CHANGING THE SECURITY LANDSCAPE























PROTECTING HIGH-THREAT FACILITIES & CRITICAL INFRASTRUCTURE
Secure your checkpoint with our industry-leading X-ray inspection, optical inspection, and radiation detection technologies that help to uncover threats and identify and authenticate vehicles and occupants. Automate processes, control workflows, and obtain actionable intelligence with our CertScan® data integration platform from sister company, S2 Global. With our end-to-end checkpoint security technology and expert program management and support, we can help you maximize threat detection and operational success. rapiscan-ase.com
EDITORIAL
Publisher
Barry Bebbington +44 1708 229354 Barry@pubint.co.uk
Editor Cora Lydon +44 7834 244613 cora.lydon@securitymiddleeastonline.com
ADVERTISING
Worldwide
Mike Dingle +44 1752 267330 mike@securitymiddleeastonline.com

Gareth Driscoll +44 1752 260603 gareth@securitymiddleeastonline.com
Ryan Bickerton +44 1752 265802 ryan@securitymiddleeastonline.com
Rahul Vara +44 1752 604352 rahul@securitymiddleeastonline.com
Kyle Kennedy +44 7867 641955 kyle@securitymiddleeastonline.com
Marketing Manager
Paul Riglar +44 7496 377630 paul@securitymiddleeastonline.com
PUBLISHED BY Publications International Ltd
1708 229354
What a month May was! We’ve been overwhelmed with the support and praise that we received following our rst-ever Security Middle East Conference. As the longest-established and leading print security title in the region, it felt particularly important that we play our role in bringing together the sector’s foremost thought leaders and industry experts to help shape the future of security.
We’re at an exciting time – technology is evolving at pace and now it’s vital organisations understand how to implement this technology and how it can be used to boost security operations. We also have the ongoing e orts to support Saudi Vision 2030 and the challenges that brings, the drive to bring more people into the security sector and the growing threat of ever-more complex cyber attacks to contend with.
We were delighted to be joined by over 200 industry professionals on the 9th May who were eager to hear from our keynote speakers and panellists. We tackled some of the most pressing issues that our readers are facing and debated how to ensure the sector continues to move forwards. We hope that those
who attended went home with lots of new connections made and plenty of inspiration, success stories and ideas.
The Security Middle East community will be instrumental in driving change for the better, with the foundations for deploying strategic initiatives all debated and discussed at the Security Middle East Conference in the rst instance.

You can read more about this exciting event on pages 16 and 44. And if you missed it, you’ll be pleased to hear that work has already started on next year’s event, which promises to be even bigger and better.
Cora Lydon Editor cora.lydon@securitymiddleeastonline.comsmemag Security Middle East Magazine

03 Up front Foreword from the Editor
06 News Monitor
The latest regional and international security news
11 Market Monitor
A roundup of the latest security products and solutions
16
16 Security Middle East Conference
Our first conference proved to be highly successful with over 200 guests flocking to Riyadh to hear from our speakers and panellists
44 Chairperson’s round up Daniel Norman, Security Middle East Conference Chair, looks at the key points that came out of May’s conference in Saudi Arabia

38
47 Industry interview
Security Middle East Conference advisory board member Meshal Aljohani speaks to Bander Alharbi, Manager Safety and Security at King Abdullah Petroleum Studies and Research Center (KAPSARC)
FEATURES
22 AI in policing
Ashley Beck from SAS looks at how to empower a more equitable society through challenging unethical artificial intelligence
28 Counting the costs
ISSUE 132 MAY/JUNE 2023 42
Toni El Inati, Barracuda Networks, discusses how to keep a lid on spiralling data breach costs
30 The cost of human error
When it comes to cloud data breaches, human error is the number one threat, according to Thales’ 2023 Data Threat report

34 License to secure
Ekaterina Mutina from TRASSIR discusses automatic recognition systems for vehicles
38 Protecting data with physical security

Kim Rahfaldt, from AMAG Technology, writes about how vital is it to involve physical security in your cybersecurity discussions
42 The challenge of merging OT and IT
According to Hadi Jaafarawi of Qualys, OT security leaders need to lead executives to a ‘this could happen to us’ epiphany to avoid disaster
49 Cybersecurity: more than what it seems
SPA member, Guarav Saxena from Insprago Digital Solutions, looks at why cybersecurity is not just the responsibility of organisations
50 Events
Diary dates for forthcoming security exhibitions, conferences and events
The Technology Innovation Institute (TII) has launched the TII McEliece Challenges and is inviting participants to assess concrete hardness of the renowned McEliece cryptosystem by solving multiple challenges.
The challenges aim to strengthen understanding of cryptosystems that are used globally to protect privacy of individuals and organisations.
The McEliece cryptosystem is a public key encryption scheme with a reputation for resilience against attacks. Led by TII’s Cryptography Research Center (CRC), participants will be able to validate the security of the McEliece cryptosystem and, in doing so, identify possible weaknesses.
The year-long challenges will involve multiple McEliece-based cryptanalysis problems with increasing levels of difficulty
that explore three different tracks –Theoretical Key Recovery Algorithms, Practical Key Recovery, and Message Recovery.
Dr Najwa Aaraj, Chief Researcher, Cryptography Research Center, said: “In addition to providing breakthrough enhancements to the current McEliece cryptosystem, the challenges give us a
INTERNATIONAL NEWS
Analysts at the World Economic Forum are predicting that globally we’ll see 83m jobs vanish, replaced by new technologies such as machine learning, automation and AI.
The Future of Jobs Report 2023 reveals that bank tellers and related clerks, postal service clerks, cashiers and ticket clerks and data entry clerks are most at risk of their jobs becoming extinct. At the other end of the scale, the fastestgrowing jobs include AI and machine learning specialists, business intelligence analysts, digital transformation specialists and information security analysts.
Those in the tech-heavy security sector are likely to already have many of the skills required to keep pace with the evolving job market. In the report, researchers believe that the fastest-growing job sectors could expand by as much as 30% each year until 2027.
first-hand look at how the UAE’s brilliant young minds work to solve complex issues and find novel remedies to some of the world’s toughest online problems. We hope the multiple tests we present to the participants and their outcomes will further strengthen and confirm the resilience of the McEliece system.”
INTERNATIONAL NEWS
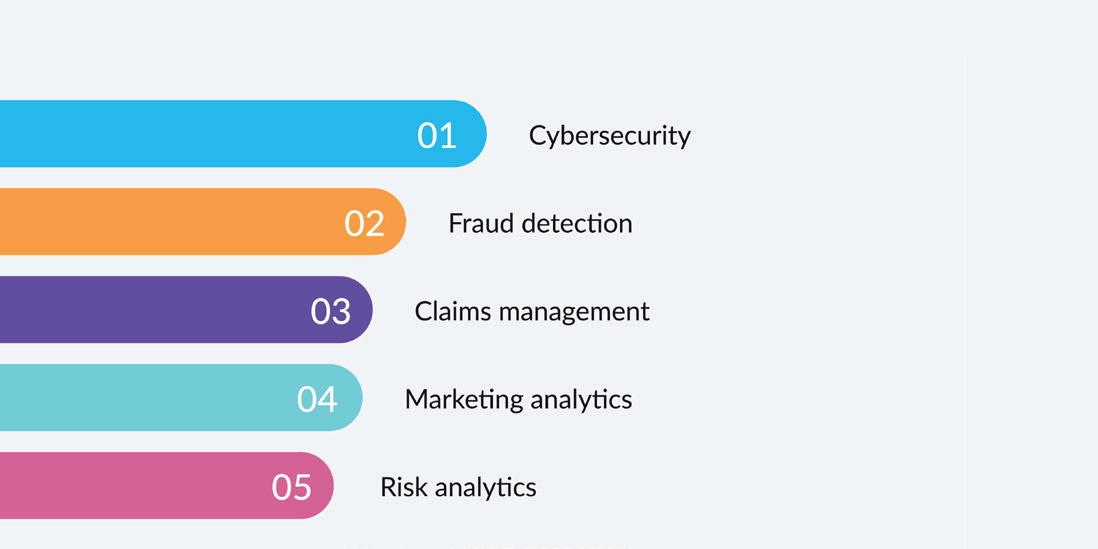
According to a Snowflake report, the world’s leading financial firms are accelerating their move to the cloud in order to strengthen cybersecurity and fraud detection. A combination of high profile cyber attacks and financial crimes with increased media and regulatory scrutiny has spurred IT teams into making cloud investments in order to protect data and maintain high levels of security and governance.

Primary business use cases organizations are looking to run in the cloud
REGIONAL NEWS
According to the State of the Market Report 2023 from Help AG, organisations across the Middle East are prioritising automation and consolidation of their cybersecurity estates
As the cybersecurity arm of e& enterprise, Help AG’s report is the only one of its kind to focus exclusively on digital security in the Middle East region. The 2023 report focused on how organisations can innovate their technology and processes and automate playbooks and operations to elevate their cybersecurity posture.
It also highlighted a number of trends for organisations to be aware of in 2023 and beyond to ensure they stay ahead of the curve:
Integrated cyber defense: With threats becoming more numerous, persistent and sophisticated, there is a need for contextualising all data points into a single action thread as a comprehensive defense against threats.
Secure cloud enablement: Ensuring a secure cloud posture involves identifying and remediating security issues,
managing and securing access to cloud resources, and complying with regulations and industry standards.
Security services edge: One of the key considerations while adopting security services at the edge in the Middle East is the growing importance of data privacy and the need for local content inspection.
Data and identity protection: Identity has become the new security perimeter. Adversaries are also reciprocating by targeting identities and gaps in governance. A very strong Identity Governance and Administration (IGA) practice will become a core requirement of security operations, and we can expect to see more focus and more investment in this area in 2023.
Internet of Things security: The IoT is the future, and organisations should aim to achieve comprehensive visibility and perform asset discovery, creating solid baseline measures for security in IoT devices, including security from the start of IoT project planning, adopting a strong zero-trust strategy, and enabling SecOps to detect, prevent and mitigate security incidents.
In its 30th year, the International Hologram Manufacturers Association (IHMA) has announced changes to its executive board.
Dr Paul Dunn is to continue for another year in his current position as Chair of the board. Ondřej Fedorčák (above) from Optaglio has been elected to the board.

Dr Dunn said: “The IHMA continues to
The United Arab Emirates has cancelled a contract with Airbus, worth nearly €800m. The contract was for 12 H225 Caracal multirole helicopters, and has been cancelled for financial and technical reasons, according to Breaking Defense.
DUBAI
Magnum Security, one of Dubai’s leading security companies, has opened its AED£55m state-of-theart accommodation facility in Jebel Ali’s Labour City. It includes training rooms equipped with the latest technology to ensure staff have the necessary knowledge and skills to carry out their duties.
According to Kaspersky, attacks were detected on 27% of industrial control systems (ICS) computers in the Middle East during Q1 2023.
BAHRAIN
According to the National Cyber Security Centre’s Chief Exec, businesses in Bahrain could soon be offered protection against cyber criminals. The protection would be offered as part of a low-cost service, with the centre planning to negotiate with telecom companies.
DUBAI
move forward and work with members and organisations to ensure that it remains a strong advocate, industry voice and effective resource for the industry in the future.
“I look forward to working with colleagues in this, the IHMA’s 30th year, helping our industry secure growth and innovate, as well as ensuring all involved in holography come together as one to secure the opportunities available for growth.”
The Emirates has now implemented digital boarding passes at Dubai International Airport. Passengers checking in at DXB Terminal 3 will now receive their mobile boarding pass by either email or SMS.
The Kuwait Interior Ministry has announced that it will be introducing biometric technology to all border crossing points, in line with its strategy of using the latest tech to enhance border and state security.
QIIB has been awarded the highest certification in cybersecurity and Payment Card Industry Data Security Standards (PCIDSS) by SISA for the eighth consecutive year.
The awards are handed out to recognise banking institutions that offer the best security standards and protection for their customer information – such as the PCI-DSS which specifically involves the protection of bank cards data.
QIIB has established advanced technological infrastructure in order to
A delegation from the United Arab Emirates, including representatives from the Supreme Audit Institution UAE and the Abu Dhabi Accountability Authority, has paid a visit to India’s Central Vigilance Commission and The Controller and Auditor General of India.

