

@military_cots www.MilitaryEmbedded.com June 2024 | Volume 20 | Number 4 John McHale Space tech recommended reading 7 Technology Update Military tests lower-stakes AI tools 8 Mil Tech Trends AI's major step onto the battlefield 20 Industry Perspective MOSA -- friend or foe? 40 NAVIGATING THE NEW FRONTIER: RAPID DEPLOYMENT AND ROBUST TESTING OF SATELLITE SYSTEMS P 16 P 28 AI and the OODA loop: How AI enhances strategic decisions for today’s warfighters By Tim Stewart, Aitech
ADI’s AD9213S is the industry-leading, commercial space qualified 10.25 GSPS RF analog-to-digital converter that helps you thrive, not just survive in space. Trust ADI to get your high speed signal processing applications to market faster.

Achieve fast data conversion at analog.com/AD9213S
on Earth.
for Space.
Trusted
Qualified
ON-CHIP DSP UP TO 5 GHz iBW DSP 70 dBFS SFDR SIMPLIFY SYSTEM DESIGN PROGRAMMABLE RADIO ARCHITECTURE

Editor’s Perspective
7 Space-tech reading list By John McHale
Technology Update
8 U.S. military trialing AI tools for more than battlefield advantage By Lisa Daigle
THE LATEST
Defense Tech Wire
10 By Dan Taylor
Editor’s Choice Products
42 By Military Embedded Systems Staff Guest Blogs
44 The promises and pitfalls of an AI-enhanced battlefield By George Kamis, Everfox
45 Beware the buzzword By Simon Collins, Abaco
Connecting with Military Embedded
46 By Lisa Daigle
WEB RESOURCES
Subscribe to the magazine or E-letter
Live industry news | Submit new products
http://submit.opensystemsmedia.com
WHITE PAPERS – Read: https://militaryembedded.com/whitepapers
WHITE PAPERS – Submit: http://submit.opensystemsmedia.com


SPECIAL REPORT: Military satellite communications
12 Automated network management keeps military SATCOM users connected By Rick Lober and Dr. Rajeev Gopal, Hughes
16 Navigating the new frontier: rapid deployment and robust testing of satellite systems By Kyle MacCoy, NI (now part of Emerson)
MIL TECH TRENDS: Enabling artificial intelligence in military systems
20 AI now playing a big role on the battlefield By Dan Taylor, Technology Editor
24 The evolution of DoD policy and the role of AI in modern warfare By Drew Thompson, Sealevel Systems
28 AI and the OODA loop: How AI enhances strategic decisions for today’s warfighters By Tim Stewart, Aitech
32 The steps to laying out an embedded system quantum roadmap By Steve Roemerman, Lone Star Analysis
INDUSTRY SPOTLIGHT: Rad-hard electronics design trends
34 Covering fault scenarios in mission-critical military Ethernet applications By Richard Tse, Microchip Technology
38 Military rad-hard designs for space … and beyond A conversation with Sean D'Arcy of Infineon Technologies and Josh Broline of Renesas By John McHale, Editorial Director
INDUSTRY PERSPECTIVE: Open standards
40 MOSA – friend or foe?
By Chip Downing, S5 Intelligence Corp.
To unsubscribe,

ON THE COVER:
The space industry is undergoing a significant transformation, with several trends shaping its future. The small-satellite revolution – due to the increased demand for satellites to perform unique missions and the focus on smaller, less expensive satellite constellations – is driving an increased focus on cost efficiency, reliable testing, rapid deployment, and scalability.
COLUMNS
4 June 2024 MILITARY EMBEDDED SYSTEMS www.militaryembedded.com 20 All registered brands and trademarks within Military Embedded Systems magazine are the property of their respective owners. © 2024 OpenSystems Media © 2024 Military Embedded Systems ISSN: Print 1557-3222 @military_cots
https://www.linkedin.com/groups/1864255/ FEATURES
Published by: www.militaryembedded.com June 2024 Volume 20 | Number 4 TABLE OF CONTENTS 12
your name, address, and subscription number as it appears on the label to: subscriptions@opensysmedia.com
email


® OFFERS THE LARGEST SELECTION OF
Most manufacturers offer just a few VPX power supplies off the shelf, with high costs for full-custom. The Behlman the most COTS AC to DC and DC to DC units configured for a wide range of high-end industrial and military applications. All feature our state-of-the-art new engineering standard, Xtra-reliable design and Xtra-rugged construction.
Insist on the leader. Not just VPX,



INVERTERS The Power Solutions Provider When it comes to VPX, one company has the most flavorS
POWER SUPPLIES,
MINIMAL COSTS FOR
ADDITIONAL CUSTOMIZATION
ONLY VPXtra
MIL-SPEC
WITH
ANY
AC POWER SUPPLIES / FREQUENCY CONVERTERS COTS POWER SUPPLIES : 631-435-0410 : sales@behlman.com : www.behlman.com
2 Analog Devices, Inc.
Trusted on Earth. Qualified for Space. 5 Behlman Electronics, Inc. –When it comes to VPX, one company has the most flavors 3 Cobham Advanced Electronic Solutions (CAES) –Pioneering advanced electronics
27 Elma Electronic –Enabling the warfighter with OpenVPX
48 GMS – X9 Spider: The world's most powerful full-featured wearable AI computer
25 Interface Concept –Elevating your embedded experience
33 Phoenix International –Phalanx II: The ultimate NAS
35 PICO Electronics Inc –Size does matter!
19 Sealevel Systems, Inc. –Testing & Simulation Standardization Fall Behind UAS Innovation
23 State of the Art, Inc. –Reliability … the only option
EVENTS
NSREC – 2024 Nuclear and Space Radiation Effects Conference July 22-26, 2024 Ottawa, Canada https://www.nsrec.com/information-2024/
embedded world North America
October 8-10, 2024 Austin, TX https://www.embedded-world.de/en/ embedded-world-wide/embedded-worldnorth-america
AUSA 2024 Annual Meeting & Exposition (U.S. Army)
October 14-16, 2024 Washington, DC
https://meetings.ausa.org/annual/2024/
AOC (Old Crows) 2024 International Symposium & Convention December 11-13, 2024 National Harbor, MD https://aoc2024.crows.org/
GROUP EDITORIAL DIRECTOR John McHale john.mchale@opensysmedia.com
ASSISTANT MANAGING EDITOR Lisa Daigle lisa.daigle@opensysmedia.com
TECHNOLOGY EDITOR – WASHINGTON BUREAU Dan Taylor dan.taylor@opensysmedia.com
CREATIVE DIRECTOR Stephanie Sweet stephanie.sweet@opensysmedia.com
WEB DEVELOPER Paul Nelson paul.nelson@opensysmedia.com
EMAIL MARKETING SPECIALIST Drew Kaufman drew.kaufman@opensysmedia.com
WEBCAST MANAGER Marvin Augustyn marvin.augustyn@opensysmedia.com
VITA EDITORIAL DIRECTOR Jerry Gipper jerry.gipper@opensysmedia.com
SALES/MARKETING
DIRECTOR OF SALES Tom Varcie tom.varcie@opensysmedia.com (734) 748-9660
STRATEGIC ACCOUNT MANAGER Rebecca Barker rebecca.barker@opensysmedia.com (281) 724-8021
STRATEGIC ACCOUNT MANAGER Bill Barron bill.barron@opensysmedia.com (516) 376-9838
STRATEGIC ACCOUNT MANAGER Kathleen Wackowski kathleen.wackowski@opensysmedia.com (978) 888-7367
SOUTHERN CAL REGIONAL SALES MANAGER Len Pettek len.pettek@opensysmedia.com (805) 231-9582
DIRECTOR OF SALES ENABLEMENT Barbara Quinlan barbara.quinlan@opensysmedia.com AND PRODUCT MARKETING (480) 236-8818
INSIDE SALES Amy Russell amy.russell@opensysmedia.com
STRATEGIC ACCOUNT MANAGER Lesley Harmoning lesley.harmoning@opensysmedia.com
EUROPEAN ACCOUNT MANAGER Jill Thibert jill.thibert@opensysmedia.com
TAIWAN SALES ACCOUNT MANAGER Patty Wu patty.wu@opensysmedia.com
CHINA SALES ACCOUNT MANAGER Judy Wang judywang2000@vip.126.com
PRESIDENT Patrick Hopper patrick.hopper@opensysmedia.com
EXECUTIVE VICE PRESIDENT John McHale john.mchale@opensysmedia.com
EXECUTIVE VICE PRESIDENT AND ECD BRAND DIRECTOR Rich Nass rich.nass@opensysmedia.com
DIRECTOR OF OPERATIONS AND CUSTOMER SUCCESS Gina Peter gina.peter@opensysmedia.com
GRAPHIC DESIGNER Kaitlyn Bellerson kaitlyn.bellerson@opensysmedia.com
Emily Verhoeks emily.verhoeks@opensysmedia.com
6 June 2024 MILITARY EMBEDDED SYSTEMS www.militaryembedded.com
FINANCIAL ASSISTANT
SUBSCRIPTION MANAGER subscriptions@opensysmedia.com OFFICE MAILING ADDRESS 3120 W Carefree Highway, Suite 1-640 • Phoenix AZ 85087 • Tel: (480) 967-5581 REPRINTS WRIGHT’S MEDIA REPRINT COORDINATOR Kathy Richey clientsuccess@wrightsmedia.com (281) 419-5725 WWW.OPENSYSMEDIA.COM ADVERTISERS PAGE ADVERTISER/AD
TITLE
9 AirBorn – Power Blade 2000W+ power module
–
Space-tech reading list
By John McHale, Editorial Director John.McHale@opensysmedia.com
One of the reasons I chose a career in aerospace and defense media is my love of space technology. Our June issue is annually one where we run much of our space content, from radiation-hardened electronics trends to satellite technology – with even more coverage of artificial intelligence (AI).
Our content this month dives into how rad-hard requirements are evolving to deal with military threats in space and how the defense world is leveraging commercial solutions for space platforms.
But don’t let your reading stop here: I love diving into articles about space technology, from the search for extraterrestrial life to histories of the space program and, of course, science fiction.
One intriguing example: Dyson spheres. A recent article, “’Dyson spheres’ were theorized as a way to detect alien life. Scientists say they’ve found potential evidence,” by Jacopo Prisco on CNN.com talks about how the radiation emitted by these theoretical spheres could be used to determine the existence of other intelligent life in the galaxy.
Prisco tells us the sphere gets its name from British American physicist Freeman Dyson, who “theorized it would be a shell made up of mirrors or solar panels that completely surrounds a star – harnessing all the energy it produces.”
The CNN article quotes Dyson’s 1960 paper explaining the concept: “’One should expect that, within a few thousand years of its entering the stage of industrial development, any intelligent species should be found occupying an artificial biosphere which completely surrounds its parent star.’” Read the article at https://www.cnn.com/ 2024/06/13/science/dyson-spheres-alien-life-evidence-scn/index.html.
The Dyson sphere concept also reminds me of the science-fiction trilogy “Ringworld,” by Larry Niven. I read the books again recently for the first time since I was a teenager. The story is set centuries in the earth’s future and details how humanity comes across a world that is one huge, rotating ring – nearly 200 million miles in diameter – and built by intelligent life that appears to be long gone. Published in 1970, it still mesmerizes today.
Back to Dyson, or more specifically his son, historian George Dyson, who is quoted in the CNN piece, saying of his Dad: “’Taking advantage of a short attention span and an aversion to bureaucracy, he contributed to five fields of mathematics and eleven fields of physics, as well as to theoretical biology, engineering, operations research, literature, and public affairs. Many of his ideas were controversial, with one of his guiding principles being that ‘It is better to be wrong than to be vague.’”
The younger Dyson is also the author of the book “Project Orion: The True Story of the Atomic Spaceship.” I picked up a copy years ago (Figure 1) and became a fan of George and his father. In the book, George Dyson tells the story of how in the 1950s the U.S. pursued using atomic bombs as the propellant for space travel. The Project Orion team was led by Dyson’s father, Freeman, and Theodore B. Taylor, an American bomb designer. Technically it could have worked, but politics got in the way.
You can read Freeman Dyson's 2020 obituary in Physics World: www.physicsworld.com/a/ freeman-dyson-unorthodox-to-the-end/.


To learn about the heroes who risked all to fly the first U.S. space missions, pick up the book “The Right Stuff,” about the original Mercury 7 astronauts – let’s remember their names: John Glenn, Alan Shepard, Scott Carpenter, Gordon Cooper, Gus Grissom, Wally Schirra, and Deke Slayton – authored by Tom Wolfe. For that matter, read anything by Tom Wolfe, fiction or nonfiction. There was never anyone like him. Yes, they made a movie of the book, but if you’d rather watch the movie than read the book, this particular column might not be for you.
And why explore these theories and technologies? Why go to the moon or Mars? I’ll let Freeman answer that, in a citation from his son’s book: “We shall know what we go to Mars for, only after we get there,” the elder Dyson wrote in May 1958. “You might as well ask Columbus why he wasted his time discovering America when he could have been improving the methods of Spanish sheep-farming. It is lucky that the U.S. government like Queen Isabella is willing to pay for the ships.”
EDITOR’S PERSPECTIVE
www.militaryembedded.com MILITARY EMBEDDED SYSTEMS June 2024 7
Figure 1 | My copy of “Project Orion.”
U.S. military trialing AI tools for more than battlefield advantage
By Lisa Daigle, Assistant Managing Editor

The use of artificial intelligence (AI) in the military is getting a lot of press these days (see pages 20-33 in this issue), and indications are that the buzz around it will only increase.
While AI tools promise to aid deployed troops on the battlefield and in the air, to be sure, they also may find a place on bases, in back-office installations, and performing more mundane – but still critical – military tasks.
The U.S. Department of Defense (DoD) signaled its commitment to AI in all parts of the military in August 2023, when Deputy Defense Secretary Kathleen Hicks established the Task Force Lima within the Chief Digital and AI Office (CDAO) as a vehicle to help the Pentagon assess, synchronize, and employ generative AI, which is broadly associated with large language models that generate (convincing but not always accurate) text, media, and software code based on human prompts. At the time, Hicks set an 18-month deadline by which the team was expected to produce deliverables plus a workable path forward that would guide the DoD’s approach to using AI.
The mission commander of Task Force Lima, U.S. Navy Captain M. Xavier Lugo, was quoted in a CDAO news release at the time of the task force’s launch that the services and commands are actively seeking to leverage the benefits and manage the risks of generative AI capabilities and LLMs across multiple mission areas, including intelligence, operational planning, programmatic and business processes. “By prioritizing efforts, reducing duplication, and providing enabling AI scaffolding, Task Force Lima will be able to shape the effective and responsible implementation of LLMs [large language models] throughout the DoD.”
During the 18-month run time of the task force – as laid out by Deputy Secretary
Hicks at the time of its inception – personnel will test AI on use cases like automating routine tasks and day-to-day activities for DoD personnel. In this way, users can test AI tools on lower-stakes tasks before the DoD goes all in on AI on the battlefield, in the air, and in the cyber domain.
Another AI project is the recent initiative by the Department of the Air Force (DAF), in partnership with the Air Force Research Laboratory (AFRL), which is currently promoting ways to enable Air Force and Space Force members, civilian employees, and contractors to responsibly experiment with generative AI to perform data-heavy yet not-ascritical tasks.
The Air Force has launched NIPRGPT, an experimental bridge to leverage generative AI on the Non-classified Internet Protocol Router Network. According to the June 2024 announcement issued by the Air Force Public Affairs office, NIPRGPT emerged as part of the Dark Saber software platform developed at the AFRL Information Directorate (Rome, New York). Dark Saber is an ecosystem of Air Force and Space Force personnel from across the DAF that brings together innovators and developers and equips them to create next-generation software and operational capabilities deployable to the other users at a rapid pace.
NIPRGPT is a free (to the unit and users) AI chatbot that allows users to have human-like conversations to complete various tasks. The GenAI tool answers user questions and assists with tasks such as correspondence, locating background papers, and coding, all within a secure computing environment.
The experiment, as DAF officials described it in the launch announcement, is a chance to perform lower-stakes (for now) real-world testing, focused on such key metrics as computational efficiency,
resource utilization, and security compliance, enabling users and officers to understand GenAI’s practical applications and challenges and ensure that future implementation is effective and efficient. DAF officials noted in the document that the platform includes opportunities for users to provide feedback, which ultimately will help to develop AI-oriented governing policies and enable informed conversations with vendors as the DAF works to integrate these tools into its operations at higher levels.
In this way, users can test AI tools on lower-stakes tasks before the DoD goes all in on AI on the battlefield, in the air, and in the cyber domain.
“Technology is learned by doing,” stated Chandra Donelson, the DAF’s acting chief data and AI officer, in the announcement. “As our warfighters, who are closest to the problems, are learning the technology, we are leveraging their insights to inform future policy, acquisition, and investment decisions.”
“NIPRGPT is a critical bridge to ensure we get the best tools we have into our team’s hands while larger commercial tools are navigating our intense security parameters and other processes,” AFRL chief information officer Alexis Bonnell noted in the DAF intro to the technology. “Changing how we interact with unstructured knowledge is not instant perfection; we each must learn to use the tools, query, and get the best results. NIPRGPT will allow airmen and Guardians to explore and build skills and familiarity as more powerful tools become available.”
TECHNOLOGY UPDATE
8 June 2024 MILITARY EMBEDDED SYSTEMS www.militaryembedded.com
Power Blade® 2000W+ Power Module
AirBorn’s new VPX Power Supply is a VITA 62, Open VPX compliant, 6U system with models for a 270 VDC input IAW MIL-STD-704. Power Blade is a SOSA aligned, rugged, highly-reliable, conduction-cooled, switch-mode unit built for high-end defense applications. Let’s go to work!
• Auxiliary DC Output: +3.3V/60A
• Efficiency of >94% Typical above 50% Load
• Input-Output Isolation 2100VDC
• Main DC Output: +12V/180A


