





Academic Authors: Jatinder Kaur, Ayushi Jain
Creative Directors: Bhavna Tripathi, Mangal Singh Rana, Satish
Book Production: Rakesh Kumar Singh
Project Lead: Jatinder Kaur
VP, Learning: Abhishek Bhatnagar
All products and brand names used in this book are trademarks, registered trademarks or trade names of their respective owners.
© Uolo EdTech Private Limited
First published 2025
This book is sold subject to the condition that it shall not by way of trade or otherwise, be lent, resold, hired out, or otherwise circulated without the publisher’s prior written consent in any form of binding or cover other than that in which it is published and without a similar condition including this condition being imposed on the subsequent purchaser and without limiting the rights under copyright reserved above, no part of this publication may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form or by any means, electronic, mechanical, photocopying, recording or otherwise, without the prior written permission of both the copyright owner and the above-mentioned publisher of this book.
Book Title: Hexa Computer Science Teacher Manual 8
ISBN: 978-81-985754-3-2
Published by Uolo EdTech Private Limited
Corporate Office Address:
85, Sector 44, Gurugram, Haryana 122003
CIN: U74999DL2017PTC322986
Illustrations and images: www.shutterstock.com, www.stock.adobe.com and www.freepik.com
All suggested use of the internet should be under adult supervision.
In today’s rapidly evolving digital landscape, computer science has become an essential field of study, shaping the world around us in countless ways. From the smartphones in our pockets to the vast networks that connect people across the globe, computer science drives innovation and progress in nearly every aspect of modern life. In today’s fast-paced digital world, understanding the basics of computer science is as important as learning to read, write, or solve maths problems.
Recognising this imperative, the National Education Policy (NEP) 2020 has strongly recommended the integration of coding skills, computational thinking, critical analysis, and problem-solving abilities into the curriculum.
Inspired by these insights, Uolo has introduced a comprehensive program, Hexa, for grades 1 to 8, to empower young minds with the knowledge and skills they need to thrive in the digital age. From the basics of how computers function to the tools that shape our digital landscape, this series opens the door to a world of endless possibilities.
We believe that learning computer science should be an engaging and accessible experience for all children. This series takes a project-based approach, allowing students to learn by way of concurrently applying acquired knowledge and skills. As they progress through the course, they will build strong foundations in computational thinking, coding basics, and digital literacy. Our program focuses on three key areas:
1. Computer Science Fundamentals: Core concepts are introduced step by step, ensuring a solid grasp of how computers function, and how information is processed and stored.
2. Latest Computer Tools: Various computer tools relevant to today’s world are included, equipping students with the confidence to thrive in the digital age.
3. Introduction to Coding: The series offers an introductory look into coding, preparing students for more advanced learning in the future.
To support teachers in delivering effective and engaging lessons, we offer a thoughtfully designed Teacher Manual to enhance the teaching and learning experience. Rather than prescribing teaching methods, the manual provides examples and demonstrates how and why teachers can apply these examples in their classes.
Each chapter in this manual is structured to provide a comprehensive lesson plan. The chapters are divided into multiple sessions, each following the Warm up, Engage, Build, and Sum up (WEBS) strategy.
• The Warm up phase sets the stage for learning by connecting to prior knowledge and building curiosity.
• The Engage phase captures the students’ attention and motivates them to participate actively.
• In the Build phase, questions from various sections are discussed to build the understanding of the students.
• Finally, the Sum up phase reinforces learning through easy-to-recall activities and questions. Time duration for each section has been suggested based on the requirements of the students. Additionally, an answer key for every chapter is provided to assist teachers in assessing their students’ understanding and guiding their learning effectively.
We hope this Teacher Manual empowers educators to implement the curriculum effectively, support diverse student learning, and create interactive, engaging environments tailored to their students’ needs and interests.
Introduction to Computer Networks
Network Terminologies and Devices
Types of Computer Networks and Topologies
Network Architectures and Protocols
Shared Drive and Network Security
lterative Statements
Introduction to Cyber Ethics and Unethical Practices
Online Safety Measures
Digital Footprints and Digital Citizenship 3
Introduction and Working of Blockchain
Cryptocurrency: A Blockchain Case Study
Basic Tags of HTML Understanding CSS
Introduction to Apps and Accessing Apps Classification of Mobile Apps
Developing an App

This chapter is divided into the following sessions
1. Introduction to Computer Networks
2. Network Terminologies and Devices
3. Types of Computer Networks and Topologies
4. Network Architectures and Protocols
5. Shared Drive and Network Security
At the end of the session, the students will be able to:
● describe computer networks and their need.
● describe the uses of computer networks.
● explain the advantages and disadvantages of computer networks.
Keywords
● Computer network: A way to connect computers using communication devices so that they can exchange data and resources with each other.
● Server: A central computer in a network in which data is stored.
Ask the students how roads are connected to form a network.
Explain the concept of computer networks, the need of computer networks, the uses of computer networks, the advantages and disadvantages of computer networks. Group discussion Conclude the concepts Assign
● Ask the students how roads are connected to form a network.
● Just like road networks, computers can also be connected to form a computer network.
● Now, build the concept that a computer network is a way to connect computers using communication devices so that they can exchange data and resources with each other.
Explain the following concepts:
Describe computer networks and their need.
Describe the uses of computer networks.
Explain the advantages and disadvantages of computer networks.
Tell the students that a computer network is a way to connect computers using communication devices so that they can exchange data and resources with each other. Also, tell the need for a computer network, as given on pages 1 and 2.
Tell the students that computer networks are used for different purposes in our daily lives like file sharing, resource sharing, communication, etc., as given on pages 2 and 3.
Tell the students that computer networks are beneficial to us in many ways but also have some disadvantages, as given on pages 3 and 4.
● Read aloud the questions provided in the Do It Yourself 1A section and encourage students to solve them. Instruct them to write the answers in the book.
Correct Responses:
1. Resource sharing is the use of a computer network to allow multiple users or devices to share a single resource, such as a printer.
2. Through file sharing
3. One scanner is sufficient since computer networks allow resource sharing.
Build
7 mins
● Conduct a group discussion in the class among students on the topic ‘Benefits of resource sharing in a computer network’.
Possible Responses: Cost savings, resource optimisation, etc.

● Conclude the session by summarising that a computer network is a way to connect computers using communication devices so that they can exchange data and resources with each other. It has many uses such as file sharing, communication, database access, data backup, etc. Also, tell the students about various advantages and disadvantages of computer networks.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Questions 1 and 4
B. Tick the Correct Option: Questions 1, 2, and 3
C. Write T for True and F for False: Question 4
D. Answer the Following Questions: Question 2
E. Apply Your Learning: Questions 4 and 5
At the end of the session, the students will be able to:
● describe network terminologies.
● explain network devices.
Keywords
● Node: A device in a computer network which is used to send or receive data.
● Packet: A unit of data or information that is transferred over a network.
● Bandwidth: The amount of data or information that can be transmitted over the internet or network.
● Hub: A networking device that transmits the received information to and from all the devices on the network.
● Router: It is a device which routes the data or information over a network.
Ask the students about the devices at home which are connected to a network. Explain about terminologies and devices associated with computer networks.
Group discussion
Conclude the concepts
homework
5 mins
Warm Up
● Ask the students about the devices at home which are connected to a network.
● Now, build the concept that there are different devices used within a computer network. Some networking devices are network interface card (NIC), hub, switch, router, etc.

Explain the following concepts:
Describe network terminologies.
Explain to the students the various network terminologies, such as node, link, packet, protocol, etc., as given on page 5.
Explain network devices. Tell the students that computer network devices are hardware components that are required for computers to communicate with one another over the network. Also tell them about the various network devices such as the Network Interface Card (NIC), Modem, Hub, etc., as given on pages 5 and 6.
● Read aloud the questions provided in the Do It Yourself 1B section and encourage students to solve them. Instruct them to write the answers in the book.
Correct Responses:
1. a. Modem b. Ethernet networking cable
2. NIC, Modem, Hub, Switch, etc.
Build
● Conduct a group discussion in the class among students on the topic ‘Role of a modem in modern communication systems’.
Possible Response: A modem enables data transmission by converting digital signals into analog signals for travel over communication lines and vice versa. This ensures seamless connectivity between digital devices and networks.
● Conclude the session by summarising that there are various network terminologies, such as node, link, packet, protocol, etc. Also, tell them that computer network devices are hardware components that are required for computers to communicate with one another over the network.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
B. Tick the Correct Option: Question 5
C. Write T for True and F for False: Question 3
D. Answer the Following Questions: Question 3
At the end of the session, the students will be able to:
● explain different types of computer networks.
● describe various types of network topologies.
Keywords
● Wireless network: A type of Local Area Network (LAN) that uses wireless communication technology to connect various devices.
Ask students if they have heard about any type of network before.
Explain to the students about types of computer networks and topologies.
● Topology: The configuration of how computer systems or network devices are connected to one another is known as a topology. 5 mins
Think and Tell Group discussion
Conclude the concepts
Assign homework 5 mins 15 mins 7 mins 3 mins
Action Plan
Warm Up
● Ask students if they have heard about any type of network before.
● Now, build the concept that there are different types of networks, which are categorised according to the geographical area they cover. They are PAN, LAN, MAN, and WAN.
15 mins
Engage
Explain the following concepts:
Learning Outcomes
Explain different types of computer networks.
Describe various types of network topologies.
Explanation
Tell the students that there are different types of networks, which are categorised according to the geographical area they cover. Also, tell them about the wireless network, as given on page 7.
Tell the students that a topology is a physical and logical layout of different devices (nodes) and connections in a network. Also, explain its different types, as given on pages 8 and 9.

● Read aloud the questions provided in the Do It Yourself 1C section, Question 2 and encourage students to solve them. Instruct them to write the answers in the book.
Correct Response:
a. PAN b. LAN c. MAN d. WAN
Build
7 mins
● Ask the students to answer the question “Which type of network will you recommend in your school to share hardware devices?” asked in the Think and Tell section on page 8.
Correct Response: LAN
● Conduct a group discussion in the class among students on the topic “How is a tree topology better than a ring topology?“ as mentioned in the Discuss section on page 9.
Possible Responses: In tree topology, nodes are connected in a parent-child hierarchical manner. Whereas, in ring topology, the nodes are connected forming a ring. Therefore, tree topology provides more flexibility and scalability by allowing multiple paths and avoiding a single point of failure. But in ring topology, if any one node fails, the entire network will fail.
● Conclude the session by summarising that computer networks are of many types, such as PAN, LAN, MAN, WAN and wireless. Also, revise with them about different topologies of computer networks such as bus, star, ring, tree, and mesh topology.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Questions 2 and 3
B. Tick the Correct Option: Question 4
C. Write T for True and F for False: Questions 1, 2, and 5
D. Answer the Following Questions: Questions 1, 4, and 5
E. Apply Your Learning: Questions 1, 2, and 3
At the end of the session, the students will be able to:
● discuss types of network architecture.
● discuss network protocols.
Keywords
● Server: A computer in a network which has all the resources and provides services to other computers.
● Clients: The computers in a network which use services provided by the server.
● Network protocol: A set of rules which governs the communication between the computers over a network.
Warm Up Engage Build Sum Up
Ask the students how computers are connected within a network.
Explain the concept of network architecture and network protocols to the students.
Group discussion Conclude the concepts
Assign homework
5 mins
Warm Up
● Ask the students how computers are connected within a network.
● Now, build the concept by introducing students to the types of network architectures: peer-to-peer and client-server architectures.
15 mins
Engage
Explain the following concepts:
Learning Outcomes
Discuss types of network architecture.
Explanation
Tell the students about peer-to-peer architecture and client-server architecture used to design networks, as given on pages 9 and 10.

Discuss network protocols.
Tell them that network protocol is a set of rules which governs the communication between the computers over a network and explain some of the network protocols, as given on pages 10 and 11.
● Read aloud the questions provided in the Do It Yourself 1C section, Question 1 and encourage students to solve them. Instruct them to write the answers in the book.
Correct Response:

Ask the following additional questions to the students to check their understanding:
● Give one example of peer-to-peer architecture.
Possible Response: Bitcoin is an example of P2P architecture.
● Ritu has sent a file to her friend using a network. Which protocol would be used in this situation?
Possible Response: FTP
Build
● Conduct a group discussion in the class among students on the topic ‘Client-server architecture’.
Correct Responses: In this architecture, one or more nodes serve as a server and all other nodes behave as clients.
3 mins
● Conclude the session by summarising the two types of network architectures, i.e., peer-to-peer architecture and client-server architecture that are used to design networks. Also, revise the different internet protocols: TCP/IP, HTTP, FTP, SMTP, and IMAP.
● Assign the following questions as homework.
■ What are clients in a client-server architecture?
Correct Response: The computers which use services provided by the server are known as clients.
■ Shreya is searching for some information on the internet. Which protocol would be used in this situation?
Correct Response: HTTP
■ What is the full form of IMAP?
Correct Response: Internet Message Access Protocol Sum Up
At the end of the session, the students will be able to:
● store and share a file on Google Drive.
● describe some security measures to secure a network.
Keywords
● Google Drive: A virtual space where you can save and share files.
● Firewall: A network security device that monitors and filters incoming and outgoing network traffic based on an organisation’s previously established security policies.
Ask the students how they share their school notebooks to complete the work.
Ask the students how they secure themselves from bacteria and infections.
Explain the concept of shared drive and network security. Group discussion Conclude the concepts
Assign homework
Action Plan
Warm Up
● Ask the students how they share school notebooks to complete the work.
● Ask the students how they secure themselves from bacteria and infections.
● Now, build the concept that Google Drive is a virtual space where we can save our files and share them with others.
● Also tell them that because of security breaches on the network, it is necessary to use some network security measures.