The strategic visit took place at the end of May and aims to build strong relationships in the audit and anticorruption fields. In addition, it is hoped it will bring mutual benefits from other initiatives and best practices.
A spokesperson for the Supreme Audit Institution (SAI) said: “The SAI UAE is continuously working to build strategic relationships with various authorities around the world, and this visit is an embodiment of our aspirations to build strategic partnerships and benefit from the best practices to improve and unify efforts aimed at combating corruption in line with the highest international standards, which is a goal we share with ADAA to ensure optimal use of public funds and resources to ensure its sustainability for the future generations.”
enhance its banking services.

Mohammad Jamil Ahmad Hamad, Chief Risk Officer at QIIB, said: “QIIB’s success in achieving the required standards for obtaining this certification is translated in the huge progress made by the bank in the field of digital transformation, as it continues to invest in its digital solutions in parallel with its increased investment in security and protection solutions for all its operations and customers’ information, and it reflects the bank’s investment in combating cybercrime, hacking and cyber fraud”.

According to insight from Future Market Insights, the global aircraft surveillance systems market is set to experience huge growth in the coming years, reaching an anticipated US$299.32m by 2033 – up from US$178.59m in 2023. These technologically advanced monitoring
tools are used to track an aircraft’s security operations, helping to safeguard passengers and deliver live footage of aircraft activity. International aviation regulatory organisations require every airline operating service to equip their fleet with a video surveillance system, and this becomes more vital with the rise in terrorist threats and assaults.

Protecting institutions, enterprises and strategic infrastructure is a constant challenge that requires very specific and constantly up-to-date knowledge and skills. With 115,000 security events monitored per second, over 1,800 cyber alarms managed and 100,000 users protected a day, Leonardo offers its knowledge and technology and an international centre of excellence that provides cyber security specialists with immersive training experiences. To protect against physical and cybernetic threats in our increasingly digital world, and to advance the promotion of a new culture in security.








Despite a continued increase in cybersecurity spending in the UAE and Saudi Arabia, organisations in the region are still poorly equipped to handle the cyber threats being thrown at them. According to new research from Trellix, 66% of CISOs in the UAE and KSA still believe their organisation lacks the right people and processes needed to be truly cyber-resilient. In addition, almost three quarters believe that their current technology set-up is insufficient.
Khaled Alateeq, Head of Middle East, Trellix (right), said: “What comes across most in this study is not the lack of investment. There are plenty of signs that commitments in this regard are on the rise, including the fact that only 36% of respondents cited budget and resource challenges.
“What emerges here is more of a misdirection of investment. We must ensure the right people and processes are in place for sure. But it is worrying that
Boasting strong security features, the RP-LPITE-442XGME industrial L2/L3 managed Ethernet switch from barox is ideal for end users looking to deploy a capable and cyber-secure managed switch for IP surveillance camera networks.

The solution provides continuous monitoring of powered cameras, and in the event of a camera failure, the switch will automatically attempt a camera reboot.
An important feature for high security applications, it also has functionality to allow all connected cameras to stay powered, meaning no vital footage is lost during routine engineering procedures.
Rudolf Rohr, barox Co-founder & Managing Partner, said: “barox’s expertise in the video and data
transmission sector has developed a real gamechanger switch, delivering Layer 3, including OSPFv2/v3 routing protocols and 10Gb capability to the industrial access world, and providing customers with cutting-edge Ethernet and PoE transmission technology.” www.barox.de
amid all the budget increases, we are not yet seeing the right tech in place.
“CISOs are telling us plainly that ‘more solutions’ is not the answer. They need a platform approach that is open and capable of learning and adapting to build a proactive defence. CISOs and their teams must be able to see, protect, and resolve. They must be able to maximise visibility and peer into every corner of the enterprise. They must be able to have coverage of every asset and be equipped with unrivalled discovery speed when picking up on potential threats. And they must be able to automate their response across this connected security ecosystem to keep their organisation from becoming the latest victim of the threat landscape.”
www.trellix.com
Analytics firm SAS is to invest US$1 billion over the next three years to develop advanced analytics solutions. Solutions will be focused on key industries including: banking, government, insurance, healthcare, retail, manufacturing and energy.
The billion-dollar investment includes direct research and development, industry-focused line-of-business teams, and industry marketing efforts.
SAS CEO Jim Goodnight, said: “Through this investment, SAS will continue to support companies using AI, machine learning and advanced analytics to fight fraud, manage risk, better serve customers and citizens, and much more. We remain steadfast in our ongoing commitment to innovation while delivering the market’s best analytics.” www.sas.com
Teledyne FLIR has announced the new Boson+ CZ 14-75, which will reduce development and operational risk and costs. Its 5X continuous zoom lens maximises performance, simplifies development and streamlines manufacturing supply chain.
The new product is ideal for unmanned aerial vehicles, perimeter surveillance, light armoured vehicle situational awareness and targeting and soldier sighting systems.
Dan Walker, Vice President, Product Management, OEM Cores, Teledyne FLIR, said: “The Boson+ CZ 14-75 camera and lens are factory-designed and integrated to optimise performance and reliability.
“Thanks to flexible and advanced lens control electronics, industry-leading 20 milliKelvin (mK) thermal sensitivity, and US-based integration support, the Boson+ CZ 14-75 streamlines development for applications requiring high-performance infrared zoom capability.” www.flir.com/bosonpluscz

British security training company, Stadium has agreed a Memorandum of Understanding with the Saudi Excellence Company to open a training academy in Saudi Arabia.
After playing a key role in last year’s FIFA World Cup in Qatar, Stadium LLC – the Qatar-based subsidiary of Stadium – will be overseeing the training of thousands of Saudi nationals in event management and safety.
The MoU will help the country to host a wide variety of international sporting events in the future, which feeds into Saudi Arabia’s Vision 2030 plans.
David McAtamney, Owner and Founder of Stadium, said: “This is a really exciting agreement which will help to play a key role in propelling sport and expanding industry in Saudi Arabia – a country which has a tremendous appetite for live events and is making significant waves in the world of sport…
“Our move into the Middle East began with the opening of our sister company Stadium LLC in Doha, Qatar, in 2020, and our plans to open a new training academy in Saudi Arabia is an exciting new chapter for us as we expand the business. www.wearestadium.com
Qognify, a leading provider of video and enterprise incident management solutions, and Johnson Controls Security Products, a unified group of access control, video, locationbased security and intrusion brands, have announced an integration between their products Qognify VMS and Kantech EntraPass.
The software integration will deliver a better understanding of situations based on the synchronisation of event and video data, which will allow for a faster and more targeted response.
For example, ‘forced door’, ‘doors held open’ and ‘clearance’ alarms from EntraPass can be displayed as events within Qognify VMS and synchronised to the associated video recording.
Jeff Tousignant, Integrations Product Manager at Johnson Controls Security Products, said: “The integration of EntraPass with Qognify VMS increases operational efficiencies by ensuring that operators are presented with all relevant information in one user interface. This helps to save time and facilitate decisions – when every second counts.”
www.qognify.com
www.johnsoncontrols.co.uk

Maé Tholoniat: Optimising parking access is part of a global reaction to the smart city and the explosion of urbanisation. Wasted fuel, stress, unproductivity, air pollution...motorists suffer the consequences of traffic worldwide. At the entrance to the parking lot, the scenario is repeated. Parking lot managers will therefore look for solutions that make access more fluid.
But this need for simplicity should not take precedence over safety. Why is this? The parking lot is the first point of entry to a facility. Whether it is underground or above ground, it usually has a direct connection to the building. In addition to unauthorised parking, theft, break-ins, or vehicle damage, the absence of secure access becomes a source of vulnerability to the intrusion of malicious individuals (acts of vandalism, terrorism, etc.). Therefore, securing access to vehicles and even to drivers, while ensuring the management of different profiles (employees, visitors, temporary staff, etc.) becomes critically important!
Maé Tholoniat: Vehicle access must be as intuitive and secure as personal identification. The security offered by UHF technologies goes far beyond simply reading license plates, which only allows a filtering capability and does not guarantee access security, as license plates can be easily copied or usurped.

The driver has a 100% passive UHF tag on his windshield, the Teletag®, which offers unlimited life, constant performance, quick return on investment, and a high security level.
When the driver arrives at the parking entrance, the vehicle is automatically
detected without having to stop or lower the window. How does it work? With the SPECTRE long-range UHF reader mounted nearby. Perfectly secure, discreet, and scalable, SPECTRE offers comfortable and reliable long-distance reading. It is market leader today!
Another important point is that parking lot access control may require the management of different sized vehicles and multiple lanes. The parking operator can then opt for a multi-antenna management. 1 to 4 antennas can be connected to SPECTRE. SPECTRE meets all security requirements and configurations – a heterogeneous fleet of vehicles (light, heavy, motorcycles, etc.), separate access control for up to 4 vehicle lanes – for smooth management at optimised costs.
Maé Tholoniat: The smartphone has become a “key.” It is already used to unlock your vehicle! We anticipated this development by creating the SPECTRE nano! With SPECTRE nano, we are reinforcing the level of security by identifying the vehicle and/or the driver. The identification mode is adapted to the level of security required.
In conjunction with STid Mobile ID®, SPECTRE nano guarantees high security and fluidity of access by reading:
n Virtual badges for visitor access management
n Teletag® for vehicle access
n Both simultaneously to identify the vehicle and its driver
Access rights are thus controlled in real time: the system guarantees that the vehicle can enter the parking lot and that the driver is authorised to enter.
An important point: the same virtual badge can also be used for both parking and building access. A single badge will manage all access! What’s more, in addition to managing all access (infrastructures, buildings, parking lots, etc.), the virtual badge will offer a whole hub of services (recharging cafeteria badges, booking meeting rooms, using printers, etc.) for greater flexibility within companies!
The parking lot manager is free to choose the solution that best suits his or her needs: SPECTRE and SPECTRE nano are perfectly suited to the most demanding security policies.
stid.com
Maé Tholoniat, Product Marketing Manager at STid, explains how to make parking access more fluid whilst still maintaining a high level of security
... BUT MORE IMPORTANTLY I’M THE FASTEST AND MOST SECURE WAY TO ACCESS YOUR CAR-PARK

With my combination of UHF and Bluetooth® technologies, I recognize your visitors, employees, their vehicles or even both at a glance. I will comply with your security policy. Together, we will manage all of your access points. Your security will be under control from end to end, even in the most challenging situations.




My compatibility with the STid Mobile ID® ecosystem enables the use of smartphones and virtual cards to access all of your organization’s critical infrastructures.
My ability to support hands-free identification will provide you with a smooth access control experience without compromising on security.
Over the course of one day, hundreds of top-level security professionals gained the chance to hear from the industry’s thought leaders, as well as network and make new connections with other sector executives at the first-ever Security Middle East Conference

The Crowne Plaza Riyadh Palace Hotel was our host for this event, which took place on May 9th 2023. Our guestlist was made up of some of the security industry’s top level executives, those who were ready to contribute to the conversations being had around the future security landscape and the journey to get there, and who were excited to hear from our keynote speakers and panellists. The 200+ guests included representatives from The Public Investment Fund (PIF), NEOM, Saudi Aramco, Royal Commission for Al Ula, Saudi National Bank and Saudi Air Navigation Services, and comprised c-level decision makers, security influencers and industry thought leaders. We were delighted to welcome so many high pro le and influential guests with a guest list to rival the who’s who of security.