• Overvoltage, Overload, & Overtemperature Protection
• Programmable Regulated Current Limit
• VITA 46.11 System Management




VPX POWER SUPPLY airborn.com
DEFENSE TECH WIRE
By Dan Taylor, Technology Editor


Bell X-plane progresses under DARPA development program Bell Textron moved into Phase 1B of the U.S. Defense Advanced Research Projects Agency (DARPA) Speed and Runway Independent Technologies (SPRINT) X-plane program, according to a Bell Textron statement. This new phase will focus on the preliminary design of an experimental aircraft aimed at combining high speed with runway independence to advance air mobility platforms. In the initial phase of the program, Bell completed a conceptual design review and is now transitioning to more detailed preliminary design efforts, with the goal of demonstrating new technologies and concepts that could transform future vertical and on-demand mobility.
Bell recently conducted a high-speed vertical takeoff and landing (HSVTOL) during a risk-reduction test. Bell’s HSVTOL technology blends the hovering capability of a helicopter with the speed (400+ knots/460+ mph), range, and survivability of a jet aircraft. Bell reported that the test of the featured advanced folding rotor, integrated propulsion, and flight-control technologies indicated progress in the development of the SPRINT X-plane.
Air-breathing hypersonic aircraft achieves milestones for AFR
Leidos completed the conceptual design review and the system requirements review for the Mayhem air-breathing hypersonic system, a project under the Air Force Research Laboratory (AFRL), according to a Leidos statement. Using the system design agent (SDA) approach, Leidos collaborated with a national team of hypersonic experts from 15 industry and academic entities, including Calspan, Draper, and Kratos Defense & Security Solutions. This collaboration focused on modular architectures and government data rights, aiming to establish a technology framework that supports superior capabilities through a joint effort with the University of Michigan’s aerospace department and the university’s x88 Model-Based Systems Engineering lab.
The AFRL intends to leverage the SDA and Leidos’s capabilities through the Expendable Hypersonic Multi-Mission Platform indefinite delivery/indefinite quantity (ID/IQ) contract to further the development of hypersonic technology.
1st Gray Eagle 25M UAS for Army National Guard to be built by GA-ASI
General Atomics Aeronautical Systems, Inc. (GA-ASI) will provide the first 12 Gray Eagle 25M (GE 25M) uncrewed aerial systems (UAS) to the Army National Guard, the company announced. This initiative, funded by 2023 congressional allocations, aims to equip the Army National Guard with enhanced multi-domain operations (MDO) capabilities, aligning them more closely with active Army divisions.
The GE 25M, an advanced version of the Gray Eagle, includes EagleEye multimode radar and electro-optical/infrared (EO/IR) sensors and supports detailed mission planning, communications, and coordination essential for effective employment in combat scenarios, as well as in domestic missions such as homeland defense and disaster response, GA-ASI stated.
 Figure 1 | Image via Bell Helicopter.
Figure 1 | Image via Bell Helicopter.
NEWS | TRENDS | D o D SPENDS | CONTRACTS | TECHNOLOGY UPDATES
10 June 2024 MILITARY EMBEDDED SYSTEMS www.militaryembedded.com
Figure 2 | Image via General Atomics.

Sea-based space launch infrastructure agreement signed with DIU Launch-infrastructure company The Spaceport Company (TSC) won a contract with the U.S. Defense Innovation Unit (DIU) to deliver cargo and enable greater access to space by leveraging a unique type of sea-based mobile space launch complex. The TSC prototype, according to the company’s announcement, is aimed at demonstrating delivery to a mission-designed orbit and test autonomy-like features of the sea launch vessel.
In Phase 1 of the Novel Responsive Space Delivery (NRSD) project, TSC is tasked with building and demonstrating foundational maritime launch technologies within the next 12 months. Depending on the outcome of the first phase, DIU may award future modular phases to TSC; the phased approach is intended to work with a company as it builds a self-contained, ocean-going space launch complex to quickly deliver satellites to orbit on a regular, commercial basis.
Avionics system from Collins Aerospace gets EASA nod for Europe upgrades
Collins Aerospace (an RTX business) has been granted certification approval from the European Aviation Safety Agency (EASA) for upgrading the avionics in the Cessna Citation CJ1+/2+ aircraft registered in Europe. The light passenger jets – used widely in Europe – are now eligible for fitting with the advanced functionality of the Collins Aerospace Pro Line Fusion integrated avionics system after receiving the EASA certification approval. The company says the upgraded avionics system is modular and intuitive to use, which eases pilot workload and provides realtime data, visual clarity, and predictability.
“Clearing this certification hurdle is a major step forward in providing European CJ customers with a solution that not only enhances their aircraft operations but can also extend the life and functionality of an aircraft,” says Nathan Voight, vice president and general manager, Business and Regional Avionics at Collins Aerospace.
Counter-UAS solutions to be deployed at European military bases
Sentrycs will deploy cyber-based RF counterdrone or counteruncrewed aerial system (UAS) technology at multiple military bases across Europe to enhance base security and address threats from small and commercial drones, the company announced. Its counter-UAS solutions perform passive detection, tracking, and neutralization of drones and can identify drone models, serial numbers, and IDs, distinguishing between friendly and enemy craft, the company states.
The systems will be installed as either standalone units or as part of a comprehensive, multilayered counter-UAS solution to provide protection against various aircraft types, the company says, adding that the deployment aims to mitigate the risks posed by drones used in ISR [intelligence, surveillance, and reconnaissance] missions, which have been a concern in Ukraine and the Middle East.
Hypersonic weapon system capability contract signed between Lockheed Martin, U.S. Army
Lockheed Martin won a contract with the U.S. Army – worth $756 million – to deliver additional capability for the U.S.’s groundbased hypersonic weapon system, the Long Range Hypersonic Weapon (LRHW). Under the terms of the new contract, Lockheed Martin will supply the Army with additional LRHW battery equipment, systems and software engineering support, and logistics solutions. The company announcement notes that Lockheed Martin initially delivered equipment in 2021.
LRHW is the first of a new class of ultrafast and maneuverable long-range hypersonic missiles that can launch from ground mobile platforms and can travel as much as 1,725 miles. The LRHW weapon system is designed to launch the common hypersonic All Up Round (AUR) – provided by the U.S. Navy-managed Conventional Prompt Strike (CPS) program – and includes the Army canister, a battery operations center, and transporter erector launchers.
 Figure 3 | Image courtesy The Spaceport Company.
Figure 3 | Image courtesy The Spaceport Company.
www.militaryembedded.com MILITARY EMBEDDED SYSTEMS June 2024 11
Figure 4 | Artist notional rendering of the Long Range Hypersonic Weapon: Courtesy Lockheed Martin.
Automated network management keeps military SATCOM users connected
By Rick Lober and Dr. Rajeev Gopal
The U.S. Department of Defense (DoD) and the U.S. Space Force (USSF) are starting to implement the government’s Digital Modernization Strategy [published in 2019], including enhanced resilient architectures, as it applies to DoD satellite communications (SATCOM). This SATCOM modernization, including enterprise management and control, will enable access to core enterprise capabilities and increase the flexibility, agility, and resiliency of DoD SATCOM.
U.S. Department of Defense (DoD) satellite communications (SATCOM) users will be able to leverage a hybrid mix of communications technologies, including both commercial and military solutions, under the government’s digital modernization strategy.
These technologies will expand the amount of capacity available across the globe as well as in specific regions, using the global reach of LEO [low-Earth orbit] satellites and the extremely high
capacity available from state-of-the-art GEO [geostationary equatorial orbit] satellites, including the JUPITER 3 (Hughes/EchoStar) satellite.
Commercial SATCOM solutions will help support this modernization effort so that warfighters can stay connected for much-needed mission resilience. Today, losing a signal can end a mission and leave personnel isolated for hours or days. The multitransport communications capabilities available to the DoD – that is, GEO, MEO [medium-Earth orbit], and LEO satellites as well as 5G and other terrestrial technologies – must be orchestrated using dynamic, agile network orchestration that works at the speed of the mission.
Agile, software-defined networking will integrate, synchronize, and orchestrate all these communications networks so they can anticipate and realign assets in near real
SPECIAL REPORT Military satellite communications 12 June 2024 MILITARY EMBEDDED SYSTEMS www.militaryembedded.com
Artist's rendering of geosynchronous satellite--U.S. Space Force Geosynchronous Space Situational Awareness Program. Image courtesy U.S. Space Force.
time. Siloed systems will not provide the optimized flexibility and control that warfighters and commanders require.
Innovation and change
Discussions during the 2024 National Space Symposium addressed an important issue: How the Department of Defense (DoD) can work more deliberately with commercial industry to modernize its capabilities. John F. Plumb, Assistant Secretary of Defense for Space Policy, focused on the DoD’s need to adapt to the rapidly changing, strategic space environment, one which does not favor the slow or those resistant to change. Secretary Plumb highlighted that commercial space integration will be critical to making these changes. Innovation from the commercial space sector has come at amazing speed and scale over the past several years. Commercial providers understand that the DoD wants to harness this speed and industry’s cost-effectiveness.
Modernization strategies
The DoD has worked hard in recent years to modernize its digital capabilities so that the U.S. military can maintain its strength and leadership in today’s constantly evolving, highly competitive environment. As a core part of this effort, DoD leaders have focused on adopting enterprise systems across the department. The 2019 DoD Digital
Modernization Strategy, a central document in this modernization work, specifically mentions one key element regarding enterprise systems: formalize and implement the Enterprise SATCOM Management and Control Reference Architecture.
DoD leadership is initiating steps to modernize DoD SATCOM into a resilient architecture that can support tactically relevant enterprise capabilities. These efforts directly support the U.S. Space Force (USSF) Vision for Satellite Communications. Retired U.S. Air Force Space Command (AFSPC) Commander General John W. “Jay” Raymond issued this vision for SATCOM, also known as the “Fighting SATCOM,” strategy and stated that AFSPC must provide an operationally effective, affordable, resilient, and secure satellite-communications architecture that supports global mission priorities and is adaptable to rapidly changing requirements, technologies, and threats. The strategy asserted that this architecture needs to deliver enterprise SATCOM capabilities to the Commander of the United States Space Command, to support joint warfighters across the full spectrum of conflict, at the speed of relevance, and in contested, degraded, and operationally limited environments.
General Raymond’s Fighting SATCOM vision foresaw the need to fulfill these goals by including a management and control framework to coordinate assets and tasking, flexible terminals that can operate in military platforms/environments, flexible networks to rapidly restore network connections, and a diverse set of space assets to provide path redundancy and operational flexibility. The flexible terminals would need the capability to “roam” across multiple waveforms, bands, and other elements of the architecture including commercial and international partner systems. This architecture can function quickly based on the use of open standards and modular satellite architectures to enable the network to deliver the most powerful benefits to the user, including seamless information-sharing across systems and users.
This approach also supports the integration of commercial off-the-shelf (COTS) technology that can lower the cost of building and maintaining the network, enabling faster software and hardware upgrades to minimize obsolescence and leverage the latest security protocols. All of these tools would help the SATCOM architecture adapt to the operational environment as it evolves, without a soldier’s manual intervention. In fact, using this paradigm, the DoD can enhance these technologies over time and leverage leading-edge technologies much more quickly – wireless LTE, 5G, cloud computing, artificial intelligence (AI), and machine learning (ML).
www.militaryembedded.com MILITARY EMBEDDED SYSTEMS June 2024 13
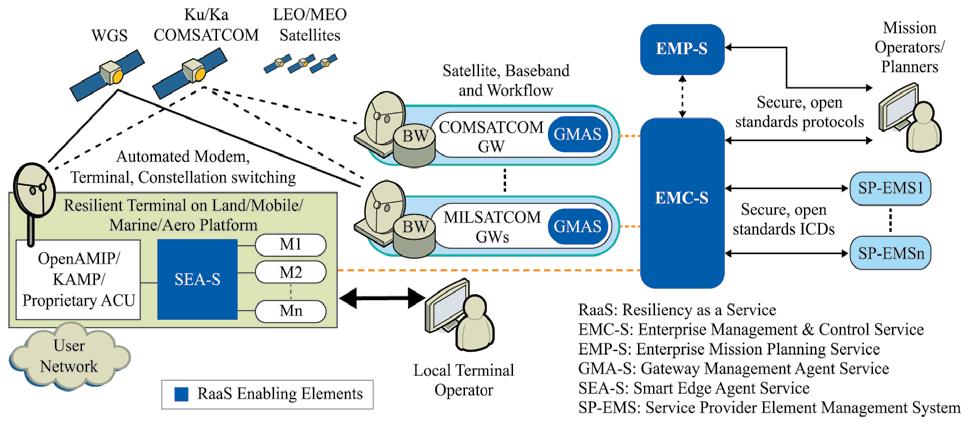
Figure 1 | Commercial providers worked alongside the key elements of the enterprise satellite communications network management system.
DoD collaborates with industry Commercial providers have worked alongside the DoD to formulate the key elements of this enterprise SATCOM network management system. In 2017, the U.S. Air Force Space and Missile Systems Center (SMC) launched the COMSATCOM Pilot Program, where several commercial providers helped assess the ideal hybrid SATCOM architecture and how diverse systems could work together to enable more flexible and resilient military satellite communications. (Figure 1.)
This pilot program encompassed three phases. In the first phase, a SATCOM strategy was recommended that supports interoperability for wideband applications to enhance communications infrastructure and reduce acquisition and operations costs. The second phase (2018) focused on how this interoperable model could be implemented by creating a flexible modem interface standard for demonstration. To support this phase, Hughes produced new terminal management agent (TMA) software implementing the USAF flexible modem interface (FMI) standard so DoD and industry could demonstrate and evaluate it.
Work on the COMSATCOM pilot program continued in 2019 with Hughes and NASA together testing the TMA/FMI technology in a demonstration with the International Space Station (ISS), autonomously switching a communications signal from the FMIoutfitted ground terminal between different modems aboard the ISS. Also demonstrated: The TMA/FMI and enterprise management and control (EMC) technologies in 2020 with full primary, alternate, continency, and emergency (PACE) planning and situational awareness using a software-defined HM400 modem and a GetSat Ku-band aero antenna with a video sensor and a Comtech DMD-2050E. This demonstration was associated with a U.S. Space Force (USSF) Space and Missile Systems Center (SMC) contract focused on producing an EMC architecture for mission planning with integrated situational awareness and an FMI-enabled aero terminal prototype for satellite communications. The pilot program continued with Phase 3 to study order-ofmagnitude improvements in SATCOM capability, affordability, and resiliency.
Work to create the EMC infrastructure continued in 2022, when the DoD CIO Office issued the Enterprise SATCOM Management and Control (ESMC) Implementation Plan. This ESMC plan has provided guidelines for EMC to help with resiliency and interoperability objectives across commercial and DoD satellite communication systems, and the foundational capabilities necessary for the ongoing future SATCOM Force Design, including increased reliance on commercial SATCOM. To realize the plan’s core capabilities, several key architecture components need to mature and then become standardized by the MILSATCOM and COMSATCOM communities to offer true “resiliency-as-a-service” to the DoD. Standardization of nomenclature, functional partitioning, and interface definitions is necessary to meet the core capability objectives.
Innovation on AI and software-defined networks
The ESMC-related developments by USSF Space Systems Command (SSC) and industry contractors have relied on available commercial industry innovation that could be leveraged as quickly as possible. The new technology has included artificial intelligence (AI) and software-defined networks (SDNs), two elements addressed in the 2019 DoD Digital Modernization Strategy. This strategy stated that the military competitor who can harness and exploit AI’s potential the fastest will accrue a significant military advantage.
For the DoD, a software-defined network would enable a network administrator to shape traffic from a centralized control console without having to touch individual switches and deliver services to wherever they are needed in the network, without regard to what specific devices a server or other hardware components are connected. The key technologies for SDN implementation are functional separation, network virtualization, and automation through programmability.
One example of commercial innovation is the smart network edge (SNE) software created by Hughes and derived from the TMA capability initially produced in 2018. This standards-based capability leverages the intelligence of AI to power autonomous satellite terminal control across diverse modems, services, satellites, and service providers. The software uses situational data – including the operational environment, mission plans, potential satellite access issues, and mission priority based on available services –to make autonomous decisions about its host terminal’s use of diverse resources.
SNE, working as a terminal agent, uses policies from EMC and overrides stovepiped systems to enable user access to diverse platforms from a single terminal without depending on single-threaded satellite systems which are vulnerable to interference due to many factors, including malicious actors, poor antenna angles, misaligned directional pointing, and more. This terminal agent also makes planning decisions based on mission priority; adverse events such as jamming, cyberattacks, and network problems; hardware failures; and availability or suitability of multi-orbit capacity at the tactical site. (Figure 2.)
Using this tool, soldiers would no longer need to change communications elements manually when original operational configurations fail and would enjoy continuous connectivity to meet mission requirements. On a satellite terminal, if a degraded or disrupted transmission occurs for any reason, automated terminal management and control will use alternate networks to “self-heal” connections. Continuous connectivity is key: According to a statement made in early 2024 by Clare Hopper, director of the USSF Commercial Satellite Communications Office, today’s military needs reliable, resilient, and secure communications as they are essential for coordination across vast distances.
ESMC is a key enabler for SATCOM flexibility and interoperability across diverse SATCOM technologies, orbits, and domains. The architecture, combined with automation at the edge, automated
SPECIAL REPORT Military satellite communications 14 June 2024 MILITARY EMBEDDED SYSTEMS www.militaryembedded.com
planning, and resource allocation with intelligent network management, can provide this flexibility across military and commercial GEO/MEO/LEO SATCOM, secure 5G, and other terrestrial transport capabilities. These multiple transports ensure connectivity in all environments. With automated orchestration, this framework can leverage the diversity and redundancy needed for enhanced resiliency. Intelligent ESMC must provide access to multiple transport paths as no one technology or service provider can meet all DoD requirements. When the ESMC leverages AI and automation to manage these paths, it can very quickly determine the best transport for the specific time and use case.
ESMC and the automated architecture can support automated PACE planning and dynamic resource allocation for realigning assets in near-real time, speed that is not available today. The time can be reduced from hours/days down to seconds, critical in decision-making and overall information dominance.
Automated planning: A planner provides input for creating a plan for these terminals. After approval, the plan is activated and automatically distributed to the terminals and peer-management system, which are part of the mission. Historically, this step has been done with time-consuming satellite access request (SAR) and gateway access request (GAR) manual processes. The network management system (NMS) enhances the request process with automatic generation of plans by using a rules-based engine and addressing mission input from the operator. NMS includes full PACE facets in these plans so that SNE can activate and use various components to address specific adversities such as cyberattacks, RF jamming, or equipment failure. In certain situations, it may be better for the NMS to regenerate these plans as part of dynamic planning and resource allocation.
Management interfaces: NMS and SNE support FTI [fault-tolerant interface], being standardized with IEEE and the U.S. DoD, for automated distribution of plans and terminal configuration to terminals and collecting situational awareness data to include network, cyber, RF, and equipment status and performance. NMS also supports the service provider
interface to provide bulk resource-configuration information to a peer-management system (such as gateway element management system) and collect bulk situationalawareness information from the peer for multiple terminals under their scope.
Ensuring military SATCOM users stay connected
The DoD’s Enterprise SATCOM Management and Control Implementation Plan spells out how the DoD plans to achieve DoD SATCOM modernization through development of and access to core enterprise capabilities. Once employed, these capabilities will increase the flexibility, agility, and resiliency of DoD SATCOM, while leveraging the full use of a hybrid, heterogeneous enterprise that uses the best mix of commercial and military solutions. Such a plan can become a reality by integrating commercial industry innovation quickly: Automation will provide dynamic PACE planning by leveraging an AI-based rules-based engine, delivering real-time monitoring of transport links and enabling one or more active transports based on the platform and its deployment of the radios and terminal. U.S and global national security require near-real time situational awareness and communications for mission success in contested environments. MES

