priority is for all of that visual information – video, data, application, screens – to be available for sharing to teams that may be located in different places, with a full set of tools that allows them to work together as if they were all in the same room.
Closed-circuit television surveillance and monitoring assist in securing sites or part of sites 24 hours a day. Whether installing the CCTV solution, making updates, or monitoring the systems, we have all the end-to-end resources to put these into place. At CIS we have a fully functioning Control Room which is resourced 24 hours a day, 7 days a week and can provide your business with remote monitoring, alarm response, lone working and many more solutions.






CIS Security Operations Centre (CSOC) provides the following services:
� Alarm Monitoring and Response
� CCTV Remote Monitoring
� Remote Patrols of Premises Using CCTV
� Remote Video Access Control Management
� Remote Control of Premises Access Control Systems
� Key Holding
� Lone Worker Monitoring
� Facilities Help Desk
� Virtual Control Room People Services
� Monitoring Staff Welfare and
� Timekeeping/Attendance monitoring


The remote monitoring platform we use is Gemini, here is some further information.
Since Gemini was launched ten years ago, it has become the most widely adopted integrated monitoring software in the UK and is also used in many overseas control rooms. Gemini v2.0 incorporates many new features — enhancements to CCTV alarm handling, solutions for managing ‘problem sites and quicker deployment of interfaces and modules. There are also changes to Gemini PC and Smartphone Web, along with reporting updates and encryption features.
Gemini CCTV Integration
Gemini CCTV integration enables the user to receive alarms, live and event video, PTZ control, camera selection and many other features. The level of integration depends upon the CCTV product functionality and the controls provided by the manufacturer. Provided below is a list of CCTV products where at least minimum functionality is supported. As manufacturers improve their products and software is continuously enhanced, the integration functionality is subject to change.
CCTV handling can be configured to be handled in a variety of ways –
� The video alarm clip or event is automatically brought to screen
� A ‘View Camera’ action can be configured as a discretionary or mandatory alarm processing task
� Live and event/alarm video can be viewed in the same user interface
� View Camera actions can be associated with signals from alarm panels for video verification
� Sites, cameras, and camera groups can be accessed ad hoc or by schedule
� Cameras and camera groups can be viewed and selected from interactive site plans
� Video ports from different systems and different sites can be sent to a review monitor
� Event clips and downloaded video can be selected by timeline and exported for playback in any standard Windows Media Player
The full range of CCTV management features are supported, including on screen PTZ control, event and log search, remote relay operation, multiple reference images, camera isolation, CCTV guard tour, false alarm filtering, runaway signal monitoring, video export (VMP file), image resolution control, scheduled site visits, listen in and speak to site.
SUPPORTED CCTV SYSTEMS


Adata Honeywell Fusion/HRDP
Adpro FastTrace 1 Honeywell RapidEye
Adpro FastTrace 2 Milestone
Apollo Panasonic
Avigilon Pinetron
Axis Rialto
Bosch Divar RSI Videofied
CamDisc/CamTel Samsung
Dahua SmartTel
Davantis SystemQ Alien
Dedicated Micros TeleEye
Genie Videocon VXM, VXH, ITX, AHD, HD-IP, 960H
Geovision
Heitel
Video IQ
Videoswitch
Hikvision Xtralis V3100
Avigilon Pro March Networks
I will require the following details of your systems to carry out and end to end test. Your system maintenance engineers should be able to provide the following information.
CCTV System details required:
� CCTV device manufacturer and model
� External WAN IP address (will require relevant port(s) forwarded which depends on CCTV manufacturer and device)
� Confirmation as to whether you require remote CCTV alarm monitoring, or just ad-hoc / guard tours etc, or both – and specifically what actions you would like us to carry out
� If your system already supports remote monitoring, the login and password to give is access to your system would be sufficient.
If require your fire and intruder alarms to be monitored, I will require the following details:


Fire & Intruder Alarm System details required
Details for each alarm panel site –
� Protocol(s) supported by your customer’s alarm panel (for PSTN will be either Fast Format, Contact ID, or SIA). Your system maintenance team can help you with these details
� We will then provide you with the telephone numbers of our receiver lines, and a Transmitter ID ‘chip’ number for your engineer to program into the panel (this ID links the panel to the customer account in Gemini)
� If you have an IP panel, then it is likely it can be supported by Gemini with an additional receiver driver
Once we have gathered all the required information and completed the tests we will need call out and key holding details from you to finalise the setup.
If you are interested in going ahead with the remote monitoring services, please get in touch and I will create a bespoke quotation for your requirements.








7.REFUGE ALARM SYSTEMS


REFUGE ALARM SYSTEMS
C-TEC Disabled Refuse Systems
C-TEC’s cost-effective and easy-to-install SigTEL system is designed to meet the demand for BS 5839 Part 9 compliant disabled refuge, fire telephone and stadium marshalling systems. Current Building Regulations insist all new nondomestic buildings with more than one storey provide ‘refuge’ areas – safe places where people who cannot easily use fire escapes and evacuation lifts can call for assistance and wait until help arrives. SigTEL provides simple, effective two-way communication in these areas to assist rescue teams in determining where assistance is required and to reassure people help is on the way. It can also be used by trained personnel in sports stadia etc to help ensure the orderly evacuation of people in an emergency.
Ground Control
Our SigTEL 4–224-line emergency voice communication system comprises three wall-mounting master controllers (the ECU-4, ECU-8 and the ECU-16 which can handle 4, 8 or 16 lines). Typically located in a building’s control room or fire services access point, they allow emergency personnel to communicate via a telephone-style handset with the system’s ‘outstations. A powerful networking facility allows up to 14 master controllers (any mix) to be interlinked meaning systems of up to 224 lines can easily be created.

Desk Control


For SigTEL systems with multiple outstations, our new ECU-224-line desk controller is just the job for Disabled Refuge or Fire Telephone Outstations! Connect it to a SigTEL controller using an ECU-723 interface/ network card and away you go!

Hands off
Designed for disabled refuge systems, our ‘Type B’ outstations offer true hands-free duplex speech and allow anyone in a refuge area to communicate with building control at the touch of a button. Features include additional connections for an optional induction loop system and a general-purpose relay output that closes on activation of the unit.
Accessible To All

BS 8300 recommends all disabled refuge outstations have facilities to assist the hearing impaired. Our new PDA103i is a ‘bolt on’ hearing loop system that can be used to help satisfy this requirement. Housed in a water-resistant enclosure it has adjustable input and output controls so it can be set up to suit the exact characteristics of any environment. Ensure your disabled refuge systems – both new and existing –are accessible to all by connecting a PDA103i to your outstations today!


On Call

Our ‘Type A’ telephone-style outstations are designed for use in stadium marshalling systems and other emergency evacuation applications. Comprising a telephone handset in a push-to-open or key lockable red steel cabinet, they are typically located at entrances and fire-fighting lobbies to allow fire marshals and other trained personnel to communicate with building control during an emergency.
Free to Roam
C-TEC’s roaming portable handsets and fire telephone jack plates are increasingly in demand overseas where ‘Type A’-style portable handsets and jack plate combinations are accepted by prevailing standards. Jack plates are typically located in stairwells and risers allowing marshals, security guards and sports stewards to plug their handsets into them in an emergency.
Power to the people
With fire legislation in many countries now stating any power supply performing a mandatory function of a fire alarm system must be certified to EN54-4, C-TEC’s range of Series 5 switch-mode digital hybrid LPCB/ VDS certified power supplies has come into its own. Ideal for controlling beam detectors, auto-dial communicators, aspirating smoke detectors, electromagnetic door holders, ventilation systems and more, the range comprises 1.5A, 3A and 5A 24V units and a 2A 12V unit. A comprehensive range of non-EN54 PSUs is also available.