A er a brief co ee reception as we welcomed our guests to the hotel, we were settled into the main room. Daniel Norman, Regional Director, EMEA at the Information Security Forum (ISF), took the stage to welcome everyone to this exciting event and set the scene for our audience, before launching an introduction video. This video helped set out the aims for the event and
focused on the importance of the Security Middle East Conference 2023 and its role in bringing together c-level decision makers to help shape and de ne the future of security in Saudi Arabia and the wider Middle East region.
Norman took on the role of conference Chair, introducing each speaker and our panel members. The rst keynote speaker Norman introduced was Abdulrahman AlFadhel, who is a former Re nery Manager for Saudi Aramco. He spoke knowledgeably to our audience about how vital it is for organisations to work with security services.
In his example, he explained that should the re nery be shut for a single day, the potential costs could be signi cant – as high as 1.5m rial. He focused on building collaboration, particularly important during the maintenance shut-down period of re neries. He also conveyed the importance of properly running a re nery in order to save lives and establish the backbone of the Saudi Arabian economy.
www.securitymiddleeastconference.com
Following Mr Al-Fadhel’s enlightening keynote it was time for our rst panel discussion of the day. The topic was addressing the talent gap in Saudi Arabia’s security sector and our panellists were in good hands with Luke Bencie, Managing Director of Security Management International, LLC moderating the proceedings. He was responsible for guiding discussions with Khalid Alghamdi, Chief Executive O cer, NOMD Security Solutions; Rakan Alsharekh Chief Human Resources
O cer, SAFE; and Rear Admiral Muneer Almehanna sharing their own experiences on the panel.
This panel proved popular with lots of audience engagement from people obviously keen to explore how to address one of the sector’s most pressing challenges. The focus was on career paths, education and what is actually causing the talent gap – our panellists determined that a real issue was technology moving faster than people can actually keep up with.
A short break for refreshments followed
and gave our attendees the opportunity to interact with our sponsors, who had lined the break-out space to share their own expertise and solutions for keeping on top of security challenges. Our sponsors for this event were Genetec, Eagle Eye Networks, Obvious Technologies, Darktrace, Axis Communications and the ISF, with SAFE, Security Professionals’ Association for SIRA (SPA) and The Security Institute also supporting the event. We were also delighted to have our Education Partner on board, The University of South Florida, who supplied our attendees with accreditation in the form of a digital badge and a certificate confirming their dedication to furthering the industry.
Once everyone had had their chance for a quick revitalising break it was straight on to our next keynote speaker: Steven Kenny from Axis Communications. Kenny immediately sparked intrigue with the line: “This is how a 17-year-old cost TalkTalk hundreds of millions of pounds… just because he could.”
He then underlined how vital it is to understand that a group doesn’t need to be funded or organised – or indeed even a group – to cause a massive data breach, using the global telecoms company case study as his captivating example. The onus, he hammered home to the listeners,
is on the organisation entirely.
We hope his stark warning – that a disgruntled nobody with half-decent computer know-how has the potential to cripple a company – is one everyone takes on board. The key learning for our audience was that any piece of technology that is part of a company’s wifi could be the company’s downfall if not adequately protected.
Our final session before lunch was the Smart City development panel discussion which was moderated by Professor Borhen Marzougui. He was joined on stage by Craig Ross, Senior Safety & Security Manager, Diriyah Gate Development Authority; Dr Mohammad Alketbi, Founder, Forceis Security; Dr Mohammed Aladalah, tech security expert; Wissam Acra, Middle East Sales Director, Genetec; and Mohammad AlMajed, Product Development Director, TAHAKOM.
Our expert panellists took it in turns to share their thoughts on what really is a smart city. The overwhelming take-home was that a smart city needs to be more than just futuristic and digital. Rather, a smart city must be fully connected for the benefit of residents and this includes the physical elements too.
With our panellists’ words of wisdom still ringing in their ears, it was time
for our guests to enjoy lunch. While it goes without saying that they enjoyed the various buffets laid on and the pleasing surroundings of the downstairs room complete with water feature – the networking opportunities here were the star of the show.
Guests hopped from table to table, making new acquaintances, greeting old ones and generally forging and building on connections for the benefit of their careers. This was a great opportunity for the audience to network in an informal way and with the benefit of the past few hours still fresh in their minds. With plenty of useful connections made, within the hour it was time to return for the final sessions of the day.
Taking the spot directly after lunch was always going to be a tough gig, but Salman Alghamdi’s keynote speech was packed with information to help elevate security professionals’ career and knowledge, ensuring all eyes were firmly on him.

He spoke about the digital transformation we’re seeing within industrial security, touching on change management and stressing the importance of understanding the role of, and reading, morale in your business. Through implementing high security protocols it is possible to essentially control the presence of your business, he told us, as he delved further into the journey of a business.







While Daniel Norman had been everpresent throughout proceedings, introducing guests and panellists, he took to the stage as moderator for our nal discussion panel. Resiliency in the Age of Digitisation was being debated by our panellists: Ibrahim Al-Asaker, Saudi Chapter Lead, Cloud Security Alliance; Dr Faisal Abdulaziz Alfouzan, Assistant Professor in Cybersecurity and Networks; Khalid Saad Al Medbel, General Director Information Security, Ministry of Health; and James Connolly, Director of Strategic Engagements, Darktrace – who this panel was arranged in association with.
There were plenty of discussions around Saudi Vision 2030 – where we are now and where do we need to be? There was also many stories shared of battling malware, with our panel members recalling for the audience how they’ve interacted with malware and threat actors. Norman also explained more about the simulations that are run by the ISF to help keep cyber professionals’ skills fresh.





With the day about to draw to a close there was just time for Norman to thank our Advisory Board who were
instrumental in helping identify, develop and re ne the topics we covered at the conference. Helping to shape the content and feel of the event were Turki Al Shalhoub; Meshal Aljohani; Sami AlThowaini; Daniel Norman; Alaa Dalghan; Luke Bencie; Dr Mohammad Alketbi and the editor Cora Lydon.
He also extended our thanks and gratitude to our event sponsors – Genetec, Eagle Eye Networks, Obvious Technologies, Darktrace, Axis Communications and the ISF, without who the event would still be top of our wish list. And also the support of SAFE – who provided security at the event –, SPA and The Security Institute, as well as The University of South Florida for joining as our Education Partner.
This invite-only event more than met its goal of shaping future security solutions by giving a stage to leading gures to share their knowledge and encouraging collaboration and the exchange of ideas between speakers, panellists and the audience.



In fact, so successful was the event that we’re already turning our attention to the Security Middle East Conference 2024. We look forward to bringing you news of the next edition of this industry-de ning event in the coming months.



Decision-making processes within policing incidents and investigations have many elements which are fed by information at each stage. The importance of data with integrity that is representative of all information available is crucial to ensure decisions are made using the entire picture. If officers don’t have a clear representation of all information this can lead to catastrophic consequences.
Using Artificial Intelligence (AI) and analytics, to support investigators with insights, can increase the level of efficiency and effectiveness in performing reactive and proactive duties. It also helps law enforcement gain the much-needed trust and confidence of the communities they serve, providing them with the information they need to safeguard people from harm, whether physical, emotional, or financial.

There are many benefits that AI solutions bring to the world of law enforcement. Yet, poor design or misuse of these solutions could cause irreparable harm to society. For example, AI systems are vulnerable to biases and errors. The output quality of any AI analysis depends heavily on the quality of the provided data; if the data is already biased, then the program will replicate it into the results. Therefore, the development of
AI systems must always be conducted in a responsible manner, closely built with investigators aligned with their objectives.
When it comes to the development of ethical AI technologies for law enforcement, it is essential that these are being built alongside each police department, ensuring people from different specialisms, different cultures and experiences – and crucially, the people who will use the technology – are involved. This approach injects breadth and depth of understanding to extract real value from every piece of data owned and received by law enforcement. Having a deep understanding within the investigation of ‘The Policing Objective’ and ‘What data translates to valuable information?’ is critical to encourage focus and improve efficiencies to protect people, while taking cognisance of privacy and civil liberties.
For instance, if an investigator is faced with thousands of lines of data that have been legally obtained for a policing purpose, and this data includes information that is unrelated to the investigation, such as personal information belonging to a completely
unconnected person, this can increase the risk of collateral intrusion. However, if this data is weaved with indications of serious criminality, then how do investigators minimise the intrusion of privacy, while maintaining their ability to understand the identity of subjects/suspects and the risk that they present, from that data?
This is where ethically developed technology that embeds trust and confidence into its use, and maintains human involvement at the heart of its development, comes into the picture.
AI technologies work well only when they are used to enhance – not replace – human decision-making. AI systems do not understand our goals in society by default. When working to improve law enforcement, as well as criminal justice, we need to inform systems of our goals in order to achieve them in an equitable and fair manner. We also have to ensure that the stakeholders who inject value are involved at every stage, including pre- and post-implementation of technological support solutions to gain differing perspectives of output and impact. We need to learn from experience and from data owned by significant
Ashley Beck, Senior Industry Consultant – Global, Fraud & Security Intelligence Division at SAS, looks at how unethical AI challenges within policing can help to empower more equitable societies

“How do investigators minimise the intrusion of privacy, while maintaining their ability to understand the identity of subjects/ suspects and the risk that they present, from that data?”
others as well as law enforcement organisations, to feed back into the technology and support the prevention of further victims as well as detect criminals, stopping them in their tracks.
The sources of information to support this approach could be derived from many data streams, which perhaps wouldn’t be immediately obvious. An example of this is an anonymous survey of young people to understand the volume and types of exploitation that have gone unreported. Questions could be asked like, how many children have been randomly contacted by a stranger? On what platform did this occur? Understanding not only the information reported to police, but also using data external to the organisation can be key to the development of technology that can truly capture, elevate, and illuminate the threat and risk posed that law enforcement agencies need to act on quickly as a result.
Post-pandemic, we have witnessed an 83% rise in children being targeted by strangers looking to exploit them. If we combine survey information, thirdparty organisation and public sector data, alongside policing data, this could generate an enhanced proactive approach to tackle a growing problem where children remain at risk online on a daily basis. On a recent exercise carried out, an account was created on a mainstream platform where the settings were set to public. A video was posted of a child playing with collector cards associated with children. The focus of the video was only on the child’s hands. Within six minutes the account received a message from a stranger: “Hi”. On reviewing this account, it appeared that there were various posts that would appeal to young boys. Further investigation revealed that this account belonged to an adult male. The risk to children who are trusting and could perceive this account as being
another child, is real.
Data can elevate the understanding of modus operandi in the criminal world, which can enable the translation of a preventative message to communities and also feed into the enhancement of technology to further enrich future law enforcement capabilities.
Anyone who develops technology that enhances decision-making with automated, data-driven insights should bear the responsibility for transparent and equitable outcomes. There are a number of ways that we can ensure transparency and accountability in a joint venture between software vendors, policing agencies, and national security organisations. But first, can the process behind that decision be explained?
As a result, we have to make sure that not only is the investigator able to explain decision making to authorities, the public and the judicial system, but also the police officers themselves need to understand the objectives, capabilities, and limitations of AI. In order to inspire public confidence and trust, ensuring that the data is explainable to different people is of utmost significance. Through the development of linguistic rules, for example, investigators would have a clear vision as to why data elements are being presented to them. Users would also be presented with the probability of an event occurring, therefore, sieving the data and creating rules and alerts to generate action quickly. They would also understand clearly why data has been omitted from the extraction, therefore allowing a truly ethical, informed decision with the support of technology.
Machine Learning can also be utilised to feed into the explainable rules, creating an ecosystem of development,
extraction, and decision-making that is ethical, trustworthy, and transparent. Accountability starts and ends with the law enforcement professional who uses AI to make a faster, better-informed decision. The initial collection of data plays a major part in this discussion as well.
Another point we should keep in mind is that most law enforcement professionals did not sign up to be data scientists. Therefore, the emphasis is shifting to education and training in policing, which is crucial to eliminate the fear of data and digital evidence or intelligence gathering. Investigations have changed dramatically over the years, where the sentiment of ‘every contact leaves a trace’ transformed from purely the physical space of DNA, CCTV, etc. to add in the digital landscape to the areas where evidence would exist and hold real value. Police officers are very keen to learn because this shift towards gathering digital evidence has been recognised. They desperately want to stay ahead and be able to investigate and explain complex crimes. So, ongoing education and training play a huge part in elevating the investigative capability.
In order to ensure ethical use of AI, law enforcement organisations need to partner with a technology company that essentially enables the organisation, the technology, and the police officers to grow and learn together collectively. Most importantly, they need to make sure that this is not just a textbook exercise. This way, remaining ahead of the curve is achievable. www.sas.com
“Machine Learning can also be utilised to feed into the explainable rules, creating an ecosystem of development, extraction, and decision-making that is ethical, trustworthy, and transparent”
Introducing the new Vue Consoles. Seeing consoles in a brand new light. Configurable. Connectable. Adjustable. Just plain more than able. And able to accommodate multi-operator solutions. Static or height adjustable. Horizontal / vertical adjustable monitor mounts offer complete ergonomic viewing. Or should we say Vue-ing? Because everything allowing a mission critical room to operate with 100% focus went into every design detail. This is productivity by design.