Rick Lober is Vice President and General Manager of the Defense and Government Systems Division (DGSD) at Hughes Network Systems. He has more than 25 years of experience with COTS and full military communications and intelligence programs. He earned both a Bachelor and Master of Science Degree in electrical engineering from the University of Illinois, Urbana, and is a member of Eta Kappa Nu, Tau Beta Pi, TEC, IEEE, AFCEA, AUSA, AAAA, AUVSI, and the Society of Satellite Professionals International (SSPI). Lober holds a patent on cellular communications for emergency response.

Dr. Rajeev Gopal is Vice President, Advanced Systems at Hughes Defense and Government Systems. In more than 25 years at Hughes, Dr. Gopal has held a variety of leadership roles in satellite network systems engineering and software development; most recently, he has focused on AI/ML, software-defined networking, 5G, and enterprise management architectures. Prior to joining Hughes, Dr. Gopal led automation projects for clinical and cancer research and development at CTIS. Dr. Gopal earned a Ph.D. in computer science from Vanderbilt University (Nashville, Tennessee) and a bachelor of engineering degree in electrical engineering from the Birla Institute of Technology & Science (BITS) in Pilani, India.
Hughes Network Systems • https://www.hughes.com/
www.militaryembedded.com MILITARY EMBEDDED SYSTEMS June 2024 15
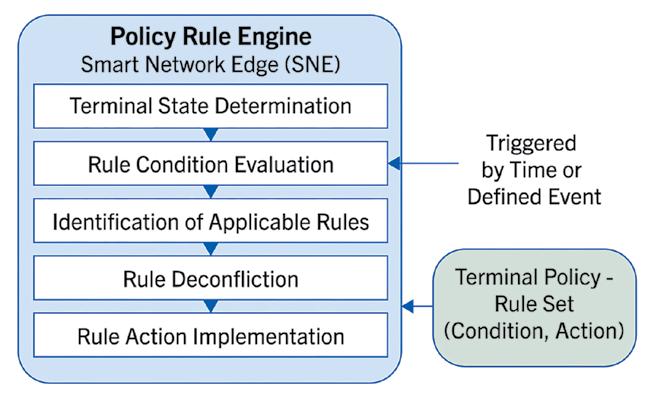
Figure 2 | A policy rule engine helps users and systems make planning decisions.

Navigating the new frontier: rapid deployment and robust testing of satellite systems
By Kyle MacCoy
The space industry is undergoing a significant transformation, with several trends shaping its future. The small-satellite revolution – due to the increased demand for satellites to perform unique missions and the focus on smaller, less expensive satellite constellations – is driving an increased focus on cost efficiency, reliable testing, rapid deployment, and scalability.
The space industry’s shift toward small satellites, innovative data link systems, and modern testing approaches requires engineers and systems to adapt to meet the demands of rapid deployment and evolving technology in order to ensure reliable communication in everexpanding space endeavors. Data link system testing and emulation is critical to ensuring reliable data transfer once deployed to ensure safe and secure communication for satellite-to-satellite and satellite-to-ground systems. Use of complex technologies such as
electronically scanned array (ESA) antennas and software-defined radio (SDR) back ends drive modularity and adaptability. Because traditional, monument-type test systems are not flexible or scalable enough to tackle these challenges, multifunctional instruments and platform-based test solutions offer a radical new method to futureproof systems for the coming satellite deployment wave.
Orbital solutions to terrestrial challenges
The space industry is currently undergoing a remarkable metamorphosis characterized by several interconnected trends. First, there has been a rapid surge in the number of companies and governmental entities venturing into outer space. These stakeholders are actively participating in satellite deployments, which are becoming more common. The driving force behind this growth lies in the burgeoning demand for space-based applications that serve critical national interests: In the defense and national-security arenas, satellites are being deployed to provide surveillance, reconnaissance, and
SPECIAL REPORT Military satellite communications 16 June 2024 MILITARY EMBEDDED SYSTEMS www.militaryembedded.com
Engineers and space agencies must address issues related to launch coordination, orbital management, and efficient deployment strategies, all of which rely on safe, secure data transmittal and communication.
communications capabilities crucial for safeguarding borders, monitoring potential threats, and ensuring strategic preparedness.
Broadband communication concerns are being tackled through the proliferation of internet services based on satellite communication. Satellites facilitate global connectivity, bridging gaps in remote theaters for rapid, real-time situational awareness. Even climate research, which can affect operational environment and resource allocation in new and expanding theaters of interest, relies heavily on satellite data. These orbiting observatories help scientists track weather patterns, study climate change, and assess environmental conditions globally.
The Space Development Agency predicted several years ago that as many as 50,000 satellites will circle the globe within the next decade. This ambitious endeavor encompasses both low-Earth orbit (LEO) and geosynchronous positions. The rapid deployment of such a substantial number of satellites presents logistical challenges: Engineers and space agencies must address issues related to launch coordination, orbital management, and efficient deployment strategies, all of which rely on safe, secure data transmittal and communication.
The space industry’s market value is undergoing notable expansion, with one
estimate noting that it reached approximately $384 billion globally in 2022. This economic growth reflects the increasing importance of satellite technology and its multifaceted applications. The confluence of increased participation, satellite deployment, and market expansion underscores the urgency of addressing communications infrastructure challenges. As humans venture further into space, ensuring reliable data links between satellites and ground stations becomes paramount.
Importance of SATCOM data link and telemetry test
The influx of new space companies and the desire to deploy emerging technologies have created a critical need for robust testing of data link systems. These systems facilitate the transmission of data to and from Earth, and between satellites themselves, essential for the function of both individual satellites as well as extensive constellations. Engineers must ensure the reliability of communication links, whether it involves a satellite communicating with one or multiple ground stations in configurations such as two-way transmission, receive links, or “bent-pipe” setups in which the data transmitted to the satellite is sent right back down again, with the only processing performed being retransmitting of the signals.
The small-satellite constellations being deployed to facilitate new applications can range from one craft to several thousand, each satellite rapidly orbiting the earth. The shifting nature of deployments presents a challenge for communications and connectivity for both inter-satellite and ground-station data links. In response, cuttingedge communications systems have been developed using modern ESA antennas that can rapidly shift one or more beams without any mechanical movement. This setup enables the telemetry, tracking, and control (TT&C) of multiple satellites at once while in the field of view of the array.
More importantly, these ESA arrays are inherently modular and scalable, which means that ground terminals and payloads can be optimized for specific applications and missions. These data links are further supported via software-defined radio (SDR) backends, which enable adaptive and reconfigurable data links such as the protocols prescribed by the Consultative Committee for Space Data Systems (CCSDS), a multinational forum convened for the development of communications and data systems standards for spaceflight.
Testing the systems
Traditional testing of these systems typically requires a substantial setup involving a large rack of equipment. This includes vector network analyzers (VNAs), vector signal transceivers (VSTs), signal generators, and spectrum analyzers, along with specialized hardware like telemetry receivers or emulators, often necessitating a golden or already calibrated device under test (DUT). The assembly and maintenance of these racks is not only costly but also cumbersome, involving multiple equipment providers and extensive third-party software for integration. This “old-school” approach results in an inefficient and unscalable system, ill-suited to the accelerating pace of satellite production and the need for rapid deployment and upgrades of ground systems.
Further, each phase of the development cycle – from R&D and prototyping to component function and parametric testing, all the way through to final system validation –requires unique protocols and test capabilities. (Figure 1.)
The modern approach to satellite testing emphasizes the integration of functions and adaptability across the satellite’s lifecycle. Instruments that combine these capabilities facilitate a more streamlined process, allowing engineers to move swiftly and efficiently from concept to orbit. These instruments are scalable and upgradable, aligning with the fast-paced evolution of production rates and technological requirements with our burdensome upgrade and maintenance costs.
www.militaryembedded.com MILITARY EMBEDDED SYSTEMS June 2024 17
Solutions for SATCOM data link and telemetry validation
The best solution for SATCOM and telemetry systems validation consists of commercial off-the-shelf (COTS) modular hardware and flexible software tools to address RF signal fidelity, system-level validation, and digital system test requirements. Solutions built on modular test platforms such as PXIe can be customized and modified to meet specific I/O performance requirements. Instruments such as a VST, which combines both a vector signal generator (VSG) and a vector signal analyzer (VSA) can transmit and receive TT&C and SATCOM data link signals performing key signal fidelity measurements such as modulation accuracy, transmit power, and more.
A VST can be augmented with additional instruments such as a high-speed serial coprocessor with full-rate streaming to and from an open FPGA capable of hosting real-time, inline signal processing and channel models. With a coprocessor configuration, a VST is capable of being transformed into an RF channel emulator, unlocking the ability to perform full system-level validation. (Figure 2.)
Digital system test can be accomplished with the use of flexible I/O modules and FPGAs [field-programmable gate arrays], as well as with a digital front-end configuration. Combining a large user-programmable FPGA with a serial or parallel digital I/O board to meet the system interfacing and IP protocol requirements of satellite payload subsystems allows unique test setups and protocols to be achieved with minimal

investment in new hardware. Engineers can import custom digital protocols to emulate digital interfaces without using custom hardware.
The coming horizon of testing and deployment
As the space sector continues to expand, the importance of adopting these integrated and efficient testing solutions will also increase. With testing, users can ensure that new technologies can be deployed effectively, manage the increasing congestion in space, and maintain the integrity of essential satellite functions. This shift is not merely a response to current challenges but a proactive approach. MES
Kyle MacCoy has been in the aerospace, defense, and government sector for more than 15 years. He has worked as an engineer supporting the U.S. Navy and the Marine Corps on multiple vertical-lift platforms, in the commercial sector producing airliner hardware, and in the startup world to produce and launch space vehicles. Now with NI (part of Emerson), Kyle is fulfilling the role of solution marketer focusing on the SLV [satellite launch vehicle] applications in CNS [celestial navigation systems] and radar/electronic warfare. Readers may reach the author at kyle.maccoy@ni.com.
NI (now part of Emerson) https://www.ni.com/en.html
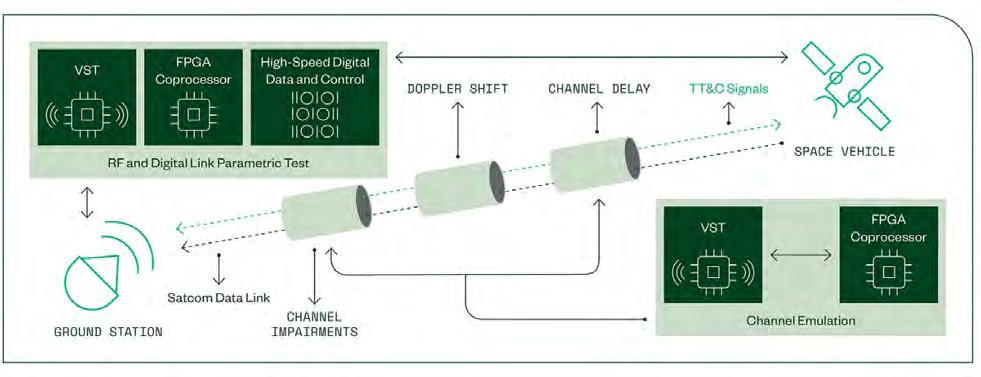 Figure 2 | SATCOM telemetry validation with COTS NI PXIe modules.
Figure 2 | SATCOM telemetry validation with COTS NI PXIe modules.
SPECIAL REPORT Military satellite communications 18 June 2024 MILITARY EMBEDDED SYSTEMS www.militaryembedded.com
Figure 1 | An engineer is shown preparing for satellite test in lab.
Testing & Simulation Standardization Fall Behind UAS Innovation
Earle Foster, Senior VP Sales, Sealevel Systems, Inc.