Access all areas!


Our market-leading NC951 accessible toilet alarm kit contains everything you need to create a BS8300 clause compliant single zone emergency assistance system including a stylish double gang call controller, ceiling pull, overdoor light c/w sounder and reset point c/w sounder. Systems can be easily expanded to include up to three additional 800 Series Call System devices. Recently updated to include a Call Accept function, in the true spirit of BS8300 the NC951 now provides audible and visual indication inside the WC that help is on the way.

Addressing the Standards
Introducing our new QT951 addressable disabled persons toilet alarm kit, specifically designed to meet the rising demand for true BS8300 compliant accessible WC alarm functionality on our Quantec addressable call system. This costeffective expansion kit allows people in distress to call for assistance and staff to send a confirmation signal that help is on the way. Must be used in conjunction with a Quantec controller.



8. BODY WORN CAMERAS


BODY WORN CAMERAS
CIS Innovative Solutions recommed the following three BWC systems
HALO
Next-generation body cam technology. HALO is a complete safety solution, using innovation to stay ahead of threat and reduce risk. Lives and businesses are better safeguarded by more advanced camera tech on the ground, and more intelligent asset management in the cloud.
HALO HORIZON
The HALO Horizon range is IP68 waterproof certified and AES256 encrypted. Paired with our HALO DAMS system it is the world’s most complete protection solution. It’s ready for what’s on the horizon and for what’s coming next. A Wider range of features for what’s ahead. Future-proofed technology for what’s beyond.









VB400 Motorola Body Worn Camera
Intended to support your workers when dealing with aggression or confrontations on a daily basis, the VB400 enables you to foster trust between your team and the public by providing an unbiased independent witness. See what your team sees and watch key decisions unfold, either in real time or after the fact.
The VB400 seamlessly fits around your existing workflows. All configuration and maintenance can be done ahead of time with our easy-to-use backend software, VideoManager – so your workers can grab their cameras and get to work with minimal training and disruption. In the field, features including dual microphones, a wide-angle lens and intuitive buttons ensure that every interaction can be captured in high-definition from start to finish.
All footage is stored and encrypted on the VB400 until it is redocked, at which point it is offloaded securely and automatically. But your cameras are just one part of your operation. Combine other pieces of technology – such as fixed video and Bluetooth sensors – with the VB400’s superior connectivity for a more complete and effective response.







ALWAYS READY TO RECORD



WHETHER YOU’RE USING A SINGLE CAMERA OR STREAMING LIVE BODY-WORN AND FIXED VIDEO INTO THE SAME VMS, THE VB400’S CONNECTIVITY ENABLES YOU TO UNDERSTAND THE FULL CONTEXT OF A SITUATION. SEE THE BIGGER PICTURE.

EVERY ASPECT OF THE VB400, FROM ITS RESILIENT OUTER CASING TO THE WAY IT FITS ON YOUR UNIFORM, IS BUILT TO LAST – NO MATTER HOW OR WHERE YOUR TEAM WORKS.
Your body-worn cameras should fit around your organization’s routine operations – which means accommodating a variety of shift patterns, environments, and uniforms. That’s why the VB400 is as tough as your team is: compatible with whatever clothing they’re wearing, it can record for however long they’re on duty and withstand whatever conditions they encounter.
TEMPERATURE & WEATHER RESISTANT
The environment shouldn’t stop you from getting the video you need. Operate in temperatures between -20°C and +50°C, with IP67 rating for protection against wind, rain and snow.
SHIFT-LONG BATTERY LIFE
Record for up to 12 hours continuously on a single charge. Configurable standby and safety modes preserve battery life.
RUGGEDISED EXTERIOR
Protect your evidence in a resilient outer casing. Certified to MIL-STD-810G drop test requirements, the VB400 is built to withstand the rigours of the job – whatever that entails.
SECURE MOUNTING OPTIONS
Be confident in the knowledge that your VB400 will stay firmly attached to your uniform, regardless of whether you’re wearing a shirt, jacket or protective clothing.
VB400 BODY-WORN





Body-worn cameras provide an invaluable first-person perspective. And now, these insights aren’t just after the fact; equipped with multiple ways to connect, the VB400 gives you crucial insights when you need them most. Use Peer-Assisted Recording to ensure every angle is being documented, stream over Wi-Fi to the Video Management System (VMS) that handles your fixed CCTV cameras and use built-in GPS to keep track of your team’s locations.

HYTERA Body Worn Cameras
Hytera VM750D body camera is designed to capture, store, and upload evidence such as pictures, videos, and audios in the field. It plays a leading role in building trust with the public, in promoting officer accountability, and in enhancing transparency between the police and the citizen.










9. RADIO SYSTEMS

RADIO SYSTEMS

Analog and digital two-way radios differ in several ways, including their technology, performance, and features. In this blog, you can examine their key differences, as well as how operators of analogue radios can migrate to the advanced capabilities of digital radios.
ANALOG VS. DIGITAL TWO-WAY RADIOS
The standard for analogue two-way radios were created by the FCC in the late 1970s and have been popular for decades. However, the Digital Mobile Radio (DMR) standard was created in 2007 as a more advanced level of communication for the same type of applications. While analogue allows twoway communications in certain frequency bands for business and commercial systems. Analog radios are simple to use and are often all that is needed on a personal level. On the other hand, when you need a more advanced radio capable of messaging, location services and more, then look towards digital radios.
How Digital DMR Works
Both analogue and digital radios are capable of sending signals over a radio channel using a Very High Frequency (VHF) or Ultra High Frequency (UHF) carrier waves. In simple terms, analogue radios use frequency modulation (FM) to encode a voice signal within a carrier wave. Your voice changes, or modulates, the frequency of the wave. The difference between the modulated frequency and the baseline channel frequency can then be demodulated by the receiving radio and turned back into a comprehensible voice message.





Digital radios do the same thing, but they have an extra encoding step before the voice signal reaches the carrier wave. The voice message is encoded into binary packets (ones and zeroes). These packets of numbers are then able to modulate the frequency of the carrier wave. The modulated frequency of a digital signal is not a continuous wave but instead an intermittent stepped change (as illustrated bottom left).
Digital Mobile Radio (DMR) is an open digital mobile radio standard defined by ETSI (The European Telecommunications Standards Institute), and this is applicable all over the world. All commercial products must comply to it, and users are not locked into proprietary solutions. The DMR standard Consists of DMR Tier I, Tier II and Tier III. Each tier provides different functionality and coverage range.

Digital radios provide several advantages and additional benefits compared to analogue radios as follows:


Increased Channel Capacity
DMR uses the two-slot TDMA in a 12.5 kHz channel – this means that, as opposed to analogue communication, you have two slots for communication instead of one. Time is essentially split up in milliseconds so that users don’t notice the time gaps, allowing a doubling of capacity for two channels instead of one.
Analog radios support up to 16 channels, and some analogue radios have continuously rotating channel selector switches that can support up to 128 channels. DMR radios with advanced trunking technology can support hundreds of channels.
Longer Range
A standard analogue radio is going to decrease in signal the closer you get towards its maximum range, at which point, all you hear is white noise. On the other hand, a digital radio is going to remain much more consistent in sound quality regardless of distance to or from the maximum range.
An analogue radio and digital radio with the same transmission power radio will transmit over the same distance, the digital radio will remain loud and clear all the way to the end of the covered area whereas the analogue radio will gradually fade towards the end of the covered area.
With the use of repeaters, the range of digital radios can extend for hundreds of miles, and even without repeaters they are far superior in range to analogue radios. Analog radios have continuously rotating channel selector switches that can support up to 128 channels. Unlike analogue, digital transmissions can be in any form such as voice or data.
Clearer Audio
Analog signals are typically less tolerant to external noise interference, which means lots of unwanted background noise that can get in the way of crisp and clear communications. In other words, noise adds extra random information to analogue signals.
Each time the signal is amplified the noise is also amplified. Digital radios feature real-time audio processing that focuses on speech and reduces any background noise. This means that the received audio quality is enhanced when compared to an analogue radio system.

