





Uolo’s Tekie program offers a coding-focused curriculum for grades 1 to 8, preparing students for the technology-driven world. We present a carefully crafted Teacher Manual to assist teachers in delivering effective and engaging lessons to students. Rather than prescribing teaching methods, the manual provides examples and demonstrates how and why teachers can apply these examples in their classes.
The Teacher Manual includes a suggested implementation plan to help teachers navigate the curriculum better throughout the academic year. Within the academic year, the Tekie program prescribes the following types of chapters and sessions:
Familiarisation: this period builds familiarity with the Tekie program and the digital platform.
Theory: these periods are dedicated to the Computer Science Theory chapters. These topics are mostly delivered in the classroom.
Tools: these periods are dedicated to the Computer Tools chapters. These topics involve almost equal numbers of classroom and computer labs sessions.
Coding: these periods are dedicated to the Coding chapters. These topics have more computer lab sessions.
Additional Hands-on Time: these are additional computer lab periods that teachers can use to revise topics or dedicate for completion of projects.
Revision: these are additional classroom periods that teachers can use to revise topics or cover syllabus backlogs.
Each chapter in this manual is structured to provide a comprehensive lesson plan. The chapters are divided into multiple sessions, each following the Warm up, Engage, Build, and Sum up (WEBS) strategy. The Warm up phase sets the stage for learning by connecting to prior knowledge and building curiosity. The Engage phase captures the students’ attention and motivates them to participate actively. In the Build phase, questions from various sections are discussed to build the understanding of the students. Finally, the Sum up phase reinforces learning through easy-to-recall activities and questions. Time duration for each section has been suggested based on the requirements of the students. Additionally, an answer key for every chapter is provided to assist teachers in assessing their students’ understanding and guiding their learning effectively.
Lastly, we understand that the Indian education landscape is quite diverse. To suit the needs of all types of schools, we have built-in extra higher-order chapters in the content books. These extra chapters are clearly marked in the table of contents of this manual. We suggest that the teacher completes the main chapters first and then move to higher-order optional chapters only if there is sufficient time left in the academic year and learners are ready for more challenging content.
We hope that this teacher manual will empower teachers to use the curriculum effectively, support the learning of all students thoroughly, create learning opportunities and design interactive learning environments that cater to the students’ needs and interests.

1
Networking Fundamentals����������������������������������������������������������������������������������������������
Introduction to Computer Networks
Network Terminologies and Devices
Types of Computer Networks and Topologies
Network Architectures and Protocols
Shared Drive and Network Security
2 Introduction to Database Management System
Databases and DBMS 1
Databases and DBMS 2
Structured Query Language 1
Structured Query Language 2
More SQL Queries 1
More SQL Queries 2
3 Fundamentals of Python
Introduction to Python, Data Types, and Variables
Operators
Conditional Statements
lterative Statements
In the magical world of Avora, three friends—Mel, Conji, and Eva—discover that the Magical Garden is trapped in endless winter due to a dark spell cast by Lord Ero. Fairy Joy, under the spell, reveals that Ero has hacked the magical network to control all magic in Avora. The trio seeks guidance from the Elders, who explain that Ero exploited magical technologies, similar to how hackers manipulate systems.
To stop him, they visit the Space Centre, a hub of magical knowledge, where they learn about blockchain and cybersecurity to secure the fairy network. However, Ero initiates his attack, forcing the trio to use a time-travel spell to prevent his rise. They design an app to track Ero, encrypt their magic, and build protective firewalls, paralleling digital security measures.
In a final showdown, they confront Ero, learning he is the estranged son of the Elder Wizard, driven by bitterness. With teamwork, courage, and their understanding of magic and technology, they defeat Ero, restore balance, and revive the Magical Garden. The story highlights the ethical use of power and the importance of responsibility in both magic and technology.
● Mel, Conji and Eva enjoy the amazing morning breeze in Avora.
● Conji suggests visiting the Magical Garden where they can meet Joy.
● The colours are missing from Magical Garden and it is too cold when they reach.
● They feel that something terrible has happened with Joy and the Magical Garden.
● Suddenly Mel saw a letter stating that the magical garden and the network of fairies had fallen under Lord Ero’s spell. Joy was hidden in a safe place to restore the magical network of fairies.
● Mel was surprised when she heard the term “magical network of fairies”.
● Conji told Mel that the magical network of fairies is a way fairies communicate with each other.
● But Conji is confused about computer networks.
● Mel explains the computer network to Conji.
5.
At the end of the session, the students will be able to:
● describe computer networks and their need.
● describe the uses of computer networks.
● explain the advantages and disadvantages of computer networks.
Keywords
● Computer network: A way to connect computers using communication devices so that they can exchange data and resources with each other.
● Server: A central computer in a network in which data is stored.
Ask the students how roads are connected to form a network.
Explain the concept of computer networks, the need of computer networks, the uses of computer networks, the advantages and disadvantages of computer networks. Group discussion Conclude the concepts
Assign homework
● Ask the students how roads are connected to form a network.
● Just like road networks, computers can also be connected to form a computer network.
● Now, build the concept that a computer network is a way to connect computers using communication devices so that they can exchange data and resources with each other.