Unmanned Aerial Systems (UAS) are among the fastest innovating product segments of the worldwide economy. As these UAS innovations and new technologies are developed, rigorous testing is required, especially when the application relates to the control systems. Currently, testing UAS systems is time –and resource – consuming.
For all UAS, and unmanned systems in general, safety is the number one priority for developers and manufacturers. That said, most commercial UAS platforms and payloads are too small to carry redundant hardware components like an extra motor or backup actuators. Therefore, the safety redundancy in commercial UAS platforms tends to come in the form of software redundancies in the control system. As a result, the control systems of UAS platforms tend to be the most complex component, responsible for the operation of the vehicle under nominal conditions, as well as making safety decisions under failure conditions.
Current UAS Testing Procedures
Faults or failure conditions in a UAS are quite rare under normal operation. Therefore, testing requires running massive sequences of repeated experiments to ensure that the UAS’s control system can both detect and handle unexpected part or component failures or faults. Further, the certification and licensing process for commercial UAS in the US is, to put mildly, unclear. There is no widely recognized safety assessment standard for UAS platforms. Rather, several stopgaps have been cobbled together from various outlying standards for passenger aircraft – experimental airworthiness certificates for example.
As such, the current state of testing for commercial UAS platforms runs a wide spectrum, from sequencing the unmanned vehicle through the same test regimens required of passenger aircraft to running a test regimen more akin to that of hobbylevel radio-controlled planes.
Challenges with Experimental Testing for UAS
As UAS platforms continue to increase in complexity, experimental testing is becoming more and more of a hindrance to manufacturers. The testing methods are high-cost, labor and time-intensive, and inefficient. The increasing complexity of control systems has made the experimental testing methods increasingly inefficient, in terms of revealing potential safety issues and covering the testing cases.
As the disadvantages of utilizing purely experimental testing methods are becoming more apparent, new simulation and test methods (real-time simulation methods, high-precision modeling, system identification methods, and model-based safety assessment methods) are becoming the trend for both manned and unmanned vehicles. Experimental testing cannot – and should not – be completely abandoned, but simulation testing techniques are taking on more and more safety testing and assessment tasks.
Capitalizing on Existing Aerospace Test Capabilities
Testing plans should not only rely on hardware, but there is room for expanding the role of software and simulation-based testing. These testing procedures not only ensure safety and optimal performance, but they are also intended to help reduce costs associated with damaged equipment.
Sealevel’s team has worked extensively with a developer of GNSS (Global Navigation Satellite System) and RF simulation systems. These test systems for flight software provide extensive, controlled testing prior to field testing. As part of the serial expansion, they rely on Sealevel USB to serial products.
As the need for established test systems and protocols becomes an increasing priority, the hope is that the creation of such policies and protocols will catch up to the innovations in UAS design and manufacturing.
For more information about our experience, visit sealevel.com.

ADVERTORIAL EXECUTIVE SPEAKOUT
Sealevel Systems, Inc. | www.sealevel.com
MIL TECH TRENDS
Enabling artificial intelligence in military systems

AI now playing a big role on the battlefield
By Dan Taylor
The prospect of artificial intelligence (AI) promises to remove soldiers from the battlefield, increase the effectiveness of platforms and weapons, and enable better decision-making, but for years these benefits have been theoretical rather than practical.
In 2024 there are signs that artificial intelligence (AI) is finally being used on the battlefield after years of planning, and the U.S. military and industry are vying to get in on the AI push. Recent military operations in current hot spots including Ukraine and Gaza show just how AI is being used in battlefield contexts and how global militaries might start using this technology.
For example, a Ukrainian startup called Swarmer conducted a field test near Kyiv during which personnel deployed a swarm of drones that were coordinated through AI to perform a specific mission:
The X-62 Variable In-Flight Simulator Test Aircraft (VISTA) flies over Edwards Air Force Base, California. In April 2024, the VISTA aircraft flew in the first-ever in-air tests of artificial intelligence (AI) algorithms piloting an F-16 jet autonomously as part of the Defense Advanced Research Projects Agency (DARPA) Air Combat Evolution (ACE) program. Air Force photo by Kyle Brasier.
20 June 2024 MILITARY EMBEDDED SYSTEMS www.militaryembedded.com

identifying and destroying hidden targets without human pilot intervention for navigation, according to a Politico report by Gian Volpicelli, Veronika Melkozerova, and Laura Kayali, titled “Our Oppenheimer moment”: “In Ukraine, the robot wars have already begun.” The process began with reconnaissance drones identifying the best flight paths autonomously, followed by bombers that executed the attack. A final pass using an uncrewed aerial system (UAS) confirmed the destruction of the targets.
In another example, a Washington Post article titled “Israel offers a glimpse into the terrifying world of military AI” by Ishaan Tahroor reports that Israel is using
an AI-based program named “Lavender”: The system reportedly marks individuals Israel has associated with Hamas for airstrikes. One report indicates Israel has used the tool to identify as many as 37,000 people as targets, with almost no human oversight.
The defense industry has explored a wide range of uses for AI, from crunching data to coordinating drones.
AI analytics is one area that has seen a boom in activity. As data needs grow, so does the demand for technology that can sort through this data and provide actionable insights. The U.S. military has explored the type of AI analytics technology that can quickly sort through data collected on the battlefield to provide insights to a combatant commander.
Drone swarms have been another focus of AI tech. The U.S. Department of Defense (DoD) announced the Replicator Initiative last year, which aims to remove barriers and quickly field innovative capabilities to warfighters to handle specific operational challenges, and AI-powered drone swarms have been a big part of that effort.
AI may be important not just for executing swarm operations, but also for defending against them in the field. AI will be necessary to coordinate “large numbers of autonomous agents in dynamic and contested environments,” says Timothy Stewart, director of business development at Aitech (Chatsworth, California). The company is working on AI algorithms and machine-learning techniques to help military forces detect, analyze, and respond to swarm threats.
“These types of attacks pose one of the more significant risks to ground vehicles and in-field operations, where vehicles and personnel are left exposed and less able to maneuver across certain terrains,” Stewart says.
In the future, uncrewed systems powered by AI will be the norm, which will fundamentally change battlefield strategies, he argues.
“Robotics enhance force protection by reducing the reliance on human operators in high-risk environments, mitigating potential casualties, and preserving operational continuity in the face of adversarial swarm attacks,” Stewart says. “These platforms can operate autonomously or collaboratively with crewed assets, forming a networked ecosystem capable of adapting and responding to swarms in real time.”
In an experiment involving manned aircraft, the U.S. Defense Advanced Research Projects Agency (DARPA) conducted the first-ever in-air tests of AI algorithms piloting an F-16 fighter jet autonomously in April 2024, after years of preliminaries. The AI did more than pilot the plane – it engaged in direct combat scenarios against a humanpiloted counterpart. The test was part of DARPA’s Air Combat Evolution (ACE) program, which is dedicated to integrating AI into tactical aviation and establishing a framework for ethical and trusted human-machine teaming.
AI also enables faster deployment of capabilities to the field. Doug Beck, director of the Defense Innovation Unit, said at the XPONENTIAL 2024 exhibition in April 2024 that the DoD is using AI and machine learning (ML) to speed up software improvements to uncrewed vehicles across the services from a matter of months to a few days.
Officials ask industry to tackle AI challenges
Officials are openly asking the industry to focus more on AI in their development efforts. Melissa Johnson, the acquisition executive at U.S. Special Operations Command (USSOCOM, headquartered in Tampa, Florida), told SOF Week attendees in Tampa last month that AI is a growing part of the organization, saying that the industry needs to develop AI-powered solutions to solve today’s difficult data challenges.
www.militaryembedded.com MILITARY EMBEDDED SYSTEMS June 2024 21
“We need to be thinking about data governance, we need to be thinking about how that data is connected – all those things that are not exactly exciting to care about, but are vitally important to making sure that we get a capability downrange,” Johnson told the assembled audience at SOF Week.
AI can help with the integration of systems, which is a major focus of USSOCOM, Johnson said, adding that collaborative and autonomous systems would also be key to the service going forward.
“Being able to use much smaller things and getting them into a contested environment … and to be able to be survivable and lethal and provide that awareness is where we’re taking this,” she said. “And it’s not just one component. It’s not just one domain. But it’s crossing those domains.
“We are definitely investing in artificial intelligence and using it in ways for integrated deterrence, but also we tend to use it in ways for crisis response and counterterrorism,” she added.
AI is “really the name of the game,” she stated.
USSOCOM Commander Bryan P. Fenton also acknowledged AI’s growing influence in his keynote at SOF Week, urging industry to take the challenge seriously.
“Whatever you knew about artificial intelligence six months ago, forget about it,” stated USSOCOM Commander Bryan P. Fenton in his SOF Week address. “It’s just moving at such a rate of speed ... It’s pretty frightening.” (Figure 1.)
Practical ways AI can help
The services are proactive about leveraging AI across multiple domains and exploring new companies and new commercial AI solutions. For example, at many defense trade shows more and more vendors are showcasing products and services powered by AI.
At SOF Week, engineers at Primer AI showcased a tool that takes a massive amount of publicly available data from sources around the web and combines it with private data collected by an organization’s own internal network to create comprehensive situational awareness. At another SOF Week booth, Exovera demonstrated its AI analytical platform intended to help identify patterns to unlock a “wealth of new intelligence,” as described by Exovera CEO Bob Sogegian.
Defense engineering firm BlueHalo showcased an autonomous maritime vehicle under development with Kraken using AI/ML technology. At XPONENTIAL 2024,


BlueHalo was also on hand to demonstrate its AI/ML-powered swarming UAS, which essentially act as a truck or vehicle for any sensor an operator wants to put on them. (Figure 2.)
Speeding decision-making
AI enables the collection and analysis of large amounts of data to help soldiers make faster (and better) tactical decisions, says Shan Morgan, Vice President of Sales at Elma Electronic (Fremont, California).
“Our products are used extensively in support of [applications] that involve intensive data acquisition and processing, often requiring the use of AI in decision-making,” says Ram Rajan, Vice President of Engineering at Elma Electronic. Elma is focused on designing to the points laid out in the Sensor Open Systems Architecture (SOSA) Technical Standard to develop integrated, AI-ready platforms to support C5ISR [command, control, communications, computers, cyber, intelligence, surveillance, and reconnaissance], electronic warfare (EW), and electro-optical/ infrared (EO/IR) applications in DoD programs. (Figure 3.)
Practical applications for AI include realtime object tracking for soldiers with advanced cameras and night vision, training troops in battle scenarios,
Figure 2 | BlueHalo’s HaloSwarm, an autonomous uncrewed vehicle with AI/ML swarm logic capabilities, showcased at XPONENTIAL 2024. Image courtesy MES.
MIL TECH TRENDS Enabling artificial intelligence in military systems 22 June 2024 MILITARY EMBEDDED SYSTEMS www.militaryembedded.com
Figure 1 | USSOCOM Commander Bryan P. Fenton speaks to attendees at SOF Week in May 2024. Image courtesy MES.

seamless language translation, wearable tech with health monitoring, and AI-driven robots and UASs, Morgan says.
AI and lethal force
Despite the benefits of AI there are those who are concerned about ethics –particularly the idea of using AI for lethal force. That consideration doesn’t just apply for armed drones – even dataanalytics platforms that use AI could have their conclusions used to make lethal force decisions. Israel’s Lavender AI targeting technology has been criticized for not having enough human oversight, raising the concern that innocent civilians could be identified as targets by unchecked AI software.
All defense companies developing some form of AI will argue that their system only enhances human decision-making rather than replacing it. But it might be wise to have guardrails in place, says Chris Ciufo, chief technology officer at General Micro Systems (Rancho Cucamonga, California).
Ciufo says he believes there are a few potential pitfalls with AI. One point he makes is that soldiers may become overly dependent on AI, leaning on it more and more for decisions and losing some of their own critical-thinking skills in the process. Another issue with leaning on AI is outsourcing life-or-death decisions to computers, and the industry should be careful about how quickly it hands that power to AI – or perhaps not do it at all.
“If you are in a battle situation and AI is presenting you a literal piece of the battlefield, if it’s identifying threats that it sees and if it’s predicting – based upon history either from the current battle
or hundreds of previous battles fought across the world – that enemies are likely to come through that valley over there ... you might say, ‘all right, let’s just blow it up,’” he says. “Or the computer will automatically blow it up.”
In battlefield situations like this, AI is focused on finding patterns. It may consider irrelevant data like the color of a building or whether a car is parked out front and use it as an indication it belongs to a terrorist group, Ciufo argues. As a
result, AI could put innocent people at risk by having them erroneously tagged by unchecked AI systems as targets.
AI can help with efficiency on the battlefield, but if militaries can’t resist the urge to lean on it for decisions, it could lead to unpleasant consequences in the future.
“Just because we can, should we? Where do we stop? Can you trust the AI, and how do you verify?” Ciufo asks. MES

Reliability… the Only Option
NASA first selected our chip resistors for a mission to Jupiter and Saturn that launched in 19 7 7 and is still operating in interstellar space. Our chip resistors continue to be selected for high reliabilit y applications on Ear th and in space On Ear th, our resistors are selected for mission critical applications in militar y weapon and defense systems In space, our chips are found in weather and communications satellites and on missions to Mars, Jupiter, and Pluto
Mission Critical? Choose State of the Ar t resistors.
St a te o f the A r t, Inc.
R E SIS TI V E P RODUC T S Made
 Figure 3 | Elma Electronic’s JetSys-5320, its NVIDIA Jetson TX2- based rugged AI-enabled computer.
Figure 3 | Elma Electronic’s JetSys-5320, its NVIDIA Jetson TX2- based rugged AI-enabled computer.
he USA .
www.militaryembedded.com MILITARY EMBEDDED SYSTEMS June 2024 23
MIL TECH TRENDS
Enabling artificial intelligence in military systems

The evolution of DoD policy and the role of AI in modern warfare
By Drew Thompson
Integrating artificial intelligence (AI) into military applications presents complex and multifaceted challenges, encompassing technological advancements, policy frameworks, strategic considerations, and ethical concerns. To keep pace with the rapid speed with which AI technology continues to improve and evolve, the U.S. Department of Defense (DoD) has established a unified adoption strategy aimed at improving the organizational environment within which DoD leaders and warfighters will be able to make rapid, well-informed decisions by expertly leveraging high-quality data, advanced analytics, and AI for enduring decision advantage.
24 June 2024 MILITARY EMBEDDED SYSTEMS www.militaryembedded.com
The use of AI in military and battlefield applications is a relatively new phenomenon, but limited use of the technology is already benefitting warfighters. In this nascent form, AI is largely being used in information gathering and processing capacities. For example, AI is much more efficient than humans at sifting through large amounts of data and images or monitoring feeds for meaningful information.
One of the more significant current applications is threat identification and recognition, especially in air combat. This can be done through locating unique radio or radar signals that are emitted by individual aircraft or aircraft types. In the past, this was an enormous undertaking, requiring a wide variety of sensors operating and recording information from many different sources and frequency ranges. This sensor data was then analyzed by specialists to locate and identify various signals associated with individual aircraft or aircraft types. Today, the identification work conducted by many individuals, over dozens or hundreds of hours, can be done in milliseconds to seconds by AI systems.
The hardware powering military AI
There are several different hardware components used in military AI applications.
High-performance computing (HPC): The majority of military AI applications require powerful computing resources to process large volumes of data and perform complex calculations in real time. HPC systems, including but certainly not limited to supercomputers and clusters of high-end servers, provide the necessary computational power.
There has been a tremendous amount of discussion and scholarship around the location of these HPC resources. There is one school of thought that argues the HPC components are more appropriately located in a central area, far away from a battlefield. The alternative view is that all of the computation should be pushed to the edge.
Performing most of the intensive computation in a central location allows a much larger amount of, and a much larger range
of types of, equipment and components. However, this makes the networks or “pipes” a much more crucial component of AI applications.
Alternatively, field-deployed edge hardware is more size-constrained than externally located hardware. Edge hardware is limited by size, while external hardware is limited by the security and strength of the pipes.
Graphics processing units (GPUs): GPUs are not strictly necessary but are often used for accelerating AI computations, particularly when utilizing machine learning and deep learning algorithms. GPUs are a major benefit in applications that rely on parallel processing. Military AI systems often utilize GPUs for tasks such as image recognition, object detection, and autonomous navigation.
Software for AI algorithms and UI
AI algorithms and models: Military AI applications rely on advanced algorithms and models to perform tasks like image recognition, natural language processing, decision making, and predictive analytics.
Simulation/training software with large data sets: To train AI systems and simulate various scenarios, specialized software platforms are used, which enable realistic simulations of military environments, tactics, and equipment. To best train military AI, these simulations require applying massive data sets – the more data, the better.
Integration software: Military AI systems need to integrate with the existing infrastructure and interact with other systems seamlessly and intuitively. Soldiers in the field cannot be expected to navigate challenging user interfaces within software platforms.