Explain the following concepts:
Describe how to access a file from a shared drive.
Describe some security measures to secure a network.
Tell the students that they can share their data with other users even if they are living in a very faraway place through Google Drive. Tell them how to store and share a file on Google Drive, as given on pages 11 to 13.
Tell students that because of security breaches on the network, it is necessary to use some network security measures. Discuss safe online practices, as given on page 14.
Ask the following questions to the students to check their understanding:
● Tom wants to share some photos with his friend. Where can he share the photos?
Possible Response: He can use Google Drive to share photos.
● Name some antiviruses.
Possible Responses: AVG, Quick Heal, Norton, McAfee, Avast, etc.
Build
7 mins
● Conduct a group discussion in the class among students on the topic ‘Safe Online Practices’.
Possible Responses: Clear browser cookies, remove unknown or unwanted applications, regularly update all applications and software, etc.
3 mins
Sum Up
● Conclude the session by summarising that students can share their data with other users even if they are living in a very faraway place through Google Drive. Revise how to store and share a file on Google Drive. Also, tell them that a firewall is a network security device that monitors and filters incoming and outgoing network traffic. Discuss some of the safe online practices also.
● Assign the following from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Question 5
Additional questions
● Can a receiver of the file shared via Google Drive edit the file?
Correct Response: Yes, if permission is given.
● What are some examples of firewalls?
Possible Responses: Sophos Firewall, Check Point Firewall, pfSense Plus, WatchGuard, etc.
● Why are antiviruses necessary?
Correct Response: Computers are vulnerable to attacks or viruses when they are connected to a network. Therefore, it is necessary to install antivirus software on the computer system.
This chapter is divided into the following sessions
1. Introduction to Cyber Ethics and Unethical Practices
2. Online Safety Measures
3. Digital Footprints and Digital Citizenship
At the end of the session, the students will be able to:
● explain cyber ethics.
● describe some key aspects of cyber ethics.
● beaware of different problems in achieving cyber ethics.
● describe some unethical practices.
Keywords
● Cyber ethics: The study of appropriate behaviour and moral principles in the digital sphere is known as cyber ethics.
● Cyberbullying: It refers to using the internet to harass, scare, or hurt people.
● Phishing: It is a dishonest internet practice in which attackers pretend to be reliable organisations and trick people into disclosing personal information.
Ask the students which ethics they follow in their lives. Explain the concept of cyber ethics and unethical practices. Group discussion
Conclude the concepts Assign homework

● Ask the students which ethics they follow in their lives.
● Now, build the concept that you must follow some ethics while working on the computer which are known as cyber ethics, also referred to as internet ethics or online ethics.
Explain the following concepts:
Learning Outcomes
Explanation
Explain cyber ethics. Discuss with the students that the study of appropriate behaviour and moral principles in the digital sphere is known as cyber ethics, also referred to as internet ethics or online ethics, as given on page 18.
Describe some key aspects of cyber ethics.
Explain to them that these ethical principles are essential to ensure responsible and ethical conduct in the use of technology and the online environment, as given on pages 18 and 19.
Aware of different problems in achieving cyber ethics.
Describe some unethical practices.
Tell them about some issues in achieving cyber ethics, as given on page 19.
Identity theft happens when someone pretends to be someone else. He/she does this often to steal money, data, or other important information, like credit card details, bank details, etc. This can really hurt people, causing them emotional and financial problems.
Describe some unethical practices that are prevalent in society these days, like cyberbullying, cyberstalking, plagiarism, phishing, hacking, spamming, and identity theft, as given on pages 19 to 21.
● Read aloud the question provided in the Do It Yourself 2A section and encourage the students to solve the questions. Instruct the students to write the answers in their book.
Correct Responses:
Match the following.
Spamming
Pretending to be a reliable source in order to trick others into disclosing their passwords or personal information.
Phishing Sending emails or messages that are meaningless and unnecessary. Identity theft When an unauthorised person tries to access a computer system, a network, or data.
Hacking Stealing someone’s personal information to commit fraud.
● Pihu is working on the computer. Which cyber ethics should she follow to be a responsible user of the technology?
Possible Responses: Privacy Safeguards, Online Behaviour, Digital Security, Bridging the Digital Divide, and Accountability.
Online safety measures are safeguards and behaviour designed to keep your security, privacy, and personal information safe when using the internet. Here are some important tips for online safety:
Use Secure Passwords: Create strong, challenging passwords for each of your accounts and change them frequently. Use a combination of symbols, numbers, and letters.
Phishing Alert: Be wary of emails, messages, or websites that request private data, such as passwords or credit card numbers. Before sharing any personal information, make sure the sender or website is
● Rohan, a school teacher, wants to implement cyber ethics in his school. What possible problems he may face in achieving this?
Possible Responses: Restriction, Interpretation, Enforcement, Anonymity, and Evolving Technology.
● Naina has copied Ranbir’s content without his permission and represented it as her creation. Is she following unethical practices?
Possible Response: Yes, copying someone’s content without permission is called plagiarism.
7 mins
● Conduct a group discussion in the class among students on the topic “Think of issues on which people might disagree regarding online behaviour”, as given in the Discuss section on page 19.
Possible Responses: Privacy, Cyberbullying, Online Harassment, Freedom of Speech, Intellectual Property, etc. are some issues on which people might disagree regarding online behaviour.
● Conduct a group discussion in the class among students on the topic “Is it ethical to copy any data for your project from the internet?”, as given in the Discuss section on page 20.
Possible Responses: Copying data from the internet without the permission of the creator is an unethical practice.
3 mins
● Conclude the session by summarising that the study of appropriate behaviour and moral principles in the digital sphere is known as cyber ethics, also referred to as internet ethics or online ethics. These ethical principles are essential to ensure the responsible and ethical conduct in the use of technology and the online environment. Also, describe some issues in achieving cyber ethics, such as restrictions, interpretation, enforcement, anonymity, and evolving technology.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Questions 1, 2, 3, 4, and 5
B. Tick the Correct Option: Questions 2, and 4
C. Who Am I?: Questions 1, 3, and 4
D. Write T for True and F for False: Questions 1, 2, and 5
E. Answer the Following Questions: Questions 1, 4, and 5
F. Apply Your Learning: Questions 1, 2, 3, 4, and 5

At the end of the session, the students will be able to:
● explain some online safety measures.
Keyword
● Online safety measures: These refer to safeguards and behaviours designed to keep your security, privacy, and personal information safe when using the internet.
Ask the students if they have ever shared their personal information online. Explain online safety measures to the students. Think and Tell Conclude the concepts Assign homework
Warm Up
● Ask the students: Have you ever shared your personal information online?
● Now, build the concept that you should follow some online safety measures to be safe while working on the internet.
Explain the following concepts:
Learning Outcome
Explanation
Explain some online safety measures. Discuss with the students that online safety measures are safeguards and behaviours designed to keep your security, privacy, and personal information safe when using the internet, as given on pages 21 to 23.
Ask the Additional Questions to the students to Check for Understanding:
● Name some online safety measure that you should follow.
Possible Response: Use secure passwords, regularly update softwares, use secure wifi, etc.
● Mahi wants to set a strong password for her email account. What should she do to make the password strong?
Possible Responses: She can use a combination of symbols, numbers, and letters to make the password strong.
7 mins
Build
● Ask the students to answer the question “What measures should you follow while shopping online?”, asked in the Think and Tell section on page 23.
Possible Responses: Use secure passwords, shop from trusted websites, beware of phishing scams, use secure payment methods, protect personal information, etc., are some security measures that should be followed.
Sum Up
3 mins
● Conclude the session by summarising that online safety measures are safeguards and behaviours designed to keep your security, privacy, and personal information safe when using the internet.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
B. Tick the Correct Option: Question 1
E. Answer the Following Questions: Question 3

At the end of the session, the students will be able to:
● describe digital footprints.
● describe digital citizenship.
Keywords
● Digital footprints: It is an online activity trail which may include everything you do online, like sending emails, publishing on social media, and even just surfing websites.
● Digital citizenship: The term used to describe the ethical and responsible use of technology is known as digital citizenship.
Ask the students if they have ever noticed that the things they search for on the internet appear as advertisements while scrolling through social media apps.
Explain digital footprints and digital citizenship to the students.
Warm Up
● Ask the students if they have ever noticed that the things they search for on the internet appear as advertisements while scrolling through social media apps.
● Now, build the concept by telling them about digital footprints.
Explain the following concepts:
Describe digital footprints.
Explanation
Tell them that your digital footprint reveals where you have been online, just like your footprints in the sand do, as given on page 24.
In India, when someone writes a book, creates music, or makes art, their work is protected by copyright. This protection lasts for their whole life, and then an additional 60 years. If there are many authors, it lasts for 60 years after the last author passes away.
Describe digital citizenship. Explain to them that by engaging in good digital citizenship, we help create a more secure and civilised online community for everyone, as given on page 24.

● Read aloud the question provided in the Do It Yourself 2B section and encourage the students to solve the questions. Instruct the students to write the answers in their book.
Tick () the activity that will contribute to the digital footprint:
Shopping for a school bag
Posting a comment on a friend's picture on social media Watching a movie
● What are some examples of a digital footprint?
The study of appropriate behaviour and moral principles in the digital sphere is known as cyber ethics, also referred to as internet ethics or online ethics.
Possible Responses: Social media posts, online shopping, emails, search history, online comments and reviews are some examples of digital footprint.
While using the internet, you have to be very careful and respect others’ privacy.
● Hina is posting some offensive messages on her social media account. What would you suggest to her about this action?
Using the internet to harass, scare, or hurt people is referred to as cyberbullying.
Cyberstalking is the practice of constantly following someone’s online activity, mostly with the intention of frightening or upsetting them.
When someone copies another person’s ideas, work, or content without giving proper credit or getting permission, it is called plagiarism.
Phishing is a dishonest internet practice in which attackers pretend to be reliable organisations and trick people into disclosing personal information, such as passwords or financial information.
Hacking involves unauthorised access to computer systems, networks, or devices.
7 mins
Possible Response: To be a good digital citizen, she should avoid posting any kind of offensive or dangerous material on social media. Build
● Conduct a group discussion in the class among students on the topic “Examples of Digital Citizenship”. Possible Responses: Respecting others, privacy protection, use reliable sources, online etiquette.
Spamming refers to sending lots of unwanted and annoying messages to many people, often to make money or promote something.
● Conclude the session by summarising that an online activity trail is what a digital footprint looks like. It includes everything you do online, including sending emails, publishing on social media, and even just surfing websites. Digital citizenship is the term used to describe the ethical and responsible use of technology.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
PM
B. Tick the Correct Option: Questions 3 and 5
C. Who Am I?: Questions 2 and 5
D. Write T for True and F for False: Questions 3 and 4
E. Answer the Following Questions: Question 2

This chapter is divided into the following sessions
1. Introduction and Working of Blockchain
2. Cryptocurrency: A Blockchain Case Study
At the end of the session, the students will be able to:
● describe blockchain.
● explain the features of blockchain.
● explain the working of blockchain.
● explain the challenges of blockchain.
Keyword
● Blockchain: The technology that stores information in the form of blocks connected through a chain one after another.
Ask the students if they have worked on a shared document.
Explain the meaning of the term blockchain and its features.
Explain to them about the workings and challenges of blockchain.
Group discussion Think and Tell
Conclude the concepts
Assign homework
5 mins Warm Up
● Ask the students if they have worked on a shared document. Then, explain to them that if they make any changes to the document, it will be visible to all.
● Relate the concept of Blockchain technology so that it also works in the same manner.
Explain the following concepts:
15 mins
Describe blockchain. Describe to the students that blockchain helps computers to keep important information safe by connecting the pieces of information together in a way that is hard to cheat. Give examples to communicate the correct meaning of the given terms, as given on page 28.
Explain the features of blockchain.
Explain the workings of blockchain.
Explain the challenges of blockchain.
Tell the students that there are many features of blockchain. Explain the meaning of each feature of blockchain, like decentralisation, security and immutability, transparency, user privacy, and security. Discuss the various features of blockchain, as given on page 29.
Explain the step-by-step process of buying and selling artwork using blockchain. Describe the working mechanism of blockchain to the students by explaining the example, as given on pages 29 to 31.
Describe the challenges of blockchain technology, as given on page 31.
● Read aloud the questions provided in the Do It Yourself 3A section and encourage the students to solve the questions. Instruct the students to write the answers in their book.
Correct Responses:
1. c. A decentralised digital book of records
2. a. F b. T c. F d. F
3. No, because once information is added to a block in the blockchain, it cannot be changed without everyone knowing.
1. What is a block in blockchain technology?
2. Explain the meaning of “Blockchain is transparent in nature.”
Correct Responses:
1. A blockchain is a decentralised database that keeps an ever-expanding collection of organised records known as blocks. These blocks are interconnected through cryptography.
2. Blockchain technology is transparent in nature as information is not hidden from the user.

● Conduct a group discussion in the class among the students based on the topic “What would happen if one or two individuals of the group could add details in the diary that were not accurate?” provided in the Discuss section on page 28.
Possible Response: The accuracy and integrity of the diary’s information would be compromised, leading to potential misinformation or confusion.
● Ask the students to answer the question “What information is so important on the agreement that the blockchain should not allow any party to change it? ” asked in the Think and Tell section given on page 30.
Possible Response: The blockchain ensures critical information like ownership, transactions, or contracts remains immutable to maintain trust and security.
● Conclude the session by summarising that blockchain technology is used to keep the information safe from the hands of the intruders. There are many features of blockchain technology, as it is decentralised, secure, immutable, and transparent. Give examples to explain the workings and challenges of the blockchain to the students.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Questions 1, 2, 3, and 4
B. Tick the Correct Option: Questions 1, 2, 3, and 4
C. Who Am I?: Questions 1 and 3
D. Write T for True and F for False: Questions 1, 2, and 3
E. Answer the Following Questions: Questions 1, 2, 3, 4, and 5
F. Apply Your Learning: Questions 1, 2, and 4
At the end of the session, the students will be able to:
● describe cryptocurrency.
● describe how cryptocurrency works on the blockchain.
Keyword
● Cryptocurrency: It is a purely digital or virtual currency that can work as a medium to exchange.
Ask the students if they can recall what blockchain technology is and the challenges that can be faced while using it. Explain the students what cryptocurrency is. Describe how cryptocurrency works on the blockchain. Group discussion Conclude the concepts Assign homework
● Ask the students if they can recall what blockchain technology is and the challenges that can be faced while using this technology. Tell the students that cryptocurrency is an application of blockchain technology.
Explain the following concepts:
Learning Outcomes
Explanation
Describe cryptocurrency. Tell the students about the INR as the national currency of India. Explain the difference between cryptocurrency and normal currency. Describe cryptocurrency to the students, as given on page 32.

Describe how cryptocurrency works on the blockchain.
Describe how to implement cryptocurrency using blockchain technology. Explain how buying and selling using cryptocurrency is different from the usual or traditional method, as given on pages 32 to 34.
● Read aloud the questions provided in the Do It Yourself 3B section and encourage the students to solve the questions. Instruct the students to write the answers in their book.
Correct Responses:
1. Cryptocurrency: Digital currency that works on blockchain.
Bitcoin: A famous example of cryptocurrency.
Traditional currency: Physical coins and banknotes used for buying.
2. Similarities:
● Both traditional currencies and cryptocurrencies can be used to buy goods and services.
● They both have value and can be exchanged for other currencies or assets.
Differences:
● Traditional currencies are regulated by governments but cryptocurrencies are decentralised.
● Traditional currency transactions go through banks, whereas, cryptocurrency transactions are recorded on a public ledger.
7 mins
Build
● Conduct a group discussion in the class on the topic “Importance of Cryptocurrency”.
Possible Response: Cryptocurrency replaces the traditional banking method for buying and selling of products.
3 mins
● Conclude the session by summarising that blockchain technology is very important, and its application is cryptocurrency which ditches the traditional banking system, and also makes buying and selling of products easier and safer.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Question 5
C. Who Am I?: Questions 2, 4, and 5
D. Write T for True and F for False: Questions 4 and 5
F. Apply Your Learning: Question 3
This chapter is divided into the following sessions
1. Introduction to Apps and Accessing Apps
2. Classification of Mobile Apps
3. Developing an App
At the end of the session, the students will be able to:
● discuss what an app is.
● explain different types of apps.
● access apps.
Keywords
● Apps: They are software programs or mobile applications that can be downloaded and installed on electronic devices like smartphones, tablets, and computers.
● Mobile Apps: Mobile apps are programs you install on your phone to make it more fun or helpful for whatever you want to do.
● Desktop Apps: Desktop apps are like the computer version of the apps that you use on your phone, but they are designed to work on your computer and do all sorts of things, from writing documents to playing games or editing pictures.
● Web Apps: A web app is a software application that operates on web servers and is accessed by users through web browsers over the internet.

Ask the students if they have played games on their parents’ mobile.
Explain to the students the concept of apps.
Discuss different types of apps. Tell them about different methods to access the apps.
Think and Tell
Group discussion
Conclude the concepts
Assign homework
● Ask students if they have played games on their parents’ mobile.
● Tell the students that the game they played is an app.
Explain the following concepts:
Explanation
Discuss apps. Discuss with the students that an app refers to a program or software application designed to perform specific tasks or functions on a computer, smartphone, tablet, or other kinds of digital devices, as given on page 38.
Explain different types of apps.
Explain to the students about different types of apps like social networking apps, productivity apps, gaming apps, food delivery and cooking apps, as given on pages 38 to 40.
Access apps. Tell the students that they can access apps from their mobile phones, desktops, or directly from the web, as given on pages 40 to 42.
● Read aloud the question provided in the Do It Yourself 4A section and encourage the students to solve the questions. Instruct the students to write the answers in the book.
Correct Responses:
app
delivery app
Build







7 mins
● Ask the students to answer the question “What are the most popular apps according to you?”, asked in the Think and Tell section on page 40.
Possible Responses: Zomato, Microsoft Word, Facebook, Google Drive, Temple Run, etc.
● Conduct a group discussion in the class among students based on the topic “Why do you think apps were invented? How do they make our lives easy?”, as given in the Discuss section on page 41.
Possible Responses: Apps were invented to provide users with convenient access to specific functionalities or services on digital devices such as smartphones, tablets, and computers. These apps make our lives easy as they can be used for playing games, accessing social media, learning, productivity, communication, and many other activities.
Sum Up
3 mins
● Conclude the session by summarising an app refers to a program or software application designed to perform specific tasks or functions on a computer, smartphone, tablet, or other kinds of digital devices. There are different types of apps like social networking apps, productivity apps, gaming apps, food delivery and cooking apps. One can access apps from their mobile phones, desktops, or directly from the web.

● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Questions 1 and 5
B. Who Am I?: Question 3
C. Write T for True and F for False: Questions 1 and 3
D. Answer the Following Questions: Question 3
E. Apply Your Learning: Question 4
At the end of the session, the students will be able to:
● classify mobile apps.
Keywords
● Native apps: They are specifically designed for particular types of phones, such as iPhones or Android phones.
● Hybrid apps: They can work on different types of phones and use web technologies, allowing them to work on multiple platforms and access device features.
● Educational apps: These apps are software applications designed to facilitate learning and provide educational content on various subjects and skills.
● Social networking apps: These apps are like virtual platforms where you can meet and talk to your friends and even make new ones.
● Entertainment apps: These apps are online portals for having fun and enjoyment on your phone or tablet.
● Banking apps: These apps are like a virtual bank branch on your phone or tablet.
● E-commerce apps: These are online stores on your phone or tablet.
Ask the students to name any app that they have used for entertainment. Discuss how to classify apps based on how they are created and used.
● Ask the students to name any app that they have used for entertainment.
● Relate to the concept that today we have apps for almost everything. Tell them there are educational apps, social networking apps, entertainment apps, banking apps, and e-commerce apps.

Explain the following concepts:
Classify mobile apps. Discuss with the students that the apps can be classified based on the technology used to create them, and their usage, as given on pages 43 to 45.
● Read aloud the question provided in the Do It Yourself 4B section and encourage the students to solve the questions. Instruct the students to write the answers in the book.
Correct Responses:
1. Native apps: Camera, Gallery, Clock, Maps
Hybrid apps: Uber, Zomato, Instagram, Telegram, and X (formerly known as Twitter) I use native apps the most.
2. a. Educational apps
b. Social networking apps
c. Banking apps
d. E-commerce apps
e. Entertainment apps Build
● Conduct a group discussion in the class among students based on the topic “How can we get hybrid apps on our phones? Is it similar to how we get the native apps?”, as given in the Discuss section on page 44.
Possible Responses: We can download hybrid apps from the app stores. Getting hybrid apps on your phone is generally similar to getting native apps.
● Conclude the session by summarising that apps can be classified based on the technology used to create them as native and hybrid. Based on their usage, apps can be classified as educational apps, social networking apps, entertainment apps, banking apps, and e-commerce apps.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Questions 2, 3, and 4
B. Who Am I?: Questions 1, and 5
C. Write T for True and F for False: Questions 2 and 4
D. Answer the Following Questions: Questions 1, 2, and 4
E. Apply Your Learning: Questions 2, 3, and 5
At the end of the session, the students will be able to:
● create an app.
● create code for the app.
● test the app.
Keyword
● MIT App Inventor: It is a visual development platform that allows users to create mobile applications for Android devices without the need to write traditional codes.
Ask the students whether they know how to operate apps.
Demonstrate to the students how to develop an app using MIT App Inventor.
Attempt the given activity.
Conclude the concepts Assign homework
Warm Up
● Ask the students whether they know how to operate apps.
● Now, build the concept by asking the students whether they will be excited to create apps themselves.
Engage
Explain the following concepts:
Learning Outcomes
15 mins
Explanation
Create an app. Explain to the students that MIT App Inventor is a visual development platform that allows users to create mobile applications for Android devices without the need to write any traditional codes, as given on page 46. Also, demonstrate to them how to create an app, as given on pages 46 to 50.

Create code for the app. Tell the students that they can create code for their app by using various blocks present in the Blocks Editor. Demonstrate to them the steps to create code for the app, as given on pages 51 and 52.
Test the app. Demonstrate to them the steps to test an app, as given on pages 52 and 53.
● Read aloud the question provided in the Do It Yourself 4C section and encourage the students to solve the questions. Instruct the students to write the answers in the book.
Correct Responses:
1. Do it yourself in the Lab
Build
7 mins
● Sharon wants to surprise her dad with a personalised birthday gift. Help her to create an app with a button that, when pressed, displays an image of flowers.

3 mins
● Conclude the session by summarising that MIT App Inventor is a visual development platform that allows users to create mobile applications for Android devices without the need to write traditional codes. Also summarise how to create an app, create code for the app, and test the app.
● Assign the additional activity given on the panel to the students as homework.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
B. Who Am I?: Questions 2 and 4
C. Write T for True and F for False: Question 5
D. Answer the Following Questions: Question 5
E. Apply Your Learning: Question 1
This chapter is divided into the following sessions
1. Databases and DBMS
2. Structured Query Language
At the end of the session, the students will be able to:
● describe databases and its advantages.
3. More SQL Queries
● describe the concept of Database Management System.
Keywords
● Database: Data organised and structured in a digital form on a computer.
● DBMS: A database management system (DBMS) is a software application that enables you to construct, operate, and interact with databases.
● Data: It is a collection of fundamental facts and figures that are recorded in a database.
● Database Access Language: It is a language that allows users to give commands to a database to operate the stored data.
Ask the students about the importance of the library. Also, ask them how they fetch a book in a library. Explain to the students the meaning of the databases and their advantages. Explain to them the meaning of the term DBMS—its role, types, and different components. Group

● Ask the students about the importance of the library.
● Ask the students about the process of fetching a type of book. For example, if he/she wants to find a science fiction book, then in what column will they search for the book?
● Tell the students that just like how books are properly organised in a library, data stored in a computer are also organised in the form of a database.
Explain the following concepts:
Describe database and its advantages.
Describe the concept of a DBMS.
Explain to the students that a database is a collection of tables, where each table consists of rows and columns. Explain the structure of a table. Also, explain the advantages of databases, as given on the pages 55 and 56.
Explain the concept of DBMS to the students. Also, tell them about its role. Tell the students that there are four types of DBMS, such as HDBMS, RDBMS, OODBMS, and NDBMS. Tell them about the various components of a DBMS, such as data, hardware, software, users, procedures and Database Access Language, as given on pages 56 to 58.
● Read aloud the questions provided in the Do It Yourself 5A section and encourage the students to solve the questions. Instruct the students to write the answers in their book.
Correct Responses:
1. The components of DBMS are data, hardware, software, users, procedures, and Database Access Language.
2. There are four types of DBMS, such as HDBMS (Hierarchical Database Management System), RDBMS (Relational Database Management System), OODBMS (Object-oriented Database Management System), and NDBMS (Network Database Management System). Build 7 mins
● Conduct a group discussion in the class among the students based on the topic “Is it important for data to be organised”, provided in the Discuss section on page 56.
Correct Responses: Organising data is essential to facilitate readability and streamline work processes. Analysing raw data can be challenging, so arranging it systematically is crucial to effectively representing and interpreting information.
● Ask the students to give the answer to the question “Where have you seen the use of a database in your daily life?”, asked in the Think and Tell section on page 55.
Possible Responses: School
Correct Responses: School, shops, mall, office, and hospital
● Ask the students to give the answer to the question “Do you think that a person with special knowledge of databases is required to handle it?”, asked in the Think and Tell section on page 57.
Possible Responses: Yes, No
Correct Response: Yes. Databases are complex systems that require expertise to manage, design, and maintain.
3 mins
● Conclude the session by summarising that a database is a collection of tables that helps to organise data. A database management system (DBMS) is a software application that enables you to construct, operate, and interact with databases.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Questions 1, 2, and 3
B. Tick the Correct Option: Questions 1, 2, 3, and 4
D. Write T for True and F for False: Questions 1, 2, and 4
E. Answer the Following Questions: Questions 1, 3, and 4

At the end of the session, the students will be able to:
● know what SQL is.
● know the types of SQL statements.
● know the main data types used in SQL.
● identify the keys defined for a table.
● revise the basic SQL commands learnt in the previous grade.
Keywords
● SQL: SQL, or Structured Query Language, is a powerful tool used for managing and manipulating data in databases.
Ask students how they can retrieve specific data from databases. Explain to the students what SQL is. Explain the types of SQL statements and the data types in SQL. Explain the different keys in a database. Revise the basic SQL commands learnt in the previous grade.
● Keys: Keys in a database are used to define any constraints on the table. Keys are also used to establish and identify relationships between tables. 5 mins
● Ask the students how they can retrieve specific data from databases.
● Tell them that they can use SQL, or Structured Query Language for managing and manipulating data in databases.
Explain the following concepts:
Explain SQL and types of SQL statements.
Explain main data types used in SQL.
Describe the keys in a database.
Revise some basic SQL commands learnt in the previous grade.
Explain to the students that SQL is a powerful tool used for managing and manipulating data in databases. Explain to them the types of SQL statements, i.e., DDL and DML, as given on pages 58 and 59.
Explain to the students the main data types used in SQL, such as number, character, varchar, date, and time, as given on page 59.
Explain to them the main keys that can be defined for a table, such as the primary key, candidate key, composite key, and the foreign key, as given on page 60.
Revise with students some of the basic SQL commands such as the ‘Create Table’, ‘Insert’, and ‘Select’ commands, as given on pages 60 and 61.
Ask the following additional questions to check the students’ understanding:
● What is the full form of DDL?
Correct Response: Data Definition Language
● What is a primary key?
Correct Response: The primary key is the attribute or set of attributes in a table that uniquely identifies a row in that table.
● Which statement is used to query the database and retrieve specific data?
Possible Responses: Create Table/Insert/Select
Correct Response: Select
Build
7 mins
● Conduct a group discussion in the class on the topic “SQL: A Powerful Tool for Database Management and Operations”
Correct Response: SQL provides a way to communicate with and manipulate databases through the following main operations:
i. Data Querying: Allows users to retrieve specific data from databases.
ii. Data Manipulation: Includes commands to insert, update, and delete data.
iii. Data Definition: Enables users to define and modify the structure of the database objects, such as creating, altering, and dropping tables.

● Conclude the session by summarising that SQL, or Structured Query Language, is a powerful tool used for managing and manipulating data in databases. SQL statements are classified into two categories: Data Definition Language (DDL) and Data Manipulation Language (DML). The main data types used in SQL are number, character, varchar, date, and time. Keys in a database are used to define any constraints on the table. Basic SQL commands used are ‘Create Table’, ‘Insert’, and ‘Select’ commands.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Question 5
B. Tick the Correct Option: Question 5
E. Answer the Following Questions: Question 2
F. Apply Your Learning: Questions 1 and 5
Learning Outcomes
At the end of the session, the students will be able to:
● use the ‘Select’ statement with additional clauses.
● update data in a table.
● delete data from a table.
● use aggregate functions.
● search for specific data in a MySQL database.
Keyword
● Wildcard operators: These operators are special characters in SQL for pattern matching in text data.
Warm Up Engage Build Sum Up
Ask the students how they can modify existing records in a table.
Explain to the students some more SQL queries. Group discussion Conclude the concepts
Assign homework 5 mins 15 mins 7 mins 3 mins
Warm Up
Action Plan
● Ask the students how they can modify existing records in a table.
5 mins
● Tell the students that the ‘Update’ command modifies existing records. Also, tell them that they can delete data from a table, use aggregate functions to perform calculations on a set of values, and many other operations.
15 mins
Engage
Explain the following concepts:
Learning Outcomes
Use the ‘Select’ statement with additional clauses.
Explanation
Explain to the students that there are some more clauses which can be used with the ‘Select’ statement other than the ‘Where’ clause. Tell them about the ‘Order By’ clause and the ‘Distinct’ clause, as given on pages 61 and 62.

Update data in a table.
Delete data from a table.
Use aggregate functions.
Search for specific data in a MySQL database.
Explain to the students that the ‘Update’ command modifies existing records, as given on page 62.
Tell the students that the ‘Delete’ command removes records from a table, as given on page 62.
Explain to the students about common aggregate functions to perform calculations, such as Count(), Sum(), Avg(), Max(), and Min(), as given on pages 62 and 63.
Tell the students that they can use SQL queries by specifying some condition to search for specific data using the ‘Where’ clause or the wildcard operators, as given on pages 63 and 64.
● Read aloud the questions provided in the Do It Yourself 5B section and encourage the students to solve the questions. Instruct them to write the answers in their book.
Correct Response:

● Conduct a group discussion in the class on the topic ‘Aggregate Functions to Perform Calculations using SQL’.
Correct Responses: Count(), Sum(), Avg(), Max(), Min()
● Conclude the session by summarising that the ‘Order By’, ‘Distinct’, and ‘Where’ clause are some of the clauses that can be used with the ‘Select’ statement. The ‘Delete’ command removes records from a table. Aggregate functions perform calculations on a set of values and return a single value. To search for specific data in a MySQL database, use the ‘Where’ clause or the wildcard operators.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Question 4
C. Who Am I?: Questions 1, 2, 3, 4, and 5
D. Write T for True and F for False: Questions 3 and 5
E. Answer the Following Questions: Question 5
F. Apply Your Learning: Questions 2, 3, and 4
This chapter is divided into the following sessions
At the end of the session, the students will be able to:
● create a video in Canva.
● define components of a video editor in Canva.
● add videos in Canva.
Keyword
● Video Editing: It is a process of arranging and modifying video clips to create a video project.
Have you ever watched a video that captivated you with its visuals and made you feel something? What made it so effective? Tell the students about the Canva video editor and its components. Also explain to them about adding videos by using upload and Canva’s video library. Group
Action Plan
Conclude the concepts
Assign homework
5 mins
Warm Up
● Ask the students if they have ever watched a video that captivated them with its visuals and made them feel something. What made it so effective?
● Now, build the concept by telling them how to create a video in Canva.

Explain the following concepts:
Create a video in Canva.
Define components of a video editor in Canva.
Define the concept of a video editor to the students. Tell them how to create a video in Canva as given on pages 68 and 69.
Discuss the components of video editor like canvas, timeline, zoom control, grid view, preview, elements, text tool, uploads, draw, projects, notes and Canva assistant as given on pages 69 and 70.
Add videos in Canva. Discuss with the students how to add the video in Canva using upload and Canva’s video library, as given on pages 70 and 71.
● Ask the following questions to the students provided in the Do It Yourself 6A section and encourage the students to solve the questions. Instruct the students to write the answers in their book.