Digital technology also allows the receiving radios to auto-correct any errors in the received signal to maintain audio quality at the extremes of the radio coverage. Hytera digital radios contain unique technology that filters communication channels, fills in microscopic gaps, breaks in transmission, and minimizes error rates. Digital radios can make your communications clearer by reducing unwanted background audio and focusing on the wanted speech. Increased audio quality in poor coverage areas reduces the need to repeat information and improves efficiency.
Longer Battery Life
Because they are more efficient, digital radios feature a longer battery life, and require less frequent charging or battery change out. The difference is substantial because digital radios extend operational battery life for several hours. That means more reliable communications and eliminates the need for staff to carry multiple batteries for a single shift.
Security and Privacy
One of the most important advantages is security. With digital radios, encryption can be used without degrading the quality of the audio, or the range at which the radio works.
GPS and other Advanced Features


Additional capabilities enabled by digital radio technology include GPS tracking, text messaging and data services, private calling, group calls, and safety features
Trunking
Trunked Radio systems are two-way radio systems that optimize voice call or data traffic through a limited number of frequencies, maximizing the available resource for a large group of users. This is critical to ensure that communication is always instant and available for professional or enterprise level users.
DMR Tier III Trunked Radio utilizes repeater technology with a dedicated control channel, managed by a server. This allows resources to be brought together, controlling radio traffic for multiple user groups. Unlike other networks, DMR Tier III trunked networks deliver feature-rich, missioncritical communications over large geographic areas making it useful for enterprise level operations. Digital radio repeaters can be connected over IP networks to enable wide-area radio network of multiple repeaters.
INSTANT
INSTANT PTT COMMUNICATION

WAVE PTX
WAVE PTX MOBILE APPLICATION
MOBILE APPLICATION
TURN YOUR SMARTPHONE OR TABLET INTO A PTT HANDSET.
TURN YOUR SMARTPHONE OR TABLET INTO A PTT HANDSET.
Below are two Digital Radio Systems that Innovative Solutions recommend
Combine the speed and simplicity of PTT with the power of multimedia communication, all at the touch of a button.
Combine the speed and simplicity of PTT with the power of multimedia communication, all at the touch of a button.
TURN YOUR SMARTPHONE OR TABLET INTO A PTT HANDSET.
TURN YOUR SMARTPHONE OR TABLET INTO A PTT HANDSET.
Wave – Network-Independent Broadband PTT
WAVE PTX MOBILE APPLICATION
Combine the speed and simplicity of PTT with the power of multimedia communication, all at the touch of a button.
Combine the speed and simplicity of PTT with the power of multimedia communication, all at the touch of a button.
PTT
TURN YOUR SMARTPHONE INTO A MULTI-CHANNEL COMMUNICATION DEVICE WITH THE WAVE PTX MOBILE APP
TURN YOUR SMARTPHONE INTO A MULTI-CHANNEL COMMUNICATION DEVICE WITH THE WAVE PTX MOBILE APP
TURN YOUR SMARTPHONE OR TABLET INTO A PTT HANDSET.
SINGLE APP. TWO MODES.
SINGLE APP. TWO MODES.
Combine the speed and simplicity of PTT with the power of multimedia communication, all at the touch of a button.
TURN YOUR SMARTPHONE INTO A MULTI-CHANNEL COMMUNICATION DEVICE WITH THE WAVE PTX MOBILE APP
TURN YOUR SMARTPHONE INTO A MULTI-CHANNEL COMMUNICATION DEVICE WITH THE WAVE PTX MOBILE APP
Select one of two client modes: PTT Radio to emulate the experience of a conventional two-way radio, or Standard mode, which offers device-based management of contacts and talkgroups.
Select one of two client modes: PTT Radio to emulate the experience of a conventional two-way radio, or Standard mode, which offers device-based management of contacts and talkgroups.
SINGLE APP. TWO MODES.

MULTIMEDIA MESSAGING
INSTANT PTT COMMUNICATION
INSTANT PTT COMMUNICATION
LOCATION AND MAPPING
MULTIMEDIA MESSAGING LOCATION AND MAPPING
PTT COMMUNICATION MULTIMEDIA MESSAGING LOCATION AND MAPPING
MULTIMEDIA MESSAGING LOCATION AND MAPPING


Key Features
Key Features
SINGLE APP. TWO MODES.
• Group and Private PTT calls
• Group and Private PTT calls
Select one of two client modes: PTT Radio to emulate the experience of a conventional two-way radio, or Standard mode, which offers device-based management of contacts and talkgroups.
• Voice message fallback
Select one of two client modes: PTT Radio to emulate the experience of a conventional two-way radio, or Standard mode, which offers device-based management of contacts and talkgroups.
• Real-time presence
• Real-time presence
• Do not disturb
• Do not disturb
• Priority talkgroup scan
• Priority talkgroup scan
Key Features
Key Features
• Background calling
• Background calling
• Group and Private PTT calls
• Group and Private PTT calls
• Real-time presence
• Real-time presence
• Do not disturb
• Do not disturb
• Voice message fallback
• Text messaging
• Text messaging
• Video, photo and file sharing
• Video, photo and file sharing
• Location, mapping, and tracking
• Location, mapping, and tracking
• Geofencing
• Geofencing
• Voice message fallback
TURN YOUR SMARTPHONE INTO A MULTI-CHANNEL COMMUNICATION DEVICE WITH THE WAVE PTX MOBILE APP
• Priority talkgroup scan
SINGLE APP. TWO MODES.
• Voice message fallback
• Text messaging
• Text messaging
• Video, photo and file sharing
• Priority talkgroup scan
• Background calling
• Background calling

AVE PTX WIRELESS S E R VICE
WITH TL K S E R I ES
RADIOS
AVE PTX WIRELESS S E R VICE COMBINED WITH TL K S E R I ES WO-WAY RADIOS
HE BENEFITS OF WAVE PTX WITH A RUGGED TWO-WAY O ON A NATIONWIDE NETWORK.
ou can be up and running in less than 24 hours nd thanks to 4G network speeds, connections faster and more reliable
HE BENEFITS OF WAVE PTX WITH A RUGGED TWO-WAY O ON A NATIONWIDE NETWORK.*
ou can be up and running in less than 24 hours nd thanks to 4G network speeds, connections faster and more reliable

TLK 100 PORTABLE OR TLK 150 MOBILE TWO-WAY RADIO
RAPID, RELIABLE DEPLOYMENT. USE NATIONWIDE.
• Video, photo and file sharing
• Location, mapping, and tracking
• Geofencing
Select one of two client modes: PTT Radio to emulate the experience of a conventional two-way radio, or Standard mode, which offers device-based management of contacts and talkgroups.
Key Features
• Group and Private PTT calls
• Real-time presence
• Do not disturb
• Priority talkgroup scan
• Background calling
• Voice message fallback
• Text messaging
• Video, photo and file sharing
• Location, mapping, and tracking
• Geofencing
• Geofencing