Begin the mission at winsted.com
winsted.com
ALL ADVANTAGES IN ONE PRODUCT
COLOR IMAGING
HIGH RESOLUTION IMAGING
CLEANING SYSTEM
FLUSH MOUNT HOUSING
FULLY TRAVERSABLE
FULL VIEW OF UNDERCARRIAGE

AUTOMATIC COMPARISON FEATURE


OTHERS:
ONLY BLACK/WHITE IMAGING OR LOW CONTRAST COLOR IMAGING
LOW RESOLUTION
BADLY ILLUMINATED UNDERCARRIAGE

MISSING DOOR SILLS / RUNNING BOARDS


As the Middle East makes a concerted effort to grow its knowledge and skillsbased economy, the role of data in driving innovation, transformation and success cannot be overstated. From unlocking unparalleled insight into consumer preference and behaviours and uncovering opportunities to optimise processes, to identifying entirely new means of revenue generation, data is key. And just as businesses understand this value, so too do cybercriminals.
The latest wave of digital transformation, accelerated by the pandemic, has redefined – if not entirely eliminated –the traditional enterprise perimeter. The systems and individuals creating and consuming precious data are no longer confined securely within the walls of the organisation. Instead, they operate from anywhere, anytime and via a myriad of devices and networks. For attackers, this means that they no long need to focus only on exploiting robust firewalls and IT policies, but can target a weaker link, which could be an employee accessing sensitive data from their local coffee shop. Attackers’ growing success in doing so is highlighted in IBM’s Cost of a Data Breach Report 2022 in which 83% of surveyed organisations report that they had experienced more than one breach. Also worrying for businesses is that, according to the same report the average cost of a data breach has increased by 12.7% since 2020. The shift to widespread remote working has also had an impact on the extent of data breaches. IBM’s report reveals that, on average, breaches cost US$1 million more when remote working was being undertaken compared to organisations where this was not the case. While these figures are already intimidating, the reality is even more grim for organisations in the Middle East where the average cost per breach (US$7.46 million) is the second highest in the world.
We’ve all heard the saying ‘Data is the new oil’, and if Middle East companies hope to extract its full value for business, they need to take a leaf out of the paybook of the region’s Oil & Gas sector and do everything in their power to prevent leaks. Here are some key steps that organisations can take to reduce the likelihood of breaches, and the cost should one occur.
Adopt a Zero Trust strategy: This is an effective way to protect access and data whether it is stored centrally, at a remote location, or on a cloud platform by implementing access control across users and devices.
Protect data with backup and encryption: Should a breach occur, these steps will reduce the likelihood that data can be stolen or misused. Attackers often target your backups to prevent you from being able to recover your data. As part of your backup process, remember your onpremise data as well as data in the cloud/ SaaS applications such as Microsoft 365.
Invest in XDR capabilities: IBM’s report found that organisations that have XDR in place shortened breach lifecycles by about a month. Specifically, organisations with XDR took 275 days to identify and contain a breach compared to 304 days for those without. This represents a 10% difference in response times. Being able to spot a breach faster can significantly reduce its impact and the associated costs. An XDR platform offers continuous security monitoring with response services for their managed endpoints, networks, and cloud.
Protect your email: Cyberattacks often start with a phishing email to capture
admin or user credentials. Choose an email security solution with AI capability that enables proactive threat discovery and automates remediation.
Secure your applications: Applications often have open vulnerabilities that can be exploited to gain access to your data. Use an application security solution that defends against web application vulnerabilities such as OWASP Top 10, zero-day and brute force attacks.
Create and maintain an incident response playbook: Pre-planning is critical to ensure that everyone within an organisation knows the steps that are required should a breach occur. IBM’s report clearly showed the benefits that flow from having detailed plans in place that guide actions if and when a data breach occurs. Organisations that had an incident response plan in place reported an average of US$2.66 million lower breach costs compared with organisations that don’t have IT teams and plans in place. This represents a saving of 58%.
As organisations in the Middle East steam ahead with their plans for ambitious digital transformation, cybercriminals will only have greater reason to target their data. Consequently, we can expect the cost of breaches to rise, presenting a formidable risk to both the bottom line, and reputation of organisations that find themselves in attackers’ crosshairs.

As data shows, preventive measures can drastically reduce the overall expense and effort associated with data breaches. Organisations that conduct due diligence and shore up their defences will find themselves able to stem the tide of breaches.
www.barracuda.com
As cyber attacks soar, here’s how businesses can curtail the cost of data breaches according to Toni El Inati – RVP Sales, META & CEE, Barracuda Networks
Thales’ annual report looks at the latest data security threats, trends and emerging topics following a survey of nearly 3,000 IT and security professionals based in 18 countries including the United Arab Emirates, and across both private and public sector organisations.
It’s likely that readers of Security Middle East will have experienced some form of security threat over the past year. According to Thales, more than a third (37%) of those surveyed experienced a data breach in the past 12 months, including 22% who reported that the company they worked for had been a victim of a ransomware attack.
With workloads increasingly being moved to the cloud it’s hardly surprising that cloud assets are proving to be the biggest target for cyber attackers. In 2022, 49% of people questioned by Thales said that at least 40% of data stored in the cloud was classified as sensitive. In 2023, this had grown to 75% of people agreeing with that figure. When it came to identifying the most at-risk cloud assets, 28% of people cited SaaS apps and cloud-based storage, with 26% saying cloud-hosted
applications and 25% saying cloud infrastructure management.
Sebastien Cano, Senior Vice President for Cloud Protection and Licensing activities at Thales, said: “Enterprises continue to see a serious threat landscape. Our findings indicate good progress is being made in certain areas, including MFA adoption and increased use of data encryption. However, there is still a lot of security gaps regarding data visibility.
“In an increasingly cloud-first world, organisations must maintain better control over their data so they can serve their stakeholders with greater safety and trust. As data sovereignty and protection regulations around the world tighten, security teams will need far more confidence in protecting where their data is being stored and how it is moving and being used.”
In light of this changing threat landscape, businesses need to respond and plan their data security strategies accordingly to ensure threats are addressed promptly. However, with simple human error, misconfiguration and other mistakes being named as the leading cause of
cloud data breaches it can be difficult to predict human nature.
For organisations that had been affected by a data breach in the past 12 months, 55% of respondents noted that human error or misconfiguration were the primary cause. As a result, a majority of 28% of those surveyed said identity and access management (IAM) was the best line of defence and the most effective tool to mitigate the risk of a simple mistake causing a catastrophic breach.

Just because an organisation isn’t being attacked by a nefarious individual doesn’t mean a breach as a result of human error is small. Simple mistakes like a file being deleted or information shared with the wrong person are far more common than cyberattacks and so their impact on a business can be significant. Not only can they be costly mistakes, but they can also lead to unnecessary downtime. In fact, figures highlighted by Datto revealed that human error was the number one culprit for downtime.
When an engineer working at a data centre near London’s Heathrow airport reconnected a power supply in a rush he could never have anticipated that it would lead to the mass cancellation of flights,
The 2023 Thales Data Threat Report has revealed that human error is the main cause of cloud data breaches, and it can be a costly mistake
75,000 British Airways’ passengers grounded and cost the airline some £80m in lost revenue and compensations. But his actions caused a power surge, which meant massive damage to British Airway’s information technology systems.
For Sony, when confidential company data was released online it wasn’t just the estimated $15m it ended up costing the company – but the reputational damage. It is widely believed that the company was the victim of a targeted phishing campaign which saw employees clicking on malicious emails which gave hackers access to the Sony network.
Once you’re able to identify the most common simple mistakes that employees make it becomes much easier to tackle them. Key ones to look out for include:

If spotted early – at the time it happens – it can be easier to deal with. When it’s not picked up until later if is harder to manage, especially if the file name can’t be recalled, or the date it was deleted. Having a back up in place can help to avoid too much disruption.
n Social engineering
Social engineering attacks are instigated by a hacker, but it is human error that leads to the breach. Cyberattackers will target employees with an email that is designed to trick employees into believing it is legitimate when in fact it carries malicious attachments. Attackers are using increasingly more sophisticated methods and the key to avoiding trouble is educating all employees and having best practices in place to ensure they know how to handle and verify such emails.
n Poor integrations
Another potential opportunity for data loss and breaches is when third party software is integrated, particularly if the integration includes any kind of data migration. Anyone adding new software must ensure it comes from reputable sources and is compatible with systems currently being used. It’s also a good idea to use test environments to spot any errors before it is fully rolled out.
Ultimately strengthening your protocols against human error will help to shore up your organisation’s defences. Training
will go a long way to achieving this. All staff should receive regular training, not only on the basics such as how to save, modify and delete files or folders, but also on the risks of data breaches and how to recognise phishing emails. Make sure staff know who to contact should an incident occur and that they understand how vital it is to contact them immediately when they realise something is wrong. Time really can be of the essence in some cases.
Tighter access control limits can also be initiated to ensure that people only have access to the data they need and only for the length of time it is needed. This approach should always be a ‘least privilege’ approach, which will limit how much data they have access to, reducing the volume of data that could be accidently breached. While it can’t prevent data being mishandled, it will help to protect more of your sensitive data.
Human error data breaches are not entirely preventable but the use of intelligent software can also help. By automating more tasks – such as gathering, sorting or categorising data –you can also minimise potential risks at this stage.