Build
7 mins
● Conduct a group discussion in the class among the students based on the topic ‘Canva’s Timeline feature’.
Possible Responses: The timeline is a critical component that allows you to control the timing of your video. You can arrange elements on the timeline to determine when they appear and for how long. It helps you arrange objects like text, images and videos in the desired sequence.
Correct Responses: Sum Up
3 mins
● Conclude the session by summarising the process of creating a video and explaining the components of the video editor in Canva such as timeline, zoom controls, grid view, etc. Explore the steps to add a video into Canva by using upload and Canva’s video library options.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Questions 1, 2, 3, and 5
B. Tick the Correct Option: Questions 1 and 4
C. Who Am I?: Questions 1, 2, 4, and 5
D. Write T for True and F for False: Questions 1 and 4
E. Answer the Following Questions: Questions 1, 2, and 4
F. Apply Your Learning: Questions 4 and 5

At the end of the session, the students will be able to:
● use basic video editing tools.
● apply effects on videos.
● download and share a video.
Keywords
● Animation: It makes video more dynamic.
● Downloading: It lets you save your video.
● Sharing: It helps you show videos to others or collaborate on it.
Ask students the meaning of editing. Tell the students about basic video editing tool and effects on video like by applying filters. Also explain adding text and graphics and using animation. Describe the steps to download and share videos in Canva.
Action Plan
Warm Up
● Ask students the meaning of editing.
● Now, build the concept by telling them the meaning of editing and then tell them about basics of video editing.
Engage
Explain the following concepts:
Learning
Explanation
Use basic video editing tools. Explain the students about some basic video editing tools like trimming, splitting resizing, and cropping video along with the steps to do so. Tell them about adding and edit audio in Canva as given on pages 71 to 73.
Apply effects on videos.
Download and share a video.
Tell the students that you can enhance your video in Canva by applying filters, adding text and graphics, and using animation along with their steps, as given on pages 73 and 74.
Tell the students that downloading lets you save your video, while sharing helps you show it to others or collaborate on it. Explain the steps in downloading and sharing, as given on page 75.
● Ask the following questions to the students provided in the Do It Yourself 6B section and encourage the students to solve the questions. Instruct the students to write the answers in their book.
Correct Responses:
1. Fill in the blanks:
a. Upload b. timeline c. Elements d. beginning or end e. share
2. Solve the following crossword using the given hints: Across:
1. Filter 4. Split 6. Play Down:
2. Resize 3. Upload 5. MP4
Build
7 mins
● Ask the students to answer the question “Have you ever used the preview option in any application before finalising your video?”, in the Think and Tell section on page 75. Possible Response: Yes/No.
3 mins
● Conclude the session by summarising the steps to use basic video editing tools such as trimming and splitting a video, resizing and cropping a video, and adding and editing audio. Additionally, explain the steps to apply effects to videos, including using filters and effects, adding text and graphics, applying animations, and downloading and sharing the video.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Question 4
B. Tick the Correct Option: Questions 2, 3, and 5
C. Who Am I?: Question 3
D. Write T for True and F for False: Questions 2, 3, and 5
E. Answer the Following Questions: Questions 3 and 5
F. Apply Your Learning: Questions 1, 2, and 3

This chapter is divided into the following sessions
1. Introduction to Python, Data Types, and Variables
2. Operators
3. Conditional Statements
4. Iterative Statements
At the end of the session, the students will be able to:
● explain Python, its features, and syntax.
● describe Python data types.
● describe what a variable is, create a variable, and name a variable.
● describe the print function, multiple assignment and dynamic typing.
Keywords
● Python: Python is a high-level dynamic programming language that is interpreted, and focused on code readability.
● Data types: The data type specifies the kind of information that will be kept in a variable.
● Variables: The reserved memory areas used to hold values in a Python program are known as variables.
Ask the students what they know about Python programming. Then, introduce the basic concepts of Python to them.
Explain to the students what Python is. Get them familiar with Python’s features, data types, and variables.
Attempt the given activity.
Conclude the concepts
Assign homework
Warm Up
5 mins
● Ask the students what they know about Python programming. Then, introduce the basic concepts of Python to them.
15 mins
Explain the following concepts:
Explain Python, its features, and syntax.
Tell the students that Python is a dynamic programming language. Also explain the features and syntax of Python, as given on page 79.
Describe Python data types. Explain the various Python data types to students, such as int, float, string, list, etc., as given on pages 79 and 80.
Describe what a variable is, create a variable, and name a variable.
Describe the print function, multiple assignment and dynamic typing.
Tell the students that the reserved memory areas used to hold values in a Python program are known as variables. Also, tell them how to create a variable and how to name them, as given on pages 80 and 81.
Tell students that the print function can be used to output a Python variable. Demonstrate to them how they can create several variables in a single statement with Python. Also, explain the concept of dynamic typing, as given on pages 81 and 82.
● Read aloud the questions provided in the Do It Yourself 7A section and encourage the students to solve the questions. Instruct the students to write the answers in their book. Ctr valid ctr valid name1 valid city:Delhi invalid
7 mins
● Create a Python program to assign the following values to the given variables and then display their values and data type.
a = 1000
b = 100.50
c = “Amit Tandon”
d = True
Correct Response:
a = 1000
b = 100.50

c = “Amit Tandon”
d = True
print(a, b, c, d)
print(type(a))
print(type(b))
print(type(c))
print(type(d))
● Conclude the session by summarising that Python is a dynamic programming language. Various data types in Python are int, float, string, etc. The variables are the containers for storing data of various types. The print() function can be used to output a Python variable. Python specifies the kind of variable used during program execution. This concept is known as dynamic typing.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Questions 1 and 5
B. Tick the Correct Option: Questions 1 and 2
C. Who Am I?: Question 5
D. Write T for True and F for False: Question 1
E. Answer the Following Questions: Questions 3 and 4
F. Apply Your Learning: Question 1
At the end of the session, the students will be able to:
● perform operations using different types of operators.
Keyword
● Operators: Operators are predefined symbols that perform operations on one or more operands.
Assign students some mathematical expressions to solve. Then, relate how these operations can be performed using Python operators. Discuss the concept of operators. Discuss arithmetic, assignment, comparison, and logical operators.
Attempt the given activity.
● Assign students some mathematical expressions to solve.
● Then, relate how these operations can be performed using Python operators.
Engage
Explain the following concepts:
Learning Outcome
Perform operations using different types of operators.
Conclude the concepts Assign homework
Explanation
Explain to the students that operators are predefined symbols that perform operations on one or more operands. Discuss various types of operators and their precedence rule, as given on pages 82 to 83.
● Ask the following additional questions to check the students’ understanding.
1. Which operator is used to calculate the remainder of a division in Python?

Correct Response: The modulus operator '%' is used to calculate the remainder of a division in Python.
2. What is the difference between the comparison operators and the logical operators?
Correct Response:
Comparison operators are used to compare two values, whereas, the logical operators are used to combine conditional statements.
7 mins
Build
● F = m × a and E = m × c2 are two of the most famous equations in science. Yamato uses them to make an equation of his own: X = (E + F) × (E - F) / m.
Assuming m = 10, a = 8, and c = 4, write a program that displays the value of X.
Correct Response:
m = 10
a = 8
c = 4
F = m * a
E = m * c * c
X = (E + F) * (E - F) / m
print(“Value of X: “, X)
Sum Up
3 mins
● Conclude the session by summarising that operators are predefined symbols that perform operations on one or more operands. Discuss various types of operators and their precedence rules.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Question 2
B. Tick the Correct Option: Question 3
C. Who Am I?: Question 1
D. Write T for True and F for False: Question 2
At the end of the session, the students will be able to:
Ask the students about some real-life situations where they have to make choices based on a given condition.
● use different types of conditional statements in Python programming. 5 mins
Discuss the concept of conditional statements. Discuss the if, if-else, and if-elif-else statements.
Attempt the given activity.
Conclude the concepts
Assign homework 5 mins 15 mins 7 mins 3 mins
● Ask the students about some real-life situations where they have to make choices based on a given condition.
● Then, relate this concept to decision-making in Python.
Explain the following concepts:
Use different types of conditional statements.
Explanation
Describe to the students what are conditional statements. Elaborate each type of conditional statements, i.e., if statement, if-else statement, if-elif-else statement, as given on pages 84 to 87.
● Ask the following additional questions to check the students’ understanding.
1. What are the three main types of conditional statements in Python?
Correct Response: The three main types of conditional statements are: 'if', 'if-else', and 'if-elif-else'.

2. What will be the output of the following code?
x = 10
if x > 5:
print("Greater than 5") else:
print("5 or less")
Correct Response: Greater than 5
● An amusement park is planning to make an auto-ticket vending machine that vends tickets to visitors based on certain conditions. The conditions are mentioned below.
If the visitor’s age is greater than 15 and his or her height is more than 5.5 feet, the machine displays “You get access to all rides!”.
If the conditions are not met, it displays “You get access to the kid’s rides only!”.
Take the input of age and height from the user and store it in the variables age and height, respectively. Don’t forget to convert them into the float() data type. Then, use the if-else to write a program to print the above mentioned outputs.
Correct Response:
age = float(input(“Enter your age: “))
height = float(input(“Enter your height: “))
if age>15 and height>5.5:
print(“You get access to all rides!”)
else:
print(“You get access to the kid’s rides only!”)
● Conclude the session by summarising that the programming languages use conditional statements that make decisions to control the direction or flow of the program execution. Types of conditional statements used in Python are: if statement, if-else statement, and if-elif-else statement.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
B. Tick the Correct Option: Questions 4 and 5
C. Who Am I?: Question 2
D. Write T for True and F for False: Questions 3 and 4
E. Answer the Following Questions: Question 5
At the end of the session, the students will be able to:
● use different types of iterative statements in Python programming.
Warm Up
Ask the students to write their names ten times in their notebooks.
Then, explain that in programming, iterative statements (like loops) are used to repeat actions, just like they repeated writing their names.
Discuss the concept of iterative statements.
Discuss the while loop and for loop.
Attempt the given activity.
Conclude the concepts
Assign homework
5 mins
Warm Up
● Ask the students to write their names ten times in their notebooks.
● Then, explain that in programming, iterative statements (like loops) are used to repeat actions, just like they repeated writing their names.
Engage
Explain the following concepts:
Learning Outcome
Use different types of iterative statements.
Explanation
Tell the students that loops are useful in Python because they allow you to execute a block of code repeatedly. Describe the two primitive loop statements of Python, i.e., while loop and for loop, along with their syntax, flowcharts, and codes, as given on pages 87 to 91.
Attempt the Coding Challenge. Encourage students to attempt the coding challenge to write a Python program to create a geometry calculator, as given on page 92.

● Read aloud the questions provided in the Do It Yourself 7B section and encourage the students to solve the questions. Instruct them to write the answers in their book.
Correct Responses:
1. # Python program to compute sum of digits in a number. # Function to get sum of digits def getSum(n): sum = 0 for digit in str(n): sum += int(digit) return sum n = 12345 print(getSum(n))
2. num = int(input(“ Enter a number : “))
# using the for loop to generate the multiplication tables print(“Table of: “) for a in range(1,11): print(num,’x’,a,’=’,num*a)
3. metres = float(input(“Enter the value in metres: “)) centimetres = metres * 100 print(metres, “metres is equal to”, centimetres, “centimetres.”)
Build
● Print the first 10 natural numbers using a while loop.
Correct Response: num = 1 while num <= 10: print(num) num += 1
● Conclude the session by summarising that loops are useful in Python because they allow you to execute a block of code repeatedly. Describe the two primitive loop statements of Python, i.e., while loop and for loop, along with their syntax, flowchart, and code.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Questions 3 and 4
C. Who Am I?: Questions 3 and 4
D. Write T for True and F for False: Question 5
E. Answer the Following Questions: Questions 1 and 2
F. Apply Your Learning: Questions 2, 3, and 4
This chapter is divided into the following sessions
1. Strings
2. String Manipulation in Python
At the end of the session, the students will be able to:
● describe what strings are.
● explain different types of strings.
● use an eval function.
● create strings in Python.
Keyword
● String: A string is a data type that represents a sequence of characters.
Ask the students what they think the meaning of the word ‘string’ is.
Tell the students what strings are. Explain to them the different types of strings. Also, explain to them how to create strings in Python.
Action Plan
Warm Up
● Ask the students what they think the meaning of the word ‘string’ is.
● Now, build the concept by telling them a string is a data type that represents a sequence of characters.

Explain the following concepts:
Describe what strings are.
Explain different types of strings.
Tell the students that a string is a data type that represents a sequence of characters. In Python, strings are enclosed in single quotes (' ') or double quotes (" ")., as given on page 96.
Describe to the students that there are two types of strings: Single-line string and multi-line string, as given on page 96.
Use an eval function. Describe to the student that the eval() function evaluates a string expression and returns the result. Also, tell them about its syntax and example, as given on page 97.
Create strings in Python.
Describe to the student that in Python, single, double, or even triple quotes can be used to create strings, as given on page 97.
Ask additional questions from the students to check for understanding.
1. Name the two types of strings.
2. What is the syntax of the eval() function?
Correct Responses:
1. Single-line string and Multi-line string
2. Syntax: result = eval(expression)
Build
7 mins
● Conduct a group discussion in the class among the students on the topic “Difference between single-line and multi-line strings.”
Possible Responses: A single-line string can be enclosed in either single quotes or double quotes. Whereas, a multi-line string can be enclosed in either three single quotes (''' ''') or three double quotes (""" """).
3 mins
Sum Up
● Conclude the session by summarising that a string is a data type that represents a sequence of characters. In Python, strings are enclosed in single quotes. (' ') or double quotes (" "). These values can be words, symbols, characters, numbers, or a combination of all these. There are two types of strings in Python i.e., single-line string and multi-line string. In Python, single, double, or even triple quotes can be used to create strings.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Questions 1 and 2
B. Tick the Correct Option: Questions 1 and 4
C. Who Am I?: Questions 1 and 2
D. Write T for True and F for False: Questions 1 and 4
E. Answer the Following Questions: Questions 1 and 4
F. Apply Your Learning: Question 4
At the end of the session, the students will be able to:
● manipulate the string using various methods.
● solve the given examples.
Ask the students to write their first name and last name separately. Then, have them combine the two to form their full name, repeat the last name three times, and replace the last name with a friend’s last name.
Discuss the various methods to manipulate strings in Python. Also, help them solve the given examples. Attempt the given activity.
Conclude the concepts
Assign homework
● Ask the students to write their first name and last name separately. Then, have them combine the two to form their full name, repeat the last name three times, and replace the last name with a friend’s last name.
● Then, relate these operations to string manipulation in Python.
Explain the following concepts:
Manipulate the string using various methods.
Solve the given examples.
Demonstrate to them how to concatenate two or more strings, replicate a string, replace a string, find the length of a string, access characters in a string, do string slicing, use in-built string methods and make decisions using string methods, as given on pages 98 to 102.
Tell the students to solve the examples, as given on page 103.