• Location, mapping, and tracking

TLK 100 PORTABLE OR TLK 150 MOBILE TWO-WAY RADIO
RAPID, RELIABLE DEPLOYMENT. USE NATIONWIDE.
TLK 100 and TLK 150 two-way radios provide businesses with instant push-to-talk team communications over a nationwide LTE cellular network. Maximize coverage, connections, and productivity without expanding infrastructure.
Key Features
• Over-the-Air device management
• Powerful and slim design
TLK 100 and TLK 150 two-way radios provide businesses with instant push-to-talk team communications over a nationwide LTE cellular network. Maximize coverage, connections, and productivity without expanding infrastructure.
• Wi-Fi connectivity
Key Features
• Location tracking
• Over-the-Air device management
• Powerful and slim design
• Wi-Fi connectivity
• Location tracking
• Portable battery lasts full shift
• Loud and clear audio
• Private and group push-to-talk
• Real-time presence
• Portable battery lasts full shift
• Loud and clear audio
• Private and group push-to-talk
• Real-time presence


IDARO – Team Communications

Team Communication –Without Boundaries
Ever thought how great it would be to have the reliability and simplicity of two way radios with the global coverage of mobile?
IDARO is the revolutionary smart solution that takes instant team communications to the next level. Marrying the functions of two way radios with the features of a smartphone, IDARO instantly connects your teams, across global networks, at the touch of a button, no matter the sector.
One Device Multiple Functions
With IDARO, there is no need to carry separate radios, smartphones, or other devices around with you. A single handset, a single contract, and you have all the communication functions you need at your fingertips

Teams work better with IDARO


Whether it’s a single conversation, a group call, or a company-wide session, IDARO is the smart solution for any organisation, bringing teams together instantly and effectively with a single touch of a button. Faster than scrolling through contact lists or setting up online meetings, IDARO is the responsive solution you need.
Always-On Global Connectivity
As businesses increase their geographical reach and more and more people work from remote locations, IDARO removes the coverage limits of analogue and digital radios to connect everyone in your team, wherever they are. Utilise broadband networks with PTT communication that allows you to connect from anywhere with network coverage.
GROUP OR INDIVIDUAL CALLS
A single person can reach hundreds of users, organised in groups or have 1-to-1 private calls or send messages outside of a group.
TASK MANAGER & CENTRAL COMMAND
Assign tasks to team or individuals. Real time status report. Multiscreen central command centre.
The IDARO Handset
As tough as a two-way radio, as featurerich as a smartphone – IDARO handsets deliver the best of both worlds.
EMPLOYEE SAFETY
Man Down: automatic emergency notification. Fall detection with instant alert. Conforms to British certification standards.
LOCATION & MAPPING
Real time location and Geo-fencing on a map, creates alerts, records last location, and provides coverage in enclosed environmentsstandards.




10. X-RAY SCANNERS

SMITHS DETECTION
HI-SCANTM 6040-2is

HI-SCAN 6040 DV is an advanced dual-view X-ray inspection system for automatic detection of explosives and liquids. The dual view increases operational efficiency by eliminating the need to re-position or re-scan objects.
Offering superior image quality, smart display functions and easy integration into tray handling and management systems, it is the ideal solution for efficient screening in high threat applications such as airports, government facilities, embassies, or banks.
EDS CB C1 and LEDS algorithms – in combination with the optional iCMORE weapons capability for automatic detection of pistols, revolvers, gun
parts, flick, and fixed blade knives –elevate security, efficiency, and automation, without requiring additional hardware.
The HI-SCAN 6040 DV also provides high levels of protection against cyber threats by applying industry best practices such as operating system hardening, a host-based firewall, TripWire integrity monitoring and powerful user management with highly configurable password policies.
HI-SCAN 6040 DV is compatible with the Checkpoint.Evoplus screening and management platform which supports actionable operational data insights and health status monitoring plus centralised screening.
Straightforward integration into Smiths Detection or third-party tray handling lanes makes it an ideal choice for highthroughput applications.
Feature Highlights




HI-SCAN 5030C


The HI-SCAN 5030C X-ray scanner is an ideal solution for screening mail and personal belongings in commercial and public buildings due to its size, mobility and durability.
The HI-SCAN 5030C is specifically designed to enhance security screening operations from courthouses to corporate campuses. Its compact size and lightweight construction enable it to fit seamlessly into checkpoints and mailrooms. Vibration absorbers make it possible to transport HI-SCAN 5030C between various locations without requiring re-calibration, providing maximum flexibility.
Featuring proven HiTrax 3 electronics and software platform to enhance and expedite security screening operations. It produces reliable and easy-tointerpret scanned images enabling screening personnel to make threat and contraband assessment of parcels to personal items quickly and confidently.
The HI-SCAN 5030C is available as a stationary desktop scanner or as a mobile version on wheels featuring vibration shock absorbers and a storage compartment.
Feature Highlights




TR40 CABINET X-RAY SCANNER

The very latest generation TR40 +Smart Scan cabinet scanner from Todd Research provides a new benchmark of threat detection and
image management for compact cabinet scanners. At the heart of the TR40 +Smart Scan is a completely new software platform, managing the functionality and an intuitive user interface via a touch screen monitor. The smart card login means the TR40 +Smart Scan can be configured to enable data collection of individual user sessions further enhancing the effectiveness of the operators.
This is the largest cabinet scanner in the range, the generous chamber can accommodate mail sacks, large boxes and courier deliveries, with its one touch operation the TR40 allows rapid processing of scanned items all within a compact footprint.
XRC 60-40P (SHORT CONVEYOR)

The XRC 60-40P conveyor x-ray scanner is our most compact scanner of this size, boasting a range of advanced image processing functions, and topof-the-line software features. These cutting-edge technologies work together to make the scanner incredibly easy for operators to use, while also ensuring a high level of threat detection accuracy.






11.POST ROOM SYSTEMS



MyTAG – Post Room

Reinventing Postroom Systems – affordable tracking software for inbound and outbound mail.
MyTAG Post room is a flexible and low-cost system that allows you to securely manage your inbound and outbound mail. From the traditional receiving, collection, sorting and distribution of mail, to scanning in order to electronically manage workflow, provide archive records or enhance courier/ client accountability, all key processes are included.
MyTAG Postroom is already trusted by property managing agents, facilities management companies, buildings with multiple occupants and city offices. The system’s low cost and simplicity makes it ideal for any organisation that receives mail and parcels, and needs proof of collection for outbound items.

HOW IT WORKS
SCAN the incoming item’s barcode using a mobile device or tablet or generate your own unique tracking number. Use a barcode or unique reference number for outbound mail.
RECORD the date, time and place the item was scanned. Information can be accessed from anywhere using your desktop PC, mobile device or tablet. You can also report damages and save images
EMAIL a notification to the recipient or sender automatically, which can include notes and collection/tracking information.
TRACK mail and parcels in real-time from anywhere, avoiding disputes caused by delayed, damaged or lost items.
PROOF OF DELIVERY OR DISPATCH is provided by the date and time the item was received or collected by the recipient, or the despatch details. A signature can be captured for additional accountability.
REPORTING can be tailored to your needs and used for auditing. Use filters to breakdown reports by client, courier, dates and times and highlight trends including busy periods to assist with resource planning. Automatically send predefined reports and graphics to authorise email addresses.





Omni-Post Mail Room Delivery Tracking Software
Delivery tracking software is a cloud-based solution which can be used for internal delivery tracking needs. Delivery tracking allows organisations and businesses to log all inbound parcels and mail items via an easy-to-use system for end-to-end custody tracking and visibility.
Information can be accessed on any PC, mobile device, tablet or iOS/Android phone either within the building or remotely for live location tracking.