• Large range of Ethernet Switches
• 1U enclosure, 3U & 6U VPX
• Managed Layer 2+/3 switches
• 1/10/25/40/100 Gigabit Ethernet
• Aligned with the SOSA™ Technical Standard
• Air-cooled, conduction-cooled, AFT grades


www.elma.com www.interfaceconcept.com Contact our North American sales and support provider: sales@elma.com • 510-656-3400 Elevating your embedded experience IC-PUB MES1-052024-exe.indd 1 06/05/2024 18:01 www.militaryembedded.com MILITARY EMBEDDED SYSTEMS June 2024 25
U.S. Department of Defense AI policy
The U.S. Department of Defense (DoD) has been strategically incorporating AI and machine-learning (ML) technologies through various policies and strategic documents over the past few years. The DoD’s published “2018 DoD Artificial Intelligence Strategy” laid the groundwork for developing a centralized infrastructure, integrating new technology, and achieving international leadership in AI ethics and safety. Subsequent strategies, such as the “2020 DoD Data Strategy” and the creation of the Chief Digital and Artificial Intelligence Office (CDAO), further emphasized the importance of data-centric approaches and the optimization of AI capabilities across the DoD.
The current guiding policy, outlined in the “2023 DoD Data, Analytics, and AI Adoption Strategy,” builds upon the previous policy documents and places a major focus on speed, agility, learning, and responsibility. It emphasizes decentralized authority and the creation of tight feedback loops between developers and end-users, aimed at enhancing the decision-making processes within the DoD. The 2023 strategy outlines a foundational, guiding approach to AI rather than a step-by-step guide.
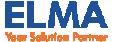
Key components of the 2023 strategy include the AI Hierarchy of Needs (Figure 1), which prioritizes high-quality data as the foundation for insightful analytics and responsible AI development. The strategy also advances the need for user-friendly infrastructure and continuous refinement of policies and processes to ensure responsible AI implementation.
Deployed AI solutions
There are a wide variety of manufacturers and contractors that are currently incorporating AI into military applications. These manufacturers and contractors range from
large established companies like Boeing, General Dynamics, Lockheed Martin, Raytheon, and Northrop Grumman to upstarts such as Anduril.
Shooter-detection systems: While not a strictly military application, shooterdetection systems have evolved an AI-integrated solution that enables first responders to pinpoint the exact location of gunfire. The system uses a series of acoustic and infrared flash-detection sensors integrated into video, accesscontrol, and mass-notification systems. The data collected by the sensor system is fed through an I/O module directly into an AI-powered software platform, which can determine if and when a gunshot happens, pinpoint its exact location, notify authorities, and send mass notifications, all within 0.5 seconds.
Tactical Intelligence Targeting Access Node (TITAN): The Tactical Intelligence Targeting Access Node, or TITAN, is a scalable and expeditionary intelligence ground station that will accelerate and
Figure 1 | The DoD AI Hierarchy of Needs prioritizes high-quality data. Image courtesy U.S. Department of Defense. MIL TECH TRENDS Enabling artificial intelligence in military systems 26 June 2024 MILITARY EMBEDDED SYSTEMS www.militaryembedded.com

simplify the Army’s ability to access and process massive volumes of intelligence, surveillance, and reconnaissance (ISR) data.
Physically, the TITAN (Figure 2) is a mobile data center with integrated power, heating and cooling, redundant communications, and computing plat forms, all built into a large truck-based platform. The vehicle-mounted expe ditionary ground stations will use AI to provide deep-sensing capability that will enable long-range precision fires for the modern battlespace. Using AI, the TITAN will perform data integration, fusion, processing, and analytic capa bilities using AI and ML to automate and assist the Army in shortening sensor-toshooter timelines.
The Sealevel Relio R1 Rugged embedded computer is at the heart of the TITAN system. The Relio R1 Rugged monitors TITAN’s overall health and performance. The small-form-factor computer hosts multiple software appli cations and interprets data from a wide variety of internal sensors.
AI going forward
The integration of AI into military appli cations represents a significant advance ment in modern warfare, offering enhanced capabilities in information processing, threat identification, and decision-making processes. The evolu tion of AI technology is linked with the development of robust technological infrastructure, guided by strategic initiatives and policy frameworks set forth by organizations like the CDAO. While AI presents immense potential for improving military effectiveness, it also raises important considerations regarding responsible development, deployment, and the implications of
autonomous systems in conflict scenarios. Continued collaboration between manufacturers and developers, policymakers, and warfighters will be crucial in ensuring that military AI applications enhance operational capabilities and responsibly contribute to global security. MES

Drew Thompson is a technical writer and marketing specialist for Sealevel Systems, the leading designer and manufacturer of embedded computers, industrial I/O, and software for critical communications. He holds an M.S. in global studies and international affairs from Northeastern University. Thompson can be reached at drew.thompson@sealevel.com.
Sealevel Systems • https://www.sealevel.com/

www.militaryembedded.com MILITARY EMBEDDED SYSTEMS June 2024 27
Figure 2 | Shown is the TITAN ALPHA working concept vehicle. Photo credit: Palantir.
MIL TECH TRENDS

AI and the OODA loop: How AI enhances strategic decisions for today’s warfighters
By Tim Stewart
New technologies, tactics, techniques, and procedures are becoming increasingly vital on the battlefield. The U.S. military is acutely aware of this and is integrating lessons learned from recent military operations in the Ukraine, as well as other conflicts, into the Combined Joint All Domain Command and Control (CJADC2), a warfighting concept that has the U.S. Department of Defense (DoD) seeking to achieve decision superiority.
Decision superiority is crucial in winning a battle: It strengthens the warfighter’s capability to “sense, make sense of, and act” (SMSA, in U.S. Department of Defense [DoD] parlance) at all levels and phases of war, across all domains, and with allied partners to swiftly deliver critical information. To achieve this warfighting concept to its fullest potential, there must be a clear path towards attaining it. Artificial intelligence (AI) is that path. AI enables decision superiority by helping to greatly reduce certain risks found in the extremely complex scenarios of warfighting.
Analyzing risk in today’s military operations
Knowing how to identify, analyze, and address critical challenges and risks, as well as develop potential technical solutions, is important in today’s military operations. This is especially true since most breaching assets will likely be conducted using unmanned or optionally manned systems. Being able to recognize, then utilize, these factors as a strategic asset will help to advance the CJADC2 initiative and improve decision superiority across military missions.
In pursuit of these goals, large amounts of data will need to be secured and transmitted across tactical networks to synchronize reconnaissance, security, and logistics as well as maneuver vehicles, fire on the enemy, and assist with other warfighting functions. Overall, CJADC2 aims to unify the massive quantities of data that different military divisions gather across a broad range of distributed sensors, and enable it to be processed into actionable information.
Those with strategic, operational, and tactical interests in the mission must
Enabling artificial intelligence in military systems 28 June 2024 MILITARY EMBEDDED SYSTEMS www.militaryembedded.com

use the most relevant information they receive to execute their missions. Held together by a robust set of communication and data sharing initiatives, CJADC2 aims to get the right information into the right hands, enabling organizations to achieve enhanced effects in their specific areas of responsibility.
How data helps with the risk
To apply and assess technology in the decision-making process, a model is
required. The OODA loop – Observe, Orient, Decide, Act – is well-known and widely accepted, developed by U.S. Air Force Colonel John Boyd. This four-step process is followed closely in the warfighter community today.
1. Observe your environment and gather information.
2. Orient yourself to that information by analyzing it and understanding its meaning.
3. Decide on what action to take based on your observations and orientation.
4. Act on your decision.
The OODA loop emphasizes the importance of speed and agility in decision-making and action-taking. The goal is to complete the loop as quickly and efficiently as possible so that you can adapt to changing circumstances and take advantage of opportunities as they arise. (Figure 1.)
Note that the OODA loop and CJADC2’s SMSA cycle share similarities in decisionmaking. Both emphasize rapid information processing, adaptation, and action. OODA’s observation and orientation mirror CJADC2’s “sense,” focusing on intelligence-gathering and understanding. OODA’s decision and action align with CJADC2’s “make sense of” and “act,” where decisions are based on analyzed data and executed with agility. Both prioritize agility and adaptability in decision-making to maintain superiority in contested domains.
AI’s role in the OODA loop
In the observe phase, AI-powered sensors, drones, satellites, and surveillance systems collect vast amounts of data from the battlefield. These data streams provide commanders with real-time situational awareness, offering insights into enemy movements, terrain conditions, and friendly-force positions. AI algorithms process this data, filtering out noise, identifying relevant patterns, and detecting potential threats, enabling commanders to rapidly assess the evolving situation.
During the orient phase, AI processing facilitates the analysis and synthesis of the gathered information. Machine learning algorithms analyze historical data, identify trends, and generate predictive models to anticipate enemy intentions and behavior. By leveraging AI-driven analytics, commanders gain a deeper understanding of the operational environment, enabling them to formulate effective strategies and courses of action to achieve mission objectives.
In the decide phase, AI algorithms provide decision support by evaluating multiple courses of action and assessing their potential outcomes. By simulating different
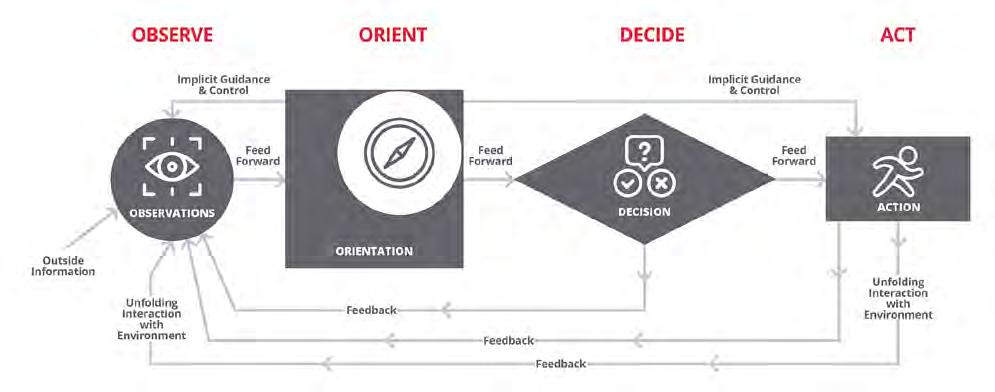
1 | Applying AI at the edge (AIAE) to the OODA loop speeds decision-making capabilities for improved decision superiority. www.militaryembedded.com MILITARY EMBEDDED SYSTEMS June 2024 29
Figure
scenarios and conducting probabilistic risk assessments, AI processing assists commanders in making informed decisions under uncertainty. These decision support tools enable commanders to weigh the risks and benefits of various options and select the most optimal course of action to achieve tactical or strategic goals.
In the act phase, AI processing facilitates the execution of chosen courses of action, enhancing the speed, precision, and coordination of military operations. Autonomous systems, guided by AI algorithms, perform tasks such as targeting, logistics, and maneuvering with minimal human intervention. By automating routine tasks and optimizing resource allocation, AI-driven systems enable military forces to maintain operational tempo and exploit fleeting opportunities on the battlefield.
Edge processing for more actionable data
One of the most important considerations is that decisions must be made at the edge, or not remotely from a command center. Moving to the edge greatly reduces latency and enhances flexibility in a rapidly changing environment, thereby making the warfighter nimble and ready for anything.
Having AI at the edge (AIAE) enables the deployment of AI algorithms on devices physically close to the data source. Connecting sensors directly via AIAE greatly reduces latency between the observe-orient steps in the OODA loop, as noted above, for example.
AIAE processing and decision-making markedly reduces latency between the orientdecide steps as well, since there is no need to transmit large amounts of data for additional decision-making steps to the external center and then wait for the decision to be sent back. Sending the “act” command using an AIAE infrastructure will reduce latency for the decide-act steps for the same reasons.
Enabling AI in military operations
Graphics processing units (GPUs) are designed to handle large amounts of data in parallel and are widely used for AI applications. Because of advances in technology, small-form-factor, higher-performance computers are being brought to market with the combination of general-purpose graphics processing units (GPGPUs) and central processing units (CPUs) that can be used for AIAE applications.
By leveraging the parallel processing power of GPUs, GPGPUs can accelerate a wide range of AI applications. (Figure 2.)
What can be used?
The NVIDIA Jetson family of modules combine AI-capable GPGPUs with multicore CPUs, for a tightly coupled, high-performance, low-power supercomputer that can support AI processing capabilities and decision-making applications software.
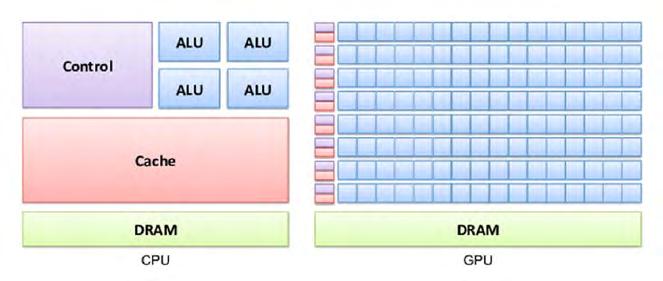
Overall, CJADC2 aims to unify the massive quantities of data that different military divisions gather across a broad range of distributed sensors, and enable it to be processed into actionable information.
NVIDIA’s Jetson family of products has the option of several modules with different form factors, performance, and maximum power options. (Figure 3.)
The NVIDIA Jetson Xavier NX module provides six trillion floating points operations per second (TFLOPS) performance with a maximum power of 15 watts, performance comparable to a several-hundred-watt workstation with processor and GPU cards.
This kind of computing architecture can process and apply AI algorithms for 20-plus high-definition video inputs with 1040p resolution at a rate of 30 frames per second. It has enough bandwidth to run AI applications servicing multiple high-definition cameras in a system.
From the size, weight, and power (SWaP) plus performance perspective, a ruggedized NVIDIA Jetson Xavier NX module is suitable for use in AIAE applications because units can be as small as 4 inches by 2.3 inches by 3.9 inches, weigh as little as 1.3 pounds, and offer just 15 watts of power. (Figure 4.)
More demanding performance needs can use larger and higher-power rugged solutions based on higher-performance NVIDIA Jetson modules. These types of rugged GPGPU-based units can also support industry standard interfaces, including Ethernet (1 GbE and/ or 10 GbE), CAN bus, serial ports, etc.).
Figure 2 | A GPU’s parallel processing architecture enables faster computation than a CPU, facilitating the use of AI in military applications.
MIL TECH TRENDS Enabling artificial intelligence in military systems 30 June 2024 MILITARY EMBEDDED SYSTEMS www.militaryembedded.com

An Ethernet interface can be used as a communication channel to other “smart”’ boxes and mission computers in systems. It can also be used for interactions with external equipment through wireless communications converters. If low-latency Ethernet communication is required, time sensitive networking (TSN) or time-triggered Ethernet (TTE) can be used.
Using an Ethernet network for internal communications enables the user to implement multiple redundancy levels, from physical cables to routers and

packets. Implementing IEEE 1588 time distribution protocol across the network enables all network elements to be synchronized to a single time source.
Besides high-speed sensor processing, GPGPU units can be used to process data coming from lower-speed sensors –analog I/O, discrete I/O, serial ports, etc. Combining these functions into one AIAE unit can help to eliminate additional electronics boxes and associated harnesses in a vehicle, further reducing the SWaP of electronics equipment.
AI is the advantage in decision superiority
For the DoD, achieving the CJADC2 vision begins with demanding that industry be able to connect every current sensor that can support battlespace awareness, as well as make sensor data available to any potential user, at any level of operation. This datasharing construct can create secured battlespace awareness, wherein actions in one part of the single, integrated, global battlespace can be understood and inform actions and decisions required in other areas.
The integration of AI processing within the OODA loop framework has revolutionized military decision-making, providing commanders with unprecedented capabilities to adapt, react, and prevail in complex and contested environments. By leveraging AI-driven technologies, the U.S. military has enhanced its ability to maintain a competitive edge on the modern battlefield, ensuring superiority in an era defined by rapid technological innovation and strategic competition. MES

Tim Stewart is Director, Business Development, at Aitech. He has 20 years of experience in hightechnology hardware, software, and network products, with 11 years as a relationship executive managing requirements and challenges of companies seeking partnerships and critical corporate development. Tim holds a BS in mechanical engineering and physics from Boston University.
Aitech • https://aitechsystems.com/
Figure 3 | The NVIDIA Jetson family includes different modules with various form factors, performance, and maximum power options.
www.militaryembedded.com MILITARY EMBEDDED SYSTEMS June 2024 31
Figure 4 | Compact, high-performance AI supercomputers process vast amounts of sensor data at the edge.
MIL TECH TRENDS
The steps to laying out an embedded system quantum roadmap
By Steve Roemerman
Enabling