● Read aloud the questions provided in the Do It Yourself 8A section and encourage students to solve them. Instruct them to write the answers in the book.
Correct Responses:
1. user_input = input("Enter a string: ")
letters = 0
digits = 0 for char in user_input: if char.isalpha(): letters += 1 elif char.isdigit(): digits += 1
print("Number of letters:", letters)
print("Number of digits:", digits)
2. letter = input("Enter a letter: ").lower() if letter in 'aeiou': print("The letter is a vowel.") else:
print("The letter is a consonant.") else:
print(“The letter is a consonant.”)
Build
7 mins
● Write a program to concatenate two strings and display the length of the concatenated string.
Correct Response:
str1 = input("Enter the first string: ")
str2 = input("Enter the second string: ")
concatenated_string = str1 + str2
print("Concatenated String:", concatenated_string)
print("Length of the concatenated string:", len(concatenated_string))
● Conclude the session by summarising that how to concatenate two or more strings, replicate a string, replace a string, find the length of a string, access characters in a string, do string slicing, use in-built string methods and make decisions using string methods.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Questions 3 and 4
B. Tick the Correct Option: Questions 2 and 3
C. Who Am I?: Questions 3 and 4
D. Write T for True and F for False: Questions 2 and 3
E. Answer the Following Questions: Questions 2 and 3
F. Apply Your Learning: Questions 1, 2, and 3

This chapter is divided into the following sessions
1. Lists
2. Tuples
At the end of the session, the students will be able to:
● explain what a list is.
● describe the characteristics of a list.
● create a list in Python.
● access elements of a list.
● use a set of built-in methods on lists.
Keywords
● List: It is a collection of various kinds of values. It can hold multiple values in a single variable.
● Indexing: It is used in Python to access list elements.
Ask the students to prepare a list of fruits. Then, relate this concept to lists in Python.
Explain to the students about a list and its characteristics. Also demonstrate to them how to create a list, access elements of a list, and use a set of built-in methods on lists.
Attempt the given activity.
Conclude the concepts
Assign homework
Up
● Ask the students to prepare a list of fruits.
● Then, relate this concept to lists in Python.
Explain the following concepts:
Explain what a list is. Explain to the students that lists are a fundamental data type in Python. It is a collection of various kinds of values, as given on page 107.
Describe the characteristics of a list.
Create a list in Python.
Access elements of a list.
Use a set of built-in methods on lists.
Tell the students the various characteristics of a list that are ordered, accessed via the index, allow duplicate values, mutable, and variable size, as given on page 107.
Demonstrate to the students how to create a list in Python by enclosing the values or elements within square brackets [ ], separated by commas. Also tell them how to create a list with duplicate elements and mixed types of elements, as given on pages 107 and 108.
Tell the students that indexing is used in Python to access list elements. Demonstrate how to access elements of a list by writing Python codes, as given on page 108.
Tell the students that Python has a set of built-in methods that you can use on lists, for example, append(), clear(), count(), pop(), remove, etc. Demonstrate how to use these methods on lists by writing Python codes, as given on pages 109 to 111.
● Read aloud Question 2 provided in the Do It Yourself 9A section and encourage the students to solve the question. Instruct the students to write the answers in their book.
Correct Response: list = [‘hat’, ‘shoes’, ‘belt’, ‘watch’, ‘jeans’] list.sort()
print(“Items to buy (alphabetically sorted):”) print(list) 5 mins
● Create a list of subjects (Maths, English, Science, Hindi, and Computer). Print all subjects from the list, one by one.
Correct Response: subject_list = [“Maths”, “English”, “Science”, “Hindi”, “Computer”] for x in subject_list: print(x)

● Conclude the session by summarising that lists are a fundamental data type in Python. It is a collection of various kinds of values. Revise the various characteristics of a list that are ordered, accessed via the index, allow duplicate values, mutable, and variable size. Indexing is used in Python to access list elements. Python has a set of built-in methods that you can use on lists.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Questions 1, 3, and 5
B. Tick the Correct Option: Questions 1, 2, 3, and 4
C. Who Am I?: Questions 1, 2, 3, and 4
D. Write T for True and F for False: Questions 1, 3, 4, and 5
E. Answer the Following Questions: Questions 1 and 3
F. Apply Your Learning: Questions 2, 4, and 5
At the end of the session, the students will be able to:
● explain what a tuple is.
● describe the characteristics of a tuple.
● create a tuple in Python.
● access elements of a tuple.
● use built-in methods on tuples.
● delete elements of a tuple.
● differentiate between lists and tuples.
Keyword
● Tuple: A tuple is an ordered, immutable collection of things or values.
Ask the students to list the names of any three fruits and explain that these items, when grouped together using parentheses, form a tuple in Python.
Explain to the students about a tuple and its characteristics. Demonstrate to them how to create a tuple, access elements of a tuple, use built-in methods on tuples, and delete elements of a tuple. Tell them the differences between lists and tuples.
● Ask the students to list the names of any three fruits.
Attempt the given activity.
Conclude the concepts
Assign homework
5 mins
● Then, explain that these items, when grouped together using parentheses, form a tuple in Python, which is a collection that holds multiple items in a fixed order.

Explain the following concepts:
Explain what a tuple is. Tell the students that a tuple is an ordered, immutable collection of things or values, as given on page 111.
Describe the characteristics of a tuple.
Create a tuple in Python.
Access elements of a tuple.
Use Python has two built-in methods that you can use on tuples.
Delete elements of a tuple.
Differentiate between lists and tuples.
Explain to the students the characteristics of a tuple that are ordered, accessed via the index, immutable, and allows duplicate values, as given on page 111.
Tell the students that they can create a tuple by placing the values or elements inside the parentheses ( ), separated by commas. Demonstrate to them how to create a tuple with a single item, duplicate elements, and mixed elements, as given on pages 111 and 112.
Tell the students that indexing is used in Python to access tuple elements. Demonstrate to them how to access elements in a tuple, as given on page 112.
Demonstrate to the students how to use built-in methods count() and index() on tuples, as given on pages 112 and 113.
Tell the students that the tuple items are immutable. However, in order to delete the elements of a tuple, you can convert the tuple into a list, change the list, and convert the list back into a tuple. Demonstrate how to delete the elements of a tuple using the same concept, as given on pages 113 and 114.
Explain to the students that lists and tuples are both used to store items and organise data. But in lists, the elements can be changed after they are defined, while in tuples, the elements cannot be changed at all, as given on page 114.
● Read aloud Question 1 provided in the Do It Yourself 9A section and encourage the students to solve the question. Instruct the students to write the answers in their book.
Correct Response:
tuple = (‘potato’, ‘tomato’, ‘brinjal’, ‘ginger’, ‘garlic’) print(tuple)
Build
● Write a code to combine or merge two given tuples.
tuple1 = (1, 3, 5)
tuple2 = (2, 4, 6)
Correct Response:
tuple1 = (1, 3, 5)
tuple2 = (2, 4, 6)
result_tuple = tuple1 + tuple2 print(result_tuple)
7 mins
● Conclude the session by summarising that a tuple is an ordered, immutable collection of things or values. Revise the characteristics of a tuple that they are immutable, ordered, accessed via the index, and allow duplicate values. Revise about indexing in Python to access tuple elements. Python has two built-in methods that you can use on tuples: count() and Index(). To delete elements of a tuple, you need to first convert the tuple into a list. Also revise the differences between lists and tuples.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Questions 2 and 4
B. Tick the Correct Option: Question 5
C. Who Am I?: Question 5
D. Write T for True and F for False: Question 2
E. Answer the Following Questions: Questions 2, 4, and 5
F. Apply Your Learning: Questions 1 and 3

This chapter is divided into the following sessions 1. Basics of HTML
Basic Tags of HTML
At the end of the session, the students will be able to:
● define HTML.
● explain about tags.
● discuss about elements.
● explain attributes.
● tell the structure of an HTML document.
Keywords
Understanding CSS
How to Use CSS in a Web
● HTML: HTML, the short form for HyperText Markup Language, is a markup language used to design web pages.
● Markup language: It refers to a language which creates a layout of web pages and applies formatting to them.
● Text editor: It is a software used to write the code of HTML documents.
● Web browser: A web browser is used to access and view web pages.
● Web page: It is a document placed on the World Wide Web (WWW) as a part of a website.
Ask the students if they know what a web page is.
Discuss HTML and its basic terminologies such as tags, elements, attributes, etc., with the students. Think and Tell Conclude the concepts Assign homework
5 mins
Warm Up
● Ask the students if they know what a web page is.
● Now, build the concept by telling them that HTML is a markup language used to design web pages.
15 mins
Engage
Explain the following concepts:
Learning Outcomes
Explanation
Define HTML. Discuss with the students that HTML stands for HyperText Markup Language. HTML is a markup language used to design web pages. It defines the structure of a web page and tells the web browser how and where to display the content of the web page, as given on page 118.
Explain about tags. Describe that a tag is a basic building block of an HTML document that specifies how the content is displayed on the web page, as given on page 118.
Discuss elements. Explain to the students that the combination of the opening tag, content and closing tag is known as an element. There are two types of elements in HTML which are container elements and empty elements, as given on page 119.
Explain attributes. Describe to the students that an attribute provides additional information about an HTML element and modifies its behaviour, as given on page 119.
Tell the structure of an HTML document.
Explain to them that the structure of an HTML document is divided into two main parts: the head and the body, as given on pages 119 and 120.
● Read aloud the questions provided in the Do It Yourself 10A Question 1 section and encourage the students to solve the questions. Instruct the students to write the answers in their book.
Correct Responses:
1. <html></html>, <head></head>, and <body></body>
Build
7 mins
● Ask the students to answer the question, “How are tags and attributes different?”, mentioned in the Think and Tell section on page 119.
Possible Responses: A tag is a basic building block of an HTML document that specifies how the content is displayed on the web page. Whereas, an attribute provides additional information about an HTML element and modifies its behaviour.

● Conclude the session by summarising that HTML stands for HyperText Markup Language. HTML is a markup language used to design web pages. A tag is a basic building block of an HTML document that specifies how the content is displayed on the web page. The combination of an opening tag, content and closing tag is known as an element. An attribute provides additional information about an HTML element and modifies its behaviour. The structure of an HTML document is divided into two main parts: the head and the body.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Questions 1 and 2
B. Tick the Correct Option: Question 1
D. Write T for True and F for False: Question 1
E. Answer the Following Questions: Questions 1 and 2
At the end of the session, the students will be able to:
● explain and use basic tags of HTML.
Ask the students if they have ever noticed various objects on a website. Relate this to the concept of tags in HTML that these objects can appear on a web page with the help of various tags.
Demonstrate how to use basic HTML tags to create a web page.
Attempt the given activity.
Conclude the concepts
Assign homework
5 mins
Warm Up
● Ask the students if they have ever noticed various objects on a website.
● Then, relate this to the concept of tags in HTML that these objects can appear on a web page with the help of various tags.
15 mins
Engage
Explain the following concepts:
Learning Outcome
Explanation
Explain and use basic tags of HTML. Discuss some basic tags in HTML like <h1> to <h6>, <sub>, <sup>, <b>, etc. Also demonstrate how to use these tags to create a web page, as given on pages 120 and 121.
● Read aloud the questions provided in the Do It Yourself 10A Question 2 section and encourage students to solve them. Instruct them to write the answers in the book.
Correct Responses:
2. a. <b> b. <p> c. <i>

● Create a web page and give a heading as “Introduction to My Web page”. The output should look like given below:
Correct Response:
<html>
<head>
<title> Text Formatting Example </title>
</head>
<body>
<h1> Welcome to My Web Page </h1>
<p> This is a simple paragraph with some <em> emphasised </em> text. We can also use superscript and subscript: </p>
<p> The chemical formula for water is H<sub>2</sub>O, and the famous equation is E = mc<sup>2</ sup>. </p>
<p> Feel free to explore the content on this page. Thank you for visiting! </p>
</body>
</html>
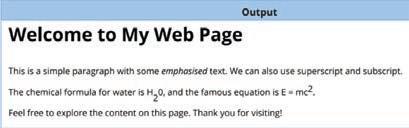
Sum Up
3 mins
● Conclude the session by summarising the basic tags of HTML like <h1> to <h6>, <sub>, <sup>, <b>, etc. Give them an example to explain each tag.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Question 3
B. Tick the Correct Option: Questions 2 and 3
C. Who Am I? : Question 1
D. Write T for True and F for False: Questions 3 and 4
F. Apply Your Learning: Question 1
At the end of the session, the students will be able to:
● define CSS.
● discuss about CSS selectors.
● explain properties and values.
Keyword
● CSS: CSS, the short form for Cascading Style Sheets, is a language used to style HTML elements.
Ask the students if they know how can they change the look and feel of a web page.
Explain about CSS, selectors, properties and values to the students.
Group discussion Conclude the concepts Assign homework
● Ask the students if they know how they can change the look and feel of a web page.
5 mins
● Now, build the concept that Cascading Style Sheets (CSS) is a language used to style the HTML elements. It allows us to change the look and feel of the web pages.
15 mins
Engage
Explain the following concepts:
Learning Outcomes
Explanation
Define CSS. Describe that Cascading Style Sheets (CSS) is a language used to style the HTML elements. It allows us to change the look and feel of the web pages, as given on page 121.
Discuss about CSS selectors. Tell the students that CSS uses selectors to target HTML elements. Selectors can target elements by tag name, class, ID, attribute, and more, as given on page 121.

Explain properties and values.
Discuss with the students that CSS is used in a property-value pair. CSS properties define the styles that are to be applied to the selected elements, and values specify the settings for those properties. Explain about different CSS properties, as given on pages 121 and 122.
Ask the following questions to the students to check for understanding.
Describe the following properties.
1. padding
2. margin
3. opacity
4. text-align
Correct Responses:
1. Padding sets the space around the content of the element.
2. Margin sets the space around the element itself.
3. Opacity specifies the transparency of the element.
4. Text-align aligns the text horizontally within a box.
Build
7 mins
● Conduct a group discussion in the class among the students on the topic ‘ What is the use of selectors?’
Possible Responses: CSS uses selectors to target HTML elements. Selectors can target elements by tag name, class, ID, attribute, and more.
3 mins
Sum Up
● Conclude the session by summarising that Cascading Style Sheets (CSS) is a language used to style HTML elements. CSS uses selectors to target HTML elements. Selectors can target elements by tag name, class, ID, attribute, etc. CSS is used in a property-value pair.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
B. Tick the Correct Option: Question 4
C. Who Am I? : Questions 2 and 4
D. Write T for True and F for False: Question 2
E. Answer the Following Questions: Questions 3 and 4
At the end of the session, the students will be able to:
● use CSS on a web page.
By now the students must be aware of the concept of CSS in web development. Ask them some basic questions to check their knowledge.
Discuss different ways to use CSS on a web page.
Attempt the given activity.
Conclude the concepts
Assign homework
Warm Up
● By now the students must be aware of the concept of CSS in web development. Ask them some basic questions to check their knowledge.
Engage
Explain the following concepts:
Learning Outcome
Explanation
Use CSS on a web page. Tell the students that CSS can be used in three ways on a web page which are, Inline CSS, Internal CSS, and External CSS, as given on pages 44 and 45.
● Ask the following additional questions to the students to check their understanding:
1. What is the purpose of CSS in web development?
Correct Response: CSS is used to style and layout web pages, including changing colours, fonts, spacing, and positioning of elements.
2. Write one example of an inline CSS style.
Possible Response: <p style="color: blue;">Hello, world!</p>

● Create a navigation bar with the help of <a> and <nav> tags. Style it with the help of CSS options. The output should look like the one as given below: Correct Response: <html>
<head>
<title>Home Page</title> <style>
h1 { background-color: purple; color: white; text-align: center; padding: 1em; } nav { background-color: grey; overflow: hidden; } nav a { float: left; display: block; color: white; text-align: center; padding: 14px 16px; text-decoration: none; } nav a:hover { background-color: olive; color: white; } </style> </head> <body>
<h1>Navigation</h1>
<nav>
<a href="https://uolo.com/index.html">Home</a>
<a href="https://uolo.com/about-us.html">About Us</a>
<a href="https://uolo.com/request-demo.html">Contact</a> </nav>
</body>
</html>

Sum Up
3 mins
● Conclude the session by summarising that CSS can be used in three ways on a web page which are, Inline CSS, Internal CSS, and External CSS.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Question 4
C. Who Am I? : Question 3
F. Apply Your Learning: Question 2