All you need to do is add a list of recipients to the admin back-end, and they will become searchable on any device using an app. Using barcode technology, a PDA (Personal Digital Assistant), or any mobile device you can access the backend admin interface where all information is stored. PDA’s can display who the recipient is, the delivery details and the details of the item due for delivery. It can also notify recipients and senders of the package’s location before delivery.



Smart Lockers
ExPD Smart Lockers provide self-service storage, contactless operation and secure protection for personal belongings and business assets.
Smart Lockers
Smart Locker transfers may be convenient, but they are also the most secure way to transfer any item with full traceability and accountability throughout the handover process.
ExPD Smart Lockers provide self-service storage, contactless operation and secure protection for personal belongings and business assets.
Our Smart Lockers are fully customisable, simple to install and simple to use, with superb technology developed by our own in-house team.
Smart Locker transfers may be convenient, but they are also the most secure way to transfer any item with full traceability and accountability throughout the handover process.
Our Smart Lockers are fully customisable, simple to install and simple to use, with superb technology developed by our own in-house team.







HOW DO SMART LOCKERS WORK?

How do Smart Lockers work?

SmartLocker
Connected - Accountable - Safe - Secure
Manual handling is no longer the preferred method of transaction when it comes to delivering and retrieving parcels, Smart Lockers can ensure handovers of any kind are contact free.
handling is no longer the preferred method of transaction when to delivering and retrieving Smart Lockers can ensure handovers of any kind are contact free.
Step 1

Employee or courier enters recipient details and locker size needed







Step 2 Deposits parcel and closes the door
Step 3
Locker notifies recipient with a QR key





Step 4
Recipient scans code to auto-open locker






12.VISITOR MANAGEMENT SYSTEMS



MyTAG Visitor Management System
A flexible low-cost solution for managing your site visitors and guests.
Key Features
� Interactive Calendar
� QR code and contactless sign in
� Evacuation notifications to all hosts and guests
� Automatic Email & SMS Notifications
� Personalise Invites
Enhance your guest experience
Send invites with ease
The easy to use form sends your personalised invites to upcoming guests, inviting them to attend the site at a your selected appointment time and requests their approval. Once approved they receive a QR code via email with a Google Maps integrated link to your address. Personalise your invites with your own text and instructions for attending your site.

Your visits at a glance
All current and upcoming visits displayed clearly on our interactive calendar. Create, amend and remove appointments simply. The ability to see who has confirmed or denied their attendance will help you plan your day for you and your staff.
Contactless Sign-In
Guests arriving on site can use the QR code or PIN code provided in their email invitation to securely self sign-in to your site using any modern tablet or mobile device set up on your site. Guests can also be checked in manually at reception and can be confirmed as ‘’Security Checked’’.
Automatic Notifications
MyVisitor automatically notifies hosts of their guests arrival once they have checked in.
Notifications can be sent via e-mail or SMS depending on the hosts preference.



Yardi Bluepoint

Staff, tenants and occupiers, reception teams and building management can access real-time visitor data. This allows for strategic decision-making on staffing, space utilisation and compliance. Smarter visitor access control gives you the ability to manage visitor movement and add additional layers of building security.
FEATURES AND BENEFITS
Awareness with Real-time Data

Bluepoint integrates with tenant platforms such as OfficeApp and HqO and leading access control manufacturers including, Lenel S2, CCure and Gallagher. So, whether you need hybrid, flexible, contactless or experience led visitor management, Yardi Bluepoint has you covered.
� Gain actionable insights to enable safer and more efficient management of your spaces
� Stay up to date with planned visitors and keep account of drop-in visitor numbers
� Plan in advance for reception services, security and visitor amenity requirements by reviewing Bluepoint data
Enhanced Experience
� Create branded visitor invitations with key information such as pre-visit forms or travel details.
� Integrate Bluepoint with on-site access control and include a QR code in the visitor invite for fast check-in
� Deliver a great experience from short-term visitors and event attendees to contractors and staff



Security and Compliance
� GDPR Compliant – stay up to date with visitors in your building for critical security and compliance
� Gain an accurate overview of who is where and when in your building with Bluepoint’s checkin and check-out process
� Implement additional security with timelimited, temporary access passes for visitors and staff

Easy to Integrate

Tenant Empowerment
� Manage access permissions for meetings and events and enable your tenants to book timelimited appointments by visitor type
� Integrate with existing tenant management software to provide a seamless experience
� Invite visitors directly from any calendar: Outlook, Gmail; desktop or mobile – Bluepoint is compatible with all calendar apps
� Fully featured API allows for smart connections with new and existing building management technology
� Access control integrations with leading manufacturers and tenant engagement platforms allow for an improved experience
� Easy to implement and secure. The Bluepoint team are on hand to ensure a successful deployment.



Contactless Access
� Bluepoint visitor management allows for smart access using existing access control with a mobile QR code or access card
� Activated Bluepoint QR codes can be used with speed lanes, lifts and even meeting rooms
� Facilitate contactless check-ins with a free standing or desk mounted kiosk
ExPD Sky Visitor System

SkyVisitor, the visitor management system from ExPD, ensures checking in to your building is the simplest and most professional experience possible.
First impressions count, but regulatory compliance and the safety of visitors, contractors and your team, matter even more – SkyVisitor has that covered too.
Little can be more important in facilities management, than the way you physically manage visitors, contractors and your people to and through your buildings. We work with everything from prestigious multi-tenanted apartments and corporate headquarters, to food handling facilities, shopping centres and NHS Estates.
SkyVisitor goes to work before your visitor, guest or contractor even arrives on site.



When the host books a visit, the visitor management system automatically issues an invitation email. Although auto-generated, the content of the email can be branded and is fully customisable to include all the information the guest needs to simply and safely begin that visit.
That includes your location, which entrance to arrive at, and how to request and be assigned a parking space. It accommodates ad hoc visitors, contractors and staff and can outline security requirements and include essential health and safety information. It can even provide pass numbers or keys or include a unique QR code for
contact-free, speedy check-in from their smartphone or mobile computer.
In addition to the systems for all visitor check-ins, SkyVisitor makes the management of staff, visitors and contractors on-site safer, more professional and more accountable. Pre‐planned visits ensure all documentation is in place before an individual even arrives on site. It also acts as a second layer of health and safety management and accountability.
Only once the host checks documentation is submitted and correct is the visit from a staff member, visitor or contractor approved.




Managing visitors and reporting mechanisms
The SkyVisitor Portal includes dynamic, real-time lists of expected, arrived and departed staff, visitors and contractors and allows for future planning and resourcing. Reports can include visitor statistics, trends, volumes, no‐shows and much more, ensuring your reception systems are working effectively. These can flag trends before they become issues.
Reporting and improving
The Online Portal allows you to view dynamic lists of expected, arrived and departed visitors and produce statistical reports such as visitor statistics, trends, volumes, no-shows and much more. SkyVisitor allows you to create your own custom reports and have these saved in the system. This means that you can get customised meaningful data out of your visitor system.
Photo badges
The integrated visitor photo badge system is quick and simple, badges can even be pre-printed for planned arrivals. They can be produced at any size on a host of printers: card, paper, thermal, re‐writable card or label.
Item control
Items issued to visitors – such as radios, keys, access cards and fobs – can be registered through SkyVisitor and onscreen alerts created when the visitor checks out.
Multiple Locations
The system is set up with a location hierarchy. This can be separate offices, different parts of sites etc. Having multiple locations allows you to report on activity at different offices for example. It also means that you can have different rules and workflows for visitors at each location.
Express Check in
If a visitor is pre-booked they can be sent a QR code before their arrival. When the visitor arrives at the site they can scan their QR code on a scanner at the check-in location and this instantly checks the visitor in. Doing this speeds up the check-in process and also means that it is a contactless check-in.
Access Control
SkyVisitor has the ability to integrate directly with your access control system. You are able to define what locations visitors have access to via your visitor system, you can also see when a visitor has moved between areas at your site.