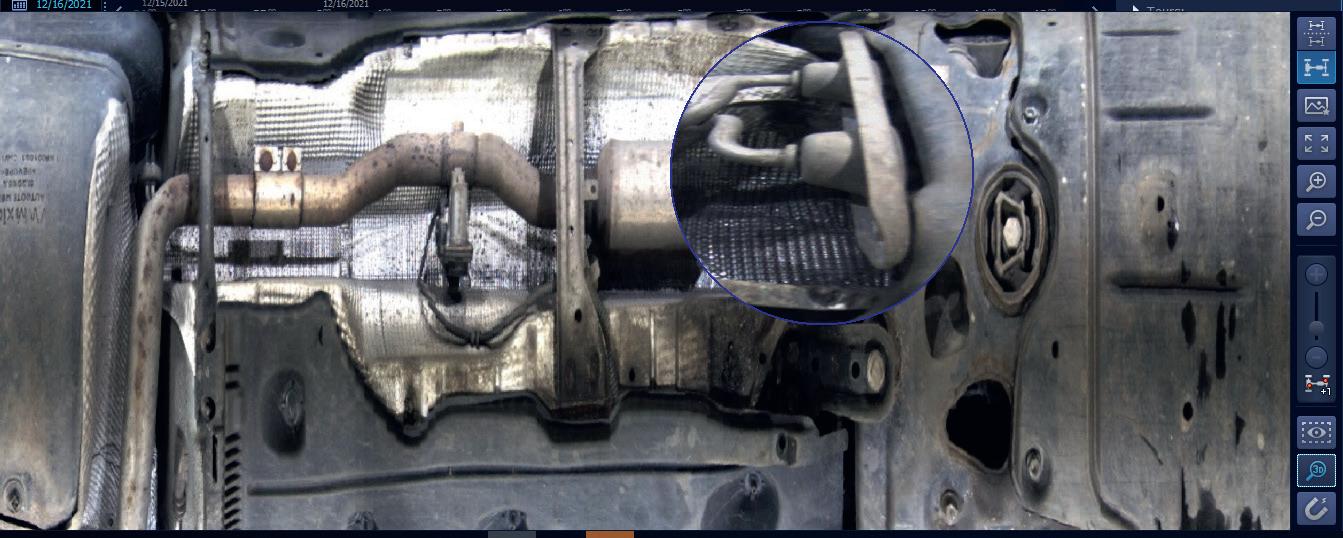
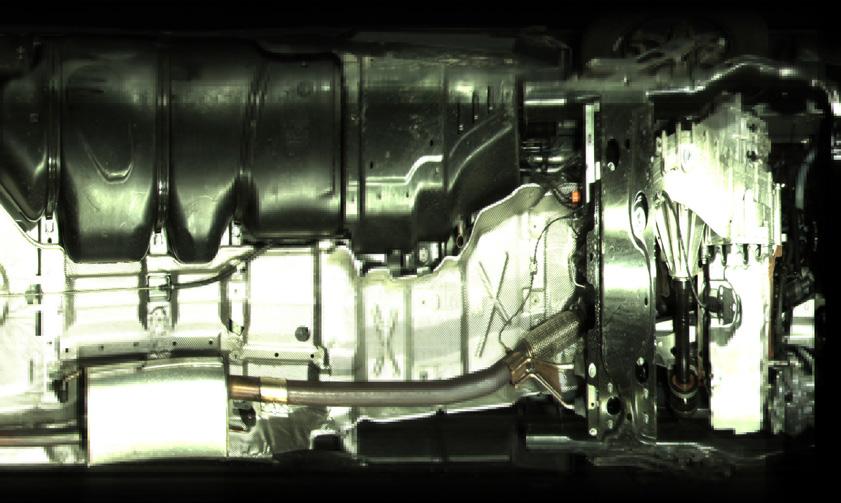
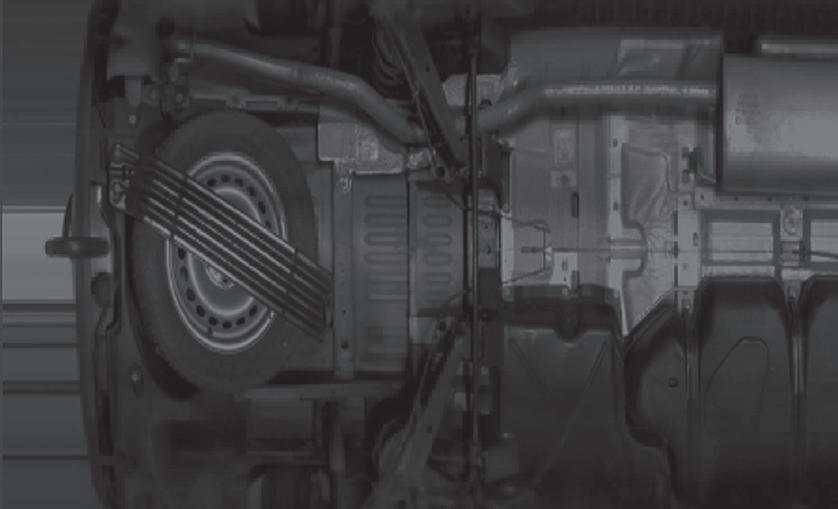
In the two years since it was rst introduced to the Middle East market, the SecurOS® UVSS become the security checkpoint screening technology of choice for a wide range of end users. With its unique combination of features and aesthetically pleasing form factor and powerful and e cient so ware, the SecurOS UVSS has signi cantly improved the undercarriage inspection process via the power of automated, arti cial intelligence (AI)-powered video analytics.

Modern approaches to the development and operation of UVSS solutions require innovation and revolutionary changes that change the UVSS market. For ISS, this is not only an easily installed UVSS platform and powerful so ware, it is a whole ecosystem based on a modern SecurOS® platform.
SecurOS® Eco system allows to use almost any ISS analytics and integrate with any third-party systems, turning UVSS solutions into intelligent check points that integrate all engineering systems into a single control center based
on SecurOS UVSS solution.

Choosing the right UVSS solution is an investment in the future. It consists not only of the costs of the UVSS platform and so ware, but also of additional costs – such as the mounting and installation, maintenance and ensuring a high level of service during operation.
Everything has been thought of here - from ease of installation and commissioning of the UVSS platform to an e cient cleaning system that provides the highest level of service during operation. All UVSS operator interfaces are also carefully designed, which greatly a ects the speed, e ciency and reliability of inspections, which also increases the total cost of ownership for the client.
The SecurOS® UVSS has become the under-vehicle surveillance system of choice in the “third wave” of advanced security solutions currently sweeping through the Middle East. The system, which is patent protected, has been a major improvement over prior legacy

technologies in terms of e ectiveness, speed and ease of implementation.
Notably, the ISS system was chosen at the end of last year to protect all the stadiums and fan zones of the high-pro le Qatar FIFA World Cup tournament. In partnership with the Supreme Committee for Delivery & Legacy and a large on-site technical team, ISS installed 40 UVSS units at vehicle checkpoints for the World Cup stadiums in and around Doha along with three logistics areas and a fan zone to safeguard visitors and make the screening process safer, faster and more e cient.
Recently, ISS Qatar got awarded another large-scale project for the supply of SecurOS® UVSS to Doha newest airbase.

In the UAE and Saudi Arabia, the UVSS has already been adopted by the UAE Army, Dubai Prison, Moro Hub – DEWA, the Digital Arm of Dubai Electricity and Water Authority, ZATCA (the Saudi Zakat, Tax and Customs Authority), KAPSARC (King Abdullah Petroleum Studies and Research Center) and the Alsalam Royal Palace in Jeddah.
Earlier this year, ISS and Saudi-based Advanced Electronics Company – AEC, an acknowledged forerunner in the design, manufacture, sale and repair of diverse electronics and ICT products and systems, formally signed an agreement to manufacture the SecurOS® UVSS at AEC’s facilities in the Kingdom of Saudi Arabia, meeting not just signi cant public and private Saudi demand for the UVSS, but also the export markets of the GCC and beyond.




For those looking to the future, the choice is clear – SecurOS® UVSS from ISS.




Ekaterina Mutina, Marketing Manager for TRASSIR looks at how automatic recognition systems for vehicles are helping to keep businesses running smoothly and safely and supporting smart city management

The use of automatic licence plate recognition systems has become more widespread in the Middle East –partially fuelled by the growing trend for implementing smart cities, as well as the advances being made in artificial intelligence technology which is helping to power these systems.
In order to meet the objectives of a smart city, it’s vital that the necessary elements are in place and this includes technology for the precise controlling and management of traffic conditions, increased surveillance and safety on the roads and the avoidance of traffic incidents. Therefore, the deployment of automatic recognition systems for vehicles should be a key priority in smart city management.
Automatic number plate recognition (ANPR) systems have already been used for decades, predominantly by police forces around the world. But their use has now spread to organisations who are looking to introduce their own vehicle surveillance methods as well as monitor parking situations.
Although the use of auto recognition systems for vehicles is a relatively new concept outside of the police force, many businesses already rely heavily on such security systems. After all, they have many advantages to offer securityconscious organisations. The distributed structure allows you to maintain operations even when individual elements of the system break down. In addition, the camera requirements are minimal because processing of the video
stream is carried out on the server. The effectiveness of this technology has already been proven and is successfully used for a range of tasks:
































n Restriction of access to the territory
There are territories that not everyone is permitted to enter, and in this case, the licence plate recognition system is one of the most convenient and inexpensive ways to restrict access to unauthorised vehicles.
n Organisation of parking
This includes paid parking lots in shopping and business centres, private parking lots designed for storing cars overnight, intercepting parking lots, and many others.
n Organisation of payment for parking services
The licence plate recognition system for paid parking is capable not only of identifying incoming and outgoing vehicles, but also of automating the payment process.
n Traffic flow management
In urban conditions, authorised vehicles require passage to a particular territory. These can be cars of special services, such as police, ambulances, the Ministry of Emergency Situations, city service vehicles engaged in street cleaning or rubbish collection, as well as public transport – buses and minibuses, ordinary taxis, or car-sharing vehicles. With the help of licence plate recognition systems, you can
flexibly configure access levels and create territories where only certain types of transport are allowed to enter.
n Managing vehicle time spent on the territory
In many cases, there is a need to limit not only the entry itself, but the time a vehicle spends on the territory. This is in demand at airports, train stations, metro stations, transport hubs, intercept parking lots, and residential territories.
n Vehicle registration
Sometimes it is necessary to simply register all incoming and outgoing vehicles, for example, to collect statistics that allow you to analyse traffic congestion.
n Vehicle tracking
Auto recognition systems can also track the appearance of vehicles from a watch list created especially for this purpose and issue an alarm signal when they appear.
The market offers different versions of the vehicle recognition system, but as a rule, it is hardware and software based on AI technologies. As a general rule, these systems have a wide range of capabilities that include the most basic – such as automatically detecting and determining the vehicle type, the licence plate in real-time and then storing it and cross referencing it to white/black lists.
In addition, many also offer the option for detailed reports, as well









































































































































































































































































































































“The latest improvements in the field of auto detection have been aimed at improving vehicle tracking using AI technologies, which are the basis for a more accurate classification of cars in the future”
as integration with speed measuring devices and security complexes including access control and re alarm equipment (barriers).
Note that the degree to which AI technologies are applied plays a great role in the work of vehicle detection systems. Many tasks are solved more e ciently with AI than using standard mechanisms of the past.
For example, in the TRASSIR system, the neural network is able to accurately determine the coordinates of the corners of the licence plate (even if it is located at an angle to the camera) for further alignment, which allows it to determine and record the car’s data as accurately as possible. It has been proven by experience that the system’s implementation allowed users to save money on the maintenance and development of facilities in the elds of construction, retail and industry. In some cases, the time of vehicle control at the checkpoint was reduced by half.
The latest improvements in the eld of auto detection have been aimed at improving vehicle tracking using AI technologies, which are the basis for a more accurate classi cation of cars in the future. Since vehicles can greatly di er visually from one another, the neural network calculates a vector of unique features of the car to improve the accuracy of recognition and tracking. This allows cars to be better and more accurately classi ed by appearance.
Market trends are such that systems are constantly being improved. Manufacturers continuously collect feedback from users, and each example is taken into account when making changes to the end product. We can look at the following areas for improving the module:
■ Training on new data
■ Application of the latest neural network architectures
■ Improvement of the quality monitoring process
■ Other unique developments. www.trassir.com






As a rule of thumb most licence plate recognition algorithms follow the below steps:
1 Firstly the LPR engine looks to identify the positioning of the licence plate within the image – this is known as framing or localisation. This steps helps the LPR to focus only on the licence plate and disregard any other data.
2 Angular corrections help the LRP to decode licence plates that have been captured at awkward angles –for example on the side or from above. The algorithms also correct for perspective too.
3 Filters are then applied to help eliminate shadows and any shaded areas. Edge detection, in particular, is used when there is a high contrast between the background and the text being identi ed. Some systems use sophisticated technology that blends together multiple images of the same licence plate to get the clearest image.
4 Tools such as whitespace delineation are used to nd the space between letters on the licence plate. Character segmentation works by detecting each individual character. Errors are more likely to occur here if the spacing of the characters on the licence plate is variable.