This chapter is divided into the following sessions
1. Creating Forms in HTML 1
2. Creating Forms in HTML 2
At the end of the session, the students will be able to:
● describe HTML forms.
● discuss about the various elements of a form.
● create and display a form.
● use the attributes of the <form> element.
● validate a form.
Keywords
● HTML form: HTML forms are commonly used when websites need to gather information from users.
● Form validation: Form validation is to ensure that users provide the correct type of information.
Ask the students whether they have ever filled a form online.
Then, tell them that these forms can be created online using HTML tags.
Describe to the students about HTML forms. Explain to them about the various form attributes. Discuss with them how to validate a form.
Attempt the given activity.
Conclude the concepts
Assign homework
Warm Up
● Ask the students whether they have ever filled a form online.
● Then, tell them that these forms can be created online using HTML tags.
Engage
Explain the following concepts:
5 mins
15 mins
Explanation
Describe HTML forms. Tell the students that HTML forms are used to collect information from users, such as their names, email addresses, and hobbies, as given on page 126.
Discuss about the various elements of a form.
Create and display a form.
Use the attributes of the <form> element.
Explain the various form elements like <input>, <textarea>, <button>, and <select>. Demonstrate the usage of elements and options in forms, as given on pages 126 to 129.
Demonstrate to them how to use different elements to create a form, as given on pages 129 and 130.
Demonstrate the different attributes used to control the behaviour of the form, as given on page 131.
Validate a form. Tell the students that form validation means checking the form details provided by the user, as given on page 131.
● Read aloud the questions provided in the Do It Yourself 11A section and encourage the students to solve the questions. Instruct the students to solve the answers in their books.
Correct Answers:
1. a. Radio b. Action
2. a. Method attribute specifies the Hyper Text Transfer Protocol (HTTP) method to be used.
b. The Radio button option allows users to select one option from a list.
Build
● Create a simple HTML form for a student to enter the name and age.
Correct Response:
<!DOCTYPE html>
<html>
<head>
<title>Simple Form</title>
</head>
7 mins

<body>
<h2>Simple Form</h2>
<form> <label>Name:</label><br>
<input type="text" name="name"><br><br> <label>Age:</label><br> <input type="number" name="age"><br><br>
<input type="submit" value="Submit"> </form> </body> </html>
3 mins
● Conclude the session by summarising that HTML forms are used to collect information from users. <input>, <textarea>, <button>, and <select> are the various form elements. We have various form attributes that are used to control form elements. Also, validation of the form means checking the form details provided by the user.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Questions 1, 2, 3, and 4
B. Tick the Correct Option: Questions 1, 2, 3, 4, and 5
C. Write T for True and F for False: Questions 1, 2, 3, 4, and 5
D. Answer the Following Questions: Questions 1, 2, 4, and 5
E. Apply Your Learning: Questions 2 and 3
At the end of the session, the students will be able to:
● develop an HTML form.
● decorate the form using internal CSS.
Keyword
● Internal CSS: You can make your HTML forms look attractive and arrange them on a web page by using the style element.
Warm Up
Ask the students to draw and decorate simple forms in their notebooks.
Engage Build Sum Up
Describe CSS and the usage of CSS in HTML. Explain how to style a form using internal CSS. Attempt the given activity.
Action Plan
Conclude the concepts
Assign homework
Warm Up
● Ask the students to draw and decorate simple forms in their notebooks.
● Tell them that they can also decorate their forms in HTML. 15 mins
Engage
Explain the following concept:
Learning Outcome
Explanation
Use internal CSS. Demonstrate the usage of internal CSS to style a form in HTML, as given on pages 131 to 132.

● Read aloud the question provided in the Do It Yourself 11A section and encourage the students to solve it. Instruct the students to write the answer in their books.
Correct Answer: Question 1: c. <style>
● Create a simple HTML form for a student. Include fields Name and Email. Use internal CSS to style the form.
Correct Response: <html> <head>
<title>Form Styling</title> <style>
form { width: 400px; /* Set the width of the form. */
margin: 0 auto; /* Center-align the form. */
padding: 50px; /* Add some padding for spacing. */ background-color: #f2f2f2; /* Set the background colour.*/ border: 1px solid #ccc; /* Add a border. */
}
label {
display: block; /* Display labels as block elements for better spacing. */ margin-bottom: 10px; /* Add some space between labels */ font-weight: bold; /* Make labels bold. */
}
/* Style for form input fields */ input[type="text"],
input[type="email"] {
width: 100%; /* Set input fields to 100% width. */ padding: 10px; /* Add padding for input fields. */
margin-bottom: 15px; /* Add space between input fields. */ border: 1px solid #ccc; /* Add a border to input fields. */
}
/* Style for the submit button */
input[type="submit"] {
background-color: #007bff; /* Set a background colour for the button. */ color: #fff; /* Set text color to white. */ padding: 10px 20px; /* Add padding for the button. */ border-radius: 3px; /* Add rounded corners to the button. */ }
</style> </head> <body> <form>
<label for="name">Name:</label>
<input type="text" id="name" name="name"> <label for="email">Email:</label>
<input type="email" id="email" name="email"> <button type="submit" value="Submit">Submit</button> </form> </body> </html>
Sum Up
● Conclude the session by summarising the importance of CSS in forms.
3 mins
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Question 5
D. Answer the Following Questions: Question 3
E. Apply Your Learning: Question 1

This chapter is divided into the following sessions
1. Adding Images and Creating Links
2. Inserting Audio and Video in a Web page
At the end of the session, the students will be able to:
● add images.
● create links.
Keyword
● Link: A link, also known as a hyperlink, is a text with the functionality to navigate you to some other web pages of the website.
Ask the students importance of adding images in a web page.
add images and create links on the web pages.
Warm Up
● Ask the students importance of adding images in a web page.
● Now, build the concept by telling them multimedia elements like images, links, audio, and video are used to enhance the user experience on a web page.
Explain the following concepts:
Add images. Tell them that they need to use the <img> tag to add images to a web page, as given on pages 136 to 138.
Create links. Describe that the <a> tag is used to create links in HTML. Tell them how to create links on a web page, as given on pages 138 and 139.
● Read aloud the questions provided in the Do It Yourself 12A section and encourage the students to solve the questions. Instruct the students to write the answers in their book.
Correct Responses:
1. a. <img src=”flower.jpg” alt=”Flower”>
b. <a download href=”flower1.jpg”> Flower </a>
2. img { border: 10px solid }
Build
● Create a web page on the ‘Healthy Lifestyle’. Add an appropriate image.
Correct Response:
<html>
<head>
<title>Healthy Lifestyle</title>
</head>
<body>
<h1>Healthy Lifestyle</h1>
<div>
<img src="HealthyLifeStyle.jpg" alt="Healthy Life Style">
7 mins
<p>Living a healthy lifestyle can make all the difference in the world as you navigate life's journey. Making healthy decisions isn't always simple; finding the time and energy to cook nutritious meals or exercise frequently can be challenging. But throughout your entire life, your achievements will be rewarded in a variety of ways. <br><br>Healthy lifestyle has led to many <i><b>amazing discoveries</b></i>, such as healthy body and positive mind set.
</p>

● Conclude the session by summarising that the <img> tag of HTML allows us to add images to the web page. A link, also known as a hyperlink, is a text with the functionality that helps you to navigate some other web page of the website. The <a> tag is used to create links in HTML.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Questions 1 and 2
B. Tick the Correct Option: Questions 1 and 3
C. Who Am I?: Question 1
D. Write T for True and F for False: Questions 1, 3, and 4
E. Answer the Following Questions: Questions 1 and 3
F. Apply Your Learning: Questions 1, 3, and 4
At the end of the session, the students will be able to:
● add audio on a web page.
● add video on a web page.
Warm Up
Ask the students if they like to listen to music and watch videos online.
Tell them that they can insert audio and video files in their web pages.
Discuss how to add audio and video on a web page.
Attempt the given activity.
the concepts
Warm Up
● Ask the students if they like to listen to music and watch videos online.
● Tell them that they can insert audio and video files in their web pages.
Engage
Explain the following concepts:
Learning Outcomes
Add audio on a web page.
Add video on a web page.
Explanation
Demonstrate to the students that HTML provides the <audio> tag to insert audio files on a web page. Explain to them the various attributes of the <audio> tag. Also demonstrate to them how to create a web page to add an audio file, as given on page 140.
Tell the students that HTML allows us to add a video on a web page using the <video> tag. Explain to them the attributes of the <video> tag. Demonstrate to them how to create a web page to add a video, as given on page 141.

● Read aloud the questions provided in the Do It Yourself 12B section and encourage students to solve them. Instruct them to write the answers in the book.
Correct Responses: 1.
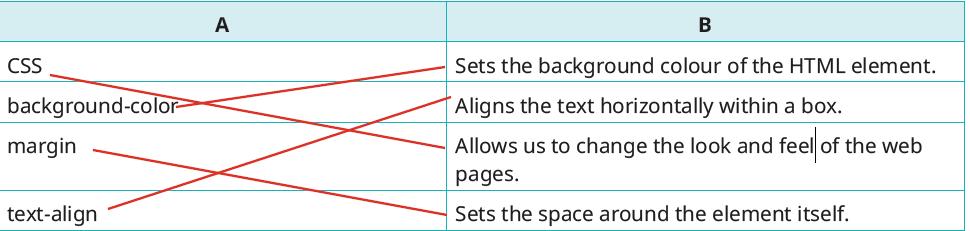
2. Autoplay, Controls, Loop
Build
● Create a simple web page and insert an audio and a video file in the web page.
Correct Response:
<!DOCTYPE html>
<html>
<head>
<title>Media Page</title>
</head>
<body>
<h2>Audio and Video Example</h2>
<h3>Audio</h3>
<audio controls>
<source src="audio-file.mp3" type="audio/mpeg">
Your browser does not support the audio element.
</audio>
<br><br>
<h3>Video</h3>
<video width="320" height="240" controls>
<source src="video-file.mp4" type="video/mp4">
Your browser does not support the video tag.
</video>
</body>
</html>
● Conclude the session by summarising that HTML provides the <audio> tag to insert audio files on a web page. The <source> tag is used with the <audio> tag to specify the path of the audio file. HTML allows us to add a video on a web page using the <video> tag. The <source> tag is used with the <video> tag to specify the path of the video file.
● Assign the following questions from the Chapter Checkup given at the end of the chapter as homework.
A. Fill in the Blanks: Questions 3 and 4
B. Tick the Correct Option: Questions 2 and 4
C. Who Am I?: Questions 2, 3, and 4
D. Write T for True and F for False: Question 2
E. Answer the Following Questions: Questions 2 and 4
F. Apply Your Learning: Question 2

Chapter Checkup
A. Fill in the Blanks.
1. Computer network 2. Bus 3. MAN 4. Inconsistency 5. Antivirus
B. Tick () the Correct Option.
1. c. High maintenance cost 2. a. Data, Resources 3. d. Redundancy 4. a. LAN 5. c. Router
C. Write T for True and F for False.
1. T 2. F 3. F 4. F 5. T
D. Answer the Following Questions.
1. WAN (Wide Area Network) connects computers from various countries and continents. WAN connects different LANs and MANs from across the globe. The internet is an example of a WAN.
2. Following are the advantages of computer networks:
a. Cost Reduction: Because the hardware resources (printers and scanners) are shared among all the computers on the network, the cost of additional equipment is saved.
b. Less Data Redundancy: Data redundancy occurs when the same piece of data exists in multiple places. All the data on the computer network is stored on the server. Therefore, there is less redundancy in the network.
c. Less Data Inconsistency: Data inconsistency means when the same data exists in different formats at different places. Since data redundancy is reduced, it also reduces data inconsistency.
d. Data Centralisation: All the data in a computer network is stored on a server at a centralised location. This centralised storage of data provides easy accessibility to all users.
e. Data Recovery: The server’s capability of taking regular data backup helps with easy data recovery in case of data loss or network failure.
3. A hub is a networking device that transmits the received information to all the devices on the network. A router is a device which routes the data or information over a network.
4. In star topology, the nodes are connected to a centralised hub, switch, or a computer, forming a star. The disadvantage of the star topology is that if the central computer fails, the whole network will be disabled.
5. Following are the differences between bus and ring topologies:
In a bus topology, all the nodes are connected to a single common cable. In ring topology, the nodes are connected to each other, forming a ring.
A node puts a message on the cable that is sent to all other nodes in a network.
E. Apply Your Learning.
1. She should use a WAN.
2. Ring topology
A node forwards the message received from the previous node to the following node.
3. Wi-Fi is more beneficial than a wired network because it uses wireless communication technology to connect various devices like computers, smartphones, tablets, etc., to the internet without the need for physical cables.
4. Three disadvantages of computer networks are security concerns, data loss in case of a network failure, and complex architecture.
5. Connecting computers to computer networks brings many benefits, such as file sharing, communication, database access, data backup, etc.
Chapter Checkup
A. Fill in the Blanks.
1. Cyberbullying 2. Permission 3. Sensitive 4. Harmful 5. Identity
B. Tick () the Correct Option.
1. b. To imitate trusted entities 2. b. Ethical hacking 3. a. To track your online actions
4. c. Financial gain and dishonest behaviour 5. c. Acting ethically and responsibly online
C. Who Am I?
1. Digital Citizen 2. Online Etiquette 3. Cyberbullying 4. Plagiarism 5. Digital Footprints
D. Write T for True and F for False.
1. T 2. T 3. F 4. T 5. F
E. Answer the Following Questions.
1 Using the internet to harass, scare, or hurt people is referred to as cyberbullying. Cyberbullying can happen if you send or receive messages to humiliate or threaten someone, spread untrue rumours, post embarrassing images, or create fake profiles.
2. Digital citizenship is the term used to describe the ethical and responsible use of technology. Digital citizenship is important for young internet users because, by engaging in good digital citizenship, they help create a more secure and civilised online community for everyone.
3. Three online safety measures that can help protect personal information and privacy are:
i. Use Secure Passwords: Create strong, challenging passwords for each of your accounts and change them frequently. Use a combination of symbols, numbers, and letters.
ii. Protect Personal Information: Exercise caution while disclosing personal information on websites and social media. Do not disclose too much personal information to the public.
iii. Privacy Settings: Limit who can view your information, review and modify the privacy settings on social media sites and online accounts.
4. Intellectual property refers to the ownership and protection of creative and unique ideas, inventions, and digital works over the internet. Examples include copyrights, patents, trademarks, and trade secrets.
5. The advantages of cyber ethics are:
i. Privacy Safeguards: Cyber ethics emphasises on protecting people’s privacy online. This includes respecting user consent, handling sensitive data securely, and preventing unauthorised access or data breaches.
ii. Online Behaviour: Cyber ethics promotes respectful and responsible online communication. This involves refraining from cyberbullying and other harmful types of behaviour.
iii. Digital Security: Intellectual property refers to the ownership and protection of creative and unique ideas, inventions, and digital works over the internet. It is very important to respect and not use people’s digital work online, such as videos, music, and software, without permission.
iv. Bridging the Digital Divide: Not all sections of society have the same access to technology. The poor, for example, have limited access. Ethical use of technology promotes equitable access to technology for all members of society.
v. Accountability: People and organisations need to be accountable for their online behaviour in the digital age. This includes taking responsibility for errors, making changes for harm done, and upholding moral principles in all online activities.
F. Apply Your Learning.
1. Sneha's classmates are exhibiting inappropriate behaviour, which falls under cyberbullying. Using the internet to harass, scare, or hurt people is referred to as cyberbullying. This is unethical behaviour as it can cause emotional distress and harm self-esteem.
2. The name of the activity is spamming. Spamming refers to sending lots of unwanted and annoying messages to many people, often to make money or promote something.