Explain the following concepts:
Describe computer networks and their need.
Describe the uses of computer networks.
Explain the advantages and disadvantages of computer networks.
Tell the students that a computer network is a way to connect computers using communication devices so that they can exchange data and resources with each other. Also, tell the need for a computer network, as given on pages 5 and 6.
Tell the students that computer networks are used for different purposes in our daily lives like file sharing, resource sharing, communication, etc., as given on pages 6 and 7.
Tell the students that computer networks are beneficial to us in many ways but also have some disadvantages, as given on pages 7 and 8.
● Read aloud the questions provided in the Do It Yourself 1A section and encourage students to solve them. Instruct them to write the answers in the book.
Correct Responses:
1. Resource sharing is the use of a computer network to allow multiple users or devices to share a single resource, such as a printer.
2. Through file sharing
3. One scanner is sufficient since computer networks allow resource sharing
● Conduct a group discussion in the class among students on the topic ‘Benefits of resource sharing in a computer network’.
Possible Responses: Cost savings, resource optimisation, etc.
● Conclude the session by summarising that a computer network is a way to connect computers using communication devices so that they can exchange data and resources with each other. It has many uses such as file sharing, communication, database access, data backup, etc. Also, tell the students about various advantages and disadvantages of computer networks.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Questions 1 and 4
B. Tick the Correct Option: Questions 1, 2, and 3
C. Write T for True and F for False: Question 4
D. Answer the Following Questions: Question 2
E. Apply Your Learning: Questions 4 and 5
At the end of the session, the students will be able to:
● describe network terminologies.
● explain network devices.
Keywords
● Node: A device in a computer network which is used to send or receive data.
● Packet: A unit of data or information that is transferred over a network.
● Bandwidth: The amount of data or information that can be transmitted over the internet or network.
● Hub: A networking device that transmits the received information to and from all the devices on the network.
● Router: It is a device which routes the data or information over a network.
Ask the students about the devices at home which are connected to a network. Explain about terminologies and devices associated with computer networks.
Group Discussion Conclude the concepts Assign homework
5 mins
Warm Up
● Ask the students about the devices at home which are connected to a network.
● Now, build the concept that there are different devices used within a computer network. Some networking devices are network interface card (NIC), hub, switch, router, etc.

Explain the following concepts:
Describe network terminologies. Explain to the students the various network terminologies, such as node, link, packet, protocol, etc., as given on page 9.
Explain network devices. Tell the students that computer network devices are hardware components that are required for computers to communicate with one another over the network. Also tell them about the various network devices such as the Network Interface Card (NIC), Modem, Hub, etc., as given on pages 9 and 10.
● Read aloud the questions provided in the Do It Yourself 1B section and encourage students to solve them. Instruct them to write the answers in the book.
Correct Responses:
1. a. Modem b. Ethernet networking cable
2. NIC, Modem, Hub, Switch, etc.
Build 7 mins
● Conduct a group discussion in the class among students on the topic ‘Role of a modem in modern communication systems’.
Possible Response: A modem enables data transmission by converting digital signals into analog signals for travel over communication lines and vice versa. This ensures seamless connectivity between digital devices and networks.
● Conclude the session by summarising that there are various network terminologies, such as node, link, packet, protocol, etc. Also, tell them that computer network devices are hardware components that are required for computers to communicate with one another over the network.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
B. Tick the Correct Option: Question 5
C. Write T for True and F for False: Question 3
D. Answer the Following Questions: Question 3
At the end of the session, the students will be able to:
● explain different types of computer networks.
● describe various types of network topologies.
Keywords
● Wireless network: A type of Local Area Network (LAN) that uses wireless communication technology to connect various devices.
● Topology: The configuration of how computer systems or network devices are connected to one another is known as a topology.
Warm Up Engage Build Sum Up
Ask students if they have heard about any type of network before. Explain to the students about types of computer networks and topologies.
Think and Tell Group discussion
Action Plan
Conclude the concepts
Assign homework
5 mins
Warm Up
● Ask students if they have heard about any type of network before.
● Now, build the concept that there are different types of networks, which are categorised according to the geographical area they cover. They are PAN, LAN, MAN, and WAN.

Explain the following concepts:
Explain different types of computer networks.
Describe various types of network topologies.
Tell the students that there are different types of networks, which are categorised according to the geographical area they cover. Also, tell them about the wireless network, as given on page 11.
Tell the students that a topology is a physical and logical layout of different devices (nodes) and connections in a network. Also, explain its different types, as given on pages 12 and 13.
● Read aloud the questions provided in the Do It Yourself 1C section, Question 2 and encourage students to solve them. Instruct them to write the answers in the book.
Correct Response:
a. PAN b. LAN c. MAN d. WAN Build
7 mins
● Ask the students to answer the question “Which type of network will you recommend in your school to share hardware devices?” asked in the Think and Tell section on page 12.
Correct Response: LAN
● Conduct a group discussion in the class among students on the topic “How is a tree topology better than a ring topology?“ as mentioned in the Discuss section on page 13.
Possible Responses: In tree topology, nodes are connected in a parent-child hierarchal manner. Whereas, in ring topology, the nodes are connected forming a ring. Therefore, tree topology provides more flexibility and scalability by allowing multiple paths and avoiding a single point of failure. But in ring topology, if any one node fails, the entire network will fail.
3 mins
Sum Up
● Conclude the session by summarising that computer networks are of many types, such as PAN, LAN, MAN, WAN and wireless. Also, revise with them about different topologies of computer networks such as bus, star, ring, tree, and mesh topology.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Questions 2 and 3
B. Tick the Correct Option: Question 4
C. Write T for True and F for False: Questions 1, 2, and 5
D. Answer the Following Questions: Questions 1, 4, and 5
E. Apply Your Learning: Questions 1, 2, and 3
At the end of the session, the students will be able to:
● discuss types of network architecture.
● discuss network protocols.
Keywords
● Server: A computer in a network which has all the resources and provides services to other computers.
● Clients: The computers in a network which use services provided by the server.
● Network protocol: A set of rules which governs the communication between the computers over a network.
Warm Up Engage Build Sum Up
Ask the students how computers are connected within a network.
Explain the concept of network architecture and network protocols to the students.
Group discussion Conclude the concepts
Assign homework
5 mins
Warm Up
● Ask the students how computers are connected within a network.
● Now, build the concept by introducing students to the types of network architectures: peer-to-peer and client-server architectures.
15 mins
Engage
Explain the following concepts:
Learning Outcomes
Discuss types of network architecture.
Explanation
Tell the students about peer-to-peer architecture and client-server architecture used to design networks, as given on pages 13 and 14.