There is a tendency to think of quantum technology as being “far in the future” or something that’s “too big” to matter for systems at the military edge or other embedded systems. You might think, “My company isn’t really in a business impacted by this.” You aren’t alone, but you would still be mistaken. So, is it time to panic? No, but it is time to lay out
for your organization.
Organizations can take a number of steps to work toward quantum readiness.
Step zero: Understand what every intelligence agency knows – your encryption is a ticking time bomb
One of the first applications of quantum computers will be the destruction of the two most pervasive forms of encrypting information. Opponents who “harvest now, decrypt later” are collecting your encrypted files. These will be stored until mature quantum computers are available. Your files are a future liability, particularly when they are in motion.
You might think “I’m fully compliant, and we comply with FIPS 140-2 (or some other standard).” That’s good and necessary, but probably insufficient. Planning for a move to quantumresistant encryption is essential. In fact, the National Institute of Standards and Technology (NIST) has been benchmarking and promoting it. (Figure 1.)
Before the new standards come out, you need to protect today’s data. If you have older systems using outdated encryption, like DES [data encryption standard] or short key lengths, your teams should be moving away from those standards NOW. This might mean some SCADA controllers collecting HVAC data, or any other old legacy systems which are not being updated. Consider what information is worth protecting two to five years from now and prioritize what is moved to the new schemes.
You may have a fiduciary responsibility to do this to protect your company. You likely have a duty of care for your stakeholders whose data you house, whether those are customers, employees, vendors, or stockholders. Consider this before you move to the four steps in building your roadmap.
Step one: Begin to understand the ways in which quantum technology will change our organizations and how we perform our missions
Don’t think of quantum technology as just “computing.” Quantum entanglement as a form of communication is already
 Figure 1 | The first four algorithms NIST announced for post-quantum cryptography are based on structured lattices and hash functions, two families of math problems that could resist a quantum computer’s assault. Diagram: N. Hanacek/NIST.
a quantum roadmap
Figure 1 | The first four algorithms NIST announced for post-quantum cryptography are based on structured lattices and hash functions, two families of math problems that could resist a quantum computer’s assault. Diagram: N. Hanacek/NIST.
a quantum roadmap
in military systems 32 June 2024 MILITARY EMBEDDED SYSTEMS www.militaryembedded.com
artificial intelligence
providing tantalizing results. For embedded systems, you might consider that currently installed fiber-optic networks will probably allow us to share both conventional and quantum data.
Quantum technology will change more than computing and networking. It will change sensors, precision timing, and other components of modern systems. Since embedded systems depend on things like precision timing and support the processing appetite of data-rich sensors, it’s worth the effort to imagine how quantum computing would change product offerings, system configurations, and future mission capabilities.
Only your team can determine what this means for your organization. Before you spend a great deal of time and money, strive to gain some understanding about what can change, and how it might shift your competitiveness. You may later need to spend a great deal, but throwing money at quantum now is a bad bet for most organizations.
Don’t fool yourself into thinking expensive activity is valuable progress. That mistake is just as bad as doing nothing.
Step two: Look deeply into what quantum can’t change Google, IBM, Amazon, and others are putting great effort into the development of quantum neural networks. This is due in part to the hope that quantum artificial intelligence (AI) is likely to be less of a data hog than the current mainstream systems.
But understand that this kind of AI still depends on enormous amounts of labeled data, and that much of the quantum AI work is focused on just making AI possible on a quantum machine which does not yet exist.
Some competitive advantages won’t be impacted by quantum technology, and this will be true for your organization as well. Be careful, though: This is an area where disciplined thinking is hard. It is also where hubris and denial are amazingly easy.
Only your team can determine how this question applies to your products and systems.
Step three: Think about where quantum allows you to exploit your core competencies to create future competitive advantage Your competencies are your own. But if you complete steps zero through two, you will find some opportunities to consider. A few of those opportunities will be worth the allocation of some investment. For example, expertise in sophisticated use of uncertainty, which is at the core of many of quantum’s most promising attributes, creates a natural area to focus R&D efforts.
For example, some defense companies’ core competencies include sophisticated use of uncertainty, which is at the core of many of quantum’s most promising attributes. In turn, that creates a natural way to think about where an organization’s R&D team should focus.
Step four: Build a quantum roadmap for your organization It won’t be perfect. Developments in coming months and years will require revisions.
Competitors will create some surprises. You’ll have to adjust your course. Revisions and adjustments are only possible if you have a course previously charted.
Sharing roadmap capabilities with key customers is essential: They’ll want and need to know your plans to extend leadership in prescriptive and predictive analytics.
What roadmap will you share with your stakeholders? MES

Steven Roemerman is the chairman and CEO of Lone Star Analysis and has served in this role since 2004. Previous CEO roles have included Incucomm Inc., a business incubator which launched several companies; and Crosspan Technologies, a subsidiary of Raytheon. He has served as an officer or director in more than a dozen other corporations in technology, aerospace, finance, nonprofits, and transportation.



Lone Star Analysis
www.militaryembedded.com MILITARY EMBEDDED SYSTEMS June 2024 33 AS 9100D / ISO 9001:2015 CERTIFIED PHALANX II: THE ULTIMATE NAS Supports AES-256 and FIPS140-2 encryption Utilizing two removable SSDs, the Phalanx II is a rugged Small Form Factor (SSF) Network Attached Storage (NAS) file server designed for manned and unmanned airborne, undersea and ground mobile applications. www.phenxint.com PHX_OSP_3.375_4.875.indd 1 1/22/18 11:36 AM
• https://www.lone-star.com/

Covering fault scenarios in mission-critical military Ethernet applications
By Richard Tse
Time-sensitive networking (TSN) can be used in military systems to detect and contain the propagation of faults and to enhance the availability and integrity of time in an Ethernet network. When combined with hardening strategies, TSN enables Ethernet to be used for mission-critical applications in harsh environments.
Ethernet is rapidly being deployed as the primary networking technology for both military and commercial systems. To enable Ethernet to take part in mission-critical applications, it must be resilient to faults and – because it is a networking technology – this resilience must cover device-level faults as well as interdevice faults. While the probability of a device-level fault could be reduced by using hardened devices, improving the consequences of device-level and interdevice faults requires higherlevel functions. Time-sensitive networking (TSN) provides such functions for Ethernet.
Ethernet is ubiquitous because it is simple, inexpensive, flexible, and constantly improving. However, its lack of intrinsic resilience to faults has limited its use in mission-critical applications. In harsh-environment scenarios, hardening strategies are used for mission-critical
electronics design trends INDUSTRY SPOTLIGHT 34 June 2024 MILITARY EMBEDDED SYSTEMS www.militaryembedded.com
Rad-hard

applications to reduce the probability of faults in a device. These device-level strategies do not enhance a network’s ability to deal with the consequences of such a fault, however, when it inevitably occurs. Higher-level mechanisms are needed for this.
The Time Sensitive Networking (TSN) Task Group of the Institute of Electrical and Electronics Engineers (IEEE) 802.1 Working Group has a charter to enable determinism in Ethernet networks. This determinism covers packet latency, latency variation, and loss, but also results in improved resilience to faults. The IEEE P802.1DP Task Group is defining a profile of TSN for aerospace onboard Ethernet communications, enabling Ethernet to service mission-critical applications. This profile might also be appropriate for the use of Ethernet in military applications like the U.S. Army’s Ground Combat Systems Common Infrastructure Architecture (GCIA), which integrates multiple systems and eliminates redundancies in service vehicles by using open architecture.
Traffic management and policing
Mission-critical networks are highly managed: The bandwidth used by each Ethernet stream (a unidirectional flow of data from a talker to a listener) is planned and constrained so that the combination of all streams does not cause congestion in the network. A single-event upset (SEU) could result in a “babbling” transmitter, which leads





800 431-1064 Fax 914-738-8225 E Mail: info@picoelectronics.com from lowprofile .18"ht. SURFACE MOUNT (and thru-hole) Transformers & Inductors Size does matter! • Audio Transformers • Pulse Transformers • DC-DC Converter Transformers • MultiPlex Data Bus Transformers • Power & EMI Inductors See Pico’s full Catalog immediately www.picoelectronics.com PICO Electronics, Inc. 143 Sparks Ave. Pelham, N.Y. 10803-1837 Certified to AS9100D ISO 9001:2015 Delivery - Stock to one week VISIT OUR EXCITING NEW WEBSITE www.picoelectronics.com A19_MILEmbedSys_2_2125x10.qxp_A19.qxd 4/3 www.militaryembedded.com MILITARY EMBEDDED SYSTEMS June 2024 35
to the generation of excess bandwidth on a stream of a device and corresponding network congestion. This congestion could cause increased latency, latency variation, and packet loss on other streams. To prevent this, TSN offers per-stream transmission management at each transmitting port and per-stream policers at each receiving port.
One form of TSN transmission management is the credit-based shaper algorithm, known as CBS (which is specified by 8.6.8.2 of IEEE 802.1Q-2022). The CBS function uses credits to create a stream whose bandwidth usage is steadily paced and constrained. Credits are added at a configured rate, X, when no frame from that stream is being transmitted. Credits are added at a rate of X – Y, where Y is the rate of the Ethernet link, when a frame from that stream is being transmitted. Transmission of a frame from a stream is not initiated unless the stream has a non-negative credit value.
The policer that corresponds to CBS is the per-stream filtering and policing (PSFP) flow metering function (which is specified by 8.6.5.5 of IEEE 802.1Q-2022). It discards frames from a stream when the stream exceeds its configured average or peak bandwidth rate.
Another form of TSN transmission management is commonly known as the time-aware shaper (TAS) (which is specified by 8.6.8.4 of IEEE 802.1Q-2022). TAS creates timedivision multiplexed transmission windows and places frames from a stream (or from a set of streams) into their designated windows. Streams in one window are isolated from streams in other windows.
The policer that corresponds to TAS is the PSFP stream gating function (which is specified by 8.6.5.4 of IEEE 802.1Q-2022). It discards any frame that is not entirely contained within its designated window.
Figure 1 shows sets of CBS, TAS, and PSFP functions associated with some Ethernet devices. The ordering of the CBS, TAS, and PSFP functions shows that a fault in a transmitter that causes excess transmission bandwidth and/or misaligned transmissions on a stream is immediately policed at the adjacent downstream receiver, which stops the fault from affecting other streams.
As seen in Figure 1, if the CBS function for stream 1 erroneously transmitted at 6 Gbps and was not policed, the 10 Gbps egress port of Ethernet Switch 1 would be overwhelmed with 11 Gbps of traffic. The resulting congestion on this egress port could affect
streams 2 and 3. Fortunately, the PSFP flow metering function in Ethernet Switch 1 polices stream 1 and limits it to 5 Gbps.
Analogously, a good transmitter combined with a faulty policer would not have a deleterious effect on other streams because the transmitted traffic is already behaving properly.
Lastly, the CBS and TAS functions are in a different device from their corresponding PSFP flow metering and stream gating functions. It is improbable that both the transmission and policing functions would suffer faults on the same Ethernet stream at the same time.
Time availability and integrity
Many modern applications are timesensitive, so the sharing of a common time-of-day (ToD) is important. For mission-critical applications, the availability and the integrity of this ToD are vital.
ToD can be distributed accurately (within sub-microseconds) by Ethernet using the mechanisms from IEEE 802.1AS, Timing and Synchronization for Time-Sensitive Applications. These mechanisms are commonly referred to as PTP [precision timing protocol].
While PTP has been used successfully in commercial applications, its lack of inherent abilities to immediately overcome a fault and to check the integrity
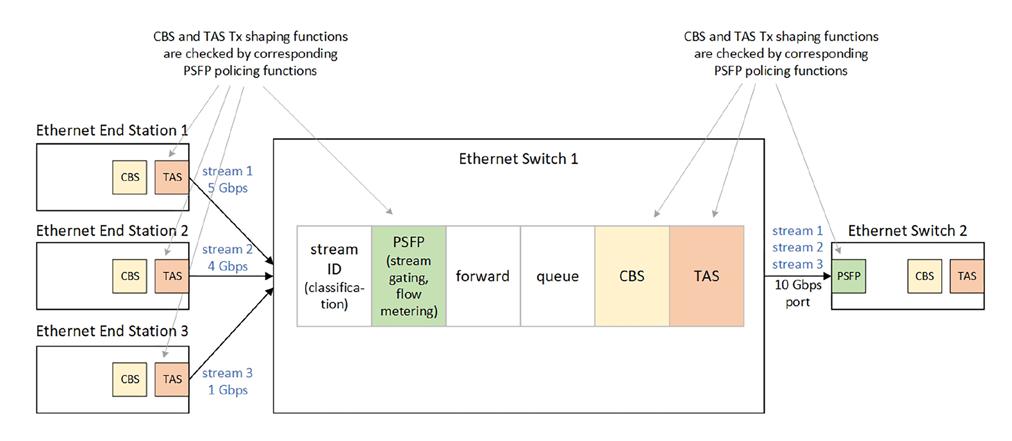
Figure 1 | CBS, TAS, and PSFP functions in Ethernet devices. INDUSTRY SPOTLIGHT Rad-hard electronics design trends 36 June 2024 MILITARY EMBEDDED SYSTEMS www.militaryembedded.com
of the received ToD has limited its use in mission-critical applications. These issues are addressed by work that was started for IEEE 802.1DP and is, ultimately, expected to be finished in an amendment of IEEE 802.1AS. The concepts of this work are discussed here.
A typical connection from a PTP grandmaster clock (GM) to a clock target is shown in Figure 2. The availability of the ToD could be temporarily lost if one of the PTP relay instances or one of the links fails and causes the connecting path to the clock target to change. The integrity of the ToD at the clock target cannot inherently be trusted because it could be undetectably corrupted by any of the PTP instances in the connecting path or even by the GM itself.
To increase availability and enable integrity, multiple (two or three) GMs connect to the clock target through independent paths and through a fault-tolerant timing module (FTTM, not yet standardized). An example with three GMs distributing ToD independently through multiple PTP relay instances, PTP end instances, and an FTTM to the clock target is shown in Figure 3.
This solution increases availability because multiple instances of ToD are available through the FTTM to the clock target. If one is lost due to a fault, another is still available.
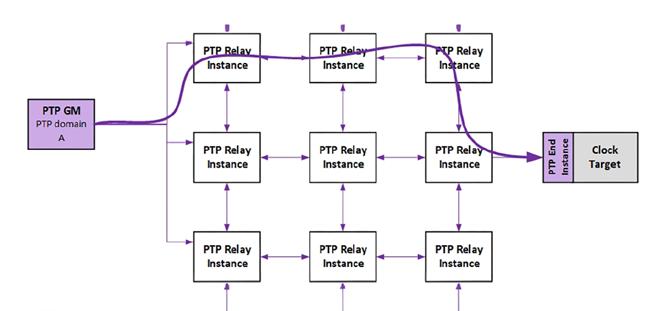
Additionally, this solution enhances integrity because the multiple ToDs can be compared. An error in one can be detected by its deviation from the other(s). The GMs are synchronized to each other using a time-agreement generation function that is resilient to Byzantine faults, thus keeping them independent of each other. [Note: A Byzantine fault is a state of a computer system, particularly distributed computing systems, where components may fail and there is imperfect information on whether a component has failed.]
Use of independent network paths eliminates potential common mode failures in the ToDs delivered to the FTTM. The FTTM compares ToDs, determines which ToDs can be trusted, and selects a trusted ToD for the clock target. MES

Richard Tse is an Associate Fellow-Architecture at Microchip Technology with extensive experience in semiconductor devices and network architectures. He was the chair/editor of IEEE 1914.3, Radio over Ethernet Encapsulations and Mappings, and contributes to IEEE 802.1, IEEE 802.3, and IEEE 1588 standards, with multiple contributions on the fault-tolerant timing module for TSN. He holds an M.Sc. in electrical engineering from the University of Alberta in Canada.
Microchip Technology • https://www.microchip.com/
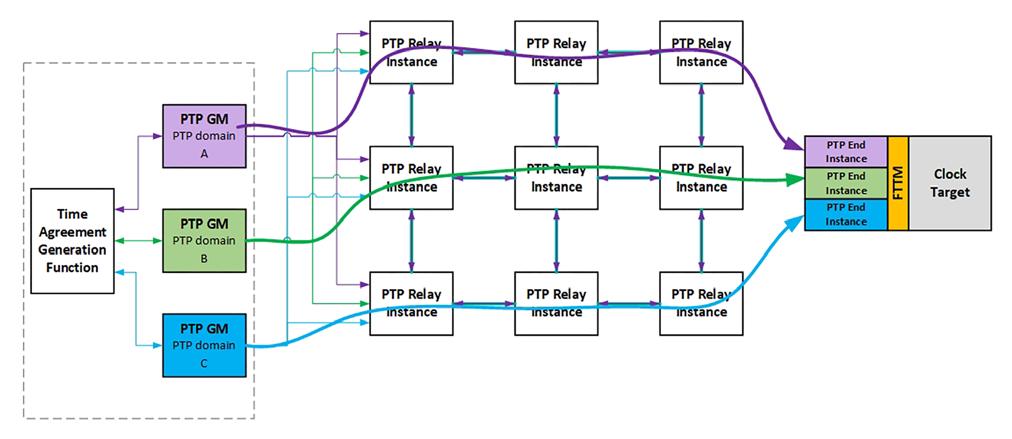 Figure 2 | Typical connection from a GM to a clock target.
Figure 2 | Typical connection from a GM to a clock target.
www.militaryembedded.com MILITARY EMBEDDED SYSTEMS June 2024 37
Figure 3 | Independent connections from three GMs to a FTTM and clock target.