3. Prabha should not respond to the email asking for her bank account details. This might be an attempt at phishing, which is a dishonest internet practice in which attackers pretend to be reliable organisations and trick people into disclosing personal information like their financial information. The attackers can then use this information to do malicious things, like steal money or identities. The most common form of phishing is email phishing.
4. Ravi should be aware of and follow the given ethical practices while being online to search for information:
i. Privacy protection: Digital citizens should keep their information private, including passwords and communications.
ii. Using reliable sources: Always verify the reliability of information before sharing it to stop the spread of false information.
iii. Copyright awareness: Be aware of copyright and refrain from using other people’s work frequently. Do not use anybody else’s work without their consent or due attribution.
iv. Cybersecurity: Follow practices such as using secure passwords and keeping software up-to-date to attain a secure working environment.
5. We should not believe and respond to an email stating that we have won an iPhone. This might be an attempt of email phishing, which is a dishonest internet practice in which attackers pretend to be reliable organisations and trick people into disclosing personal information like their financial information. The attackers can then use this information to do malicious things, like steal money or identities.
Chapter Checkup
A. Fill in the Blanks.
1. block 2. blockchain 3. privacy 4. individuals 5. bank
B. Tick () the Correct Option.
1. a. Anyone can easily change information in a blockchain
2. b. Transparency
3. b. Every individual on the blockchain
4. d. Difficulty in communication between different blockchains
C. Who Am I?
1. Blockchain 2. Cryptocurrency 3. Banking system 4. Indian Rupee, or INR 5. Block
D. Write T for True and F for False.
1. F 2. T 3. T 4. F 5. F
E. Answer the Following Questions.
1. Blockchain is a shared, unchangeable record that helps track transactions and assets in a business network. It is a digital technology for storing and securing information. For example, cryptocurrencies do not have a banking system that records transactions. They work on blockchain.
2. Cryptocurrency is a purely digital or virtual currency that can also work as a medium of exchange. But, it exists only in digital form and doesn’t have physical coins or banknotes. Bitcoin is the name of a famous Cryptocurrency.
3. Blockchains ensure security and immutability as they do not allow any user to change or delete the information. Also, no user can see each other’s personal information.
4. Transparency, means that everyone who is a part of that blockchain can see all the information, and nothing is kept hidden from them. This helps to build trust among the users.
5. Following are the challenges of blockchains: i. Long Validation Process: Blockchains can provide accurate information, but the process of validation itself is sometimes very cumbersome.
ii. Slow Speed in Working with Large Amounts of Information: If there are too many transactions that involve several people, then maintaining verified information at each step would become very difficult. So, while working on a larger scale, maintaining speed with security is difficult.
iii. Interoperability: Blockchains are decentralised, and different blockchains can be fundamentally different in the way they have been designed and created. This sometimes makes it difficult for different blockchains to communicate with one another.
iv. Legal Challenges: Laws related to IT and technology tend to vary from country to country, so legal situations while dealing with blockchains might be complicated.
F. Apply Your Learning.
1. Decentralised system
2. Using blockchain for library book management enables immutable records of book transactions, ensuring accuracy in borrowing and returning processes. Decentralisation enhances reliability and accessibility for all users.
3. If anyone could change their cryptocurrency balance to show that they have more money than they actually do, the system would become unreliable. To prevent this, blockchain ensures that all transactions are verified and securely recorded. We do not have a bank in the case of cryptocurrencies, but the information regarding the amount is held within the blockchain. This information has been verified by multiple users, and records can be doublechecked at any time and from any place.
4. The INR is the national currency of our country. When we make a digital transaction, the bank digitally certifies that we have the money and lets us make the purchase. Once the purchase is made, the money is immediately debited from our bank account. Blockchain often involves using cryptocurrencies, like Bitcoin, for payment. Unlike traditional currencies, cryptocurrencies do not have a banking system that records transactions. Information regarding the amount is held within the blockchain. This information can be verified by multiple users, and records can be double-checked at any time and from any place.
Chapter Checkup
A. Fill in the Blanks.
1. app 2. E-commerce 3. Hybrid 4. palette 5. social networking
B. Who Am I?
1. Banking app 2. MIT App Inventor 3. App 4. Properties section 5. Hybrid
C. Write T for True and F for False. 1. T 2. T 3. F 4. T 5. T
D. Answer the Following Questions.
1. Banking apps are like a virtual bank branch on your phone or tablet. They are the special apps provided by your bank to help you do immediate money transactions without going to the bank in person.
2. Hybrid apps can work on different types of phones and use web technologies, allowing them to work on multiple platforms and access device features. They are compatible with both iPhones and Android phones and can be downloaded and installed from their respective app stores, such as the Google Play Store for Android phones and the App Store for iPhones.
3. Difference between web apps and desktop apps:
Desktop Apps
Desktop apps are like the computer version of the apps you use on your phone, but they are designed to work on your computer and do all sorts of different things, from writing documents to playing games or editing pictures.
Web Apps
A web app is a software application that operates on web servers and is accessed by users through web browsers over the internet.

Desktop apps can be used on a computer or a laptop where they are installed and run locally. Since web apps are hosted on web servers, users can access them from anywhere, using various devices, without the need for installation
Skype, Microsoft PowerPoint, Paint, Microsoft Excel, and iTunes are a few examples of desktop apps.
Padlet, YouTube, Gmail, and Google Drive are a few examples of web apps.
4. Native apps are specifically designed for a particular type of phone, such as iPhones or Android phones. They are known for their high speed and excellent performance because they are designed exclusively for your phone. Examples of native apps include Camera, Gallery, Clock, Maps, and Settings.
5. MIT App Inventor is a visual development platform that allows users to create mobile applications for Android devices without the need to write traditional codes. It provides a visual, drag-and-drop interface for designing the user interface and functionality. Users can assemble components and connect blocks to create the app’s logic.
E. Apply Your Learning.
1. Ramesh can visit the following website: https://appinventor.mit.edu/
2. E-commerce apps are online stores on your phone or tablet. They are special apps that let you shop for all sorts of things without having to go to a physical store. A few examples are Amazon, Flipkart, etc.
3. Umang can download an app from the Apple App Store.
4. Web apps, short for web applications, are software applications that run on web servers and are accessed through web browsers over the internet.
5. Meher has installed a hybrid app.
Chapter Checkup
A. Fill in the Blanks.
1. data 2. column 3. DBMS 4. percent 5. SQL
B. Tick () the Correct Option.
1. b. A collection of organised information 2. c. Oracle 3. d. Network
4. c. A row in a database table 5. b. Composite Key
C. Who Am I?
1. Wildcard operator: A special character for pattern matching in text data
2. DBMS: A software application that helps users create, manage, and access databases
3. Different types of DBMS: Relational, hierarchical, and network
4. Components of a DBMS: Data, hardware, software, users, procedures, and database access language
5. Attribute: A column in a database table
D. Write T for True and F for False.
1. T 2. T 3. T 4. F 5. F
E. Answer the Following Questions.
1. Relational Database Management System (RDBMS) holds data in the form of tables, which are made up of rows and columns.
2. The SQL statements or commands that are used to insert, delete, or update data in the table of the database are called DML commands. For example, insert, delete, update, etc.
3. Here are some of the advantages of using a database:
● It can carry vast quantities of data.
● It can organise data in a manner that makes it easier to retrieve.
● It can be used to modify and erase data rapidly.
● It can be used to share data with others.
4. A database management system (DBMS) is a software application that enables you to construct, operate, and interact with databases. Some common examples of DBMSs are MySQL, Microsoft SQL Server, and Oracle.
5. Wildcard operators in SQL are special characters for pattern matching in text data. They help in finding data that matches a pattern, not just an exact value. They are used with the ‘like’ clause in an SQL query. Two main wildcard characters used in SQL are ‘%’ (matches multiple characters) and ‘_’ (matches a single character).
F. Apply Your Learning.
1. Select Emp_ID, Emp_Name From Employee;
2. Select Emp_Name From Employee Where Salary<23000;
3. Select Emp_ID, Emp_Name From Employee Where Salary>23000;
4. Select Max(Salary), Min(Salary) From Employee;
5. Insert into Employee (Emp_ID, Emp_Name, Salary) Values (5, 'Raman', 27500); Insert into Employee (Emp_ID, Emp_Name, Salary) Values (6, 'Smita', 24300);
Chapter Checkup
A. Fill in the Blanks.
1. uploads 2. create a design 3. preview 4. trim and split 5. canvas
B. Tick () the Correct Option.
1. b. The timing of video elements 2. c. Animate 3. b. MP4
C. Who Am I?
b. Uploads 5. a. Zoom controls
1. Timeline 2. Canvas 3. Animate 4. Grid view 5. Elements
D. Write T for True and F for False.
1. T 2. F 3. F 4. T 5. T
E. Answer the Following Questions.
1. Video editing is the process of arranging and modifying video clips to create a video project. It involves cutting, adding and enhancing clips to make the video more interesting and effective.
2. Timeline helps arrange objects like text, images and images in the desired sequence.
3. Basic video editing tools are trimming, splitting, resizing, and cropping video.
4. The Preview option allows you to see how your video will appear to your audience. It is a valuable tool for reviewing your video before finalising it, ensuring everything looks and sounds just right.
5. Steps to add a text:
1. Click on the Text option in the sidebar.
2. Select a text style and click on it to add it to the canvas.
3. Double-click on the text box to edit the text. Change the font, size, colour and position as needed.
4. Click on the Elements option in the sidebar. Search for graphics or stickers and drag them onto the canvas.

F. Apply Your Learning.
1. She can resize the video clip from its ends to fit it according to the dimensions.
2. Kavita can addthe background music to her video by clicking on the Audio effects option on the top of the canvas.
3. Rahul wants to add captions to his video by clicking on the text option to add text.
4. Ravi needs to ensure that video elements appear at the right times. Timeline tool is used in Canva to manage the timing of these elements.
5. Arjun uses the Draw tool to create a drawing using his imagination.
Chapter Checkup
A. Fill in the Blanks.
1. indentation 2. precedence 3. iterate 4. end 5. dictionary
B. Tick () the Correct Option.
1. a. Guido van Rossum 2. d. Sequence Types 3. a. Exponentiation 4. d. Decision-making
5. a. Greater
C. Who Am I?
1. == 2. if-elif-else 3. break 4. range() 5. Boolean
D. Write T for True and F for False.
1. T 2. F 3. T 4. F 5. T
E. Answer the Following Questions.
1. A while loop runs as long as a specified condition is true, making it ideal when the number of iterations is unknown. In contrast, a for loop iterates over a sequence or range, making it suitable when the number of iterations is predetermined. While loops can risk infinite looping if the condition is not updated, for loops handle iteration automatically.
2. The Python continue statement returns control to the beginning of the loop. Whereas, the Python break statement brings control out of the loop..
3. Following are the rules to define a variable:
● A variable name starts with a letter or the underscore character. It cannot start with a number or any special character like $, (, *, %, etc.
● A variable name can only contain alpha-numeric characters.
● Python variable names are case-sensitive, which means str1 and STR1 are two different variables in Python.
● Python keywords cannot be used as variable names.
4. The data type specifies the kind of information that will be stored in a variable. The various data types available in Python are int, float, strings, list, tuple, dictionary, boolean, set, etc.
5. Conditional statements in programming languages make decisions to control the direction or flow of the program execution.
In the if-else condition, if the condition is true, a block of statements inside the if block will be executed; but if the condition is false, the blocks in the else statement will be executed.
F. Apply Your Learning.
1. <class 'bool'>
2. for num in range(1, 11): print(num)
3. side_length = 7 area = (3**0.5 / 4) * side_length**2 print("The area of the equilateral triangle is:", area)
4. number = int(input("Enter a number: "))
next_number = number + 1
previous_number = number - 1
print("Next number is:", next_number)
print("Previous number is:", previous_number)
Chapter Checkup
A. Fill in the Blanks.
1. single, double 2. changed 3. indexing 4. concatenate
B. Tick () the Correct Option.
1. c. Both a and b 2. b. string[-1] 3. b. replace() 4. a. '''This is a multi-line string'''
C. Who Am I?
1. String 2. eval() 3. * (asterisk) operator 4. Indexing
D. Write T for True and F for False.
1. T 2. F 3. F 4. T
E. Answer the Following Questions.
1. A single-line string can be enclosed in either single quotes or double quotes. Whereas, a multi-line string can be enclosed in either three single quotes (''' ''') or three double quotes (""" """).
2. Through indexing, characters at the beginning of the string can be accessed using positive address references, starting from 0 for the first character, 1 for the next character, and 2 for the next to the next character. Characters at the end of the string can be accessed using negative address references such as –1 for the last character, –2 for the next-to-last character, and so on.
3. The string slicing function in Python is used to access a selection of characters in a string using the slicing operator (:). It includes the character at the start index but excludes the character at the end index. Indexes start at 0 from the beginning of the string and -1 from the end.
4. Strings in Python are immutable, meaning once a string is created, its content cannot be changed. Any operation that modifies a string creates a new string instead of altering the original one.
F. Apply Your Learning.
1. str1 = "Hello" str2 = "World" result = str1 + " " + str2 print(result)
2. string = "Learning Python is fun!" print("\nExtracted substring 'Python':") print(string[9:15])
3. sentence = "Learning Python is fun!" print(sentence) print(sentence.replace("fun", "awesome"))
4. expression = "3 + 4" result = eval(expression) print(result)
Chapter Checkup
A. Fill in the Blanks.
1.

B. Tick () the Correct Option.
1. b. remove the last element from the list.
2. a. There is no limit to the size of a list, c. A list may contain the same type of objects.
3. b. L.remove(3) and d. L.pop(3) 4. b. List and d. Set 5. b. 2
C. Who Am I?
1. sort() 2. Tuple 3. List 4. append() 5. ‘*’ operator
D. Write T for True and F for False.
1. F 2. T 3. F 4. T 5. F
E. Answer the Following Questions.
1. The characteristics of the lists are given below:
Ordered: In a list, the values or items have a defined order, and this order does not change. If you add new values to a list, they are placed at the end of the list.
Accessed via the Index: You can access list elements using an index, which starts at 0. Hence, the first element of a list is present at index 0, not 1.
Allows Duplicate Values: A list can contain duplicate values. Since values are indexed in a list, it can have items with the same value but a different index.
2. To create a tuple with a single item, you have to add a comma after the item; otherwise, Python will not recognise it as a tuple.
Example: mytuple = ("Delhi",) print(mytuple)
3. Difference between pop() and remove() methods: pop() method remove() method
pop(): This method is used to remove the element at the specified position.
Syntax: list.pop(position)
list = [3, 4, 9, 3, 8, 9] list.pop(2) print(list)
Output: [3, 4, 3, 8, 9]
4. Difference Between Lists and Tuples
remove(): This method is used to remove the first occurrence of the specified element.
Syntax: list.remove(element)
list = [3, 4, 9, 3, 8, 9] list.remove(3) print(list)
Output: [4, 9, 3, 8, 9]
Lists are mutable. Tuples are immutable.
You can easily insert or delete data items in a list. You cannot directly insert or delete data items in a tuple.
Lists have several built-in methods. Due to immutability, a tuple does not have many built-in methods.
Lists are generally slightly slower than tuples because of their mutability.
Lists are created using square brackets [].
Example: list1 = [1, 2, 3]
5. Three characteristics of a tuple are:
Tuples are faster than lists.
Tuples are created using parentheses ().
Example: tuple1 = (1, 2, 3)
● Ordered: In a tuple, the values or items have a defined order, and this order does not change.
● Accessed via the Index: The tuple element can be accessed via the index. It means that the tuple index always starts with 0. Hence, the first element of a tuple is present at index 0, not 1.
● Immutable: The tuple items are immutable. The meaning of immutable is “unable to be changed”. It means that we cannot add, modify, or remove items in a tuple after it has been created.
F. Apply Your Learning.
1. Code to covert the given list to tuple: L = [1, 5, 8, 9, 15] T = tuple(L) print(T)
2. Code to create a list with single element: my_list = [42] print(my_list)
3. Code to create a tuple T with the given data: T = (9, 'Ram', 7, 5, 'Hema') print(T)
4. Adding a student’s name, “Sushma”, at the end of the given list: Stu_list = ["Lata", "Rama", "Ankit", "Vishal"] Stu_list.append("Sushma") print(Stu_list)
5. Creating a list of strings and access the elements using index: my_list = ["apple", "banana", "cherry", "date"] print(my_list[0]) print(my_list[1]) print(my_list[2]) print(my_list[3])
Chapter-10 More on HTML
Chapter Checkup
A. Fill in the Blanks.
1. HTML 2. element 3. <sub> 4. inline
B. Tick () the Correct Option.
1. a. To write the code of web pages 2. b. closing 3. a. <title> and </title> 4. b. padding
C. Who Am I?
1. <em> 2. colon (:) 3. External CSS 4. Opacity
D. Write T for True and F for False.
1. F 2. T 3. T 4. F
E. Answer the Following Questions.
1. The term ‘markup language’ refers to a language which creates the layout of web pages and applies formatting to them. It makes the objects on the web page like text, image, audio, etc., more interactive, and it also enriches the look and feel of the web pages.
2. The syntax to add an attribute is as follows: <element attribute=”value”>Content</element> Where,
Element: The HTML element to which the attribute belongs.
Attribute: The name of the attribute.
Value: The value assigned to the attribute.
3. The padding property sets the space around the content of the element. Whereas, the margin property sets the space around the element itself.
4. CSS uses selectors to target HTML elements. Selectors can target elements by tag name, class, ID, attribute, and more.