Discuss network protocols.
Tell them that network protocol is a set of rules which governs the communication between the computers over a network and explain some of the network protocols, as given on pages 14 and 15.
● Read aloud the questions provided in the Do It Yourself 1C section, Question 1 and encourage students to solve them. Instruct them to write the answers in the book.
Correct Response:
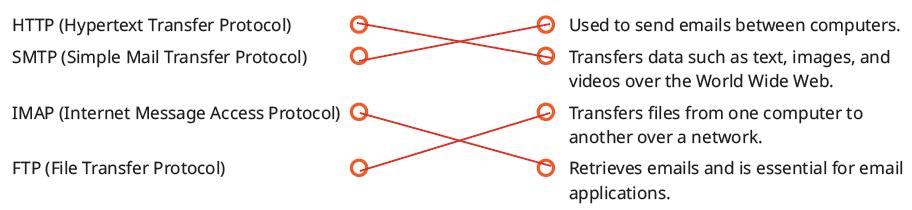
Ask the following additional questions to the students to check their understanding:
● Give one example of peer-to-peer architecture.
Possible Response: Bitcoin is an example of P2P architecture.
● Ritu has sent a file to her friend using a network. Which protocol would be used in this situation?
Possible Response: FTP
Build
● Conduct a group discussion in the class among students on the topic ‘Client-server architecture’.
Correct Responses: In this architecture, one or more nodes serve as a server and all other nodes behave as clients.
● Conclude the session by summarising the two types of network architectures, i.e., peer-to-peer architecture and client-server architecture that are used to design networks. Also, revise the different internet protocols: TCP/IP, HTTP, FTP, SMTP, and IMAP.
● Assign the following questions as homework.
■ What are clients in a client-server architecture?
Correct Response: The computers which use services provided by the server are known as clients.
■ Shreya is searching for some information on the internet. Which protocol would be used in this situation?
Correct Response: HTTP
■ What is the full form of IMAP?
Correct Response: Internet Message Access Protocol Sum Up
At the end of the session, the students will be able to:
● store and share a file on Google Drive.
● describe some security measures to secure a network.
Keywords
● Google Drive: A virtual space where you can save and share files.
● Firewall: A network security device that monitors and filters incoming and outgoing network traffic based on an organisation’s previously established security policies.
Ask the students how they share their school notebooks to complete the work.
Ask the students how they secure themselves from bacteria and infections.
Explain the concept of shared drive and network security. Group discussion Conclude the concepts
Assign homework
Action Plan
Warm Up
● Ask the students how they share school notebooks to complete the work.
● Ask the students how they secure themselves from bacteria and infections.
● Now, build the concept that Google Drive is a virtual space where we can save our files and share them with others.
● Also tell them that because of security breaches on the network, it is necessary to use some network security measures.

Explain the following concepts:
Describe how to access a file from a shared drive.
Describe some security measures to secure a network.
Tell the students that they can share their data with other users even if they are living in a very faraway place through Google Drive. Tell them how to store and share a file on Google Drive, as given on pages 15 to 17.
Tell students that because of security breaches on the network, it is necessary to use some network security measures. Discuss safe online practices, as given on page 18.
Ask the following questions to the students to check their understanding:
● Tom wants to share some photos with his friend. Where can he share the photos?
Possible Response: He can use Google Drive to share photos.
● Name some antiviruses.
Possible Responses: AVG, Quick Heal, Norton, McAfee, Avast, etc.
Build
7 mins
● Conduct a group discussion in the class among students on the topic ‘Safe Online Practices’.
Possible Responses: Clear browser cookies, remove unknown or unwanted applications, regularly update all applications and software, etc.
3 mins
Sum Up
● Conclude the session by summarising that students can share their data with other users even if they are living in a very faraway place through Google Drive. Revise how to store and share a file on Google Drive. Also, tell them that a firewall is a network security device that monitors and filters incoming and outgoing network traffic. Discuss some of the safe online practices also.
● Assign the following from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Question 5
Additional questions
● Can a receiver of the file shared via Google Drive edit the file?
Correct Response: Yes, if permission is given.
● What are some examples of firewalls?
Possible Responses: Sophos Firewall, Check Point Firewall, pfSense Plus, WatchGuard, etc.
● Why are antiviruses necessary?
Correct Response: Computers are vulnerable to attacks or viruses when they are connected to a network. Therefore, it is necessary to install antivirus software on the computer system.
In the magical world of Avora, three friends—Mel, Conji, and Eva—discover that the Magical Garden is trapped in endless winter due to a dark spell cast by Lord Ero. Fairy Joy, under the spell, reveals that Ero has hacked the magical network to control all magic in Avora. The trio seeks guidance from the Elders, who explain that Ero exploited magical technologies, similar to how hackers manipulate systems.
To stop him, they visit the Space Centre, a hub of magical knowledge, where they learn about blockchain and cybersecurity to secure the fairy network. However, Ero initiates his attack, forcing the trio to use a time-travel spell to prevent his rise. They design an app to track Ero, encrypt their magic, and build protective firewalls, paralleling digital security measures.
In a final showdown, they confront Ero, learning he is the estranged son of the Elder Wizard, driven by bitterness. With teamwork, courage, and their understanding of magic and technology, they defeat Ero, restore balance, and revive the Magical Garden. The story highlights the ethical use of power and the importance of responsibility in both magic and technology.
● The spaceship with Mel, Conji, and Eva landed in Avora two days before its destruction started.
● Everyone was enjoying the spring season in Avora, and the trio decided to protect the people at any cost.
● Mel decided to trace the location of Lord Ero using the app they created to see where Lord Ero is right now.
● The trio realised that Lord Ero already knew that they were going to travel back in time with the ancient spell, and he was heading towards them.
● Conji suggested finding out the place where Lord Ero will attack first, and Mel suggested using DBMS for this purpose.
● DBMS will help to observe the pattern in which Lord Ero attacks and give a list of all the possible locations.
● Eva and Conji have no idea about Database Management System (DBMS), so Mel decided to explain the concept to them.
This chapter is divided into the following classroom and lab sessions
1. Databases and DBMS 1
2. Databases and DBMS 2
3. Structured Query Language 1
4. Structured Query Language 2
5. More SQL Queries 1
6. More SQL Queries 2