13. KEY MANAGEMENT SYSTEMS



MyTAG – Key & Asset Management
MyTAG Key and Asset management will improve management of your portable assets, saving you time and money, and allowing you to demonstrate the professionalism of your processes and systems.
MyTAG technology uses secure Near Field Communication (NFC) tags with cloud based software, which allows companies to manage and monitor keys (or other portable assets) that are logged in and out of business premises. This simple to use system provides you with the whereabouts of every key you manage. The same system is also used for bicycles, heaters and any other portable items that need to be managed.

All physical keys are tagged with a unique NFC key tag. When a key is used, it is tapped on the tablet to launch the checkout interface and information about who took the key and when it is due back is recorded. When the key is returned, it is tapped again on the tablet to check it back into the system. Automatic reminders are issued to follow up on keys which are overdue for return.
Improving Efficiencies and Security
MyTAG replaces outdated and inefficient processes. Replacing paper based log books makes the key management process faster and more accurate, and reduces the risk of human error. Being careless with keys is a huge potential security risk, which can damage your reputation should things go wrong.
Cloud Based Solution
The easy to use, cloud based system is simple to install, with no requirement to integrate into existing IT systems, allowing you to be up and running quickly. The low cost of installation, and low operational costs, allow you to start saving time and money immediately.
Real Time Management Information


The MyTAG Key and Asset Management dashboard allows you to access real time information on the whereabouts of every key you manage, from wherever you are. You can instantly find whether a key has been checked out, taken away from your business premises, by whom, and why they have taken it. The system can send reminders via text or email about unreturned keys, allowing you to follow up quickly, reducing the risk of loss. This saves time hunting for missing keys, and the cost of key replacement when they cannot be found.
High Security Key Filing System 150/HS
� Designed specifically for high security environments
� Manufactured from 3mm welded steel plate body with a 6mm steel door
� 3-way locking mechanism for added protection
� Standard locking – CEN/VDS approved double bitted lock and 2 keys
� Adjustable colour coded and numbered hook bars allow the layout to be customised
� Ingenious key tabs are designed to hang so that the number is always visible
� Key locations can be recorded on the control index which is removable for added security
� Durable Light Grey paint finish will suit most environments
� Supplied with bol ts and plugs for surface mounting. Alternatively recess into the wall for greater security



Traka – ASSA ABLOY
Electronic key management systems
Traka is the leading solution for securing and tracking keys, trusted worldwide by many of the world’s biggest organizations across nearly every sector. Our proven and reliable key cabinets provide fast and convenient access to keys for the right people at the right time, with total control and centralized visibility.


Electronic key control systems with audit trail
Traka’s electronic key cabinets are an intelligent management solution that help secure, control and audit the use of every key.Only authorised staff are allowed access to the custom key cabinets and only then, to designated keys. Our high-security electronic key control solutions provide a full audit trail of who removed the key, when it was taken and when it was returned keeping your staff accountable at all times.
Intuitive & efficient management
� Authorized users can quickly access the system via access card, fingerprint or PIN
� You determine who has access to which keys, and when
� An audit trail is recorded of every transaction for total accountability
� Set curfews to ensure that keys are returned on time
� Receive instant notifications of important events, such as an overdue item
� Dozens of customizable features allow the system to meet your unique access protocols
Key benefits


� Robust key storage in secure, networked electronic cabinets
� Traka iFob ensures reliable recordkeeping
� Web-based management and reporting platform saves time
� Auditable reporting and management reporting on key use
� Integrates with other access management solutions to provide an integrated access management solution.
� Our systems scale with your business needs
Much more than key security
Controlling access to your key inventory is important for the safety, security and efficiency of your business. Traka Touch Pro key cabinets provide efficient, automated access to keys while maintaining the strict security protocols that protect your operation, all with no adminitrative oversight required.
Key control: scalable to enterprise level
Key control solutions ranging from a simple, standalone system, to thousands of networked systems across the globe.
� Four key cabinet sizes (5-180 key positions) available for any application.
� Scalable and modular design allows the solution to grow with the needs of your business
� Centrally manage all key cabinets and equipment lockers from TrakaWEB, with regionalization for simplified administration


TRAKA TOUCH PRO L

Traka’s intelligent key management systems secure, manage and audit the use of every key in your business.
The Traka Touch Pro is our most secure and sustainable key management range to date.
The Touch Pro L electronic key management system is designed especially for larger organizations with a high key turnover. Accommodate up to 180 keys (360 using double-density strips) in one key cabinet, and up to 720 keys using extension units.
� Manage up to 180 sets of keys or 360 using doubledensity strips in one unit
� Manage up to 720 using extension units
� Secure and durable
� Modular and scalable
TRAKA TOUCH PRO M


Traka’s electronic key management solutions secure, manage and audit the use of every key in your business.
The Traka Touch Pro range of key cabinets is our most secure and sustainable to date.
Touch Pro M key cabinets are a versatile solution allowing for system scalability. Accommodate up to 60 key sets in this innovative key cabinet or 120 using double-density receptor strips. Or up to 480 keys using extension units.
� Manage up to 60 sets of keys (120 with doubledensity strips) in one unit
� Manage up to 480 using extension units
� Secure and durable
� Modular and scalable
TRAKA TOUCH PRO S


Traka’s electronic key management systems secure, manage and audit the use of every key in your business.
The Traka Touch Pro range is built to last, built for simplicity, built for flexibility, and built with sustainability in mind.
Traka Touch Pro S key cabinets can manage 20 keys (or 40 keys using double-density strips) and are ideal for organizations with smaller amounts of keys to control.

� Manage up to 20 sets of keys (40 with doubledensity strips)
� Secure and durable
� Modular and scalable


THE HC SERIES FOR PROPERTY MANAGEMENT
Traka HC key cabinets are uniquely designed for the property management sector, which require strict control over a high volume of keys in a small footprint.
Paired with the suite of administrative tools and detailed reporting via our web-based software, The HC line of cabinets offer a total solution for the property management industry.
Traka’s HC Series of Key Cabinets is exclusively produced for the Property Management sector.

TRAKA 21

Traka21’s innovative plug and play system provide small to mediumsize businesses with the very latest in intelligent key management products. Simple, efficient, and cost-effective, Traka21 helps trace and account for every key or keyset, which are individually locked in place, ensuring that critical business operations are never jeopardized.
Ensuring that the right keys are available to the right people at the right times is a concern for every organization. Traka21 is a sophisticated stand-alone key management system that combines innovative RFID technology and robust design to provide small and medium-sized businesses with our advanced key management products of 21 keys or keysets in an affordable plug and play unit.








14.PATROL MANAGEMENT SYSTEMS



CIS In-House Patrol Management Systems
CIS The Hub Patrol System
The hub is a bespoke cloud-based platform that supports security personnel on-site.
The Hub comprises various key applications including the Daily Occurrence Book, Incident Management, Hub Patrol, Document Manager and Site Visit Assessments.
The Hub constantly updates to keep up with modern security trends supporting on-site teams.



The Hub Patrol is a real-time patrol solution which allows fast, secure, and efficient access to patrol data. Anywhere that there is a need to prove and ensure the physical attendance of a person at a specific location, the Hub Patrol is the ideal solution for the following key reasons:
� It will give you an audit trail to prove the location and activity of your staff and assets.
� It is simple for the end user with minimal set-up time
� It offers proof of attendance in realtime, with alerts being supplied if there are non-attendance risks.
� Managers and staff can exchange actions and messages via mobile phone.
The Hub Patrol dashboard gives the Controller access to view live patrols and can communicate with the Patrol Office.