F. Apply Your Learning.
1. HTML code to display the following output: a3 − b3 Factorisation: (a − b) × (a2 + ab + b2) <!DOCTYPE html>
<html>
<head>
<title>Factorisation</title>
</head> <body>
<p>a<sup>3</sup> - b<sup>3</sup> Factorisation: (a - b) × (a<sup>2</sup> + ab + b<sup>2</sup>)</p> </body>
</html>
2. CSS code to create a box using <div> tag: <!DOCTYPE html>
<html> <head>
<title>Box Example</title> <style> .box { height: 400px; width: 500px; border: 5px solid grey; }
</style> </head> <body> <div class="box"></div> </body> </html>
Chapter Checkup
A. Fill in the Blanks.
1. form 2. <textarea> 3. radio 4. required 5. inline
B. Tick () the Correct Option. 1. b. <form> 2. b. text 3. a. <select> 4. d. pattern 5. c. To submit the form
C. Who Am I?
1. Arithmetic operator 2. document.write() 3. JavaScript 4. if… else… if statement
D. Write T for True and F for False.
1. T 2. T 3. F 4. T 5. T
E. Answer the Following Questions.
1. An HTML <form> element is used to create fields where users can provide information in an interactive way. It includes fields where users can type text, numbers, email addresses, and passwords, and indicate choices like selecting check boxes or clicking buttons.
2. Form validation is crucial to ensure that users provide the correct type of information. HTML introduced built-in form validation, using attributes like required, min, max, and pattern.
For example: <label for=”age”>Age:</label>
<input type=”number” id=”age” name=”age” required min=”18” max=”99”>
3. Setting properties of a form using internal CSS is also known as embedded CSS or inline CSS. You can make your HTML forms look attractive and arrange them on your web page by using the <style> element. This <style> element is placed in the <head> section of your HTML document. Steps to set properties of a form using internal CSS are:
● Open an HTML Document: Start by creating a standard HTML document structure, including the <!DOCTYPE html>, <html>, <head>, and <body> elements.
● Include the <style> Element: Inside the <head> section of your HTML document, include a <style> element.
● Select the Form Element: To target the form you want to style, use the form selector.
● Define CSS Properties: Within the selected form CSS block, you can define various CSS properties to control the appearance of the form.
● Style Form Elements: Inside a form block, you can target specific form elements such as labels, input fields, buttons, and other related elements.
● Save and Apply: When you have defined your internal CSS rules, save the HTML document.
4. Forms can have various attributes to control the behaviour of a form:
Action: Specifies the URL to which form data will be submitted.
Method: Specifies the HyperText Transfer Protocol (HTTP) method to be used (either “GET” or “POST”).
Name: Assigns a name to the form for easy identification.
Target: Specifies where to display the response after form submission.
5. The <input> element is used to create various fields to collect different types of information from users, such as text, email addresses, passwords, and more. The <label> element is used to attach a text with the input fields. Some common types of input fields are:
Text Input: It is used to take textual information from the user like name, age, roll number, etc.
Email Input: It is used to take the email address as information from the user.
F. Apply Your Learning.
1. <html> <head>
<title>Parents' Feedback Form</title> <style>
/* Internal CSS styles for the form */ form {
width: 450px; /* Set the width of the form */ margin: 0 auto; /* Center-align the form */ padding: 30px; /* Add padding for spacing */ background-color: #e8f4f8; /* Set a light background color */ border: 2px solid #ccc; /* Add a border */ border-radius: 8px; /* Rounded corners */

}
/* Style for form labels */ label {
display: block; /* Display labels as block elements for better spacing */ margin-bottom: 10px; /* Add space between labels */
font-weight: bold; /* Make labels bold */ font-family: Arial, sans-serif; /* Set font family */ }
/* Style for form input fields */ input[type="text"], input[type="email"], input[type="number"], textarea { width: 100%; /* Set input fields to 100% width */ padding: 10px; /* Add padding for input fields */ margin-bottom: 15px; /* Add space between input fields */ border: 1px solid #ccc; /* Add a border to input fields */ border-radius: 4px; /* Rounded corners */ }
/* Style for the submit button */ button[type="submit"] {
background-color: #28a745; /* Set background color for the button */ color: #fff; /* Set text color to white */ padding: 10px 20px; /* Add padding for the button */ border-radius: 5px; /* Rounded corners for the button */ border: none; /* Remove border */ font-size: 16px; /* Increase font size */ } </style> </head> <body> <h1>Parents' Feedback Form</h1> <form>
<label for="student_name">Student Name:</label> <input type="text" id="student_name" name="student_name" required><br>
<label for="parent_name">Parent Name:</label>
<input type="text" id="parent_name" name="parent_name" required><br>
<label for="class">Class:</label>
<input type="text" id="class" name="class" required><br>
<label for="section">Section:</label>
<input type="text" id="section" name="section" required><br>
<label for="email">Email Address:</label>
<input type="email" id="email" name="email" required><br>
<label for="comments">Feedback/Comments:</label>
<textarea id="comments" name="comments" rows="4" required></textarea><br>
<button type="submit" value="Submit">Submit</button> </form> </body> </html>
2. <html> <head>
<title>Favourite Subject Survey</title> <style>
/* Internal CSS styles for the form */ form { width: 400px; /* Set the width of the form */ margin: 0 auto; /* Center-align the form */ padding: 30px; /* Add padding for spacing */ background-color: #f1f1f1; /* Set a light background color */ border: 2px solid #ccc; /* Add a border */ border-radius: 8px; /* Rounded corners */ }
/* Style for form labels */ label { display: block; /* Display labels as block elements for better spacing */ margin-bottom: 10px; /* Add space between labels */

font-weight: bold; /* Make labels bold */ font-family: Arial, sans-serif; /* Set font family */ }
/* Style for radio buttons */ input[type="radio"] {
margin-right: 10px; /* Add some space between the radio button and the label */ }
/* Style for the submit button */ button[type="submit"] {
background-color: #007bff; /* Set background color for the button */ color: #fff; /* Set text color to white */ padding: 10px 20px; /* Add padding for the button */ border-radius: 5px; /* Rounded corners for the button */ border: none; /* Remove border */ font-size: 16px; /* Increase font size */
}
</style> </head> <body>
<h1>Favourite School Subject Survey</h1> <form>
<label for="math">Mathematics:</label>
<input type="radio" id="math" name="subject" value="Mathematics" required><br>
<label for="science">Science:</label>
<input type="radio" id="science" name="subject" value="Science" required><br>
<label for="history">History:</label>
<input type="radio" id="history" name="subject" value="History" required><br>
<label for="english">English:</label>
<input type="radio" id="english" name="subject" value="English" required><br>
<button type="submit" value="Submit">Submit</button> </form> </body>
3. <html>
<head>
<title>Ice-Cream Parlour Order</title>
<style>
/* Internal CSS styles for the form */ form {
width: 400px; /* Set the width of the form */ margin: 0 auto; /* Center-align the form */ padding: 30px; /* Add padding for spacing */
background-color: #f1f1f1; /* Set a light background color */ border: 2px solid #ccc; /* Add a border */ border-radius: 8px; /* Rounded corners */
/* Style for form labels */ label {
display: block; /* Display labels as block elements for better spacing */ margin-bottom: 10px; /* Add space between labels */
font-weight: bold; /* Make labels bold */
font-family: Arial, sans-serif; /* Set font family */
/* Style for checkboxes */ input[type="checkbox"] { margin-right: 10px; /* Add space between the checkbox and the label */ }
/* Style for the submit button */ button[type="submit"] {
background-color: #007bff; /* Set background color for the button */ color: #fff; /* Set text color to white */ padding: 10px 20px; /* Add padding for the button */ border-radius: 5px; /* Rounded corners for the button */ border: none; /* Remove border */ font-size: 16px; /* Increase font size */

</style> </head> <body>
<h1>Choose Your Favourite Ice-Cream Flavours</h1> <form>
<label for="chocolate">Chocolate</label>
<input type="checkbox" id="chocolate" name="flavours" value="chocolate">
<label for="vanilla">Vanilla</label>
<input type="checkbox" id="vanilla" name="flavours" value="vanilla">
<label for="choco-chip">Choco-Chip</label>
<input type="checkbox" id="choco-chip" name="flavours" value="choco-chip">
<label for="strawberry">Strawberry</label>
<input type="checkbox" id="strawberry" name="flavours" value="strawberry">
<label for="butterscotch">Butterscotch</label>
<input type="checkbox" id="butterscotch" name="flavours" value="butterscotch">
<button type="submit" value="Submit">Submit</button> </form> </body> </html>
Chapter Checkup
A. Fill in the Blanks.
1. images 2. URL 3. audio 4. controls
B. Tick () the Correct Option.
1. b. src 2. c. autoplay 3. c. anchor tag 4. a. .mp4
C. Who Am I?
1. <a> tag 2. <audio> tag 3. <video> tag 4. controls
D. Write T for True and F for False.
1. F 2. T 3. T 4. F
E. Answer the Following Questions.
1. Alt attribute is used to specify the alternate text which appears only if the specified image is not loaded due to some reason.
2. You can specify multiple audio sources in an <audio> tag by using multiple <source> elements inside the <audio> tag. Each <source> element can specify a different audio file format to ensure compatibility with various browsers.
3. The <nav> tag allows us to create a set of links.
4. The controls attribute in the <audio> and <video> tags adds built-in playback controls, such as play, pause, etc., making it easier for users to interact with the media directly without needing external tools.
F. Apply Your Learning.
1. <img src="ramanujan.jpg" alt="Srinivasa Ramanujan" width="300" height="400">
2. <a href="https://www.wikipedia.org" target="_blank">Go to Wikipedia</a>
3. <audio controls>
<source src="example.mp3" type="audio/mp3"> </audio>
4. <img src="image.jpg" alt="Sample Image" width="300" height="200"> <a href="image.jpg" download>Download this image</a>
A. Fill in the Blanks.
1. Computer Network 2. Digital citizenship 3. Bitcoin 4. Elements
B. Tick () the Correct Option.
1. a. Data redundancy 2. a. Number 3. c. Mobile
C. Write T for True and F for False.
1. T 2. T 3. F 4. F
D. Answer the Following Questions.
1. Network interface card (NIC) is a hardware component installed on a computer to connect a computer to a network. It is a circuit board or a chip without which a computer cannot connect with another computer on a network.
2. Blockchain is a shared, unchangeable record that helps track transactions and assets in a business network.
3. Here are some of the key roles or functions of a DBMS:
Storing Data: A DBMS can retain a huge amount of data in an organised form. This makes it easy and simple to access and recover the data when necessary.
Managing Data: A DBMS can manage the data in a database, such as adding, removing, modifying, and restoring data. It may also help to ensure that the data is genuine and consistent.
Protecting Data: A DBMS can protect the data in a database from unauthorised entry, change, or loss. It can do this by applying security measures such as user login and encryption.
Querying Data: You can access a specified piece of information from the database by making use of queries. This means that users may ask questions about the data, and the DBMS will deliver the results of the query.
4. Educational apps, social networking apps, entertainment apps, banking apps, and e-commerce apps.
F. Apply Your Learning.
1. Hub is a networking device that transmits the received information to all the devices on the network. A hub has many ports in it. A computer that intends to be connected to the network is plugged into one of these ports. Whereas, a switch is a device that connects different computers on a network. It transfers data from one computer to another. A switch receives data from one computer, processes that data, and forwards that data to the destination device.
2. No, you should not trust the message. It is likely a phishing attempt to steal personal information. Always be cautious with unsolicited messages and links.
3. Relational Database Management System (RDBMS) are the most commonly used type of DBMS. They hold data in the form of tables, which are made up of rows and columns. Each row represents a record, and

each column indicates a field. RDBMS are highly efficient in preserving and locating data, and they are also quite adaptable. Some notable RDBMSs include MySQL, Oracle, and Microsoft SQL Server. Object-Oriented Database Management System (OODBMS) stores data in the form of objects. Objects are like records, but they may also have methods, which are like functions. OODBMS is well-suited for keeping complicated data, such as data that is tied to things in the real world.
4. Kashika has downloaded a mobile app. These are apps that are installed from an app store, not preinstalled on the phone.
A. Fill in the Blanks.
1. Syntax 2. single, double 3. list 4. Web browser
B. Tick () the Correct Option.
1. c. Floor division 2. b. Subscript 3. b. <form>. 4. b. loop
C. Write T for True and F for False.
1. T 2. T 3. F 4. T
D. Answer the Following Questions.
1. In the Python programming language, the types of conditional statements are: i. The if statement ii. The if-else statement iii. The if-elif-else statement
2. Indexing is used in Python to access list elements. Suppose there are n number of elements in a list. Therefore, the list indexing will start at 0 for the first element and n-1 for the last element. You can use these index values to access the items in the list. The index must be an integer.
3. Forms can have various attributes to control the behaviour of a form:
Action: Specifies the URL to which form data will be submitted.
Method: Specifies the HyperText Transfer Protocol (HTTP) method to be used (either "GET" or "POST"). GET is better for submitting non-sensitive information, whereas POST is used to submit sensitive information.
Name: Assigns a name to the form for easy identification.
Target: Specifies where to display the response after form submission (e.g., in the same window or in a new one). It takes any one value from the _blank, _self, _parent and _top values
4. src, alt, width, and height are attributes of the <img> tag.
F. Apply Your Learning.
1. string1 = "Good" string2 = "Morning" result = string1 + " " + string2 print(result)
2. T = (7, 'Alia', 7, 4, 'Jiya') print(T)
3. The formula for the area of an equilateral triangle is:
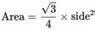
Following is the program: side = 10
area = (3**0.5 / 4) * (side** 2) print("The area of the equilateral triangle is:", area)
Uolo has introduced a comprehensive program, Hexa, for Grades 1 to 8, aimed at empowering young minds with essential knowledge and skills for the digital age.
To support the effective implementation of Hexa in classrooms, this Teacher Manual has been thoughtfully designed. It provides structured lesson plans for each chapter, guiding teachers through both classroom instruction and computer lab activities. Every lesson follows Uolo’s research-based WEBS framework, which simplifies teaching methodologies and enhances lesson delivery, making learning more engaging and impactful for students.
• Sharp Lesson Planning: Each lesson plan focuses on specific sub-learning outcomes within a chapter and are designed for delivery within the stipulated class or lab time.
• Real-life and Application-based Questions: Additional questions that link Computer Science to real-life contexts and assist teachers to develop learners' conceptual understanding and application skills.
• Support and Detailed Solutions: In-depth solutions for in-class and post-class activities to reinforce learning.
Uolo partners with K-12 schools to bring technology-based learning programs. We believe pedagogy and technology must come together to deliver scalable learning experiences that generate measurable outcomes. Uolo is trusted by over 15,000+ schools across India, South East Asia, and the Middle East.
ISBN 978-81-985754-3-2