At the end of the session, the students will be able to:
● describe databases and its advantages.
● describe the concept of Database Management System.
Keywords
● Database: Data organised and structured in a digital form on a computer.
● DBMS: A database management system (DBMS) is a software application that enables you to construct, operate, and interact with databases.
● Data: It is a collection of fundamental facts and figures that are recorded in a database.
● Database Access Language: It is a language that allows users to give commands to a database to operate the stored data.
Ask the students about the importance of the library. Also, ask them how they fetch a book in a library. Explain to the students the meaning of the databases and their advantages. Explain to them the meaning of the term DBMS—its role, types, and different components.
● Ask the students about the importance of the library.
Group discussion
Think and Tell
Conclude the concepts
Assign homework
● Ask the students about the process of fetching a type of book. For example, if he/she wants to find a science fiction book, then in what column will they search for the book?
● Tell the students that just like how books are properly organised in a library, data stored in a computer are also organised in the form of a database.
Explain the following concepts:
Describe database and its advantages.
Explain to the students that a database is a collection of tables, where each table consists of rows and columns. Explain the structure of a table. Also, explain the advantages of databases, as given on the pages 101 and 102.
Describe the concept of a DBMS.
Explain the concept of DBMS to the students. Also, tell them about its role. Tell the students that there are four types of DBMS, such as HDBMS, RDBMS, OODBMS, and NDBMS. Tell them about the various components of a DBMS, such as data, hardware, software, users, procedures and Database Access Language, as given on pages 102 to 104.
● Read aloud the questions provided in the Do It Yourself 6A section and encourage the students to solve the questions. Instruct the students to write the answers in their book.
Correct Responses:
1. The components of DBMS are data, hardware, software, users, procedures, and Database Access Language.
2. There are four types of DBMS, such as HDBMS (Hierarchical Database Management System), RDBMS (Relational Database Management System), OODBMS (Object-oriented Database Management System), and NDBMS (Network Database Management System).
7 mins
Build
● Conduct a group discussion in the class among the students based on the topic “Is it important for data to be organised”, provided in the Discuss section on page 102.
Correct Responses: Organising data is essential to facilitate readability and streamline work processes. Analysing raw data can be challenging, so arranging it systematically is crucial to effectively representing and interpreting information.
● Ask the students to give the answer to the question “Where have you seen the use of a database in your daily life?”, asked in the Think and Tell section on page 101.
Possible Responses: School
Correct Responses: School, shops, mall, office, and hospital
● Ask the students to give the answer to the question “Do you think that a person with special knowledge of databases is required to handle it?”, asked in the Think and Tell section on page 103.
Possible Responses: Yes, No
Correct Response: Yes. Databases are complex systems that require expertise to manage, design, and maintain.
Sum Up
3 mins
● Conclude the session by summarising that a database is a collection of tables that helps to organise data. A database management system (DBMS) is a software application that enables you to construct, operate, and interact with databases.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Questions 1, 2, and 3
B. Tick the Correct Option: Questions 1, 2, 3, and 4
D. Write T for True and F for False: Questions 1, 2, and 4
E. Answer the Following Questions: Questions 1, 3, and 4

At the end of the session, the students will be able to:
● describe databases and its advantages.
● know the concepts related to Database Management System.
● Database: Data organised and structured in a digital form on a computer.
● DBMS: A database management system (DBMS) is a software application that enables you to construct, operate, and interact with databases.
● Data: It is a collection of fundamental facts and figures that are recorded in a database.
● Database Access Language: It is a language that allows users to give commands to a database to operate the stored data.
Let the students watch the video or the learning slides related to the topic on the digital panel.
Explain to the students the meaning of the databases and their advantages.
Explain to them the meaning of the term DBMS—its role, types, and different components.
Attempt the activity on the Assignment page.
Conclude the concepts Assign homework
5 mins
● Instruct the students to go to the Tekie’s Digital platform and open a Lab session on Databases and DBMS 2.
● Show the learning slides or the video and discuss the concepts shown on the panel.
Explain the following concepts:
Describe the meaning of the term database.
Demonstrate the concepts related to Database Management System.
Explain to the students that a database is a collection of tables, where each table consists of rows and columns. Explain the structure of a table. Also, explain the advantages of database, as given on pages 101 and 102.
Explain the concept of DBMS to the students. Also, tell them about its role. Tell the students that there are four types of DBMS, such as HDBMS, RDBMS, OODBMS, and NDBMS. Tell them about the various components of a DBMS, such as data, hardware, software, users, procedures, and Database Access Language, as given on pages 102 to 104.
● Ask the questions provided on the slides one by one to assess the students’ understanding. Discuss the answers to the questions with the students. If necessary, ask additional relevant questions.
7 mins
Build
● Instruct the students to attempt the assignment by clicking on the Assignment tab.
● Explain the activity to the students. Sum Up
3 mins
● Conclude the session by summarising that a database is a collection of tables that helps to organise data. A database management system (DBMS) is a software application that enables you to construct, operate, and interact with databases.
● Assign the additional activity given on the panel to the students as homework.

At the end of the session, the students will be able to:
● know what SQL is.
● know the types of SQL statements.
● know the main data types used in SQL.
● identify the keys defined for a table.
● revise the basic SQL commands learnt in the previous grade.
Keywords
● SQL: SQL, or Structured Query Language, is a powerful tool used for managing and manipulating data in databases.
Ask students how they can retrieve specific data from databases. Explain to the students what SQL is. Explain the types of SQL statements and the data types in SQL. Explain the different keys in a database. Revise the basic SQL commands learnt in the previous grade.
● Keys: Keys in a database are used to define any constraints on the table. Keys are also used to establish and identify relationships between tables. 5 mins
● Ask the students how they can retrieve specific data from databases.
● Tell them that they can use SQL, or Structured Query Language for managing and manipulating data in databases.
Explain the following concepts:
Explain SQL and types of SQL statements.
Explain main data types used in SQL.
Describe the keys in a database.
Revise some basic SQL commands learnt in the previous grade.
Explain to the students that SQL is a powerful tool used for managing and manipulating data in databases. Explain to them the types of SQL statements, i.e., DDL and DML, as given on pages 104 and 105.
Explain to the students the main data types used in SQL, such as number, character, varchar, date, and time, as given on page 105.
Explain to them the main keys that can be defined for a table, such as the primary key, candidate key, composite key, and the foreign key, as given on page 106.
Revise with students some of the basic SQL commands such as the ‘Create Table’, ‘Insert’, and ‘Select’ commands, as given on pages 106 and 107.
Ask the following additional questions to check the students’ understanding:
● What is the full form of DDL?
Correct Response: Data Definition Language
● What is a primary key?
Correct Response: The primary key is the attribute or set of attributes in a table that uniquely identifies a row in that table.
● Which statement is used to query the database and retrieve specific data?
Possible Responses: Create Table/Insert/Select
Correct Response: Select
Build
7 mins
● Conduct a group discussion in the class on the topic “SQL: A Powerful Tool for Database Management and Operations”
Correct Response: SQL provides a way to communicate with and manipulate databases through the following main operations:
i. Data Querying: Allows users to retrieve specific data from databases.
ii. Data Manipulation: Includes commands to insert, update, and delete data.
iii. Data Definition: Enables users to define and modify the structure of the database objects, such as creating, altering, and dropping tables.