The system highlights which patrols are still ongoing so that they can be monitored.
The Manager can get time-sensitive information from the dashboard and can search for a specific time period if required.

The Patrol Report includes the Patrol Officer’s name for audit purposes.
The system records the GPS location of the device whenever it hits a point and when you click on the position this opens up Google Maps and display the location.
The system requires users to hit the start and finish NFC points. The system has the ability to make the Officers conducting patrols follow the same route through the force sequence feature.
The end user can add notes and pictures which will appear on the report.

Patrols conducted can be exported in PDF format.
The system has an automated mailing feature which can be set up to send customers patrol reports either as the patrol is completed, on a daily, weekly, or monthly basis.
Customers can have access to the system to view the patrol, daily occurrence, incident reporting and site visits.



MyTAG Proof of Presence
Proof of presence, time and attendance, proof of ser vicing, security patrols and much more!
MyTAG Proof of Presence provides trusted proof that a person was at a given location at specific times, allowing proof of servicing times, security patrols, visit periods and other time/location-based events. An efficient and effective solution for managing services, MyTAG allows you to demonstrate professionalism and compliance as well as saving you time and money.
MyTAG Secure NFC Tags are installed as checkpoints at key building locations, or on fixed assets and each tag is activated with the tap of a low cost Near Field Communication (NFC) device. This simple tap is all that the person needs to deliver trusted proof of presence at a given checkpoint. If a report is required, a proprietary application can be engaged on the mobile device, providing immediate feedback to team members or managers, via photo, video or text entries. This allows action to be taken quickly, whatever the issue.

Secure and Trusted
MyTAG Secure NFC Tags are patented and cannot be copied or cloned, unlike bar codes, QR codes or standard NFC tags. Proof of presence is guaranteed, using NFC and Global Positioning System (GPS) technology, allowing you to demonstrate full compliance with servicing commitments. Legal, warranty and contractual obligations can be proven, whether they relate to buildings or their assets, and whether they are carried out by employees or contractors.

Saving Time and Money

MyTAG replaces time consuming manual and paper-based systems, with a quick and easy to use electronic one. Timestamped proof of presence at the start and end of service visits provides verifiable proof of servicing times, meaning contractors are only paid for the work carried out, and ensuring the correct servicing frequencies.
Real Time Information
The MyTAG dashboard allows you to access real time and historical management information from wherever you are. Service or maintenance histories can quickly be downloaded, without the need to search logbooks or archives. This allows a quick response to any queries or issues and provides an instant overview of current activities.
Cloud Based Solution
The easy to use, cloud-based system is simple to install, with no requirement to integrate into existing IT systems, allowing you to be up and running quickly. It is intuitive to use, so employees and contractors require little training, and the low cost of installation and operation mean that you can start to reap the benefits immediately.
MyTAG Proof of Presence is the base of our simple and easy to use Time and Attendance system. Ideal for part-time and temporary employees, everyone is assigned an individual tag, which is scanned when they start and end their shift. An accurate record of hours worked can be automatically inputted into the payroll system, or transferred to Excel if required, supporting efficient contractor management.
MyTAG Proof of Presence can be used to prove delivery of any facilities services against agreed SLAs and KPIs. With the critical importance of cleaning during the Coronavirus pandemic, it provides evidence that crucial tasks, such as high touch point and washroom cleaning, have been completed according to the schedule.






Artificial Intelligence for CCTV Control Rooms
PELCO CALIPSA – Video analytics software for corporate safety and security
Enhance the efficiency and performance of your corporate security SOC operations with Calipsa Pro Analytics, AI analytics software for real-time and forensic analysis.

Benefits












REMARK
Creating safer, smarter businesses with AI-driven video analytics.
Turn your video footage into actionable insights for quickly identifying and addressing incidents.
� A user-friendly and smart camera system designed for your business.
� Our industry-leading video analytics capabilities have earned the trust of our customers.
� Turn your video footage into actionable insights that enhance security, safety, and productivity.


Enhanced security with Advanced AI analytics

SSP has developed advanced AI models that cover a wide range of security or safety functions, object (appearance and attributes) detection and recognition, protective equipment, vehicle plate number, unattended object, abnormal behaviour – falling/running, fire, and smoke, etc.

Empower real-time situational awareness to enhance operational efficiency
SSP combines all the AI alert events by organizing the geographic map information and dashboard in a userfriendly way so that the management team can understand the whole operation and provide actionable insights to the staff for making decisions and deploying the resources for rapid actions on stopping crimes and preventing loss.

Search and resolve incidents faster

Remarks video analytics features advanced search methods to assist & speed up investigations.

Unify your locations on one dashboard
Seamlessly integrate cameras from any location into a unified management platform with easy setup, boosting your system’s return on investment.



Biometrics
As facial recognition technology has only recently become available on the market, you may be wondering what aspects can play a role in the application. Below will provide better insight into what facial recognition access control entails exactly, and what to consider when purchasing such a system.

















Quick Access at All Times
Because biometric facial recognition is based on something people always carry with them, they will never face a closed door. As all faces are unique, people can be distinguished from one another and identified by means of their facial features.
An additional advantage is that only minimal active cooperation is required of the user at the access control point. As soon as a face enters the camera’s focus range, the software can check the authorisation. As access passes are no longer necessary, they also cannot be forgotten. Moreover, there is no longer needed to wait for a colleague to dig through their things for a pass and hands are free to hold coats and bags.
Drone Technology
No Sharing of Passes
One common issue in access control is the sharing of personal passes with colleagues. Such improper use can lead to unauthorised people entering the premises. Using facial recognition prevents unknown individuals from passing through access control just like that.
Furthermore, facial recognition access control makes it impossible to steal or copy an access pass. The result is an improvement in the level of security overall.


Tando™ is a self-navigating AI-based security robot drone that monitors and alerts you about intruders, security breaches, safety issues, and potential hazards while eliminating false alarms. Tando™ is a flexible, efficient, and future-proof security solution for commercial spaces. While not in flight, Tando™ docks on the ceiling, serving as a security camera.


Tile™ is our patented ceiling-mounted docking & charging station. Tile™ is designed to support Tando™’s zero breaks schedule so Tando™ can monitor and inspect your space for security, safety, and maintenance issues even while charging. Tando™ can “hop” from Tile™ to Tile™ to cover large spaces more efficiently.

Control Bridge is the brain that manages Tando™’s operations. Create new missions and schedules, launch ad-hoc missions and get alerts on events, detections and changes customed to your needs. The Control bridge SW easily connects to any building system and other IoT devices.
Smart Building Application


CIS Innovative Solutions have teamed up with MyTAG and Mallcom to launch a smart building App. The App will be aimed at facilities management and occupiers.
Incorporated within the App will be broadcast messaging system, post room/deliveries, visitor management, local restaurant offers, news and travel.

The App will be a communication tool for all building users and can be tailored and branded specifically per building.