5 Optical character recognition techniques are then used to identify each character. This could include pattern matching, proportion, pixel repetition and edge tracing.
6 The nal step checks the characters identi ed and their sequence against rules that are speci c to each region.
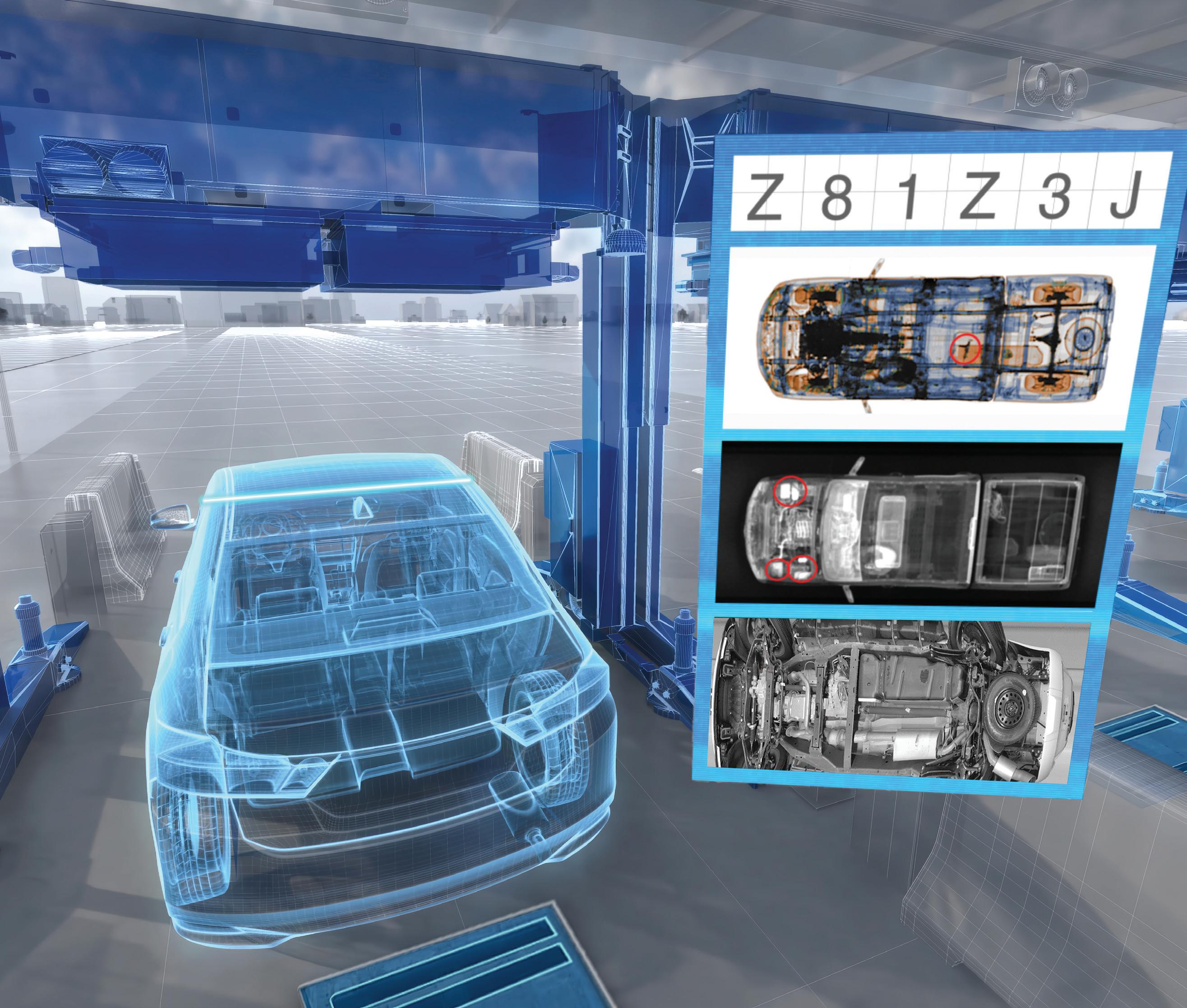
Ensuring your personnel and facility are well protected from threats requires a thorough understanding of who and what is entering your facility—before they gain access. Vehicle access control points are a key component of a comprehensive security plan, offering a physical barrier to deter bad actors from entering a defined perimeter. Today, vehicle checkpoints can provide robust security that goes well beyond traffic gates to give security personnel more information about the people and vehicles seeking entry to the facility.
Defining the ideal vehicle checkpoint requires a comprehensive review of each unique security mission. Factors such as threat level, traffic volume, site constraints, budget, personnel, and data requirements all need to be considered. When seeking a solution that fully optimises threat detection and operational efficiency, agencies employ a mix of advanced X-ray inspection, radiation detection, intelligent optical inspection, and data integration systems in conjunction with traffic management systems and sensors.
In the illustration of a vehicle checkpoint (Figure 1), several technologies are utilised to maximise threat detection and throughput. Each system provides a key piece of data about the vehicle and its occupants so that security personnel can determine with greater accuracy if it is safe to permit entry. For example, facial recognition and radio-frequency identification (RFID) technologies assist with identity verification by quickly and accurately matching the vehicle occupant’s face or unique identifier with their identity document or an existing database, while license/number plate readers assist in identifying vehicles and tracking their movement around the facility.
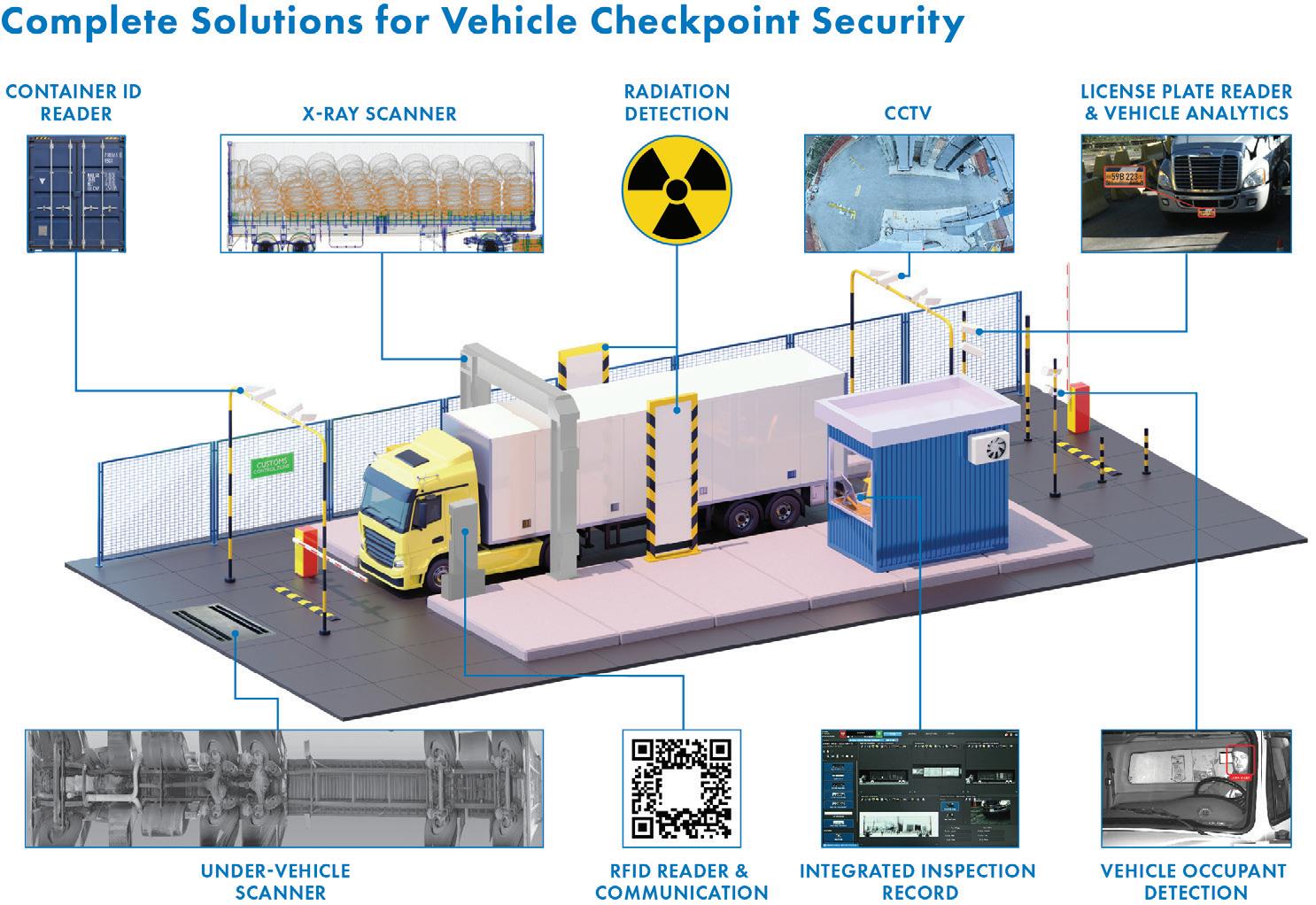
Various detection technologies, including X-ray scanners, radiation
detection systems, and under-vehicle imaging systems are also employed to screen the vehicle to help uncover concealed threats. Under-vehicle imaging systems take a clear picture of the undercarriage of a vehicle and compare it to a reference image to identify foreign objects. X-ray scanners can leverage multiple detection technologies to screen occupied vehicles. Low-energy transmission imaging helps to uncover hidden metallic threats, such as guns, and backscatter imaging technology provides photo-like images that highlight concealed organic threats and contraband, including explosives, plastic weapons, and drugs.
A data integration platform provides a centralised hub for collecting all the information provided by the security systems and sensors and presents it in a single, comprehensive inspection record. This holistic view allows operators to make a more informed assessment of each vehicle and its occupants and enhances their ability to quickly uncover

and respond to potential threats. The data integration platform can also integrate workflows into the operation based on the collected data, automating traffic management systems to improve the checkpoint’s efficiency and throughput.
Whether your checkpoint requires one or all these security technologies, selecting a provider that can define and deliver your ideal solution is essential. By working with a single supplier that can deliver the full range of solutions and has a proven track record of successful deployments, installations, and support, customers benefit from receiving the right solution for their mission, the ease of working with one supplier throughout the entire process, and a trusted resource for support post-installation. www.rapiscan-ase.com