● Conclude the session by summarising that SQL, or Structured Query Language, is a powerful tool used for managing and manipulating data in databases. SQL statements are classified into two categories: Data Definition Language (DDL) and Data Manipulation Language (DML). The main data types used in SQL are number, character, varchar, date, and time. Keys in a database are used to define any constraints on the table. Basic SQL commands used are ‘Create Table’, ‘Insert’, and ‘Select’ commands.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Question 5
B. Tick the Correct Option: Question 5
E. Answer the Following Questions: Question 2
F. Apply Your Learning: Questions 1 and 5
At the end of the session, the students will be able to:
● know what SQL is.
● know the types of SQL statements.
● know the main data types used in SQL.
● identify the keys defined for a table.
● revise the basic SQL commands learnt in the previous grade.
Keywords
● SQL: SQL, or Structured Query Language, is a powerful tool used for managing and manipulating data in databases.
● Keys: Keys in a database are used to define any constraints on the table. Keys are also used to establish and identify relationships between tables.
Let the students watch the video or the learning slides related to the topic on the digital panel.
Explain to the students what SQL is. Explain the types of SQL statements and the data types in SQL. Explain the different keys in a database. Revise the basic SQL commands learnt in the previous grade.
Attempt the activity on the Assignment page.
Conclude the concepts
Assign homework
● Instruct the students to go to the Tekie’s Digital platform and open a Lab session on Structured Query Language 2
● Show the learning slides or the video and discuss the concepts shown on the panel.

Explain the following concepts:
Explain SQL and types of SQL statements.
Explain main data types used in SQL.
Describe the keys in a database.
Revise some basic SQL commands learnt in the previous grade.
Explain to the students that SQL is a powerful tool used for managing and manipulating data in databases. Explain to them the types of SQL statements, i.e., DDL and DML, as given on pages 104 and 105.
Explain to the students the main data types used in SQL, such as number, character, varchar, date, and time, as given on page 105.
Explain to them the main keys that can be defined for a table, such as the primary key, candidate key, composite key, and the foreign key, as given on page 106.
Revise with students some of the basic SQL commands such as the ‘Create Table’, ‘Insert’, and ‘Select’ commands, as given on pages 106 and 107.
Build
● Instruct the students to attempt the assignment by clicking on the Assignment tab.
● Explain the activity to the students.
7 mins
3 mins
● Ask the questions provided on the slides one by one to assess the students’ understanding. Discuss the answers to the questions with the students. If necessary, ask additional relevant questions. Sum Up
● Conclude the session by summarising that SQL, or Structured Query Language, is a powerful tool used for managing and manipulating data in databases. SQL statements are classified into two categories: Data Definition Language (DDL) and Data Manipulation Language (DML). The main data types used in SQL are number, character, varchar, date, and time. Keys in a database are used to define any constraints on the table. Basic SQL commands used are ‘Create Table’, ‘Insert’, and ‘Select’ commands.
● Assign the additional activity given on the panel to the students as homework.
Learning Outcomes
At the end of the session, the students will be able to:
● use the ‘Select’ statement with additional clauses.
● update data in a table.
● delete data from a table.
● use aggregate functions.
● search for specific data in a MySQL database.
Keyword
● Wildcard operators: These operators are special characters in SQL for pattern matching in text data.
Warm Up Engage Build Sum Up
Ask the students how they can modify existing records in a table.
Explain to the students some more SQL queries. Group discussion Conclude the concepts
Assign homework 5 mins 15 mins 7 mins 3 mins
Warm Up
Action Plan
● Ask the students how they can modify existing records in a table.
5 mins
● Tell the students that the ‘Update’ command modifies existing records. Also, tell them that they can delete data from a table, use aggregate functions to perform calculations on a set of values, and many other operations.
15 mins
Engage
Explain the following concepts:
Learning Outcomes
Use the ‘Select’ statement with additional clauses.
Explanation
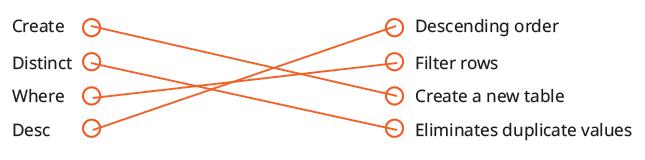
Explain to the students that there are some more clauses which can be used with the ‘Select’ statement other than the ‘Where’ clause. Tell them about the ‘Order By’ clause and the ‘Distinct’ clause, as given on pages 107 and 108.