16. HOSTILE VEHICLE MITIGATION


Matador 4 Bollards
Base plate consisting of 2No. central sliding and 2No. fixed bollards. Opening aperture – 3991mm
Classification: IWA 14-1: 2013 Bollard V/7200[N2A]/64/90:0.1
Manual version (where you would physically push the 2No. central sliding bollards to the side)


Terror Stopper 1 Bollards
To supply and install Terror Stopper 1 PAS 68 Static Bollard – 219mm diameter bollard 7.5 tonne vehicle at 30 mph. PAS68:2010 rating of V7500(N2)48/90/0.0/0.0


Truckstopper 07 +100mm – (Fixed) Bollards


Comes complete with Core Bollards, Socket, standard oval stainless-steel shroud, and rebar. (200mm Foundation/40mph Solution)


Auto Arm Barrier

� Auto Arm Barrier – 30mph Impact
Tested Barrier Equipment (PAS 68:2010 V/[N2]7500/48/90:2.4/7.9)
� 4 metre clear opening, Model 942
Impact Tested heavy duty, Electrohydraulic traffic control barrier: 230v single phase or 400-volt three phase supply with an operating speed of approximately 15 seconds per raise or lower for a 5-metre boom (QTY 1)
� Fixed-end support structure to receive barrier boom when in the lowered position (QTY 1) OR 6 metre clear opening, Model 942 Impact
Tested heavy duty, Electro-hydraulic traffic control barrier: 230v single phase or 400-volt three phase supply with an operating speed of approximately 15 seconds per raise or lower for a 5-metre boom. (QTY 1)

� Fixed-end support structure to receive barrier boom when in the lowered position (QTY 1) Control Equipment.
� Dual aspect Red/Green traffic light and mounting post. (QTY 2)
� HGV height control reader posts to mount intercom equipment. (QTY 2)
� Vandal resistant intercom system comprising: 2 controls to 1 receiver units, suitable for external use. (QTY 2)
� Housing mounted “test/access isolate” key switch, control unit. (QTY 1)
� Safety Equipment Safety induction loop vehicle detection system. (QTY 1)
� Photocell safety system. (QTY 2)
� BAE sensor, presence detection system. (QTY 2)
Inclusions
The operation of automatic rising arm traffic barriers can create a hazard to persons or vehicles in the vicinity of the barrier. The above Safety equipment is included to negate some, or all this hazard Additional Safety equipment may be available, please check with us for details. Control of the barrier will be as follows: Entry will be affected by: – Intercom and push button provided by Safetyflex. Exit will be affected by: –Exit vehicle detection loop provided by Safetyflex. Please note that our proposal is subject to site survey to confirm barrier length required to secure intended location.
� Generic drawings (up to revision c) showing suggested equipment layouts and incorporating standard “as tested” civil works and local cable ducting requirements. Where there is a requirement to validate foundation details in respect of transition between adjacent equipment, or local ground conditions, Heras can recommend a suitably qualified structural / civil engineer to undertake this work at additional cost.
� Delivery to site using a HIAB vehicle consisting of two consignments for separate delivery of stanchions and the remainder of barrier equipment –Commissioning of the equipment shown in Section 1.


Road Blocker
We can supply a Shallow Mount Viper Roadblocker crash tested to 7.5 tonnes @ 80kph.
Barriers are 3.0 metre, so you would need 2No. for the larger openings.


Automatic Raised & Static Bollards
Another option is to have a mixture of fixed and automated raised bollards.





Manual PAS rated barrier


PAS68/IWA – HVM Planters
Tested to the limits and bearing the PAS 68: 2010 standard, our security planters are in place outside banks, local authority buildings and railway stations across the country, ready to mount an effective defence against any vehicle used as a battering ram.
Their appeal is that while they are capable stopping and disabling a 7.5 tonne truck travelling at 64kmh, the planters are aesthetically pleasing and can be used to mount an attractive floral display to bring a touch of nature’s colour to the concrete jungle.
They are available in three different sizes and range of finishes, including stainless steel and bronze patina, the security planters can be installed quickly and, at 100mm, have the shallowest fixings in the industry, so there’s no danger of disturbing underground facilities.
� Identical to standard planters
� Available in 3 sizes and in a range of colours
� Surface mounted
� Enhances the landscape as well as providing protection
� Easily and quickly installed by our trained fitters







17. CAR PARK MANAGEMENT SYSTEMS


Introduction

Parking Management systems have become a crucial part of the parking process for both parking operators and users with the emergence of parking technologies. Nowadays, parking management without a systematic system is complex and, in some cases, even impossible. Parking management systems provide convenience and flexibility when controlling the flow of vehicles in a parking area. With a CIS Innovative Solutions management system, you can enjoy various parking facilities and ensure outstanding results. Investing in a good parking solution is necessary to manage your car park effortlessly. Our expertise will assist you in understanding why you need an efficient parking management system and how it can benefit you.
Advantages of an Innovative Parking Management Solution
As we navigate the benefits of parking management systems, it’s evident how crucial they’ve become in today’s car park landscape. These systems make the parking process efficient and add value in ways we might not always recognise at first glance. Let’s explore these benefits in detail:
Superior Technology
Parking management systems are known for their integration with technology. Most of these systems are based on improved models and technological innovations so that they can be used in various car parks. Moreover, you can customise the smart system based on the needs and requirements of your car park, whether for residential or commercial use.
Better parking experience
Better car park management means happier customers. A parking management system enhances the customer journey by providing a unified procedure. An efficient parking management system enables users to find empty parking spaces, saving time and fuel and improving customer satisfaction.
Increased Protection
Parking management systems have advanced security features like ANPR technology to enable you to prevent parking misuse and suspicious activity in your parking facility. Parking management systems provide upgraded security, safety and privacy so car owners can rest assured that their cars are well-protected.
Reduced traffic and pollution


Vehicles circling an area searching for an empty parking space cause most city traffic. Moreover, significantly driving around or waiting for a parking space to be vacant burns through a lot of fuel and releases emissions daily.
An optimal parking management system opens the option of quicker parking that significantly reduces city traffic, driving time, vehicle emissions, and carbon footprint.
Easy implementation and management
Another benefit of a parking management system is that it can be designed and implemented efficiently. These systems have a well-organised structure; you can easily manage, control, and regulate them. CIS Innovative car parking management systems are also user-friendly, so the parking staff won’t have any difficulties handling the system, thus improving the whole car park management process.
Cost-effective
Another advantage of installing a CIS Innovative Solutions parking management system is the cost.
It runs on a low workforce so that you can save money and time. Another great feature of a parking management system is controlling the car park/ streetlights and other services that require electricity. You can set all electrical devices to shut automatically at a particular time every day or remotely switch them on/off depending on the car park usage level. The potential options are limitless.
Uses integrated software and applications
Parking management solutions use software and applications that can be combined. Depending on your car park’s requirements, many customisation options are available. Whatever your requirement is, an effective parking management system will accommodate this and make the parking experience more convenient. Implementing the correct parking management system saves costs, time and energy. With the increasing need for parking, upgrading to a well-organised parking space is crucial.
At CIS Innovative Solutions, we aim to make your car as precisely as you want. Our parking management system guarantees that your parking facility will work far more efficiently.

Conclusion

In short, parking management systems give smart and easy solutions for today’s car park challenges. Using tech, they make parking smoother and better, helping with convenience and safety and looking after the environment. Making parking methods better saves time and money for everyone. There are many good things about parking management systems for car park owners and those who use them. Owners get things done more efficiently, while people parking find it simple and stress-free. These ways of working lead the way in making parking less of a headache, cutting down on pollution, and making our city spaces last longer.
The information found within the CIS Innovative Solutions Catalouge are an illustrative portfolio of the services and products we offer. Tailored solutions and custom engineering are available to mitigate all risks through in-depth site surveys.
Please contact the team using the details below if you would like to book a site survey or require further product information.

M: 07825 191 613
T: 020 8690 1903 kuldeep.kainth@cis-security.co.uk
M: 07407 816 319 T: 020 8690 1903 george.harwood@cis-security.co.uk



M: 07712 664 380
T: 020 8690 1903