Securing cyber assets is more than trying to stop people from hacking into a network; organisations must also watch and prevent threats from the inside. Insider threats can easily be more dangerous to an organisation since employees have easier access to data than outsiders. Because of that, ownership of cybersecurity falls partly in physical security, which can provide education, best practices and tools to help identify insider threats.
Securing cyber assets from the inside out needs to be part of an organisation’s standard operating procedure.
From a physical security perspective, organisations need to limit access to data centres, server rooms and other areas where data is stored using access control measures such as access cards and biometric readers. Multi-factor dual authentication adds additional security for these sensitive areas.
Surveillance cameras and video management systems can deter unauthorised access and provide evidence in the event of a security breach.
In addition to ensuring that data storage devices are kept in secure areas,
when the hardware is no longer needed, dispose of it properly. Securely erase data from hard drives and other storage devices before disposal to prevent data breaches.
Physical security and cybersecurity play different but complementary roles in an organisation’s overall security programme. Physical security must be part of the cyber conversation and vice versa. By working together, they can improve the organisation’s overall security posture and protect against both physical and cyber threats.
Physical and cyber teams can share information about overall security. Everyone brings expertise to the table. Sharing information about security incidents, threats, and risks to help everyone understand the nature of the threats they face can help everyone to develop better security protocols and procedures.
Both teams can conduct joint security assessments to identify vulnerabilities and potential security gaps in both physical and cyber domains. By working together, they can develop a comprehensive security strategy that
addresses all areas of vulnerability, reducing or eliminating gaps.
Both departments can collaborate on incident response planning to ensure that the organisation is prepared to respond to both physical and cyber threats. This includes developing procedures for responding to security breaches, conducting drills and exercises to test response plans, and coordinating communication among different departments.
Joint training and education help both departments understand the importance of security and their roles in maintaining it. This can include training on password management, phishing awareness, and physical security protocols. The physical security team should include the cyber team in active shooter training to help them understand the roles of each security team member and the process involved in reducing risk to all involved in taking down a shooter. The cyber team may identify ways they can add value or assist during a crisis.
And the physical security team should understand the risks and processes involved in responding to and managing a cyber attack or crisis. The physical security team may identify ways they can step up and assist.
Kim Rahfaldt, Director of Marketing and Public Relations at AMAG Technology, looks at why physical security must be involved in the cyber conversation at every level
Working together provides a holistic approach to security.
Organisations need both proactive and reactive security measures to have a complete security programme and support a holistic approach.
Proactive security ensures that only authorised users have access to sensitive data and systems. Organisations can implement role-based access control, which grants users access only to the data and systems needed to perform their job functions. Role-based access control helps prevent unauthorised access to sensitive data and systems.
An identity management system can automate the process of provisioning and de-provisioning user access. This ensures that access is granted and revoked in a timely manner or in accordance with company requirements or policies. Not only does this reduce the risk of human error and improve security, but in heavily regulated sectors, such as airports or healthcare, identity management systems can be set up to coincide with personnel certifications before they expire. This can eliminate thousands if not millions of dollars in fines.
Access control systems collect a lot of data that when filtered correctly through an analytics system can identify nefarious behaviour or insider threats. Access control data can be analysed to identify usual access patterns, such as an employee accessing sensitive data or door access outside of their normal working hours, or outside of their job responsibilities.
An analytics system delivers critical information through data analysis to
help identify the employees, contractors and other identities that may pose the highest risk to an organisation. Each person’s access history and patterns are analysed and a risk score is assigned and updated over time. Anomalous behaviour is flagged, helping identify potential threats, better control access and prevent data theft. Identifying potentially risky behaviour, allows earlier detection of potential threats, thereby mitigating risk and reducing the potential cost of an incident.
For example, increased attempts to access sensitive data or systems may indicate an employee has become disgruntled or is planning to leave the organisation. This information helps the security team determine a course of action and involve other departments if necessary.
If you’re an end user, you need to lean on your integrator and manufacturer to help you. Both can provide experience and expertise and not only understand industry best practices, but a manufacturer can identify if there are product features that can be utilised to help you meet your security goals. Often an end user doesn’t realise they have features within their existing product set that can help them.
If you’re an integrator, work closely with your manufacturers to help your end users. Tap the manufacturer’s expertise and resources and engage them with the end user. It’s a win-win!
Technology is constantly changing and the threats are getting more sophisticated
so having an established process to keep assets secure in the long term requires operational processes to be in place. Organisations must future-proof their cyber assets using best practices. They must continuously analyse their current technology and assess risks associated with its use such as the potential for data breaches. Once the vulnerable systems are identified, a risk assessment can determine the potential impact of a security breach. Develop a replacement plan to replace vulnerable systems with more secure alternatives. The plan should include an implementation timeline, budget considerations and resource allocation.
Cybersecurity lifecycle management helps organisations ensure that their IT assets are properly secured throughout their lifespan so sensitive information is protected. After deployment, companies must maintain ongoing operations and maintenance, and then properly dispose of IT assets by securely wiping or destroying to prevent unauthorised access to sensitive information.
Conducting regular penetration (pen) tests can identify weaknesses in security controls and help proactively address vulnerabilities being exploited by an insider threat or attacker. Pen testing is often overlooked but organisations can’t afford to ignore it.
Physical security systems operate on a network, automatically making them part of the cybersecurity conversation. When physical security and IT work together, organisations will find more value in their technology investments, streamline communications and processes, and transform their security programmes.
www.amag.com
“Increased attempts to access sensitive data or systems may indicate an employee has become disgruntled or is planning to leave the organisation”
It was fruitful to attend the informative talks & panel discussions as well as to network with professionals & companies in the industry
200+ attendees
Senior security personnel & c-suite executives attended from industries including:
Oil, gas and chemicals
Telecoms
Information Technology & Services
Government authorities, ministries and royal commissions
Security consulting & service providers

Mining & metals
City developments & gigaprojects
Customs, airports & ports departments
Banking & nance
20+ countries
106 organisations represented
4 networking sessions
Including:
9 exhibition stands
Public Investment Fund
Red Sea Global
NEOM
National Security Services Company
Royal Commission Alula
Riyadh Airports
FIFA World Cup
Embassies of UK, Denmark and Belgium
Tahakom
Zatca
British American Tobacco
SAB Bank
Attending was a fantastic opportunity to connect with industry experts and gain insights into the latest security trends and challenges
Interested in the Security Middle East Conference 2024? Contact Ryan Bickerton at Ryan@SecurityMiddleEastOnline.com
Salman Alghamdi Keynote Speaker, Saudi Aramco Industrial Security Operation Saeed Alshehri KAPSARC
OT security leaders must guide C-suites to a ‘this could happen to us’ epiphany, or risk disaster, says Hadi
Jaafarawi, Managing Director for Middle East, Qualys
In recent years, amid the whirlwind of cyberattacks that hit organisations as they hybridised their infrastructures, IT security was a frequent concern of boards and CISOs. But in a region engaged in rapid economic diversification, particularly in the manufacturing and heavyindustry spaces, security investment for operational technology and industrial control systems is strangely lagging.
The lack of action is troubling for two reasons. One, OT/ICS systems are at the core of industries that governments have singled out as ripe for digitisation. The United Arab Emirates’ Operation 300bn initiative is just one illustration of this point. This means that entire nations have a greater stake than ever in such industries not being victims of a cyberattack. The second reason for alarm is that regional OT is more vulnerable than ever because it is no longer air-gapped. Modern efficiency drives have made it necessary for ICS to join the Internet of Things.
At a time when downtime would be more damaging than ever, it is more likely than ever before. This calls for immediate action. According to the Dragos 2022 ICS/ OT Cybersecurity Year in Review report, just over half (53%) of ICS and OT systems now have external network connections. IT and OT are starting to merge. But if that is so, we must rise to the challenge of merging their security and governance.
Gone are the days when we could simply prioritise operations and consider cybersecurity a frivolous luxury in OT. Like its information counterpart, OT now recognises the critical nature of comprehensive visibility — the obvious need to know what the security team is protecting. IT teams use metrics such as the percentage of assets that are managed versus those that are unmanaged. Vulnerability tracking is not an exact science, but it is improving, despite the new hybrid reality where connected user devices hop the corporate perimeter fence and return at will multiple times daily.
OT must find a way to duplicate this level of control. While physical plant machinery isn’t subject to a user’s whimsical road trip the way a laptop or tablet would be, it still has multiple interconnected components, including staff-assigned IT assets that can move off premises. OT ecosystems
are notorious for unknown assets and unknown connections. This realisation alone makes the case for enhanced procedures — asset management, patching, network segmentation, threat intelligence, and more.
Think about Industroyer, malware that targeted ICS systems used in electrical substations in Ukraine. Consider the general-purpose INCONTROLLER, which goes after programmable logic controllers (PLCs) to access devices, download and upload files, and exploit vulnerabilities. OT attacks are on the rise. Even if you are not following specific strains, you will have heard of the US’ Colonial Pipeline story. Real damage is occurring with direct economic and safety consequences.
Prevention starts with an overhaul of access controls and continues with improvements in intrusion-detection and analysis capabilities. Real-time asset detection will help with both steps. While a lot of good work on industry standards has already happened, each organisation can take matters into its own hands. Merging IT and OT security management into one team will help. But this is a challenge because of the difference in skill sets. OT teams tend to have engineering backgrounds and prioritise operational uptime. IT teams are steeped in data, software, and network topology and think little of users having a cup of tea while their desktop or laptop is patched or upgraded.
Critical infrastructure such as production lines, power generators, or drills have no interest in tea breaks and could not afford to take them if they did. They must operate 24-7. How do we apply patches to such machinery? Downtime has a direct impact on revenue. And while those with an IT background may make the reasonable point that downtime will be longer if a cyberattack occurs, the OT mindset may not be receptive to offline repairs when equipment is operating within normal parameters.
It is important to merge the teams so that the issue of controlled outages vs uncontrolled outages can be adequately aired and addressed at the policy level. In the end, the conversation can be boiled down to the balance sheet. The board’s primary responsibility is to shareholders, and many industry analysts predict that risk-based KPIs will soon be written into C-level employment contracts. A CISO that can present a cyberattack as a greater risk than planned downtime will find it increasingly easy to grab the attention of senior executives in the coming years.