Military rad-hard designs for space … and beyond
By John McHale, Editorial Director
As space becomes the next domain for weapons and military threats, designers of radiation-hardened electronics are seeing more requirements for greater radiation-resistant components. In this conversation with Sean D’Arcy, Senior Director, Aerospace and Defense/IR HR at Infineon Technologies and Josh Broline, Senior Director of Marketing and Applications at Renesas, we discuss this challenge as well as the hottest applications for military space, the use of commercial off-the-shelf (COTS) components, and if open architectures may be leveraged in spacecraft designs.
MCHALE: What are the factors driving military radiation-hardened (rad-hard) designs today? In other words, what are your military customers looking for in this area?
D’ARCY: Historically, high-value onorbit space vehicles and strategic programs dominated the militaries’ need for radiation-hardened products. And while that will remain, we are starting to see concerns about various weapons being put on orbit by adversaries and bad actors that may drive an increased interest in higher TID and SEE [total
ionizing dose and single-event effects] for electronic designs. A technology change is the move towards phased array for on-orbit assets. There is a limited portfolio of rad-hard components that can support the FPGA [field-programmable gate array] and high-speed converters, especially in power, which is critical for high-value military communications systems.
BROLINE: Mostly parts fabbed on dielectrically isolated processes that won’t latch up. They continue to prefer parts in hermetic packages sold to DLA [Defense Logistics Agency] (military drawings, SMDs [surface-mount devices].)
MCHALE: What is the hottest application for rad-hard electronics? Small sats? Avionics, manned space flight, something else? Why?
D’ARCY: Right now, I personally see us at a crossroads as to what the future mix of radiation-tolerant versus radiation-hardened will be. I encourage people to think
Sean D'Arcy
Rad-hard electronics design trends INDUSTRY SPOTLIGHT 38 June 2024 MILITARY EMBEDDED SYSTEMS www.militaryembedded.com
Josh Broline
about the need for rad-hard not by orbit but by value of function and duration. Small satellites are moving towards shorter-duration missions that allow for rapid upgrading of technology across a constellation while, for example, the high-value assets like GPS are going to remain rad-hard. Over the next 15 years the greatest growth will be in manned space and lunar exploration where mission success is critical.
BROLINE: Currently, we are seeing a huge increase in the number of customers using the AMD/Xilinx Versal FPA in many applications across the board requiring the need for a multiphase power architecture to meet the high-power core requirements of that FPGA (0.8V, 130A).
MCHALE: Are you seeing military space system requirements revolving more around the modular open systems approach (MOSA) strategy, open architectures, and open standards? If yes, how?
D’ARCY: My opinion is that we are still a few years away from any type of open standard for military space systems in the radiation-hardened market space. SDA [Space Development Agency] may drive an open architecture to speed payload development, but the large radhard programs are very specialized and low-volume, which may take a longer time to move towards standards. An example, again, is the GPS constellation, which is highly customized, and both bus and payload are very specific.
BROLINE: These types of initiatives are typically wrapped up in the processors/processing architectures and software. For what goes around the processors (power, sensor signal processing, etc.), we typically don’t run into these standards.
MCHALE: Reduced cost requirements often mean more requests for COTS [commercial off-the-shelf] components in space. How do you meet this demand while maintaining reliability?
D’ARCY: I see couple of ways to satisfy the need for COTS or automotive parts
on orbit. First is that this is the genesis of radiation-tolerant parts where industry tests and qualifies the parts to a lower TID and SEE requirement but still provides an expected level of performance in the radiation and environmental challenges found in space applications. An advantage to having the semiconductor manufacturer do it is that the cost is incurred once not repeated by each payload or bus manufacturer saving cost across the industry. Second is the use of radiation-hardened components in guard systems or critical power systems while radiation-tolerant is used in the noncritical systems. For example, you use radiation-hardened MOSFETs to switch and control power, which allows you to mitigate any power failure due to radiation or environmental effects and, more importantly, power cycle lower-reliability components and designs. Related to this is using a guard card function with radiation-hardened parts to monitor a number of radiation tolerant cards or subsystems and reset them and reload them when required.
"Small satellites are moving towards shorter-duration missions that allow for rapid upgrading of technology
across a constellation while, for example, the high-value assets like GPS are going to remain rad-hard. Over the next 15 years the greatest growth will be in manned space and lunar exploration where mission success is critical."
– Sean D'Arcy,
Infineon Technologies
BROLINE: Using COTS for space is risky. We’ve radiation-tested many COTS parts and most perform poorly when exposed to TID and/or the SEE environment. Our strategy is to design product specifically for the radiation environment. We also use processes for our wafer fabs that we are confident will give us the radiation performance we need. We then offer these parts on various flows to address the different needs for different programs. One flow specifically created for reduced-cost programs is our rad-tolerant plastic program.
MCHALE: How is the government’s long-term plans to increase funding for domestic microelectronics production impacting defense space systems? When will we see the impact?
D’ARCY: This is a critical need for the United States and its allies given the vulnerability, geographically, of a significant part of the semiconductor industry. This is important in all defense applications including defense and needs to be accelerated. I think we are already seeing the impact as the United States and allies (“friendshoring”) continue to understand the risk in the present supply chain. We are seeing major investments that are already seeing more designs being built in the U.S.
BROLINE: There will be an uplift over time in more domestic fab, assembly, and test options. This will certainly take time to become established, but the DoD and supply base will be able to take advantage of those additional options. Whether for the likes of supply-chain redundancy, next-generation technology, or something else, this will help with the robustness/reliability of the supply base over time. MES
Sean D’Arcy is Senior Director, Aerospace and Defense/IR HR at Infineon Technologies. Josh Broline is Senior Director of Marketing and Applications at Renesas.
Infineon Technologies • https://www.infineon.com/ Renesas Electronics • https://www.renesas.com/us/en
www.militaryembedded.com MILITARY EMBEDDED SYSTEMS June 2024 39
MOSA – friend or foe?
By Chip Downing

As I travel to various places around the world, I am surprised by the perception that different government and supplier organizations have of the modular open systems approach (MOSA). MOSA is designed to lower costs for global coalition forces while accelerating new, highly competitive capabilities for the warfighter, but folks still do not understand these benefits and sometimes turn MOSA into something that should be feared.
Let us be clear – MOSA simply wants to enable the rapid insertion of the most competitive warfighter technologies. I looked at three of its architectural and operational capabilities:
1. To drive affordable innovation throughout the supply chain based upon open standards and an open systems architecture (OSA);
2. To leverage the latest advancements in silicon with software that fully enables artificial intelligence (AI) that will augment rapid Combined Joint All-Domain Command and Control (CJADC2) decision-making;
3. To fully enable CJADC2 to deliver the most comprehensive situational-awareness visualizations to the warfighter and commanders for rapid and precise executions of threat responses.
The mandate for MOSA MOSA is not a new, unproven process for efficiency – it is a remarkably simple and straightforward open systems blueprint for procuring the best, most competitive technologies for creating unequivocal advantages for all coalition armed forces. Ten years ago, MOSA was an interesting purchasing and design concept; today, MOSA is the U.S. Department of Defense (DoD)-preferred method for implementation of open systems and is in fact required by U.S. law. Title 10 U.S.C. 4401(b) states that all major defense-acquisition programs (MDAP) are to be designed and developed using a MOSA that:
› Employs a modular design that uses modular system interfaces between major systems, major system components, and modular systems
› Is subjected to verification to ensure that relevant modular system interfaces comply with, if available and suitable, widely supported and consensus-based standards
› Uses a system architecture that allows severable major system components at the appropriate level to be incrementally added, removed, or replaced throughout the life cycle of a major system platform to afford opportunities for enhanced competition and innovation.
› Complies with the technical data rights set forth in 10 U.S.C. 3771-3775
Core requirements for MOSA
Achieving the benefits of MOSA requires adherence to five major MOSA principles:
1. Establish an enabling environment – A program manager must establish supportive system requirements, business practices, technology development, acquisition, test & evaluation, and product support strategies.
2. Employ modular design – Functionality must be isolated during the design process to enable the system to be easier to develop, maintain, modify, and upgrade. A modular systems design will provide the foundation to upgrade or change functions that change or evolve quickly over time with minimum impact on the rest of the system. This is accomplished using open industry standards for key interfaces.
3. Designate key interfaces – A MOSA system design manages key interfaces to utilize open standards to produce the most life cycle benefits possible.
4. Use open standards – Open hardware and software interface standards must be well-defined, mature, widely used, and readily available, enabling rapid interchangeability, interoperability, interconnection, compatibility, communication, and logistics support. Open standards managed by independent standards organizations enable immediate support from a wide supply chain supporting an existing market with proven commercial products and related safety and security certification evidence.
5. Certify conformance – MOSA module verification and conformance to key interfaces based upon open industry standards is the foundation of program efficiency. Proven conformance notably reduces multiple-supplier integration risk, driving accelerated deployment and higher levels of quality throughout the system.
Open standards
40 June 2024 MILITARY EMBEDDED SYSTEMS www.militaryembedded.com
INDUSTRY PERSPECTIVE
The use of the FACE standard in MOSA programs
The use of The Open Group Future Airborne Capability Environment (FACE) Technical Standard and Business Approach is now widely referenced as a proven strategy to use open standardsbased software in programs using MOSA. The FACE business approach and technical standard is independently managed by The Open Group as a consortium; more than 100 government and industry entities have worked to establish this open avionics environment for all military airborne platforms. The consortium was formed in 2010 and is made up of military customers, avionics suppliers, and academia.
The FACE Technical Standard and Business Approach enables the U.S. and coalition partners to enable military aircraft to rapidly refresh their avionics platforms to support the latest advances in computer hardware and software. The FACE Technical Standard, a “standard of standards,” is based upon existing and proven open standards. There are over 60 open standards that the FACE standard supports, and these are managed by independent standards organizations that serve the global avionics community. These organizations include ANSI, ARINC, IEEE, IETF, Khronos Group, Object Management Group (OMG), and The Open Group, and they manage standards as diverse as ARINC 653, C/C++, DDS, IPv6, Java, OpenGL, POSIX, TCP, and Vulkan, with a wealth of existing commercial solutions. Many of these commercial products have existing airworthiness-certification evidence that both reduces risk and accelerates the deployment of critical airborne software.
Conformance eases integration and accelerates deployment
One of the hallmark achievements of the FACE Consortium is the creation of a conformance program to evaluate the presence of the key interfaces defined in the FACE Technical Standard. Conformance is also a key pillar of MOSA. FACE Conformance means that a product meets 100% of the applicable FACE Technical Standard requirements. There is no conformance category for a product that does not meet 100% of FACE API requirements – this condition provides greater assurance that
conformant products are both portable and reusable, and should accelerate integration of software modules from a diverse supply chain.
One of the unsung heroes of the FACE approach is the adoption of proven industry standards. Instead of writing an entirely new and unproven set of APIs and a new, proprietary, U.S.-only solution stack, the FACE technical team decided early on that the use of existing avionics standards was the fastest and most feasible path to accelerating new capabilities to the warfighter. This standard-of-standards approach based upon open software standards already proven by global commercial suppliers accelerates military avionics efforts and does not waste industry time rewriting proven standards with yet another new, unproven, and proprietary API. Another benefit of this approach is that many commercial avionics software suppliers already have existing airworthiness certification evidence that is proven in flight – this proof reduces program risk and further accelerates the deployment of critical airborne software.
Is MOSA a friend? Or a foe?
MOSA brings with it a wide range of beneficial qualities. The only entities that should fear MOSA are first, supplier entities that have enjoyed unbridled largesse with government customers because they have a captive supply chain that locks in uncompetitive capabilities to the warfighter, or second, program managers who fear the change that MOSA brings and enjoy a cozy relationship with a single-source supply chain that requires minimum effort to manage. Although MOSA is driven from the top of the U.S. DoD, it is not a USAonly concept, and at its core is designed to be highly inclusive of the exceptional innovation of global defense partners.
MOSA is a friend of our warfighters. Its adoption across all armed forces and their supply chains will increase our global military competitiveness against all adversaries. MES
Chip Downing is the founder of S5 Intelligence Corp.
S5 Intelligence Corp. • www.s5int.com
The McHale Report, by mil-embedded.com
Editorial Director John McHale, covers technology and procurement trends in the defense electronics community.
THE ARCHIVED MCHALE REPORTS AVAILABLE AT: https://militaryembedded.com/newsletters/the-mchale-report www.militaryembedded.com MILITARY EMBEDDED SYSTEMS June 2024 41

Tactical radio communications
The GENSS is a tactical radio communications solution that gives users software-defined flexibility: The system integrates multimission and multimode functionalities, providing reliable battlefield connectivity. Its design features modular architecture to ensure solid interoperability and adaptability, enabling it to be used for both voice and data communications in military settings. Additionally, the modular design can stand alone, integrates into any existing radio infrastructure, and will be compatible with future systems.
Developed by designers with military operational experience and leading U.K. scientists and engineers, GENSS tactical communication system operates across multiple bands including HF, VHF, UHF, and satellite (L-Ku), which ensures beyond-lineof-sight functionality and enables communications on the move. The secure, high-capacity design supports high-bandwidth data transmission and voice communications across land, sea, and air platforms. Additionally, GENSS is engineered to enhance network sensing capabilities, enabling increased data rates and adaptive modulation waveforms that adjust to tactical scenarios, thereby minimizing detection risks and extending data-management capabilities for rapid tactical and strategic updates.
IC prevents failure modes
The AP54RHC288 Arbiter is an integrated circuit (IC) designed to prevent propagation of failure modes in power supply, motor control, and other half-bridge and full-bridge applications. The IC prevents cross-conduction and shoot-through in these applications by preventing FET [field-effect transistor] drivers from seeing two high control signals, regardless of the state of the input control signals. The AP54RHC288 is single-event effect (SEE)-resilient and is intended for use as fault containment in mission-critical applications.

A related component is the AP54RHC301 Voter, which enables triple-mode redundancy for mission-critical applications by providing reliable arbitration between redundant channels. Apogee calls it the industry’s first standalone voter or multiple signalinput IC that enables more reliable systems without designers and users needing to purchase all radiation-hardened components for their small satellite systems. The Voter chip is also designed to prevent fault propagation between non-radiation-tolerant components in systems. The part is also available with higher levels of radiation tolerance – the 300 krad (Si) variant – for geosynchronous orbit and deep-space applications.
http://www.apogeesemi.com/

Edge node management
The Terminus tool is designed for monitoring and managing edge nodes. This tool facilitates rapid node setup and management, enabling users to transition from installation to operational status in less than three minutes. Occupying less than 1 GB of memory, it features low size, weight, power, and cost (SWaP-C), aiming it at use in denied, interrupted, or limited (DIL) environments. The interface is easy to use as it maintains a consistent look and feel across various devices and dashboards, adheres to MaterialUI standards, employs DevSecOps methodologies, and integrates feedback from network experts and users. It also uses progressive disclosure techniques to display only the necessary information as needed. The management tool gives users a visual status and health of each device at a glance and also enables the creation, logging, and tracking of network events throughout their activity life cycles. Terminus prioritizes critical information, helping users eliminate irrelevant data and resolve issues swiftly through guided workflows. The tool is designed to be adaptable, requiring no expert intervention for modifications, and is compatible with any baseband kit. Additional asset packs can extend its functionality to various equipment, and it supports the application of updates and patches during runtime without the need for reinstallation, thereby ensuring continuous and reliable operation.
Codemettle | https://codemettle.com/
EDITOR’S CHOICE PRODUCTS
Apogee Semiconductor |
42 June 2024 MILITARY EMBEDDED SYSTEMS www.militaryembedded.com
Spectra Group | https://spectra-group.co.uk/
EDITOR’S CHOICE PRODUCTS

Tactical GNSS-INS system
The VN-210, offered by VectorNav, is a tactical-grade global navigation satellite system-aided inertial navigation system (GNSS/INS) designed to provide precise position, velocity, and attitude solutions. This navigation system integrates advanced inertial sensors and GNSS technology into a compact module suitable for rugged environments. The VN-210 features a 3-axis accelerometer, a 3-axis gyro, and a 3-axis magnetometer, alongside a multiband GNSS receiver. It offers specifications including dynamic heading accuracy of 0.05˚ to 0.1˚, dynamic pitch/roll accuracy of 0.015˚, and gyro in-run bias stability of less than 0.6˚ per hour, making it suitable for critical navigation tasks.
The device offers robust environmental resilience against dust, water, pressure, and temperature, with certifications including IP-68, DO-160G, MIL-STD-1275E, MIL-STD-461G, and MIL-STD-810G, ensuring its performance in harsh conditions. It supports multiband GNSS frequencies such as L1/L2/E1/E5b, enhancing its tracking capabilities across various applications. The VN-210 claims ultra-low size, weight, and power (SWaP), with dimensions of 56 mm by 56 mm by 31 mm and a weight of 155 grams (5.47 ounces). Its operational power consumption is less than 2.7 W, and it can handle navigation data at 400 Hz and IMU data at 800 Hz, ensuring rapid data processing and transmission.
Short-range reconnaissance UAS
The Teal 2 small uncrewed aerial system (sUAS) can handle short-range reconnaissance missions, having earned a Blue UAS Certification from the U.S. Department of Defense (DoD). This certification highlights its compliance with stringent design standards crucial for operation in combat and tactical scenarios. Designed for use by military personnel, law enforcement, firefighters, wildlife managers, and industrial inspectors, the Teal 2 can be operated during both day and night operations. Its payload, the FLIR Hadron 640R dual camera module, integrates both electro-optical (EO) and infrared (IR) technologies, enabling the operators to detect and track objects and assess threats under various visibility conditions.