Update data in a table.
Delete data from a table.
Use aggregate functions.
Search for specific data in a MySQL database.
Explain to the students that the ‘Update’ command modifies existing records, as given on page 108.
Tell the students that the ‘Delete’ command removes records from a table, as given on page 108.
Explain to the students about common aggregate functions to perform calculations, such as Count(), Sum(), Avg(), Max(), and Min(), as given on pages 108 and 109.
Tell the students that they can use SQL queries by specifying some condition to search for specific data using the ‘Where’ clause or the wildcard operators, as given on pages 109 and 110.
● Read aloud the questions provided in the Do It Yourself 6B section and encourage the students to solve the questions. Instruct them to write the answers in their book.
Correct Response:
● Conduct a group discussion in the class on the topic ‘Aggregate Functions to Perform Calculations using SQL’.
Correct Responses: Count(), Sum(), Avg(), Max(), Min()
● Conclude the session by summarising that the ‘Order By’, ‘Distinct’, and ‘Where’ clause are some of the clauses that can be used with the ‘Select’ statement. The ‘Delete’ command removes records from a table. Aggregate functions perform calculations on a set of values and return a single value. To search for specific data in a MySQL database, use the ‘Where’ clause or the wildcard operators.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Question 4
C. Who Am I?: Questions 1, 2, 3, 4, and 5
D. Write T for True and F for False: Questions 3 and 5
E. Answer the Following Questions: Question 5
F. Apply Your Learning: Questions 2, 3, and 4
At the end of the session, the students will be able to:
● use the ‘Select’ statement with additional clauses.
● update data in a table.
● delete data from a table.
● use aggregate functions.
● search for specific data in a MySQL database.
Keyword
Let the students watch the video or the learning slides related to the topic on the panel.
● Wildcard operators: These operators are special characters in SQL for pattern matching in text data. 5 mins
Warm Up
Explain to the students some more SQL queries. Attempt the activity on the Assignment page.
Conclude the concepts
Assign homework
● Instruct the students to go to the Tekie’s Digital platform and open a Lab session on More SQL Queries 2.
● Show the learning slides or the video and discuss the concepts shown on the panel.
Engage
Explain the following concepts:
Learning Outcomes
Use the ‘Select’ statement with additional clauses.
Explanation
Explain to the students that there are some more clauses which can be used with the ‘Select’ statement other than the ‘Where’ clause. Tell them about the ‘Order By’ clause and the ‘Distinct’ clause, as given on pages 107 and 108.

Update data in a table.
Delete data from a table.
Use aggregate functions.
Search for specific data in a MySQL database.
Demonstrate to the students how the ‘Update’ command modifies existing records, as given on page 108.
Demonstrate to the students how the ‘Delete’ command removes records from a table, as given on page 108.
Explain to the students about common aggregate functions to perform calculations, such as Count(), Sum(), Avg(), Max(), and Min(), as given on pages 108 and 109.
Demonstrate to the students how they can use SQL queries by specifying some condition to search for specific data using the ‘Where’ clause or the wildcard operators, as given on pages 109 and 110.
● Ask the questions provided on the slides one by one to assess the students’ understanding. Discuss the answers to the questions with the students. If necessary, ask additional relevant questions.
7 mins
● Instruct the students to attempt the assignment by clicking on the Assignment tab.
● Explain the activity to the students.
3 mins
● Conclude the session by summarising that the ‘Order By’, ‘Distinct’, and ‘Where’ clause are some of the clauses that can be used with the ‘Select’ statement. The ‘Delete’ command removes records from a table. Aggregate functions perform calculations on a set of values and return a single value. To search for specific data in a MySQL database, use the ‘Where’ clause or the wildcard operators.
● Assign the additional activity given on the panel to the students as homework.
This chapter is divided into the following lab sessions
1. Introduction to Python, Data Types, and Variables
2. Operators
3. Conditional Statements
4. Iterative Statements
At the end of the session, the students will be able to:
● explain Python, its features, and syntax.
● describe Python data types.
● describe what a variable is, create a variable, and name a variable.
● describe the print function, multiple assignment and dynamic typing.
Keywords
● Python: Python is a high-level dynamic programming language that is interpreted, and focused on code readability.
● Data types: The data type specifies the kind of information that will be kept in a variable.
● Variables: The reserved memory areas used to hold values in a Python program are known as variables.
Let the students watch the video or the learning slides related to the topic on the digital panel.
Explain to them what Python is. Get them familiar with Python’s features, data types, and variables.
Attempt the activity on the Assignment page.
Conclude the concepts Assign homework
Warm Up
5 mins
● Instruct the students to go to Tekie’s Digital platform and open a Lab session on Introduction to Python, Data Types, and Variables
● Show the learning slides or the video and discuss the concepts shown on the panel.
Explain the following concepts:
Explain Python, its features, and syntax.
15 mins
Tell the students that Python is a dynamic programming language. Also explain the features and syntax of Python, as given on page 1.
Describe Python data types. Explain the various Python data types to students, such as int, float, string, list, etc., as given on pages 1 and 2.
Describe what a variable is, create a variable, and name a variable.
Describe the print function, multiple assignment and dynamic typing.
Tell the students that the reserved memory areas used to hold values in a Python program are known as variables. Also, tell them how to create a variable and how to name them, as given on pages 2 and 3.
Tell students that the print function can be used to output a Python variable. Demonstrate to them how they can create several variables in a single statement with Python. Also, explain the concept of dynamic typing, as given on pages 3 and 4.
● Ask the questions provided on the slides one by one to assess the students’ understanding.
● Read aloud the questions provided in the Do It Yourself 1A section and encourage the students to solve the questions. Instruct the students to write the answers in their book.
7
● Instruct the students to attempt the assignment by clicking on the Assignment tab.
● Explain the activity to the students.
3
● Conclude the session by summarising that Python is a dynamic programming language. Various data types in Python are int, float, string, etc. The variables are the containers for storing data of various types. The print() function can be used to output a Python variable. Python specifies the kind of variable used during program execution. This concept is known as dynamic typing.
● Assign the additional activity given on the panel to the students as homework.

● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Questions 1 and 5
B. Tick the Correct Option: Questions 1 and 2
C. Who Am I?: Question 5
D. Write T for True and F for False: Question 1
E. Answer the Following Questions: Questions 3 and 4
F. Apply Your Learning: Question 1
At the end of the session, the students will be able to:
● perform operations using different types of operators.
Keyword
● Operators: Operators are predefined symbols that perform operations on one or more operands.
Let the students watch the video or the learning slides related to the topic on the digital panel. Discuss the concept of operators. Discuss arithmetic, assignment, comparison, and logical operators. Attempt the activity on the Assignment page.
Conclude the concepts Assign homework
Warm Up
● Instruct the students to go to the Tekie’s Digital platform and open a Lab session on Operators.
● Show the learning slides or the video and discuss the concepts shown on the panel.
Engage
Explain the following concepts:
Learning Outcomes
Perform operations using different types of operators.
Explanation
Explain to the students that operators are predefined symbols that perform operations on one or more operands. Discuss various types of operators and their precedence rule, as given on pages 4 to 6.
● Ask the questions provided on the slides one by one to assess the students’ understanding.
● Discuss the answers to the questions with the students. If necessary, ask additional relevant questions.

● Instruct the students to attempt the assignment by clicking on the Assignment tab.
● Explain the activity to the students.
Sum Up 3 mins
● Conclude the session by summarising that operators are predefined symbols that perform operations on one or more operands. Discuss various types of operators and their precedence rules.
● Assign the additional activity given on the panel to the students as homework.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Question 2
B. Tick the Correct Option: Question 3
C. Who Am I?: Question 1
D. Write T for True and F for False: Question 2
At the end of the session, the students will be able to:
Let the students watch the video or the learning slides related to the topic on the digital panel. Discuss the concept of conditional statements. Discuss the if, if-else, and if-elif-else statements. Attempt the activity on the Assignment page.
● use different types of conditional statements in Python programming. 5 mins
Warm Up
Conclude the concepts
Assign homework
● Instruct the students to go to the Tekie’s Digital platform and open a Lab session on Conditional Statements.
● Show the learning slides or the video and discuss the concepts shown on the panel.
Engage
Explain the following concepts:
Learning Outcome
Use different types of conditional statements.
15 mins
Explanation
Describe to the students what are conditional statements. Elaborate each type of conditional statements, i.e., if statement, if-else statement, if-elif-else statement, as given on pages 6 to 9.
● Ask the questions provided on the slides one by one to assess the students’ understanding. Discuss the answers to the questions with the students. If necessary, you may ask additional relevant questions.

● Instruct the students to attempt the assignment by clicking on the Assignment tab.
● Explain the activity to the students. Sum Up 3 mins
● Conclude the session by summarising that the programming languages use conditional statements that make decisions to control the direction or flow of the program execution. Types of conditional statements used in Python are: if statement, if-else statement, and if-elif-else statement.
● Assign the additional activity given on the panel to the students as homework.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
B. Tick the Correct Option: Questions 4 and 5
C. Who Am I?: Question 2
D. Write T for True and F for False: Questions 3 and 4
E. Answer the Following Questions: Question 5
At the end of the session, the students will be able to:
● use different types of iterative statements in Python programming.
Let the students watch the video or the learning slides related to the topic on the digital panel. Discuss the concept of iterative statements.
Discuss the while loop and for loop.
Attempt the activity on the Assignment page.
Conclude the concepts Assign homework
mins
5 mins
Warm Up
● Instruct the students to go to the Tekie’s Digital platform and open a Lab session on Iterative Statements.
● Show the learning slides or the video and discuss the concepts shown on the panel.
Engage
Explain the following concepts:
Learning Outcome
Use different types of iterative statements.
Attempt the Coding Challenge
15 mins
Explanation
Tell the students that loops are useful in Python because they allow you to execute a block of code repeatedly. Describe the two primitive loop statements of Python, i.e., while loop and for loop, along with their syntax, flowcharts, and codes, as given on pages 9 to 13.
Encourage students to attempt the coding challenge to write a Python program to create a geometry calculator, as given on page 14.
● Ask the questions provided on the slides one by one to assess the students’ understanding. Discuss the answers to the questions with the students. If necessary, you may ask additional relevant questions.

● Read aloud the questions provided in the Do It Yourself 1B section and encourage the students to solve the questions. Instruct them to write the answers in their book.
Correct Responses:
1. # Python program to compute sum of digits in a number. # Function to get sum of digits def getSum(n): sum = 0 for digit in str(n): sum += int(digit) return sum
n = 12345
print(getSum(n))
2. num = int(input(“ Enter a number : “)) # using the for loop to generate the multiplication tables print(“Table of: “) for a in range(1,11): print(num,’x’,a,’=’,num*a)
3. metres = float(input(“Enter the value in metres: “))
centimetres = metres * 100 print(metres, “metres is equal to”, centimetres, “centimetres.”)
Build
● Instruct the students to attempt the assignment by clicking on the Assignment tab.
● Explain the activity to the students.
● Conclude the session by summarising that loops are useful in Python because they allow you to execute a block of code repeatedly. Describe the two primitive loop statements of Python, i.e., while loop and for loop, along with their syntax, flowchart, and code.
● Assign the additional activity given on the panel to the students as homework.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Questions 3 and 4
C. Who Am I?: Questions 3 and 4
D. Write T for True and F for False: Question 5
E. Answer the Following Questions: Questions 1 and 2
F. Apply Your Learning: Questions 2, 3, and 4
Chapter Checkup
A. Fill in the Blanks.
1. Computer network 2. Bus 3. MAN 4. Inconsistency 5. Antivirus
B. Tick () the Correct Option.
1. c. High maintenance cost 2. a. Data, Resources 3. d. Redundancy
4. a. LAN 5. c. Router
C. Write T for True and F for False.
1. T 2. F 3. F 4. F 5. T
D. Answer the Following Questions.
1. WAN (Wide Area Network) connects computers from various countries and continents. WAN connects different LANs and MANs from across the globe. The internet is an example of a WAN.
2. Following are the advantages of computer networks:
a. Cost Reduction: Because the hardware resources (printers and scanners) are shared among all the computers on the network, the cost of additional equipment is saved.
b. Less Data Redundancy: Data redundancy occurs when the same piece of data exists in multiple places. All the data on the computer network is stored on the server. Therefore, there is less redundancy in the network.
c. Less Data Inconsistency: Data inconsistency means when the same data exists in different formats at different places. Since data redundancy is reduced, it also reduces data inconsistency.
d. Data Centralisation: All the data in a computer network is stored on a server at a centralised location. This centralised storage of data provides easy accessibility to all users.
e. Data Recovery: The server’s capability of taking regular data backup helps with easy data recovery in case of data loss or network failure.
3. A hub is a networking device that transmits the received information to all the devices on the network. A router is a device which routes the data or information over a network.
4. In star topology, the nodes are connected to a centralised hub, switch, or a computer, forming a star. The disadvantage of the star topology is that if the central computer fails, the whole network will be disabled.
5. Following are the differences between bus and ring topologies:
In a bus topology, all the nodes are connected to a single common cable.
A node puts a message on the cable that is sent to all other nodes in a network.
E. Apply Your Learning.
1. She should use a WAN.
2. Ring topology
In ring topology, the nodes are connected to each other, forming a ring.
A node forwards the message received from the previous node to the following node.
3. Wi-Fi is more beneficial than a wired network because it uses wireless communication technology to connect various devices like computers, smartphones, tablets, etc., to the internet without the need for physical cables.
4. Three disadvantages of computer networks are security concerns, data loss in case of a network failure, and complex architecture.
5. Connecting computers to computer networks brings many benefits, such as file sharing, communication, database access, data backup, etc.