With the right metrics, security leaders can compare the short-term effects of upgrades against the devastating potential losses from attacks. Many cautionary tales are out there to help drive home the point — from Colonial Pipeline to the closer-to-home Saudi Aramco’s 2012 tussle with Shamoon. Real-world consequences can help to diffuse the abstract perception many noncybersecurity executives have of an attack scenario.
Following their ‘This could happen to us’ epiphany, senior executives may be more open to planned downtime. If downtime is impossible for operability or safety reasons, mitigation measures will at least become a task for multiple teams rather than just the SOC, and the costs of inaction will be better understood. Security will then be able to work more effectively across IT and OT to protect sensitive assets. Processes like applying updates will be structured correctly and tied to risk management. New threats targeting ICS and OT systems will still be there, but teams will no longer be powerless in combating them. And with a common team pulling in a common direction toward a common purpose, the organisation will be better prepared for the sinister forest ahead.
www.qualys.com


success of our first ever conference and the messages coming through from our industry expert panels
The inaugural Security Middle East Conference was a major success for the security community. Over 200 security leaders filled the conference in Riyadh on the 9th May to discuss a variety of security threats and opportunities, hearing from world-class key notes and panellists; from cyber resilience, to the skills gap in the region, to industry and regional collaboration, it is clear that Vision 2030 presents a plethora of unique, multidimensional challenges to overcome. As Chairperson, I found the insights and strategic initiatives compelling. Whilst there is a significant amount of work to overcome over the next 7-10 years, the community itself is strong, energised and the desire to protect, defend and
overcome these challenges is profound. Below are some of my key takeaways from the event itself:
While physical security has traditionally received strong attention and investment in the Middle East, the perception of the importance and value of cybersecurity lagged somewhat behind. However, it is now clear that cyber resilience, the modern, more all-compassing term for effective cyber risk management and security, is a fundamental business driver for companies, governments and vendors in the region. All organisations, from multi-billion dollar GIGA projects, to smaller government institutions, are
experiencing cyber attacks from a variety of well-funded, intelligent cyber threat actors. Organisations need to take a holistic approach to improve their cyber resilience and remain steadfast in the face of these complex, demanding threats. The key message from presentations and the panel session was that cyber threats can manifest anywhere across the organisation, as well as the supply chain. Monitoring the threats that may impact the organisation internally and throughout the supply chain, maintaining a register of the organisation’s unique asset profile, combined with investment in a suite of robust, internationally accepted controls, are the hallmarks of a resilient enterprise. Partnered with effective risk management and mature business continuity, crisis management and disaster recovery strategies can keep organisations resilient in the face of an ever-changing and dynamic threat landscape.
With ambitious GIGA projects, emerging technologies and a maturing economy, the Middle East is struggling to find strong security candidates across cyber and physical domains. Coupled with the perception that the security profession is somewhat of an immature field, with unclear pathways, hiring the right people and incentivising them along their corporate journey is a real challenge for all organisations. Developing an enticing environment for university students to move into the security field, with a
clear line of sight to senior management and beyond is a challenge that all organisations face globally.
To push security matters into the boardroom, the message from the conference was that security needs to rebrand itself away from a cost-centre and more towards a value-add. By partnering the security tooling and capabilities with traditional value-add functions like marketing, communications and sales, security can become a multi-faceted department. For example, behavioural monitoring and analytics systems that security use for threat intelligence and protection can be re-used to understand buyer behaviour, trend analysis and predictive analytics.
It is clear that the Middle East trails slightly behind the global security
community when it comes to regional and international collaboration and threat intelligence sharing. Governments, regulators and organisations alike are not building and maintaining strong associations or partnerships. This can bleed into weak and even conflicting regional and international regulations that can hinder progress and stunt development for ambitious organisations. E ective information sharing and diverse threat intelligence can add valuable insight into the threat landscape and potentially looming incidents. Partnerships, industry collaboration, government bodies and regulators can contribute information and foster meaningful relationships which can prepare organisations for future threats.
With the countdown to Vision 2030 looming, the security community has to take proactive steps to protect the region. Threat actors are biding their time
www.securitymiddleeastconference.com
to attack, compromise and steal from a resource-rich and abundant area of the planet. The threats are forever changing, dynamic and intelligent; security professionals must remain one-step ahead, or face a continued, uphill battle to protect what the Middle East is ghting so hard to develop. The Security Middle East Conference will be back in 2024 to drive collaboration, information sharing and development of best practice to support the community and the region.
Find out more about the Security Middle East Conference on page 16

About the author
Dan Norman is the Regional Director, EMEA for the ISF. The ISF is a leading authority on cyber, information security and risk management. Its members comprise some of the world’s leading organisations featured on the Fortune 500 and Forbes 2000 lists. For more information visit www.securityforum.org
Maxxess
Around 20 years ago, 2003, I entered the security industry as a security o cer with Vinnell Arabia, a subsidiary of Northrop Grumman, where I worked alongside multinational military-trained personnel and gained valuable insight into the security business, starting from the operational level which allowed me to gain hands-on experience with security protocols, best practices, and technologies commonly used in the industry. I pursued my personal development by receiving training from top security international institutes. I was part of a team that designed and implemented security plans for residential and work areas in Riyadh, adhering to the best standards and systems. This helped me understand how to create a comprehensive solution to secure people and assets.
In 2014, I joined King Abdullah Petroleum Studies and Research Center (KAPSARC) to help set up and establish the security for the organisation. Working with security professionals, I was able to develop personnel, equipment, and procedural security elements to create a safe environment for KAPSARC employees, residents, and visitors.


One of the most signi cant security challenges facing organisations is ensuring that their personnel are properly trained in security protocols and procedures. Another signi cant challenge is to raise public awareness of security
threats. Finally, balancing security and individual privacy is an ongoing challenge for organisations and governments. While security measures are necessary to protect public safety and prevent criminal activity, they can also infringe on individual privacy rights. Striking the right balance between security and privacy requires careful consideration of the risks and bene ts of di erent security measures, as well as respect for individual rights and freedom.
I became an ASIS member in 2005, seeking a reputable security certi cation to enhance my knowledge and skills in the eld. Although I initially joined a study group, work obligations prevented me from completing the program. However, I resumed my certi cation journey and ultimately earned my CPP (Certi ed Protection Professional) designation from ASIS.
The CPP demonstrated my great knowledge in the security business, increasing my career growth opportunities. The ASIS standards and books are valuable references for me to perform my daily work requirements, providing me the knowledge and references in variety of security elds. Finally, I am looking forward to attending the Global Security Exchange (GSX) this year, which is an excellent platform for security professionals to stay updated on the latest trends and systems in the security eld.
The security landscape is likely to become more complex and challenging in the coming years, requiring organisations to stay vigilant and adapt to new threats and technologies.
We might see greater emphasis on physical security with more investment in physical security measures, such as access control and surveillance systems and increased use of AI and automation with more advanced algorithms and greater integration with other security systems. I also expect to see increased use of biometric technology such as ngerprint scanners and facial recognition systems.
In the next 10 years, we can expect to see a greater emphasis on balancing security needs with individual privacy rights and expect a greater focus on privacy concerns. As security measures become more advanced and invasive, there will be a growing concern about privacy rights.
Meshal Aljohani is on the Advisory Board for the Security Middle East Conference









Many of the world’s most iconic buildings choose Fastlane turnstiles to secure their people and assets. Our market-leading entrance control products include the very latest integrations with both facial and biometric recognition systems. The latest updates to our popular Glassgate 150 and 300 models now include increased lane widths and our Sidegate Detection® technology.












The security space has witnessed a drastic transformation over the past three decades, whether it is the type of threats, preventive models, or technology. Of all the changes, one of the most profound metamorphoses has been in the domain of cybersecurity.
The biggest challenge for cybersecurity evolution is that not only are the old threats still prevalent and stronger, but new and innovative threats are growing out of the technological advancement.
Just a few decades ago, the traditional cybersecurity was mainly focused around creating defensive barriers against malware and computer viruses, around xed boundaries. However, as new data storage and connectivity technologies gain prominence, along with the ampli ed dependence on automation, the whole playing eld has transformed.
Not only that, but the players have changed, the rules, devices and even the game itself has changed.
Essentially, anyone with a smartphone, laptop, tablet or even a credit card is a potential victim; so practically, most of the modern population is a sitting duck for cyber criminals. Although everyone has various degrees of vulnerability, the people most at risk are children and the elderly. This is mainly because these
demographics have the devices and technology but not enough knowledge or technical maturity to manage the digital perpetrators.
Almost all cases of successful online scams in the US and UK are targeted at people over 60 years or older; identity the s or nancial scams target women; while most of the cyberbullying cases are encountered by preteens and teenagers. The current scenario appeals special focus on children, who are among the most vulnerable and where the psychological impact is far more long-lasting.
One of the hunting grounds of cybercriminals is the online gaming platforms, metaverse spaces and socialising platforms. These criminals befriend children online and slowly gather as much personal information about them and their family, while posing a fake front. Once they have enough data on the child and even sensitive photos or videos, they will use this to blackmail and manipulate the child. A child’s brain is not yet developed enough to make sense of everything and therefore triggers massive amounts of trauma, anxiety, and depression, which leads to mental health disorders. Apart from this, there could be worse repercussions involving brainwashing for murders, mass shootings,
self-harm, suicide and even terrorism.
It is not enough to have antivirus, antimalware, or child-friendly device settings, because the criminals and their views are floating everywhere across the internet. The child does not even have to interact with a criminal to be influenced. Reading blogs, articles, watching videos, listening to podcasts etc. is enough to manipulate their innocent minds. The responsibility for child protection is not with a cybersecurity expert or the authorities alone; in fact, the onus squarely sits with the parents, teachers, and other adults around a child.
The most powerful line of defence is ‘knowledge’. Children and their caregivers must be sensitised, educated, and informed of the potential cyberthreats lurking around in a harmless looking device and how they can prevent, mitigate and defend against it. They also need to be trained on how a child should handle cyberspace safely and how to protect themselves. Ultimately, it is about how and what the human inputs are to a device that will determine the level of safety for the child and not the complacent dependence on so ware or hardware.
“Children and their caregivers must be sensitised, educated, and informed of the potential cyberthreats lurking around in a harmless looking device”
Please check the event websites for the most upto-date details as dates can change all the time.
6-8 June
Securex South Africa
Gallagher Convention Centre, Johannesburg, South Africa
securex.co.za
13-14 June
CYSEC SAUDI
Dammam, Saudi Arabia
saudi.cysecglobal.com
19-21 July
Secutech Vietnam Friendship Cultural Palace, Hanoi, Vietnam secutechvietnam.tw. messefrankfurt.com
15-17 August
CyberDSA 2023 Kuala Lumpur Convention Centre, Malaysia
cyberdsa.com
23-24 August
Indonesia Smart Industrial Expo The Bekasi Junction Indonesia
tpmi-group.com/ smart-industrial-expo
4 September
Airport Innovation Conference

Radisson Blu Hotel, Riyadh, KSA airportinnovationsummit. csevents.ae
13-14 September
IDC CIO Summit 2023
Fairmont Riyadh, Riyadh, Saudi Arabia idc.com/events
19-21 September
SECURA North Africa
SAFEX (Union Hall) Algiers Exhibition Centre, Algiers, Algeria securanorthafrica.com
3-5 October
Intersec Saudi Arabia
Riyadh International Convention and Exhibition Center (RICEC), Riyadh, Saudi Arabia intersec-ksa.ae. messefrankfurt.com
9-10 October
7th edition OFSEC
Oman Convention & Exhibition Centre, Muscat, Oman ofsecevent.com
11-12 October
Natural Disasters Expo
Messe Frankfurt, Hall 11, Frankfurt, Germany naturaldisastersshow.de



Utilities are an important element of critical infrastructure that always requires high level of security at all times. Ensuring a consistently high level of security is crucial and any harm inflicted upon these services has the potential to disrupt people’s daily lives, result in financial losses, and even endanger lives. One of the challenges faced by the industry is controlling access to geographically dispersed and often unmanned sites. Moreover, this task must be accomplished while adhering to rigorous industry regulations, which adds to the complexity.
1 Manage staff and vendor access to keys and assets thru secure access solutions like Curfew management, Multiple Authorizations, Email alerts.
2 Streamlining operational process while keeping it safe to follow like ensuring keys and assets are available 24/7 to authorized users only; assuring keys and assets never leave the facility and ensuring dangerous machines are shut off and secured before commencing maintenance work.
3 Ensure compliance with governing authority by securing all keys and equipment, prove an audit trail of their use and be able to show conformity with regulatory compliance processes
■ Increase efficiency and reduce downtime wasted on locating devices.
■ Lower maintenance cost due to higher levels of user accountability and responsibility

■ Empower businesses with detailed reporting from data collected, on which informed decisions can be made
Traka is the global leader in intelligent management solutions for keys and equipment. Traka’s solutions help all types of organizations control their important assets, improving productivity and accountability, and reducing risk in critical processes.


For more information on Traka’s specialist key management solutions for retail banking, please visit: www.traka.com


Traka makes your
and assets work for you like never before