The Teal 2 is equipped with a dual-axis EO/IR gimbal that enhances the small craft’s imaging capabilities, featuring a 16 MP EO sensor and a Boson 640 radiometric IR sensor. This setup ensures comprehensive visibility through multiple thermal-imaging palettes, each suited to different operational needs such as identifying heat signatures or navigating through low-light environments. These capabilities are housed in a rugged 2.7-inch frame that enables quick deployment and a high degree of portability for use during fast-paced field operations. Additionally, the Teal 2 uses AES-256 encryption to ensure secure communications, which means that users will have a high level of data protection during sensitive missions.
Teal Drones | https://tealdrones.com/

Decision optimization module
TANDOM, the Tactical ANalytic Decision Optimization Module, is aimed at improving users’ decision-making in dynamic environments by providing real-time sensor fusion capabilities. It integrates inputs from a diverse array of sensors – including chemical, radiological, biological, video, and environmental – into a coherent and intuitive tactical display. This capability enables operators to concentrate on high-confidence events, thereby reducing the cognitive load and facilitating prompt, accurate decision-making. The system’s advanced analytics help users to detect events that might otherwise be overlooked, all while maintaining a low false-alarm rate.
The TANDOM software is housed on a mini-PC and is compatible with industry-standard I/O protocols, making it easy to integrate into various operational contexts, whether from a fixed base or an expeditionary mission or in individual warfighter applications. Key features of TANDOM include its sensor input-agnostic design, real-time operation and fusion, high scalability, and ability to learn continually which improves reliability over time. Interface independence, with support for formats including CoT and ISA, supports users on different military and tactical systems.
Arete | https://arete.com/
Vectornav | https://www.vectornav.com/
www.militaryembedded.com MILITARY EMBEDDED SYSTEMS June 2024 43
The promises and pitfalls of an AI-enhanced battlefield
By George Kamis, Everfox
In October 2023, the Biden administration issued an Executive Order focused on ensuring that artificial intelligence (AI) – which has captured headlines of late largely due to the rise of ChatGPT –is developed safely and securely. In a military context, this move will include the drafting of a memorandum, produced by the National Security Council and the White House Chief of Staff, that details how the U.S. military can ethically and effectively use AI to carry out its missions while also countering its use by adversaries.
Such guidance couldn’t come at a more opportune time. As AI continues to advance at an extraordinary pace, military and industry both must clearly understand the tools, processes, and procedures required of AI in a military context.
AI-enabled military tools in use
One promising area for AI on the battlefield is autonomous defense. Currently, Ukraine is using autonomous drones to identify and strike Russian targets. According to the Center for European Policy Analysis, AI automates the takeoff, targeting, and landing of uncrewed aerial systems (UASs). But automated defense systems have been around for some time now – and were doing AI-adjacent things before it was labeled as such. The Patriot Missile System, which the U.S. sent to Ukraine in the spring of 2024, was actually first used in combat in the 1991 Gulf War.
However, such systems are not immune to error. For example: During the war in Iraq, the Patriot identified a target as an Iraqi missile when it was in fact a U.K. fighter jet. This instance of so-called friendly fire offers an important lesson for the AI-enabled battlefield: A human should always be kept in the loop to vet the data and decision-making before a kinetic action takes place. Another area well-suited for AI is identifying changes

in surveillance videos; again, however, AI should not be making the final decision. Instead, it should simply alert someone to look more closely at the change in question.
Processing AI-generated insights
Artificial intelligence also has the potential to play an important supporting role on the battlefield, particularly when it comes to enabling and securing information-sharing. It’s no secret that the ability to access and exchange data is integral to collaborative warfighting. In Ukraine, for instance, social media content is being used to identify Russian assets. Open-source weather data can also play a crucial role in executing military missions.
To that end, the AI-enabled battlefield cannot exist without cross-domain solutions to serve as the information highway between data that exists at different classification levels. Cross-domain solutions ensure that all unclassified data is vetted and sanitized before it’s pushed up to a higher classification level. The benefits of this approach are twofold: the AI engine has a richer overall data set to analyze, while the algorithm’s integrity is maintained.
Because AI is so adept at analyzing large data sets, it also holds tremendous potential to improve cybersecurity, which is particularly important as cyberattacks play an evergrowing role in warfare. Russia, for one, has been carrying out cyberattacks against Ukraine for nearly a decade now. AI should definitely be part of the process of continuously monitoring military networks. Generally speaking, AI can spot anomalies and threats far faster than human analysts, including advanced phishing and malware attacks.
Establishing proper AI procedures
AI is undoubtedly going to impact the battlefield but it’s important to ensure that the hype around it doesn’t distort our expectations. While generative AI in particular created a lot of buzz this year, a recent report from Gartner (https://www.gartner.com/en/ articles/what-s-new-in-artificial-intelligence-from-the-2023-gartner-hype-cycle) asserts that we’re at the peak of its hype cycle. Many existing machine learning technologies have already been rebranded as AI because that’s where the money is. But while AI is transformative, it should still be conceptualized as a tool that must be vetted and supervised by trained military personnel.
Despite its immense computing power, AI should not be considered a silver bullet. It’s an extremely useful tool, but much like a calculator, AI is only as good as the data it’s given. To reap the benefits of AI, the military cannot focus myopically on the technology itself. Instead, the emphasis should be on building sociotechnical systems where people and computers work together to make decisions.
Put another way, AI should be treated as another knowledgeable person on the team, as opposed to a piece of technology that takes precedence over military decisionmaking. Thus, it’s crucial to train soldiers and other military personnel on the proper procedures for working alongside AI.
George Kamis is CTO of Everfox (formerly Forcepoint Federal).
Everfox • https://www.everfox.com/
BLOG
44 June 2024 MILITARY EMBEDDED SYSTEMS www.militaryembedded.com
Beware the buzzword
By Simon Collins, Abaco
Artificial intelligence (AI) is a real buzzword across all industries right now, but coverage across the media spectrum is not always helpful. We’re seeing mindboggling new technical capabilities being demonstrated each week, but it’s often hard to tie these to real-world use-cases; this, coupled with hype-tobust predictions and discussions about “artificial general intelligence” serve to further distort the narrative.
The defense industry is no exception –there are many instances where personnel could and should be kept out of harm’s way by increasing use of technology, including the use of machine learning (ML) to perform repetitive or dangerous tasks. However, linking the real operational use cases with nearterm capabilities – as well as articulating the aspirational use cases and the art of the possible – can be challenging.
In the world of physics, there is a relatively small number of people trying to find a single unifying “Theory of Everything.” However, for most practical purposes, Newton’s Laws of Motion have proved perfectly adequate for three and a half centuries. Similarly, instead of expecting a single “AI” to solve all our problems or a single robot to carry out all tasks, the reality is that incremental, well-bounded component parts will gradually begin to automate pieces of the whole.
In the defense domain, there are many problems well-suited to the application of AI and ML. In particular, cognitive overload driven by increasing numbers of increasingly high-resolution sensors and augmented by nontraditional data sources can cause damaging or even fatal delays in responding to a threat. This is an area where AI/ML is demonstrably able to help by trawling through this mass of data, classifying and correlating those items of genuine importance, and communicating and

presenting these to troops and commanders for assessment. We should not expect that aforementioned single AI to perform all of these tasks – in fact, small, bounded, and provable components of the whole solution will plug into existing tacticalawareness systems.
Pushing it to the edge
There are numerous challenges presented by the desire to process data in this way. Battlefield communication is limited in bandwidth and is subject to stringent security. To process such huge volumes of data necessitates inference close to the sensors, at the edge nodes on the tactical network. Deployment and updating of inferencing models to the edge nodes requires new infrastructure, as does recovery of sensor data relating to corner cases to inform the work flow of retraining new, more-capable models. Digital twins, synthetic data generation, and comprehensive simulation offline from operation are shown to have significant benefits in the creation of competent inferencing systems.
At each point in the battlefield domain, there needs to be an appropriate level of processing performance to deal with the increasing demands of applying, maintaining pace with the art of the possible that we see in other domains, such as on-road autonomous driving. The size, weight, and power (SWaP) of the computing systems will vary according to the capability of the platforms on which it will be deployed; larger platforms will be able to sustain high SWaP, and hence higher performance and greater capability, but all of the computing elements need to be able to survive the harsh environment of the battlefield.
Other defense use cases include application in logistics resupply and casualty evacuation; both of these can be extremely risky areas of operation and put personnel at significant risk of injury. Again, the AI/ML implementations will improve parts of these tasks in an evolutionary way – initially, think increasing automation of tasks, rather than a leap to full autonomy. The use of technology must serve to protect human soldiers, not to endanger them through error or unreliability.
There are many demonstrable ways in which AI/ML technology is gaining acceptance and proving to be useful without the need to wait for, or worry about, an allencompassing artificial general intelligence agent. We won’t see a “Terminator” style robot any time soon, and we should all be grateful for that!
Simon Collins is Director of Product Management at Abaco Systems.
Abaco Systems · https://www.abaco.com/
BLOG
www.militaryembedded.com MILITARY EMBEDDED SYSTEMS June 2024 45
CONNECTING WITH MIL EMBEDDED
GIVING BACK
GIVING BACK
By Editorial Staff
Each issue, the editorial staff of Military Embedded Systems will highlight a different organization that benefits the military, veterans, and their families. We are honored to cover the technology that protects those who protect us every day.

This issue we are highlighting Task Force Dagger Special Operations Foundation, a veteran-operated 501(c)(3) nonprofit, which has provided critical support to wounded, ill, or injured U.S. Special Operations Command members and their families since its founding in 2009.
Task Force Dagger’s three core programs – Health Initiatives, Immediate Needs, and Rehabilitative Adaptive Events – strive to quickly step in when there’s an emergency, provide next-generation health solutions for issues, and organize events that help Special Operations Forces (SOF) members with recovery.
Exposures and experiences shared among the SOF service members directly correlate with the many adverse health conditions they come home with, and the foundation’s staff wants to be in the forefront of raising awareness for toxic exposure-related illness. The SOF Health Initiatives Program enables access to functional medicine approaches for SOF service members and families that deliver lifestyle, integrative, and nutritional interventions. The goal of the program is to provide a framework for a personoriented approach to wellness that restores warfighters to optimal health.
Additionally, the Immediate Needs program assists service members and their families with immediate needs that are not covered by the U.S. Department of Defense, the Veterans’ Administration, or their health insurance; while Rehabilitative Adaptive Events for SOF community members and families are designed to offer encouragement and assist with the service member’s rehabilitation and recovery from service-related wounds or injuries. Family participation in activities such as scuba diving, white-water rafting, biking, or kayaking, fosters family bonding and teamwork necessary for overcoming service-related injuries and helps the family heal together.
For more information, visit https://www.taskforcedagger.org/.
PODCAST
McHale Report Podcast: With Guest Jake Braegelmann
Sensor processing at the edge, being SOSA aligned, and DoD acquisition process
The definition of “AI at the edge” often depends on whom you are speaking with and what market they are in. In the military electronics arena, Military Embedded Systems Editorial Director John McHale thinks that Jake Braegelmann, Vice President of Business Development at New Wave Design, has a very valid definition: Braegelmann says that the edge is where the sensor collects the data and AI can enable the filtering of that data in real time to get actionable intelligence to decision-makers.
In this podcast, McHale and Braegelmann discuss the concept of AI at the edge in depth; they also talk about the U.S. Department of Defense’s (DoD’s) modular open system approach (MOSA) mandate. Jake talks about what it means to be aligned to the Sensor Open Systems Architecture (SOSA) Technical Standard and dives into some common misconceptions about the standard. Jake also shares news about his company’s recent name change and its updated website.
Listen to the podcast: https://tinyurl.com/2pjf7swn
Listen to more podcasts: https://militaryembedded.com/podcasts
WHITE PAPER
How Minimizing Pulse Droop in GaN Power Amplifiers Improves Radar Range
By Michael Gurr, Analog Devices
Gallium nitride (GaN) power amplifiers (PAs) have enabled modern phased-array radar performance to greatly exceed prior generations with their high power density, reducing the need for bulky and lossy combining networks.

This white paper focuses on GaN PA pulse droop as a nonideality of real-world radar performance and covers the steps that can be taken to mitigate pulse droop’s negative impact on radar range. With advanced solidstate electronics inserted at the output stages for many radar RF chains, system engineers and designers can set specifications to achieve improved range, resolution, and sensing capabilities. Additionally covered: Devices that minimize pulse droop to meet the demands of today’s high-performance phased-array radars.
Read this white paper: https://tinyurl.com/2p9sh669
Read more white papers: https://militaryembedded.com/whitepapers
| PODCAST | WHITE PAPER | BLOG | VIDEO | SOCIAL MEDIA | WEBCAST 46 June 2024 MILITARY EMBEDDED SYSTEMS www.militaryembedded.com
www.militaryembedded.com
NAVIGATE ... THROUGH ALL PARTS OF THE DESIGN PROCESS





TECHNOLOGY, TRENDS, AND
PRODUCTS DRIVING THE DESIGN PROCESS

Military Embedded Systems focuses on embedded electronics – hardware and software – for military applications through technical coverage of all parts of the design process. The website, Resource Guide, e-mags, newsletters, podcasts, webcasts, and print editions provide insight on embedded tools and strategies including technology insertion, obsolescence management, standards adoption, and many other military-specific technical subjects.
Coverage areas include the latest innovative products, technology, and market trends driving military embedded applications such as radar, electronic warfare, unmanned systems, cybersecurity, AI and machine learning, avionics, and more. Each issue is full of the information readers need to stay connected to the pulse of embedded technology in the military and aerospace industries.
militaryembedded.com


































 Figure 1 | Image via Bell Helicopter.
Figure 1 | Image via Bell Helicopter.

 Figure 3 | Image courtesy The Spaceport Company.
Figure 3 | Image courtesy The Spaceport Company.







 Figure 2 | SATCOM telemetry validation with COTS NI PXIe modules.
Figure 2 | SATCOM telemetry validation with COTS NI PXIe modules.








 Figure 3 | Elma Electronic’s JetSys-5320, its NVIDIA Jetson TX2- based rugged AI-enabled computer.
Figure 3 | Elma Electronic’s JetSys-5320, its NVIDIA Jetson TX2- based rugged AI-enabled computer.
















 Figure 1 | The first four algorithms NIST announced for post-quantum cryptography are based on structured lattices and hash functions, two families of math problems that could resist a quantum computer’s assault. Diagram: N. Hanacek/NIST.
a quantum roadmap
Figure 1 | The first four algorithms NIST announced for post-quantum cryptography are based on structured lattices and hash functions, two families of math problems that could resist a quantum computer’s assault. Diagram: N. Hanacek/NIST.
a quantum roadmap











 Figure 2 | Typical connection from a GM to a clock target.
Figure 2 | Typical connection from a GM to a clock target.