Chapter Checkup
A. Fill in the Blanks.
1. data 2. column 3. DBMS 4. percent 5. SQL
B. Tick () the Correct Option.
1. b. A collection of organised information 2. c. Oracle 3. d. Network
4. c. A row in a database table 5. b. Composite Key
C. Who Am I?
1. Wildcard operator: A special character for pattern matching in text data
2. DBMS: A software application that helps users create, manage, and access databases
3. Different types of DBMS: Relational, hierarchical, and network
4. Components of a DBMS: Data, hardware, software, users, procedures, and database access language
5. Attribute: A column in a database table
D. Write T for True and F for False.
1. T 2. T 3. T 4. F 5. F
E. Answer the Following Questions.
1. Relational Database Management System (RDBMS) holds data in the form of tables, which are made up of rows and columns.
2. The SQL statements or commands that are used to insert, delete, or update data in the table of the database are called DML commands. For example, insert, delete, update, etc.
3. Here are some of the advantages of using a database:
● It can carry vast quantities of data.
● It can organise data in a manner that makes it easier to retrieve.
● It can be used to modify and erase data rapidly.
● It can be used to share data with others.
4. A database management system (DBMS) is a software application that enables you to construct, operate, and interact with databases. Some common examples of DBMSs are MySQL, Microsoft SQL Server, and Oracle.
5. Wildcard operators in SQL are special characters for pattern matching in text data. They help in finding data that matches a pattern, not just an exact value. They are used with the ‘like’ clause in an SQL query. Two main wildcard characters used in SQL are ‘%’ (matches multiple characters) and ‘_’ (matches a single character).
F. Apply Your Learning.
1. Select Emp_ID, Emp_Name From Employee;
2. Select Emp_Name From Employee Where Salary<23000;
3. Select Emp_ID, Emp_Name From Employee; Where Salary>23000;
4. Select Max(Salary), Min(Salary) From Employee;
5. Insert into Employee Values (5, 'Raman', 27500); Insert into Employee Values (6, 'Smita', 24300);
Chapter Checkup
A. Fill in the Blanks.
1. indentation 2. precedence 3. iterate 4. end 5. dictionary
B. Tick () the Correct Option.
1. a. Guido van Rossum 2. d. Sequence Types 3. a. Exponentiation 4. d. Decision-making 5. a. Greater
C. Who Am I?
1. == 2. if-elif-else 3. break 4. range() 5. Boolean
D. Write T for True and F for False.
1. T 2. F 3. T 4. F 5. T
E. Answer the Following Questions.
1. A while loop runs as long as a specified condition is true, making it ideal when the number of iterations is unknown. In contrast, a for loop iterates over a sequence or range, making it suitable when the number of iterations is predetermined. While loops can risk infinite looping if the condition is not updated, for loops handle iteration automatically.
2. The Python continue statement returns control to the beginning of the loop. Whereas, the Python break statement brings control out of the loop.
3. Following are the rules to define a variable:
● A variable name starts with a letter or the underscore character. It cannot start with a number or any special character like $, (, *, %, etc.
● A variable name can only contain alpha-numeric characters.
● Python variable names are case-sensitive, which means str1 and STR1 are two different variables in Python.
● Python keywords cannot be used as variable names.
4. The data type specifies the kind of information that will be stored in a variable. The various data types available in Python are int, float, strings, list, tuple, dictionary, boolean, set, etc.
5. Conditional statements in programming languages make decisions to control the direction or flow of the program execution.
In the if-else condition, if the condition is true, a block of statements inside the if block will be executed; but if the condition is false, the blocks in the else statement will be executed.
F. Apply Your Learning.
1. <class 'bool'>
2. for num in range(1, 11): print(num)
3. side_length = 7 area = (3**0.5 / 4) * side_length**2
print("The area of the equilateral triangle is:", area)
4. number = int(input("Enter a number: ")) next_number = number + 1 previous_number = number - 1
print("Next number is:", next_number) print("Previous number is:", previous_number)

This teacher manual has been designed to implement Tekie, the storytelling-based Coding and Computer Science program. The manual consists of lesson plans within each chapter that teachers transact within classrooms and computer labs. Each lesson is based on a research-based ‘WEBS’ framework that simplifies pedagogical practices for teachers and enables them to deliver effectively.
• Sharp Lesson Planning: Each lesson plan focuses on specific sub-learning outcomes within a chapter and are designed for delivery within the stipulated class or lab time.
• Real-life and Application-based Questions: Additional questions that link Computer Science to real-life contexts and assist teachers to develop learners’ conceptual understanding and application skills.
• Support and Detailed Solutions: In-depth solutions for in-class and post-class activities to reinforce learning.
Uolo partners with K-12 schools to provide technology-enabled learning programs. We believe that pedagogy and technology must come together to deliver scalable learning experiences that generate measurable outcomes. Uolo is trusted by over 15,000+ schools across India, Southeast Asia, and the Middle East.
ISBN 978-81-978912-5-0